概述
选择题 50 分(原题率 80%):http://tieba.baidu.com/p/1250021454?&share=9105&fr=sharewise&unique=967707B1DAECEF4A785B61D29AF36950&st=1639102957&client_type=1&client_version=12.10.1&sfc=copy&share_from=post
1
程序执行的六个过程
E d i t → P r e P r o c e s s → C o m p i l e → L i n k → L o a d → E x e c u t e {\rm Edit} \space \rightarrow \space {\rm Pre \space Process} \space \rightarrow \space {\rm Compile} \space \rightarrow \space {\rm Link} \space \rightarrow \space {\rm Load} \space \rightarrow \space {\rm Execute} Edit → Pre Process → Compile → Link → Load → Execute
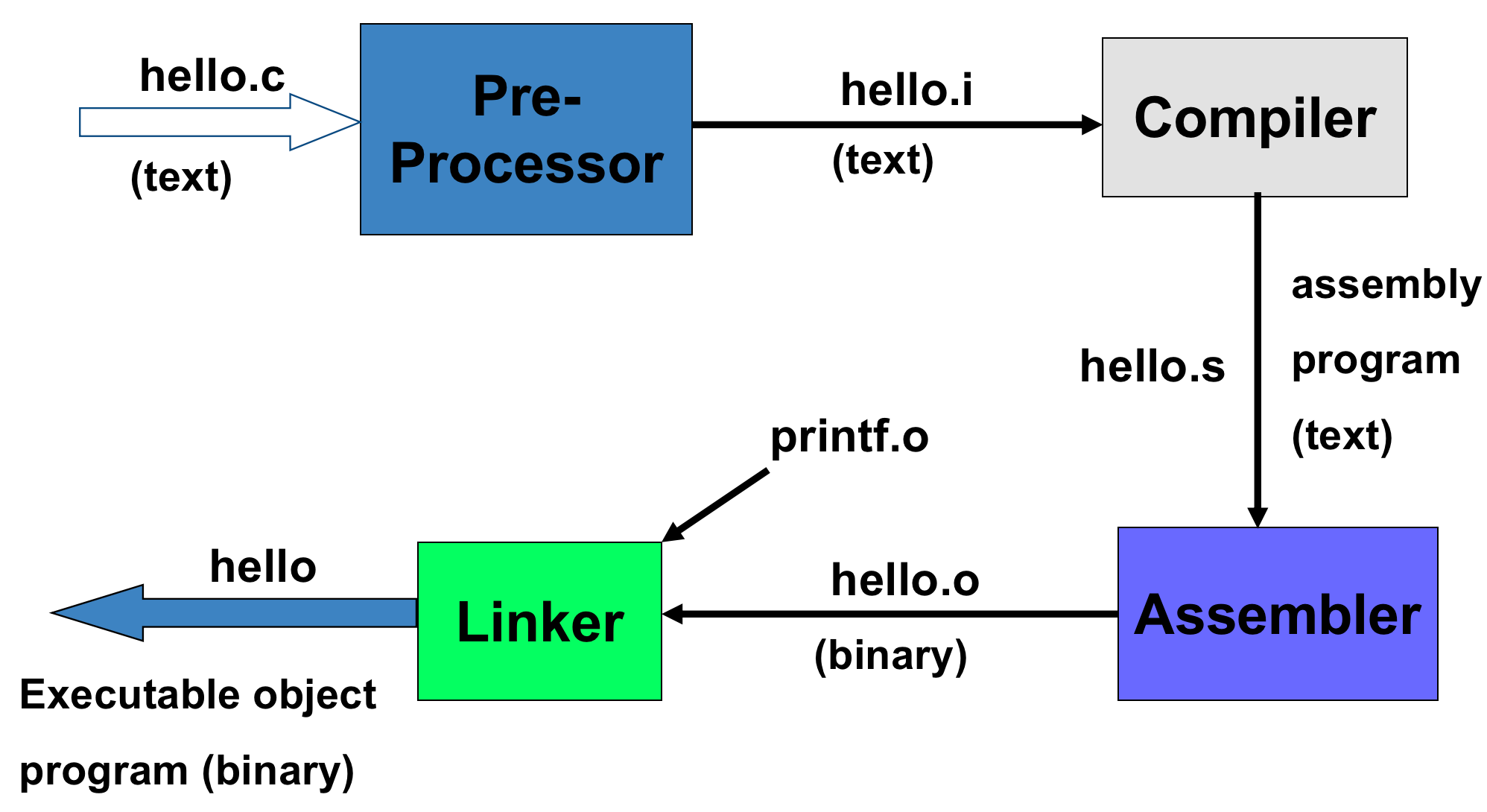
2
浮点数编码
Fixed Point Natation
使用 . . . 分割整数部分与小数部分
- 例如: 5.7 5 10 = 101.1 1 2 5.75_{10} = 101.11_2 5.7510=101.112
有理数的表示: ∑ k = − j i b k ⋅ 2 k \displaystyle \sum^i_{k=-j} b_k \cdot2^k k=−j∑ibk⋅2k
BCD - Binary Coded Decimal
每个十进制的数字使用 4 bit 的二进制数存储
Decimal: 0 1 2 3 4 5 6 7 8 9
BCD: 0000 0001 0010 0011 0100 0101 0110 0111 1000 1001
Decimal: 127.33
BCD: 0001 0010 0111 .0011 0011
IEEE Floating Point
使用 V = ( − 1 ) s × M × 2 E V=(-1)^s \times M \times 2^E V=(−1)s×M×2E 表示一个数:
- 符号(sign):
s
s
s 决定这个数是负数(
s
=
1
s=1
s=1)还是正数(
s
=
0
s=0
s=0)
- 对于数值 0 0 0 的符号位解释作为特殊情况处理
- 尾数(significand)
M
M
M 是一个二进制小数
- 范围: 1 ∼ 2 − ϵ 1 \sim 2-\epsilon 1∼2−ϵ 或 0 ∼ 1 − ϵ 0 \sim 1 - \epsilon 0∼1−ϵ
- 阶码(exponent)
E
E
E 的作用是对浮点数加权
- 权重是 2 2 2 的 E E E 次幂(可能是负数)
将浮点数的位表示划分为三个字段,分别对这些值进行编码:
- 一个单独的符号位 s s s 直接编码符号 s s s
- k k k 位的阶码字段 e x p = e k − 1 ⋯ e 1 e 0 exp=e_{k-1} \cdots e_1 e_0 exp=ek−1⋯e1e0 编码阶码 E E E
-
n
n
n 位小数字段
f
r
a
c
=
f
n
−
1
⋯
f
1
f
0
frac=f_{n-1} \cdots f_1 f_0
frac=fn−1⋯f1f0 编码尾数
M
M
M
- 编码出来的值 M M M 依赖于阶码字段 E E E 的值是否等于 0 0 0
单精度浮点数(float,
32
32
32 bits):
s
=
1
&
k
=
8
&
n
=
32
s=1 \space \space \& \space \space k=8 \space \space \& \space \space n=32
s=1 & k=8 & n=32
双精度浮点数(double,
64
64
64 bits):
s
=
1
&
k
=
11
&
n
=
52
s=1 \space \space \& \space \space k=11 \space \space \& \space \space n=52
s=1 & k=11 & n=52
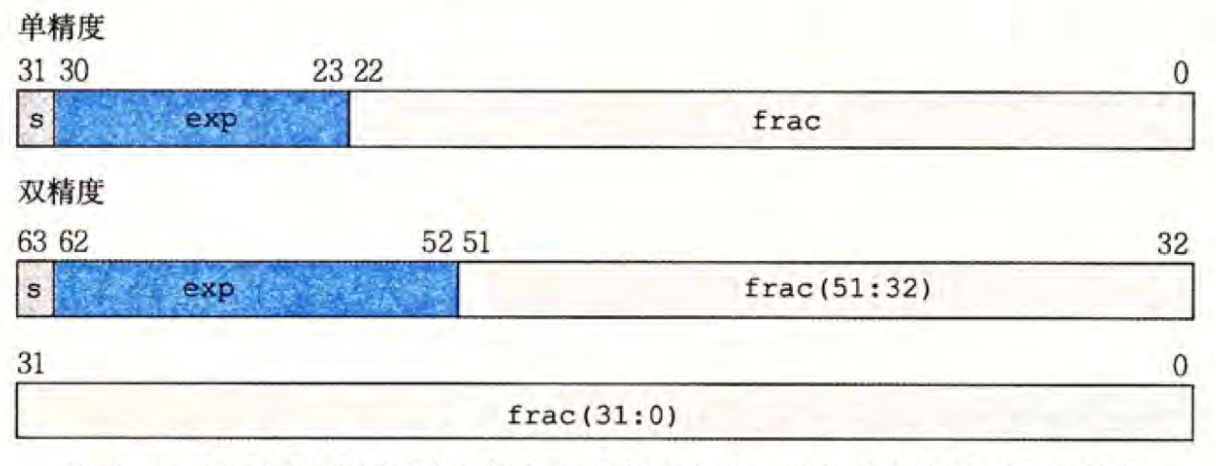
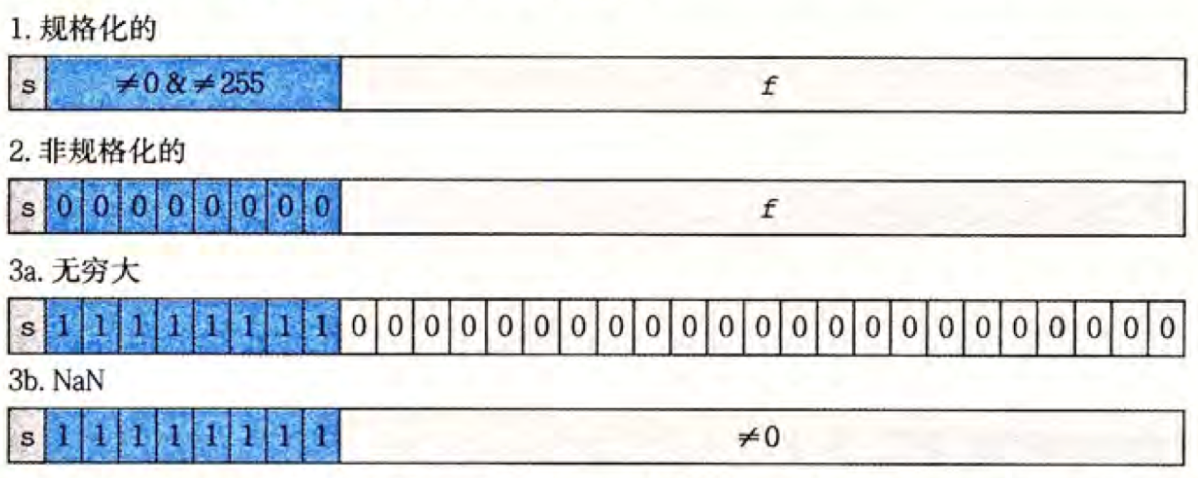
给定位表达,根据 e x p exp exp 的值,被编码的值可以分成三种不同的情况(最后一情况有两个变种):
- 规格化的值
-
e
x
p
exp
exp 的位模式既不全为
0
0
0 也不全为
1
1
1
- 阶码
E
=
e
−
B
i
a
s
E = e - Bias
E=e−Bias
- e e e 是无符号数,其位表示为 $e_{k-1} \cdots e_1 e_0 $
- B i a s = 2 k − 1 − 1 Bias = 2^{k-1} - 1 Bias=2k−1−1(单精度是 127 127 127,双精度是 1023 1023 1023)
- 阶码
E
=
e
−
B
i
a
s
E = e - Bias
E=e−Bias
- 小数字段
f
r
a
c
frac
frac 被解释为描述小数值,其中
0
≤
f
<
1
0 \le f < 1
0≤f<1,其二进制表示为
0.
f
n
−
1
⋯
f
1
f
0
0.f_{n-1}\cdots f_1 f_0
0.fn−1⋯f1f0
- 尾数定义为 M = 1 + f M = 1+f M=1+f
-
e
x
p
exp
exp 的位模式既不全为
0
0
0 也不全为
1
1
1
- 非规格化的值
- 阶码域全为 0 0 0
- 阶码值
E
=
1
−
B
i
a
s
E = 1 - Bias
E=1−Bias
- B i a s = 2 k − 1 − 1 Bias = 2^{k-1} - 1 Bias=2k−1−1(单精度是 127 127 127,双精度是 1023 1023 1023)
- 尾数 M = f M=f M=f
- 特殊值
- 阶码域全为 1 1 1
- 小数域
- 小数域全为零时,表示无穷
- 当 s = 0 s=0 s=0 时,值为 − ∞ - \infty −∞
- 当 $s = 1 $ 时,值为 + ∞ + \infty +∞
- 小数域为非零时,表示 N a N NaN NaN
- 小数域全为零时,表示无穷

例题
转换 23.7 5 10 23.75_{10} 23.7510
23.7 5 10 = 2 3 10 + 0.7 5 10 = 10111.1 1 2 = 1.01111 1 2 × 2 4 23.75_{10} = 23_{10} + 0.75_{10} = 10111.11_2 = 1.011111_2 \times 2^4 23.7510=2310+0.7510=10111.112=1.0111112×24
因此:
- s = 0 s=0 s=0
- M = 1.01111 1 2 ⇒ f = M − 1 = 0.01111 1 2 ⇒ f r a c = 0111110 … 0 M=1.011111_2 \space \space \Rightarrow \space \space f=M-1=0.011111_2 \space \space \Rightarrow \space \space frac=0111110\dots0 M=1.0111112 ⇒ f=M−1=0.0111112 ⇒ frac=0111110…0
- E = 4 ⇒ e = E + B i a s = ( 4 + 127 ) 10 = 13 1 10 = 1000001 1 2 ⇒ e x p = 10000011 E=4 \space \space \Rightarrow \space \space e = E + Bias = (4 + 127)_{10} = 131_{10} = 10000011_2 \space \space \Rightarrow \space \space exp = 10000011 E=4 ⇒ e=E+Bias=(4+127)10=13110=100000112 ⇒ exp=10000011
故: 23.7 5 10 = ( s ∣ e x p ∣ f r a c ) 2 = ( 0 ∣ 10000011 ∣ 01111100000000000000000 ) 2 23.75_{10} = (s|exp|frac)_2=(0|10000011|01111100000000000000000)_2 23.7510=(s∣exp∣frac)2=(0∣10000011∣01111100000000000000000)2
转换 1011 1101 0100 0000 0000 0000 0000 000 0 2 1011 \space 1101 \space 0100 \space 0000 \space 0000 \space 0000 \space 0000 \space 0000_2 1011 1101 0100 0000 0000 0000 0000 00002
- s = 1 s=1 s=1
- e x p = 01111010 ⇒ E = e − B i a s = ( 01111010 ) 2 − 12 7 10 = − 5 10 exp=01111010 \space \space \Rightarrow \space \space E=e-Bias = (01111010)_2 - 127_{10} = -5_{10} exp=01111010 ⇒ E=e−Bias=(01111010)2−12710=−510
- f r a c = 10 … 0 ⇒ f = 0. 1 2 ⇒ M = 1 + f = 1. 1 2 frac=10\dots0 \space \space \Rightarrow \space \space f=0.1_2 \space \space \Rightarrow \space \space M = 1 + f = 1.1_2 frac=10…0 ⇒ f=0.12 ⇒ M=1+f=1.12
故: 1011 1101 0100 0000 0000 0000 0000 000 0 2 = ( − 1 ) s × M × 2 E = − 0.04687 5 10 1011 \space 1101 \space 0100 \space 0000 \space 0000 \space 0000 \space 0000 \space 0000_2 = (-1)^s \times M \times 2^E = - 0.046875_{10} 1011 1101 0100 0000 0000 0000 0000 00002=(−1)s×M×2E=−0.04687510
位运算(必考,10分)
/*
* bitAnd - x&y using only ~ and |
* Example: bitAnd(6, 5) = 4
* Legal ops: ~ |
*/
int bitAnd(int x, int y) {
return ~((~x) | (~y));
}
/*
* bitOr - x|y using only ~ and &
* Example: bitOr(6, 5) = 7
* Legal ops: ~ &
*/
int bitOr(int x, int y) {
return ~((~x) & (~y));
}
/*
* isZero - returns 1 if x == 0, and 0 otherwise
* Examples: isZero(5) = 0, isZero(0) = 1
* Legal ops: ! ~ & ^ | + << >>
*/
int isZero(int x) {
return !x;
}
/*
* minusOne - return a value of -1
* Legal ops: ! ~ & ^ | + << >>
*/
int minusOne(void) {
return ~0;
}
/*
* TMax - return maximum two's complement integer
* Legal ops: ! ~ & ^ | + << >>
*/
int tmax(void) {
return 0x7fffffff;
}
/*
* bitXor - x^y using only ~ and &
* Example: bitXor(4, 5) = 1
* Legal ops: ~ &
*/
int bitXor(int x, int y) {
return (~x) & y;
}
/*
* getByte - Extract byte n from word x
* Bytes numbered from 0 (LSB) to 3 (MSB)
* Examples: getByte(0x12345678,1) = 0x56
* Legal ops: ! ~ & ^ | + << >>
*/
int getByte(int x, int n) {
return (x >> (n << 3)) & 0xff;
}
/*
* isEqual - return 1 if x == y, and 0 otherwise
* Examples: isEqual(5,5) = 1, isEqual(4,5) = 0
* Legal ops: ! ~ & ^ | + << >>
*/
int isEqual(int x, int y) {
return !(x ^ y);
}
/*
* negate - return -x
* Example: negate(1) = -1.
* Legal ops: ! ~ & ^ | + << >>
*/
int negate(int x) {
return (~x) + 1;
}
/*
* isPositive - return 1 if x > 0, return 0 otherwise
* Example: isPositive(-1) = 0.
* Legal ops: ! ~ & ^ | + << >>
*/
int isPositive(int x) {
return !((x >> 31) | !x);
}
/* NegativeNum using only ~ and & , ignore 0
* Example: NegativeNum(-5) retrun -5 , NegativeNum(5) retrun -5, Negative(0) can
return any value
* Legal ops: ~ &
* Max ops: 8 */
int NegativeNum (int x) {
}
3
看懂指令(mov, jmp, add, call, ret, push, pop)
字节对齐、sizeof
数组 低地址指向高地址(会用)
寄存器
栈指针 %rsp 用于指明运行时栈的结束位置
| 四字(64 位) | 双字(32 位) | 作用 |
|---|---|---|
%rax | %eax | 返回值 |
%rbx | %ebx | 被调用者保存 |
%rcx | %ecx | 第 4 个参数 |
%rdx | %edx | 第 3 个参数 |
%rsi | %esi | 第 2 个参数 |
%rdi | %edi | 第 1 个参数 |
%rbp | %ebp | 被调用者保存 |
%rsp | %esp | 栈指针 |
%r8 | %r8d | 第 5 个参数 |
%r9 | %r9d | 第 6 个参数 |
指令
| 指令 | 作用 |
|---|---|
MOV | 复制数据 |
PUSH | 将数据压入栈中 |
POP | 将数据从栈中弹出 |
LEA | 加载有效地址(Load Effective Address) |
ADD /SUB/MUL/DIV | 加/减/乘/除 |
INC | 加一 |
JMP | 指令跳转 |
CALL/RET | 调用/返回过程(Procedure) |
4
指针的三个问题:
- 指针的值
- 指针的地址
- 指针指向的地址/值
5
函数调用、函数返回过程(必考,15分)
栈帧(Stack Frame)
ESP, EBP, EIP
函数调用过程
当函数被调用时,编译器与硬件:
- 将函数参数压栈
- 将返回地址压栈
- 将帧指针(Frame Pointer)压栈
- 将帧指针(Frame Pointer)设置为等于栈指针(Stack Pointer)的值
- 将栈指针下移
函数返回过程
当函数返回时,编译器与硬件:
- 将栈指针(Stack Pointer)设置为等于帧指针(Frame Pointer)的值
- 将旧的帧指针的值弹栈
- 使
%EBP的值等于旧的帧指针的值 - 将返回地址弹栈,并将
%EIP的值设置为其值 - 将参数弹栈
栈帧
栈帧通常包含以下元素:
- 传给函数的参数
- 函数调用者的返回值
- 函数调用者的
%ebp - 分配给函数本地变量的空间
- 已保存的寄存器
ESP、EBP、EIP
当调用函数时:
EIP寄存器里存储的是 CPU 下次要执行的指令的地址EBP寄存器里存储的是栈的栈底指针,通常叫栈基址,是开始进行函数调用之前,由ESP传递给EBP的ESP寄存器里存储的是在调用函数之后的栈顶,并且始终指向栈顶
当函数返回时:
- 系统根据
EIP寄存器里存储的地址,CPU 就能够知道函数调用完,下一步应该做什么 EBP寄存器存储的是栈底地址,而这个地址是由ESP在函数调用前传递给EBP的。等到调用结束,EBP会把其地址再次传回给ESP。所以ESP又一次指向了函数调用结束后的栈顶地址。
6
缓冲区溢出
如何避免缓冲区攻击:
- 使用限制长度的库函数(不使用不好的函数)
fgets而不是getsstrncpy而不是strcpy
- 栈使用随机的偏移
- 数据执行保护(不让栈上指令执行)
- 内存要么可写,要么可执行,但二者不能兼得
- 检查栈缓冲区溢出的标志
- Stack Canaries:在栈的返回地址的存储位置之前放置一个整形值,该值在装入程序时随机确定;栈缓冲区攻击时从低地址向高地址覆盖栈空间,因此会在覆盖返回地址之前就覆盖了警惕标志;返回返回前会检查该警惕标志是否被篡改。
7
动态内存分配(堆/栈)
栈和堆的比较
静态内存分配:程序变量、静态的局部变量、字符串常量
内部/外部碎片
管理堆上内存的数据结构:环形双向链表(Circular Doubly-LinkedList)、分配树(Allocation Tree)
静态分配
静态分配的变量
- 全局变量
- 被声明为
static的局部变量 - 显式常量(例如字符串等)
动态分配
栈分配
- 最常用的方式
- FIFO
- 向低地址增长
- 寄存器
%ebp保存栈顶地址 - 寄存器
%esp保存栈底地址
堆分配
- 使用
malloc和free释放内存空间
栈 v.s. 堆
- 栈空间是自动(隐式)分配的;堆空间是手动(显式)分配的
- 栈空间在离开作用域时自动销毁;堆空间需要使用
free请求销毁空间
8
定义 mymalloc 的数据结构与算法
- 封装
malloc函数- 对结构体(分配的空间)进行初始化
- 封装
free函数- 检查错误(Fence 对不对、checkout 对不对)
- 修改 line number
9
垃圾回收概念、四种算法(标记清扫、复制、引用计数、分代式垃圾回收,掌握)、伪代码(只有标记清扫有伪代码)
标记清除(Mark and Sweep)
过程
- Mark:对 root nodes 可达的节点进行标记(Mark)
- Sweep:对未标记的节点进行清除(Sweep),并消除可达节点的标记
可以成为 root nodes(根节点)的元素
- 寄存器中的值
- 全局/静态变量
- 栈中的局部变量
- 函数中的局部变量
优点
- 不需要手动运行(会在堆满了的时候自动运行)
- 能找到并释放所有无用的内存块
缺点
- 标记清除算法会锁住其他进程,导致一段明显的停顿时间,影响性能
- 会产生碎片
复制法(Copying Collection)
使用 2 个堆:1 个给程序使用,另 1 个直到 GC 时都不使用
过程
- 从 root nodes 开始遍历所有可达节点
- 将所有可达节点从正在使用的堆移动到另一个堆
- 删除掉所有留在原来的堆里的数据
- 切换堆
优点
- 速度比标记清除快(只需要一次遍历)
缺点
- 空间利用率大幅下降
引用计数(Reference Counting)
- 为每个对象维护一个指向这个对象的指针的计数器
- 当计数器等于 0 时,即其是一个不可达节点(garbage)
缺点
- 维护引用计数器的开销
- 无法解决循环引用
分代式(Generational Garbage Collection)
达尔文的进化论:新生物种是最容易被淘汰的
- 将对象分为多个年代
- 例如 G0、G1,其中 G0 包含所有的年轻的对象
- 不需要遍历整个引用树
- 大多数的回收在新生代完成
10
程序优化的流程
- Create benchmark
- Find hotspots
- Investigate causes
- Modify application
- Retest using benchmark
Amdahl’s Law 概念与计算
主要思想:当对系统的某个部分加速时,其对系统整体性能影响取决于该部分的重要性和加速程序
若系统执行某应用程序需要时间
T
o
l
d
T_{old}
Told;假设系统某部分所需执行时间与该时间的比例为
α
\alpha
α,而该部分性能提升比例为
k
k
k(即该部分初始所需时间为
α
T
o
l
d
\alpha T_{old}
αTold,现在所需时间为
(
α
T
o
l
d
)
/
k
(\alpha T_{old}) / k
(αTold)/k),因此,总的执行时间应为:
T
n
e
w
=
(
1
−
α
)
T
o
l
d
+
(
α
T
o
l
d
)
/
k
T_{new} = (1 - \alpha)T_{old} + (\alpha T_{old})/k
Tnew=(1−α)Told+(αTold)/k
由此,可以计算加速比:
S
=
T
o
l
d
T
n
e
w
=
1
(
1
−
α
)
+
α
/
k
S = \frac {T_{old}} {T_{new}} = \frac 1 {(1 - \alpha) + \alpha / k}
S=TnewTold=(1−α)+α/k1
Timer concept - multiplechoice
11
Optimization approaches(要能列出来)
看 ppt
最重要的优化是算法上的优化
- Code Motion(代码移动)
- Reduction in Procedure Call(减少过程调用)
- Eliminate Unneeded Memory References(减少不需要的内存访问)
- Loop Unrolling(循环展开)
- Common Subexpression Elimination(消除公用子表达式)
- Avoiding Temporary Variables(避免临时变量)
- 减少内存分配
molloc - 减少重分配,尽量重用
12
存储器的层次结构(Memory Hierarchy):
- Register
- L1/L2/L3
- Memory(内存)
- 硬盘
- 分布式文件系统
金字塔结构
云存储(Cloud Storage)的概念、优缺点(适当背一下)
Locality concept(时间、空间局部性)
云存储
概念
把数据存放在通常由第三方托管的多台虚拟服务器,而非专属的服务器上。
优点
- 企业只需要依实际使用的存储空间支付费用。
- 企业并不需要在自己的数据中心或办公室里安装实体的存储设备,大大减少 IT 和管理的成本。
- 日常维护工作,如备份、资料复制、或是增加存储设备添购等工作,都转移给托管的服务提供商,让企业更可以专注在自己的核心业务上。
缺点
- 当所欲存储的资料较为机密时,则对存放于云存储服务提供商的安全性有疑虑。
- 访问性能可能比本地端存储设备的性能低。
- 资料的可靠性和可用性将取决于广域网,以及服务商所提供的预防措施好坏。
- 当用户有特殊的资料使用记录追踪需求时(如公务部门依据规章和条例的要求,而需留存某些电磁记录时),使用云计算及云存储将使工作复杂度增加。
- 虽然可以一次提供给多人资料,或是传递资料给位于不同地方的人,但单人在转移资料的时候(例如文件由手机发送至电脑,或是由电脑发送至手机)因为需要重新“上传”与“下载”,会像是在绕远路一般,不如使用传输线的快。
- 传递大型资料的话,若是互联网断线或是云服务供应商出现差错,小则需要重新传输,大则有可能会导致资料上的差错或丢失。
Locality
时间局部性:程序在运行时,最近刚刚被引用过的一个内存位置容易再次被引用,比如在调取一个函数的时候,前不久才调取过的本地参数容易再度被调取使用。
空间局部性:最近引用过的内存位置以及其周边的内存位置容易再次被使用。空间局部性比较常见于循环中,比如在一个数列中,如果第 3 个元素在上一个循环中使用,则本次循环中极有可能会使用第 4 个元素。
13
缓存(cache)的基本结构
三种类型的缓存(全相联、组相联等)
Cache miss rate calculation(看清楚是什么类型的缓存)
缓存友好的代码 cache- aware programming* (loop fission, Cache Collisions, Row-major order and Column-major order, Loop Tiling* code implement)
14
linker/loader 概念(要能讲出这是干嘛的)
静态链接过程 Static Linking Process(符号解析合并重定位)
Symbol Resolution concept / strong and week symbol
理解链接实验的过程
linker 链接器
链接器(Linker)是一个程序,将一个或多个由编译器或汇编器生成的目标文件外加库链接为一个可执行文件。
loader 加载器
加载程序:加载程序是将程序的机器代码加载到系统内存中的程序。
Static Linking Process(静态链接过程)
- Symbol Resolution(符号解析)
- Object files define and reference symbols.
- Linker associate each symbol reference with exactly one symbol definition.
- Combination(组合)
- Relocation(重定位)
- Compiler and assemblers generate code and data sections that start at address 0.
- Linker reloacates theses sections by associating a memory location with each symbol defination and modifying references to those symbols so that they point to this memory location.
Symbol Resolution
确定符号引用关系,将每个模块中引用的符号与某个目标模块的定义符号建立关联
每个定义符号在代码段(函数)和数据段(变量)都分配了存储空间,将引用符号与定义符号建立关联后,就可以在重定位时将引用符号的地址重定位为相关联的定义符号的地址。
符号解析的整体过程
- 找到程序中有定义和引用的符号(包括函数和变量)
- 编译器将定义的符号放在符号表中:
- 符号表是一个结构数组
- 每个表项包含符号名、长度位置等信息
- 链接器将每个符号的引用都与一个确定的符号定义建立关联
Strong & Week Symbol
- Strong Symbol - procedures and initialized globals
- Weak Symbol - uninitialized globals
符号链接的规则
- Strong Symbol 只能出现一次
- 同名的 Week Symbol 可以被 Strong Symbol 覆盖
- 如果有多个 Week Symbol,链接器会随机选择一个
15
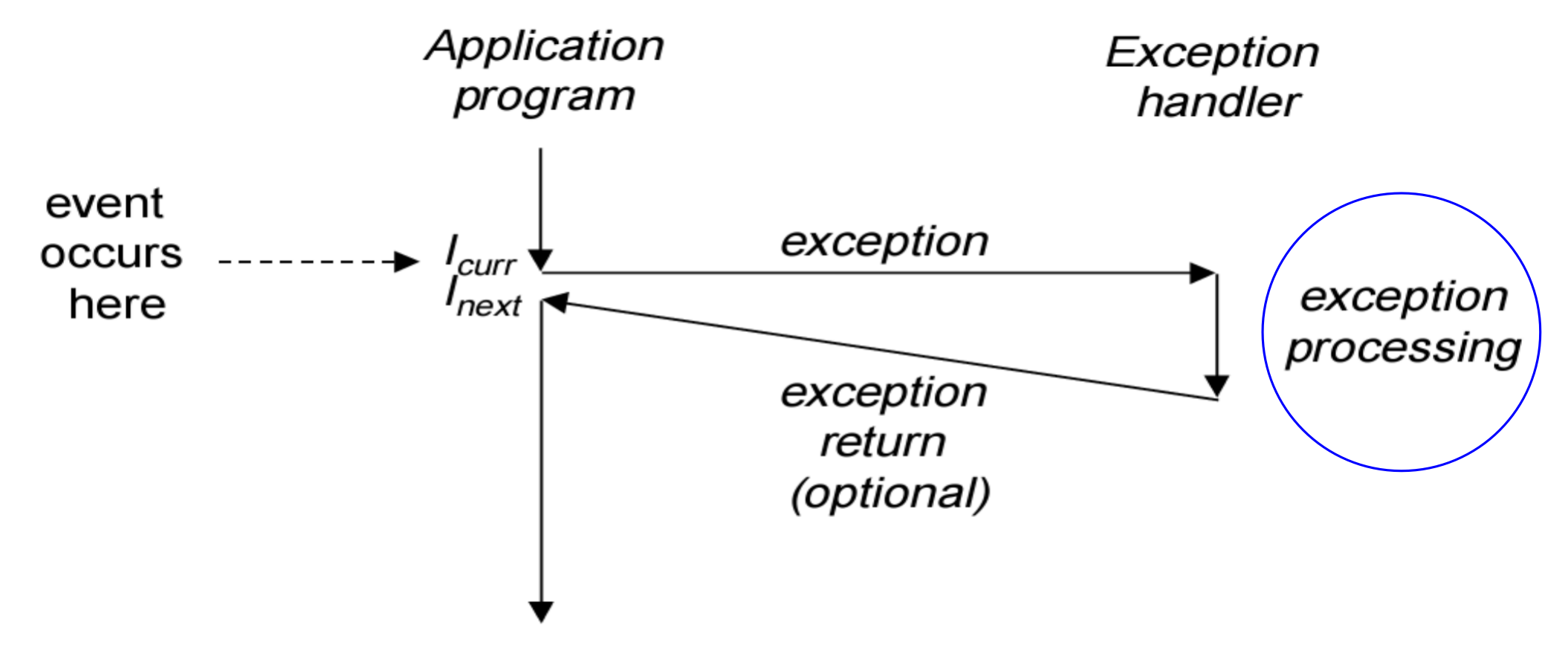
四种类型的异常、产生的原因是什么、怎么进行异常处理、处理完后返回到哪里
不要求进程、Windows编程等
4 种类型的异常与其产生的原因
- Interrupts: Signal from I/O device, INTR/NMI
- Traps: System Call
- Faults: Potentially recoverable error, Page Fault, 除零
- Aborts: Nonrecoverable error
异常处理
选择题
1
1. Which of the following Visual C++ objects are contained within a “Project”?
I. Files, II. Visual C++ Solutions, III. Flow charts
2. In Visual C++, a Win32 Console Application is ()
a. the status window of the Visual C++ environment
b. built by using sophisticated “Application Wizards”
c. a program that is able to control the operating system of a windows computer
d. the simplest type of application Visual C++ can generate
3. Which of the following is able to describe a computation at the highest level of abstraction?
a. C++ code
b. logic Gates
c. machine code
d. C code
4. Consider the following fragment of C++ source code.
string msg;
unsigned int x; int y;
cin >> msg >> x >> y;
cout << x + y;
Which of the following is (are) true regarding execution of the segment?
1.The input statement will always take the same amount of time to execute.
2.The output statement will always be executed immediately after the input statement.
3.If x and y are both positive, an integer greater than both will be printed.
a. II and III only
b. I and II only
c. none
d. II only
5. Integrated programming environments make it difficult to mix and match tools from different sources. This is ()
a. good, because tools from different sources cannot be made to interact with each other
b. bad, because no single vendor is likely to be the source of all the best tools
c. bad, because all the tools will then have the same user interface
d. good, because it ensures compilation is not done incrementally by accident
6. Compared to a sequence of machine code instructions, a fragment of C code ()
a. may describe the same algorithm
b. is the native way to program most computers
c. describes the actions of the computer, not just of the CPU
d. does not engage any transistors during its execution
7. Which of the following does a debugger do?
- Analyze the source code to find programming errors.
- Decode machine code generated by a compiler.
- Stop execution of a program.
8. When using a debugger to find the cause of a program’s incorrect behavior, ()
a. it is often necessary to start the program multiple times under the debugger
b. the faulty code fragment must first be identified
c. the program is usually executed to the point at which the behavior occurs and then executed backwards to find the cause
d. it is fastest to start by stopping the debugger long before the behavior appears
2
1. In a computer with 4-byte words, which of the following C expressions tests whether ptr contains the address of a word?
I. (ptr & 3) == 0
II. (ptr | 3) == 0
III. (ptr % 4) == 0
a. III only
b. I only
c. I and III only
d. II only
看
ptr指向的字节的最后两位是不是0x11(注:字节小端排序)
2. What happens in a C program when an addition would cause integer overflow?
a. An incorrect result is produced and execution continues.
b. An exception-handler is called with the two operands as parameters.
c. Execution is terminated.
d. The correct value is coerced to a floating point number.
3. In C, what is the following binary number 11010101 in hexadecimal?
a. 0xD5
b. 0x5D
c. 0xB5
d. 0xAB
4. What is the purpose of the exponent in floating point numbers?
a. to specify the base as binary, octal, or hexadecimal
b. the mantissa is raised to the power of the exponent
c. to indicate where the decimal or binary point should be
d. to specify the superscript
5. How is -10 (decimal) represented in an 8-bit 2’s complement binary format?
a. 11110110
b. 11110101
c. 10001010
d. 11111010
6. In C, using default floating point settings, what happens when a floating-point computation results in an overflow? 、
a. An erroneous value is computed and execution continues.
b. Program execution is halted.
c. A special value “infinity” is computed, testable with _finite().
d. An exception is raised unless disabled by calling _controlfp().
7. What is the value of the following C expression 0x1234 & 0x5432?
a. 0x1111
b. 0x6666
c. 0x1030
d. 0x5636
8. Which of the following numerical operations is most likely to lead to loss of precision?
a. Floating-point multiplication
b. Integer addition
c. Floating-point addition
d. Integer multiplication
9. Which of the following could be represented by one bit of information?
a. the color of a single pixel on a true-color computer display
b. an ASCII character
c. the position of a light switch
d. the current channel of a television receiver
10. Which of the following statements about floating-point numbers in C is true?
I. Floating-point numbers are often only approximations of real numbers.
II. A 32-bit float only approximates decimal fractions, but a 64-bit double represents them exactly.
III. Floating-point numbers can represent any rational real number but not irrationals.
a. I only
b. I and III only
c. II only
d. I and II only
11. How is 46 (decimal) represented in an 8-bit 2’s complement binary format?
a. 00101110
b. 01000110
c. 00011110
d. 00101100
12. What is the value of the following C expression 0x1234 ^ 0x5432?
a. 0x1030
b. 0x5434
c. 0x5636
d. 0x4606
3
1. The program counter contains
a. the number of CPU instructions a program has executed so far
b. the number of times a program has been executed
c. the amount of memory a program is currently using
d. the address of the CPU instruction that is about to be fetched
2. Which of the following is a good reason (are good reasons) to equip the CPU with small amounts of fast memory?
I.To make the design of the compiler simpler
II.To make some CPU instructions smaller
III.To make some CPU instructions faster
3. Which of the following must be true if a program is stopped at a specific line within the Visual C++ debugger?
I. There is at least one breakpoint enabled.
II. There is a breakpoint enabled on that line.
III. There is a breakpoint enabled on the line preceding that line
none
4. Programs compiled for an Intel Pentium processor do not execute properly on a SPARC processor from Sun Microsystems because ()
a. copyrights regarding code cannot be violated
b. the operation codes understood by the two processors are different
c. the assembly mnemonics for the same “opcode” are different in the two processors
d. the memory of a SPARC CPU is numbered from top to bottom
5. Within Visual C++, which of the following will reveal the value of variable when the program is stopped at a breakpoint?
I. Placing the mouse pointer over the variable name in the source file window.
II. Inserting a printf() in the program.
III. Typing the variable name on the “Watch” window.
6. Immediately after the CPU executes an instruction that is neither a branch nor a jump instruction, the program counter ()
a. remains unchanged
b. is incremented to point to the following instruction
c. has a value that cannot be determined without further information
d. is incremented by one
7. A CPU register is a word of CPU memory that ()
a. houses a critical variable for the duration of the execution of a program
b. records the results of periodic CPU diagnostics
c. is explicitly loaded and unloaded from normal memory by compiler-generated instructions
d. is automatically loaded when a CPU instruction refers to a word of normal memory
8. Which of the following computations may be performed by exactly one CPU instruction?
- a = 5;
- a = b + c * 5;
- for (i = 0; i < 10; i += a[i++]);
9. Suppose that, using a tool such as the memory window of Visual C++, we found that a certain set of contiguous memory locations contained the integer 0xC605CD623A8365000000. What could these memory locations hold? (D)
- the integer 0xC605CD623A8365000000
- a string
- a CPU instruction
10. A branch instruction ()
a. sets the program counter to one of two possible values
b. increases the program counter by a fixed amount
c. sets the program counter to one of many possible values
d. unconditionally sets the program counter to its operand
11. A jump instruction ()
a. changes the program counter only if its operand is equal to zero
b. changes a pointer to point to the next element of an array
c. increases the program counter
d. unconditionally sets the program counter to its operand
12. The machine code generated from source code by a compiler ()
a. associates variable values with their names
b. executes more quickly than the source code
c. does not preserve all the information given in the source code
d. can be easily inspected to check the correctness of the compiler
13. Which of the following are true of the effect that optimizations have on the machine code generated by compilers?
I. The resulting code will be faster and/or smaller.
II. The resulting code will be clearer.
III. The resulting code will be harder to debug.
4
1. In C, assuming that an int takes 4 bytes, if array a is declared as follows and a has the value 0x10000, what is the value of the expression a + 2?
int a[12];
a. 0x10004
b. 8 plus the contents of location 0x10000
c. 0x10002
d. 0x10008
2. The Visual C++ Memory window displays ()
a. the contents of memory, interpreted in one of several ways, without the associated variable names
b. the names and values of variables in memory, interpreted in one of several ways
c. the names and values of variables in memory, interpreted as 32-bit integers no matter what the variables’ types
d. the contents of memory, interpreted as 32-bit integers, without the associated variable name
3. Consider the following code fragment.
int a;
int b;
int main(int argc, char *argv[]) {
int c;
int d;
...
/* some code */
}
Which of the following must be true?
a. The value of *d is closer to the value of *c than to the value of *a.
b. The value of &d is closer to the value of &c than to the value of &a.
c. The values of *a and *b are closer to each other than the values of *c and *d.
d. The values of &a and &b are closer to each other than the values of &c and &d.
4. Consider the following code.
char a[100];
a[99] = *((char *) (((int) &a[0]) + 4))
If integers are 32 bits wide, which of the following values is equal to a[99]?
a. a[4]
b. the integer stored in the bytes a[4], a[5], a[6] and a[7]
c. a[3]
d. a[0] + 4
5. Which of the following statements about alignment within C struct’s is true?
I. Alignment may cause the allocation of unused space.
II. Alignment is required by all modern processors.
III. Alignment can help processors access data more efficiently.
6. In C, assuming that an int takes 4 bytes, how many bytes are required to represent the following array int a[12];?
a. 12
b. 52
c. 48
d. 44
7. Given the following declaration and initialization of char s[] = "string";, what is the value of the expression s[6]?
a. ‘\n’
b. an unpredictable value
c. ‘g’
d. ‘\0’
8. Given the address of a C struct at runtime, how is the address of a member element in the struct determined?
a. A linear search is made from the base address of the struct.
b. The element name is looked up in a symbol table.
c. A constant offset associated with the member is added to the address.
d. The struct consists of an array of pointers to the elements of the struct.
9:In one computer, the bytes with addresses A, A+1, A+2 and A+3 contain the integer 256, and the variable declared with int *a; has the value A. In a different computer, the bytes with addresses B, B+1, B+2 and B+3 also contain the integer 256, and the variable declared with int *b has the value B. Which of the following are necessarily true? (A)
- The contents of
A+1are equal to the contents ofB+1. - The contents of
A+1are equal to the contents ofB+2. *a == *b
10. We want the variable factorialfunc to hold the address of the first instruction of the following function:
int factorial(int n) {
if (n == 1)
return n;
return n * factorial(n -1);
}
How would we declare the variable?
a. int (int) * factorialfunc;
b. int (*factorialfunc)(int);
c. factorial() * factorialfunc;
d. we can’t: C cannot extract the addresses of instructions.
5
1. Consider the program given below.
#include <stdio.h>
int callee(void) {
int count = 5;
printf("%d ", (int) &count);
return count;
}
int main (int argc, char *argv[]) {
int count = 4;
count = callee();
printf("%d ", (int) &count);
return 0;
}
Which of the following describes the output of the program?
a. Two different integers are printed, and the value of neither can be determined from the information given.
b. One integer is printed twice, and its value cannot be determined from the information given.
c. 5 is printed twice on the same line.
d. 5 and 4 are printed, in that order on the same line.
2. What does the following program print?
int callee(int* count) {
count++;
return *count;
}
int main(int argc, char *argv[]) {
int count = 4;
int retval;
retval = callee(&count);
printf("%d", retval);
return 0;
}
a. 8
b. 4
c. 5
d. cannot be determined from the information given.
3. At which of the following times is an activation record created?
I. When a program starts executing.
II.Every time a function is invoked.
III.When a variable is declared.
4. What does the following program print?
void callee(int* count) {
(*count)++;
}
int main (int argc, char *argv[]) {
int count = 4;
callee(count); // Wrong! => D. compile error
printf("%d", count);
return 0;
}
a. 5
b. 8
c. 4
d. nothing: it will not compile successfully
应该是
callee(&count);
5. Consider the following program segment.
int factorial(int* arg) {
int n = *arg;
if (n == 1)
return n;
return n * factorial(n - 1);
}
When the segment is executed, the variable n is allocated to ()
a. just one address, and it is not known to the compiler
b. just one address, and it was chosen by the compiler
c. many addresses none of which is known to the compiler
d. many addresses that were chosen by the compiler
具体地址在编译期不可知
6: Consider the following program.
int i;
int j = 1;
int callee(int number) {
int plusone;
plusone = number + 1;
return plusone;
}
int main(int argc, char *argv[]) {
if (j == 1)
return callee(i);
return j;
}
Which of the following are allocated in the activation record immediately after the function callee() is invoked?
a. i, j and number only.
b. i only.
c. plusone only.
d. plusone and number only.
7. Consider the following program.
int i;
int* jp = &i;
void main(int i, char * argv[]) {
printf("%d %d\n", (int) &i, (int) jp);
}
Which of the following describes what it prints?
a. two values, one 4 greater than the other
b. nothing: it will not compile because it is ambiguous
c. two very different integers
d. two integers that are exactly the same
8. Consider the following program.
int square(int* arg) {
int n = *arg;
return n * n;
}
int main(int argc, char * argv[]) {
int arg = strtol(argv[1], NULL, 0);
return square(arg);
}
When it is executed with the argument 5, the variable n is allocated to ()
a. exactly one address not known to the compiler.
b. many addresses chosen by the compiler.
c. exactly one address chosen by the compiler.
d. many addresses neither of which are known to the compile
9. What is printed as a result of execution of the following program?
#include <stdio.h>
void callee(int *count) {
(*count)++;
}
int main(int argc, char *argv[]) {
int count = 4;
callee(&count);
printf("%d", count);
return 0;
}
a. 8
b. 5
c. 4
d. It cannot be determined from the information given.
10. Consider the following segment of C source code.
int a = 8;
int b = *&a;
What is the value of variable b at the end of execution of the segment?
a. &a
b. a
c. (int) &a
d. (int) &b
11. In a computer in which both addresses and integers are 32 bits wide, how many bytes of memory will the compiler allocate for following code fragment? ©
int a;
int *b = &a;
a. 0
b. 32
c. 8
d. 4
12. Activation records are organized in stacks because ()
a. they are seldom needed during program execution.
b. stacks are simple enough for the hardware to manage.
c. stacks allow activation records to be pushed and popped in any order.
d. functions need to access all the variables of the functions that call them.
13. When executing a function callee(), which of the following are true regarding the value of the frame pointer?
I. It marks the top of the stack frame of the function that invoked callee().
II. It marks the bottom of the stack frame of callee()
III. It is the top of the stack.
14. Consider the following function.
int factorial(int n) {
if (n == 1) return n;
return n * factorial(n - 1);
}
How many activation records are “popped” when it is invoked by the expression factorial(4)?
a. 0
b. 5
c. 4
d. 1
6
1. Which of the following are true about statically allocated data in C programs?
- Its location is chosen by the compiler.
- Its location may change during execution if more memory is required.
- Its location is not known directly but can be found in a static symbol table.
2. A memory leak is caused by a ()
a. function that allocates a large amount of memory from the heap
b. bug in which too much memory is allocated, causing internal fragmentation
c. bug in the memory allocator that fails to free memory
d. failure to free allocated memory
3. In C, local variables allocated inside functions are allocated ()
a. in a fifo
b. on the stack
c. in static storage
d. in the heap
4. Suppose a compiler uses static storage to store all variables, function parameters, saved registers, and return addresses. Which of the following language features can this compiler support?
I. Local variables.
II. Function calls.
III. Recursion.
递归是动态的
5. The key feature of implicit memory management is that memory is freed automatically. Which of the following features of C make(s) it difficult to add support for implicit memory management in C?
I.Pointers are not always initialized.
II.Type casting makes it impossible to know when a value could be a pointer.
III. C programs can allocate memory at runtime.
至少能看出来最后一个是错的
6. Which of the following features apply to standard heap allocation in C?
I.The size of heap objects must be known at compile time.
II.Heap memory must be explicitly allocated.
III.Heap memory is deallocated when a function returns.
7. In this sequence of C statements
long a[10];
ptr = a + 5;
*ptr++ = x;
the last line could be rewritten as ()
a. a[6] = x;
b. ptr = x; *ptr++;
c. a[5] = x; ptr = ptr + 1;
d. ptr = ptr + 1; *ptr = x;
8. Consider the following fragment of C code.
int *p = (int *) calloc(100);
int *q = p;
free(p);
Immediately after executing it, which of the following are true about p and q?
I.p and q are identical pointers to freed storage.
II.p points to freed storage, and q points to an allocated block of size 100.
III.p should not be free()d again, but invoking free(q) is all right.
9. In C, to allocate an array of 100 longs on the heap you should write ()
a. long a[] = (long *) malloc(100);
b. long *a = (long *) malloc(100);
c. long *a = (long *) malloc(100 * sizeof(long));
d. long a[100] = (long *) malloc(sizeof(a));
10. What is the value of an uninitialized pointer variable declared within a function?
a. its last value from the previous call to the function
b. 0xDEADBEEF
c. the value is undefined
d. 0 (or NULL)
11. Consider a system in which memory consists of the following hole sizes in memory order:
H0 H1 H2 H3 H4 H5 H6 H7
10KB 4KB 20KB 18KB 7KB 9KB 12KB 15KB
and a successive segment request of
a) 12 KB
b) 10KB
c) 9KB
Which of the following sentences is true? (D)
I. First Fit algorithm allocates H2, H0, H3 for the mentioned request.
II. Worst Fit algorithm allocates H2, H3, H7 for the mentioned request.
III. Best Fit algorithm allocates H6, H0, H5 for the mentioned request.
Worst Fit:取最大的
12. Consider the malloc() function. Which one of the following sentences is correct? ( D)
a. The malloc() returns the amount of memory allocated
b. The malloc() allocates the desired amount of memory on the stack
c. The allocated memory is only local to the function
d. The malloc() allocates the desired amount of memory on the heap
只在堆 Heap 上分配内存
7
1. what will be the output ?
void main(){
char *p="hello world!";
int *q;
p++;
q = (int *)p;
q++;
printf("%s%s\n",p,q);
}
A.hello world!hello world!
B.ello world! world!
C.error
D.ello world!llo world!
2. what properties of a variable are specified by the static keyword in c?
i.the variable will be statically allocated.
ii.the variable name will be visible only to functions defined within the same file.
iii.the variable’s value does not change very often. the compiler uses this fact to focus optimizations on other variables.(10.0分)
3. in c, calloc() differs from malloc() in that calloc()
A.detects memory allocation errors.
B.is faster.
C.sets the contents of the block to zero before returning.
D.allocates additional memory from the stack.
5. a static variable by default gets initialized to ()
A.1
B.blank space
C.0
D.garbage value
7. in c, when a struct is freed, ()
A.only those pointers within the struct that point into the heap are freed automatically.
B.a destructor function is called automatically to clean up.
C.any pointers within the struct are also freed automatically.
D.no pointers within the struct are freed automatically.
8. why is it wrong to return the address of a local variable?
A.it allows illegal access to the variable from arbitrary functions.
B.the local variable may be in a machine register.
C.the variable address is invalid after the return.
D.it is faster to return the value of the variable.
9. in c, which of the following is the best way to detect when a pointer is freed twice?
A.set pointers to null after freeing them.
B.modify free() to set the freed data to zero.
C.flag all blocks as free or not, and check the flag when calling free().
D.keep a log of addresses that have been freed and scan the log before calling free().
10. to resolve memory leaks in c, one common approach is ()
A.to add padding before and after allocated memory blocks and to fill that memory with a known value.
B.to check whether the number of calls to malloc() is greater than the number of calls to free().
C.to ensure that memory blocks are allocated only on word boundaries.
D.to store the source code line whence each block is allocated.
8
1. How does JAVA handle memory allocation?
a. JAVA always uses a garbage collector.
b. JAVA has a garbage collector that can be used or turned off.
c. Allocation and deallocation is the responsibility of the programmer.
d. Allocation and deallocation is completely shielded from the programmer.
2. A garbage collector ()
a. frees memory blocks that cannot be reached by dereferencing pointers.
b. removes old versions of local variables from the stack .
c. frees memory blocks marked as “deleteable”.
d. frees all memory blocks that will not be accessed in the future.
3. A memory pool is a large block of memory from which small objects are allocated piecemeal by breaking them off from the pool as required. Under which of the following conditions would such a scheme result in greatly improved performance? (A)
I. All objects allocated from the pool are freed at around the same time.
II. All objects allocated from the pool are of similar sizes.
III. A garbage collector takes care of freeing memory.
4. Reference counts used in implementations of garbage collectors count ()
a. the number of times a block has been allocated.
b. the number of times a block has been accessed.
c. the number of pointers pointing to a block.
d. the number of times a datum has been referenced inside each block.
5. To quickly allocate and free many variables of a commonly used data type, we could ()
a. coalesce blocks when they are freed.
b. use sizes which are powers of two.
c. keep a linked list of free objects of that type’s size.
d. minimize the size of the data type.
6. the advantage of using copying gc including ()
i. A copying collector is generally more efficient than a non-copying collector
ii. The copying gc can make use of heap memory effectively.
7. A garbage collector starts from some “root” set of places that are always considered “reachable”, such as
i. CPU registers
ii. stack
iii. global variables
8. which statement is true?
A.The best- fit method chooses the largest free block into which the requested segment fits.
B.For the best- fit method, the list of free blocks should be ordered according to increasing memory addresses
C.Using the first- fit algorithm on a free list that is ordered according to decreasing block sizes results in low performance for allocations, but avoids external fragmentation.
D.Using the first- fit algorithm on a free list that is ordered according to increasing block sizes is equivalent to using the best- fit algorithm.
9. Mark-and-sweep garbage collectors are called conservative if ()
A.they coalesce freed memory only when a memory request cannot be satisfied
B.they perform garbage collection only when they run out of memory
C.they treat everything that looks like a pointer as a pointer
D.they do not free memory blocks forming a cyclic list
10. which of the following statements are true?
i.The fi rst- fi t memory allocation algorithm is slower than the best- fi t algorithm (on average).
ii.Deallocation using boundary tags is fast only when the list of free blocks is ordered according to increasing memory addresses.
D.none of them
9
1. Which of the following are useful for observing program performance?
I. Direct measurement with a stopwatch.
II. Statistical Sampling.
III. System Monitors
2. Which of the following approaches towards optimizing programs is most advisable?
a. “Optimize as you go”: make sure every function is optimized before writing the next one.
b. Optimize after all functions are written and debugged.
c. Optimize main() first.
d. Optimize the more complex functions first.
3. Which of the following is likely to offer the best performance improvement for programs that spend 50% of their time comparing strings?
a. Store strings uniquely so that pointer comparison can be used.
b. Be sure to use hardware string-comparison instructions.
c. Write in-line code for string comparison to eliminate a procedure call.
d. Call a library function for string comparison.
4. In the process of Software Optimization Process, what should do first?
a. Investigate causes of Hotspots
b. find the Hotspots
c. Modify application.
d. think of better Algorithm or using better Data structure
5. “Wall time” measures ()
a. idle time.
b. the total duration of a program’s execution.
c. the time a program spends waiting for input and output.
d. the user time plus the system time.
6. What is TSC?
a. A timer mechanism of OS
b. A system call of OS
c. A timer mechanism of x86 platform, which is the shortname of Time stamp counter
d. A timer mechanism of C library
7. “CPU time” measures ()
a. the time spent executing system functions.
b. the time spent by a program executing program instructions
c. wall time
d. the percentage utilization of the CPU by the system.
8. Which is a function call of C library?
a. Clock()
b. SetTimer
c. gettimeofday()
d. GetLocalTime
9. Which of the following are advantages of using statistical sampling to profile programs?
I. Exact run times of all functions can be determined.
II. Code can be instrumented automatically.
III. The performance impact due to measurement can be minimal.
10. Amdahl’s law, applied to program optimization, says that ()
a. each optimization about doubles a program’s performance
b. program measurement is a prerequisite to optimization
c. algorithmic design is more important than code quality for performance
d. successive program optimizations tend to produce diminishing returns
11. General wisdom, expressed by the 80/20 rule, says that ()
a. 80% of the execution time is in the user interface, and 20% does the real work
b. algorithmic improvements account for the smallest amount of performance gain
c. most execution time is spent in a small amount of code
d. optimization can obtain between 20 and 80 percent improvement
10
1. Which of the following is likely to offer the best performance improvement for programs that spend 50% of their time comparing strings?
a. Be sure to use hardware string-comparison instructions.
b. Store strings uniquely so that pointer comparison can be used.
c. Write in-line code for string comparison to eliminate a procedure call.
d. Call a library function for string comparison.
2. Read the following code, and how can we optimize it?
void lower1(char *s)
{
int i;
for (i = 0; i < strlen(s); i++)
if (s[i] >= 'A' && s[i] <= 'Z')
s[i] -= ('A' - 'a');
}
a. Enhancing Parallelism
b. Loop Splitting
c. Reducing Procedure Calls
d. Converting to Pointer Code
3. Which of the following is/are related to optimizing program performance by making it running fast ()
I. By using faster algorithm
II. By not using pointer
III .By using data structure that occupy less memory space
4. Which of the following is normal skill of making program run faster ()
I. Reducing Procedure Calls
II. Enhancing Parallelism
III. Eliminating Unneeded Memory References
5. In order to optimizing program performance, we should know ()
I. What is the hot spot
II. Understanding features of that processor on which the program will run
III. All the system calls that the program uses.
6. To quickly allocate and free many variables of a commonly used data type, we could ()
a. keep a linked list of free objects of that type’s size.
b. minimize the size of the data type.
c. use sizes which are powers of two.
d. coalesce blocks when they are freed.
7. On the following opinions of optimizing C programs, which is/are right?
I. Just config the compiler in its optimizing setting, then nothing else need to
II. Understanding the feature of CPU is needless
III. Everything can be done in the C level, so it is needless to know the assembly code
none
8. On profiling, which is/are wrong?
I.GPROF is the profilling tool on Linux platform
II. it can be used to estimate where time is spent in the program
III. it can incorporate instrumentation code to determine how much time the different parts of the program require.
none
9. Which of the following approaches towards optimizing programs is most advisable?
a. Optimize the more complex functions first.
b. “Optimize as you go”: make sure every function is optimized before writing the next one.
c. Optimize after all functions are written and debugged.
d. Optimize main() first.
10. Which of the following is not optimization technique?
a. constant folding
b. code motion
c. memory aliasing
d. loop unrolling
11
1. what can loader do?
i. translate the c code into machine code (by Compiler)
ii.resolution (by Linker)
iii.load or map the executable object file from the disk to memory
2. which section is used for resolution(符号解析)
i. elf header
ii. section header tables
iii. .symtab
iv. .rel.text and .rel.data (10.0分)
3. where the field, which describes whether relocatable object file is using little endian or big endian, locates?
A.elf header
B…text
C.section header tables
D…bss
5. which variable will be put into bss? 未初始化或被初始化为0的全局或静态变量
int printf( const char* format, ... );
int global_init_var = 84;
int global_uninit_var;
void func1(int i) {
printf("%d\n", i);
}
int main(void) {
static int static_var = 85;
static int static_var2;
int a = 1;
int b;
func1( static_var + static_var2 + a + b );
return a;
}
i a and b
ii static_var
iii global_init_var
iv global_uninit_var
6. which file format is used for executable object file
i. pe
ii. coff
iii.elf
iv. a.out
7. what can linker do?
i. resolution
ii.relocation
iii.take the same kind of sections from relocatable object files, and put them together according to their types
8. at what time can linking happen? 这是广义上的链接
i.compile time
ii.load time
iii.run time
9. which section is used for relocation 重定位
i. elf header
ii. section header tables
iii. .symtab
iv. .rel.text and .rel.data
12
1. Which of the following is (are) true of the concept of locality of reference?
I. It is used to predict future memory references precisely, with the help of the compiler.
II. It is a quality of typical programs.
III. It has been mathematically proven.
2. Which of the following levels of a typical memory hierarchy transfers data in chunks of biggest size?
a. cache <–> main memory.
b. CPU registers <–> cache.
c. they all transfer one byte at a time.
d. main memory <–> disk.
3. Current technology trends suggest that the need for memory hierarchies ()
a. will disappear when “broadband” communications start delivering data over the internet at speeds greater than 1Mbps.
b. will disappear once processors reach clock frequencies greater than about 1000MHz.
c. will disappear once DRAM speeds improve.
d. will never disappear.
4. Which of the following is necessarily true regarding the following code fragment?
a = b;
c = d;
if (e == 1) return;
a. It exhibits no locality of reference.
b. It exhibits locality of reference no matter where the variables are allocated.
c. It exhibits locality of reference but only when a == b.
d. It exhibits locality of reference because the variables are allocated near each other.
5. Which of the following manages the transfer of data between the cache and main memory?
a. Compiler.
b. Operating System.
c. Hardware.
d. Registry.
6. Which of the following levels of a typical memory hierarchy transfers data in chunks of smallest size?
a. they all transfer one byte at a time.
b. main memory <–> disk.
c. cache <–> main memory.
d. CPU registers <–> cache.
7. Compared to dynamic RAM (SRAM), disks are ()
I. more expensive per megabyte.
II. slower per word access.
III. more persistent.
8. Which of the following manages the transfer of data between the CPU registers and the cache?
a. Hardware.
b. Operating System.
c. Registry.
d. Compiler.
9. A memory hierarchy ()
a. limits programs’ size but allows them to execute more quickly.
b. takes advantage of the speed of SRAM and the capacity of disk.
c. makes programs execute more slowly but allows them to be bigger.
d. is a way of structuring memory allocation decisions.
10. Compared to static RAM (SRAM), dynamic RAM (DRAM) is ©
- more expensive per megabyte.
- slower per word access.
- more persistent.
13
1. lru is an effective cache replacement strategy primarily because programs ()
A.exhibit locality of reference
B.read data much more frequently than write data
C.usually have small working sets
D.none of the above
2. when a cache is full and a new cache line needs to be fetched into it, which of the following is a pretty good, practical approach?
A.choosing the cache location currently occupied by the least-recently-used data.
B.randomly selecting a cache location for the new line.
C.choosing always the same cache location for the new line.
D.denying the memory operation that caused the fetch of the new line.
3. a program whose code and data together occupy fewer than 256 kbytes is executed on a computer with a 512 kbyte direct cache. which of the following is true? (10.0分)
A.there is no telling, from the information given, how many bytes will be fetched from main memory.
B.no bytes will be fetched from main memory
C.every instruction fetch will cause a cache miss.
D.some bytes, but at most 256 kbytes, will be fetched from main memory.
4. when the following code fragment is executed on a computer with 32-bit integers and a fully-associative cache with 32-byte cache lines, how many bytes of the array a will be fetched into the cache from main memory?
int a[100];
for (i = 0; i < 17; sum += a[i], i++);
A.at most 96.
B.at most 68.
C.exactly 17.
D.exactly 32.
5. your computer has 32-bit integers and a direct cache containing 128 32-byte cache lines. in the following code fragment, the compiler allocates a at address 0x800000 and b at address 0x801000. before the execution of the code fragment, the arrays a and b have never been used, so they are not in the cache. what is the minimum number of bytes from each of the arrays a and b that could be fetched into the cache from main memory, during the execution of the code?
int b[1024];
int a[1024];
for (i = 0; i < 17; sum += a[i] + b[i], i++);
A.96
B.17
C.68
D.1088
6. which facts about the cache can be determined by calling the following function?
int data[1 << 20];
void callee(int x) {
int i, result;
for (i = 0; i < (1 << 20); i += x) {
result += data[i];
}
}
i cache line size
ii cache size
iii cache speed
7. a certain program is found to execute with a cache hit ratio of 0.90 on computer a, and of 0.95 on computer b. however, because of other design parameters of these computers, its wall time is the same in both a and b. then, a clever programmer finds a way to improve the locality of the program, so that it now executes with a hit ratio of 0.92 on a, and of 0.97 on b. which of the following statements is valid?
A.the wall time is now smaller on b than on a.
B.the wall time is now greater on b than on a.
C.the wall time is still the same on a and b, though it is smaller than before on both of them.
D.it is impossible to change the hit ratio of a program.
8. consider the following fragments from two versions of a program. version a version b
// version a
for (i = 0 ; i < n ; i++ ) {
read(i);
calculate(i);
write(i);
}
// version b
for (i = 0 ; i < n ; i++ ) {
read(i);
}
for (i = 0 ; i < n ; i++ ) {
calculate(i);
}
for (i = 0 ; i < n ; i++ ) {
write(i);
}
which of the following are true of version b, compared to version a?
i b may be faster because of cache effects.
ii b may be slower because of cache effects.
iii b may execute at essentially the same speed as a.
9. about the cache in a computer system, which is true
(a) every computer system has 3 level cache, that is l1, l2, l3 cache
(b) every computer systems’ cache system have data cache and instruction cache
© every computer systems’ cache system has 2 level cache, that is l1, and l2 cache
(d) every computer system’s cache system has l1 and l2 cache inside cpu chip(10.0分)
A.ii and iii only
B.none
C.i only
D.i and iii only
10. two computers a and b with a cache in the cpu chip differ only in that a has an l2 cache and b does not. which of the following are possible?
i.b executes a program more quickly than a.
ii.a executes a program more quickly than b.
iii.while executing a program, a fetches more data from main memory than does b.
A.i and ii only.
B.i, ii and iii.
C.i and iii only.
D.ii only.