UFS 1-UFS RPMB
- 1 RPMB介绍
- 2 RPMB Well Known Logical Unit Description
- 3 Requirements
- 3.1 RPMB Resources
- 3.2 Algorithm and Key for MAC Calculation
- 3.3 RPMB Message Components
- 3.4 Request Message Types
- 3.5 Response Message Types
- 3.6 RPMB Operation Result
- 4 Implementation
- 4.1 RPMB Message
- 4.2 MAC Calculation
- 4.3 RPMB Message Data Frame Delivery
- 5 SECURITY PROTOCOL IN/OUT Commands
- 5.1 CDB format of SECURITY PROTOCOL IN/OUT commands
- 5.2 Supported security protocols list description
- 5.3 Certificate data description
- 6 RPMB Operations
- 6.1 Request Type Message Delivery
- 6.2 Response Type Message Delivery
- 6.3 Authentication Key Programming
- 6.4 Read Counter Value
基于UFS 3.1
1 RPMB介绍
A signed access to a Replay Protected Memory Block is provided. This function provides means for the system to store data to the specific memory area in an authenticated and replay protected manner. This is provided by first programming authentication key information to the UFS device memory (shared secret).
提供对重放保护内存块的签名访问。此功能为系统提供了以经过身份验证和重放保护的方式将数据存储到特定内存区域的方法。这是通过首先将身份验证密钥信息编程到 UFS 设备内存(共享机密)来提供的。
As the system cannot be authenticated yet in this phase the authentication key programming have to take in a secure environment like in an OEM production. Further on the authentication key is utilized to sign the read and write accesses made to the replay protected memory area with a Message Authentication Code (MAC).
由于系统在此阶段还无法通过身份验证,因此身份验证密钥编程必须采用安全环境,如 OEM 生产。此外,身份验证密钥还用于使用消息身份验证代码 (MAC) 对对重放保护内存区域进行的读写访问进行签名。
Usage of random number generation and count register are providing additional protection against replay of messages where messages could be recorded and played back later by an attacker.
随机数生成和计数寄存器的使用提供了额外的保护,防止消息重放,攻击者可以在以后记录和重放消息。
2 RPMB Well Known Logical Unit Description
The RPMB is contained in a unique well known logical unit whose size is defined in the RPMB Unit Descriptor. RPMB well known logical unit size shall be a multiple of 128 Kbytes, therefore its minimum size is 128 Kbytes. The contents of the RPMB well known logical unit can only be read or written via successfully authenticated read and write accesses. The data may be overwritten by the host but can never be erased.
RPMB 包含在一个独特的众所周知的逻辑单元中,其大小在 RPMB 单元描述符中定义。 RPMB 众所周知的逻辑单元大小应为 128 KB 的倍数,因此其最小大小为 128 KB。 RPMB 众所周知的逻辑单元的内容只能通过成功验证的读写访问来读取或写入。数据可能会被主机覆盖,但永远不会被擦除。
All accesses to the RPMB will reference the specific RPMB well known logical unit number (W-LUN).
所有对 RPMB 的访问都将引用特定的 RPMB 众所周知的逻辑单元号 (W-LUN)。
RPMB well known logical unit may be configured into multiple RPMB regions where each RPMB region has its own dedicated authentication key, write counter, result register, and logical address which starts from zero. Refer to 13.2.3 to see how to configure RPMB well known logical unit into multiple RPMB regions.
RPMB众所周知的逻辑单元可以配置成多个RPMB区域,其中每个RPMB区域都有自己专用的认证密钥、写计数器、结果寄存器和从零开始的逻辑地址。参考 13.2.3 了解如何将 RPMB 众所周知的逻辑单元配置为多个 RPMB 区域。
Each RPMB region can process a single RPMB authenticated operation at any given point in time where a single authenticated RPMB operation corresponds to whole Figure 12.2 Authentication Key Programing Flow, Figure 12.3 Read Counter Value Flow, or Figure 12.6 Authenticated Secure Write Protect Configuration Block Read Flow, and so on as listed in Table 12.5 Request Messge Types. For example, the Initiator 3 may start an authenticated operation in RPMB Region 0 and Initiator 4 in RPMB Region 1. The RPMB Region 0 should be accessed by a new authenticated operation request after completing the authenticated operation started by Initiator 3; and RPMB Region 1 after completing the request from the Initiator 4.
每个 RPMB 区域可以在任何给定时间点处理单个 RPMB 身份验证操作,其中单个身份验证 RPMB 操作对应于整个图 12.2 身份验证密钥编程流程、图 12.3 读取计数器值流程或图 12.6 身份验证安全写保护配置块读取流程,等等,如表 12.5 请求消息类型中所列。例如,Initiator 3可能在RPMB Region 0启动鉴权操作,Initiator 4在RPMB Region 1启动鉴权操作。在完成Initiator 3启动的鉴权操作后,RPMB Region 0应该被新的鉴权操作请求访问;和 RPMB Region 1 在完成 Initiator 4 的请求后。
3 Requirements
3.1 RPMB Resources
- Authentication Key
- Type: Write once, not erasable or readable
- Size: 32 bytes
- Description: Authentication key register which is used to authenticate accesses when MAC is calculated. Each RPMB region has a dedicated authentication key. 说明:认证密钥寄存器,用于计算MAC时对访问进行认证。每个 RPMB 区域都有一个专用的身份验证密钥。
- Write Counter
- Type: Read only
- Size: 4 bytes
- Description: Counter value for the total amount of successful authenticated data write requests made by the host. The initial value of this register after production is 0000 0000h. The value will be incremented by one automatically by the UFS device along with each successful programming access. The value cannot be reset. After the counter has reached the maximum value of FFFF FFFFh, it will not be incremented anymore (overflow prevention). Each RPMB region has dedicated write counter.
- 说明:主机发出的成功验证数据写入请求总数的计数器值。该寄存器生产后的初始值为0000 0000h。随着每次成功的编程访问,该值将由 UFS 设备自动递增 1。该值无法重置。计数器达到最大值 FFFF FFFFh 后,将不再递增(防止溢出)。每个 RPMB 区域都有专用的写计数器。
- Result Register
- Type: Read only
- Size: 2 bytes
- Description: This register provides the result of an authenticated operation. Each RPMB region has dedicated result register.
- 说明: 该寄存器提供经过身份验证的操作的结果。每个 RPMB 区域都有专用的结果寄存器。
- RPMB Data Area
- Type: Readable and writable
- Size: Multiples of 128 Kbytes defined in RPMB Unit Descriptor
- 128 Kbytes minimum, 16 Mbytes maximum.
- Each RPMB region size is defined as bRPMBRegion0Size – bRPMBRegion3Size in the RPMB Unit Descriptor.
- 每个 RPMB 区域大小在 RPMB 单元描述符中定义为 bRPMBRegion0Size – bRPMBRegion3Size。
- Description: Data which can only be read and written via successfully authenticated read/write access. This data may be overwritten by the host but can never be erased.
- 描述:只能通过成功验证的读/写访问来读取和写入的数据。此数据可能会被主机覆盖,但永远不会被擦除。
- Secure Write Protect Configuration Block
-
Type: Readable and writable
-
Size : 256 Bytes
-
Description: Secure Write Protect Configuration Block is supported by RPMB region 0 only. This block is used for configuring secure write protect areas in logical units. There is one Secure Write Protect Configuration Block for each logical unit. Each Secure Write Protect Configuration Block has up to four Secure Write Protect Entries. Each entry represents one secure write protect area. If an entry is not used, then the related fields shall contain a value of zero. The Secure Write Protect Configuration Block is structured as shown in Table 12.1.
-
说明:安全写保护配置块仅受 RPMB 区域 0 支持。该块用于配置逻辑单元中的安全写保护区。每个逻辑单元都有一个安全写保护配置块。每个安全写保护配置块最多有四个安全写保护条目。每个条目代表一个安全写保护区。如果不使用entry,则相关字段应包含零值。安全写保护配置块的结构如表 12.1 所示。
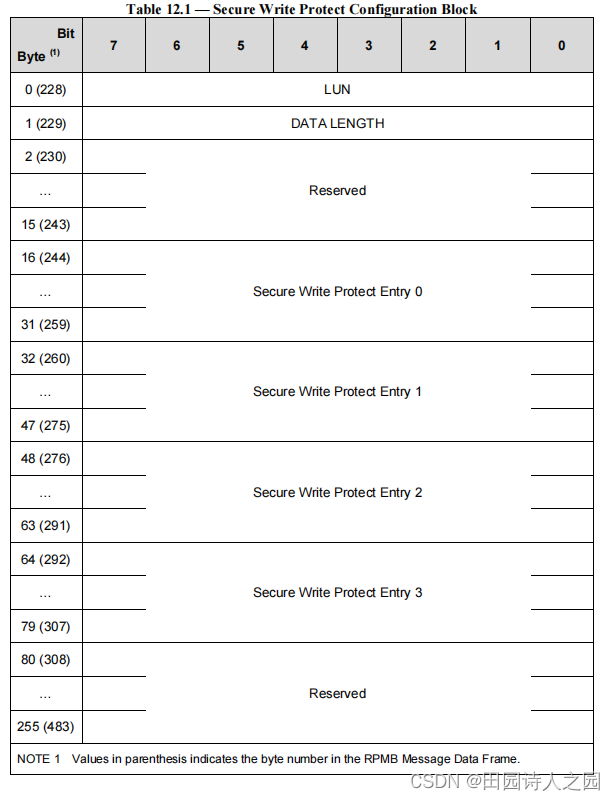
NOTE 1 Values in parenthesis indicates the byte number in the RPMB Message Data Frame.
注 1 括号中的值表示 RPMB 消息数据帧中的字节数。- a) LUN : The LUN field indicates the logical unit to which secure write protection shall apply. Valid values are from 0 to the number of LU specified by bMaxNumberLU.
- LUN :LUN 字段指示应用安全写保护的逻辑单元。有效值从 0 到 bMaxNumberLU 指定的 LU 数。
- DATA LENGTH : The DATA LENGTH field specifies the length in bytes of the Secure Write Protect Entries (0 for no entry, 16 for one entry, 32 for two entries, 48 for three entries and 64 for four entries). In a write request, the device shall ignore the bytes from DATA LENGTH + 16 to 255 and set these bytes of the Secure Write Protect Configuration Block to zero.
- DATA LENGTH:DATA LENGTH 字段指定安全写保护条目的字节长度(0 表示无条目,16 表示一个条目,32 表示两个条目,48 表示三个条目,64 表示四个条目)。在写请求中,设备应忽略从 DATA LENGTH + 16 到 255 的字节并将安全写保护配置块的这些字节设置为零。
- Secure Write Protect Entry 0 to Entry 3 : The Secure Write Protect Configuration Block may contain only the Entry 0, the Entries 0 and 1, the Entries 0, 1 and 2, or all four Entries. If the Secure Write Protect Configuration Block does not contain any entry (DATA LENGTH = 00h), all entries in the specified logical unit will be removed. Table 12.2 defines the structure of Secure Write Protect Entry.
- 安全写保护条目 0 到条目 3:安全写保护配置块可能仅包含条目 0、条目 0 和 1、条目 0、1 和 2,或所有四个条目。如果安全写保护配置块不包含任何条目(DATA LENGTH = 00h),则指定逻辑单元中的所有条目都将被删除。表 12.2 定义了安全写保护入口的结构。
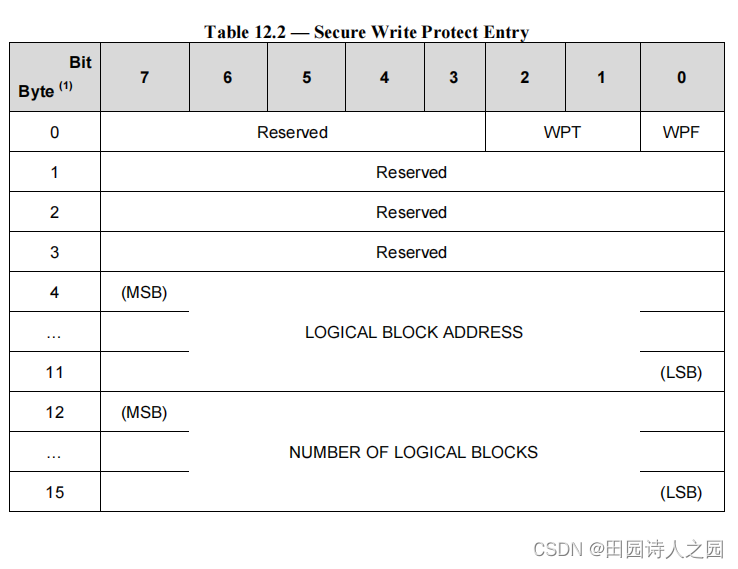
- d) WPT (Write Protect Type) : The write protect type field (WPT) specifies how WPF bit may be modified.
- WPT(写保护类型):写保护类型字段 (WPT) 指定如何修改 WPF 位。
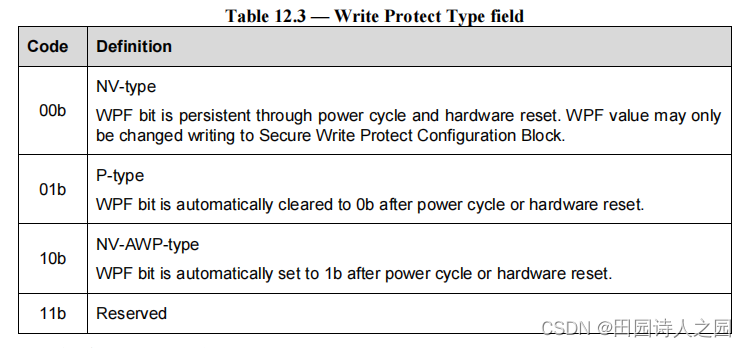
- e) WPF (Write Protect Flag) :
- 0b : Secure Write Protection is disabled.
- 1b : Secure Write Protection is enabled.
A WPF set to one specifies that the logical unit shall inhibit alteration of the medium for LBA within the range indicated by LOGICAL BLOCK ADDRESS field and NUMBER OF LOGICAL BLOCKS field. Commands requiring writes to the medium shall be terminated with CHECK CONDITION status, with the sense key set to DATA PROTECT, and the additional sense code set to WRITE PROTECTED.
设置为 1 的 WPF 指定逻辑单元应禁止在 LOGICAL BLOCK ADDRESS 字段和 NUMBER OF LOGICAL BLOCKS 字段指示的范围内更改 LBA 的介质。要求写入介质的命令应以检查条件状态终止,检测键设置为数据保护,附加检测代码设置为写入保护。
-
Logical units that contain cache shall write all cached logical blocks to the medium (e.g., as they would do in response to a SYNCHRONIZE CACHE command with the LOGICAL BLOCK ADDRESS field and the NUMBER OF LOGICAL BLOCKS field set to the values indicated in the Secure Write Protect Entry) prior to enabling the write protection.
包含高速缓存的逻辑单元应将所有高速缓存的逻辑块写入介质(例如,它们响应 SYNCHRONIZE CACHE 命令时所做的操作,其中逻辑块地址字段和逻辑块数量字段设置为安全写入中指示的值保护条目)之前启用写保护。
A WPF bit set to zero specifies that the logical unit may allow writing to the medium, depending on other write inhibit mechanisms implemented by the logical unit.
设置为零的 WPF 位指定逻辑单元可以允许写入介质,具体取决于逻辑单元实现的其他写禁止机制。
WPF shall be set to zero after device manufacturing.
WPF 应在设备制造后设置为零。
- f) LOGICAL BLOCK ADDRESS : This field specifies the LBA of the first logical block of the Secure Write Protect area.
- LOGICAL BLOCK ADDRESS:该字段指定安全写保护区域的第一个逻辑块的LBA。
- g) NUMBER OF LOGICAL BLOCKS : This field specifies the number of contiguous logical blocks that belong to the Secure Write Protect area. If the NUMBER OF LOGICAL BLOCKS field is set to zero, then the secure write protection shall apply to the entire logical unit. In that case, only Entry-0 needs to be configured to enable secure write protection for the entire logical unit.
- NUMBER OF LOGICAL BLOCKS:该字段指定属于安全写保护区域的连续逻辑块的数量。如果 NUMBER OF LOGICAL BLOCKS 字段设置为零,则安全写保护将应用于整个逻辑单元。在这种情况下,只需配置 Entry-0 即可为整个逻辑单元启用安全写保护。
3.2 Algorithm and Key for MAC Calculation
The message authentication code (MAC) is calculated using HMAC SHA-256 as defined in [HMAC- SHA]. The HMAC SHA-256 calculation takes as input a key and a message. The resulting MAC is 256 bits (32 bytes), which are embedded in the data frame as part of the request or response.
消息认证代码 (MAC) 是使用 [HMAC-SHA] 中定义的 HMAC SHA-256 计算的。 HMAC SHA-256 计算将密钥和消息作为输入。生成的 MAC 为 256 位(32 字节),作为请求或响应的一部分嵌入到数据帧中。
The key used for the MAC calculation is always the 256-bit Authentication Key stored in the target RPMB region. The message used as input to the MAC calculation is the concatenation of the fields in the RPMB packet.
用于 MAC 计算的密钥始终是存储在目标 RPMB 区域中的 256 位身份验证密钥。用作 MAC 计算输入的消息是 RPMB 数据包中字段的串联。
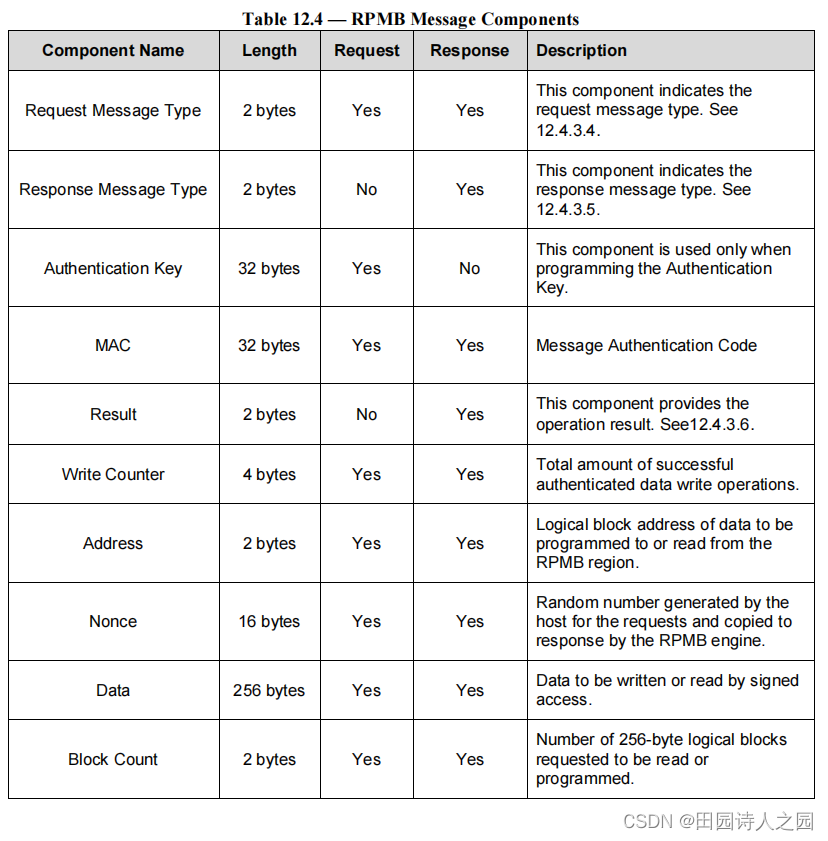
3.3 RPMB Message Components
Each RPMB message includes specific components. These components are displayed in Table 12.4.
每个 RPMB 消息都包含特定的组件。这些组件显示在表 12.4 中。
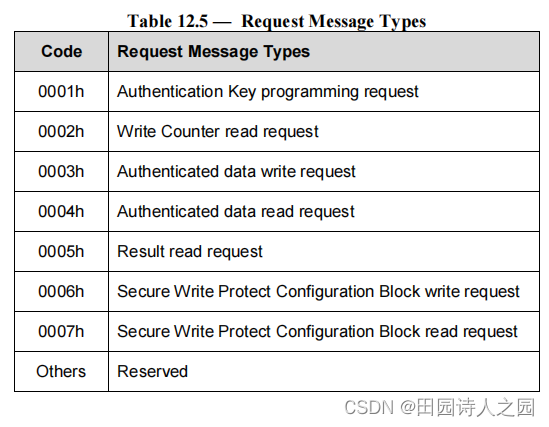
3.4 Request Message Types
The following request message types are defined to support RPMB. These messages are sent from the host to the device.
定义了以下请求消息类型以支持 RPMB。这些消息从主机发送到设备。
- Authentication Key programming request
- Write Counter read request
- Authenticated data write request
- Authenticated data read request
- Result read request
- Secure Write Protect Configuration Block write request
- Secure Write Protect Configuration Block read request
Table 12.5 defines the Request Message Type codes for the various messages.
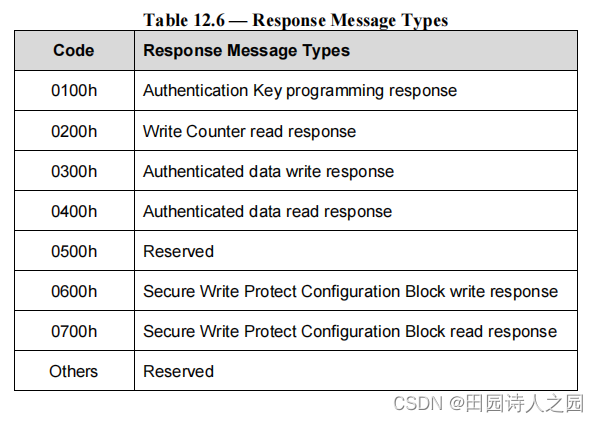
3.5 Response Message Types
The following response message types are defined to support RPMB. These messages are sent from the device to the host.
定义了以下响应消息类型以支持 RPMB。这些消息从设备发送到主机。
- Authentication Key programming response
- Write Counter read response
- Authenticated data write response
- Authenticated data read response
- Secure Write Protect Configuration Block write response
- Secure Write Protect Configuration Block read response
Table 12.6 defines the Response Message Type codes for the various messages.
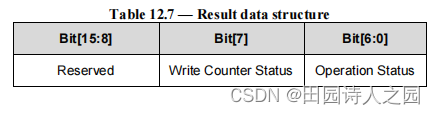
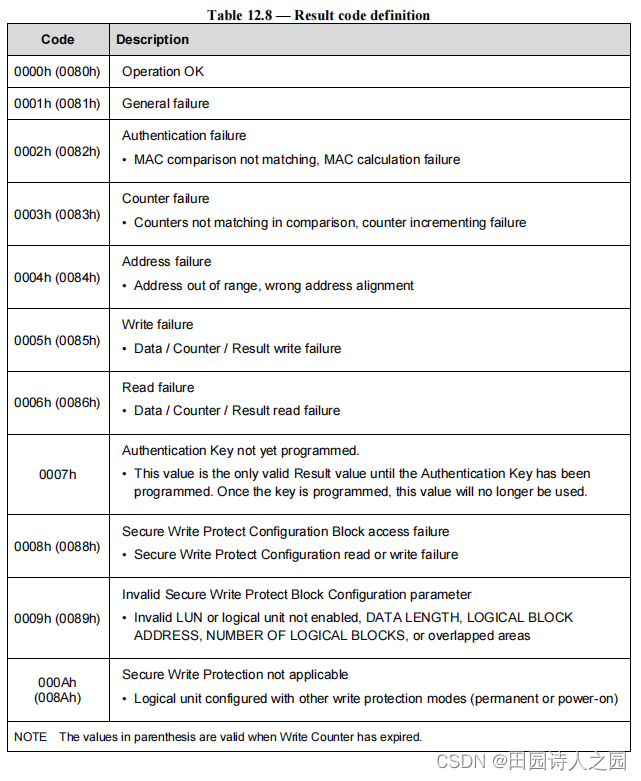
3.6 RPMB Operation Result
Result component of an RPMB message is composed of two bytes. The most significant byte is reserved and shall be set to zero.
RPMB 消息的结果部分由两个字节组成。最高有效字节保留并应设置为零。
4 Implementation
4.1 RPMB Message
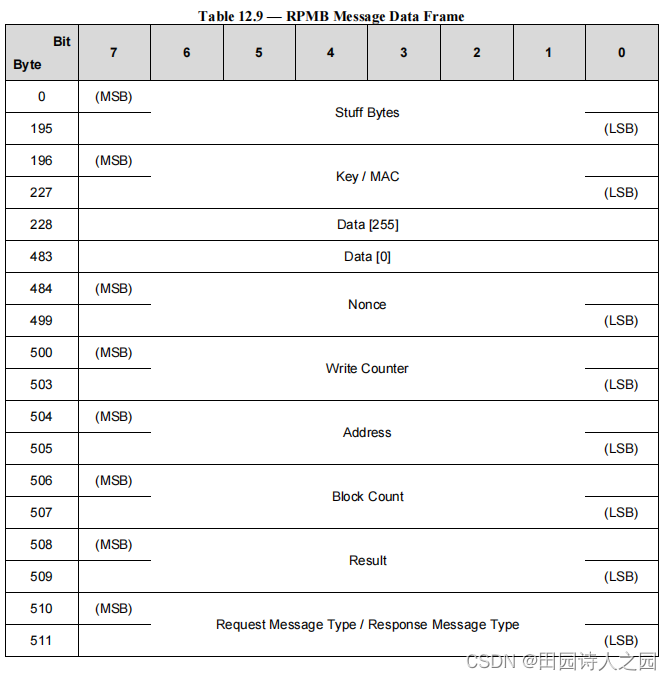
An RPMB Message may be composed of one or more RPMB Message Data Frames.
一个 RPMB 消息可能由一个或多个 RPMB 消息数据帧组成。
RPMB Message Data Frame size is 512 bytes and it is organized as shown in Table 12.9.
RPMB 消息数据帧大小为 512 字节,其组织如表 12.9 所示。
4.2 MAC Calculation
The key used for the MAC calculation is always the 256 bit Authentication Key stored in the device. Input to the MAC calculation is the concatenation of the fields in the RPMB Message Data Frames from byte 228 to byte 511 (stuff bytes and the MAC are excluded).
用于 MAC 计算的密钥始终是存储在设备中的 256 位身份验证密钥。 MAC 计算的输入是 RPMB 消息数据帧中从字节 228 到字节 511 的字段的串联(不包括填充字节和 MAC)。
If RPMB Message is composed by several RPMB Message Data Frames then the input message to MAC is the concatenation of bytes [228:511] of each data frame in the order in which the data frames are sent.
如果 RPMB 消息由多个 RPMB 消息数据帧组成,则 MAC 的输入消息是每个数据帧的字节 [228:511] 的串联,按数据帧的发送顺序排列。
The MAC is valid only in the last data frame.
MAC 仅在最后一个数据帧中有效。
4.3 RPMB Message Data Frame Delivery
The RPMB messages are delivered using SCSI security protocol commands:
RPMB 消息使用 SCSI 安全协议命令传送:
- SECURITY PROTOCOL IN is used to send request messages to the device
- SECURITY PROTOCOL IN 用于向设备发送请求消息
- SECURITY PROTOCOL OUT is used to request to the device the sending of response messages.
- SECURITY PROTOCOL OUT 用于请求设备发送响应消息。
5 SECURITY PROTOCOL IN/OUT Commands
SECURITY PROTOCOL IN command and SECURITY PROTOCOL OUT command defined in [SPC] are used to encapsulate and deliver data packets of any security protocol between host and device without interpreting, dis-assembling or re-assembly the data packets for delivery.
[SPC]中定义的SECURITY PROTOCOL IN命令和SECURITY PROTOCOL OUT命令用于在主机和设备之间封装和传递任何安全协议的数据包,而不需要对数据包进行解释、拆解或重组以进行传递。
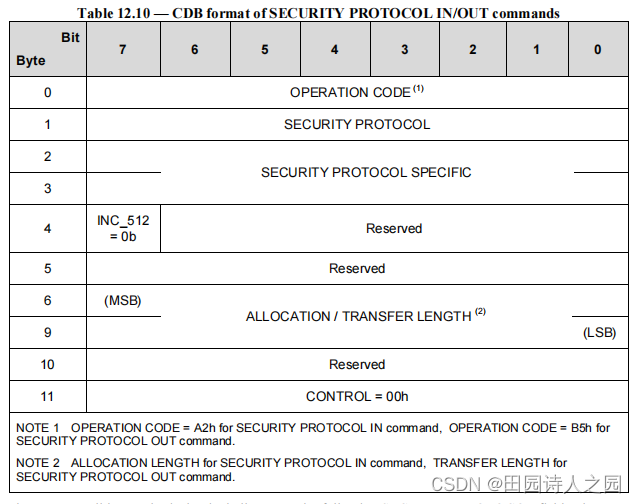
The SECURITY PROTOCOL IN command and SECURITY PROTOCOL OUT command contain a SECURITY PROTOCOL field. A unique security protocol ID is assigned by T10 for JEDEC UFS application.
SECURITY PROTOCOL IN 命令和 SECURITY PROTOCOL OUT 命令包含一个 SECURITY PROTOCOL 字段。 T10 为 JEDEC UFS 应用分配了一个唯一的安全协议 ID。
- SECURITY PROTOCOL = ECh (JEDEC Universal Flash Storage)
5.1 CDB format of SECURITY PROTOCOL IN/OUT commands
The RPMB well known logical unit shall support the following SECURITY PROTOCOL field values:
RPMB 知名逻辑单元应支持以下安全协议字段值:
- 00h: Security protocol information
- ECh: JEDEC Universal Flash Storage (security protocol ID assigned for JEDEC UFS application)
Other values are invalid.
SECURITY PROTOCOL IN/OUT commands shall consider the unique Security Protocol ID assigned to JEDEC UFS application as the only valid Security Protocol ID.
SECURITY PROTOCOL IN/OUT 命令应将分配给 JEDEC UFS 应用程序的唯一安全协议 ID 视为唯一有效的安全协议 ID。
When the SECURITY PROTOCOL field is set to ECh (i.e., the JEDEC Universal Flash Storage),
当 SECURITY PROTOCOL 字段设置为 ECh(即 JEDEC 通用闪存)时,
- INC_512 bit shall be set to zero to specify that the ALLOCATION LENGTH or the TRANSFER LENGTH field expresses the number of bytes to be transferred.
- INC_512 位应设置为零以指定ALLOCATION LENGTH或TRANSFER LENGTH字段表示要传输的字节数。
- If the ALLOCATION LENGTH field in a SECURITY PROTOCOL IN command is not equal to aninteger multiple of 512, then the command shall be terminated with CHECK CONDITION status.
- 如果 SECURITY PROTOCOL IN 命令中的 ALLOCATION LENGTH 字段不等于 512 的整数倍,则该命令将以 CHECK CONDITION 状态终止。
- If the TRANSFER LENGTH field in a SECURITY PROTOCOL OUT command is not equal to an integer multiple of 512, then the command shall be terminated with CHECK CONDITION status.
- 如果 SECURITY PROTOCOL OUT 命令中的 TRANSFER LENGTH 字段不等于 512 的整数倍,则该命令将以 CHECK CONDITION 状态终止。
- The SECURITY PROTOCOL SPECIFIC field specifies the RPMB Protocol ID.
- SECURITY PROTOCOL SPECIFIC 字段指定 RPMB 协议 ID。
The RPMB Protocol ID indicates the RPMB region as defined in Table 12.11
RPMB 协议 ID 表示表 12.11 中定义的 RPMB 区域
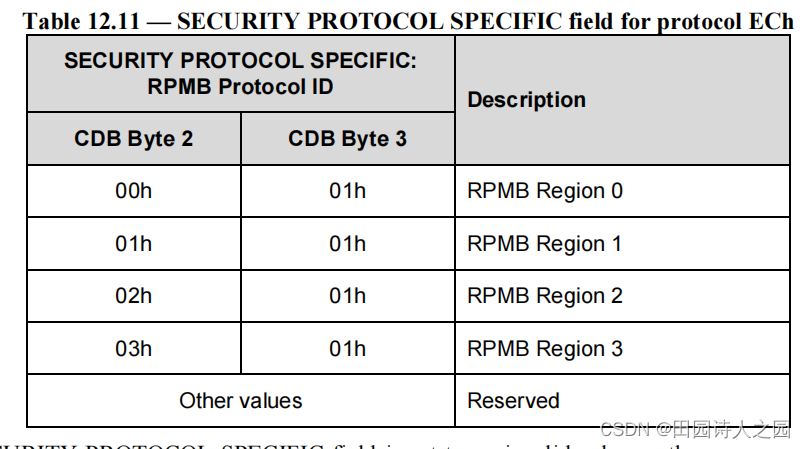
If the SECURITY PROTOCOL SPECIFIC field is set to an invalid value or the corresponding RPMB region is not enabled, then SECURITY PROTOCOL IN/OUT command shall be terminated with CHECK CONDITION status, with the sense key set to ILLEGAL REQUEST and the additional sense code set to INVALID FIELD IN CDB.
如果 SECURITY PROTOCOL SPECIFIC 字段设置为无效值或相应的 RPMB 区域未启用,则 SECURITY PROTOCOL IN/OUT 命令应以 CHECK CONDITION 状态终止,感知键设置为 ILLEGAL REQUEST 并设置附加感知代码到 INVALID FIELD IN CDB。
Secure Write Protect Configuration Block write and Secure Write Protect Configuration Block read request are supported only by RPMB region 0.
安全写保护配置块写入和安全写保护配置块读取请求仅由 RPMB 区域 0 支持。
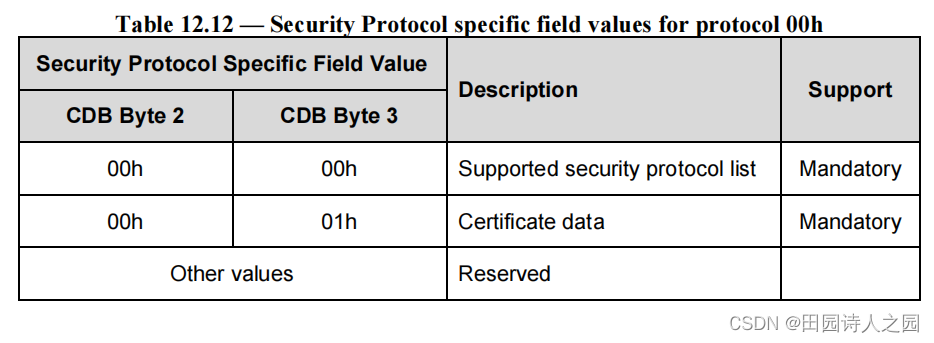
As required by [SPC], the SECURITY PROTOCOL value of 00h (security protocol information) shall be supported if the SECURITY PROTOCOL IN command is supported by the device. The security protocol information security protocol (i.e., the SECURITY PROTOCOL field set to 00h in a SECURITY PROTOCOL IN command) is used to transfer security protocol related information from the logical unit.
根据 [SPC] 的要求,如果设备支持 SECURITY PROTOCOL IN 命令,则应支持 SECURITY PROTOCOL 值 00h(安全协议信息)。安全协议信息安全协议(即,SECURITY PROTOCOL IN 命令中的 SECURITY PROTOCOL 字段设置为 00h)用于从逻辑单元传输安全协议相关信息。
When the SECURITY PROTOCOL field is set to 00h in a SECURITY PROTOCOL IN command, the two bytes SECURITY PROTOCOL SPECIFIC field shall contain a numeric value as defined in Table 12.11.
当 SECURITY PROTOCOL IN 命令中的 SECURITY PROTOCOL 字段设置为 00h 时,两个字节的 SECURITY PROTOCOL SPECIFIC 字段应包含表 12.11 中定义的数值。
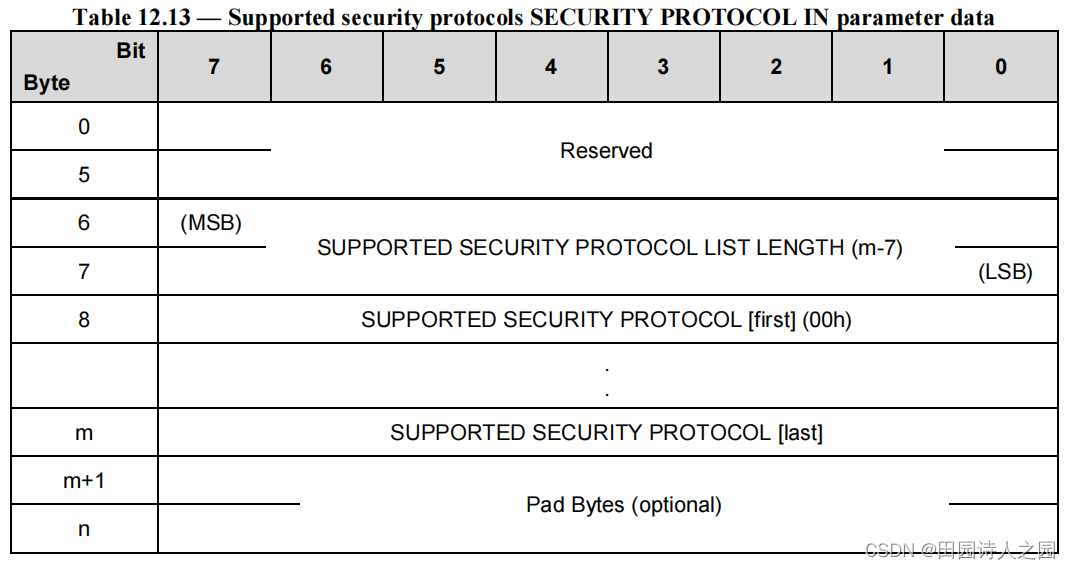
5.2 Supported security protocols list description
According to [SPC], if the SECURITY PROTOCOL field is set to 00h and the SECURITY PROTOCOL SPECIFIC field is set to 0000h in a SECURITY PROTOCOL IN command, the parameter data shall have the format shown in Table 12.13.
根据 [SPC],如果在 SECURITY PROTOCOL IN 命令中 SECURITY PROTOCOL 字段设置为 00h 并且 SECURITY PROTOCOL SPECIFIC 字段设置为 0000h,则参数数据应具有表 12.13 中所示的格式。
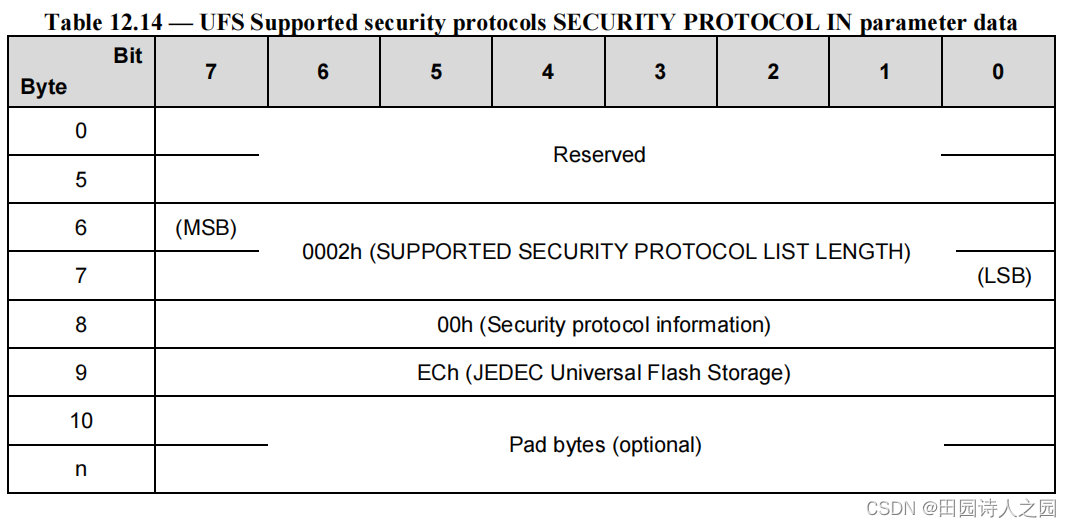
Security protocol information (00h) and the JEDEC Universal Flash Storage (ECh) are the only valid security protocol ID’s supported by the RPMB well known logical unit, therefore Table 12.13 shall be implemented as defined in Table 12.14.
安全协议信息 (00h) 和 JEDEC 通用闪存 (ECh) 是 RPMB 知名逻辑单元支持的唯一有效安全协议 ID,因此表 12.13 应按照表 12.14 中的定义实施。
5.3 Certificate data description
If the SECURITY PROTOCOL field is set to 00h and the SECURITY PROTOCOL SPECIFIC field is set to 0001h in a SECURITY PROTOCOL IN command, the parameter data shall have the format shown in Table 12.14.
如果在 SECURITY PROTOCOL IN 命令中 SECURITY PROTOCOL 字段设置为 00h 并且 SECURITY PROTOCOL SPECIFIC 字段设置为 0001h,则参数数据应具有表 12.14 中所示的格式。
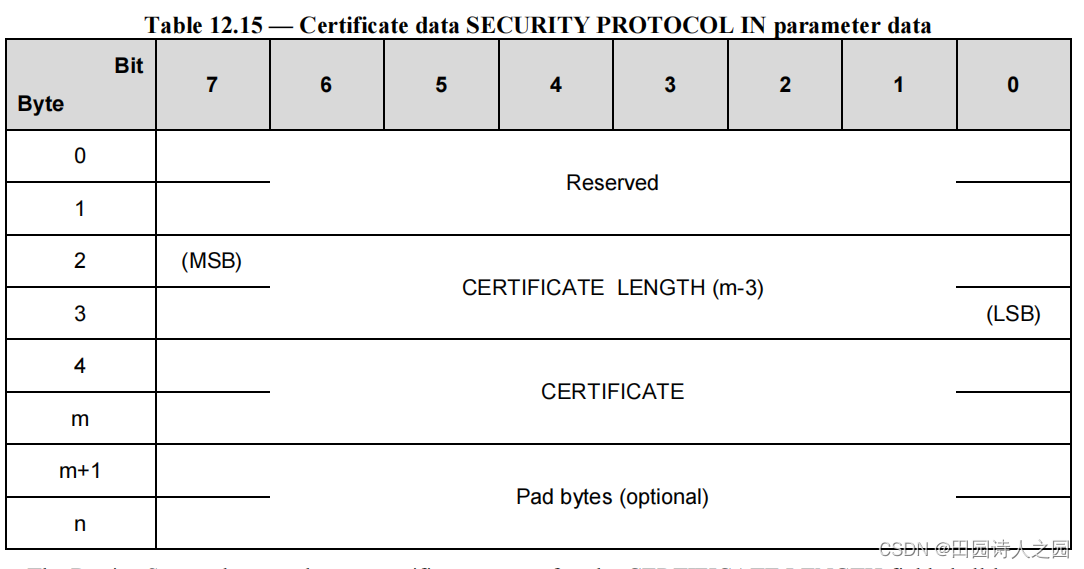
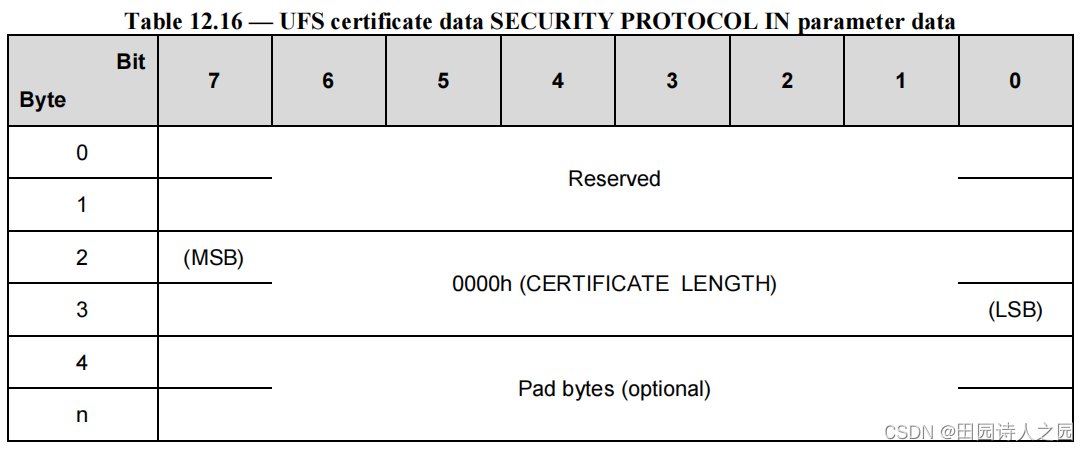
The Device Server does not have a certificate to transfer, the CERTIFICATE LENGTH field shall be set to 0000h. therefore Table 12.15 shall be implemented as defined in Table 12.16.
设备服务器没有要传输的证书,证书长度字段应设置为 0000h。因此表 12.15 应按照表 12.16 中的定义执行。
6 RPMB Operations
6.1 Request Type Message Delivery
- Only one RPMB operation can be executed at any time.
- 任何时候只能执行一个 RPMB 操作。
- An initiator sends request type message to RPMB well known logical unit to request the execution of an operation.
- 发起者向 RPMB 众所周知的逻辑单元发送请求类型消息以请求执行操作。
- To deliver a request type message, the initiator sends a SECURITY PROTOCOL OUT command with SECURITY PROTOCOL field is set to ECh (i.e., the JEDEC Universal Flash Storage) and indicating the target RPMB region in the SECURITY PROTOCOL SPECIFIC field.
- 传递一个请求类型消息,发起者发送一个 SECURITY PROTOCOL OUT 命令,SECURITY PROTOCOL 字段设置为 ECh(即 JEDEC 通用闪存),并在 SECURITY PROTOCOL SPECIFIC 字段中指示目标 RPMB 区域。
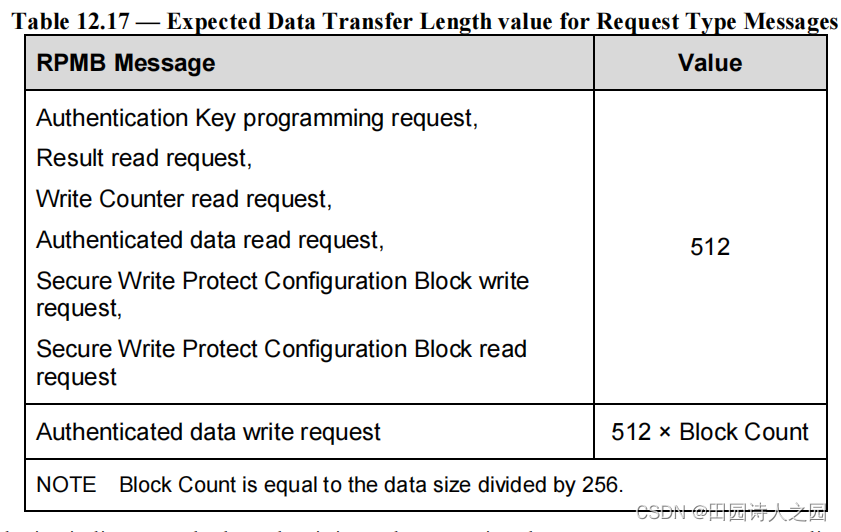
- For an authenticated data write request, the data to be written into the RPMB data area is included in the request message. The maximum data size in a single Authenticated Data Write request is equal to bRPMB_ReadWriteSize × 256 bytes; multiple Authenticated Data Write operations should be executed if the desired data size exceeds this value.
- 对于鉴权数据写请求,需要写入RPMB数据区的数据包含在请求消息中。单个Authenticated Data Write请求中的最大数据大小等于bRPMB_ReadWriteSize × 256字节;如果所需的数据大小超过此值,则应执行多个经过身份验证的数据写入操作。
- For SECURITY PROTOCOL OUT command, the Flags.W in the COMMAND UPIU is set to one since data is transferred from the host to the device.
- 对于 SECURITY PROTOCOL OUT 命令,COMMAND UPIU 中的 Flags.W 设置为 1,因为数据从主机传输到设备。
- Table 12.17 defines the Expected Data Transfer Length field value in the COMMAND UPIU for the various cases.
- 表 12.17 定义了各种情况下 COMMAND UPIU 中的 Expected Data Transfer Length 字段值。
- The device indicates to the host that it is ready to receive the request type message sending READY TO TRANSFER UPIU. If the Expected Data Transfer Length is 512 byte, then Data Buffer Offset field shall be set to a value of zero and Data Transfer Count field shall be set to a value of 512.
- 设备向主机表明它已准备好接收发送 READY TO TRANSFER UPIU 的请求类型消息。如果预期数据传输长度为 512 字节,则数据缓冲区偏移字段应设置为零值,数据传输计数字段应设置为 512 值。
- The number of bytes requested in a single READY TO TRANSFER UPIU shall not be greater than the value indicated by bMaxDataOutSize attribute. A single READY TO TRANSFER UPIU may request the transfer of one or more RPMB Messages.
- 在单个 READY TO TRANSFER UPIU 中请求的字节数不得大于 bMaxDataOutSize 属性指示的值。单个 READY TO TRANSFER UPIU 可以请求传输一个或多个 RPMB 消息。
- In response to each READY TO TRANSFER UPIU, the host delivers the requested portion of the message sending DATA OUT UPIU.
- 作为对每个 READY TO TRANSFER UPIU 的响应,主机传送发送 DATA OUT UPIU 的消息的请求部分。
- To complete the SECURITY PROTOCOL OUT command, the device returns a RESPONSE UPIU with the status.
- 要完成 SECURITY PROTOCOL OUT 命令,设备会返回一个带有状态的 RESPONSE UPIU。
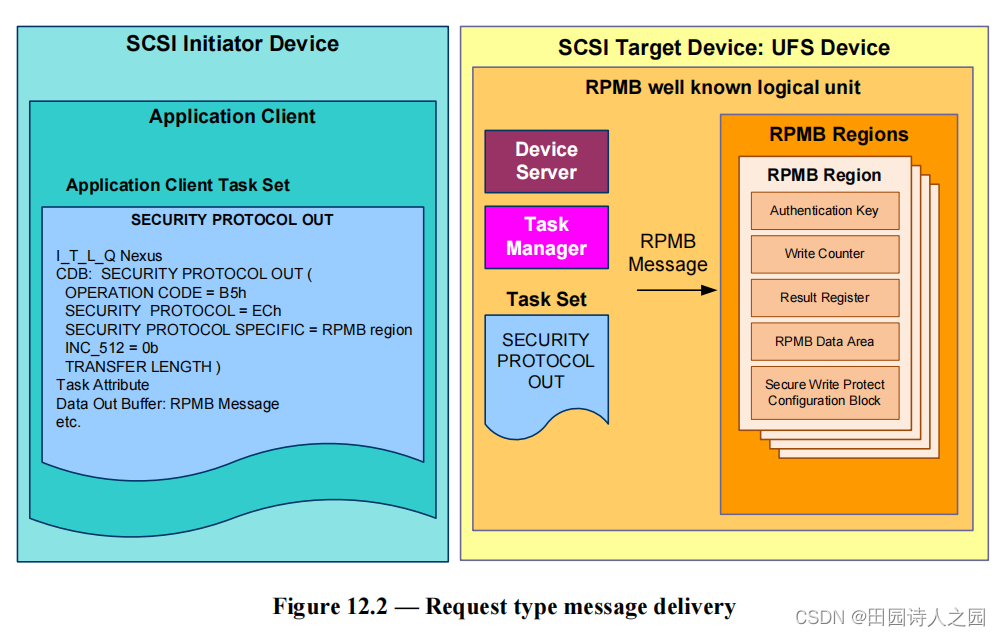
- Figure 12.2 depicts a request type message delivery. The application client loads the RPMB Message in the Data Out Buffer and indicates the target RPMB Region in SECURITY PROTOCOL SPECIFIC field.
- 图 12.2 描述了请求类型的消息传递。应用程序客户端在数据输出缓冲区中加载 RPMB 消息,并在 SECURITY PROTOCOL SPECIFIC 字段中指示目标 RPMB 区域。
6.2 Response Type Message Delivery
- A initiator requests the RPMB well known logical unit to send a response type message to retrieve the result of a previous operation, to retrieve the Write Counter, to retrieve data from the RPMB data area, or to retrieve the contents of a Secure Write Protect Configuration Block.
- 发起者请求 RPMB 知名逻辑单元发送响应类型消息以检索先前操作的结果、检索写计数器、从 RPMB 数据区检索数据或检索安全写保护配置块的内容。
- To request the delivery of a response type message, the host sends a SECURITY PROTOCOL IN command with SECURITY PROTOCOL field is set to ECh (i.e., the JEDEC Universal Flash Storage) and indicating the RPMB region in the SECURITY PROTOCOL SPECIFIC field.
- 为了请求传递响应类型消息,主机发送一个 SECURITY PROTOCOL IN 命令,其中 SECURITY PROTOCOL 字段设置为 ECh(即 JEDEC 通用闪存)并在 SECURITY PROTOCOL SPECIFIC 字段中指示 RPMB 区域。
- For an authenticated data read the data from the RPMB data area is included in the response message.
- 对于经过身份验证的数据,从 RPMB 数据区读取的数据包含在响应消息中。
- For SECURITY PROTOCOL IN command, the Flags.R in the COMMAND UPIU is set to one since data is transferred from the device to the host.
- 对于 SECURITY PROTOCOL IN 命令,COMMAND UPIU 中的 Flags.R 设置为 1,因为数据从设备传输到主机。
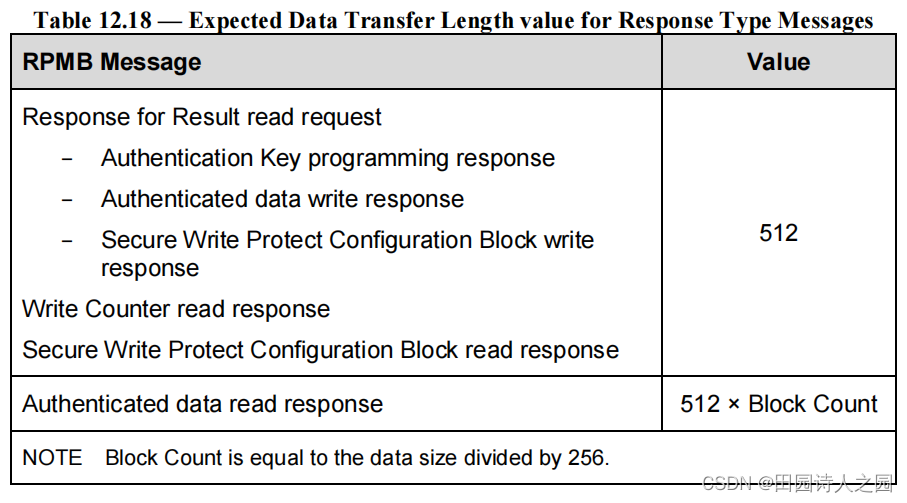
- Table 12.18 defines the Expected Data Transfer Length field value in the COMMAND UPIU for the various cases.
- 表 12.18 定义了各种情况下 COMMAND UPIU 中的 Expected Data Transfer Length 字段值。
- The device returns the result or data requested in the RPMB message. The RPMB message is delivered by sending one or more DATA IN UPIU in the data phase. A single DATA IN UPIU may deliver one or more RPMB Messages.
- 设备返回 RPMB 消息中请求的结果或数据。 RPMB消息通过在数据阶段发送一个或多个DATA IN UPIU来传递。单个 DATA IN UPIU 可以传送一个或多个 RPMB 消息。
- The data size in DATA IN UPIU shall not exceed the value indicated by bMaxDataInSize attribute.
- DATA IN UPIU 中的数据大小不应超过 bMaxDataInSize 属性指示的值。
- To complete the SECURITY PROTOCOL IN, the device sends a RESPONSE UPIU with the status.
- 为了完成 SECURITY PROTOCOL IN,设备发送一个带有状态的 RESPONSE UPIU。
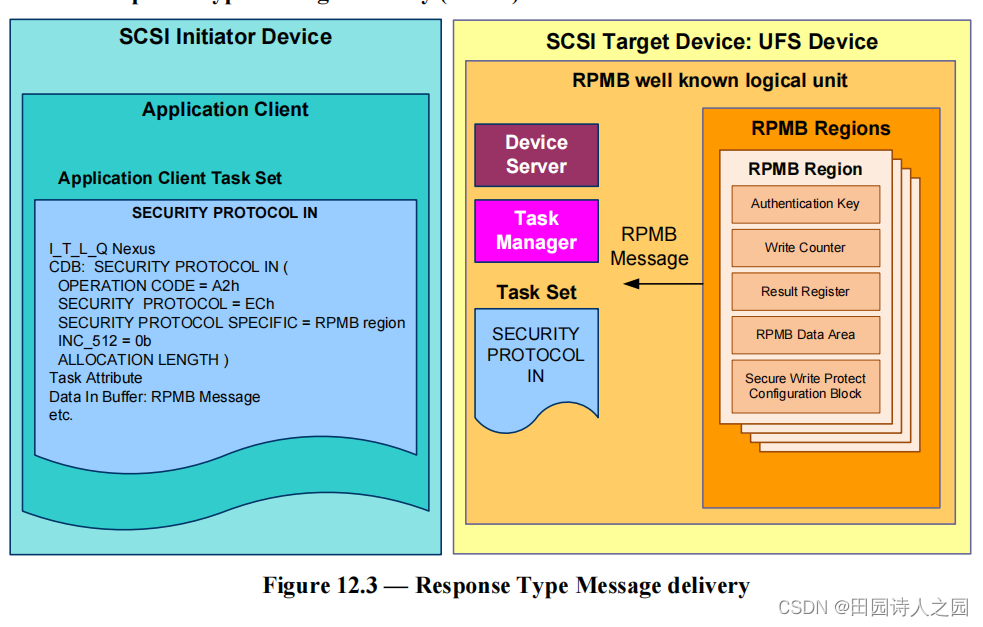
- Figure 12.3 depicts a response type message delivery. An application client requests a RPMB Region to transfer the RPMB Message in the Data In Buffer specifying the RPMB Region ID in SECURITY PROTOCOL SPECIFIC field of the CDB.
- 图 12.3 描述了响应类型的消息传递。应用程序客户端请求 RPMB 区域传输缓存中数据中的 RPMB 消息,并在 CDB 的安全协议特定字段中指定 RPMB 区域 ID。
6.3 Authentication Key Programming
- The Authentication Key programming is initiated by a SECURITY PROTOCOL OUT command
- 身份验证密钥编程由 SECURITY PROTOCOL OUT 命令启动
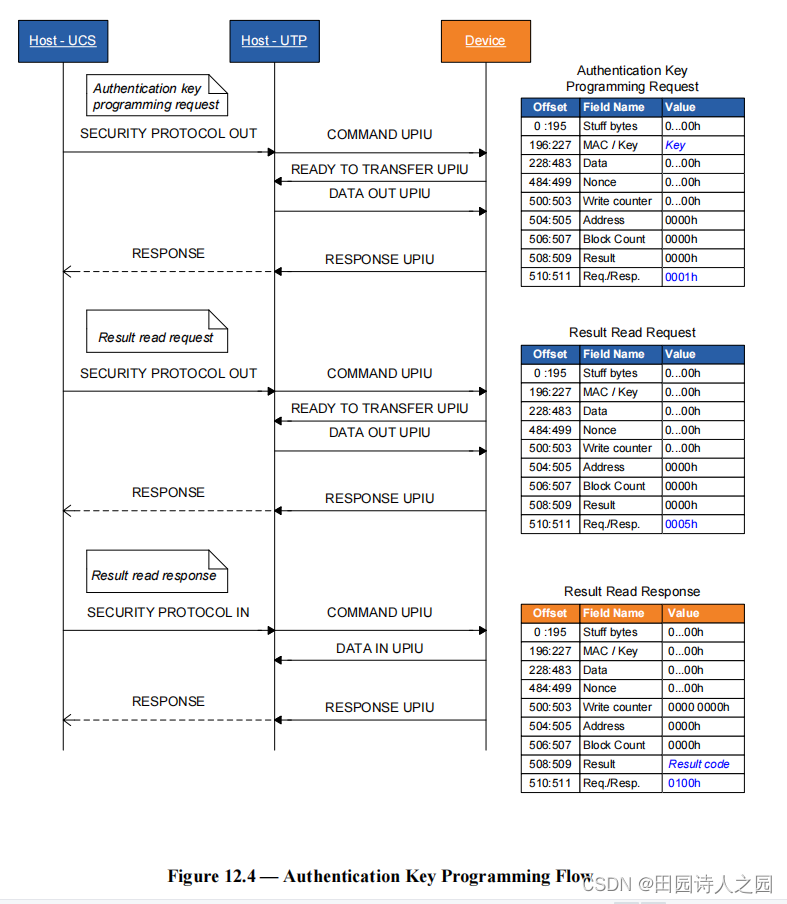
- An initiator sends the SECURITY PROTOCOL OUT command with SECURITY PROTOCOL field set to ECh and indicating the RPMB region in the SECURITY PROTOCOL SPECIFIC field. The RPMB data frame includes the Request Message Type = 0001h and the Authentication Key.
- 发起者发送 SECURITY PROTOCOL OUT 命令,SECURITY PROTOCOL 字段设置为 ECh,并在 SECURITY PROTOCOL SPECIFIC 字段中指示 RPMB 区域。 RPMB 数据帧包括 Request Message Type = 0001h 和 Authentication Key。
- The device returns GOOD status in status response when Authentication Key programming is completed.
- 当 Authentication Key 编程完成时,设备在状态响应中返回 GOOD 状态。
- The Authentication Key programming verification process starts by issuing a SECURITY PROTOCOL OUT command
- Authentication Key 编程验证过程通过发出 SECURITY PROTOCOL OUT 命令开始
- An initiator sends a SECURITY PROTOCOL OUT command with SECURITY PROTOCOL field set to ECh and indicating the RPMB region in the SECURITY PROTOCOL SPECIFIC field. The RPMB data frame contains the Request Message Type = 0005h (Result read request). Note that any request other than the Result read request from any initiator will overwrite the Result register of the RPMB Region.
- 发起者发送 SECURITY PROTOCOL OUT 命令,SECURITY PROTOCOL 字段设置为 ECh,并在 SECURITY PROTOCOL SPECIFIC 字段中指示 RPMB 区域。 RPMB 数据帧包含请求消息类型 = 0005h(结果读取请求)。请注意,任何发起者发出的 Result 读取请求以外的任何请求都会覆盖 RPMB Region 的 Result 寄存器。
- The device returns GOOD status in status response when the operation result is ready for retrieval.
- 当操作结果准备好检索时,设备在状态响应中返回 GOOD 状态。
- An initiator retrieves the operation result by issuing a SECURITY PROTOCOL IN command.
- 发起者通过发出 SECURITY PROTOCOL IN 命令检索操作结果。
- The SECURITY PROTOCOL field is set to ECh and the SECURITY PROTOCOL SPECIFIC field indicates the RPMB region.
- SECURITY PROTOCOL 字段设置为 ECh,SECURITY PROTOCOL SPECIFIC 字段指示 RPMB 区域。
- Device returns the RPMB data frame containing the Response Message Type = 0100h and the Result code.
- 设备返回包含响应消息类型 = 0100h 和结果代码的 RPMB 数据帧。
- If programming of Authentication Key failed then returned result is “Write failure” (0005h). If some other error occured during Authentication Key programming then returned result is “General failure” (0001h).
- 如果 Authentication Key 编程失败,则返回结果为“Write failure”(0005h)。如果在身份验证密钥编程期间出现其他错误,则返回结果为“一般故障”(0001h)。
Access to RPMB data area is not possible before the Authentication Key is programmed in the corresponding RPMB region. The state of the device can be checked by trying to write/read data to/from the RPMB data area: if the Authentication Key is not programmed then the Result field in the response message will be set to “Authentication Key not yet programmed” (0007h).
在相应的 RPMB 区域中编程验证密钥之前,无法访问 RPMB 数据区域。可以通过尝试向 RPMB 数据区域写入/读取数据来检查设备的状态:如果未对身份验证密钥进行编程,则响应消息中的结果字段将设置为“身份验证密钥尚未编程”( 0007h)。
6.4 Read Counter Value
- The Read Counter Value sequence is initiated by a SECURITY PROTOCOL OUT command.
- 读取计数器值序列由 SECURITY PROTOCOL OUT 命令启动。
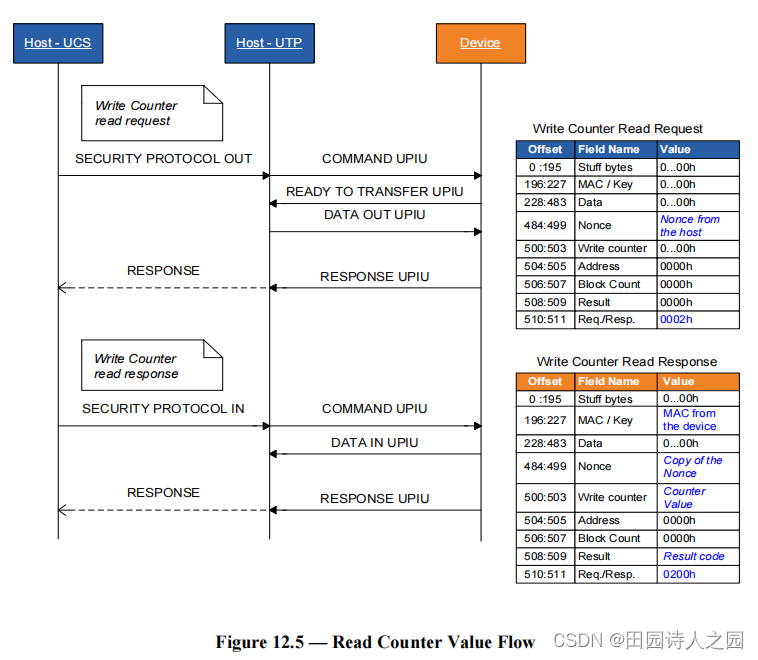
- An initiator sends the SECURITY PROTOCOL OUT command with SECURITY PROTOCOL field set to ECh and indicating the RPMB region in the SECURITY PROTOCOL SPECIFIC field. The RPMB data frame includes the Request Message Type = 0002h and the Nonce.
- 发起者发送 SECURITY PROTOCOL OUT 命令,SECURITY PROTOCOL 字段设置为 ECh,并在 SECURITY PROTOCOL SPECIFIC 字段中指示 RPMB 区域。 RPMB 数据帧包括 Request Message Type = 0002h 和 Nonce。
- When a GOOD status in the status response is received, the write counter value is retrieved sending a SECURITY PROTOCOL IN command.
- 当接收到状态响应中的 GOOD 状态时,通过发送 SECURITY PROTOCOL IN 命令检索写入计数器值。
- An initiator sends the SECURITY PROTOCOL IN command with the SECURITY PROTOCOL field is set to ECh and indicating the RPMB region in the SECURITY PROTOCOL SPECIFIC field.
- 发起者发送 SECURITY PROTOCOL IN 命令,SECURITY PROTOCOL 字段设置为 ECh,并在 SECURITY PROTOCOL SPECIFIC 字段中指示 RPMB 区域。
- The device returns a RPMB data frame with Response Message Type = 0200h, a copy of the Nonce received in the request, the Write Counter value, the MAC and the Result.
- 设备返回响应消息类型 = 0200h 的 RPMB 数据帧、请求中收到的 Nonce 副本、写入计数器值、MAC 和结果。
If reading of the counter value fails then returned result is “Read failure” (0006h/0086h).
如果读取计数器值失败,则返回结果为“读取失败”(0006h/0086h)。
If some other error occurs then Result is “General failure” (0001h/0081h).
如果发生其他错误,则结果为“一般故障”(0001h/0081h)。
If counter has expired also bit 7 is set to 1 in returned results.
如果计数器已过期,则返回结果中的位 7 也会设置为 1。



![[架构之路-202]- 常见的需求获取技术=》输出=》用户需求、客户需求(As...., I want.....)、用例图](https://img-blog.csdnimg.cn/23fcc0dfdc42409d88f1a84aaad49d32.png)