参考https://www.freebuf.com/articles/endpoint/335030.html
测试固件 https://service.tp-link.com.cn/detail_download_7989.html
固件提取
binwalk解压固件,在第一部分即为要分析的二进制文件,可以拖进ida分析
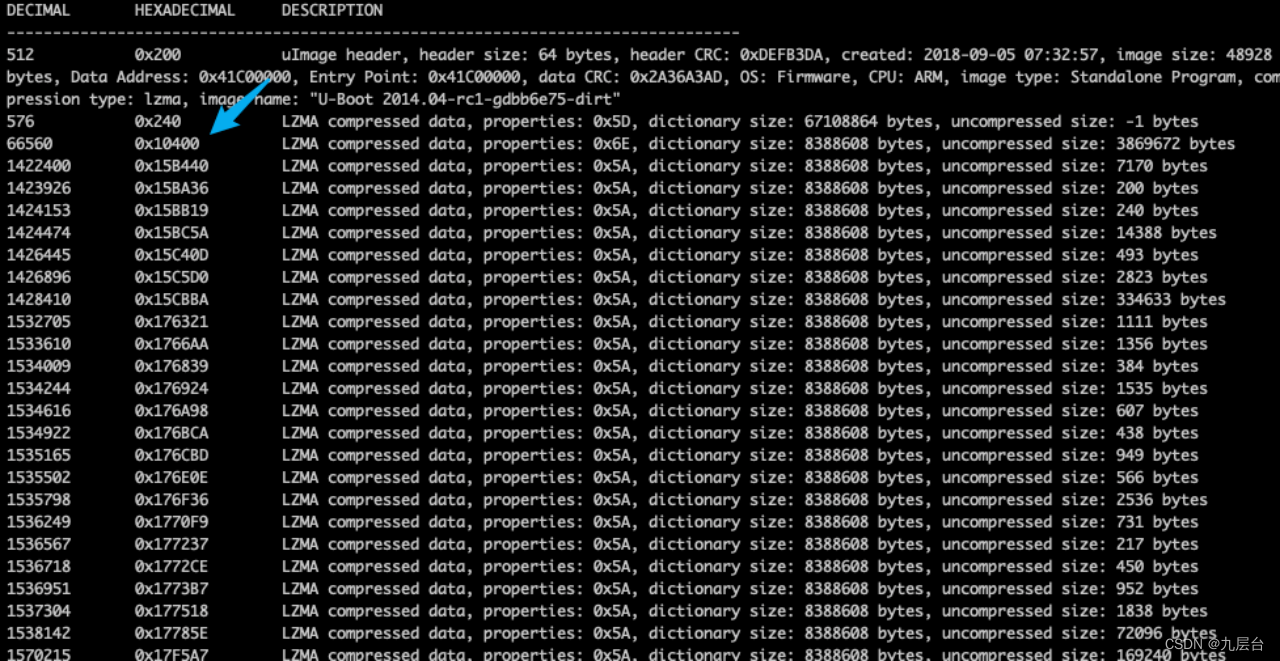
设置为arm小端字节序,点set
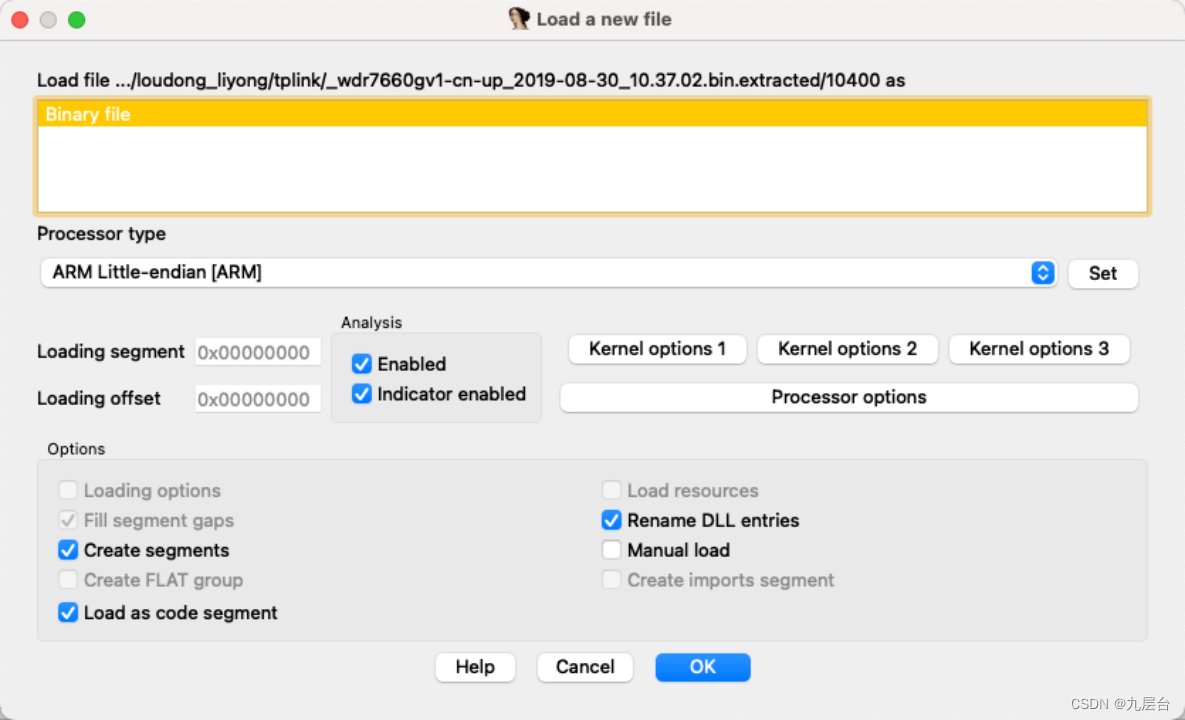
随便选择加载地址
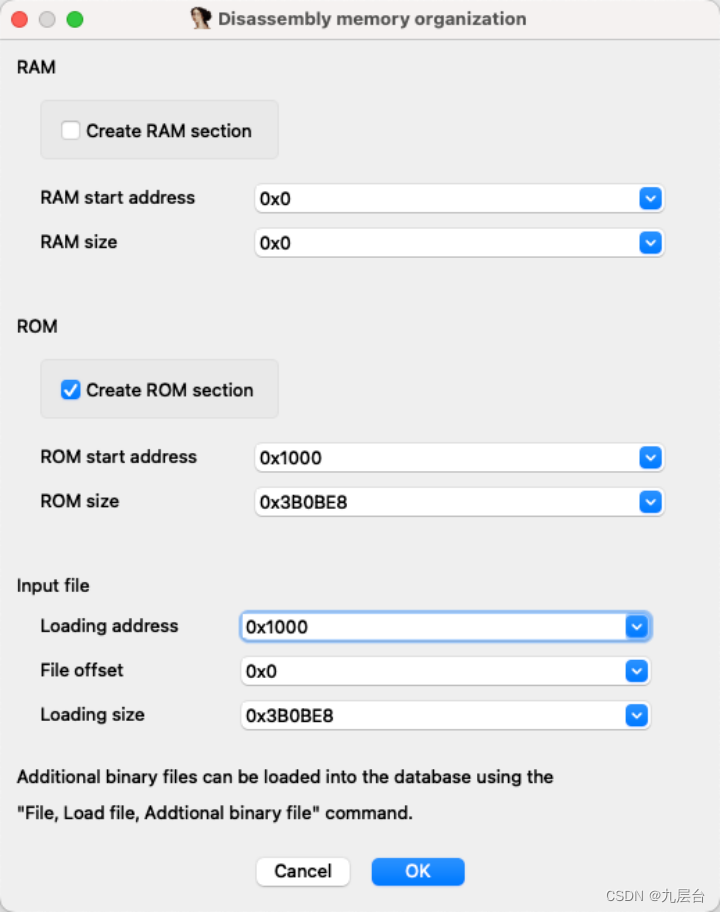
进来之后可以看到真正的加载地址
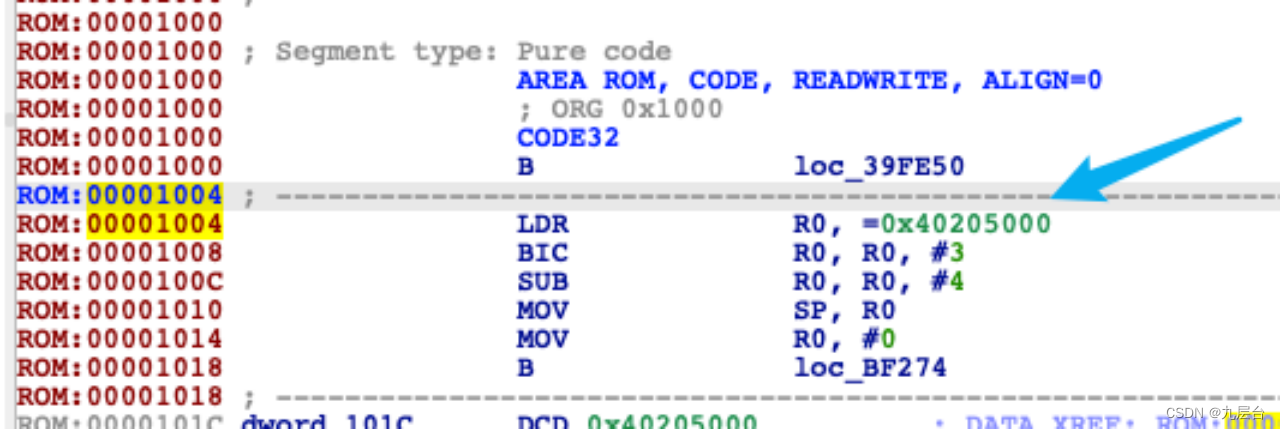
修复符号
VxWorks采用usrInit进行栈初始化,usrInit是VxWorks系统引导后运行的第一个函数。调用bzero函数对bss区的数据进行清零。
binwalk 解压得到所有内容,通过grep 搜索符号表
grep -nr "bzero" .
xxd得到对应的十六进制数
xxd -g 1 -u ./15CBBA >15CBBA.chr
确定符号表中符号的偏移,通过出现连续字符串的开始,即0x001a728
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-yNAqux7c-1691033042845)(https://secure2.wostatic.cn/static/nwoxbBWYMvVEe5bDYJ13iG/image.png?auth_key=1691033035-jSmBWdaxkSDidDnxYhjrqb-0-ae27733d97336f8f2c6794e7ad3842ce)]
在该文件的开头记录着符号表的偏移,54对应flag,0x40373684对应AES_CMAC的偏移

使用idapython脚本恢复符号表
- 重定位加载地址
- 读取符号表文件,定位到对应偏移分别得到地址和符号名
- 创建函数并设置函数名
from idaapi import *
import idc
def has_symbol(address):
symbol_name = idc.get_name(address)
return bool(symbol_name)
def read_symbol_table(filename, symbol_address_offset,symbol_offset):
with open(filename, "rb") as f:
f.seek(symbol_address_offset)
content=f.read()
with open(filename, "rb") as f:
f.seek(symbol_offset)
content_symbol=f.read()
symbol_address=[]
for item in range(0,len(content),8):
if item>=symbol_offset:
break
symbol_data = content[item:item+4] # Assuming 32-bit address, change the size as needed
symbol_address.append(int.from_bytes(symbol_data, byteorder="big"))
symbol_list=content_symbol.split(b"\x00")
print("found address,symbol len",len(symbol_address),len(symbol_list))
for a,s in zip(symbol_address,symbol_list):
yield (a,s)
def create_symbol(symbol_address, symbol_name):
add_func(symbol_address)
idc.set_name(symbol_address, symbol_name.decode(), SN_NOCHECK)
def init(ida_load_addr):
rebase_program(ida_load_addr,8) # 测试时ida会根据前一次的地址加上这个偏移得到基地址,刚开始设置为0,只执行一次即可
def main():
filename = "/Users/guosiyu/Desktop/aiwencode/loudong_liyong/tplink/_wdr7660gv1-cn-up_2019-08-30_10.37.02.bin.extracted/15CBBA"
current_base=get_imagebase()
ida_load_addr=0x40205000-current_base
symbol_address_offset = 0xc # Offset where the symbol address is located in the file
symbol_offset = 0x001a728 # Offset of the symbol in the file
init(ida_load_addr)
auto_wait()
for addr,symbol in read_symbol_table(filename, symbol_address_offset,symbol_offset):
print("found address,symbol:",hex(addr),symbol)
if(has_symbol(addr)):
continue
create_symbol(addr, symbol)
# symbol_address = base_address + symbol_address_offset
# symbol_name = "your_symbol_name" # Replace this with the desired symbol name
# print(f"Created symbol: {symbol_name} at address: 0x{symbol_address:08X}")
if __name__ == "__main__":
main()
补充
工具 https://github.com/PAGalaxyLab/vxhunter好像也可以,未测试