首先来熟悉一下ida的使用。
首先找到打开ida,点击"debugger"-> “run” -> “local windows debugger"后,从Application中找到程序并点击"ok”,程序停在入口处。
因为我们要调试的是接收数据包的加解密过程,一般来说可以从recv,WSARecv这几个常用网络API入手,这时在右边的"Module"窗口处,输入ws2查找过滤模块ws2_32.dll:
鼠标双击选中ws2_32.dll后,可以在Module窗口中双击需要查看的模块中的API函数,比如recv函数,这时主窗口显示的就是recv的反汇编代码了。
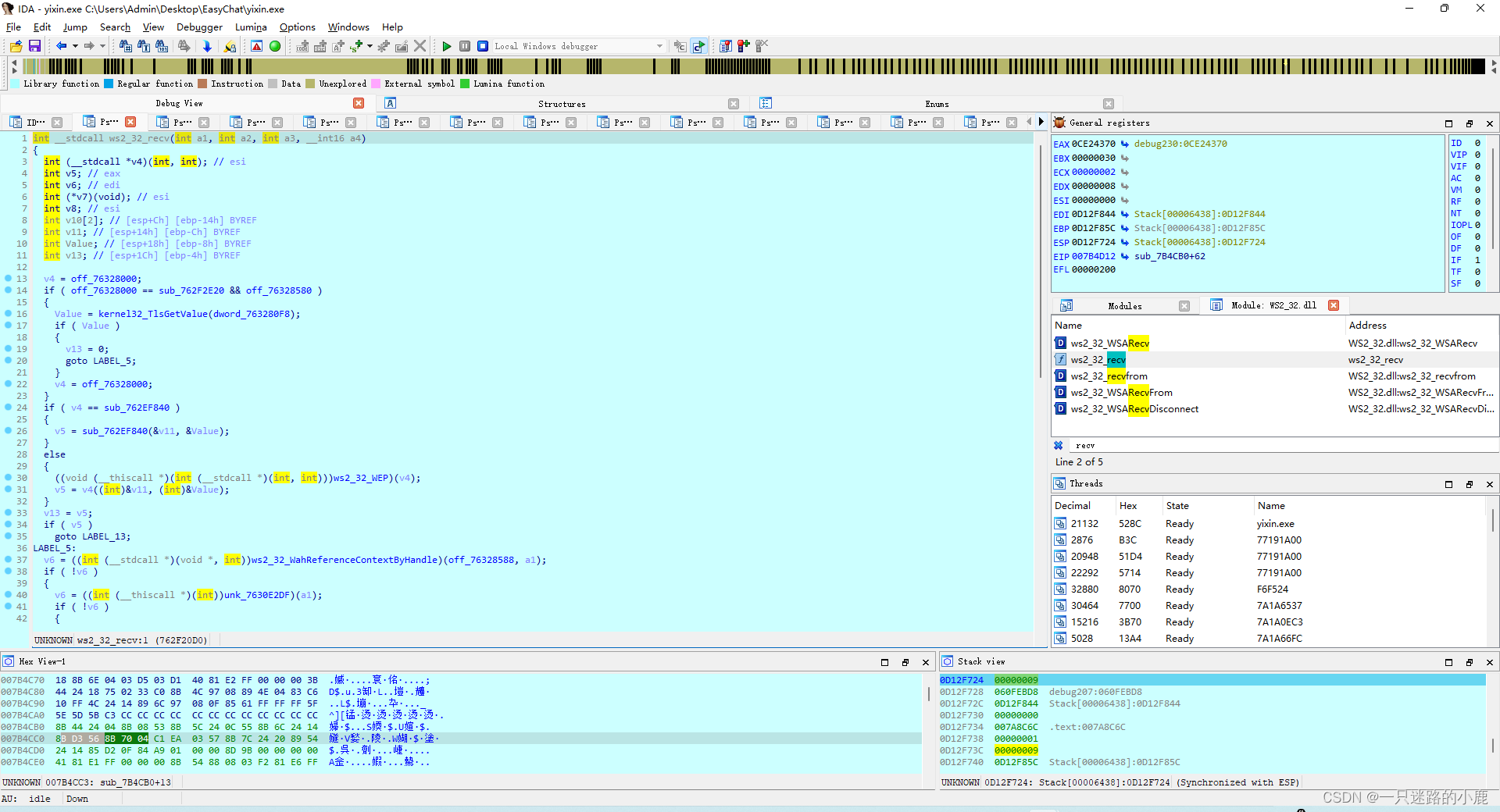
此时可以通过鼠标点击或者菜单下断点调试了。
同时,开启wireshark抓包,可以看到登录过程产生如下数据包:
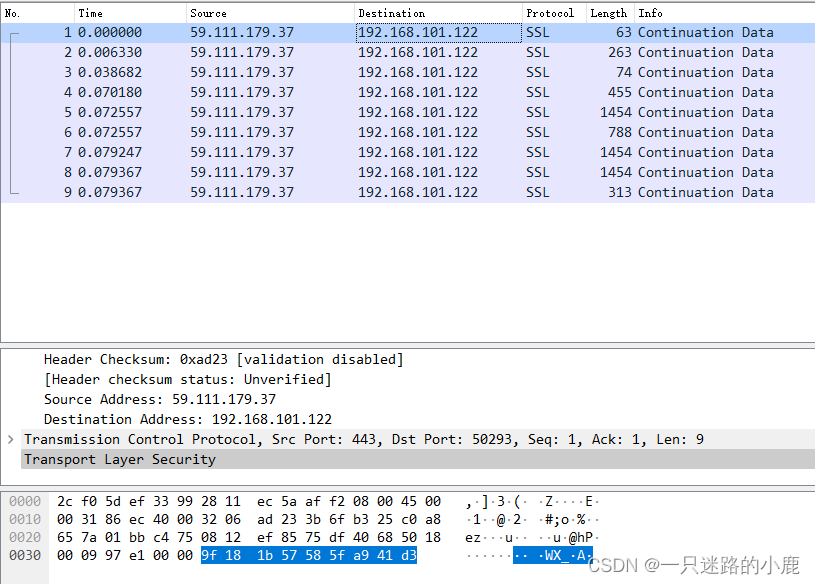
通过对recv的反复调试,在某种执念驱使下,多次低水平重复和一点一点的推进,中间经过了多次的调试和放松,最终确定了发现数据包的处理主要在一下函数中:
这里要说明2点:
- 因为程序是动态加载的,所以地址并不一定跟本文的图中相同。
- 本文是叙述性的,有很多片段是不可描述的细节总结,不可能还原全过程的所有细节。读万卷书行万里路,只看文字是无法描绘所有场景的,某些事只能在行动中定义。
recv后数据的走向如下函数所示:
int __thiscall sub_9E3A40(int this, int a2)
{
volatile signed __int32 *v3; // ebx
volatile signed __int32 *v4; // ebx
_DWORD *v5; // eax
int v6; // ebx
int v7; // ecx
int v8; // eax
int v9; // eax
_DWORD *v10; // eax
int result; // eax
int v12; // edx
int Error; // eax
int v14; // edi
LONG v15; // eax
int v16; // ecx
unsigned int v17; // [esp-4h] [ebp-20090h]
char v18; // [esp+0h] [ebp-2008Ch] BYREF
int v19; // [esp+14h] [ebp-20078h]
int pExceptionObject[4]; // [esp+28h] [ebp-20064h] BYREF
int v21; // [esp+38h] [ebp-20054h] BYREF
char *v22; // [esp+3Ch] [ebp-20050h] BYREF
_DWORD v23[4]; // [esp+40h] [ebp-2004Ch] BYREF
_DWORD *v24; // [esp+50h] [ebp-2003Ch]
char v25[8]; // [esp+58h] [ebp-20034h] BYREF
LPVOID lpMem[3]; // [esp+60h] [ebp-2002Ch] BYREF
int v27; // [esp+6Ch] [ebp-20020h] BYREF
int v28; // [esp+70h] [ebp-2001Ch]
unsigned int v29; // [esp+74h] [ebp-20018h]
char v30[131072]; // [esp+78h] [ebp-20014h] BYREF
char *v31; // [esp+2007Ch] [ebp-10h]
int v32; // [esp+20088h] [ebp-4h]
v31 = &v18;
v3 = *(volatile signed __int32 **)(this + 336);
*(_DWORD *)(this + 336) = 0;
v22 = (char *)this;
*(_DWORD *)(this + 332) = 0;
if ( v3 )
{
if ( !_InterlockedExchangeAdd(v3 + 1, 0xFFFFFFFF) )
{
(**(void (__thiscall ***)(volatile signed __int32 *))v3)(v3);
if ( !_InterlockedExchangeAdd(v3 + 2, 0xFFFFFFFF) )
(*(void (__thiscall **)(volatile signed __int32 *))(*v3 + 4))(v3);
}
}
v4 = *(volatile signed __int32 **)(this + 348);
*(_DWORD *)(this + 348) = 0;
*(_DWORD *)(this + 344) = 0;
if ( v4 )
{
if ( !_InterlockedExchangeAdd(v4 + 1, 0xFFFFFFFF) )
{
(**(void (__thiscall ***)(volatile signed __int32 *))v4)(v4);
if ( !_InterlockedExchangeAdd(v4 + 2, 0xFFFFFFFF) )
(*(void (__thiscall **)(volatile signed __int32 *))(*v4 + 4))(v4);
}
}
v21 = 1;
v29 = this - 12;
v29 = sub_9E5210(sub_9E4410, 0, &v21);
v32 = 1;
v24 = 0;
v5 = operator new(0x28u);
v6 = (int)v5;
if ( !v5 )
unknown_libname_325();
v17 = v29;
*v5 = std::_Func_impl<std::_Callable_obj<nbase::WeakCallback<std::_Bind<1,void,std::_Pmf_wrap<void (__thiscall nbiz::LinkSocket::*)(int),void,nbiz::LinkSocket,int>,nbiz::LinkSocket * const &,int &>>,0>,std::allocator<std::_Func_class<void,>>,void,>::`vftable';
sub_57E2A0(v17);
v24 = (_DWORD *)v6;
LOBYTE(v32) = 3;
v7 = v19;
if ( v19 && !_InterlockedDecrement((volatile signed __int32 *)(v19 + 8)) )
(*(void (__thiscall **)(int))(*(_DWORD *)v7 + 4))(v7);
v8 = sub_52C600(v25, v23);
LOBYTE(v32) = 4;
sub_52C680(v8);
LOBYTE(v32) = 3;
sub_52AFC0(v25);
v9 = *(_DWORD *)(sub_936F30() + 176);
if ( v9 >= 15 )
{
if ( v9 > 240 )
v9 = 240;
}
else
{
v9 = 15;
}
v10 = (_DWORD *)sub_54DA90(v9, v9 >> 31);
sub_8EBCB0(*v10, v10[1]);
LOBYTE(v32) = 5;
result = (*(int (__thiscall **)(int, char *, int, _DWORD))(*(_DWORD *)(this + 64) + 20))(this + 64, v30, 0x20000, 0);
v12 = result;
if ( result == -1 )
{
result = sub_9E2950();
v12 = result;
}
v32 = 3;
if ( v12 == -1 )
{
Error = WSAGetLastError();
v14 = Error;
if ( Error == 10035 || Error == 10036 )
return sub_52F090(v23);
v15 = sub_8EB5B0();
if ( (unsigned int)(*(int (__thiscall **)(LONG))(*(_DWORD *)v15 + 16))(v15) >= 2 )
{
v27 = 2;
v28 = 37;
v29 = (unsigned int)"E:\\14_svn_branch\\src\\biz/network/socket_wrapper.h";
sub_8EB730(&v27, "[nbiz::WouldBlock] err_code:%d", v14);
}
result = sub_9E3770(this - 12);
v16 = *(_DWORD *)(this + 4);
if ( v16 )
result = (*(int (__thiscall **)(int, int))(*(_DWORD *)v16 + 4))(v16, 1);
}
else if ( v12 > 0 )
{
if ( !*(_BYTE *)(this + 24) )
{
sub_8EA440(2, "core\\link_socket_asyncsockex.cpp", 286, "Receive Message While Not Encrypted", v18);
v22 = "Receive Message While Not Encrypted";
std::exception::exception((std::exception *)pExceptionObject, (const char *const *)&v22);
pExceptionObject[0] = (int)&nbase::NException::`vftable';
pExceptionObject[3] = 5004;
_CxxThrowException(pExceptionObject, (_ThrowInfo *)&_TI3_AVNException_nbase__);
}
v29 = 15;
v28 = 0;
LOBYTE(lpMem[0]) = 0;
LOBYTE(v32) = 7;
(*(void (__thiscall **)(_DWORD, char *, int, LPVOID *))(**(_DWORD **)(this + 8) + 24))(
*(_DWORD *)(this + 8),
v30,
v12,
lpMem);
sub_55D4C0((_DWORD *)(this + 188), lpMem, 0, 0xFFFFFFFF);
LOBYTE(v32) = 3;
if ( v29 >= 0x10 )
opus_repacketizer_destroy(lpMem[0]);
sub_9E4220((_DWORD *)(this - 12));
return sub_52F090(v23);
}
v32 = -1;
if ( v24 )
return (*(int (__stdcall **)(bool))(*v24 + 16))(v24 != v23);
return result;
}
其中的"result = (*(int (__thiscall **)(int, char , int, _DWORD))((_DWORD *)(this + 64) + 20))(this + 64, v30, 0x20000, 0);"即跳转到recv函数中,
而" (*(void (__thiscall )(_DWORD, char *, int, LPVOID *))((_DWORD **)(this + 8) + 24))(
*(_DWORD *)(this + 8),"这一行,即进入以下函数中执行:
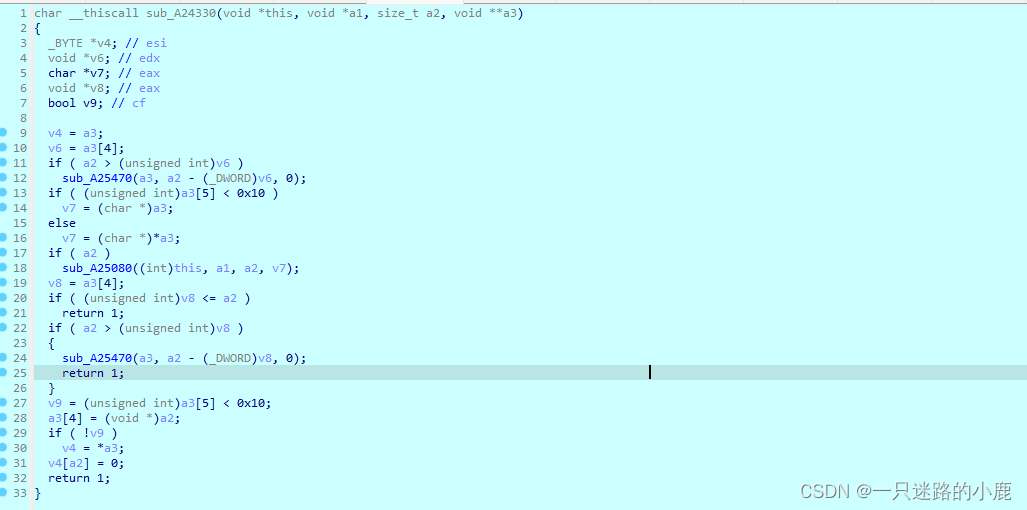
通过在接收数据的缓冲区地址中设置数据读写断点,发现最终程序经过多次跳转,进入如下函数:
_DWORD *__cdecl sub_7B4CB0(_DWORD *a1, unsigned int a2, _BYTE *a3, _BYTE *a4)
{
_DWORD *result; // eax
int v5; // ecx
char v6; // bl
int v8; // esi
int v10; // ecx
int v11; // edx
int v12; // esi
int v13; // ebx
int v14; // ecx
int v15; // edx
int v16; // esi
int v17; // ebx
int v18; // ecx
int v19; // edx
int v20; // esi
int v21; // ebx
int v22; // ecx
int v23; // edx
int v24; // esi
int v25; // ebx
int v26; // ecx
int v27; // edx
int v28; // esi
int v29; // ebx
int v30; // ecx
int v31; // edx
int v32; // esi
int v33; // ebx
int v34; // ecx
int v35; // edx
int v36; // esi
int v37; // ebx
int v38; // edx
int v39; // ebx
int v40; // edx
int v41; // ebx
bool v42; // zf
int v43; // edx
int v44; // ebx
int v45; // edx
int v46; // ebx
int v47; // edx
int v48; // ebx
int v49; // edx
int v50; // ebx
int v51; // edx
int v52; // ebx
int v53; // edx
int v54; // ebx
int v55; // edx
int v56; // ebx
unsigned int v57; // [esp+14h] [ebp+4h]
int v58; // [esp+14h] [ebp+4h]
int v59; // [esp+14h] [ebp+4h]
int v60; // [esp+14h] [ebp+4h]
int v61; // [esp+14h] [ebp+4h]
int v62; // [esp+14h] [ebp+4h]
int v63; // [esp+14h] [ebp+4h]
int v64; // [esp+14h] [ebp+4h]
int v65; // [esp+14h] [ebp+4h]
result = a1;
v5 = *a1;
v6 = a2;
v8 = a1[1];
v57 = a2 >> 3;
if ( a2 >> 3 )
{
do
{
v10 = (unsigned __int8)(v5 + 1);
v11 = result[v10 + 2];
v12 = (unsigned __int8)(v11 + v8);
v13 = result[v12 + 2];
result[v10 + 2] = v13;
result[v12 + 2] = v11;
*a4 = *a3 ^ LOBYTE(result[(unsigned __int8)(v11 + v13) + 2]);
v14 = (unsigned __int8)(v10 + 1);
v15 = result[v14 + 2];
v16 = (unsigned __int8)(v15 + v12);
v17 = result[v16 + 2];
result[v14 + 2] = v17;
result[v16 + 2] = v15;
a4[1] = a3[1] ^ LOBYTE(result[(unsigned __int8)(v15 + v17) + 2]);
v18 = (unsigned __int8)(v14 + 1);
v19 = result[v18 + 2];
v20 = (unsigned __int8)(v19 + v16);
v21 = result[v20 + 2];
result[v18 + 2] = v21;
result[v20 + 2] = v19;
a4[2] = a3[2] ^ LOBYTE(result[(unsigned __int8)(v19 + v21) + 2]);
v22 = (unsigned __int8)(v18 + 1);
v23 = result[v22 + 2];
v24 = (unsigned __int8)(v23 + v20);
v25 = result[v24 + 2];
result[v22 + 2] = v25;
result[v24 + 2] = v23;
a4[3] = a3[3] ^ LOBYTE(result[(unsigned __int8)(v23 + v25) + 2]);
v26 = (unsigned __int8)(v22 + 1);
v27 = result[v26 + 2];
v28 = (unsigned __int8)(v27 + v24);
v29 = result[v28 + 2];
result[v26 + 2] = v29;
result[v28 + 2] = v27;
a4[4] = a3[4] ^ LOBYTE(result[(unsigned __int8)(v27 + v29) + 2]);
v30 = (unsigned __int8)(v26 + 1);
v31 = result[v30 + 2];
v32 = (unsigned __int8)(v31 + v28);
v33 = result[v32 + 2];
result[v30 + 2] = v33;
result[v32 + 2] = v31;
v34 = (unsigned __int8)(v30 + 1);
a4[5] = a3[5] ^ LOBYTE(result[(unsigned __int8)(v31 + v33) + 2]);
v35 = result[v34 + 2];
v36 = (unsigned __int8)(v35 + v32);
v37 = result[v36 + 2];
result[v34 + 2] = v37;
result[v36 + 2] = v35;
a4[6] = a3[6] ^ LOBYTE(result[(unsigned __int8)(v35 + v37) + 2]);
v5 = (unsigned __int8)(v34 + 1);
v38 = result[v5 + 2];
v8 = (unsigned __int8)(v38 + v36);
v39 = result[v8 + 2];
result[v5 + 2] = v39;
result[v8 + 2] = v38;
LOBYTE(v38) = a3[7] ^ LOBYTE(result[(unsigned __int8)(v38 + v39) + 2]);
a3 += 8;
a4[7] = v38;
a4 += 8;
--v57;
}
while ( v57 );
v6 = a2;
}
v58 = v6 & 7;
if ( (v6 & 7) != 0 )
{
v5 = (unsigned __int8)(v5 + 1);
v40 = result[v5 + 2];
v8 = (unsigned __int8)(v40 + v8);
v41 = result[v8 + 2];
result[v5 + 2] = v41;
result[v8 + 2] = v40;
v42 = v58 == 1;
v59 = v58 - 1;
for ( *a4 = *a3 ^ LOBYTE(result[(unsigned __int8)(v40 + v41) + 2]);
!v42;
*a4 = *a3 ^ LOBYTE(result[(unsigned __int8)(v55 + v56) + 2]) )
{
v5 = (unsigned __int8)(v5 + 1);
v43 = result[v5 + 2];
v8 = (unsigned __int8)(v43 + v8);
v44 = result[v8 + 2];
result[v5 + 2] = v44;
result[v8 + 2] = v43;
v42 = v59 == 1;
v60 = v59 - 1;
a4[1] = a3[1] ^ LOBYTE(result[(unsigned __int8)(v43 + v44) + 2]);
if ( v42 )
break;
v5 = (unsigned __int8)(v5 + 1);
v45 = result[v5 + 2];
v8 = (unsigned __int8)(v45 + v8);
v46 = result[v8 + 2];
result[v5 + 2] = v46;
result[v8 + 2] = v45;
v42 = v60 == 1;
v61 = v60 - 1;
a4[2] = a3[2] ^ LOBYTE(result[(unsigned __int8)(v45 + v46) + 2]);
if ( v42 )
break;
v5 = (unsigned __int8)(v5 + 1);
v47 = result[v5 + 2];
v8 = (unsigned __int8)(v47 + v8);
v48 = result[v8 + 2];
result[v5 + 2] = v48;
result[v8 + 2] = v47;
v42 = v61 == 1;
v62 = v61 - 1;
a4[3] = a3[3] ^ LOBYTE(result[(unsigned __int8)(v47 + v48) + 2]);
if ( v42 )
break;
v5 = (unsigned __int8)(v5 + 1);
v49 = result[v5 + 2];
v8 = (unsigned __int8)(v49 + v8);
v50 = result[v8 + 2];
result[v5 + 2] = v50;
result[v8 + 2] = v49;
v42 = v62 == 1;
v63 = v62 - 1;
a4[4] = a3[4] ^ LOBYTE(result[(unsigned __int8)(v49 + v50) + 2]);
if ( v42 )
break;
v5 = (unsigned __int8)(v5 + 1);
v51 = result[v5 + 2];
v8 = (unsigned __int8)(v51 + v8);
v52 = result[v8 + 2];
result[v5 + 2] = v52;
result[v8 + 2] = v51;
v42 = v63 == 1;
v64 = v63 - 1;
a4[5] = a3[5] ^ LOBYTE(result[(unsigned __int8)(v51 + v52) + 2]);
if ( v42 )
break;
v5 = (unsigned __int8)(v5 + 1);
v53 = result[v5 + 2];
v8 = (unsigned __int8)(v53 + v8);
v54 = result[v8 + 2];
result[v5 + 2] = v54;
result[v8 + 2] = v53;
v42 = v64 == 1;
v65 = v64 - 1;
a4[6] = a3[6] ^ LOBYTE(result[(unsigned __int8)(v53 + v54) + 2]);
if ( v42 )
break;
v5 = (unsigned __int8)(v5 + 1);
v55 = result[v5 + 2];
v8 = (unsigned __int8)(v55 + v8);
v56 = result[v8 + 2];
result[v5 + 2] = v56;
result[v8 + 2] = v55;
v42 = v65 == 1;
v59 = v65 - 1;
}
}
result[1] = v8;
*result = v5;
return result;
}
至此,我们以比较大的把握猜测,加解密函数算法是一个rc4算法。我们知道,rc4函数需要一个初始化密钥,于是在进入加解密函数之前设置断点,我在内存中找到了这个密钥,并手动抄了出来。初始的密钥如下:
const int DecryptKey[260] =
{
0x00,0x00,0x34,0x6a,
0x81,0xD4,0xEA,0x47,
0xBC,0xC1,0x24,0xCA,
0x7B,0x19,0x70,0x2F,
0x1A,0x2A,0x68,0x62,
0xB7,0x4E,0xFB,0x53,
0x50,0x04,0x3A,0xD3,
0x48,0xDD,0x71,0x4D,
0x32,0x77,0x3F,0xEB,
0x55,0x02,0x14,0xB6,
0x93,0xA1,0xAB,0x03,
0x11,0x8F,0xF1,0x57,
0xB1,0xEE,0x52,0xB2,
0xAC,0x7A,0xAE,0x06,
0x86,0xF3,0x82,0xAA,
0xBD,0x85,0xF7,0xD9,
0x22,0xB0,0x8E,0x8A,
0x79,0xF4,0x6C,0xE7,
0xA4,0x9F,0xE3,0x96,
0xFC,0x7C,0xBA,0x2C,
0x4C,0xA3,0x80,0x98,
0x65,0x5E,0xE6,0xAF,
0xCB,0x58,0x67,0x1C,
0x08,0x4F,0x3C,0x44,
0xC9,0x6B,0xE4,0x7E,
0x1E,0x3D,0xE8,0xA6,
0xBB,0x5F,0x6F,0x59,
0x97,0x9E,0xB4,0x30,
0x2D,0x2B,0xF2,0x6E,
0x0A,0xA7,0xE9,0x5D,
0x29,0x5C,0x33,0xEF,
0x91,0xE5,0x39,0x36,
0x17,0xDF,0x31,0x45,
0x8D,0x5B,0x05,0xF0,
0xC8,0x09,0xA5,0xF9,
0x84,0xC7,0x1B,0xB5,
0xC6,0x9B,0xE2,0xC5,
0x89,0xE0,0x9A,0x27,
0xC4,0x40,0x0D,0x20,
0x66,0x7F,0xA9,0xC3,
0x07,0xB3,0x2E,0x49,
0xFA,0xD5,0xAD,0xE1,
0x83,0x6D,0x0E,0x43,
0x28,0x78,0x42,0x64,
0x8B,0x16,0x74,0x88,
0xD8,0x1F,0xA0,0x3E,
0x63,0x60,0xFD,0xA8,
0xD7,0x76,0x72,0x18,
0xDC,0x56,0xFE,0xD0,
0x90,0xD1,0x9D,0xDB,
0x94,0x8C,0xDA,0xDE,
0xBE,0xCD,0xCF,0xC2,
0x1D,0x51,0xCE,0xBF,
0x73,0x35,0x00,0x92,
0x7D,0xC0,0x12,0x69,
0x26,0x38,0x4B,0xFF,
0xED,0x9C,0x13,0xF5,
0x15,0xD2,0xEC,0xF8,
0xB9,0x46,0xA2,0x41,
0xF6,0x99,0x75,0x95,
0x87,0x23,0x10,0x61,
0x25,0xB8,0x37,0xCC,
0x0C,0xD6,0x01,0x0F,
0x21,0x4A,0x54,0x3B,
0x5A,0x0B,0x00,0x00
};
现在还有一个问题,因为我不知道这个初始化密钥来自何处,所以就面临一个问题,这个密钥是多变的吗?是否是客户指纹产生的动态密钥呢?如果是的话,那么这个密钥将毫无用处。另外,发送函数也是这样加解密的吗?于是我注册了两个账号,最终经过验证,发现该密钥是都一样的!
忘了说一声,该软件的名字叫做某网的某信,版本号4.4.1280。

因为没法上传工程文件和wireshark的抓包文件,故所有测试代码这在这里,如下所示:
#include <Windows.h>
#include <string>
#include <stdio.h>
#include <windows.h>
#include <cstdlib>
#include <iostream>
#include <vector>
#include <string>
#include <algorithm>
#include "zlib.h"
#pragma comment(lib,"zlib.lib")
using namespace std;
#define _DWORD DWORD
#define _BYTE BYTE
#define YX_KEY_LEN 260
const int constDecryptKey[YX_KEY_LEN] =
{
0x00,0x00,0x34,0x6a,
0x81,0xD4,0xEA,0x47,
0xBC,0xC1,0x24,0xCA,
0x7B,0x19,0x70,0x2F,
0x1A,0x2A,0x68,0x62,
0xB7,0x4E,0xFB,0x53,
0x50,0x04,0x3A,0xD3,
0x48,0xDD,0x71,0x4D,
0x32,0x77,0x3F,0xEB,
0x55,0x02,0x14,0xB6,
0x93,0xA1,0xAB,0x03,
0x11,0x8F,0xF1,0x57,
0xB1,0xEE,0x52,0xB2,
0xAC,0x7A,0xAE,0x06,
0x86,0xF3,0x82,0xAA,
0xBD,0x85,0xF7,0xD9,
0x22,0xB0,0x8E,0x8A,
0x79,0xF4,0x6C,0xE7,
0xA4,0x9F,0xE3,0x96,
0xFC,0x7C,0xBA,0x2C,
0x4C,0xA3,0x80,0x98,
0x65,0x5E,0xE6,0xAF,
0xCB,0x58,0x67,0x1C,
0x08,0x4F,0x3C,0x44,
0xC9,0x6B,0xE4,0x7E,
0x1E,0x3D,0xE8,0xA6,
0xBB,0x5F,0x6F,0x59,
0x97,0x9E,0xB4,0x30,
0x2D,0x2B,0xF2,0x6E,
0x0A,0xA7,0xE9,0x5D,
0x29,0x5C,0x33,0xEF,
0x91,0xE5,0x39,0x36,
0x17,0xDF,0x31,0x45,
0x8D,0x5B,0x05,0xF0,
0xC8,0x09,0xA5,0xF9,
0x84,0xC7,0x1B,0xB5,
0xC6,0x9B,0xE2,0xC5,
0x89,0xE0,0x9A,0x27,
0xC4,0x40,0x0D,0x20,
0x66,0x7F,0xA9,0xC3,
0x07,0xB3,0x2E,0x49,
0xFA,0xD5,0xAD,0xE1,
0x83,0x6D,0x0E,0x43,
0x28,0x78,0x42,0x64,
0x8B,0x16,0x74,0x88,
0xD8,0x1F,0xA0,0x3E,
0x63,0x60,0xFD,0xA8,
0xD7,0x76,0x72,0x18,
0xDC,0x56,0xFE,0xD0,
0x90,0xD1,0x9D,0xDB,
0x94,0x8C,0xDA,0xDE,
0xBE,0xCD,0xCF,0xC2,
0x1D,0x51,0xCE,0xBF,
0x73,0x35,0x00,0x92,
0x7D,0xC0,0x12,0x69,
0x26,0x38,0x4B,0xFF,
0xED,0x9C,0x13,0xF5,
0x15,0xD2,0xEC,0xF8,
0xB9,0x46,0xA2,0x41,
0xF6,0x99,0x75,0x95,
0x87,0x23,0x10,0x61,
0x25,0xB8,0x37,0xCC,
0x0C,0xD6,0x01,0x0F,
0x21,0x4A,0x54,0x3B,
0x5A,0x0B,0x00,0x00
};
int Mygzdecompress(BYTE* zdata, ULONG nzdata, BYTE* data, ULONG* ndata)
{
int err = 0;
z_stream d_stream = { 0 }; /* decompression stream */
static char dummy_head[2] =
{
0x8 + 0x7 * 0x10,
(((0x8 + 0x7 * 0x10) * 0x100 + 30) / 31 * 31) & 0xFF,
};
d_stream.zalloc = (alloc_func)0;
d_stream.zfree = (free_func)0;
d_stream.opaque = (voidpf)0;
d_stream.next_in = zdata;
d_stream.avail_in = 0;
d_stream.next_out = data;
if (inflateInit2(&d_stream, -MAX_WBITS) != Z_OK) return -1;
//if(inflateInit2(&d_stream, 47) != Z_OK) return -1;
while (d_stream.total_out < *ndata && d_stream.total_in < nzdata) {
d_stream.avail_in = d_stream.avail_out = 1; /* force small buffers */
if ((err = inflate(&d_stream, Z_NO_FLUSH)) == Z_STREAM_END) break;
if (err != Z_OK)
{
if (err == Z_DATA_ERROR)
{
d_stream.next_in = (Bytef*)dummy_head;
d_stream.avail_in = sizeof(dummy_head);
if ((err = inflate(&d_stream, Z_NO_FLUSH)) != Z_OK)
{
return -1;
}
}
else return -1;
}
}
if (inflateEnd(&d_stream) != Z_OK) return -1;
*ndata = d_stream.total_out;
return 0;
}
int zdecompress(BYTE* zdata, ULONG nzdata, BYTE* data, ULONG* ndata)
{
int err = 0;
z_stream d_stream; /* decompression stream */
d_stream.zalloc = (alloc_func)0;
d_stream.zfree = (free_func)0;
d_stream.opaque = (voidpf)0;
d_stream.next_in = zdata;
d_stream.avail_in = 0;
d_stream.next_out = data;
if (inflateInit(&d_stream) != Z_OK) return -1;
while (d_stream.total_out < *ndata && d_stream.total_in < nzdata) {
d_stream.avail_in = d_stream.avail_out = 1; /* force small buffers */
if ((err = inflate(&d_stream, Z_NO_FLUSH)) == Z_STREAM_END) break;
if (err != Z_OK) return -1;
}
if (inflateEnd(&d_stream) != Z_OK) return -1;
*ndata = d_stream.total_out;
return 0;
}
int sub_67FEF0(int a1, unsigned int a2, int a3, int a4)
{
int result; // eax@1
int v5; // ecx@1
char v6; // bl@1
int v7; // ebp@1
int v8; // edi@1
int v9; // esi@1
int v10; // ecx@2
int v11; // edx@2
int v12; // esi@2
int v13; // ebx@2
int v14; // ecx@2
int v15; // edx@2
int v16; // esi@2
int v17; // ebx@2
int v18; // ecx@2
int v19; // edx@2
int v20; // esi@2
int v21; // ebx@2
int v22; // ecx@2
int v23; // edx@2
int v24; // esi@2
int v25; // ebx@2
int v26; // ecx@2
int v27; // edx@2
int v28; // esi@2
int v29; // ebx@2
int v30; // ecx@2
int v31; // edx@2
int v32; // esi@2
int v33; // ebx@2
int v34; // ecx@2
int v35; // edx@2
int v36; // esi@2
int v37; // ebx@2
int v38; // edx@2
int v39; // ebx@2
int v41; // edx@5
int v42; // ebx@5
char v43; // zf@5
int v44; // edx@6
int v45; // ebx@6
char v46; // zf@6
int v47; // edx@7
int v48; // ebx@7
char v49; // zf@7
int v50; // edx@8
int v51; // ebx@8
char v52; // zf@8
int v53; // edx@9
int v54; // ebx@9
char v55; // zf@9
int v56; // edx@10
int v57; // ebx@10
char v58; // zf@10
int v59; // edx@11
int v60; // ebx@11
char v61; // zf@11
int v62; // edx@12
int v63; // ebx@12
char v64; // zf@12
unsigned int v65; // [sp+14h] [bp+4h]@1
int v66; // [sp+14h] [bp+4h]@4
int v67; // [sp+14h] [bp+4h]@5
int v68; // [sp+14h] [bp+4h]@6
int v69; // [sp+14h] [bp+4h]@7
int v70; // [sp+14h] [bp+4h]@8
int v71; // [sp+14h] [bp+4h]@9
int v72; // [sp+14h] [bp+4h]@10
int v73; // [sp+14h] [bp+4h]@11
result = a1;
v5 = *(_DWORD*)a1;
v6 = a2;
v7 = a3;
v9 = *(_DWORD*)(a1 + 4);
v8 = a4;
v65 = a2 >> 3;
if (a2 >> 3)
{
do
{
v10 = (v5 + 1) & 0xFF;
v11 = *(_DWORD*)(result + 4 * v10 + 8);
v12 = (v11 + v9) & 0xFF;
v13 = *(_DWORD*)(result + 4 * v12 + 8);
*(_DWORD*)(result + 4 * v10 + 8) = v13;
*(_DWORD*)(result + 4 * v12 + 8) = v11;
*(_BYTE*)v8 = *(_BYTE*)v7 ^ *(_BYTE*)(result + 4 * ((v11 + v13) & 0xFF) + 8);
v14 = (v10 + 1) & 0xFF;
v15 = *(_DWORD*)(result + 4 * v14 + 8);
v16 = (v15 + v12) & 0xFF;
v17 = *(_DWORD*)(result + 4 * v16 + 8);
*(_DWORD*)(result + 4 * v14 + 8) = v17;
*(_DWORD*)(result + 4 * v16 + 8) = v15;
*(_BYTE*)(v8 + 1) = *(_BYTE*)(v7 + 1) ^ *(_BYTE*)(result + 4 * ((v15 + v17) & 0xFF) + 8);
v18 = (v14 + 1) & 0xFF;
v19 = *(_DWORD*)(result + 4 * v18 + 8);
v20 = (v19 + v16) & 0xFF;
v21 = *(_DWORD*)(result + 4 * v20 + 8);
*(_DWORD*)(result + 4 * v18 + 8) = v21;
*(_DWORD*)(result + 4 * v20 + 8) = v19;
*(_BYTE*)(v8 + 2) = *(_BYTE*)(v7 + 2) ^ *(_BYTE*)(result + 4 * ((v19 + v21) & 0xFF) + 8);
v22 = (v18 + 1) & 0xFF;
v23 = *(_DWORD*)(result + 4 * v22 + 8);
v24 = (v23 + v20) & 0xFF;
v25 = *(_DWORD*)(result + 4 * v24 + 8);
*(_DWORD*)(result + 4 * v22 + 8) = v25;
*(_DWORD*)(result + 4 * v24 + 8) = v23;
*(_BYTE*)(v8 + 3) = *(_BYTE*)(v7 + 3) ^ *(_BYTE*)(result + 4 * ((v23 + v25) & 0xFF) + 8);
v26 = (v22 + 1) & 0xFF;
v27 = *(_DWORD*)(result + 4 * v26 + 8);
v28 = (v27 + v24) & 0xFF;
v29 = *(_DWORD*)(result + 4 * v28 + 8);
*(_DWORD*)(result + 4 * v26 + 8) = v29;
*(_DWORD*)(result + 4 * v28 + 8) = v27;
*(_BYTE*)(v8 + 4) = *(_BYTE*)(v7 + 4) ^ *(_BYTE*)(result + 4 * ((v27 + v29) & 0xFF) + 8);
v30 = (v26 + 1) & 0xFF;
v31 = *(_DWORD*)(result + 4 * v30 + 8);
v32 = (v31 + v28) & 0xFF;
v33 = *(_DWORD*)(result + 4 * v32 + 8);
*(_DWORD*)(result + 4 * v30 + 8) = v33;
*(_DWORD*)(result + 4 * v32 + 8) = v31;
v34 = (v30 + 1) & 0xFF;
*(_BYTE*)(v8 + 5) = *(_BYTE*)(v7 + 5) ^ *(_BYTE*)(result + 4 * ((v31 + v33) & 0xFF) + 8);
v35 = *(_DWORD*)(result + 4 * v34 + 8);
v36 = (v35 + v32) & 0xFF;
v37 = *(_DWORD*)(result + 4 * v36 + 8);
*(_DWORD*)(result + 4 * v34 + 8) = v37;
*(_DWORD*)(result + 4 * v36 + 8) = v35;
*(_BYTE*)(v8 + 6) = *(_BYTE*)(v7 + 6) ^ *(_BYTE*)(result + 4 * ((v35 + v37) & 0xFF) + 8);
v5 = (v34 + 1) & 0xFF;
v38 = *(_DWORD*)(result + 4 * v5 + 8);
v9 = (v38 + v36) & 0xFF;
v39 = *(_DWORD*)(result + 4 * v9 + 8);
*(_DWORD*)(result + 4 * v5 + 8) = v39;
*(_DWORD*)(result + 4 * v9 + 8) = v38;
v38 = *(_BYTE*)(v7 + 7) ^ *(_BYTE*)(result + 4 * ((v38 + v39) & 0xFF) + 8);
v38 &= 0xff;
v7 += 8;
*(_BYTE*)(v8 + 7) = v38;
v8 += 8;
} while (v65-- != 1);
v6 = a2;
}
v66 = v6 & 7;
if (v6 & 7)
{
v5 = (v5 + 1) & 0xFF;
v41 = *(_DWORD*)(result + 4 * v5 + 8);
v9 = (v41 + v9) & 0xFF;
v42 = *(_DWORD*)(result + 4 * v9 + 8);
*(_DWORD*)(result + 4 * v5 + 8) = v42;
*(_DWORD*)(result + 4 * v9 + 8) = v41;
v43 = v66 == 1;
v67 = v66 - 1;
*(_BYTE*)v8 = *(_BYTE*)v7 ^ *(_BYTE*)(result + 4 * ((v41 + v42) & 0xFF) + 8);
if (!v43)
{
do
{
v5 = (v5 + 1) & 0xFF;
v44 = *(_DWORD*)(result + 4 * v5 + 8);
v9 = (v44 + v9) & 0xFF;
v45 = *(_DWORD*)(result + 4 * v9 + 8);
*(_DWORD*)(result + 4 * v5 + 8) = v45;
*(_DWORD*)(result + 4 * v9 + 8) = v44;
v46 = v67 == 1;
v68 = v67 - 1;
*(_BYTE*)(v8 + 1) = *(_BYTE*)(v7 + 1) ^ *(_BYTE*)(result + 4 * ((v44 + v45) & 0xFF) + 8);
if (v46)
break;
v5 = (v5 + 1) & 0xFF;
v47 = *(_DWORD*)(result + 4 * v5 + 8);
v9 = (v47 + v9) & 0xFF;
v48 = *(_DWORD*)(result + 4 * v9 + 8);
*(_DWORD*)(result + 4 * v5 + 8) = v48;
*(_DWORD*)(result + 4 * v9 + 8) = v47;
v49 = v68 == 1;
v69 = v68 - 1;
*(_BYTE*)(v8 + 2) = *(_BYTE*)(v7 + 2) ^ *(_BYTE*)(result + 4 * ((v47 + v48) & 0xFF) + 8);
if (v49)
break;
v5 = (v5 + 1) & 0xFF;
v50 = *(_DWORD*)(result + 4 * v5 + 8);
v9 = (v50 + v9) & 0xFF;
v51 = *(_DWORD*)(result + 4 * v9 + 8);
*(_DWORD*)(result + 4 * v5 + 8) = v51;
*(_DWORD*)(result + 4 * v9 + 8) = v50;
v52 = v69 == 1;
v70 = v69 - 1;
*(_BYTE*)(v8 + 3) = *(_BYTE*)(v7 + 3) ^ *(_BYTE*)(result + 4 * ((v50 + v51) & 0xFF) + 8);
if (v52)
break;
v5 = (v5 + 1) & 0xFF;
v53 = *(_DWORD*)(result + 4 * v5 + 8);
v9 = (v53 + v9) & 0xFF;
v54 = *(_DWORD*)(result + 4 * v9 + 8);
*(_DWORD*)(result + 4 * v5 + 8) = v54;
*(_DWORD*)(result + 4 * v9 + 8) = v53;
v55 = v70 == 1;
v71 = v70 - 1;
*(_BYTE*)(v8 + 4) = *(_BYTE*)(v7 + 4) ^ *(_BYTE*)(result + 4 * ((v53 + v54) & 0xFF) + 8);
if (v55)
break;
v5 = (v5 + 1) & 0xFF;
v56 = *(_DWORD*)(result + 4 * v5 + 8);
v9 = (v56 + v9) & 0xFF;
v57 = *(_DWORD*)(result + 4 * v9 + 8);
*(_DWORD*)(result + 4 * v5 + 8) = v57;
*(_DWORD*)(result + 4 * v9 + 8) = v56;
v58 = v71 == 1;
v72 = v71 - 1;
*(_BYTE*)(v8 + 5) = *(_BYTE*)(v7 + 5) ^ *(_BYTE*)(result + 4 * ((v56 + v57) & 0xFF) + 8);
if (v58)
break;
v5 = (v5 + 1) & 0xFF;
v59 = *(_DWORD*)(result + 4 * v5 + 8);
v9 = (v59 + v9) & 0xFF;
v60 = *(_DWORD*)(result + 4 * v9 + 8);
*(_DWORD*)(result + 4 * v5 + 8) = v60;
*(_DWORD*)(result + 4 * v9 + 8) = v59;
v61 = v72 == 1;
v73 = v72 - 1;
*(_BYTE*)(v8 + 6) = *(_BYTE*)(v7 + 6) ^ *(_BYTE*)(result + 4 * ((v59 + v60) & 0xFF) + 8);
if (v61)
break;
v5 = (v5 + 1) & 0xFF;
v62 = *(_DWORD*)(result + 4 * v5 + 8);
v9 = (v62 + v9) & 0xFF;
v63 = *(_DWORD*)(result + 4 * v9 + 8);
*(_DWORD*)(result + 4 * v5 + 8) = v63;
*(_DWORD*)(result + 4 * v9 + 8) = v62;
v64 = v73 == 1;
v67 = v73 - 1;
*(_BYTE*)v8 = *(_BYTE*)v7 ^ *(_BYTE*)(result + 4 * ((v62 + v63) & 0xFF) + 8);
} while (!v64);
}
}
*(_DWORD*)(result + 4) = v9;
*(_DWORD*)result = v5;
return result;
}
char* FindMemory(char Flag[], int FlagLen, char Address[], int Offset)
{
for (int Cnt = 0; Cnt < Offset; Cnt++)
{
if (memcmp(Flag, Address + Cnt, FlagLen) == 0)
{
return Address + Cnt;
}
}
return FALSE;
}
unsigned int m_DecryptKey[YX_KEY_LEN];
int main(int argc, char** argv)
{
int result = 0;
char buf[0x1000];
char* decodebuf = new char[0x100000];
DWORD decodelen = 0x100000;
int zipsize = 0;
char* pos = 0;
memmove(m_DecryptKey, constDecryptKey, YX_KEY_LEN * sizeof(int));
//#define SEND_PACKET
#ifdef SEND_PACKET
const char data1[] =
"\x98\x12\x07\x55\x58\x57\xa9\x41\xd3\x01\xf7\x38\xcc\xab\xc3\xb6"
// "\x93\x05\x50\x0a\x00\x00\x0d\xc8\x00\x00\x00\x00\x00\x00\x00\x00" \
// "\x00\x00\x00\x00\x00\x06\xe4\x7d\x33\xdf\xc0\x63\x0e\x7e\xf7\x5e" \
// "\x2e\xdf\xf8\x60\xab\x53\x59\x9b\x44\xc9\x4c\x79\x64\x7e\x44\x2d" \
// "\x4a\x5e\x6c\xc6\xdf\x01\x79\xf6\x67\x91\x86\x02\x4f\x55\x9e\x01" \
// "\x34\xae\x37\xc6\x3c\xa9\x54\xd3\x6a\x33\x20\xc9\xf0\xc0\x8a\x70" \
// "\xcf\x05\x3f\x1b\x45\xc1\xe4\xb7\x01\x24\xb3\x2f\x87\xb0\x36\xf3" \
// "\x3d\x99\xba\xd7\x0f\x8c\xdf\xe1\xf0\x67\xe5\x2b\x81\x8c\x4c\xc4" \
// "\xa2\x67\xe2\xf0\xde\xd5\x1a\x21\xf7\x11\x8f\xde\xd8\x97\x5f\xa9" \
// "\x80\x07\xe1\x56\x48\x99\x1e\xc0\x15\x05\xd1\x28\xdc\xbe\x21\x6f" \
// "\x46\x48\x2a\xb4\x09\x5e\x78\x4b\x77\x5b\x28\x5c\x79\xc2\x62\x0a" \
// "\xfa\x83\x54\x3d\x85\x73\x04\xe8\x03\xc0\x68\x2e\x37\x8d\xee\x38" \
// "\x1d\x9e\x01\xfe\xb7\xbc\x0f\x49\xd4\x83\x57\xbe\xb1\xe8\x04\xf1" \
// "\x5d\x4f\x6f\x01\x04\xd3\xd6\x50\x41\x45\x10\xeb\x11\x0e\xfe\xdf" \
// "\x58\xe6\xe0\xa3\xab\x0b\xdd\xdb\xac\xf3\xb6\xdc\x17\x6a\xf7\xa0" \
// "\x0c\x2a\x4e\xc7\x67\x39\x1d\x93\x3c\xde\x59\x33\xf4\xc7\xef\x64" \
// "\x18\x0f\x22\xc4\x1e\xad\xd3\x06\xb1\x99\x4f\x9d\x62\x6b\xb4\xba" \
// "\xa6\x6e\x44\x63\xea\xb1\x1d\xb4\x28\xc5\x27\xca\xb1\x9a\x00\xbe" \
// "\x51\x03\x66\x79\x59\x1f\xb7\xca\xa6\xd8\x04\x30\x64\xc6\x3c\x76" \
// "\x57\xee\x37\x93\x2b\x3b\x50\xfd\x89\x6e\x73\x0e\x52\xa9\xf4\x87" \
// "\xed\xd5\x8a\x63\xb6\xdd\xfe\x55\xdb\x1f\x52\xa3\xc4\xac\x3c\xb1" \
// "\x70\x99\x4d\x94\x21\x51\x18\x80\x5c\xd9\x9b\x50\x85\xd0\xb2\x0c" \
// "\x51\x04\x80\x04\x43\xd1\xbc\xee\x69\x2b\x91\x4a\x64\xcb\x0e\xfc" \
// "\xda\xa7\x47\x9a\xcc\x86\x39\x71\xe9\x28\x8b\x31\x09\xba\x9a\xa3" \
// "\x50\xe6\x84\xbc\xd1\x38\x1e\x3e\xb5\x72\xad\xe4\xfa\xe0\x31\xdc" \
// "\xbf\x27\x44\x02\x53\x3a\xf4\xe4\x60\x8c\x93\xfb\x5a\x83\xf4\x24" \
// "\x1e\xe7\xcd\xc7\x95\x5a\x8f\x66\x40\x96\xae\x9a\x1e\xe6\x4a\x0b" \
// "\x72\xde\xf4\xcc\xd9\x55\xa6\x7e\x19\xc3\xaa\x67\x1d\x24\xd9\x65" \
// "\x47\xdf\x40\x82\xe8\xac\x19\xd4\x2b\x38\x2f\xd3\xa3\x64\x38\xe5" \
// "\xba\xac\x01\x1e\xf6\xf7\x4e\xfe\xf6\xee\xa5\x44\x39\x0d\x35\xe6" \
// "\x39\xc2\xcf\xf8\xd8\xdb\xa5\x88\x18\x67\xef\x25\x26\xdf\xf0\x34" \
// "\xf0\x3f\xad\xfc\xe0\xa8\x91\xee\xef\x03\x59\x9b\x97\xcc\xde\xd6" \
// "\x44\xed\xa3\xe1\x35\xda\xa8\x49\xaf\xa7\xc3\x71\xc8\x54\xff\xed" \
// "\x20\xdc\xf0\x80\xe7\x92\x5c\xf1\xae\xe7\x76\x2e\x45\x00\x9b\x71" \
// "\xd3\x9e\xee\xe8\xfb\x5e\x87\xf2\x3f\xfd\x06\xc1\xbc\x51\x25\x9e" \
// "\xc6\xd8\x8b\x1a\x48\x7d\xae\xc7\x1a\xa7\xbb\xa3\x4d\xeb\x22\x32" \
// "\xca\x6c\x72\xa0\xc3\xd3\xfe\x17\x8c\x49\x71\xb9\x6c\xf6\x6d\x1b" \
// "\x8d\x3e\x3e\x2e\x63\xb0\x7d\x63\xe6\xec\x96\x27\xed\x8d\xf7\x23" \
// "\x39\xbe\xb4\x15\x3d\x71\x00\xbd\xab\xd4\xbc\x5c\x53\x8c\x6a\x56" \
// "\xb6\xcc\xd9\x7f\xe6\x7e\xfa\x01\x3f\xa1\xfa\x78\x71\x16\xc4\x24" \
// "\x1a\x89\xe8\x9d\xe9\x43\xc1\xd1\x1b\xf6\x1c\x19\x95\xfe\x53\x4a" \
// "\x94\x9f\xbc\xdb\x82\x7f\xa7\x4b\x1d\x89\x55\x54\x32\x75\xf8\xb7" \
// "\x97\x07\x77\x02\x29"
;
int datasize = sizeof(data1) - 1;
sub_67FEF0((int)m_DecryptKey, datasize, (int)data1, (int)buf);
char data2[] =
"\x1c\x0e\x41\x47\xb4\x39\xc9\xf2\xb7\xaf\x68\x11\x8c\x12\x90\xfb" \
"\x5f\x4b\xa4\x8d\x59\x25\xc2\xb6\x8e\x09\xd1\xe8\x39\xcd\x82\x70" \
"\x45\x9c\x3f\xaa\x83\xfc\x76\xfa\x62\x42\xc2\xa2\xcd\x05\x39\x5f" \
"\x72\xbb\x88\xfd\x7b\xc6\x7c\xe3\x29\xdb\x6d\xa5\x5a\xc5\x0d\xa3"
;
datasize = sizeof(data2) - 1;
sub_67FEF0((int)m_DecryptKey, datasize, (int)data2, (int)buf);
return TRUE;
#else
const char data1[] = "\x9f\x18\x1b\x57\x58\x5f\xa9\x41\xd3"
;
int datasize = sizeof(data1) - 1;
sub_67FEF0((int)m_DecryptKey, datasize, (int)data1, (int)buf);
char data2[] =
"\xce\xf6\x62\xcf\xaa\xc3\xbb\xeb\x53\x40\x44\xb4\x34\x01\xf2\xb7" \
"\xaf\x9e\xfd\x27\x10\x90\xfb\x57\x4b\x80\x8d\x6e\x5a\x7b\xc3\x89" \
"\x38\xac\x06\x54\x9a\xb5\x45\x71\xb1\x0b\x9c\xaa\x12\x1b\xfc\x06" \
"\x6b\x7b\xcf\x9c\x31\x5f\x39\x43\xde\xb6\xca\x4d\xf3\x1a\x8c\xf2" \
"\x24\xf1\x6f\x6a\xa0\x38\x92\xf8\x89\x7a\x31\x05\x07\xcd\x55\xf3" \
"\xbe\x06\xf5\xfa\xe7\x57\x18\xae\x32\x59\x2b\x19\x29\x2d\x6a\x06" \
"\x6d\x79\x11\x57\x2b\x52\xd6\x6a\x6f\xb4\x56\x12\x52\xc2\x06\x82" \
"\xd1\x2c\xbd\xbf\x43\xb1\x58\xac\x7f\x38\x83\xe0\xcd\xe1\xe2\xac" \
"\xcf\xc8\x60\x8b\x73\xc1\xa4\x7a\x72\x6d\x8a\x95\x75\xe0\xcd\xbb" \
"\xcb\x4a\x15\x29\x0d\x3f\xde\xe9\xf2\x0f\xeb\xa6\xbf\xe9\x6d\xd5" \
"\x21\xb2\xa5\x20\x98\x93\xb0\xa6\xec\xea\x01\x44\xf4\x04\xec\x16" \
"\x03\xac\x51\xc6\x87\x05\xf9\xb8\xed\xcd\x56\x33\xba\x8d\x83\x14" \
"\x92\x93\x5b\xa6\x31\x67\x90\x6b\x65\xba\xd6\x18\x7a\x5b\xfe\x2e\x4f"
;
datasize = sizeof(data2) - 1;
sub_67FEF0((int)m_DecryptKey, datasize, (int)data2, (int)buf);
char data3[] =
"\xe2\x2e\x08\xe3\xbe\x17\x97\xfc\x61\xf8\x95\xd0\x68\x8f\x7c\x9f" \
"\xb7\x10\x6c\xac"
;
datasize = sizeof(data3) - 1;
sub_67FEF0((int)m_DecryptKey, datasize, (int)data3, (int)buf);
char data4[] =
"\x3e\x0f\xf8\x86\x97\xca\x5d\x0d\x40\x1f\x03\x26\xb6\xa0\x1a\x91" \
"\x50\x9e\x42\x55\x85\xce\x4f\xe2\xb7\x4e\xdf\x7c\xb5\xd0\x27\xa1" \
"\x98\x4f\x3f\x5d\x34\xc1\xa6\xaf\xd8\x1f\xf8\x4c\x2e\xf8\xcc\x68" \
"\xe5\x32\x69\x81\x53\x74\x8c\x56\xee\x9a\x7c\xbc\x30\xad\x58\x5f" \
"\x30\x69\xd8\x78\x4c\x1c\x67\x9f\x8a\xdf\x61\x74\xf0\x6f\xcb\x06" \
"\x22\x8e\xb8\x12\x4e\xc6\xf8\xca\x8d\x76\xb4\xbe\x52\xa9\xc8\x01" \
"\x0c\x08\x5e\x45\x06\xad\xa4\x04\x97\x6c\xf2\x72\x97\x86\xb3\x1c" \
"\xec\x92\xd5\x96\x69\x38\x5d\x72\xa7\x24\x8d\xa6\x61\x86\x28\x03" \
"\xaf\xcc\x10\x8a\x5b\xfe\xa4\x2d\x5a\x5b\x40\x88\xfc\x93\xb3\x71" \
"\x23\x19\x35\xa9\x4c\xfe\xf9\x8f\x50\xc8\x12\x80\xfb\x97\x76\xe3" \
"\x0e\xbe\x2d\xf0\x40\xae\xe9\xd1\x11\x97\xe1\xea\x25\x96\x72\x98" \
"\xee\x9e\x9b\x19\x5e\x76\x95\x7d\x86\xe0\xe6\x8e\x99\xc2\x91\xc6" \
"\xd4\x3b\xb5\xcd\x07\x0c\x1c\x9b\x78\xd6\x52\x99\x4a\xfe\x53\x6b" \
"\xf9\x0d\xcf\xcc\xbb\x43\xe3\x98\x55\x9d\x9f\x20\xaf\x8c\xb5\x9b" \
"\x86\xbb\x6b\xef\xde\x35\x36\x69\x80\x38\x7c\x39\x41\x4a\x6f\x76" \
"\xea\xf1\x9a\x47\x31\xa0\xe9\x34\xbe\x8a\xa5\x92\x86\xb4\xf4\xf9" \
"\x56\x38\x3d\xc7\xa3\x90\x0c\x7a\x18\x0f\x10\x19\x4c\xef\x9e\xde" \
"\xda\x5f\x87\x3c\x78\x7b\x46\x66\xbd\x3b\x38\xcf\xfc\x70\x1f\x4d" \
"\xae\x32\xd5\x9c\x0c\x76\xec\xdf\x5c\x25\x3f\x1e\xb5\x94\x5a\x3a" \
"\x02\x73\x8b\xa1\x42\x46\xc2\x79\xa1\xea\xb0\xcf\xee\x7e\xe6\x2a" \
"\xac\xc2\x19\x49\x8a\xcb\x84\x3e\xab\xe7\x12\x09\x61\x80\x29\x00" \
"\x22\x9d\xfd\xc7\xed\x7e\xe1\xd0\xdd\xa4\x0b\xd5\xcf\xac\xb8\x20" \
"\xb0\x5b\x63\x0c\xbc\xa2\xd5\x68\x33\x95\x61\x0a\x27\x37\xb7\x3a" \
"\xb2\xd5\x3e\x6d\xbd\xa0\xdd\xfa\xa1\x88\x88\xc1\x2e\xdd\x7e\xe2" \
"\x56\xb4\xb3\x34\x06\x62\x54\x25\x33\x7a\x8b\x10\xc8\x8a\x90\xfb\xe3"
;
datasize = sizeof(data4) - 1;
sub_67FEF0((int)m_DecryptKey, datasize, (int)data4, (int)buf);
char data5[] =
"\x2a\x2c\xc7\x56\x8f\x7e\x74\x24\x28\x0b\x7f\xfd\xdf\xe7\x17\xd2" \
"\xa0\x14\x4d\x25\xfb\x1f\x53\xc4\x7d\x86\x02\x24\x9b\xf6\x38\x1d" \
"\x3e\x1d\xe4\x3b\x56\x42\x09\x9f\xfd\xe7\x3b\xab\x23\xb5\x13\xeb" \
"\x4e\x1c\x23\xe0\xc9\x4b\x7a\x57\x96\xfa\x6f\x38\xe3\x29\x32\xbb" \
"\xbe\x22\xa2\x98\x40\xd3\x91\xba\x9d\x7c\xa3\xbc\x5b\xdc\xee\x1b" \
"\x3f\x4e\x6e\x19\x0d\x75\x39\x1e\x4b\x15\x39\xf1\xbc\x27\x02\x13" \
"\x15\x25\xe4\x2f\x99\x10\xd7\x8d\xe6\x99\x7b\x8f\xf1\xa0\x8c\x17" \
"\x91\xe4\x3d\x08\x9e\x64\x0c\xe2\x4b\x38\xd7\xe6\x0a\x54\xb3\xf1" \
"\x6c\xa6\x1a\x42\x15\x96\x4a\xfb\xc6\xaf\x5f\x91\x32\xb9\xd9\xf6" \
"\x85\x51\xe1\xb3\x72\x18\x41\x5d\x42\xcb\x4a\x1f\x90\x52\x05\x0d" \
"\x9d\xe8\xfe\x1d\x71\xfb\x9f\x92\xeb\x58\x54\xcc\x33\xa4\x14\x06" \
"\x24\xeb\x38\x80\x3f\x73\x40\x22\xd2\xe8\x47\xd8\x7c\xa0\x42\x36" \
"\x19\x5f\xbf\xbc\x63\x3b\x9b\xf1\x8d\x88\x60\x50\x5f\x52\x2e\xf4" \
"\xc9\xca\x95\x71\x3a\xcb\x9b\xdb\x47\x13\x6e\x58\x14\xe1\xe1\x89" \
"\x3c\x6b\x80\xa8\x84\xaf\x35\x68\x46\x6e\x65\x49\x8b\x32\x3e\x79" \
"\xcd\x10\xd5\x92\xc9\x6b\x42\x09\x51\xc8\x14\xec\x9f\xa6\x29\xa2" \
"\x3c\xc6\xa6\x0e\x63\xf1\xe4\xb6\x7a\x1c\x0c\xc2\x41\x74\x5d\xee" \
"\xa5\xb3\xb5\x71\x6e\xd6\x93\x85\xf9\x78\x2e\x3b\x20\x88\x11\xe8" \
"\xba\xe1\xe4\x27\x70\xa4\x39\x0b\xbf\x76\x4a\x2d\x42\xee\x4b\xf7" \
"\xce\xea\x50\x51\x13\x34\x03\x92\x39\xd1\x12\x8c\x3f\xdd\x74\x62" \
"\xb3\xb5\xba\x2d\x2e\x76\xee\xa4\xe8\x8f\xf4\x1b\x19\xa6\x84\x1a" \
"\x5f\x98\x11\x85\x13\x24\x1b\x6d\xe3\x8e\xc6\xd2\x13\xf8\x72\x24" \
"\x6f\x0c\x44\xba\xf4\xe4\xe0\x72\xde\xd8\x0b\x48\x61\x81\xa2\xfb" \
"\x76\xee\x60\x8a\xeb\x60\x91\x87\xe1\x89\xb2\xa4\x6a\x14\x5f\x65" \
"\xb7\x2b\x89\xf3\xd4\x25\x97\x2b\xbf\x2b\xba\x11\x30\x2e\xb3\xfe" \
"\x2c\xe3\x77\xd8\xf2\xc0\x61\xd2\x13\x6a\xb9\xc0\xb7\xf1\xe1\x3f" \
"\x66\x04\xf3\xa7\x1f\x55\x21\xb7\xaf\x16\x63\x8d\x73\x06\x06\x00" \
"\x64\x6a\x23\x42\xf4\x57\x08\x5f\x34\xc1\x94\xa9\xd5\xa6\x82\xee" \
"\xeb\x72\x8e\xba\x33\x6b\x68\x39\x28\xb4\xb5\x4d\xa2\x32\xe8\x76" \
"\x26\xb0\xf8\x54\xf1\xa9\xb0\x96\x8d\x8b\x7e\x56\x64\xd7\x52\x57" \
"\x84\xdb\xfd\xf0\xda\xc6\x75\x3b\x77\x16\x8b\x09\xb3\xe9\x12\xdd" \
"\x86\xb8\xf7\x05\x70\x50\xcc\x8d\x8d\x2b\xff\x2a\x53\xff\x6f\x3a" \
"\xdb\x9a\x68\x66\x6a\x4b\xa0\x33\xa9\x39\x8f\xb2\xce\x18\xf8\x59" \
"\xe7\x57\xf2\xcd\x57\x3f\x55\x23\xd9\x87\x0a\xbf\x1b\x37\xcf\xe2" \
"\xc8\x81\xb1\x31\x6a\xb4\xb8\xd4\x44\x29\x2b\xec\x6e\x67\xe7\xc7" \
"\x14\x4b\x65\xae\x42\xf2\x16\x06\x49\x75\x74\xf3\xc7\xea\x65\x18" \
"\x65\xf0\x77\x5e\xf1\x83\xa4\x99\x0f\x7f\xba\xc7\x9f\x94\x62\xad" \
"\x0f\x20\x07\xa8\x69\x7d\xc4\xff\x33\xbb\x65\xbc\x1c\x80\x9f\x36" \
"\x03\xbf\x82\xf6\x8a\x4b\xfb\x30\x22\x51\x00\xcf\xa6\xe8\x1e\xf0" \
"\x69\x01\x00\xe6\xd2\xe6\x04\x58\x7e\x87\xd3\xfe\xd4\x1a\x03\xc3" \
"\x90\xcd\x66\x40\x60\x56\x16\xb5\x84\xf7\xb5\xd7\x81\x75\x6f\x82" \
"\x0a\x2c\xaa\xe3\x3c\x6b\xa9\x99\x27\xb1\x1f\x08\xb4\x34\x5a\x46" \
"\x03\x7f\x79\x4f\x9c\xb4\x3a\x21\x7f\xbe\x0b\x3e\xdb\x54\x3c\xb6" \
"\xa0\x3c\x0e\x25\xbc\x80\xc8\x01\x03\xc7\xb0\x4a\x75\x62\xfe\x9e" \
"\x75\x3e\x7b\xe7\xe0\x57\x67\x05\x60\xb2\xec\x97\xce\xef\xb3\xad" \
"\x89\x38\x7c\x89\xc9\x85\x46\xc3\x51\x8c\xec\x40\xd2\x47\xfb\x05" \
"\x47\x98\xbb\x29\xe5\xe8\xa8\x62\x04\xa4\x25\xe5\xd4\xbe\x6a\xe9" \
"\x76\x55\x09\x88\x44\xc1\x3a\xca\x2c\x1e\x65\x28\xbe\xcd\xcb\x77" \
"\x40\xa0\x7b\x27\xfb\x0b\xc5\xee\x8c\xed\x47\x6a\x8f\xdc\xbc\x1e" \
"\xff\x36\xee\x9f\xa3\x04\x44\x02\x34\x99\x67\xa8\xaa\xe8\xc5\xe4" \
"\x09\x73\x35\x01\xb0\xb5\x39\xe3\xb5\x34\x9b\x67\x89\xbf\xf6\x92" \
"\xbc\x0e\xe4\x99\x45\xd1\x80\x7c\xbc\x1d\x55\x05\x2b\x9a\x81\xf4" \
"\xed\xc6\x91\xbf\x84\xf3\xd6\xeb\x4f\x59\x9a\xd6\x9a\xbc\xd0\x6c" \
"\x31\x7d\xff\x2f\x45\xf9\xba\x36\xde\x4b\x1a\x10\xd9\x30\x59\x21" \
"\xa6\x42\xb7\x64\x38\xf3\xef\x76\xd4\x41\x35\xc5\x05\x86\x64\x4c" \
"\xfe\xe1\xf5\x3e\xd1\x93\xc6\xe0\x55\x11\x97\xb7\x73\xa6\x82\x4c" \
"\xf3\x35\xba\x90\x03\xad\xda\x93\xd7\x0c\x77\x62\xc1\x32\x9b\xc3" \
"\xd1\xc6\xa0\x61\x01\xae\xde\x39\x6b\xbf\x71\x98\xa5\x17\x46\x4a" \
"\x4b\x1f\x62\xc8\x3b\x11\xc4\x06\x99\x54\xf1\x1a\x68\xda\xff\x18" \
"\x8f\x1e\xf5\xae\x62\xd0\x4a\x24\x64\x70\xf1\x90\xf6\x2e\x08\x36" \
"\x7a\xc3\x69\x9a\x11\xa8\x58\x13\xe4\x17\x17\xd4\x18\xc6\x5a\x1e" \
"\x8a\x8a\x1a\x98\x8b\x90\x6e\x65\x97\x01\x63\x71\x14\x8e\xb1\x94" \
"\xd3\x38\xe3\x09\xba\xe9\x42\x9d\xd3\x96\x6c\x5f\xb6\x2c\x0b\x63" \
"\xe4\xb4\xf8\xe6\x03\x4b\x82\x90\xaa\x9f\x3c\xe6\x47\x54\xcb\xbd" \
"\xc1\xda\x96\xc4\xa4\x4f\xc2\x5e\x4a\xf8\x89\x45\xbb\x97\x40\xe5" \
"\x7d\xd3\xb0\x74\x1d\x89\x0e\xa4\x5b\xdc\x10\x66\xf8\xea\xf0\x77" \
"\x9e\xa4\x22\x3f\xd7\xf1\x19\x1a\x8d\xd7\x68\x75\xf7\x4c\xcf\x10" \
"\x76\x4f\xa8\x1c\x3f\xb8\xef\x9f\x23\xd8\xe9\x22\x2d\xa4\x12\x92" \
"\xc6\x49\xdc\x95\x01\x8c\x6f\xea\xd7\x7f\xf7\xa8\x0d\x2c\xe5\xdb" \
"\x54\x57\x8b\xf2\x17\xec\xac\xd3\x50\x2c\x77\x6e\xe9\x06\x64\x71" \
"\x1f\x2c\x5a\x80\x31\x33\xca\x3e\x41\x6e\xcc\xfc\x4b\xa7\x09\x4b" \
"\xaf\x91\xfd\x50\x06\xaf\x48\xc8\x94\x24\xd0\x6a\x13\x95\xda\x5a" \
"\x54\x0a\x91\xe7\x5a\xdf\xe3\x23\x68\x02\x5b\xb6\x1d\xf4\xad\xdf" \
"\xfa\xf2\x9a\x74\xf7\x2c\x14\x1c\xfe\xd3\x0c\x8a\x0e\x09\x00\x70" \
"\x14\x36\xa5\x4d\x6a\x1d\xf1\x88\xa6\x12\x61\x85\x6f\x09\x7a\xa2" \
"\x52\xb4\xc4\x2f\xe0\xa3\x76\xdb\x2d\x0e\x1c\xd6\xfc\xe0\x9a\xa8" \
"\xa4\xa7\x86\xd0\x9f\x6b\xd2\x9d\x9f\x88\x93\x3d\x32\x64\x90\xdd" \
"\x4d\x51\x45\xa6\x9a\xbb\x1e\xc1\xab\x39\xe7\x4c\xdf\x96\x7b\xf8" \
"\x3d\xce\x4a\xa7\xcc\x2d\x1d\xba\x9d\xfb\x60\xc6\x95\x89\xb0\xd7" \
"\x84\x2d\xba\x11\xb3\xd3\xf8\x26\xe5\xcf\x8f\xb6\x9e\xff\x40\x8f" \
"\xeb\x66\x96\x08\x75\x2f\x74\x36\x30\xc3\x20\xfa\x81\xb6\xf2\x50" \
"\x91\x96\x6d\x46\xdd\x58\xdc\x09\xd9\x5f\xc2\x42\xbd\xfd\xa9\x63" \
"\xc9\x3b\xd6\xdb\x30\x9e\x23\xab\xca\xc6\x19\xea\x0b\x4d\x84\x5e" \
"\x2c\x40\x63\x30\x91\x7a\x9e\x1e\x3f\x70\xf2\xf3\xdb\x91\x30\xf1" \
"\x22\xb4\xec\xb1\x58\x0a\xf8\x14\x50\xf2\xf9\xb5\xd1\xf2\x24\x5a" \
"\x1f\xe7\x96\xa1\x39\x2d\x22\xa9\x9b\x9b\x91\xae\x55\x59\x9b\x70" \
"\xb9\xa8\xe4\xc4\xac\x09\xb6\x41\xc7\x54\x83\x10\x75\x2e\x02\x4f" \
"\x6f\xcd\x2f\xd5\x6b\x2a\x0c\xcf";
datasize = sizeof(data5) - 1;
sub_67FEF0((int)m_DecryptKey, datasize, (int)data5, (int)buf);
pos = FindMemory((char*)"\x78\x9c", 2, buf, datasize);
if (pos)
{
zipsize = datasize - (pos - buf);
result = zdecompress((unsigned char*)pos, zipsize, (unsigned char*)decodebuf, &decodelen);
}
char data6[] =
"\x9c\x28\x81\x68\xb9\x43\xc6\xb8\x2d\x1a\xc9\xee\x49\x7d\x6d\xae" \
"\x2a\x2b\x45\x6a\x9e\x3c\x93\x80\x17\x93\x0e\x97\xa0\xe4\xa4\x08" \
"\x5b\x10\x28\x99\x45\x9a\xab\xe9\x80\xe0\x98\x9a\x14\x72\x33\xc6" \
"\xce\xce\xef\xb5\xf7\x2a\x25\x59\xb5\x4e\x0c\xd6\x41\xd3\x78\xbe" \
"\x7f\xed\x0f\xcd\xa4\x87\xcf\x2c\x69\xa5\x6a\xc5\x5a\xaa\xe4\x9d" \
"\x3a\x29\x3f\x50\x81\xf9\xc3\xc9\x18\x5c\xd4\x48\x58\xfb\x1b\xb2" \
"\x36\xe9\xe2\xbd\x82\x4d\x9d\x7b\x5a\x2b\xc6\x0d\x0d\xa3\xd6\x8a" \
"\xb6\x9c\xfe\x62\x7f\x0b\x70\x92\x12\x88\x38\x6e\xeb\x8d\x47\x29" \
"\x16\x00\xaf\xc0\x09\xc4\xbe\xf6\x33\x50\x78\x09\x0c\xe6\xc2\xdd" \
"\x2e\x0b\x60\x68\xfd\x47\x43\x2f\xf9\x9d\xed\xc9\xaf\xab\x09\x8f" \
"\x6c\x5d\x44\xbf\xad\x06\x53\xad\xbd\xd5\x7f\x31\x73\x8e\x91\x26" \
"\xc8\x27\xa8\x68\x07\xa0\x78\x48\x10\xb5\x1f\xb3\x86\x72\xb9\xcf" \
"\x87\xa5\xfc\x63\xb8\x25\x7d\xcc\x62\xef\x1e\x9a\xb2\xf5\x6e\x15" \
"\x67\x2a\x03\x64\xd4\xd7\xd9\x6c\x37\x1d\xbd\x1d\xa3\xf4\x2d\x6e" \
"\xc8\xd4\x27\x2d\x58\xe2\x71\xfd\x35\x54\xa3\x1c\x51\xee\x1a\xfb" \
"\x23\x8c\x71\xea\x49\xcb\x9a\x39\x0d\x13\x86\x45\x82\xed\x5f\x69" \
"\xd6\x94\x69\x50\xf5\x12\x7a\x83\x85\xaa\x9b\x49\x92\x19\x8a\x88" \
"\x57\x20\x54\x94\xec\x9f\x70\x20\x62\xd2\x23\xbd\x41\xbe\xed\x3b" \
"\xf1\x9f\xe3\xe3\x9a\x82\xba\xdb\x10\xc7\xc2\x26\x2c\x93\x6e\x1a" \
"\xa9\xf6\x62\x8d\xce\xd3\x53\x7b\x31\x7b\x2e\x96\x72\xd8\x9b\x51" \
"\xb0\x32\xe5\x3f\xf7\xac\x0b\xe9\xd2\x3e\x42\xcb\x31\x96\x32\xe7" \
"\xf7\x07\xf9\x83\x92\xd0\x26\xaa\x8b\xe2\xef\x7f\x56\xf4\xad\xa7" \
"\x30\x9e\xe4\x29\xc0\xc1\xf5\xbd\xbe\x28\xa3\x8e\xd3\xfc\xf0\xb8" \
"\x3b\x8b\x15\x6c\xd7\x23\xe3\x6c\x6a\xc2\x5d\xaa\x3a\x8b\x57\x01" \
"\x99\x90\x51\x22\x39\x8f\x68\x2e\x90\x47\x78\x3e\x2c\x8d\xf6\x10" \
"\x4d\xc1\xd1\x7f\x6b\x4d\xa0\x09\xeb\x5c\xdf\xe3\xc1\x64\xa2\x19" \
"\x77\x19\x81\x38\x3a\x5c\xf3\x48\x81\xa6\xea\xcb\x1e\xdf\xf2\x73" \
"\x43\x3e\x70\xfd\x7f\xf1\x00\x7a\x37\xd9\x2a\x7a\x67\x50\xb2\x52" \
"\xf9\xae\x55\xfb\x0a\x41\x0f\x0a\x39\xdb\x72\x48\x90\x15\xc1\x58" \
"\xfb\xe5\x8c\xe9\x45\x82\xc2\xd8\xb6\x64\x9f\x3d\xee\x29\x58\x85" \
"\x7a\x53\x0f\xe6\x31\x1e\xc5\x0c\x8b\xa2\xc7\x32\x41\x1b\xfb\xf5" \
"\x5b\x50\x1e\x92\x59\x19\x0c\x57\x14\xdf\xfc\xba\xc0\xe8\x34\x83" \
"\x69\x38\x25\xc5\x29\x07\x40\xa0\x9b\xb5\x4b\x75\x73\xf5\x0e\x70" \
"\x19\xb5\xf9\x08\xae\x12\x6c\xa3\xa3\x58\xb4\x30\x61\xce\x0b\x89" \
"\x54\xf6\x17\x1f\x38\xde\xc5\x30\xc0\x5e\x44\xff\xb2\x6c\x34\xe0" \
"\xcf\x56\xa1\x11\x69\x78\x68\x2a\xcb\xc5\xa4\xfa\x28\xaa\x94\xcc" \
"\x50\x20\x75\x87\x5b\xc9\x56\xd2\xfa\xa8\x14\x0c\x9c\xad\x6f\x2c" \
"\xc0\x18\x74\x7c\x95\x3d\x99\x2c\x2e\x4a\x1f\xc0\x8d\x7a\x9d\xd0" \
"\x70\xbc\x37\x2a\x11\x97\xba\xdb\x63\xf0\xe7\x62\x00\x13\xa5\x40" \
"\x35\x29\x8f\x4d\xa5\xc2\xe9\x14\x5e\x81\xab\x12\xd6\x02\x0e\x79" \
"\x9f\xd3\x31\x56\x19\x22\x08\x71\xfe\x5b\x21\x5a\x64\x5a\x53\x4d" \
"\x98\x87\xcf\x06\xab\xc5\x01\x1d\x0d\x78\x88\xd1\x44\x76\x89\x90" \
"\xb5\xbe\x5a\x48\xfb\x41\x80\x78\x4c\x29\x24\x37\x58\x88\xae\x56" \
"\x0b\x21\xb3\x82\x85\xbd\xd4\xca\x17\x8f\x7e\x60\x80\xb3\x88\x20" \
"\x7f\xba\xf6\xce\xf2\x41\xaa\x5e\xa4\xe2\x5c\x1e\xdf\x39\x09\xfa" \
"\x94\x34\x16\x9c\xde\x20\x80\x12\x1b\xf6\xc6\x63\xc3\x28"
;
datasize = sizeof(data6) - 1;
sub_67FEF0((int)m_DecryptKey, datasize, (int)data6, (int)buf);
pos = FindMemory((char*)"\x78\x9c", 2, buf, datasize);
if (pos)
{
zipsize = datasize - (pos - buf);
result = zdecompress((unsigned char*)pos, zipsize, (unsigned char*)decodebuf, &decodelen);
}
char data7[] =
"\x44\x0e\xab\x42\x45\xa7\xc7\x8b\x94\x8a\xf6\xf9\x53\x91\xd4\x6b" \
"\xf5\x12\x53\x1e\x19\x90\xed\x4c\xc0\xcd\xa8\x14\x02\x47\xa5\x12" \
"\x97\x32\x79\xf7\x2f\x4f\x81\x4b\xd2\x0e\x04\x01\x7b\x99\x62\x83" \
"\xde\x54\xae\xa6\x37\x8a\x10\x15\xd7\x90\x6f\x2b\x5b\x4c\x0d\x20" \
"\xad\x21\x80\x94\xa2\x65\x09\xb0\x57\x3a\xcb\xf4\x41\x21\x0f\xb8" \
"\xcb\x31\x1d\x47\x0c\x33\x9b\x86\x5a\x5d\x12\x99\xfb\xf1\xc5\xa8" \
"\x0f\xd3\x77\x5d\x02\x0c\xbb\xbe\x7e\x0c\x67\xd8\x0c\xbc\x82\xd5" \
"\xf8\x7d\xe4\x2e\x1f\xe8\x82\xfa\x2c\x7c\xba\x4d\xd5\x70\x74\x3d" \
"\x7c\x25\xca\x06\xff\x81\x29\x7c\xce\x79\xdc\xa7\xc6\x71\x43\x43" \
"\x32\x0e\x39\xf7\x9d\x46\xf7\x26\x6a\xb9\xc5\xd4\x5f\xef\xff\xb7" \
"\xa7\xa6\x17\x2f\xae\x2e\x2c\x72\x06\xb8\x72\xbc\x81\x5c\x8f\xf2" \
"\xfd\x3d\x5a\x2a\xa2\xfa\xe4\xc0\x3f\x19\xfa\xc1\xa3\x7c\x9f\x1a" \
"\xb7\xf0\x30\x15\x94\xe4\xbc\xe1\x19\xa4\xca\x48\x2b\xd0\xfe\xee" \
"\x6b\x9f\x76\x8b\xdd\xea\x18\xbb\xde\xa8\xae\x15\x44\x9f\x3d\xf5" \
"\xf9\x61\x96\x3f\xf3\x00\x2b\xa5\x3c\x86\x1b\xa5\xea\x5b\x85\x5c" \
"\x57\xc1\x5c\x84\x97\x41\x86\xf3\x01\xc9\x53\xac\x2f\x5a\x2a\x3b" \
"\xdc\xae\x89\x12\xed\x07\x4c\x67\xd4\xb8\x1b\xcd\xb4\xcf\x0d\xb8" \
"\x5c\x92\xfb\x37\x70\x03\xdc\x77\xb6\x98\x84\xac\x99\x7b\x72\xf6" \
"\xec\xad\xa3\x95\xca\x44\x68\xc8\x49\xf6\xca\xa6\x26\x9e\x71\x90" \
"\x17\x26\x41\xa2\x3b\xd5\xea\x51\x62\xb0\xf5\x39\x18\xea\xbf\xc1" \
"\x7c\xdf\x65\xd7\xc9\xf4\xde\x77\x13\xe9\x96\x00\xff\x5b\x14\xc0" \
"\x0c\xe2\x1f\x16\x9d\x8f\xc9\x38\x90\x7f\x73\xa7\x63\xba\x45\x0d" \
"\x0b\x89\xa8\xca\x31\xdc\x9a\x33\xcb\x30\x44\x8d\x17\x90\xca\x74" \
"\x24\x7b\x81\x09\xae\x13\x04\x35\xe5\x2b\x68\xf7\x20\x78\xc0\x6b" \
"\xa8\x20\x31\x8f\xd9\xde\x0f\x0d\x1b\x50\x94\x72\x66\xbe\xce\x2b" \
"\x86\xdc\xfc\xf2\xba\x51\x15\xe2\xa2\x88\xee\x25\xc5\x07\x8c\xc2" \
"\x41\x4d\x3f\x1f\x5f\x69\xd1\x9b\x7e\x51\x3f\x96\x0e\xb8\x38\xc9" \
"\xef\x56\x82\x78\xe8\xc0\x3f\x28\x9d\x6f\x39\x15\xd6\x0c\xa7\xf7" \
"\x9b\xf7\xb6\x02\xf1\xd7\x0b\xe3\x97\xd7\x0a\x6b\x4f\x20\x1a\x9d" \
"\x40\xe4\xa2\xff\x36\xa6\x94\xfc\x4a\x90\xb8\x3a\x36\x75\xa2\x3c" \
"\x75\x62\x57\xa9\xd1\xde\x4a\xc1\x03\x42\x98\x2b\xe3\x73\xc0\x31" \
"\xd1\x1a\x24\x22\x36\xc1\xb0\x19\x12\x7a\x0d\x93\xb6\x4a\xf0\xfc" \
"\x5f\x9a\x4f\xde\x58\x2f\xb9\x3e\x5b\xf5\xb0\x9e\xa6\xcd\xf2\xf5" \
"\xbc\x2e\x5a\x2d\xaf\xeb\x50\xf1\xcf\x56\xc0\xd2\x08\x92\x3f\x73" \
"\x6c\x1b\xa1\xb8\x7c\x71\x05\x08\xb8\x02\x1e\x27\x88\x76\xed\x66" \
"\xb5\x4c\x0e\xdf\xb1\x73\xb4\x20\x40\x20\xc2\x7b\xf4\x0b\x82\x18" \
"\x19\x56\x5b\xaa\xb9\x30\x7a\xdf\xcf\x9c\x68\x47\x52\x53\x10\x9d" \
"\x2d\x0a\x20\x97\xd3\xe6\xa1\x22\x87\xee\x77\x1b\x6b\xc9\x3c\x66" \
"\x0e\x21\xaa\xb0\xe6\x35\xf0\xf4\xce\x7d\x0a\x9f\x86\x04\xd4\x93" \
"\xe7\x72\xc6\x33\x7a\x69\x93\x65\xd4\xa4\x76\xc7\x9b\x40\x35\x16" \
"\xea\x17\x01\x34\xb0\x69\x7d\x54\x43\xbb\xc0\xf3\xb8\x5b\x50\xf6" \
"\xae\x0d\x9a\x11\x7d\x3b\xe5\x72\x52\x86\x86\xad\x52\x89\x1e\x5b" \
"\x32\x64\x7b\xaf\x36\x1d\x9d\xee\x87\xca\x30\x59\x0f\x61\xd3\x03" \
"\x25\xb5\xb4\x82\x8d\x97\xa3\xd5\xf1\x3a\x06\xfb\x42\xce\xc1\x51" \
"\x73\xdb\x90\xa8\x20\xa6\xe8\xff\x6b\x73\xdf\x06\x79\x28\xbc\xb6" \
"\xf9\xcd\x86\xf4\x65\xb3\x44\x47\x1d\xcb\x45\xfb\x70\x98\x69\x54" \
"\x1b\x48\xf5\x82\xe4\xa6\xcb\xd7\xc1\xbc\x2c\x6e\x7b\x25\xed\x9c" \
"\xb0\xba\xdc\x7e\x78\xb7\x10\x1b\x17\x02\xb3\x19\x3f\x13\x57\x4b" \
"\x19\x7d\xb6\x61\x91\x48\xb8\x98\xed\xda\xd8\x06\xdb\xd0\x2b\xec" \
"\xad\x5e\xfb\xdf\xac\x08\x1e\x1e\x7f\xf9\xfa\x99\x5f\xb3\xc3\x37" \
"\x6e\x68\x18\xc1\x6d\x6a\xe4\x67\x64\xad\x4a\xbb\xf9\x9c\x18\xb6" \
"\xd0\xb5\xc2\xcb\x4f\x10\x81\xd9\x10\x78\x11\xc6\x53\xf7\xd4\x11" \
"\x6e\xb2\x42\x67\xd4\x46\xb9\xc7\x26\x28\x57\xd8\x11\xd6\x94\xf6" \
"\x9e\x31\x9c\x2f\x67\x99\xe8\x2c\x32\x12\xb4\xc8\x9c\xe8\x0d\x48" \
"\xb4\xe4\xb9\x91\x10\x23\x2a\xbe\xce\x73\xb7\xef\xde\xde\x35\x44" \
"\xfa\x06\x87\x16\x0b\x29\xfe\xbf\x2e\xe4\x36\x15\x8a\x35\x8c\xff" \
"\xbb\xef\x0a\x43\xec\x11\xf0\xe8\xc7\x3a\xd2\x50\x63\xa7\x3b\x6e" \
"\x69\xbb\xbf\xe7\x49\x20\xf8\xf0\xd0\x78\x22\x72\x31\x55\x42\x0b" \
"\xaf\x73\xe2\x27\xb3\xff\x2c\x95\xef\x8d\x20\x89\xe9\x36\x97\xe8" \
"\x75\x9c\x87\xba\x2b\x66\x25\xd4\xb2\x0f\xfe\xa5\xa3\x1e\xc7\xc6" \
"\xa4\x61\xf4\xb4\x6c\xcd\x1a\xbd\x1f\x91\xa4\x5f\xdb\x0e\x6f\xea" \
"\x50\x6f\xbc\x73\x10\x80\xaa\xa4\xdf\x0c\x28\x81\x48\x15\x5e\x69" \
"\x9d\xd0\xf0\x41\x23\xe7\x90\xdc\x87\x42\x2b\x11\xc1\x0d\xd4\x56" \
"\x48\x11\x45\x5a\xf9\x88\x1e\x16\x50\x85\x63\x20\x99\x5e\xef\x2f" \
"\xd1\xfe\x5b\x5e\x4d\x97\xde\x9c\x54\x24\xbb\x61\xda\xc6\x03\x87" \
"\xce\x3e\x79\x97\x1c\x33\x2c\xf4\x81\x23\xf6\xb6\xfe\x14\xd2\xbb" \
"\x26\x89\x19\x59\x98\x04\x8f\xda\x96\xa5\x7c\x83\xf4\xbe\x75\x9d" \
"\xe0\xaf\xea\xe1\xb0\x1a\x08\xf7\xe4\x53\xf5\x2e\xd4\x89\xec\x81" \
"\xb2\xa4\x15\xfa\xf6\xa5\xec\x3a\xce\x87\xec\x97\xb7\x45\xec\x8e" \
"\xab\x50\x86\xd2\x95\xf8\xba\x87\x01\x4b\x95\x89\xad\xdd\x64\x7d" \
"\xba\xca\x8b\x39\x80\xdd\xb8\xd3\x50\x74\x97\x34\x00\x0a\xcf\x6d" \
"\x47\x21\xed\x00\x29\x0f\x6e\x3e\x6e\xf5\xd5\x94\x0c\xfd\x24\x3f" \
"\x9f\xca\xa8\x1a\xa7\x42\x16\xb1\xa1\xe9\x8f\x19\x83\xb2\x88\x89" \
"\xbc\x03\xfa\x94\x50\xf0\xdc\x5e\x3c\xf0\x4c\x12\x3d\x00\x99\x3c" \
"\xf0\x22\xe0\xda\x3b\xd5\x5a\xbe\x82\x3b\x5f\xd2\x9c\xde\x39\xbb" \
"\x71\x81\x68\xbc\x0c\x22\xdc\x0d\x15\x50\xeb\x9e\x2d\xda\x49\x89" \
"\x38\xef\xd8\x15\x73\x2b\x85\x61\x99\x77\x9d\xbc\x91\x0d\x8b\xe2" \
"\x99\x0d\x5c\x86\x46\x8b\x2b\xfe\xf5\xd8\x03\xd2\xa7\xf4\x06\x53" \
"\x67\x67\x3b\x42\xd1\x3a\xe2\xbc\xb9\xd1\x9b\x1c\xd4\x49\xa8\x19" \
"\xcd\xd9\x6c\x9a\x23\x9a\xb8\xe0\x6c\x04\xe8\x83\xa6\x70\xf0\xad" \
"\x4b\xa2\xf1\xf4\x89\x0b\x62\x19\xda\x03\xb7\xc6\x6a\x42\x12\x9e" \
"\x7c\xa1\xcf\x39\xa8\x3a\x49\xfe\x09\xda\x19\xcc\xc4\x43\x61\x53" \
"\x1e\x2a\xe5\x55\x81\x09\x11\x41\x9b\x2f\xf1\x88\xca\xba\xe4\xbf" \
"\x84\x34\x85\x96\x95\xe2\xb4\x90\x80\x99\x66\x1f\xd0\xb3\xce\xc5" \
"\x09\x19\x84\x62\x8f\xa4\x10\x9f\x56\x9d\xa3\x04\xf9\xb1\xe8\xbe" \
"\xc0\x65\x75\x63\x46\xda\xcd\xb5\xb0\x04\xd5\x3b\x55\xe2\xee\x64" \
"\xa4\x4c\xdb\x44\xed\x79\x9a\xbd\x01\xc1\xf6\x3f\x62\x57\x1b\x7f" \
"\x41\xae\x90\xba\xbd\x1c\x20\xec";
datasize = sizeof(data7) - 1;
sub_67FEF0((int)m_DecryptKey, datasize, (int)data7, (int)buf);
pos = FindMemory((char*)"\x78\x9c", 2, buf, datasize);
if (pos)
{
zipsize = datasize - (pos - buf);
result = zdecompress((unsigned char*)pos, zipsize, (unsigned char*)decodebuf, &decodelen);
}
char data8[] =
"\x26\x90\x33\x56\x3b\x2d\xd5\x2c\x58\xfa\x62\xbb\x9f\xe5\xc0\x93" \
"\xcf\xd5\x4a\xd7\x25\x2d\xa9\xcb\x9a\xef\x5c\x92\x1f\xf1\xc7\x71" \
"\x99\x12\x1e\x9a\xa6\xa9\x31\x43\x92\xe3\x4e\xb5\xb8\xba\x30\x49" \
"\xf6\x0e\xbb\xe9\x62\x75\x40\xd8\x82\xff\x35\x68\xb5\x0f\xc1\x9f" \
"\xc6\x7e\xc4\x32\xcb\x54\xf6\xe8\x3b\x59\x9e\x93\xbc\xb5\xde\xda" \
"\xd2\xe9\x0a\x3d\x49\x2c\xaf\xe0\x6d\x05\x78\xe6\xb9\xde\xb7\xe4" \
"\xb9\x79\xb6\xa1\xda\x19\x03\x2b\x94\x0e\x52\x44\xcd\xf8\x27\xa2" \
"\x1d\xda\x9d\x39\x70\x0e\xf4\xfd\x24\xd5\x27\x0d\x57\xe9\x71\x89" \
"\xcd\x4b\x60\xac\x0a\x9a\x0e\x96\xd7\xc5\x6f\x00\xf3\xca\x22\x4e" \
"\x13\x10\xb2\x30\x41\x61\xbb\x61\xdb\x6e\x58\x91\x96\x1f\xc3\x53" \
"\xba\xce\x50\x3a\x7e\xb2\x10\xd5\x5d\x98\x71\x38\x43\x4d\x79\x6c" \
"\x8d\xae\xeb\xff\x04\x25\x06\xa2\xd9\x66\x59\xd5\xe3\xe2\x9c\x17" \
"\x1a\x81\xf3\x65\x2d\xc9\x4b\xe8\x7d\x27\x59\x29\x3b\xe5\x69\x09" \
"\x26\x59\x1f\xd3\x37\xf0\x0a\x46\x66\x83\x2e\xd3\xbc\x5b\xa1\x84" \
"\xa8\x28\x4e\x5d\x0c\x13\xd7\x70\x59\x26\xb8\x59\xc5\x72\x4f\x58" \
"\xc3\xce\x81\x77\x71\x13\x06\x3c\x74\xe5\xad\x03\x6e\xc0\xe8\x0b" \
"\x1f\x62\xd8\x2b\xe6\xde\xa6\xd6\xcd\x50\xbc\xe1\x26\x5d\x64\xa4" \
"\x6c\xb3\xa2\xe6\xe2\xe7\x22\x4a\xf5\xd5\x95\xe8\x0a\xae\xab\xeb" \
"\xab\xee\x17\x25\x06\xf2\x44\x1b\x4a\x24\xa9\xdd\x6b\x39\x8a\xae" \
"\x09\x70\xba\x35\xc3\x51\xc3\x01\xbd\x8e\xcc\x67\xb7\xd9\xf3\x5e" \
"\xd2\x6b\xe4\xaa\x58\x64\x1b\x6f\x39\xf4\x73\x2f\xf9\xc2\xd9\xdd" \
"\x3d\xd4\x61\xf3\x7f\xba\xe1\xd0\x05\x82\x8b\x20\x75\x69\xd4\xb6" \
"\x05\xae\xbb\x70\x3e\x60\x2b\x96\x4c\x6e\xe5\x70\x21\x31\x3d\xb6" \
"\x99\x09\x90\x6e\x72\xbe\xa6\xae\x6f\xb5\x56\x30\xaa\x81\xe0\xc3" \
"\x6d\x59\xbd\x7d\xbc\x24\x0d\xed\x78\x02\x18\x9f\xe0\x9d\xc3\x6c" \
"\xfa\xe0\x15\x4b\x97\xb0\x61\xf3\x02\x5f\x12\x91\x92\x99\x0b\x1c" \
"\xb3\x65\xf6\xfb\x8a\x43\x2c\x6f\xdc\x34\x68\x12\x12\xa9\x4f\x2a" \
"\xe4\x7d\x4d\x37\xf2\x56\xae\xe9\x47\x0a\x05\x0a\xd6\xbd\x05\x59" \
"\xbc\x9a\xac\x3d\x46\x25\x27\x4b\x2a\x60\x9e\x8b\x34\xa1\x35\x56" \
"\x7d\xdc\xf8\xc0\x9d\x8c\x19\x4d\xe0\xac\x2b\x32\xe5\x94\xa8\xd5" \
"\xed\xa0\xb6\x93\xfa\xce\x74\xdf\xe1\x0a\xfd\x2a\xb8\xb8\xc6\xda" \
"\x5b\x75\x87\x49\x4c\x0b\x98\xe0\xbc\xfb\xf2\x1d\xdf\xe5\x36\xbe" \
"\xc5\x84\xa8\xac\x8e\xa8\xc8\x92\x59\x1b\xaa\x48\xe3\x00\x22\x8b" \
"\x06\xa8\x4d\xb8\x89\xdc\xf6\xf2\xc3\xc6\xe5\x6a\x50\x99\xbe\xf2" \
"\x65\x1a\x1e\x23\xd0\x1b\xf8\x99\x3d\x71\xb9\x94\x01\x4e\xba\x8e" \
"\xd2\x71\x97\x24\x25\xc1\x74\x51\x76\xdc\x4a\xc9\x63\xbc\x43\x04" \
"\x86\x2e\xe3\x21\xec\x99\x2e\xe9\x0b\x27\xbc\xe7\xe5\xfd\x89\xfa" \
"\xf8\x14\x5c\xe4\x4d\x54\x46\x30\x50\x9c\xb1\x22\xf4\x9f\x8f\xce" \
"\xe3\x15\xf3\xa5\x58\xe5\x52\x39\x57\x83\x83\x71\x76\x46\x73\xb2" \
"\xb6\x81\x3b\x8b\x79\xac\x43\x1c\x7c\x3e\xd3\x5f\x93\xe7\x94\x34" \
"\xb3\xf9\x86\x96\xba\x51\xff\xdd\x3c\xa4\x59\xee\xc6\x77\xb1\x93" \
"\xad\x7a\xa4\xe8\x7d\x1a\x60\x78\x33\xcb\x7f\x28\x41\x07\x19\x51" \
"\x2e\xee\x71\x84\x67\x27\x35\xf7\xf5\x10\xb4\x0b\x0e\x1e\x8a\x29" \
"\x25\xda\xb6\xb3\x79\xac\x45\x21\x74\xa9\x9d\xae\x54\x61\xe4\x3e" \
"\xd9\x0e\xc5\xba\xec\xf5\x3f\x1c\xb6\xaa\x25\x8f\x04\xe5\x1e\xe9" \
"\x3c\x6f\x50\x74\x60\x6b\xde\x15\x51\x7b\xbc\x1d\x3a\x0e\xe7\xf5" \
"\xdd\x40\xb8\x59\x35\x82\xe7\xcb\xa9\x9e\xad\xbd\xe9\x10\x67\xba" \
"\xe2\x76\xaa\x30\x7a\xa2\x92\x24\x76\x0b\xcc\x1f\x38\x81\x52\xe2" \
"\xb1\x9d\xfe\x8b\xe8\x23\xb0\x1e\x64\x22\x1a\x55\x9c\x36\x23\x72" \
"\x24\x59\x07\x02\xe7\x9e\x95\xc9\xc3\xb4\x86\x2f\xb2\xf8\xbb\x0b" \
"\x5d\x9d\xc6\xfe\xe9\xfe\xbf\xb9\xc7\x0f\xf0\x9d\x8b\xc1\xab\xcc" \
"\x05\x64\xc0\x43\x6e\xa7\x18\x9b\x09\xd5\xf2\xe3\x30\x45\x96\x17" \
"\x6f\x8a\xc4\x05\xe7\x44\x23\x03\x94\x4a\xe2\x6c\x86\xb9\x7f\xf8" \
"\x57\xb2\xa2\x8e\x62\x35\x4d\x54\x5b\xe5\xc9\x58\x98\x7b\x86\xe3" \
"\x18\x7a\x30\x49\x38\xd7\xa9\x36\x97\xe9\xb0\xd3\x37\xe8\xf6\x5b" \
"\xb1\x5a\xae\xb7\x5f\xf8\x4e\x0b\x0a\x9d\x94\x46\x6a\xb0\xb5\xbd" \
"\x86\xb5\xa9\x83\x73\x7f\x24\x96\xaf\x70\xf6\xed\x6e\xaf\xec\x61" \
"\xf3\xf4\x80\x1b\x1c\x84\xaa\x7b\x32\x92\x2d\x1b\x2d\xb1\x72\x13" \
"\xe9\x0c\xcd\xd4\xed\x47\x10\x0d\x61\x7a\x60\x0f\x18\xec\x77\x6b" \
"\x90\x70\x1f\xcb\x26\x6b\x37\xb3\xbe\x18\xcd\x48\xba\xf7\x89\x71" \
"\xdb\x75\xcb\x3f\xfa\x7f\x61\xdd\xa2\x32\x63\x7b\xbf\x8a\x71\x47" \
"\x33\x40\x88\x30\x90\xdf\x39\x8c\x00\x2f\xfa\x0c\x5c\x37\xbf\x8d" \
"\xd2\xab\xa1\x59\xdb\xa9\xba\x24\x61\x62\x11\xdd\xc7\x9a\xe4\x17" \
"\x02\x16\x24\xaa\x43\x8a\xbb\x24\x2a\x6c\xb3\x75\x45\xb7\x3b\xf4" \
"\xca\x50\x5e\x30\xef\x48\x37\xce\xa3\xb4\x08\xec\x31\x39\x03\x10" \
"\x6d\xed\xf5\xed\x64\xe8\x4c\xd5\xc9\xaa\xdc\x7e\x74\x42\xca\xbf" \
"\x1e\x7b\xa9\x9e\x01\xe8\xcc\x91\xfc\x04\x7f\xb8\x0b\xf4\x2a\x58" \
"\x02\x56\x1a\x5a\x33\x34\x1d\x1f\x36\x46\x0d\x2d\x0c\x9a\x35\xcb" \
"\x0d\xd3\x61\x80\x52\xcb\x64\x4d\x88\xea\xcd\x12\x5e\x90\x94\xb9" \
"\x45\xf9\x51\x5e\x13\x5d\x2e\x15\x44\xde\xd9\x73\xc3\x72\xaf\x01" \
"\x07\xfe\x25\x69\x7f\x8a\x48\x25\xb2\x1f\xf0\x3a\xd3\xc4\x19\xa6" \
"\xec\xe5\x4d\x22\xcd\x24\x90\xb5\xfd\xf9\x3b\x11\x53\x95\xf7\x43" \
"\x20\xb7\xcf\xd3\xa3\x3d\x80\x1f\xc6\x50\x72\x49\xc5\x20\xce\x3b" \
"\x61\xb9\xbe\x6f\xb0\x75\x32\xce\x25\x2d\xa8\x61\xda\x30\x36\x3f" \
"\xd0\xba\xae\x2c\x10\xd0\xb4\x60\xff\xf2\xf2\x54\x01\xdf\xc1\x8b" \
"\x6a\x0c\x24\x63\x1e\xdf\x61\x5d\x28\xf1\xaa\x25\x4d\xe6\x12\xb0" \
"\x02\x74\x3b\xf9\x40\xe6\xf1\xa5\xe6\x2a\x7a\x1b\x4c\x49\xa8\x54" \
"\x75\x61\x0c\x21\xc3\x31\xf7\x1b\xcf\x92\x6a\x1b\x29\xac\x86\x9a" \
"\xc7\xaa\x38\x4e\xb2\x75\x25\x3d\xe7\x1e\x4c\x33\x60\x25\x67\xfa" \
"\xe1\x24\x04\x2e\xf0\xfc\x12\x03\x88\xe5\xbd\x30\xec\x2a\xe4\x00" \
"\x77\x81\x97\x14\xec\xee\x43\x91\xcd\xc3\xac\xc4\x58\x2d\x57\x93" \
"\xbd\x08\x9a\x30\x69\x96\x5f\x16\x6b\x6f\x75\x1d\xf0\x3e\x0b\x4c" \
"\xfc\xa0\x95\x98\x6f\xfe\xda\x3c\x8d\xdd\x5f\x6b\x66\x26\x07\x70" \
"\xe9\x81\x80\x0a\x9b\x0c\xbc\xc4\x25\xc5\x0e\x98\x8d\x6f\xf0\x1c" \
"\x02\xd8\xd8\x73\x20\x9a\xd5\x36\xb6\x51\x0a\xbf\xaa\xaa\x05\x46" \
"\xd9\x04\xe6\x2c\x57\xa5\x66\xac\x78\x8d\x5d\x0b\xf0\x39\xbf\x1f" \
"\x5d\x40\x1c\x82\x34\x9f\x66\x44\x0d\xaf\x49\xf0\xc0\xca\x2e\x50" \
"\xd0\xb2\x45\x23\x31\xa6\x86\x3e"
;
datasize = sizeof(data8) - 1;
sub_67FEF0((int)m_DecryptKey, datasize, (int)data8, (int)buf);
pos = FindMemory((char*)"\x78\x9c", 2, buf, datasize);
if (pos)
{
zipsize = datasize - (pos - buf);
result = zdecompress((unsigned char*)pos, zipsize, (unsigned char*)decodebuf, &decodelen);
}
char data9[] =
"\xf0\xa2\xe1\x66\x8b\x77\xed\x90\x48\x0d\xe0\x39\x39\x9e\xd8\x24" \
"\x13\x6c\xca\x20\x50\x88\x7a\xfa\xd0\x92\x4d\x62\x16\xbd\x7f\x37" \
"\x88\x6d\x09\x97\xa0\xa4\x12\xfb\x6f\xac\x7e\x26\x10\xfe\x5d\x65" \
"\xfc\x4d\x01\xc0\x9b\x92\x99\x26\x97\x38\xd4\xb8\x1b\x12\x1a\x51" \
"\xd0\x29\x41\x3d\xf1\xcb\x80\xab\xbb\x72\xfb\x3d\x93\x76\xf4\x22" \
"\x35\xec\xd5\x2d\xcb\xad\xa8\x0a\x19\xdb\xf9\x37\x72\x4a\xdf\x1d" \
"\xad\x50\x03\x30\xe7\xc5\xdf\xeb\xf1\x22\xfb\x61\xee\x41\x40\x08" \
"\x87\x94\x25\x07\xc7\xe8\xbb\xaa\x0e\x3c\xc2\xb6\x1f\x4b\x95\x8b" \
"\x46\x95\x59\x0f\xc5\x84\xf1\xb7\x9b\xe2\x14\x3b\x02\xf5\x61\x12" \
"\x6f\x76\xd7\x2d\xee\x8d\xf0\x6b\x4c\x19\x62\x1e\xcc\x94\x7a\xfc" \
"\x91\x40\xf9\x55\x8c\xbd\xc8\x0d\x22\xda\x68\xbe\x7a\x9a\xb4\x9b" \
"\x2d\x74\x87\xd2\x8a\xa2\x8b\xc6\x21\xb1\x52\x7a\xc3\x4a\x9e\x2a" \
"\xc3\x5e\x21\xcc\x78\x1b\x4f\x2b\xf3\x62\x57\x76\x48\x2b\x3b\xb1" \
"\x65\x28\x80\x4e\x99\xe4\x32\xa6\x59\x51\xad\x54\x52\x24\x5e\x9a" \
"\x9a\x55\xea\x8b\xa6\xa2\xdf\xa1\x50\x62\x0a\x99\xdf\x40\xfd\xf9" \
"\xf6\x90\x0d\xe0\xf5\x3c\xce\xff\xa0\x7c\xbe\xcc\x09\x4f\x18\x43" \
"\x22\x1a\xbc"
;
datasize = sizeof(data9) - 1;
sub_67FEF0((int)m_DecryptKey, datasize, (int)data9, (int)buf);
#endif
return TRUE;
}