AWS IAM
自用笔记。
Terms
IAM - Identity and Access Management, a global service
-
it gives:
- Centralized control of AWS account
- Shared access to AWS account
- Granular permissions
- Identity Federation, i.e., Facebook, LinkedIn etc.
-
it allows:
- Multi-Factor Authentications
- Temporary access for users/devices and services
- Set up own password rotationpolicy.
- Integrates with many different AWS services
- Suppor PCI DSS compliance
Root Account - created by default, shouldn’t be used or shared
Users - people within the organizations, and can be grouped. Users don’t have to belong to a group, and also can be belong to multiple groups
Groups - a collection of users under one set of permissions. Only contain users, not other groups
Roles - can be assigned to users, applications, and services to give access to AWS resources
AKA IAM roles, that will assign permissions to AWS services. Common roles: EC2 Instance Roles, Lambda Function Roles, Roles for CloudFormation
Policy - a (JSON) documnet that defines one or more permissions. It can be attached to a user, group or a role. The policy defines the permissions of the users. In AWS, the least privilege principle should be applied.
Practice Creating and Managing Users/Groups
-
access user section
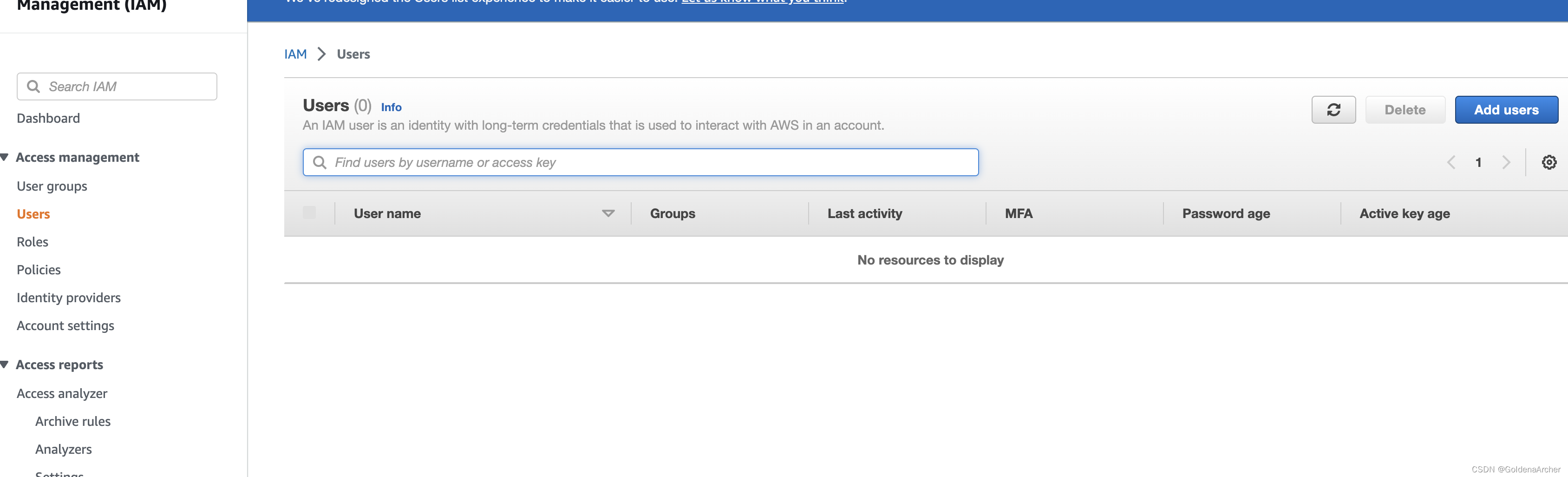
-
create user
-
provide user details
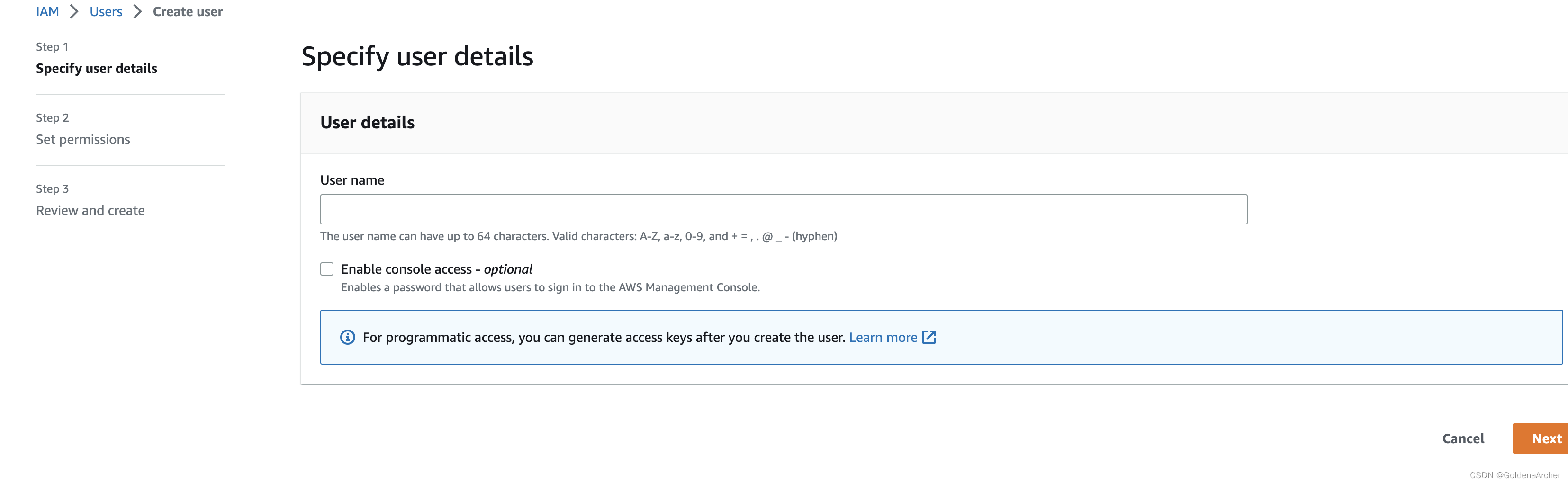
-
grant user permissions
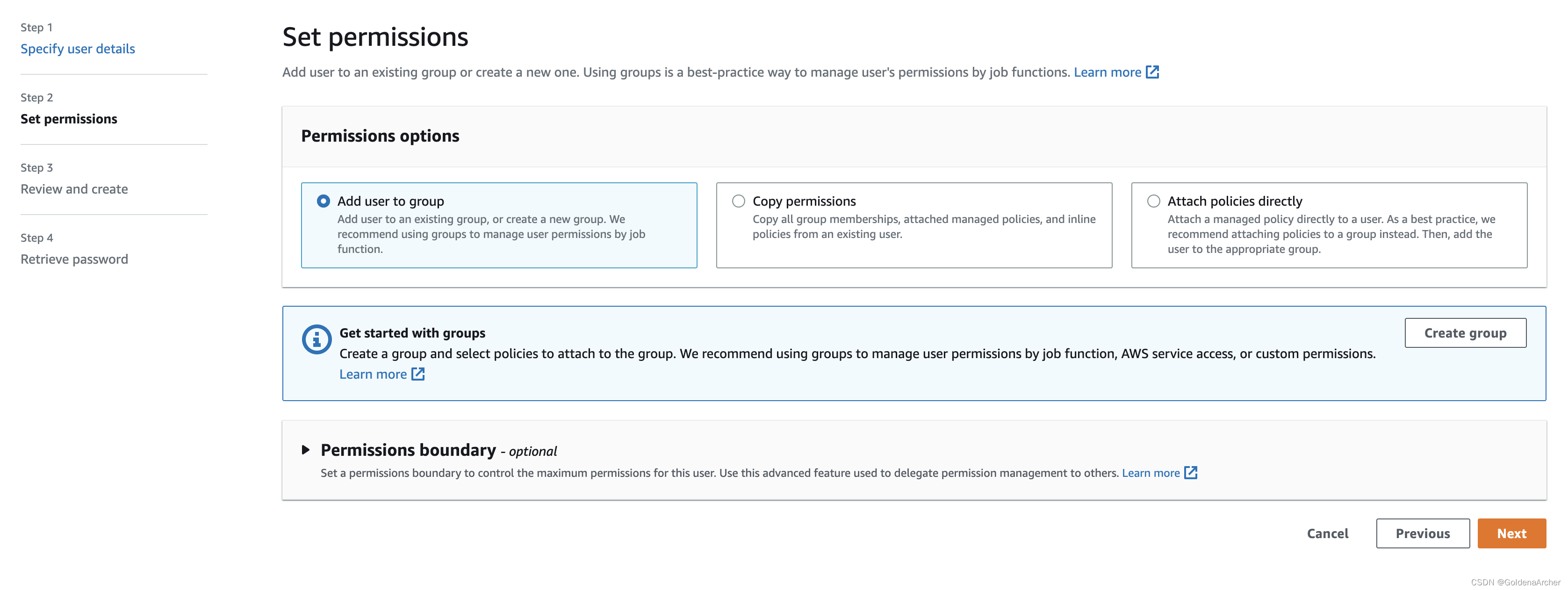
-
review and create
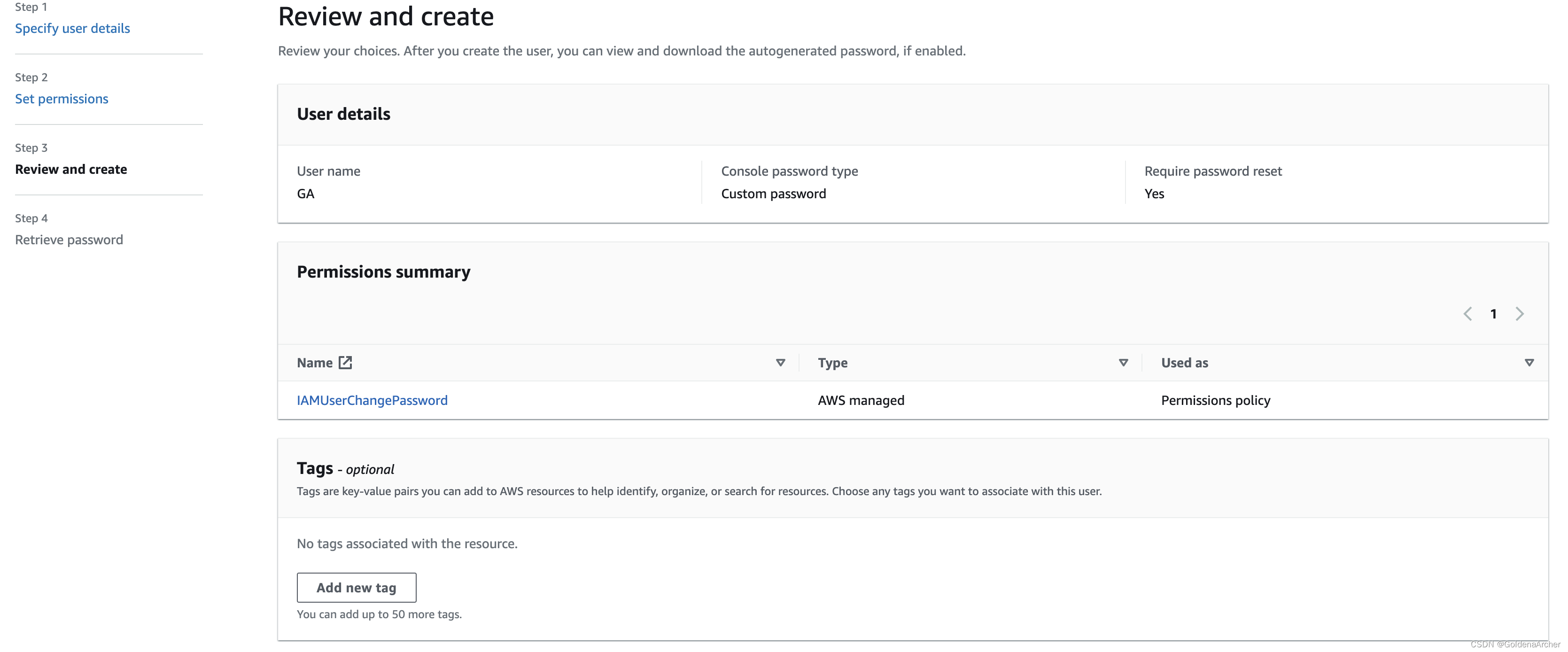

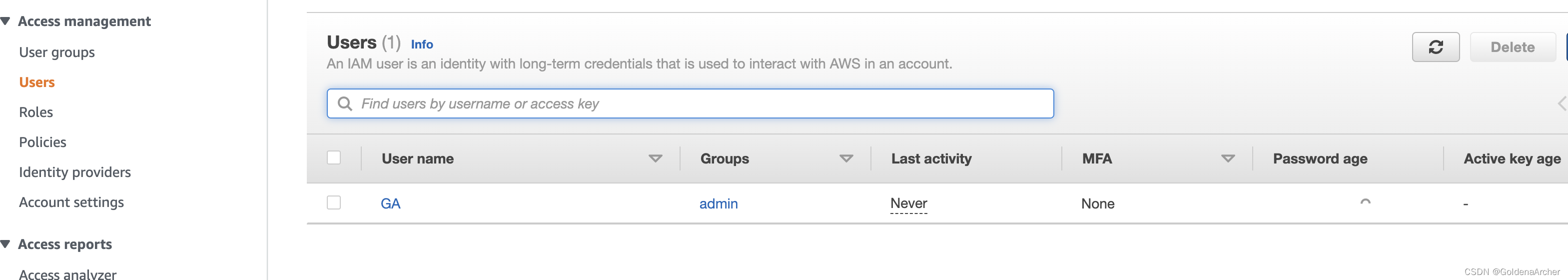
-
-
create user groups
-
select group & click on create group
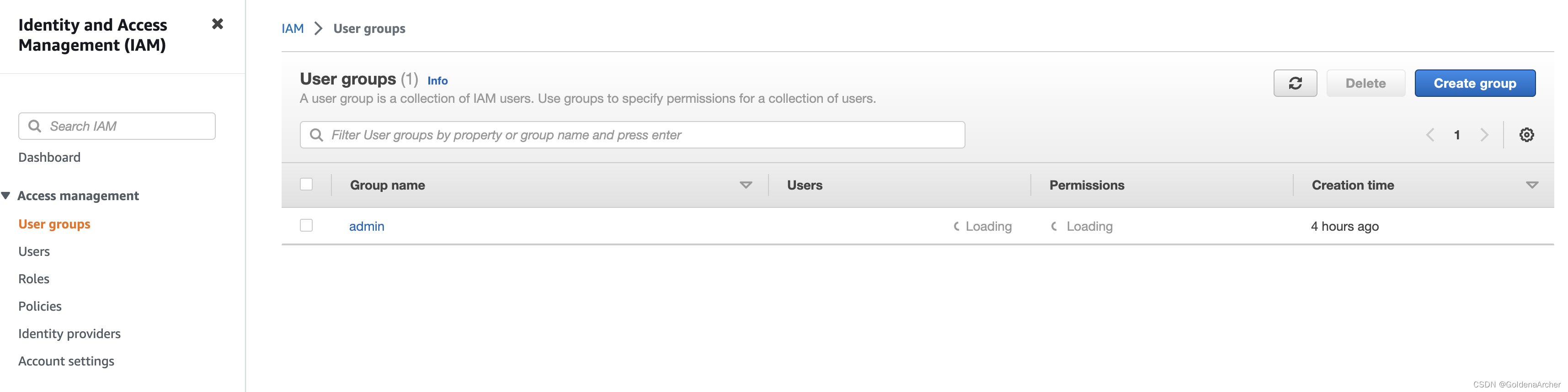
-
Name the group, add useer and attach policy
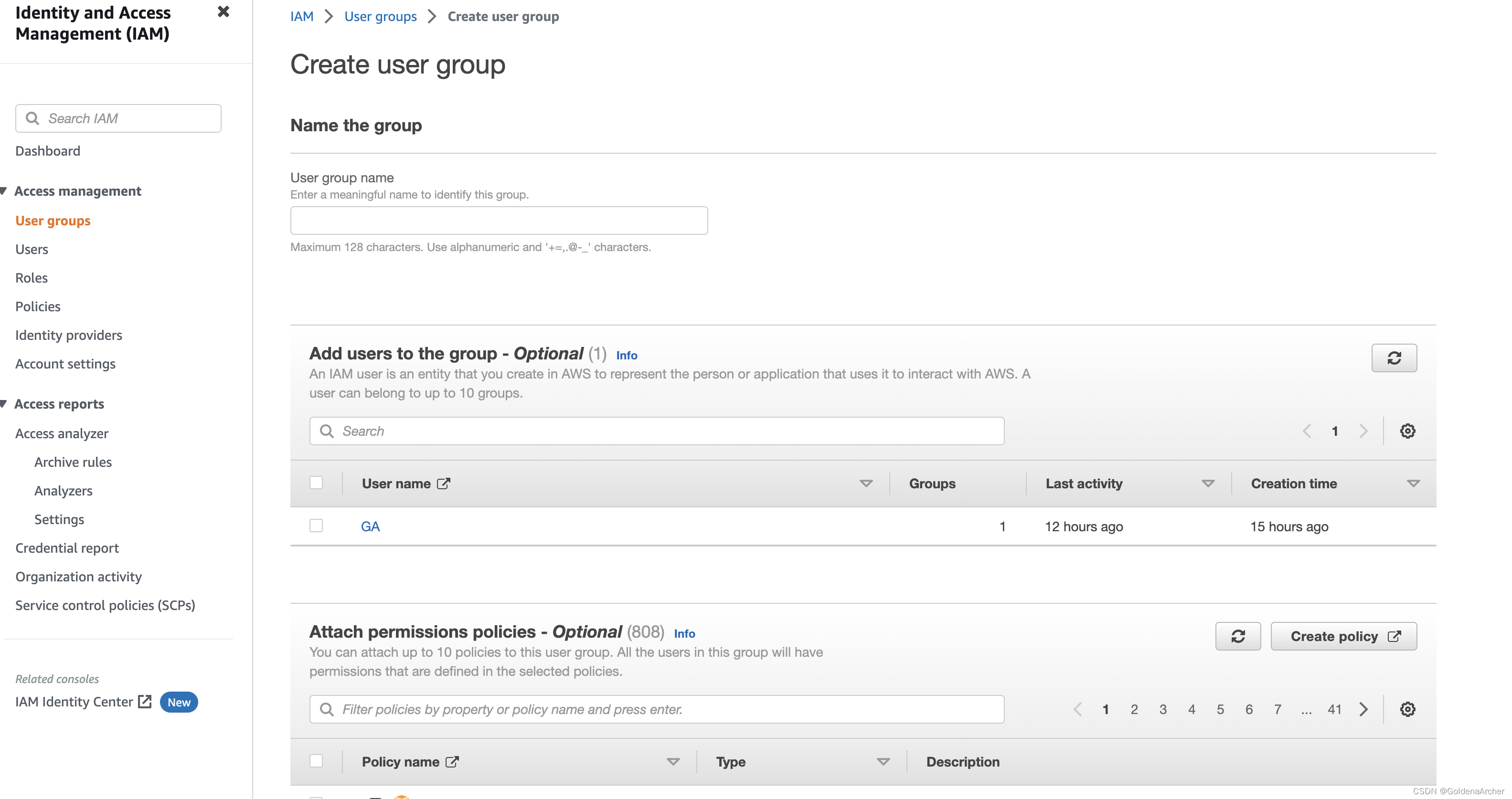
Scroll to the end of page and create group.
-
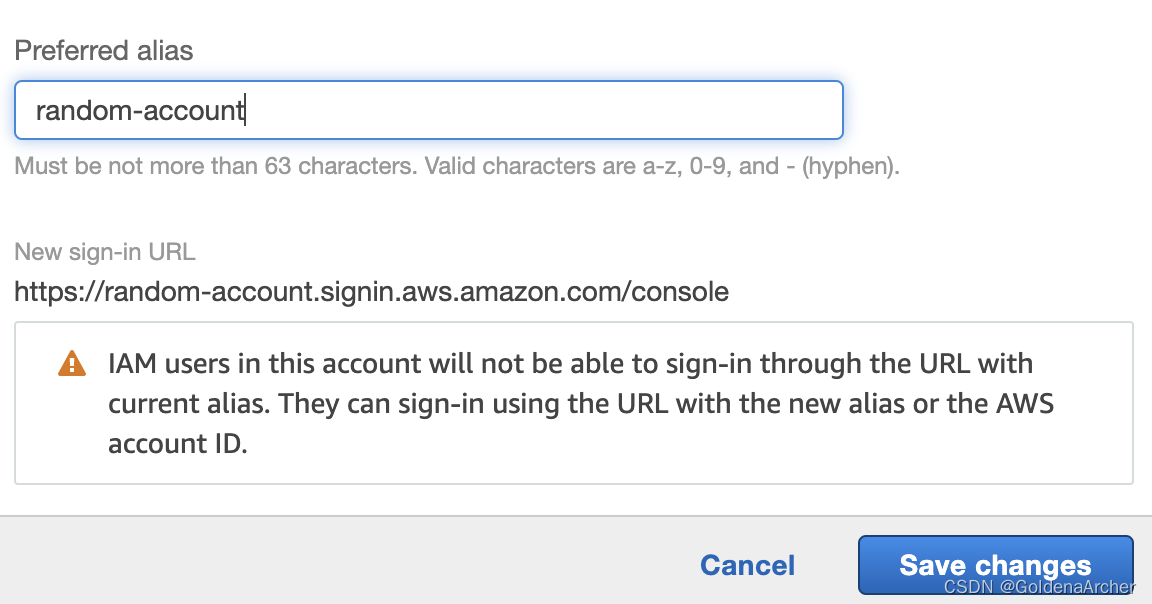
Alias
alias, after setting account with alias, IAM user can sign in using the alias address, can only be set under root account.
It can be viewed and changed on dashboard:

IAM Policy
Policy can be inherited from different group, i.e., if an user is in both group A and group B, then this user will have policy A from group A and policy B from group B attached to this user.
The format of policy looks like:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "service-prefix:action-name",
"Resource": "*",
"Condition": {
"DateGreaterThan": { "aws:CurrentTime": "2020-04-01T00:00:00Z" },
"DateLessThan": { "aws:CurrentTime": "2020-06-30T23:59:59Z" }
}
}
]
}
A policy is consists of:
-
version number - policy language version, always include “2012-10-17” (required)
2008-10-17 exists on older policy, but do not use this value as its outdated
-
id: an identifier for the policy(optional)
-
Statements: one or more individual statements (required)
statements consists of:
-
sid: an identifier for the statement (optional)
-
Effect: whether allow/deny access
-
Principal: account/user/role to which this polic applied to
required in resource-based policies
-
Action: list of actions this policy allows or denies
-
NotAction: all the actions except listed actions this policy allows or denies
A statement must include Action or NoAction
-
Resource: list of resources to which the actions applied to
-
NoResource: similar to NoAction
A statement must include Resource or NoResource
-
Condition: conditions for when this policy is in effect (optional)
IAM Password and MFA
Right now the password has default value, and can be changed under account settings:
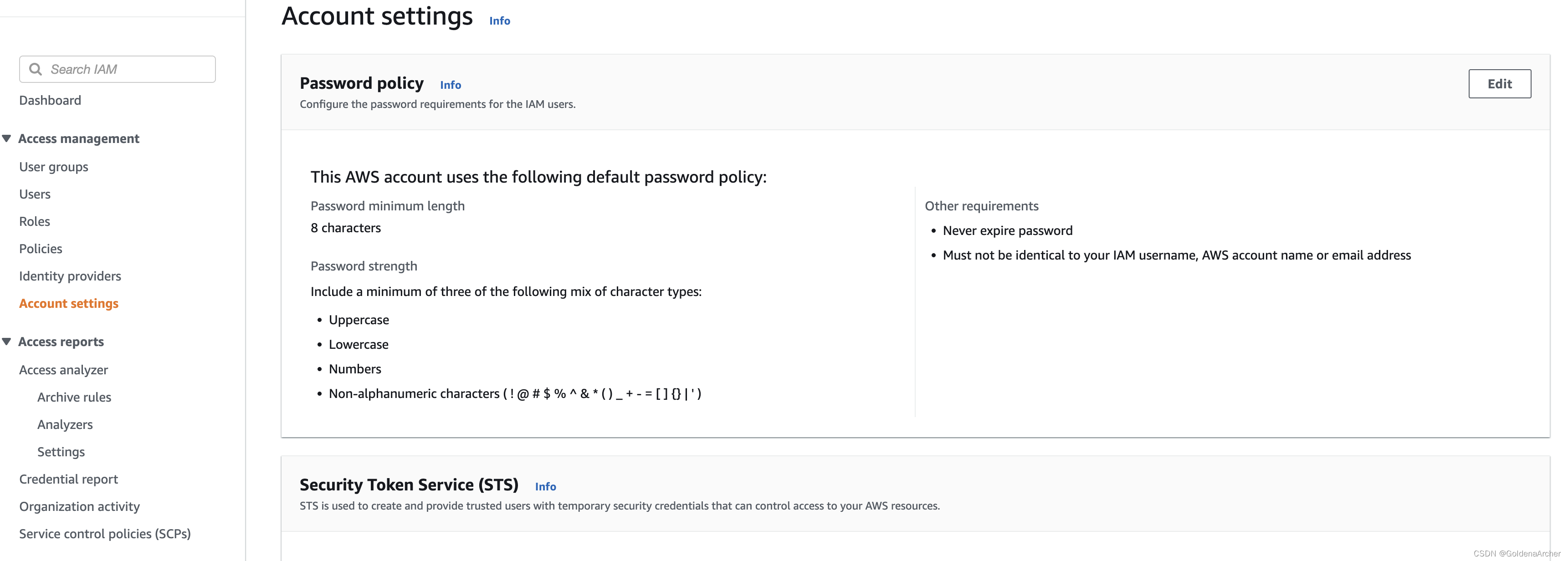
MFA can be generated under users > security credentials:

Access key can be found below MFA.
Access Key
There a 3 way to access AWS:
- AWS Management Console(website), protected by password + MFA
- AWS Command Line Interface(CLI), protected by access keys
- AWS Software Developer Kit(SDK), protected by access keys
Access keys are generated through the AWS console, the secret access key is only shown during the process of creation, if user loses it, the user will need to create it again.
Users manage their own access keys, DO NOT SHARE
Connect process:
-
download and install CLI
Download: https://docs.aws.amazon.com/cli/latest/userguide/getting-started-install.html
on Mac:
$ curl "https://awscli.amazonaws.com/AWSCLIV2.pkg" -o "AWSCLIV2.pkg" $ sudo installer -pkg AWSCLIV2.pkg -target / -
Create access key using IAM User, DO NOT use root account for it.
-
configure aws cli:
➜ ~ aws configure AWS Access Key ID [None]: ...... AWS Secret Access Key [None]: ...... Default region name [None]: us-east-1 Default output format [None]: ➜ ~ aws iam list-users { "Users": [ { "Path": "/", "UserName": "GA", "UserId": "........", "Arn": "arn:aws:iam::.......", "CreateDate": "2023-01-21T08:20:10+00:00", "PasswordLastUsed": "2023-01-21T11:30:22+00:00" } ] }
Alternative: AWS Cloud Shell (not global): https://docs.aws.amazon.com/general/latest/gr/cloudshell.html
IAM Security Tools
- IAM Credentials Report (account-level)
- IAM Access Advisor (user-level)
IAM Guidelines & Best Practices
- Don’t use the root account except for AWS account setup
- One physical user = One AWS user
- Assign users to groups and assign permissions to group
- Create a strong password policy
- Use and enforce the use of Multi Factor Authentication(MFA)
- Create and use Roles for giving permissions to AWS services
- Use Access Keys for Programmatic Access (CLI/SDK)
- Audit permissions of account with the IAM Credentials Report
- Never share IAM users & Access Keys
Questions:
-
In AWS, what is IAM used for (choose 3)
- Assigning permissions, to allow and deny access to AWS resources
- Managing access to AWS Services
- Creating and managing users and groups
-
Which of the following is NOT a feature of IAM
- Allows you to set up biometric authentication, so that no passwords are required
-
Which IAM entity can you use to delegate access to trusted entities such as IAM users, applications, or AWS services such as EC2?
- IAM Role
You can use IAM roles to delegate access to IAM users managed within your account, to IAM users under a different AWS account, to a web service offered by AWS such as Amazon Elastic Compute Cloud (Amazon EC2), or to an external user authenticated by an external identity provider (IdP) service that is compatible with SAML 2.0 or OpenID Connect, or a custom-built identity broker. IAM Roles.
-
True or False? AWS recommends that EC2 instances have credentials stored on them so that the instances can access other resources (such as S3 buckets).
- False
-
Which is the best way to enable S3 read-access for an EC2 instance?
- Create an IAM role with read-access to S3 and assign the role to the EC2 instance
-
Which of the following can you use to test that an IAM policy attached to a user, group or role works as expected?
- IAM Policy Simulator
-
What is an IAM Policy?
- A JSON document which defines one or more permissions
-
What is a proper definition of an IAM Role?
- An IAM entity that defines a set of permissions for making requests to AWS services, and will be used by an AWS service
-
Which of the following is an IAM Security Tool?
- IAM Credentials Report
-
Which answer is INCORRECT regarding IAM Users?
- IAM Users access AWS services using root account credentials
-
Which of the following is an IAM best practice?
- Don’t use the root user account
-
What are IAM Policies?
- JSON documents that define a set of permissions for making requests to AWS services, and can be used by IAM Users, User Groups, and IAM Roles
-
Which principle should you apply regarding IAM Permissions?
- Grant least privilege
-
What should you do to increase your root account security?
- Enable Multi-Factor Authentication (MFA)
-
IAM User Groups can contain IAM Users and other User Groups.
- False
IAM User Groups can not be part of other User Groups.
-
An IAM policy consists of one or more statements. A statement in an IAM Policy consists of the following, EXCEPT:
- Version
Version is part of the IAM Policy itself, not the statement.
-
According to the AWS Shared Responsibility Model, which of the following is AWS responsibility?
- AWS Infrastructure

![UE INI文件操作 INI File Operation [ Read / Write ] 插件说明](https://img-blog.csdnimg.cn/e665ccfb8b9f4d34bac062ec534502c1.png)