101、Refer to the exhibit

SwitchC connects HR and Sales to the Core switch However, business needs require that no traffic from the Finance VLAN traverse this switch.
Which command meets this requirement?
A. SwitchC(config)#vtp pruning
B. SwitchC(config)#vtp pruning vlan 110
C. SwitchC(config)#interface port-channel 1
SwitchC(config-if)#switchport trunk allowed vlan add 210,310
D. SwitchC(config)#interface port-channel 1
SwitchC(config-if)#switchport trunk allowed vlan remove 110
102、Refer to the exhibit.

Which HTTP JSON response does the python code output give?
A. NameError: name 'json' is not defined
B. KeyError 'kickstart_ver_str'
C. 7.61
D. 7.0(3)I7(4)
103、When a wired client connects to an edge switch in an SDA fabric, which component decides whether the client has access to the network?
A. control-plane node
B. Identity Service Engine
C. RADIUS server
D. edge node
104、Refer to the exhibit.
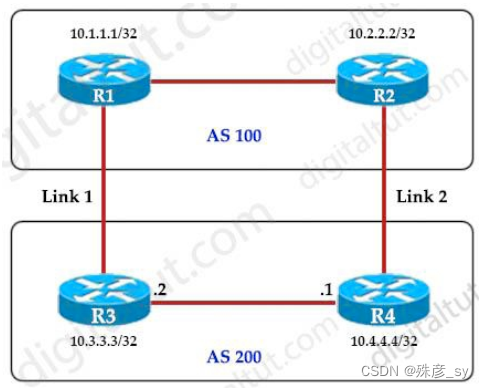
An engineer must ensure that all traffic leaving AS 200 will choose Link 2 as the exit point. Assuming that all BGP neighbor relationships have been formed and that the attributes have not been changed on any of the routers, which configuration accomplish task?
A. R4(config-router)#bgp default local-preference 200
B. R3(config-router)#neighbor 10.1.1.1 weight 200
C. R3(config-router)#bgp default local-preference 200
D. R4(config-router)#neighbor 10.2.2.2 weight 200
105、Which protocol infers that a YANG data model is being used?
A. SNMP
B. REST
C. RESTCONF
D. NX-API
106、Which configuration restricts the amount of SSH that a router accepts to 100 kbps?
A. class-map match-all CoPP_SSH
match access-group name CoPP_SSH
!
Policy-map CoPP_SSH
class CoPP_SSH
police cir 100000
exceed-action drop
! ! !
Interface GigabitEthernet0/1
ip address 209.165.200.225 255.255.255.0
ip access-group CoPP_SSH out
duplex auto
speed auto
media-type rj45
service-policy input CoPP_SSH
!
ip access-list extended CoPP_SSH
permit tcp any any eq 22
!
B. class-map match-all CoPP_SSH
match access-group name CoPP_SSH
!
Policy-map CoPP_SSH
class CoPP_SSH
police cir CoPP_SSH
exceed-action drop
!
Interface GigabitEthernet0/1
ip address 209.165.200.225 255.255.255.0
ip access-group … out
duplex auto
speed auto
media-type rj45
service-policy input CoPP_SSH
!
Ip access-list extended CoPP_SSH
deny tcp any any eq 22
!
C. class-map match-all CoPP_SSH
match access-group name CoPP_SSH
!
Policy-map CoPP_SSH
class CoPP_SSH
police cir 100000
exceed-action drop
!
Control-plane
service-policy input CoPP_SSH
!
Ip access-list extended CoPP_SSH
deny tcp any any eq 22
!
D. class-map match-all CoPP_SSH
match access-group name CoPP_SSH
!
Policy-map CoPP_SSH
class CoPP_SSH
police cir 100000 exceed-action drop
!Control-plane transit
service-policy input CoPP_SSH
!
Ip access-list extended CoPP_SSH
permit tcp any any eq 22
!
107、What NTP stratum level is a server that is connected directly to an authoritative time source?
A. Stratum 0
B. Stratum 1
C. Stratum 14
D. Stratum 15
108、How does QoS traffic shaping alleviate network congestion?
A. It drops packets when traffic exceeds a certain bitrate.
B. It buffers and queue packets above the committed rate.
C. It fragments large packets and queues them for delivery.
D. It drops packets randomly from lower priority queues.
109、n engineer is describing QoS to a client. Which two facts apply to traffic policing? (Choose two)
A. Policing adapts to network congestion by queuing excess trafficB. Policing should be performed as close to the destination as possible
C. Policing drops traffic that exceeds the defined rate
D. Policing typically delays the traffic, rather than drops it
E. Policing should be performed as close to the source as possible
110、What mechanism does PIM use to forward multicast traffic?
A. PIM sparse mode uses a pull model to deliver multicast traffic
B. PIM dense mode uses a pull model to deliver multicast traffic
C. PIM sparse mode uses receivers to register with the RP
D. PIM sparse mode uses a flood and prune model to deliver multicast traffic
111、Which two namespaces does the LISP network architecture and protocol use? (Choose two)
A. TLOC
B. RLOC
C. DNS
D. VTEP
E. EID
112、Which First Hop Redundancy Protocol should be used to meet a design requirements for
more efficient default bandwidth usage across multiple devices?
A. GLBP
B. LCAP
C. HSRP
D. VRRP
113、Refer to the exhibit.

A network engineer is configuring OSPF between router R1 and router R2. The engineer must ensure that a DR/BDR election does not occur on the Gigabit Ethernet interfaces in area 0. Which configuration set accomplishes this goal?
A. R1 (config-if) #interface Gi0/0
R1 (config-if) #ip ospf network point-to-point
R2 (config-if) #interface Gi0/0
R2 (config-if) #ip ospf network point-to-point
B. R1 (config-if) #interface Gi0/0
R1 (config-if) #ip ospf network broadcast
R2(config-if)#interface Gi0/0
R2(config-if)#ip ospf network broadcast
C. R1(config-if)#interface Gi0/0
R1(config-if)#ip ospf database-filter all out
R2(config-if)#interface Gi0/0
R2(config-if)#ip ospf database-filter all out
D. R1(config-if)#interface Gi0/0
R1(config-if)#ip ospf priority 1
R2(config-if)#interface Gi0/0
R2(config-if)#ip ospf priority 1
114、What are two reasons why broadcast radiation is caused in the virtual machine environment? (Choose two)
A. vSwitch must interrupt the server CPU to process the broadcast packet
B. The Layer 2 domain can be large in virtual machine environments
C. Virtual machines communicate primarily through broadcast modeD. Communication between vSwitch and network switch is broadcast based
E. Communication between vSwitch and network switch is multicast based
115、A company plans to implement intent-based networking in its campus infrastructure. Which design facilities a migrate from a traditional campus design to a programmer fabric designer?
A. Layer 2 access
B. three-tier
C. two-tier
D. routed access
116、When a wireless client roams between two different wireless controllers, a network connectivity outage is experience for a period of time. Which configuration issue would cause this problem?
A. Not all of the controllers in the mobility group are using the same mobility group name
B. Not all of the controllers within the mobility group are using the same virtual interface IP address
C. All of the controllers within the mobility group are using the same virtual interface IP address
D. All of the controllers in the mobility group are using the same mobility group name
117、Which algorithms are used to secure REST API from brute attacks and minimize the impact?
A. SHA-512 and SHA-384
B. MD5 algorithm-128 and SHA-384
C. SHA-1, SHA-256, and SHA-512
D. PBKDF2, BCrypt, and SCrypt
118、What is the role of the RP in PIM sparse mode?
A. The RP responds to the PIM join messages with the source of requested multicast group
B. The RP maintains default aging timeouts for all multicast streams requested by the receivers
C. The RP acts as a control-plane node and does not receive or forward multicast packets
D. The RP is the multicast that is the root of the PIM-SM shared multicast distribution tree
119、A network administrator is preparing a Python script to configure a Cisco IOS XE-based device on the network. The administrator is worried that colleagues will make changes to the device while the script is running. Which operation of the client manager in prevent colleague making changes to the device while the script is running?
A. m.lock (config=’running’)
B. m.lock (target=’running’)
C. m.freeze (target=’running’)
D. m.freeze(config=’running’)
120、What are two device roles in Cisco SD-Access fabric? (Choose two)
A. core switch
B. vBond controller
C. edge node
D. access switch
E. border node
121、Drag and drop the LISP components from the left onto the function they perform on the right. Not all options are used.

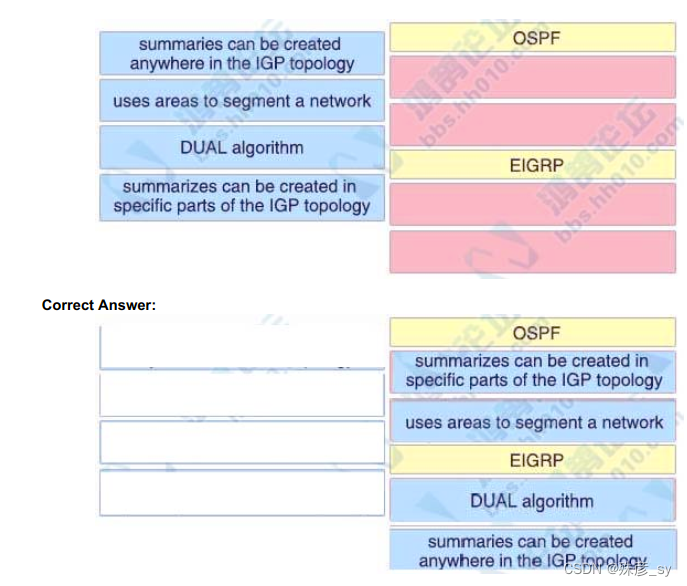
122、Drag and Drop the descriptions from the left onto the routing protocol they describe on the right.
123、Which component handles the orchestration plane of the Cisco SD-WAN?
A. vBond
B. vSmart
C. vManage
D. vEdge
124、Which two entities are Type 1 hypervisors? (Choose two)
A. Oracle VM Virtual Box
B. Microsoft Hyper-V
C. VMware server
D. VMware ESX
E. Microsoft Virtual PC
125、Which access point mode allows a supported AP to function like a WLAN client would, associating and identifying client connectivity issues?
A. client mode
B. SE-connect mode
C. sensor mode
D. sniffer mode
126、Refer to the exhibit
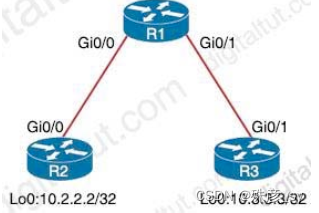
An engineer must deny Telnet traffic from the loopback interface of router R3 to the loopback interface of
router R2 during the weekend hours. All other traffic between the loopback interfaces of routers R3 and R2
must be allowed at all times. Which command accomplish this task?
A. R3(config)#time-range WEEKEND
R3(config-time-range)#periodic Saturday Sunday 00:00 to 23:59
R3(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range WEEKEND
R3(config)#access-list 150 permit ip any any time-range WEEKENDR3(config)#interface Gi0/1
R3(config-if)#ip access-group 150 out
B. R1(config)#time-range WEEKEND
R1(config-time-range)#periodic Friday Sunday 00:00 to 00:00
R1(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range WEEKEND
R1(config)#access-list 150 permit ip any any
R1(config)#interface Gi0/1
R1(config-if)#ip access-group 150 in
C. R1(config)#time-range WEEKEND
R1(config-time-range)#periodic weekend 00:00 to 23:59
R1(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range WEEKEND
R1(config)#access-list 150 permit ip any any
R1(config)#interface Gi0/1
R1(config-if)#ip access-group 150 in
D. R3(config)#time-range WEEKEND
R3(config-time-range)#periodic weekend 00:00 to 23:59
R3(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range WEEKEND
R3(config)#access-list 150 permit ip any any time-range WEEKEND
R3(config)#interface Gi0/1
R3(config-if)#ip access-group 150 out
127、Which tool is used in Cisco DNA Center to build generic configurations that are able to be applied on device with similar network settings?
A. Command Runner
B. Template Editor
C. Application Policies
D. Authentication Template
128、A client device roams between access points located on different floors in an atrium. The access points joined to the same controller and configuration in local mode. The access points are in different IP addresses, but the client VLAN in the group same. What type of roam occurs?
A. inter-controller
B. inter-subnet
C. intra-VLAN
D. intra-controller
129、What does the LAP send when multiple WLCs respond to the CISCO_CAPWAPCONTROLLER.localdomain hostname during the CAPWAP discovery and join process?
A. broadcast discover request
B. join request to all the WLCs
C. unicast discovery request to each WLC
D. Unicast discovery request to the first WLC that resolves the domain name
130、Refer to the exhibit.

What is the result when a technician adds the monitor session 1 destination remote vlan 233 command?
A. The RSPAN VLAN is replaced by VLAN 223
B. RSPAN traffic is sent to VLANs 222 and 223
C. An error is flagged for configuring two destinations
D. RSPAN traffic is split between VLANs 222 and 223
131、In an SD-Access solution what is the role of a fabric edge node?
A. to connect external Layer 3- network to the SD-Access fabric
B. to connect wired endpoint to the SD-Access fabric
C. to advertise fabric IP address space to external network
D. to connect the fusion router to the SD-Access fabric
132、Refer to the exhibit.
access-list 1 permit 172.16.1.0 0.0.0.255
ip nat inside source list 1 interface gigabitethernet0/0 overload
The inside and outside interfaces in the NAT configuration of this device have been correctly identified.
What is the effect of this configuration?
A. dynamic NAT
B. static NAT
C. PAT
D. NAT64
133、Which component of the Cisco Cyber Threat Defense solution provides user and flow context analysis?
A. Cisco Firepower and FireSIGHT
B. Cisco Stealth watch system
C. Advanced Malware Protection
D. Cisco Web Security Appliance
134、An engineer must protect their company against ransom ware attacks. Which solution allows the engineer to block the execution stage and prevent file encryption?
A. Use Cisco AMP deployment with the Malicious Activity Protection engineer enabled
B. Use Cisco AMP deployment with the Exploit Prevention engine enabled
C. Use Cisco Firepower and block traffic to TOR networks
D. Use Cisco Firepower with Intrusion Policy and snort rules blocking SMB exploitation
135、Refer to the exhibit.
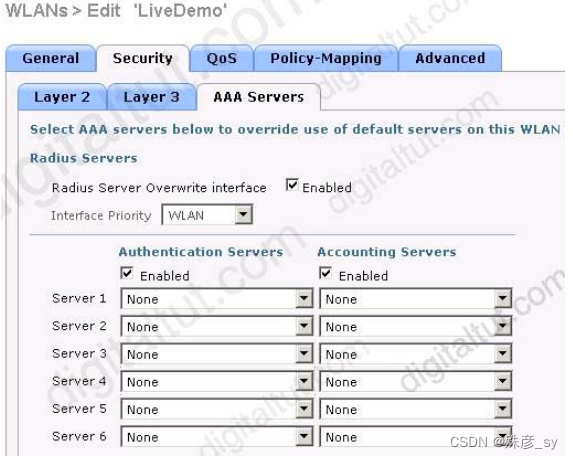
Assuming the WLC’s interfaces are not in the same subnet as the RADIUS server, which interface would the WLC use as the source for all RADIUS-related traffic?
A. the interface specified on the WLAN configuration
B. any interface configured on the WLC
C. the controller management interface
D. the controller virtual interface
136、Which benefit is offered by a cloud infrastructure deployment but is lacking in an on-premises deployment?
A. efficient scalability
B. virtualization
C. storage capacity
D. supported systems
137、Wireless users report frequent disconnections from the wireless network. While troubleshooting a network engineer finds that after the user a disconnect, the connection reestablishes automatically without any input required. The engineer also notices these message logs.

Which action reduces the user impact?
A. increase the dynamic channel assignment interval
B. increase BandSelect
C. increase the AP heartbeat timeout
D. enable coverage hole detection
138、 Which DHCP option helps lightweight APs find the IP address of a wireless LAN controller?
A. Option 43
B. Option 60
C. Option 67
D. Option 150
139、What is the process of password checks when a login attempt is made to the device?
A. A TACACS+ server is checked first. If that check fail, a database is checked
B. A TACACS+ server is checked first. If that check fail, a RADIUS server is checked. If that check fail, a local database is checked
C. A local database is checked first. If that fails, a TACACS+server is checked, if that check fails, a RADIUS server is checked
D. A local database is checked first. If that check fails, a TACACS+server is checked
140、What is the role of the vsmart controller in a Cisco SD-WAN environment?
A. IT performs authentication and authorization
B. It manages the control plane
C. It is the centralized network management system
D. It manages the data plane
141、Why is an AP joining a different WLC than the one specified through option 43?
A. The WLC is running a different software version
B. The API is joining a primed WLC
C. The AP multicast traffic unable to reach the WLC through Layer 3
D. The APs broadcast traffic is unable to reach the WLC through Layer 2
142、Which devices does Cisco Center configure when deploying an IP-based access control policy?
A. All devices integrating with ISE
B. selected individual devices
C. all devices in selected sites
D. all wired devices
143、Which method of account authentication does OAuth 2.0 within REST APIs?
A. username/role combination
B. access tokens
C. cookie authentication
D. basic signature workflow
144、What does the Cisco DNA Center use to enable the delivery of applications through a network and to yield analytics for innovation?
A. process adapters
B. Command Runner
C. intent-based APIs
D. domain adapters
145、Which action is a function of VTEP in VXLAN?
A. tunneling traffic from IPv6 to IPv4 VXLANs
B. allowing encrypted communication on the local VXLAN Ethernet segment
C. encapsulating and de-encapsulating VXLAN Ethernet frames
D. tunneling traffic from IPv4 to IPv6 VXLANs
146、Which type of antenna does the radiation pattern represent?

A. Yagi
B. multidirectional
C. directional patch
D. omnidirectional
147、Refer to the exhibit

Which command set resolves this error?
A. Sw1(config)# interface G0/0
Sw1(config-if)# no spanning-tree bpduguard enable
Sw1(config-if)# shut
Sw1(config-if)# no shut
B. Sw1(config)# interface G0/0
Sw1(config-if)# spanning-tree bpduguard enable
Sw1(config-if)# shut
Sw1(config-if)# no shut
C. Sw1(config)# interface G0/1
Sw1(config-if)# spanning-tree bpduguard enable
Sw1(config-if)# shut
Sw1(config-if)# no shut
D. Sw1(config)# interface G0/0
Sw1(config-if)# no spanning-tree bpdufilter
Sw1(config-if)# shut
Sw1(config-if)# no shut
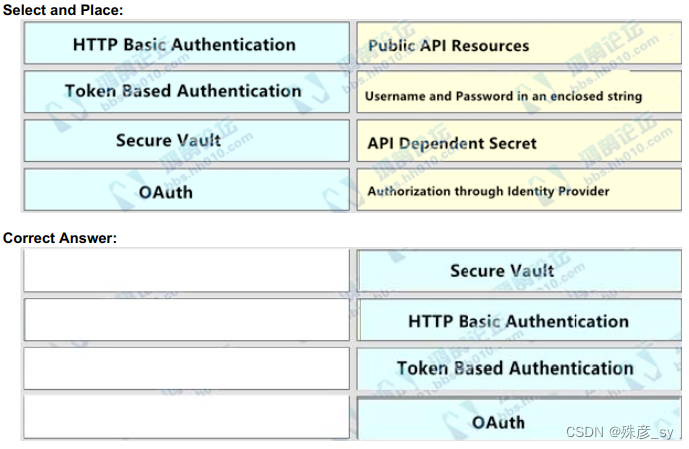
148、Drag and drop the REST API authentication method from the left to the description on the right.
149、Which two security features are available when implementing NTP? (Choose two.)
A. symmetric server passwords
B. dock offset authentication
C. broadcast association mode
D. encrypted authentication mechanism
E. access list-based restriction scheme
150、What is calculated using the numerical values of the transmitter power level, cable loss, and antenna gain?
A. EIRP
B. dBi
C. RSSI
D. SNR


![[一键CV] Blazor 拖放上传文件转换格式并推送到浏览器下载](https://user-images.githubusercontent.com/8428709/205942253-8ff5f9ca-a033-4707-9c36-b8c9950e50d6.png)