Spool Print Fool(CVE-2022-21999 )提权漏洞
文章目录
- 一、Print Spooler 简介
- 二、漏洞简介
- 三、影响版本
- 四、本地复现
- 五、漏洞修复
一、Print Spooler 简介
Print Spooler是打印后台处理服务,即管理所有本地和⽹络打印队列及控制所有打印⼯作。如果此服务被停⽤,本地计算机上的打印将不可⽤。如果此服务被禁⽤,任何依赖于它的服务将⽆法启⽤,被⼴泛应⽤于本地和内⽹中!
二、漏洞简介
2021年6⽉29⽇,安全研究⼈员在GitHub上公开了CVE-2021-1675 Windows Print Spooler远程代码执⾏漏洞的PoC。该漏洞是Microsoft 6⽉星期⼆补丁⽇中公开的⼀个RCE漏洞,其存在于管理打印过程的Print Spooler (spoolsv.exe) 服务中,会影响所有 Windows系统版本。
2022年2⽉8⽇,Windows Print Spooler(CVE-2022-2199)提权漏洞再次爆出,该漏洞是 PrintNightmare 的续集!Windows系统默认开启 Print Spooler 服务,普通⽤户可以利⽤此漏洞提升⾄管理员权限。
三、影响版本
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 (Server Core installation)
Windows Server 2012
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core
installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core
installation)
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core
installation)
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows RT 8.1
Windows 8.1 for x64-based systems
Windows 8.1 for 32-bit systems
Windows 7 for x64-based Systems Service Pack 1
Windows 7 for 32-bit Systems Service Pack 1
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows 10 Version 1607 for x64-based Systems
Windows 10 Version 1607 for 32-bit Systems
Windows 10 for x64-based Systems
Windows 10 for 32-bit Systems
Windows 10 Version 21H2 for x64-based Systems
Windows 10 Version 21H2 for ARM64-based Systems
Windows 10 Version 21H2 for 32-bit Systems
Windows 11 for ARM64-based Systems
Windows 11 for x64-based Systems
Windows Server, version 20H2 (Server Core Installation)
Windows 10 Version 20H2 for ARM64-based Systems
Windows 10 Version 20H2 for 32-bit Systems
Windows 10 Version 20H2 for x64-based Systems
Windows Server 2022 Azure Edition Core Hotpatch
Windows Server 2022 (Server Core installation)
Windows Server 2022
Windows 10 Version 21H1 for 32-bit Systems
Windows 10 Version 21H1 for ARM64-based Systems
Windows 10 Version 21H1 for x64-based Systems
Windows 10 Version 1909 for ARM64-based Systems
Windows 10 Version 1909 for x64-based Systems
Windows 10 Version 1909 for 32-bit Systems
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
四、本地复现
测试环境
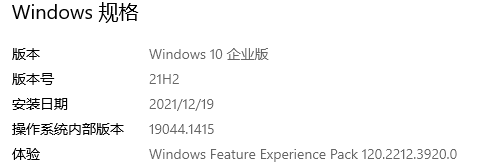
该版本在漏洞影响范围内,下面开始提权
脚本下载地址:
https://github.com/ly4k/SpoolFool
SpoolFool.exe -dll AddUser.dll
#Win10 成功执行DLL,添加本地管理员admin的用户
#admin / Passw0rd!
net user admin
使用该脚本进⾏提权时,会默认添加 admin ⽤户、密码:Passw0rd!
出现 DLL should be loaded 则表示成功!

查看是否添加成功获得 administrator权限

提权成功!此时用户admin以是管理员权限。
执⾏漏洞利⽤后,将留下以下内容以供以后清理

五、漏洞修复
临时修复方法 (针对某些业务无法及时更新补丁的情况可采取如下方法)
(1)禁⽤后台打印处理服务
win+r 输⼊:services.msc 打开服务界⾯
找到Print Splooler服务,双击该服务,将其服务停⽌,服务启动类型选择为禁⽤即可

(2)微软官⽅已针对⽀持的系统版本发布了修复该漏洞的安全补丁,建议受影响⽤户尽快安装补丁
进⾏防护。
点击此处 ->前往下载