151、Which two LISP infrastructure elements are needed to support LISP to non-LISP internetworking? (Choose two.)
A. PETR
B. PITR
C. MR
D. MS
E. ALT
152、In an SD-WAN deployment, which action in the vSmart controller responsible for?
A. handle, maintain, and gather configuration and status for nodes within the SD-WAN fabric
B. distribute policies that govern data forwarding performed within the SD-WAN fabric
C. gather telemetry data from vEdge routers
D. onboard vEdge nodes into the SD-WAN fabric
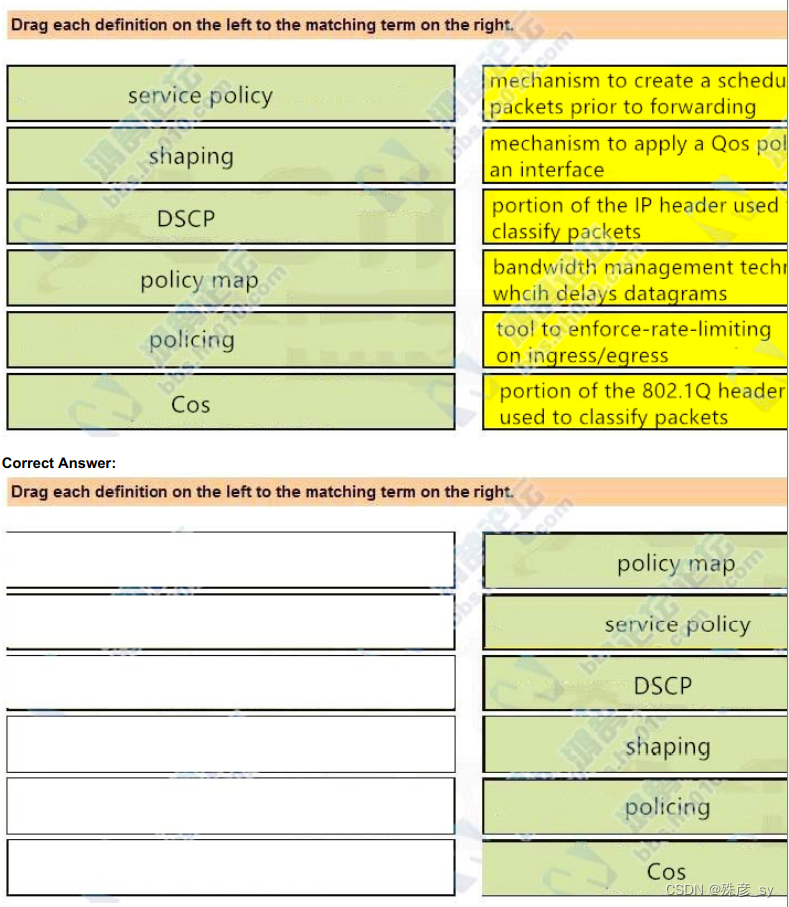
153、Drag and drop the Qos mechanisms from the left to the correct descriptions on the right
154、
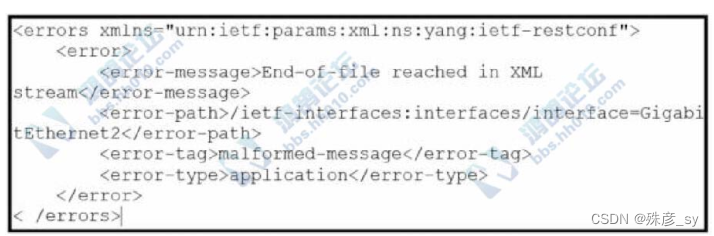
Refer to the exhibit.An engineer is using XML in an application to send information to a RESTCONFenable device.After sending the request,the engineer gets this response message and a HTTP response
code of 400.what do these responses tell the engineer?
A. The Accept header sent was application/xml
B. POST was used instead of PUT to update
C. The Content-Type header sent was application/xml
D. A JSON body was used
155、

Refer to the exhibit. An engineer must create a configuration that executes the show run command and
then terminates the session when user
CCNP logs in. Which configuration change is required?
A. Add the autocommand keyword to the aaa authentication command.
B. Add the autocommand keyword to the username command.
C. Add the access-class keyword to the aaa authentication command.
D. Add the access-class keyword to the username command
156、Which outbound access list, applied to the WAN interface of a router, permits all traffic except for httptraffic sourced from the workstation with IP address 10.10.10.1?
A. ip access-list extended 10
deny tcp host 10.10.10.1 any eq 80
permit ip any any
B. ip access-list extended 200
deny tcp host 10.10.10.1 eq 80 any
permit ip any any
C. ip access-list extended NO_HTTP
deny tcp host 10.10.10 1 any eq 80
D. ip access-list extended 100
deny tcp host 10.10.10.1 any eq 80
permit ip any any
157、
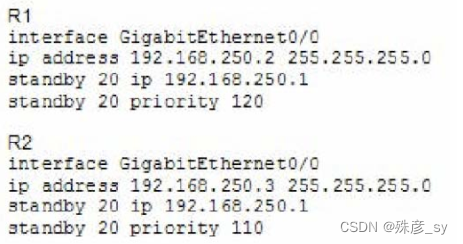
Refer to the exhibit. What are two effects of this configuration? (Choose two.)
A. R1 becomes the active router.
B. If R1 goes down, R2 becomes active but reverts to standby when R1 comes back online.
C. R1 becomes the standby router
D. If R2 goes down, R1 becomes active but reverts to standby when R2 comes back online.
E. If R1 goes down, R2 becomes active and remains the active device when R1 comes back online.
158、

Refer to the exhibit. Which command must be applied to R2 for an OSPF neighborship to form?
A. network 20.1.1.2 0.0.255.255 area 0
B. network 20.1.1.2 255.255.0.0 area 0
C. network 20.1.1.2 255.255.255.255 area 0
D. network 20.1.1.2 0.0.0.0 area 0
159、
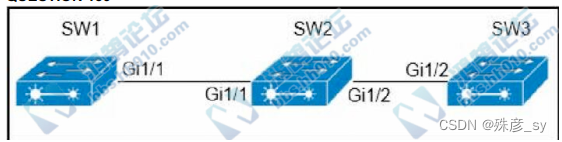
Company policy restricts VLAN 10 to be allowed only on SW1 and SW2. All other VLANs can be on all
three switches An administrator has noticed that VLAN 10 has propagated to SW3. Which configuration
corrects the issue?
A. SW1(config)#int gi1/1
SW1(config)#switchport taink allowed vlan 1-9,11-4094
B. SW2(config)#int gi1/2
SW2(config)#switchport trunk allowed vlan 10
C. SW2(config)#int gi1/2
SW2(config)#switchport trunk allowed vlan 1-9,11-4094
D. SW1(config)#int gi1/1
SW1(config)#switchport trunk allowed vlan 10
160、

Refer to the exhibit. An engineer must configure a SPAN session. What is the effect of the configuration?
A. Traffic sent on VLANs 10 and 12 only is copied and sent to interface g0/1
B. Traffic received on VLANs 10,11, and 12 is copied and sent to interface g0/1
C. Traffic received on VLANs 10 and 12 only is copied and sent to interface g0/1.
D. Traffic sent on VLANs 10, 11 , and 12 is copied and sent to interface g0/1
161、What is the result of applying this access contol list ?

A. TCP traffic with the URG bit set is allowed
B. TCP traffic with the SYN bit set is allowed
C. TCP traffic with the ACK bit set is allowed
D. TCP traffic with the DF bit set is allowed
162、

Refer to the exhibit. What does the error message relay to the administrator who is trying to configure a
Cisco IOS device?
A. A NETCONF request was made for a data model that does not exist
B. A NETCONF message with valid content based on the YANG data models was made, but the request failed.
C. The device received a valid NETCONF request and serviced it without error.
D. The NETCONF running datastore is currently locked.
163、
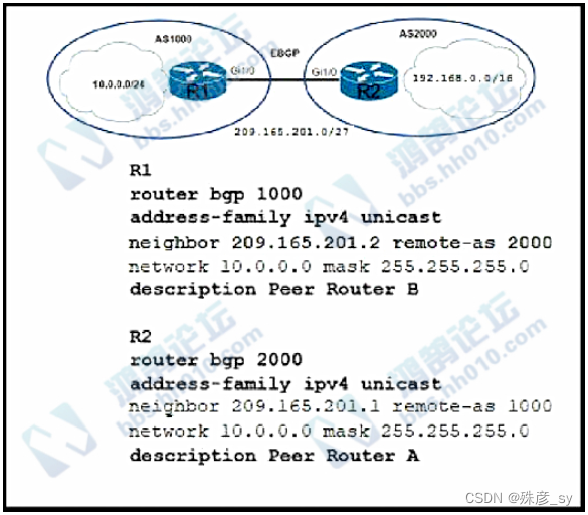
Refer to the exhibit.Which two commands are needed to allow for full reachability between AS 1000 and AS 2000?(choose two)
A. R2#network 192.168.0.0 mask 255.255.0.0
B. R1#network 192.168.0.0 mask 255.255.0.0
C. R2#network 209.165.201.0 mask 255.255.192.0
D. R2#no network 10.0.0.0 255.255.255.0
E. R1#no network 10.0.0.0 255.255.255.0
164、What is a Type 1 hypervisor?
A. runs directly on a physical server and depends on a previously installed operating system
B. runs directly on a physical server and Includes its own operating system
C. runs on a virtual server and depends on an already installed operating system
D. runs on a virtual server and includes its own operating system
165、What is the difference between CEF and process switching?
A. CEF is more CPU-intensive than process switching.
B. CEF uses the FIB and the adjacency table to make forwarding decisions, whereas process switching punts each packet.
C. CEF processes packets that are too complex for process switching to manage.
D. Process switching is faster than CEF
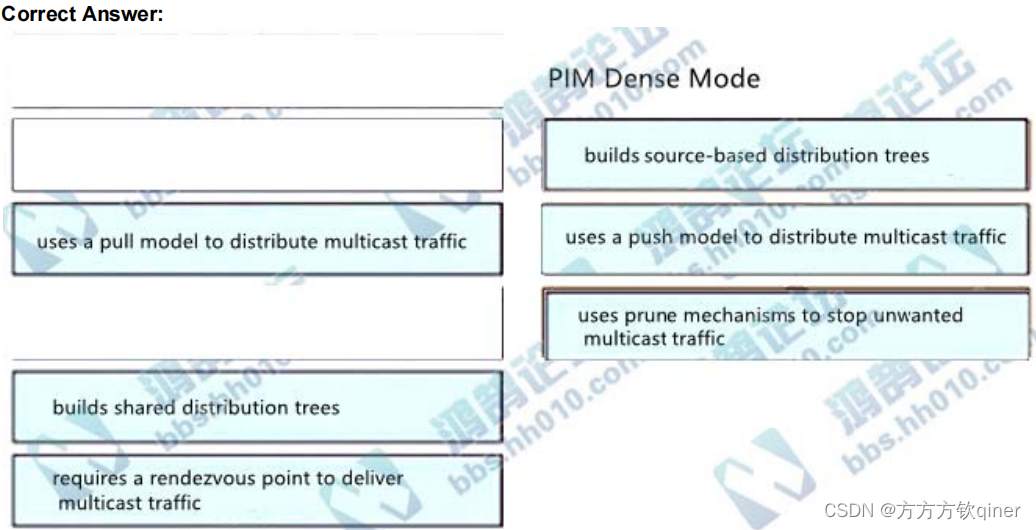
166、what is the purpose of an RP in PIM?
A. send join messages toward a multicast source SPT
B. ensure the shortest path the multicast source to the receiver
C. receive IGMP joins from multicast receivers
D. secure the communiation channel between the multicast sender and receiver
167、How do agent-based versus agentless configuration management tools compare?
A. Agent-based tools do not require a high-level language interpreter such as Python or Ruby on slave nodes
B. Agentless tools require no messaging systems bet-veen master and slaves.
C. Agent-based tools do not require instaltation of additional software packages on the slave nodes
D. Agentless tools use proxy nodes to interface with slave nodes
168、

Refer to the exhibit. An engineer configures monitoring on SW1 and enters the show show command to verify operation. What does the output confirm?
A. SPAN session 2 monitors all traffic entering and exiting port FastEthernet 0/15.
B. SPAN session 2 only monitors egress traffic exiting port FastEthernet 0/14.
C. RSPAN session 1 is incompietety configured for monitoring.
D. RSPAN session 1 monitors activity on VLAN 50 of a remote switch.
169、Refer to the exhibit. An engineer must ensure that all traffic entering AS 200 from AS 100 chooses Link 2 as an entry point. Assume tliat all BGP neighbor relationships have been formed and that the attributes have not been changed on any of the routers. Which configuration accomplishes this task?
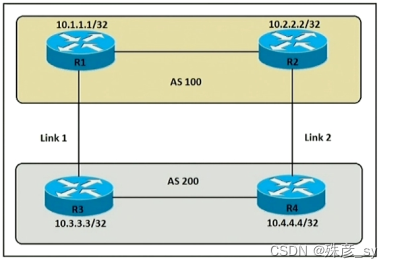
A. R4(config)#route-map PREPEND permit 10
R4(config-route-map)#set as-path prepend 200 200 200
R4(config)#router bgp 200R4(conflg-router)#neighbor 10.2.2.2 route-map PREPEND out
B. R3(config)#route-map PREPEND permit 10
R3(config-route-map)#set as-path prepend 200 200 200
R3(config)#router bgp 200
R3(conflg-router)#neighbor 10.1.1.1 route-map PREPEND out
C. R4(config)#route-map PREPEND permit 10
R4(config-route-map)#set as-path prepend 100 100 100
R4(config)#router bgp 200
R4(config-router)#neighbor 10.2.2.2 route-map PREPEND in
D. R3(config)#route-map PREPEND permit 10
R3(config-route-map)#set as-path prepend 100 100 100
R3(config)#router bgp 200
R3(config-router)#neighbor 10.2.2.2 route-map PREPEND in
170、An engineer reviews a router's logs and discovers the following entry. What is the event's logging severity level?
Router# *Jan 01 38:23:19.579: %LINK-3-UPDOWN: Interface GigabitEthernet0/1, changed state to up
A. warning
B. error
C. notification
D. informational
171、What are two reasons a company would choose a cloud deployment over an on-prem deployment?
(Choose two.)
A. In a cloud environment, the company controls technical issues. On-prem environments rely on the service provider to resolve technical issues.
B. Cloud deployments require long implementation times due to capital expenditure processes. On-prem deployments can be accomplished quickly using operational expenditure processes.
C. Cloud costs adjust up or down depending on the amount of resources consumed. On-prem costs for hardware,power, and space are on-going regardless of usage.
D. Cloud resources scale automatically to an increase in demand. On-prem requires additional capital expenditure.
E. In a cloud environment, the company is in full control of access to their data. On-prem risks access to data due to service provider outages
172、
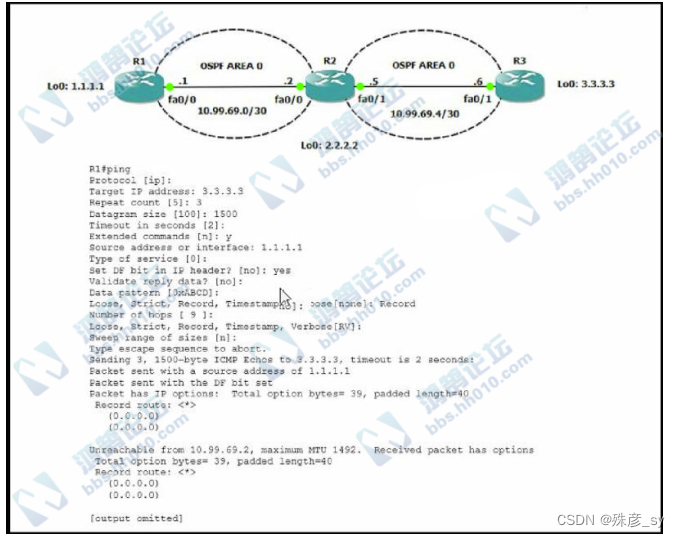
Refer to the exhibit.R1 is able to ping the R3 fa0/1 interface.why do the extended pings fail?
A. R2 and R3 do not have an OSPF adjacency
B. The DF bit has been set
C. R3 is missing a return route to 10.99.69.0/30
D. The maximum packet size accepted by the command is 1476 bytes
173、

Refer to the exhibit.which command when applied to the Atlanta router reduces type 3 LSA flooding into the backbone area and summarizes the inter-area routes on the Dallas router?
A. Atlanta(config-router)# area 1 range 192.168.0.0 255.255.248.0
B. Atlanta(config-router)# area 1 range 192.168.0.0 255.255.252.0
C. Atlanta(config-router)# area 0 range 192.168.0.0 255.255.248.0
D. Atlanta(config-router)# area 0 range 192.168.0.0 255.255.252.0
174、
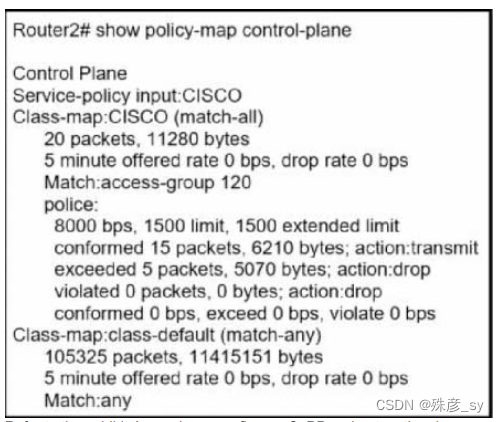
Refer to the exhibit.An engineer configures CoPP and enters the show command to verify the
implementation.what is the result of the configuration?
A. ICMP will be denied based on this configuration
B. If traffic exceeds the specified rate,it will be transmitted and remarked
C. Class-default traffic will be dropped
D. All traffic will be policed on access-list 120
175、

Refer to the exhibit.An engineer reconfigures the port-channel between SW1 and SW2 from an access port to a trunk and immediately notice this error in sw1's log:
*Mar 1 09:47:22.245: %PM-4-ERR_DISABLE:bpduguard error detected on Gi0/0, putting Gi0/0 in errdisable state
which command set resolves this error? D

176、An engineer must configure interface GigabitEthernet0/0 for VRRP group 10.when the router has the highest priority in the group,it must assume the master role.which command set must be added to the initial configuration to accomplish this task? C

177、Which two actions provide controlled Layer 2 network connectivity between virtual machines running on the same hypervisor? (Choose two.)
A. Use a virtual switch running as a separate virtual machine.
B. Use a virtual switch provided by the hypervisor
C. Use a single trunk link to an external Layer2 switch.
D. Use a single routed link to an external router on stick.
E. Use VXLAN fabric after installing VXLAN tunneling drivers on the virtual machines.
178、How does SSO work with HSRP to minimize network disruptions?
A. It enables HSRP to elect another switch in the group as the active HSRP switch.
B. It ensures fast failover in the case of link failure.
C. It enables data forwarding along known routes following a switchover, while the routing protocol reconverges.
D. It enables HSRP to failover to the standby RP on the same device
179、

Refer to the exhibit.A network engineer configures a GRE tunnel and enters the show interface tunnel command. what does the output confirm about the configuration?
A. interface tracking is configured
B. The tunnel mode is set to the default
C. The keepalive value is modified from the default value
D. The physical interface MTU is 1476 bytes
180、
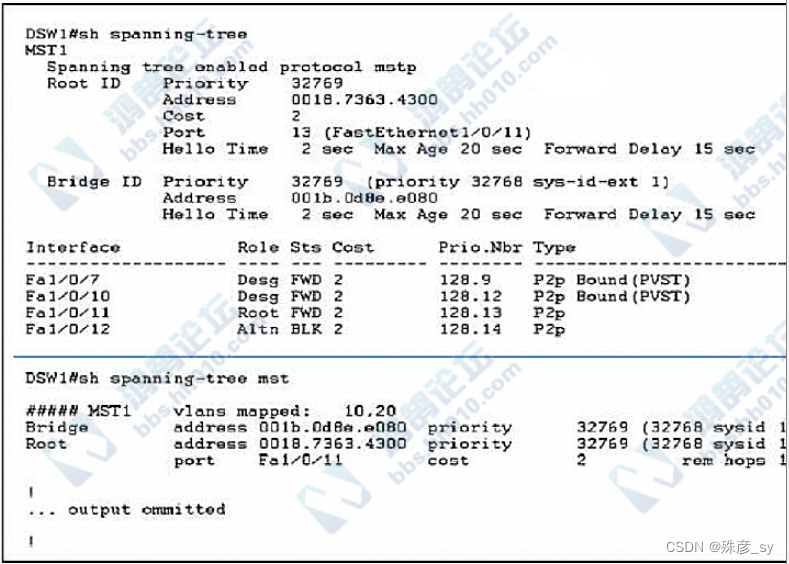
Refer to exhibit.which two commands ensure that DSW1 becones the root bridge for VLAN 10 and 20? (choose two)
A. spanning-tree mst 1 root primary
B. spanning-tree mst 1 priority 1
C. spanning-tree mst vlan 10,20 priority root
D. spanning-tree mst vlan 10,20 root primary
E. spanning-tree mst 1 priority 4096
181、How does the RIB differ from the FIB?
A. The RIB is used to create network topologies and routing tables. The FIB is a list of routes to particular network destination
B. The FIB indudes many routes to a single destination. The RIB is the best route to a single destination.
C. The RIB includes many routes to the same destination prefix. The FIB contains only the best route.
D. The FIB maintains network topologies and routing tables. The RIB is a list of routes to particular network destinations.
182、which antenna type should be used for a site-to-site wireless connection?
A. path
B. omnidirectional
C. dipole
D. Yagi
183、which two characteristics define the intent API provided by Cisco DNA Center?(choose two)
A. northbound API
B. business outcome oriented
C. device-oriented
D. southbound API
E. procedural
184、

Refer to exhibit. An engineer attempts to configure a router on a stick to route packets between
clinet,servers,and printers; howerver,initial tests show that this configuration is not working.which
command set resolves this issue? C

185、
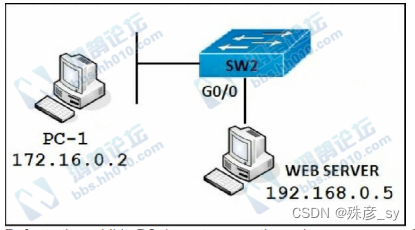
Refer to the exhibit. PC-1 must access the web server on port 8080.To allow this traffic,which statement must be added to an access control list that is applied on SW2 port G0/0 in the inbound direction?
A. permit tcp host 192.168.0.5 It 8080 host 172.16.0.2
B. permit tcp host 172.16.0.2 host 192.168.0.5 eq 8080
C. permit tcp host 192.168.0.5 host 172.16.0.2 eq 8080
D. permit tcp host 192.168.0.5 eq 8080 host 172.16.0.2
186、
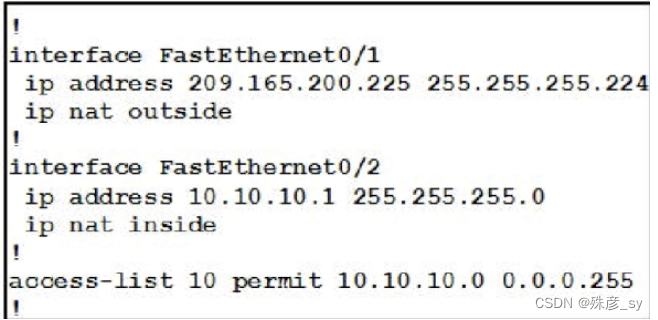
Refer to the exhibit^ Which command allows hosts that are connected to FastEthernetO/2 to access the
Internet?
A. ip nat inside source list 10 interface FastEthemet0/1 overtoad
B. ip nat outside source static 209.165.200.225 10.10.10.0 overload
C. ip nat inside source list 10 interface FastEthernetO/2 overload
D. ip nat outside source Hst 10 interface FastEthernetO/2 overload
187、How is a data modeling language used?
A. To enable data to be easily structured, grouped, validated, and replicated.
B. To represent finite and well-defined network elements that cannot be changed
C. To model the flows of unstructured data within the infrastructure.
D. To provide human readability to scnptmg languages.
188、which technology is used to provide Layer 2 and Layer 3 logical networks in the Cisco SD-Access architecture?
A. underlay network
B. VPN routing/forwarding
C. easy virtual network
D. overlay network
189、

Refer to the exhibit Which router is the designated router on the segment 192 168 0 0/24?
A. Router NewYork because it has a higher router ID.
B. This segment has no designated router because it is a nonbroadcast network type.
C. This segment has no designated router because it is a p2p network type.
D. Router Chicago because it has a lower router ID
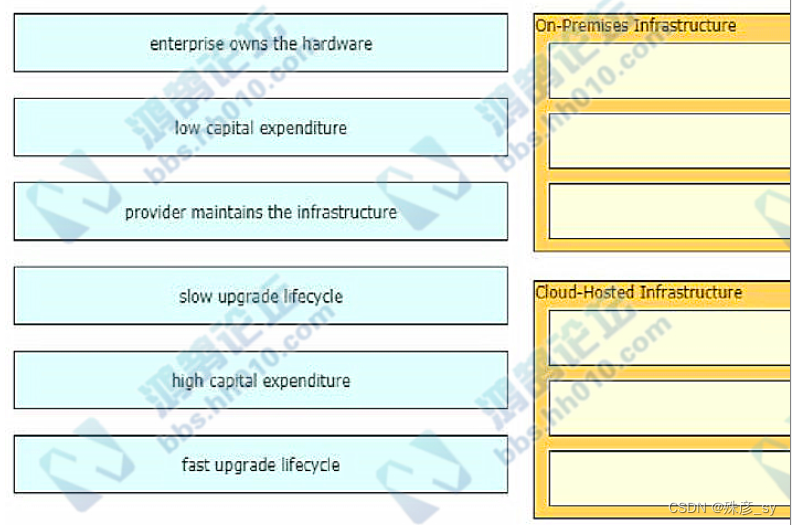
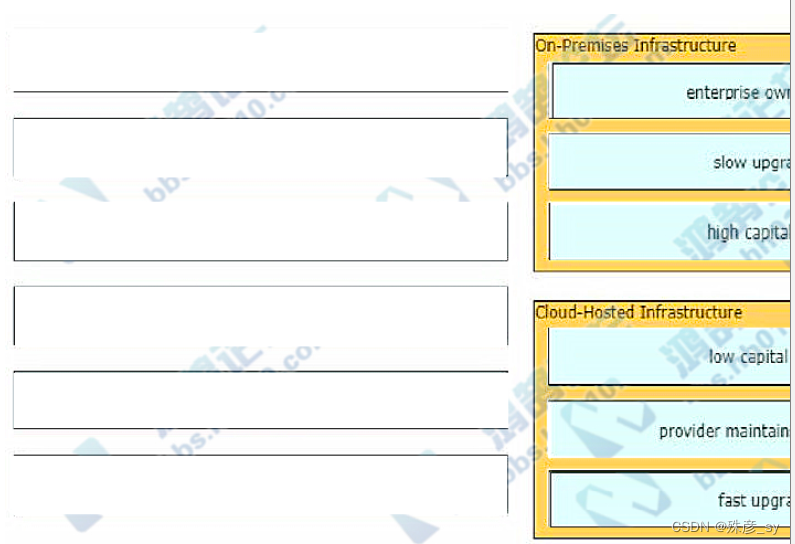
190、Drag and drop the characteristics from the left onto the infrastructure types on the right.
191、Drag and drop the DHCP message that are exchage between a client and an AP into the order they are exchage on the right

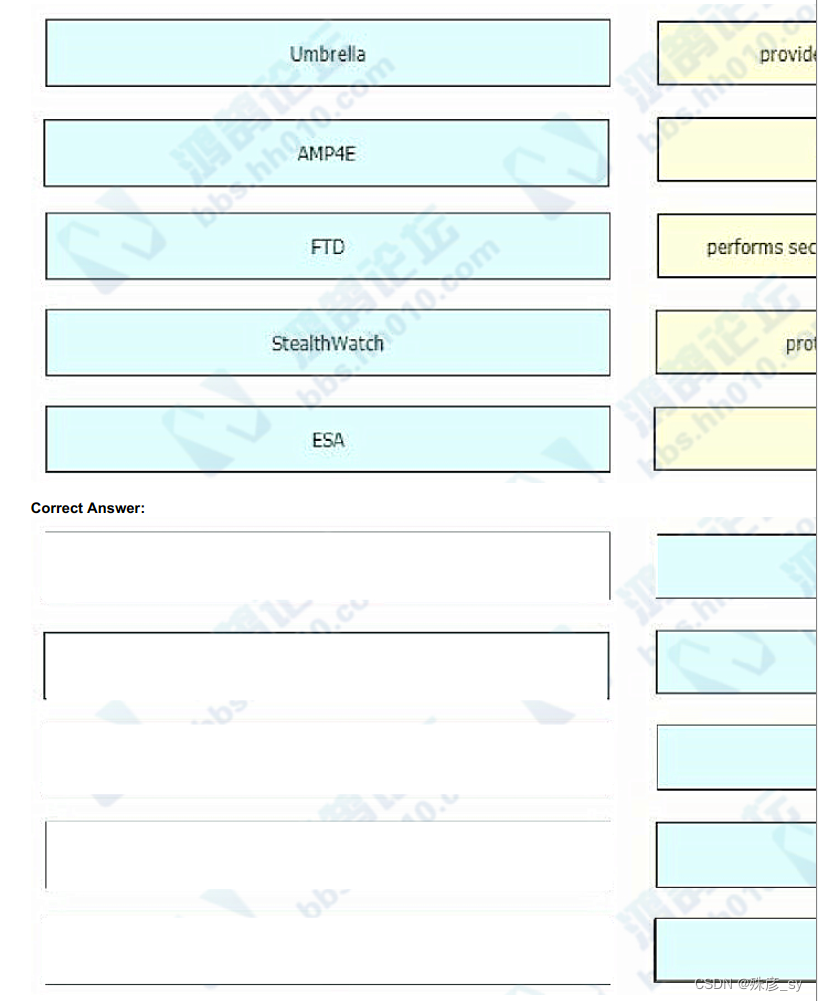
192、Drag and drop the threat defense solutions from the left onto their descriptions on the right
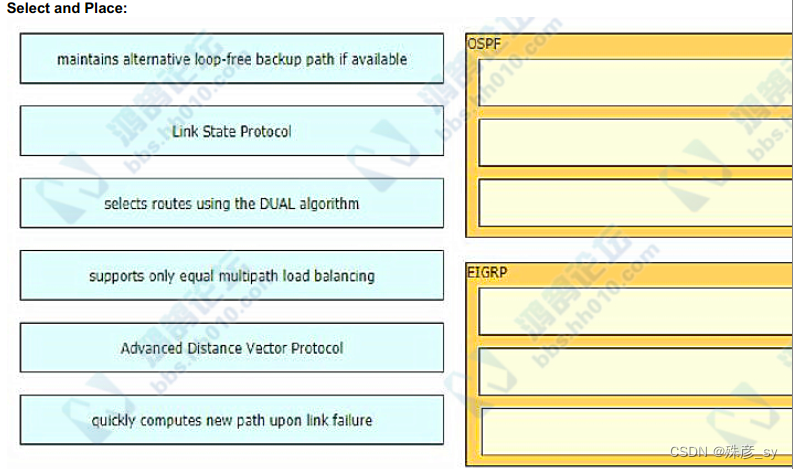
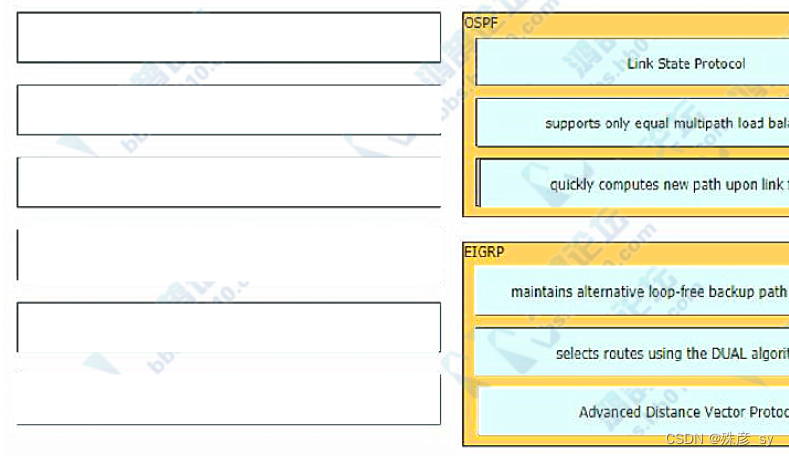
193、Drag and drop the characteristics from the left onto the routing protocols they describe on the right
194、Which element enables communication between guest VMs within a virtualized environment?
A. pNIC
B. vSwitch
C. virtual router
D. hypervisor
195、Which router is elected the IGMP Querier when more than one router is in the same LAN segment?
A. The router with the longest uptime
B. The router with the shortest uptime.
C. The router with the highest IP address
D. The router with the lowest IP address
196、Refer to the exhibit These commands have been added to the configuration of a switch. Which command flags an error if it is added to this configuration?
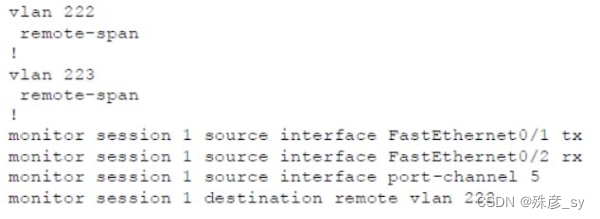
A. monitor session 1 source interface port-channel 6
B. monitor session 1 source vlan 10
C. monitor session 1 source interface FastEthernet0/1 rx
D. monitor session 1 source interface port-channel 7, port channel 8
197、"HTTP/1.1 204 No Content" is returned when the curl -i -X DELETE command is issued. Which situation has occurred?
A. The object could not be located at the URI path.
B. The command succeeded in deleting the object.
C. The object was located at the URI, but it could not be deleted.
D. The URI was invalid.
198、Refer to the exhibit. An engineer must ensure that all traffic leaving AS 200 will choose Link 2 as the exit point. Assuming that all BGP neighbor relationships have been formed and that the attributes have not been changed on any of the routers, which configuration accomplishes this task?
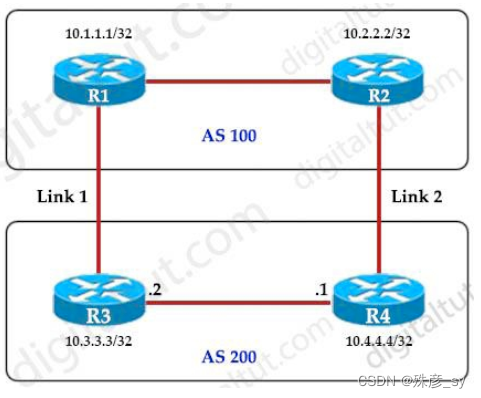
A. R3(config-router)neighbor 10.1.1.1 weight 200
B. R4(config-router)bgp default local-preference 200
C. R3(config-router)bgp default local-preference 200
D. R4(config-router)neighbor 10.2.2.2 weight 200
199、Which action is performed by Link Management Protocol in a Cisco StackWise Virtual domain?
A. It rejects any unidirectional link traffic forwarding
B. It discovers the StackWise domain and brings up SVL interfaces
C. It determines which switch becomes active or standby.
D. It determines if the hardware is compatible to form the StackWise Virtual domain.
200、Which entity is responsible for maintaining Layer 2 isolation between segments in a VXL AN environment?
A. host switch
B. switch fabric
C. VTEP
D. VNID

![[python入门㊽] - 自定义异常 raise 关键字](https://img-blog.csdnimg.cn/21440859a8fa45babbe2c453e888206c.png)

![[安装之2] 台式计算机加固态硬盘,台式机添加固态硬盘教程_台式主机固态硬盘怎么安装](https://img-blog.csdnimg.cn/img_convert/7584f95698dd42feac670cce36263797.jpeg)