1、Which function does a fabric edge node perform in an SD-Access deployment?
A. Connects endpoints to the fabric and forwards their traffic.
B. Encapsulates end-user data traffic into LISP.
C. Connects the SD-Access fabric to another fabric or external Layer 3 networks.
D. Provides reachability between border nodes in the fabric underlay.
2、Refer to the exhibit.

Which privilege level is assigned to VTY users?
A. 1
B. 7
C. 13
D. 15
3、What is the difference between a RIB and a FIB?
A. The FIB is populated based on RIB content.
B. The RIB maintains a minor image of the FIB.
C. The RIB is used to make IP source prefix-based switching decisions.
D. The FIB is where all IP routing information is stored.
4、Which requirement for an Ansible-managed node is true?
A. It must have an SSH server running.
B. It must be a Linux server or a Cisco device.
C. It must support ad hoc commands.
D. It must have an Ansible Tower installed.
5、A client device fails to see the enterprise SSID, but other client devices are connected to it.
What is the cause of this issue?
A. The client has incorrect credentials stored for the configured broadcast SSID.
B. The hidden SSID was not manually configured on the client.
C. The broadcast SSID was not manually configured on the client.
D. The client has incorrect credentials stored for the configured hidden SSID.
6、Which two descriptions of FlexConnect mode for Cisco APs are true? (Choose two.)
A. APs that operate in FlexConnect mode cannot detect rogue APs
B. FlexConnect mode is used when the APs are set up in a mesh environment and used to bridge between each other.
C. FlexConnect mode is a feature that is designed to allow specified CAPWAP-enabled APs to exclude themselves from managing data traffic between clients and infrastructure.
D. When connected to the controller, FlexConnect APs can tunnel traffic back to the controller
E. FlexConnect mode is a wireless solution for branch office and remote office deployments
7、Which OSPF network types are compatible and allow communication through the two peering devices?
A. point-to-multipoint to nonbroadcast
B. broadcast to nonbroadcast
C. point-to-multipoint to broadcast
D. broadcast to point-to-point
8、Which NGFW mode blocks flows crossing the firewall?
A. tap
B. inline
C. passive
D. inline tap
9、Which statement about route targets is true when using VRF-Lite?
A. Route targets control the import and export of routes into a customer routing table.
B. When BGP is configured, route targets are transmitted as BGP standard communities.
C. Route targets allow customers to be assigned overlapping addresses.
D. Route targets uniquely identify the customer routing table.
10、How does Cisco TrustSec enable more flexible access controls for dynamic networking environments and data centers?
A. uses flexible NetFlow
B. assigns a VLAN to the endpoint
C. classifies traffic based on advanced application recognition
D. classifies traffic based on the contextual identity of the endpoint rather than its IP address
11、Refer to the exhibit

Which statement about the OPSF debug output is true?
A. The output displays OSPF hello messages which router R1 has sent or received on interface Fa0/1.
B. The output displays OSPF messages which router R1 has sent or received on all interfaces.
C. The output displays OSPF messages which router R1 has sent or received on interface Fa0/1.
D. The output displays OSPF hello and LSACK messages which router R1 has sent or received.
12、Which LISP infrastructure device provides connectivity between non-LISP sites and LISP sites by receiving non-LISP traffic with a LISP site destination?
A. PITR
B. map resolver
C. map server
D. PETR
13、Which two protocols are used with YANG data models? (Choose two.)
A. TLS
B. RESTCONF
C. SSH
D. NETCONF
E. HTTPS
14、Which HTTP status code is the correct response for a request with an incorrect password applied to a REST API session?
A. HTTP Status Code: 200
B. HTTP Status Code: 302
C. HTTP Status Code: 401
D. HTTP Status Code: 504
15、The login method is configured on the VTY lines of a router with these parameters.. The first method for authentication is TACACS
. If TACACS is unavailable, login is allowed without any provided credentials
Which configuration accomplishes this task? D

16、Which statement about multicast RPs is true?
A. RPs are required only when using protocol independent multicast dense mode.
B. RPs are required for protocol independent multicast sparse mode and dense mode.
C. By default, the RP is needed periodically to maintain sessions with sources and receivers.
D. By default, the RP is needed only to start new sessions with sources and receivers.
17、To increase total throughput and redundancy on the links between the wireless controller and switch, the customer enabled LAG on the wireless controller.
Which EtherChannel mode must be configured on the switch to allow the WLC to connect?
A. Active
B. Passive
C. On
D. Auto
18、Which feature does Cisco TrustSec use to provide scalable, secure communication throughout a network?
A. security group tag ACL assigned to each port on a switch
B. security group tag number assigned to each user on a switch
C. security group tag number assigned to each port on a network
D. security group tag ACL assigned to each router on a network
19、An engineer configures a WLAN with fast transition enabled. Some legacy clients fail to connect to this WLAN.
Which feature allows the legacy clients to connect while still allowing other clients to use fast transition based on their OUIs?
A. over the DS
B. 802.11k
C. adaptive R
D. 802.11v
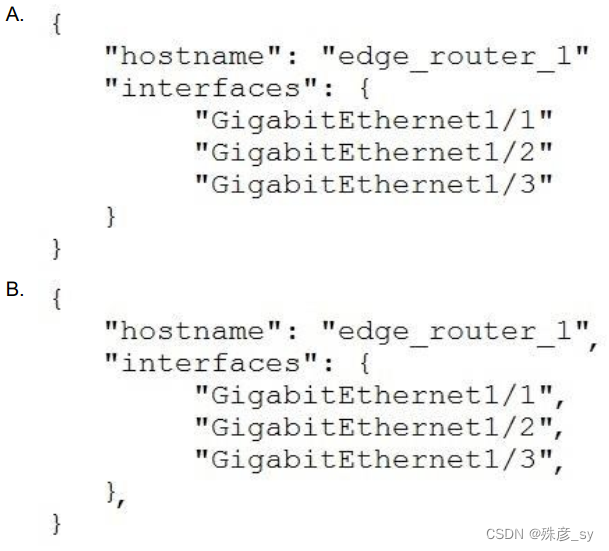
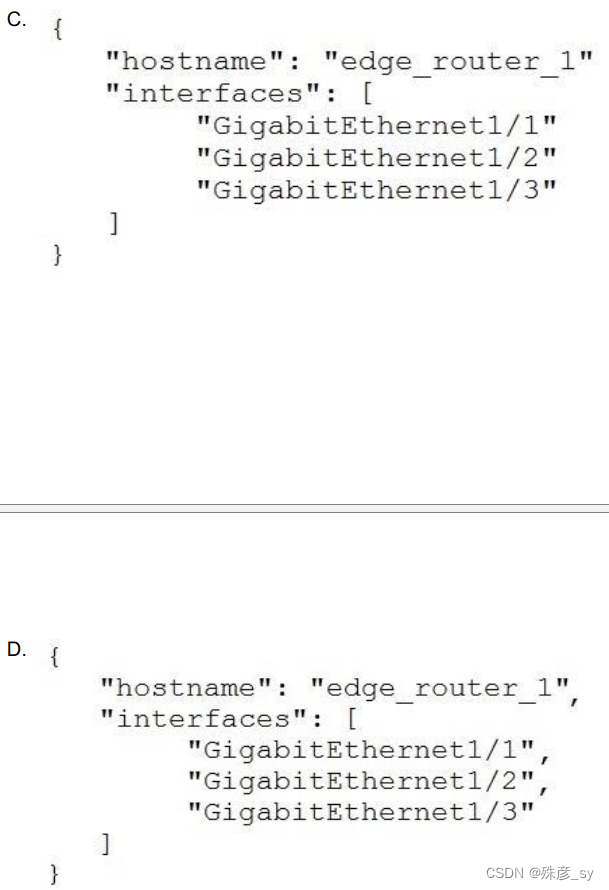
20、Which exhibit displays a valid JSON file? D
21、A network administrator is implementing a routing configuration change and enables routing debugs to track routing behavior during the change. The logging output on the terminal is interrupting the command typing process.
Which two actions can the network administrator take to minimize the possibility of typing commands incorrectly? (Choose two.)
A. Configure the logging synchronous global configuration command.
B. Configure the logging synchronous command under the vty.
C. Increase the number of lines on the screen using the terminal length command.
D. Configure the logging delimiter feature.
E. Press the TAB key to reprint the command in a new line
22、Which two pieces of information are necessary to compute SNR? (Choose two.)
A. transmit power
B. noise floor
C. EIRP
D. antenna gain
E. RSSI
23、Which statements are used for error handling in Python?
A. try/catch
B. catch/release
C. block/rescue
D. try/except
24、What are two benefits of virtualizing the server with the use of VMs in a data center environment? (Choose two.)
A. reduced rack space, power, and cooling requirements
B. smaller Layer 2 domain
C. increased security
D. speedy deployment
E. reduced IP and MAC address requirements
25、Which two steps are required for a complete Cisco DNA Center upgrade? (Choose two.)
A. automation backup
B. system update
C. golden image selection
D. proxy configuration
E. application updates
26、What is a benefit of data modeling languages like YANG?
A. They create more secure and efficient SNMP OIDs.
B. They provide a standardized data structure, which results in configuration scalability and consistency.
C. They enable programmers to change or write their own applications within the device operating system.
D. They make the CLI simpler and more efficient
27、Refer to the exhibit.
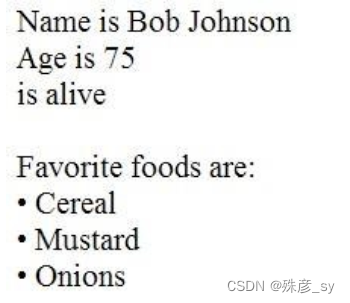
What is the JSON syntax that is formed from the data?
A. {Name: Bob Johnson, Age: 75, Alive: true, Favorite Foods: [Cereal, Mustard, Onions]}
B. {“Name”: “Bob Johnson”, “Age”: 75, “Alive”: true, “Favorite Foods”: [“Cereal”, “Mustard”, “Onions”]}
C. {‘Name’: ‘Bob Johnson’, ‘Age’: 75, ‘Alive’: True, ‘Favorite Foods’: ‘Cereal’, ‘Mustard’, ‘Onions’}
D. {“Name”: “Bob Johnson”, “Age”: Seventyfive, “Alive”: true, “Favorite Foods”: [“Cereal”, “Mustard”,
“Onions”]}
28、Based on this interface configuration, what is the expected state of OSPF adjacency?
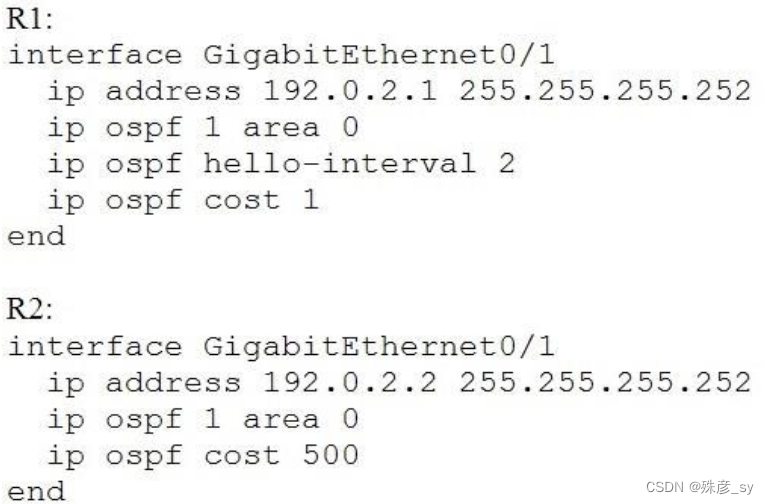
A. 2WAY/DROTHER on both routers
B. not established
C. FULL on both routers
D. FULL/BDR on R1 and FULL/BDR on R2
29、Refer to the exhibit.

Link1 is a copper connection and Link2 is a fiber connection. The fiber port must be the primary port for all forwarding. The output of the show spanning-tree command on SW2 shows that the fiber port is blocked by spanning tree. An engineer enters the spanning-tree port-priority 32 command on G0/1 on SW2, but the port remains blocked.
Which command should be entered on the ports that are connected to Link2 to resolve the issue?
A. Enter spanning-tree port-priority 4 on SW2.
B. Enter spanning-tree port-priority 32 on SW1.
C. Enter spanning-tree port-priority 224 on SW1.
D. Enter spanning-tree port-priority 64 on SW2.
30、Which JSON syntax is valid?
A. {“switch”: “name”: “dist1”, “interfaces”: [“gig1”, “gig2”, “gig3”]}
B. {/“switch/”: {/“name/”: “dist1”, /“interfaces/”: [“gig1”, “gig2”, “gig3”]}}
C. {“switch”: {“name”: “dist1”, “interfaces”: [“gig1”, “gig2”, “gig3”]}}
D. {‘switch’: (‘name’: ‘dist1’, ‘interfaces’: [‘gig1’, ‘gig2’, ‘gig3’])}
31、What are two common sources of interference for Wi-Fi networks? (Choose two.)
A. LED lights
B. radar
C. fire alarm
D. conventional oven
E. rogue AP
32、When using TLS for syslog, which configuration allows for secure and reliable transportation of messages to its default port?
A. logging host 10.2.3.4 vrf mgmt transport tcp port 514
B. logging host 10.2.3.4 vrf mgmt transport udp port 514
C. logging host 10.2.3.4 vrf mgmt transport tcp port 6514
D. logging host 10.2.3.4 vrf mgmt transport udp port 6514
33、Which behavior can be expected when the HSRP version is changed from 1 to 2?
A. No changes occur because the standby router is upgraded before the active router.
B. No changes occur because version 1 and 2 use the same virtual MAC OUI.
C. Each HSRP group reinitializes because the virtual MAC address has changed.
D. Each HSRP group reinitializes because the multicast address has changed.
34、Which protocol does REST API rely on to secure the communication channel?
A. HTTP
B. SSH
C. HTTPS
D. TCP
35、Refer to this output.
R1# *Feb 14 37:09:53.129: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up
What is the logging severity level?
A. notification
B. emergency
C. critical
D. alert
36、Refer to the exhibit.
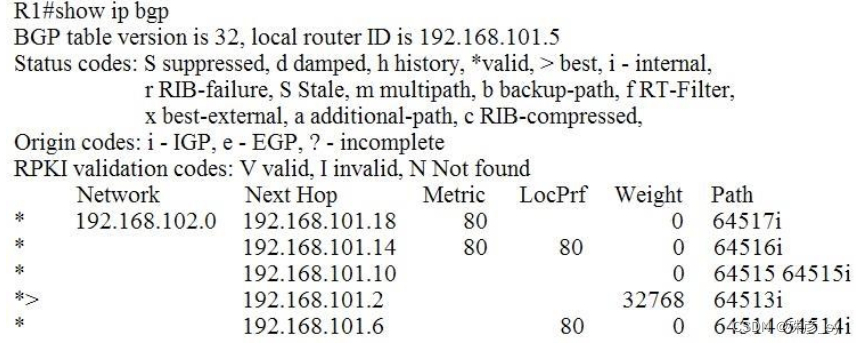
Which IP address becomes the active next hop for 192.168.102.0/24 when 192.168.101.2 fails?
A. 192.168.101.10
B. 192.168.101.14
C. 192.168.101.6
D. 192.168.101.18
37、Which PAgP mode combination prevents an EtherChannel from forming?
A. auto/desirable
B. desirable/desirable
C. desirable/auto
D. auto/auto
38、If a VRRP master router fails, which router is selected as the new master router?
A. router with the lowest priority
B. router with the highest priority
C. router with the highest loopback address
D. router with the lowest loopback address
39、Which QoS component alters a packet to change the way that traffic is treated in the network?
A. policing
B. classification
C. marking
D. shaping
40、Refer to the exhibit.
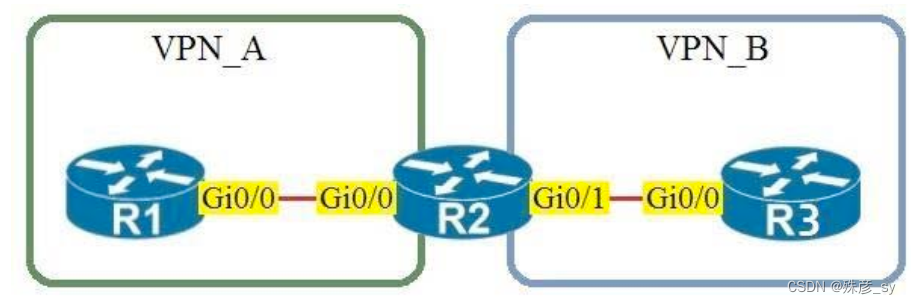
Assuming that R1 is a CE router, which VRF is assigned to Gi0/0 on R1?
A. default VRF
B. VRF VPN_A
C. VRF VPN_B
D. management VRF
41、Refer to the exhibit.
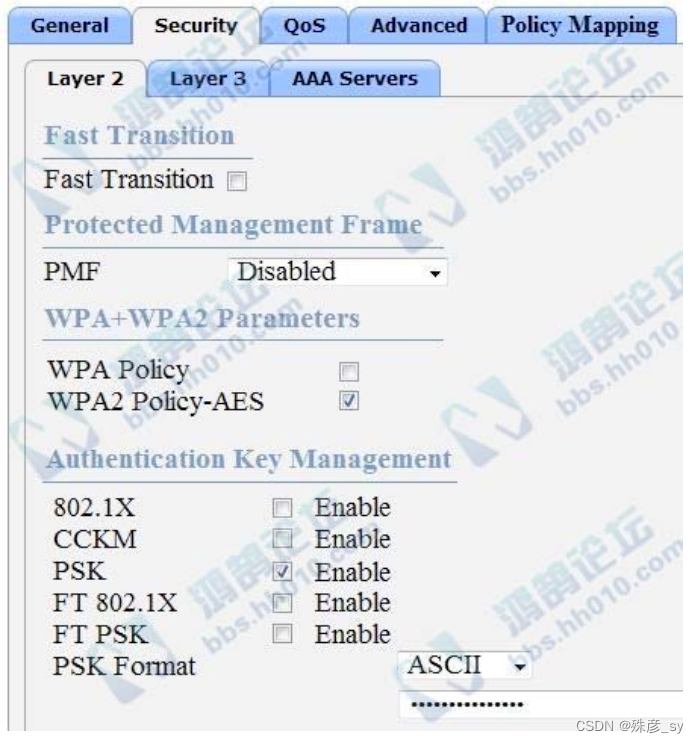
Based on the configuration in this WLAN security setting, which method can a client use to authenticate to
the network?
A. text string
B. username and password
C. RADIUS token
D. certificate
42、Which two mechanisms are available to secure NTP? (Choose two.)
A. IPsec
B. IP prefix list-based
C. encrypted authentication
D. TACACS-based authentication
E. IP access list-based
43、Which technology provides a secure communication channel for all traffic at Layer 2 of the OSI model?
A. SSL
B. Cisco TrustSec
C. MACsec
D. IPsec
44、Refer to the exhibit.
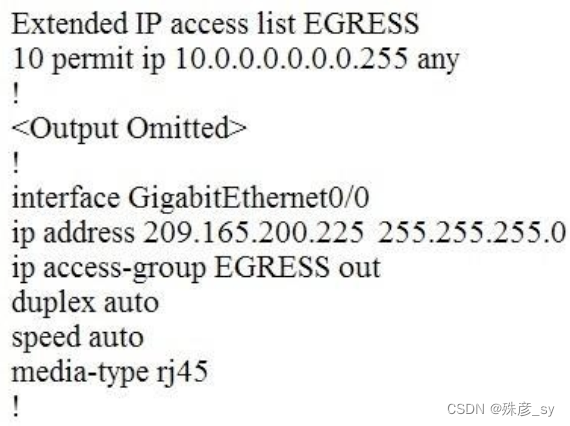
An engineer must block all traffic from a router to its directly connected subnet 209.165.200.0/24. The engineer applies access control list EGRESS in the outbound direction on the GigabitEthernet0/0 interface of the router. However, the router can still ping hosts on the 209.165.200.0/24 subnet.
Which explanation of this behavior is true?
A. Access control lists that are applied outbound to a router interface do not affect traffic that is sourced from the router.
B. After an access control list is applied to an interface, that interface must be shut and no shut for the access control list to take effect.
C. Only standard access control lists can block traffic from a source IP address.
D. The access control list must contain an explicit deny to block traffic from the router.
45、Which two methods are used by an AP that is trying to discover a wireless LAN controller? (Choose two.)
A. Cisco Discovery Protocol neighbor
B. querying other APs
C. DHCP Option 43
D. broadcasting on the local subnet
E. DNS lookup CISCO-DNA-PRIMARY.localdomain
46、Which IP SLA operation requires the IP SLA responder to be configured on the remote end?
A. UDP jitter
B. ICMP jitter
C. TCP connect
D. ICMP echo
47、Which statement explains why Type 1 hypervisor is considered more efficient than Type2 hypervisor?
A. Type 1 hypervisor is the only type of hypervisor that supports hardware acceleration techniques.
B. Type 1 hypervisor relies on the existing OS of the host machine to access CPU, memory, storage, and network resources.
C. Type 1 hypervisor runs directly on the physical hardware of the host machine without relying on the underlying OS.
D. Type 1 hypervisor enables other operating systems to run on it.
48、A client with IP address 209.165.201.25 must access a web server on port 80 at 209.165.200.225. To allow this traffic, an engineer must add a statement to an access control list that is applied in the inbound direction on the port connecting to the web servers.
Which statement allows this traffic?
A. permit tcp host 209.165.200.225 lt 80 host 209.165.201.25
B. permit tcp host 209.165.201.25 host 209.165.200.225 eq 80
C. permit tcp host 209.165.200.225 eq 80 host 209.165.201.25
D. permit tcp host 209.165.200.225 host 209.165.201.25 eq
49、In OSPF, which LSA type is responsible for pointing to the ASBR router?
A. type 1
B. type 2
C. type 3
D. type 4
50、Refer to the exhibit.

VLANs 50 and 60 exist on the trunk links between all switches. All access ports on SW3 are configured for VLAN 50 and SW1 is the VTP server.
Which command ensures that SW3 receives frames only from VLAN 50?
A. SW1(config)#vtp mode transparent
B. SW3(config)#vtp mode transparent
C. SW2(config)#vtp pruning
D. SW1(config)#vtp pruning