文章目录
- 树莓派4b部署Harbor-arm64版本
- docker-compose维护命令
- 访问harbor 192.168.1.111认用户名密码admin/Harbor12345
树莓派4b部署Harbor-arm64版本
harbor-arm版本
部署:参考
wget https://github.com/hzliangbin/harbor-arm64/releases/download/v1.9.3/harbor-offline-installer-v1.9.3.tgz
tar -xf harbor-offline-installer-v1.9.3.tgz -C /opt/
cp /opt/harbor/harbor.yml.tmpl /opt/harbor/harbor.yml
修改/opt/harbor/harbor.yml中的hostname字段为实际ip地址或者域名
注释掉https related config模块(本地环境可以直接使用http)
docker load -i /opt/harbor/harbor.v1.9.3.tar.gz
bash /opt/harbor/prepare
bash /opt/harbor/install.sh
docker-compose维护命令
cd /opt/harbor/
启动harbor: docker-compose up -d
停止harbor: docker-compose stop
重启harbor: docker-compose restart
查看harbor状态: docker-compose ps
异常:
docker-compose harbor harbor-log 报错:Authentication token manipulation error启动报错现象
docker-copmose up -d 后 harbor-log 无限重启
查看 harbor-log日志
docker logs -f harbor-log
sudo: unable to change expired password: Authentication token manipulation error
sudo: Account or password is expired, reset your password and try again
sudo: a terminal is required to read the password; either use the -S option to read from standard input or configure an askpass helper
Changing password for root.
解决方法:
1.以tar形式导出容器
mkdir -p /tmp/harbor-log
cd /tmp/harbor-log
docker export harbor-log -o harbor-log.tar
2.解压tar包,修改shadow中的权限(有想深入了解的可以百度“关于/etc/shadow 文件”)
# 解压tar包
tar xvfp harbor-log.tar
# 修改shadow文件的值
sed -i 's/:90:/:99999:/g' /tmp/harbor-log/etc/shadow
3.将修改后的shadow文件挂载到harbor-log容器内
mkdir /root/data/harbor/harbor-log-etc
cp /tmp/harbor-log/etc/shadow /root/data/harbor/harbor-log-etc/shadow
4.修改docker-compose.yml中harbor-log容器volumes配置,增加如下内容
- type: bind
source: ./harbor-log-etc/shadow
target: /etc/shadow
5.重新启动harbor
docker-compose down
docker-compose up -d
#1 外置数据库部署访问(本次部署仅测试使用,生产环境建议高可用方式部署)
192.168.1.111: redis、postgresql
#redis
mkdir -p /opt/redis/conf/
cat << EOF > /opt/redis/conf/redis.conf
#bind 127.0.0.1
protected-mode no appendonly yes
requirepass duan@1994
EOF
docker run -itd --restart=always -p 6379:6379 --name redis-server -v /opt/redis/conf:/usr/local/etc/redis -v /data/redis/data:/data -d redis:6.0.10 redis-server /usr/local/etc/redis/redis.conf
#postgresql
docker run -itd --restart=always -p 5432:5432 --name postgresql -v /data/postgresql/data:/var/lib/postgresql/data -e POSTGRES_PASSWORD=duan@1994 postgres:13.1
登录pgsql创建用户和数据库
docker exec -it postgresql bash
create user harbor with password 'harborDB';
create database harbor;
create database harbor_clair;
create database harbor_notary_server;
create database harbor_notary_signer;
GRANT ALL PRIVILEGES ON DATABASE harbor to harbor;
GRANT ALL PRIVILEGES ON DATABASE harbor_clair to harbor;
GRANT ALL PRIVILEGES ON DATABASE harbor_notary_server to harbor;
GRANT ALL PRIVILEGES ON DATABASE harbor_notary_signer to harbor;
#2 部署minio(本次部署仅测试使用,生产环境建议高可用方式部署)
sudo docker run -d -p 11000:9000 -p 11001:9090 --net=host --name minio -e "MINIO_ACCESS_KEY=minioadmin" -e "MINIO_SECRET_KEY=minioadmin@131008" -v /media/pi/Elements/minio/data:/data -v /media/pi/Elements/minio/config:/root/.minio minio/minio server /data --console-address ":11001" -address ":11000"
#3 配置harbor.yaml
# Configuration file of Harbor
# The IP address or hostname to access admin UI and registry service.
# DO NOT use localhost or 127.0.0.1, because Harbor needs to be accessed by external clients.
hostname: 192.168.86.5
# http related config
http:
# port for http, default is 80. If https enabled, this port will redirect to https port
port: 80
# https related config
#https:
# # https port for harbor, default is 443
# port: 443
# # The path of cert and key files for nginx
# certificate: /your/certificate/path
# private_key: /your/private/key/path
# # Uncomment following will enable tls communication between all harbor components
# internal_tls:
# # set enabled to true means internal tls is enabled
# enabled: true
# # put your cert and key files on dir
# dir: /etc/harbor/tls/internal
# Uncomment external_url if you want to enable external proxy
# And when it enabled the hostname will no longer used
# external_url: https://reg.mydomain.com:8433
# The initial password of Harbor admin
# It only works in first time to install harbor
# Remember Change the admin password from UI after launching Harbor.
harbor_admin_password: Harbor12345
# Harbor DB configuration
database:
# The password for the root user of Harbor DB. Change this before any production use.
password: root123
# The maximum number of connections in the idle connection pool. If it <=0, no idle connections are retained.
max_idle_conns: 50
# The maximum number of open connections to the database. If it <= 0, then there is no limit on the number of open connections.
# Note: the default number of connections is 1024 for postgres of harbor.
max_open_conns: 1000
# The default data volume
data_volume: /data
# Harbor Storage settings by default is using /data dir on local filesystem
# Uncomment storage_service setting If you want to using external storage
# storage_service:
# # ca_bundle is the path to the custom root ca certificate, which will be injected into the truststore
# # of registry's and chart repository's containers. This is usually needed when the user hosts a internal storage with self signed certificate.
# ca_bundle:
# # storage backend, default is filesystem, options include filesystem, azure, gcs, s3, swift and oss
# # for more info about this configuration please refer https://docs.docker.com/registry/configuration/
# filesystem:
# maxthreads: 100
# # set disable to true when you want to disable registry redirect
# redirect:
# disabled: false
storage_service:
s3:
accesskey: admin
secretkey: admin123456
region: us-east-1
regionendpoint: http://192.168.86.6:9000(新版本用9001)
bucket: harbor-registry
encrypt: false
secure: false
v4auth: true
chunksize: 5242880
rootdirectory: /
# Clair configuration
clair:
# The interval of clair updaters, the unit is hour, set to 0 to disable the updaters.
updaters_interval: 12
# Trivy configuration
#
# Trivy DB contains vulnerability information from NVD, Red Hat, and many other upstream vulnerability databases.
# It is downloaded by Trivy from the GitHub release page https://github.com/aquasecurity/trivy-db/releases and cached
# in the local file system. In addition, the database contains the update timestamp so Trivy can detect whether it
# should download a newer version from the Internet or use the cached one. Currently, the database is updated every
# 12 hours and published as a new release to GitHub.
trivy:
# ignoreUnfixed The flag to display only fixed vulnerabilities
ignore_unfixed: false
# skipUpdate The flag to enable or disable Trivy DB downloads from GitHub
#
# You might want to enable this flag in test or CI/CD environments to avoid GitHub rate limiting issues.
# If the flag is enabled you have to download the `trivy-offline.tar.gz` archive manually, extract `trivy.db` and
# `metadata.json` files and mount them in the `/home/scanner/.cache/trivy/db` path.
skip_update: false
#
# insecure The flag to skip verifying registry certificate
insecure: false
# github_token The GitHub access token to download Trivy DB
#
# Anonymous downloads from GitHub are subject to the limit of 60 requests per hour. Normally such rate limit is enough
# for production operations. If, for any reason, it's not enough, you could increase the rate limit to 5000
# requests per hour by specifying the GitHub access token. For more details on GitHub rate limiting please consult
# https://developer.github.com/v3/#rate-limiting
#
# You can create a GitHub token by following the instructions in
# https://help.github.com/en/github/authenticating-to-github/creating-a-personal-access-token-for-the-command-line
#
# github_token: xxx
jobservice:
# Maximum number of job workers in job service
max_job_workers: 10
notification:
# Maximum retry count for webhook job
webhook_job_max_retry: 10
chart:
# Change the value of absolute_url to enabled can enable absolute url in chart
absolute_url: disabled
# Log configurations
log:
# options are debug, info, warning, error, fatal
level: info
# configs for logs in local storage
local:
# Log files are rotated log_rotate_count times before being removed. If count is 0, old versions are removed rather than rotated.
rotate_count: 50
# Log files are rotated only if they grow bigger than log_rotate_size bytes. If size is followed by k, the size is assumed to be in kilobytes.
# If the M is used, the size is in megabytes, and if G is used, the size is in gigabytes. So size 100, size 100k, size 100M and size 100G
# are all valid.
rotate_size: 200M
# The directory on your host that store log
location: /var/log/harbor
# Uncomment following lines to enable external syslog endpoint.
# external_endpoint:
# # protocol used to transmit log to external endpoint, options is tcp or udp
# protocol: tcp
# # The host of external endpoint
# host: localhost
# # Port of external endpoint
# port: 5140
#This attribute is for migrator to detect the version of the .cfg file, DO NOT MODIFY!
_version: 2.0.0
# Uncomment external_database if using external database.
external_database:
harbor:
host: 192.168.1.111
port: 5432
db_name: harbor
username: harbor
password: harborDB
ssl_mode: disable
max_idle_conns: 2
max_open_conns: 0
clair:
host: 192.168.1.111
port: 5432
db_name: clair
username: harbor
password: harborDB
ssl_mode: disable
notary_signer:
host: 192.168.1.111
port: 5432
db_name: notary_signer
username: harbor
password: harborDB
ssl_mode: disable
notary_server:
host: 192.168.1.111
port: 5432
db_name: notary_server
username: harbor
password: harborDB
ssl_mode: disable
# Uncomment external_redis if using external Redis server
external_redis:
# support redis, redis+sentinel
# host for redis: <host_redis>:<port_redis>
# host for redis+sentinel:
# <host_sentinel1>:<port_sentinel1>,<host_sentinel2>:<port_sentinel2>,<host_sentinel3>:<port_sentinel3>
host: 192.168.1.111:6379
password: duan@1994
# sentinel_master_set must be set to support redis+sentinel
#sentinel_master_set:
# db_index 0 is for core, it's unchangeable
registry_db_index: 1
jobservice_db_index: 2
chartmuseum_db_index: 3
clair_db_index: 4
trivy_db_index: 5
idle_timeout_seconds: 30
# Uncomment uaa for trusting the certificate of uaa instance that is hosted via self-signed cert.
# uaa:
# ca_file: /path/to/ca
# Global proxy
# Config http proxy for components, e.g. http://my.proxy.com:3128
# Components doesn't need to connect to each others via http proxy.
# Remove component from `components` array if want disable proxy
# for it. If you want use proxy for replication, MUST enable proxy
# for core and jobservice, and set `http_proxy` and `https_proxy`.
# Add domain to the `no_proxy` field, when you want disable proxy
# for some special registry.
proxy:
http_proxy:
https_proxy:
no_proxy:
components:
- core
- jobservice
- clair
- trivy
访问harbor 192.168.1.111认用户名密码admin/Harbor12345
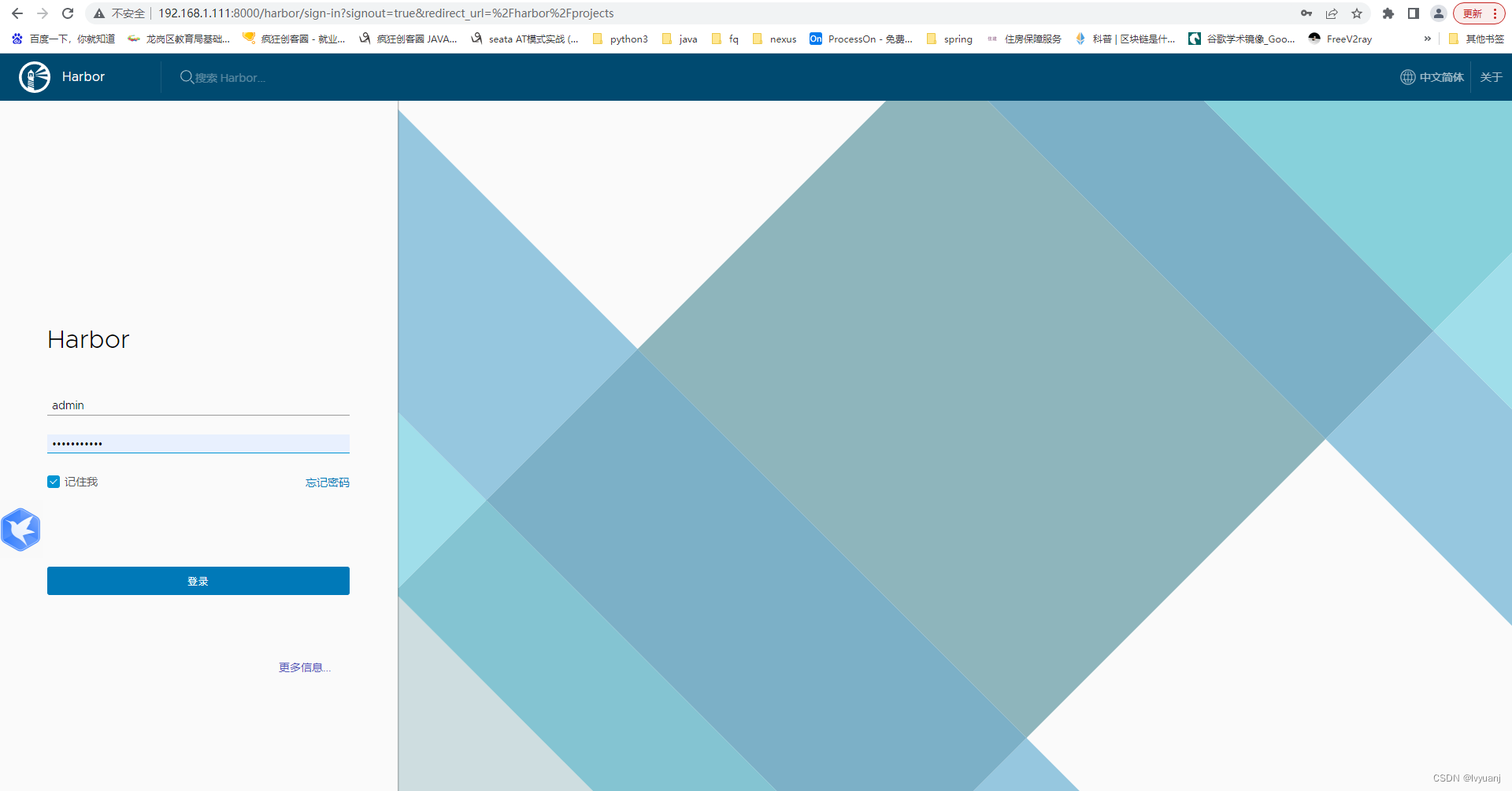
docker push 异常:
docker 在push镜像到本地registry出现的500 Internal Server Error
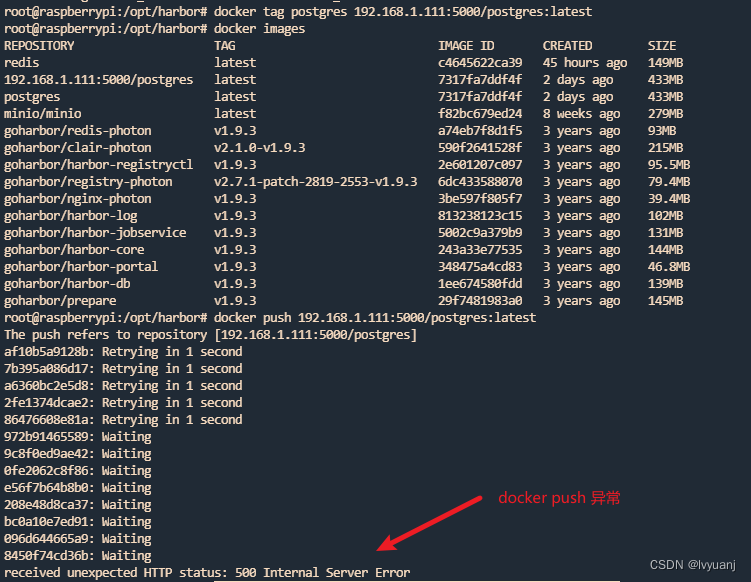
原因一:
镜像目录不符合要求:应该是两级目录以上才可以的, 如:
192.168.1.111:5000/postgres:latest 不符合要求
192.168.1.111:5000/lvyuanj/postgres:latest 符合要求
Docker push时报错:Docker denied: requested access to the resource is denied的解决办法
请遵循这两种解决方法
(1)解决方案 1:
首先,检查您的 docker hub 凭据是否输入了正确的凭据。
如果您输入的密码正确,则此错误仍然存在,请尝试注销并使用您的凭据重新登录。
对于注销使用,
docker logout
再次登录使用,
docker login
在某些情况下,此解决方案可能有效。
解决方案 2:
如果仍然如此,您在尝试解决方案 1 后仍收到此错误,您必须按照此解决方案来清除错误。
YOUR_DOCKERHUB_NAME 必须是自己harbor域名或者ip:port 例:自己私有harbor 192.168.1.111:5000
首先,登录后你必须在推送之前标记你的图像:
docker tag image_name YOUR_DOCKERHUB_NAME/image_name
然后,你必须推动它。
docker push YOUR_DOCKERHUB_NAME/image_name
完成此操作后,您将能够将 docker 镜像推送到您的存储库中,错误将消失。
再次登录使用,
docker login
在某些情况下,此解决方案可能有效。
解决方案 2:
如果仍然如此,您在尝试解决方案 1 后仍收到此错误,您必须按照此解决方案来清除错误。
YOUR_DOCKERHUB_NAME 必须是自己harbor域名或者ip:port 例:自己私有harbor 192.168.1.111:5000
首先,登录后你必须在推送之前标记你的图像:
docker tag image_name YOUR_DOCKERHUB_NAME/image_name
然后,你必须推动它。
docker push YOUR_DOCKERHUB_NAME/image_name
完成此操作后,您将能够将 docker 镜像推送到您的存储库中,错误将消失。





![[自动驾驶技术]-5 Tesla自动驾驶方案之算法(AI Day 2021)](https://img-blog.csdnimg.cn/direct/bb38da21cd6a4897a88283f993929ee3.png)