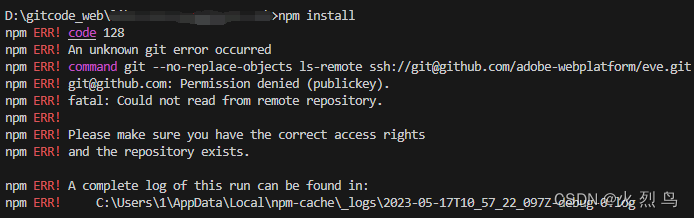
1.查壳
32位文件,加了UPX壳

2.手动脱壳
使用Ollydbg
UPX是一个压缩壳,运行了UPX将我们要运行的已经压缩的程序解压,才是真正的程序入口点OEP
我们需要将跟着汇编代码,找到程序真正的入口点
使用ESP定律可以快速定位
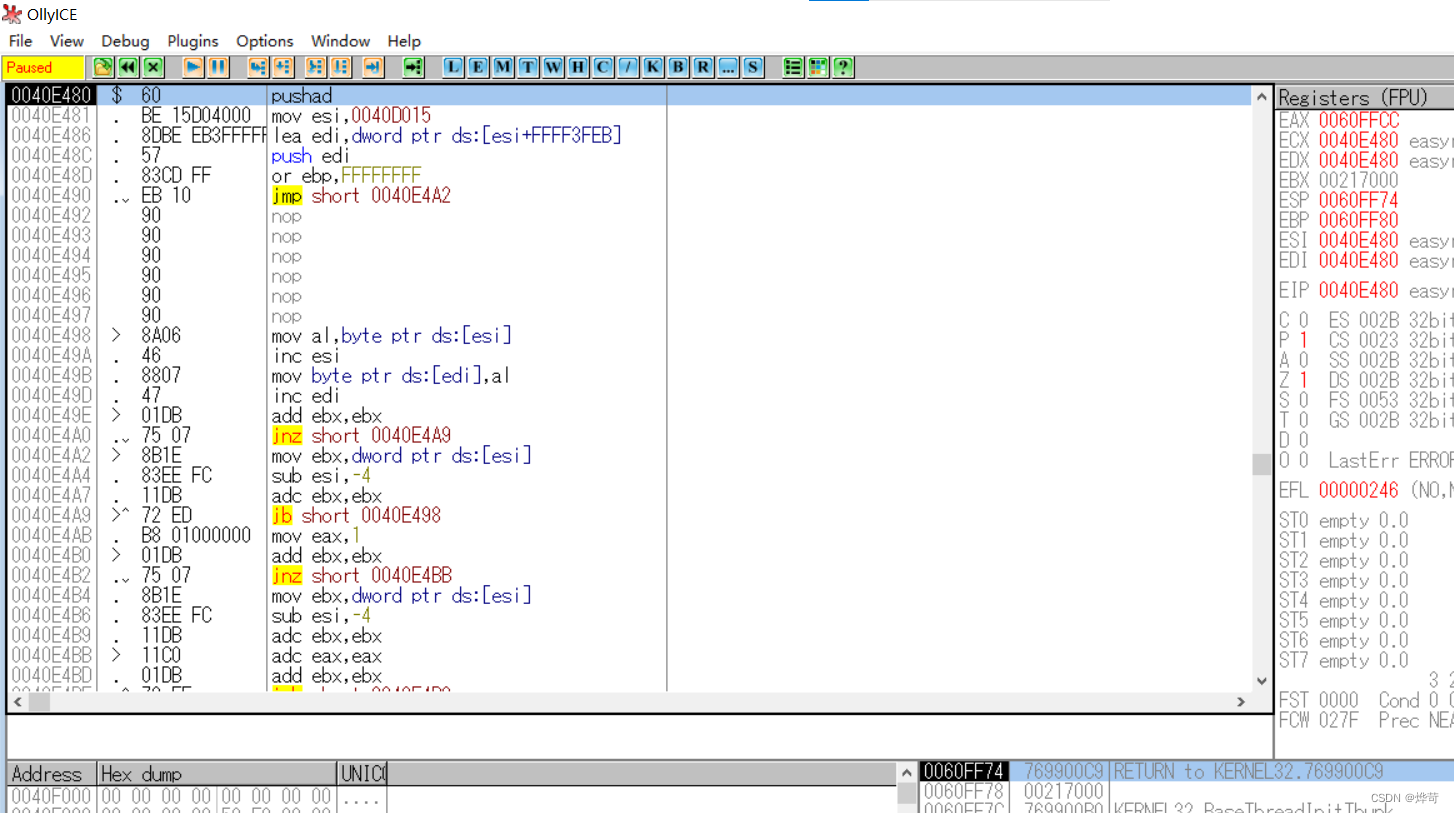
按下F7,单步运行程序
运行了一步之后,发现右侧只有ESP标红了



跟踪,选择任意长的数据,打下硬件断点
按下F9运行,断下来的位置就是程序真正的入口点

在此处重建PE文件
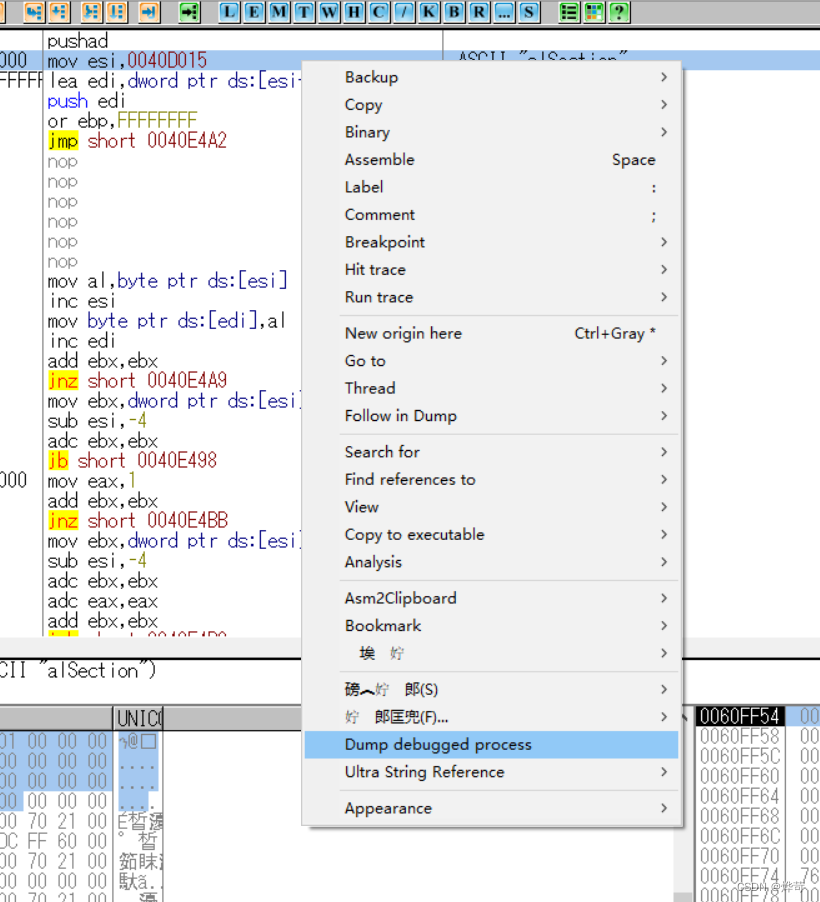

点击dump就可以了
3.IDA分析

Shift+F12打开字符串窗口

跟踪可疑字符串

找到主函数
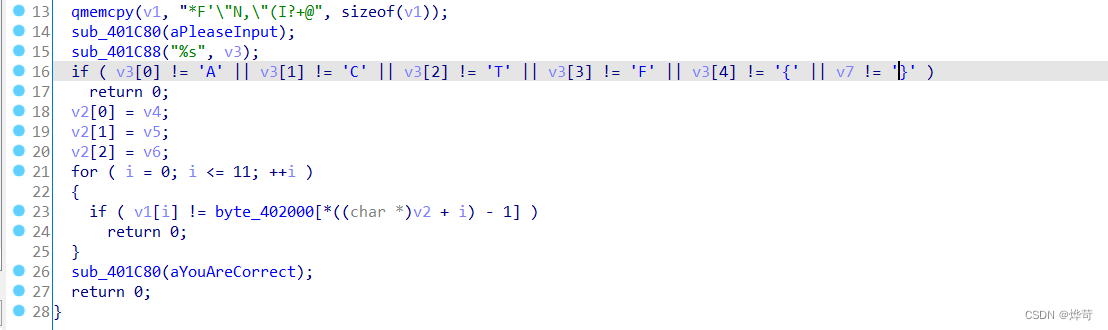 在数据处按下R,获得了对应的ASCII,是ACTF{},是一个flag的格式
在数据处按下R,获得了对应的ASCII,是ACTF{},是一个flag的格式
然后剩余的flag部分减一后如果与存储的v1数组相同就是正确的flag
v1在上面由qmemcpy赋值
获得v1的值,编写脚本
v1 = [42,70,39,34,78,44,34,40,73,63,43,64]
//v1数组
byte_402000=[0x7e,0x7d,0x7c,0x7b,0x7a,0x79,0x78,0x77,0x76,0x75,0x74,0x73,0x72,0x71,0x70,0x6f,0x6e,0x6d,0x6c,0x6b,0x6a,0x69,0x68,0x67,0x66,0x65,0x64,0x63,0x62,0x61,0x60,0x5f,0x5e,0x5d,0x5c,0x5b,0x5a,0x59,0x58,0x57,0x56,0x55,0x54,0x53,0x52,0x51,0x50,0x4f,0x4e,0x4d,0x4c,0x4b,0x4a,0x49,0x48,0x47,0x46,0x45,0x44,0x43,0x42,0x41,0x40,0x3f,0x3e,0x3d,0x3c,0x3b,0x3a,0x39,0x38,0x37,0x36,0x35,0x34,0x33,0x32,0x31,0x30,0x2f,0x2e,0x2d,0x2c,0x2b,0x2a,0x29,0x28,0x27,0x26,0x25,0x24,0x23,0x20,0x21,0x22,0x00]
//byte_402000
flag=""
for i in v1:
flag+=chr(byte_402000.index(i)+1)
print(flag)flag{U9X_1S_W6@T?}