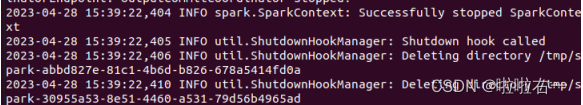
下载文件,64位主函数非常多循环
去控制流混淆,脚本下载deflat
用法
python 脚本名 文件名 起始地址
例如主函数地址是0x4007E0
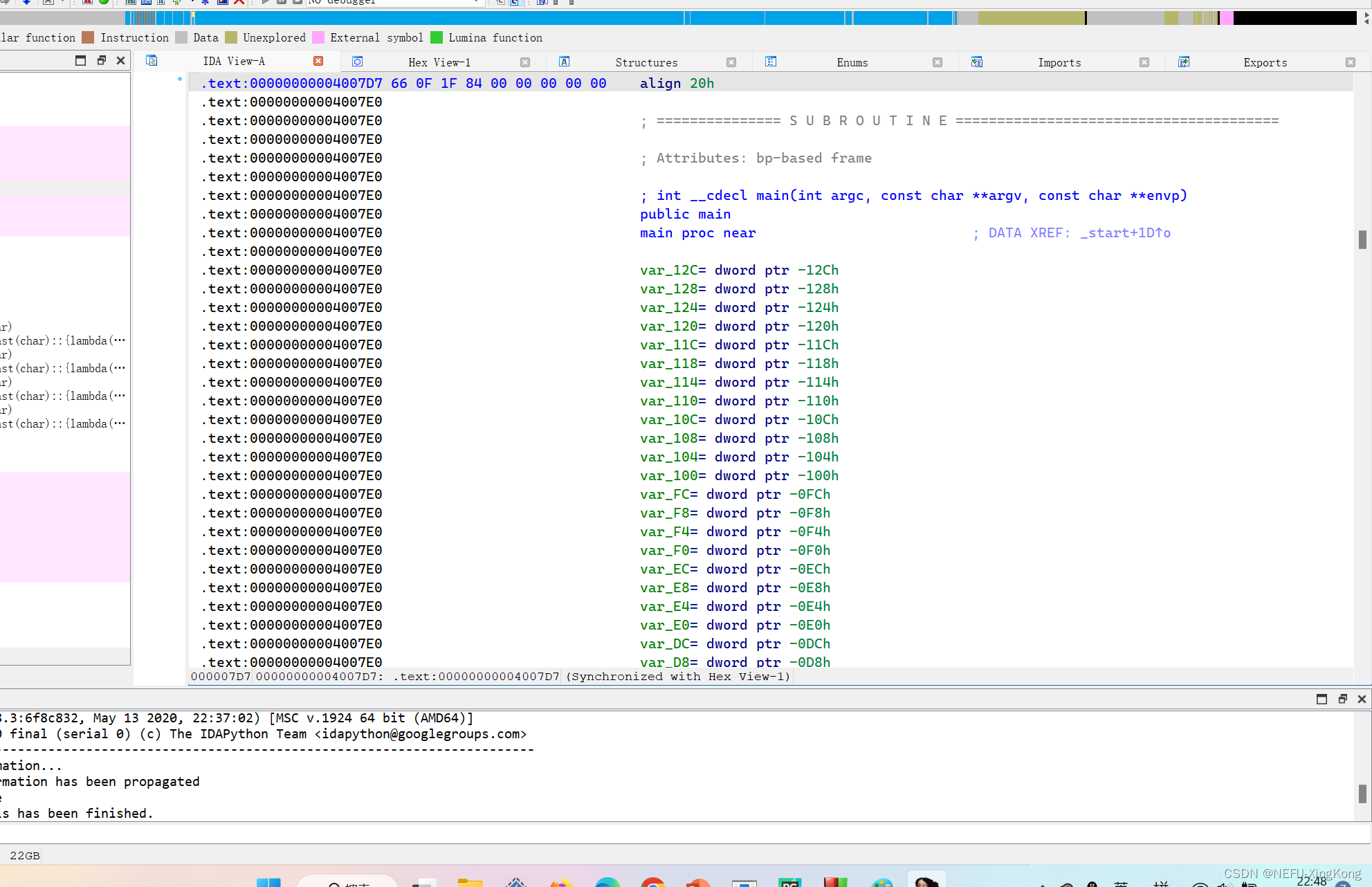
python deflat.py hardCpp 0x4007E0
然后就生成了去混淆的文件
主函数非常大,开始分析逻辑
puts("func(?)=\"01abfc750a0c942167651c40d088531d\"?");
输出01abfc750a0c942167651c40d088531d"?
s = getchar();
fgets(v24, 21, stdin);
然后输入字符串,其中第一个值给s,然后再给v24。
if ( y >= 10 && ((((_BYTE)x - 1) * (_BYTE)x) & 1) != 0 )
goto LABEL_13;
while ( 1 )
{
v20 = strlen(&s);
v34 = v20 != 21;
if ( y < 10 || ((((_BYTE)x - 1) * (_BYTE)x) & 1) == 0 )
break;
LABEL_13:
v20 = strlen(&s);
}
这里是个混淆,无论if跳不跳转,v20都等于s长度,注意s前面加了地址符&,
说明是地址,而s和v24的地址是连续的。所以v20本来应该为1,其实为21,不过v20的作用不大。,v34作用不大忽略
while ( 1 )
{
v19 = 1;
if ( y < 10 || ((((_BYTE)x - 1) * (_BYTE)x) & 1) == 0 )
break;
v19 = 1;
}
这里也有混淆,v19就是1
hile ( v19 < 21 )
{
if ( y >= 10 && ((((_BYTE)x - 1) * (_BYTE)x) & 1) != 0 )
{
v18 = v21 ^ v24[v19 - 1];
v17[0] = main::$_0::operator()(v27, (unsigned int)v18);
v16[0] = main::$_1::operator()(v25, (unsigned int)*(&s + v21 + v19 - 1));
v8 = main::$_1::operator() const(char)::{lambda(int)#1}::operator()(v16, 7LL);
v18 = main::$_0::operator() const(char)::{lambda(char)#1}::operator()(v17, (unsigned int)v8);
v15[0] = main::$_2::operator()(v28, (unsigned int)v18);
v14[0] = main::$_2::operator()(v28, (unsigned int)*(&s + v21 + v19 - 1));
v9 = main::$_2::operator() const(char)::{lambda(char)#1}::operator()(v14, 18LL);
v13[0] = main::$_3::operator()(v26, (unsigned int)v9);
v10 = main::$_3::operator() const(char)::{lambda(char)#1}::operator()(v13, 3LL);
v12[0] = main::$_0::operator()(v27, (unsigned int)v10);
v11 = main::$_0::operator() const(char)::{lambda(char)#1}::operator()(v12, 2LL);
v18 = main::$_2::operator() const(char)::{lambda(char)#1}::operator()(v15, (unsigned int)v11);
}
do
{
v18 = v21 ^ v24[v19 - 1];
v17[0] = main::$_0::operator()(v27, (unsigned int)v18);
v16[0] = main::$_1::operator()(v25, (unsigned int)*(&s + v21 + v19 - 1));
v3 = main::$_1::operator() const(char)::{lambda(int)#1}::operator()(v16, 7LL);
v18 = main::$_0::operator() const(char)::{lambda(char)#1}::operator()(v17, (unsigned int)v3);
v15[0] = main::$_2::operator()(v28, (unsigned int)v18);
v14[0] = main::$_2::operator()(v28, (unsigned int)*(&s + v21 + v19 - 1));
v4 = main::$_2::operator() const(char)::{lambda(char)#1}::operator()(v14, 18LL);
v13[0] = main::$_3::operator()(v26, (unsigned int)v4);
v5 = main::$_3::operator() const(char)::{lambda(char)#1}::operator()(v13, 3LL);
v12[0] = main::$_0::operator()(v27, (unsigned int)v5);
v6 = main::$_0::operator() const(char)::{lambda(char)#1}::operator()(v12, 2LL);
v18 = main::$_2::operator() const(char)::{lambda(char)#1}::operator()(v15, (unsigned int)v6);
}
while ( enc[v19 - 1] != v18 );
while ( y >= 10 && ((((_BYTE)x - 1) * (_BYTE)x) & 1) != 0 )
;
++v19;
}
接下来来到了重头戏了,共六个函数一个一个分析
main::$_0::operator()
char __fastcall main::$_0::operator()(__int64 a1, char a2)
{
return a2;
}
就是返回a2,我们把函数重命名为return_a2方便后续分析
main::$_1::operator() const(char)::{lambda(int)#1}::operator()
__int64 __fastcall main::$_1::operator() const(char)::{lambda(int)#1}::operator()(char *a1, int a2)
{
return (unsigned int)(*a1 % a2);
}
返回a1%a2,这里a2是常数7,命名为return_a1_mod_7
main::$_0::operator() const(char)::{lambda(char)#1}::operator()
__int64 __fastcall main::$_0::operator() const(char)::{lambda(char)#1}::operator()(__int64 a1, char a2)
{
int v2; // eax
int v3; // eax
char *v5; // [rsp+0h] [rbp-40h]
int v6; // [rsp+8h] [rbp-38h]
int v7; // [rsp+Ch] [rbp-34h]
int v8; // [rsp+10h] [rbp-30h]
int v9; // [rsp+14h] [rbp-2Ch]
char *v10; // [rsp+18h] [rbp-28h]
char v11; // [rsp+23h] [rbp-1Dh]
int v12; // [rsp+24h] [rbp-1Ch]
bool v13; // [rsp+2Ah] [rbp-16h]
bool v14; // [rsp+2Bh] [rbp-15h]
unsigned int v15; // [rsp+2Ch] [rbp-14h]
v13 = ((((_BYTE)x_5 - 1) * (_BYTE)x_5) & 1) == 0;
v14 = y_6 < 10;
v12 = 1023500310;
v11 = a2;
v10 = (char *)a1;
do
{
while ( 1 )
{
while ( 1 )
{
while ( 1 )
{
v9 = v12;
v8 = v12 + 2037067308;
if ( v12 != -2037067308 )
break;
v5 = v10;
*((_BYTE *)&v5 - 16) = v11;
v12 = -1418698808;
}
v7 = v9 + 1418698808;
if ( v9 != -1418698808 )
break;
v3 = -2037067308;
v5 = v10;
*((_BYTE *)&v5 - 16) = v11;
v15 = *((char *)&v5 - 16) + *v5;
if ( y_6 < 10 || ((((_BYTE)x_5 - 1) * (_BYTE)x_5) & 1) == 0 )
v3 = 1456142001;
v12 = v3;
}
v6 = v9 - 1023500310;
if ( v9 != 1023500310 )
break;
v2 = -2037067308;
if ( v14 || v13 )
v2 = -1418698808;
v12 = v2;
}
HIDWORD(v5) = v9 - 1456142001;
}
while ( v9 != 1456142001 );
return v15;
核心部分
v11 = a2;
v10 = (char *)a1;
v5 = v10;
*((_BYTE *)&v5 - 16) = v11;
v15 = *((char *)&v5 - 16) + *v5;
return v15;
就是返回a1+a2,命名return_a1_add_a2
main::$_2::operator()
核心部分
v12 = a2;
*((_BYTE *)&v5 - 16) = v12;
LOBYTE(v5) = *((_BYTE *)&v5 - 16);
v16 = v5;
return v16;
就是返回v5低位,就是a2re_a22
main::$_2::operator() const(char)::{lambda(char)#1}::operator()
return (unsigned int)(char)(a2 ^ *a1);
命名return_a1_XOR_a2
main::$_3::operator()
v12 = a2;
*((_BYTE *)&v5 - 16) = v12;
LOBYTE(v5) = *((_BYTE *)&v5 - 16);
v16 = v5;
return v16;
命名re_a2222
main::$_3::operator() const(char)::{lambda(char)#1}::operator()
return (unsigned int)(a2 * *a1);
return_a1_x_a2
六个大爹干完了,然后再对逻辑进行分析,就是一直变换,就是解方程
v18=v24[v19-1];
v17[0]=v18;//v17[0]=v24[v19-1];
v16[0]=s[v19-1];
v8=v16%7;//v8=s[v19-1]%7;
v18=v17+v8;//v18=v24[v19-1]+s[v19-1]%7;
v15[0]=v18;//v15[0]=v24[v19-1]+(s[v19-1]%7);
v14[0]=s[v19-1];
v9=v14^18;//v9=s[v19-1]^18;
v13[0]=v9;//v13[0]=s[v19-1]^18;
v10=v13*3;//v10=s[v19-1]^18*3;
v12[0]=v10;
v11=v12+2;//v11=s[v19-1]^18*3+2;
v18=v15^v11;//v18={v24[v19-1]+(s[v19-1]%7)}^{s[v19-1]^18*3+2}
一层一层代入就得到了v18={v24[v19-1]+(s[v19-1]%7)}^{(s[v19-1]^18)*3+2}
然后再与enc[v19 - 1]比较,然后v19加1。继续上述循环。
然后逆过去解方程
v24[v19-1]+(s[v19-1]%7)=v18^(s[v19-1]^18*3+2)
v24[v19-1]=(v18^(s[v19-1]^18*3+2))-(s[v19-1]%7)
这样就能得到每一位了。现在看开头
puts("func(?)=\"01abfc750a0c942167651c40d088531d\"?");
32位,盲猜md5加密,去进行解密,得到符号#,说明第一个字符是#,即知道了s[v19-1],v19=1;.又知道了v18即enc,我们就可以求出第二位,同理得到所有,脚本如下
enc=[0xF3, 0x2E, 0x18, 0x36, 0xE1, 0x4C, 0x22, 0xD1, 0xF9, 0x8C,
0x40, 0x76, 0xF4, 0x0E, 0x00, 0x05, 0xA3, 0x90, 0x0E, 0xA5]
lst=[35]
for i in range(len(enc)):
lst.append((((enc[i]^((lst[i]^18)*3+2)))-((lst[i]%7)))&0xff)
print(lst)
for i in lst:
print(chr(i),end='')
这里有个&0xff运算,防止数字溢出
得到flag