一、前言
目标是两台设备能通过OpenVPN TUN模式建立连接。
准备如下:
-
设备
友善R2S两台,一台做服务器,一台做客户端。
一台小米R1C,当作网关。 -
固件
采用openwrt-22.03版本,下载地址:https://downloads.openwrt.org/releases/22.03.5/targets/
也可以根据实际情况自行编译。 -
网络拓扑
小米R1C作为网关,用于配置端口转发。
网关下挂OpenVPN Server端,即Server端WAN口连接网关LAN口。
网关WAN口和Client端在同一网段,或者在不同网段,且保证Client端能够ping通服务端WAN口IP地址。 -
注意事项
三台设备要重新刷机,保持系统为默认、干净状态。
二、安装相应组件包
Server端和Client端分别安装对应组件,执行以下命令:
opkg update
opkg install openvpn-openssl openvpn-easy-rsa luci-app-openvpn
三、证书及密钥生成
证书及密钥只需要在Server侧生成即可。
-
easy-rsa目录处理
目录处理,输入以下命令:KEY_DIR=/etc/config/openvpn_easy-rsa mkdir -p $KEY_DIR ll /etc/easy-rsa/* mv /etc/easy-rsa/* $KEY_DIR ln -s $KEY_DIR/* /etc/easy-rsa ll /etc/easy-rsa/* -
easy-rsa var变量设置
/etc/easy-rsa/vars末尾添加以下内容并设置全局变量,直接执行以下命令:VARS="/etc/easy-rsa/vars" echo "" >> $VARS echo "set_var EASYRSA_REQ_COUNTRY \"CN\"" >> $VARS echo "set_var EASYRSA_REQ_PROVINCE \"Beijing\"" >> $VARS echo "set_var EASYRSA_REQ_CITY \"Haidian\"" >> $VARS echo "set_var EASYRSA_REQ_ORG \"IT\"" >> $VARS echo "set_var EASYRSA_REQ_EMAIL \"IT\"" >> $VARS echo "set_var EASYRSA_REQ_OU \"IT\"" >> $VARS echo "" >> $VARS echo "set_var EASYRSA_KEY_SIZE 2048" >> $VARS cat $VARS source $VARS执行完
source $VARS后,会出现以下打印:root@OpenWrt:~# source $VARS You appear to be sourcing an Easy-RSA 'vars' file. This is no longer necessary and is disallowed. See the section called 'How to use this file' near the top comments for more details. root@OpenWrt:~#设置EasyRAS变量,输入以下命令:
export EASYRSA_PKI="/etc/easy-rsa/pki" export EASYRSA_REQ_CN="ovpnca" export EASYRSA_BATCH="1" -
初始化pki目录
输入以下命令:cd /etc/easy-rsa easyrsa init-pki -
生成Diffie-Hellman pem并打印
输入以下命令:cd /etc/easy-rsa easyrsa gen-dh cat /etc/easy-rsa/pki/dh.pem此步骤耗时可能会比较长,请耐心等待。
-
生成ca证书及密钥并打印
输入以下命令:cd /etc/easy-rsa easyrsa build-ca nopass cat /etc/easy-rsa/pki/ca.crt -
生成Server证书及密钥并打印
输入以下命令:cd /etc/easy-rsa easyrsa build-server-full server nopass cat /etc/easy-rsa/pki/private/server.key -
生成Client证书及密钥并打印
输入以下命令:
cd /etc/easy-rsa easyrsa build-client-full client nopass cat /etc/easy-rsa/pki/private/client.key -
生成tls密钥并打印
输入以下命令:
cd /etc/easy-rsa openvpn --genkey --secret ${EASYRSA_PKI}/tc.pem cat /etc/easy-rsa/pki/tc.pem
四、OpenVPN Server配置
以下操作都在第一台R2S路由器上面执行,我们称这台路由器为Server端。
-
Server防火墙默认配置修改
规则全部改为
ACCEPT,输入以下命令查看防火墙当前默认配置:uci show firewall | grep defaults会有如下打印:
firewall.@defaults[0]=defaults firewall.@defaults[0].syn_flood='1' firewall.@defaults[0].input='ACCEPT' firewall.@defaults[0].output='ACCEPT' firewall.@defaults[0].forward='REJECT'我们需要将
firewall.@defaults[0].forward='REJECT'改为firewall.@defaults[0].forward='ACCEPT'输入以下命令:
uci set firewall.@defaults[0].forward='ACCEPT'同理修改LAN口和WAN口的配置,输入以下命令查看防火墙当前默认配置:
uci show firewall | grep zone会有如下打印:
firewall.@zone[0]=zone firewall.@zone[0].name='lan' firewall.@zone[0].network='lan' firewall.@zone[0].input='ACCEPT' firewall.@zone[0].output='ACCEPT' firewall.@zone[0].forward='ACCEPT' firewall.@zone[1]=zone firewall.@zone[1].name='wan' firewall.@zone[1].network='wan' 'wan6' firewall.@zone[1].input='REJECT' firewall.@zone[1].output='ACCEPT' firewall.@zone[1].forward='REJECT' firewall.@zone[1].masq='1' firewall.@zone[1].mtu_fix='1'将
firewall.@zone[1].input='REJECT'改为firewall.@zone[1].input='ACCEPT';将
firewall.@zone[1].forward='REJECT'改为firewall.@zone[1].forward='ACCEPT'。输入以下命令:
uci set firewall.@zone[1].input='ACCEPT' uci set firewall.@zone[1].forward='ACCEPT'执行以下命令更新防火墙配置:
uci commit firewall /etc/init.d/firewall restart -
VPN端口协议及防火墙配置
定义VPN服务端传输协议及端口,输入以下命令:
OVPN_PORT="11194" OVPN_PROTO="udp"防火墙内添加
tun+设备接口,输入以下命令:uci rename firewall.@zone[0]="lan" uci rename firewall.@zone[1]="wan" uci del_list firewall.lan.device="tun+" uci add_list firewall.lan.device="tun+" uci -q delete firewall.ovpn根据传输协议及端口对防火墙进行配置,执行以下命令:
uci set firewall.ovpn="rule" uci set firewall.ovpn.name="Allow-OpenVPN" uci set firewall.ovpn.src="wan" uci set firewall.ovpn.dest_port="${OVPN_PORT}" uci set firewall.ovpn.proto="${OVPN_PROTO}" uci set firewall.ovpn.target="ACCEPT"更新防火墙配置并查看配置参数,执行以下命令
uci commit firewall /etc/init.d/firewall restart uci show firewall.ovpn cat /proc/sys/net/ipv4/ip_forward -
接口创建及信息完善
创建一个名为ovpn_server的vpn接口,输入以下命令:export EASYRSA_PKI="/etc/easy-rsa/pki" uci set openvpn.ovpn_server="openvpn" uci set openvpn.ovpn_server.enabled="1" uci set openvpn.ovpn_server.dev="tun" uci set openvpn.ovpn_server.port="11194" uci set openvpn.ovpn_server.proto="udp" uci set openvpn.ovpn_server.comp_lzo="no" uci set openvpn.ovpn_server.log="/tmp/openvpn.log" uci set openvpn.ovpn_server.status="/tmp/openvpn.status" uci set openvpn.ovpn_server.verb="3" uci set openvpn.ovpn_server.mute="5" uci set openvpn.ovpn_server.keepalive="10 60" uci set openvpn.ovpn_server.persist_key="1" uci set openvpn.ovpn_server.persist_tun="1" uci set openvpn.ovpn_server.user="nobody" uci set openvpn.ovpn_server.group="nogroup" uci set openvpn.ovpn_server.ca="${EASYRSA_PKI}/ca.crt" uci set openvpn.ovpn_server.cert="${EASYRSA_PKI}/issued/server.crt" uci set openvpn.ovpn_server.dh="${EASYRSA_PKI}/dh.pem" uci set openvpn.ovpn_server.key="${EASYRSA_PKI}/private/server.key" uci set openvpn.ovpn_server.mode="server" uci set openvpn.ovpn_server.server="192.168.0.0 255.255.255.0" uci set openvpn.ovpn_server.tls_server="1" uci set openvpn.ovpn_server.topology="subnet" uci set openvpn.ovpn_server.route_gateway="dhcp" uci set openvpn.ovpn_server.client_to_client="1" uci commit openvpn uci add_list openvpn.ovpn_server.push="comp-lzo no" uci add_list openvpn.ovpn_server.push="persist-key" uci add_list openvpn.ovpn_server.push="persist-tun" uci add_list openvpn.ovpn_server.push="user nobody" uci add_list openvpn.ovpn_server.push="user nogroup" uci add_list openvpn.ovpn_server.push="topology subnet" uci add_list openvpn.ovpn_server.push="route-gateway dhcp" uci add_list openvpn.ovpn_server.push="redirect-gateway def1" uci add_list openvpn.ovpn_server.push="192.168.0.0 255.255.255.0" uci add_list openvpn.ovpn_server.push="dhcp-option DNS 9.9.9.9" uci add_list openvpn.ovpn_server.push="dhcp-option DNS 1.1.1.1" uci commit openvpn -
VPN服务使能
查看ovpn_server和防火墙配置,输入以下命令:uci show openvpn.ovpn_server uci show firewall.ovpn使能
ovpn_server服务器以及启动此服务,输入以下命令:/etc/init.d/openvpn enable /etc/init.d/openvpn start -
Server侧状态及log确认
查看ovpn_server启动状态,输入以下命令:pgrep -f -a openvpn有类似以下打印说明服务已启动:
root@OpenWrt:/# pgrep -f -a openvpn 2812 /usr/sbin/openvpn --syslog openvpn(ovpn_server) --status /var/run/openvpn.ovpn_server.status --cd /var/etc --config openvpn-ovpn_server.conf --up /usr/libexec/openvpn-hotplug up ovpn_server --down /usr/libexec/openvpn-hotplug down ovpn_server --script-security 2 root@OpenWrt:/#查看Server vpn log及状态log,输入以下命令:
cat /tmp/openvpn.log cat /tmp/openvpn.status有类似以下打印说明成功:
root@OpenWrt:/# root@OpenWrt:/# cat /tmp/openvpn.log 2023-08-08 01:57:40 --cipher is not set. Previous OpenVPN version defaulted to BF-CBC as fallback when cipher negotiation failed in this case. If you need this fallback please add '--data-ciphers-fallback BF-CBC' to your configuration and/or add BF-CBC to --data-ciphers. 2023-08-08 01:57:40 OpenVPN 2.5.7 aarch64-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] 2023-08-08 01:57:40 library versions: OpenSSL 1.1.1u 30 May 2023, LZO 2.10 2023-08-08 01:57:40 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts 2023-08-08 01:57:40 Diffie-Hellman initialized with 2048 bit key 2023-08-08 01:57:40 TUN/TAP device tun0 opened 2023-08-08 01:57:40 /sbin/ip link set dev tun0 up mtu 1500 2023-08-08 01:57:40 /sbin/ip link set dev tun0 up 2023-08-08 01:57:40 /sbin/ip addr add dev tun0 192.168.0.1/24 2023-08-08 01:57:40 /usr/libexec/openvpn-hotplug up ovpn_server tun0 1500 1622 192.168.0.1 255.255.255.0 init 2023-08-08 01:57:40 Could not determine IPv4/IPv6 protocol. Using AF_INET 2023-08-08 01:57:40 Socket Buffers: R=[212992->212992] S=[212992->212992] 2023-08-08 01:57:40 UDPv4 link local (bound): [AF_INET][undef]:1193 2023-08-08 01:57:40 UDPv4 link remote: [AF_UNSPEC] 2023-08-08 01:57:40 GID set to nogroup 2023-08-08 01:57:40 UID set to nobody 2023-08-08 01:57:40 MULTI: multi_init called, r=256 v=256 2023-08-08 01:57:40 IFCONFIG POOL IPv4: base=192.168.0.2 size=253 2023-08-08 01:57:40 Initialization Sequence Completed root@OpenWrt:/# root@OpenWrt:/# cat /tmp/openvpn.status OpenVPN CLIENT LIST Updated,2023-08-08 02:00:42 Common Name,Real Address,Bytes Received,Bytes Sent,Connected Since ROUTING TABLE Virtual Address,Common Name,Real Address,Last Ref GLOBAL STATS Max bcast/mcast queue length,0 END root@OpenWrt:/# root@OpenWrt:/#执行
ifconfig命令后,能够看到显示的信息中有tun0接口,如下:tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 inet addr:192.168.0.1 P-t-P:192.168.0.1 Mask:255.255.255.0 inet6 addr: fe80::5c0:4e74:d46b:8601/64 Scope:Link UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1 RX packets:0 errors:0 dropped:0 overruns:0 frame:0 TX packets:4 errors:0 dropped:0 overruns:0 carrier:0 collisions:0 txqueuelen:500 RX bytes:0 (0.0 B) TX bytes:304 (304.0 B) -
LAN侧默认网关修改
由于OpenWrt LAN侧默认网关为192.168.1.1,通过Luci界面将其修改为其它网段,这儿修改为192.168.12.1。
修改原因是OpenVPN建立隧道后,在每个私有网络中,确保私有网络内的主机具有对方私有网络的IP地址和子网掩码,以便它们可以相互通信。
五、OpenVPN Client配置
以下操作都在第二台R2S路由器上面执行,我们称这台路由器为Client端。
- 配置文件设置
创建/root/vpn并且在此文件夹下创建client.conf文件,输入以下命令:mkdir -p /root/vpn vi /root/vpn/client.confclient.conf里面输入以下信息:
其中,auth-nocache client comp-lzo no dev tun mute 10 nobind persist-key persist-tun proto udp remote 192.168.2.200 11194 remote-cert-tls server resolv-retry infinite script-security 1 verb 3 log-append /tmp/openvpn.log status /tmp/openvpn.status <key> # Insert here the client's generated private key from: # cat /etc/easy-rsa/pki/private/client.key </key> <cert> # Insert here the client's generated certificate from: # cat /etc/easy-rsa/pki/issued/client.crt </cert> <ca> # Place here the server's generated certificate from: # cat /etc/easy-rsa/pki/ca.crt </ca>remote 192.168.2.200 11194中192.168.2.200表示网关的IP地址,即网关WAN口地址。将Server生成的证书密钥按照要求填写到配置文件最后的key/cert/ca中。 - Client防火墙默认配置修改
Client侧的修改方式同Server侧一样,输入以下命令即可:
执行以下命令更新防火墙配置:uci set firewall.@defaults[0].forward='ACCEPT' uci set firewall.@zone[1].input='ACCEPT' uci set firewall.@zone[1].forward='ACCEPT'uci commit firewall /etc/init.d/firewall restart - 配置文件修改及服务使能
打开openvpn配置文件,输入以下命令:
修改vi /etc/config/openvpnconfig openvpn custom_config里面的配置:
将option enabled 0改为option enabled 1;
将option config /etc/openvpn/my-vpn.conf改为option config /etc/openvpn/my-vpn.conf;
修改后的配置文件如下:
输入以下命令启动客户端vpn服务:package openvpn ################################################# # Sample to include a custom config file. # ################################################# config openvpn custom_config # Set to 1 to enable this instance: option enabled 1 # Credentials to login #option username 'login' #option password 'password' # Password for client certificate #option cert_password 'cert_password' # Include OpenVPN configuration option config /root/vpn/client.conf/etc/init.d/openvpn enable /etc/init.d/openvpn start - Client侧状态及log确认
同Server侧一样,查看方式为:pgrep -f -a openvpn cat /tmp/openvpn.log cat /tmp/openvpn.status
六、网关配置
-
网络拓扑
小米R1C网关WAN侧地址192.168.2.200。
小米R1C网关LAN侧地址192.168.50.1。
友善R2S Server侧WAN口接小米R1C网关LAN口,R2S Server WAN口地址为192.168.50.201。
友善R2S Client侧WAN口和小米R1C网关WAN口为同一网段,R2S Client WAN口地址为192.168.2.116。 -
网关防火墙配置
浏览器输入192.168.50.1登录网关,选择【网络】->【防火墙】打开防火墙配置,如下图:
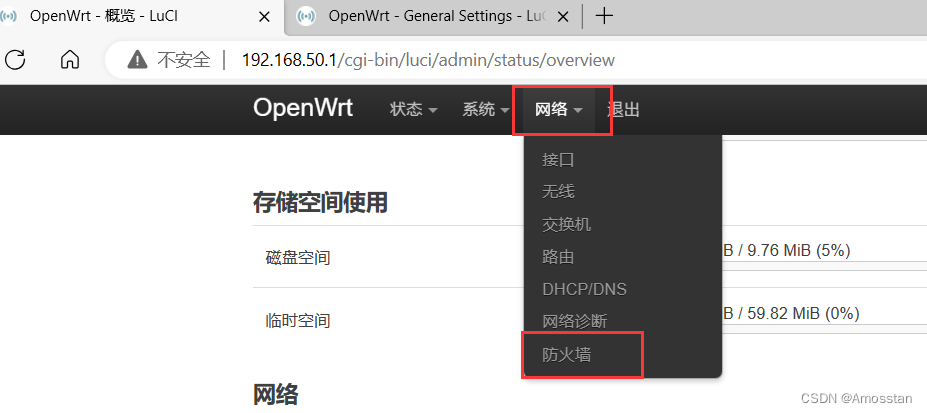
防火墙具体配置见下图画红框的部分:![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-2v3JYLm5-1692177001052)(C:\Users\xuyanbin\AppData\Roaming\Typora\typora-user-images\image-20230816170351323.png)]](https://img-blog.csdnimg.cn/562414cca68c41b2bd91b41bc1ee6c5a.png)
注意上图中【WAN => 】侧的编辑里面的一个配置项【MSS clamping】也要勾选,配置完后检测网关的防火墙设置是否和上图一样,如果一样,点击【保存并应用】。 -
网关端口转发配置
在上一步骤网关防火墙配置的基础上,点击选择【网络】->【防火墙】->【Port Forwards】-> 【添加】配置端口转发,如下图:
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-KkWFuByr-1692177001054)(C:\Users\xuyanbin\AppData\Roaming\Typora\typora-user-images\image-20230816170426335.png)]](https://img-blog.csdnimg.cn/345f02f7237146f48f077e1f686ea0fe.png)
弹出配置界面,按以下配置:![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-YHqMeRUr-1692177001054)(C:\Users\xuyanbin\AppData\Roaming\Typora\typora-user-images\image-20230816170434820.png)]](https://img-blog.csdnimg.cn/bc75bdb3e7cb491686417e910aa618ed.png)
说明:
名称填写vpn_tun
External port填写外部端口即Client侧的端口11194
Internal adress填写内部Server WAN侧的IP地址,192.168.50.201
Internal port填写内部Server侧的端口11194
配置完成后点击【保存】返回到上一层页面,确认配置无误后,点击【保存并应用】,如下图:
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-riM9ZiKU-1692177001055)(C:\Users\xuyanbin\AppData\Roaming\Typora\typora-user-images\image-20230816170524798.png)]](https://img-blog.csdnimg.cn/3594fadc58914a3fa76546a9305b6eda.png)
七、测试
先重启服务端再重启客户端。
Client侧输入ifconfig tun0,如果tun0有IP显示,则说明VPN隧道建立成功,如下所示:
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:192.168.0.2 P-t-P:192.168.0.2 Mask:255.255.255.0
inet6 addr: fe80::762a:9b34:4ee9:edb7/64 Scope:Link
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:2631 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:500
RX bytes:0 (0.0 B) TX bytes:176649 (172.5 KiB)
如果关闭网关的端口转发或者关掉Server侧的OpenVPN服务,Client侧执行ifconfig命令则不会有tun0设备。
八、参考
https://github.com/OpenVPN/openvpn/
https://openwrt.org/docs/guide-user/services/vpn/openvpn/start