601、What is a characteristic of Cisco StackWise technology?
A. It supports devices that are geographically separated.
B. It is supported on the Cisco 4500 series.
C. It combines exactly two devices.
D. It uses proprietary cabling
602、Refer to the exhibit.After coniguring HSRP an engineer enters the show standby command. Which two facts are derived from the output?(Choose two.)
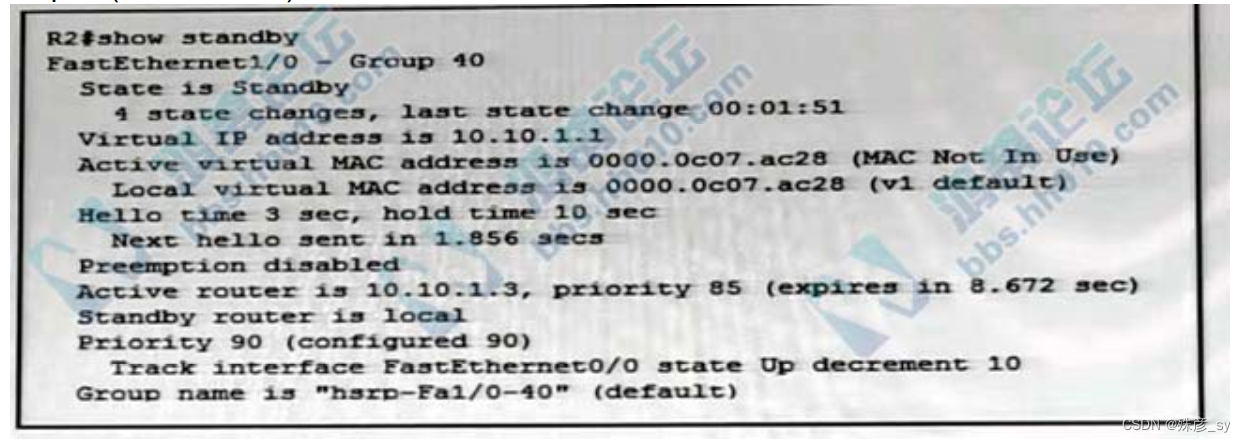
A. The router with IP 10.10 1.3 is active because it has a higher IP address
B. If Fa0/0 is shut down, the HSRP pnonty on R2 becomes 80
C. R2 Fa1/0 regains the primary role when the link comes back up
D. R2 becomes the active router after the hold time expires
E. R2 is using the default HSRP hello and hold timers
603、 Refer to the exhibit. After the code is run on a Cico IOS-XE router, the response code is 204 ,What is the result of the script?
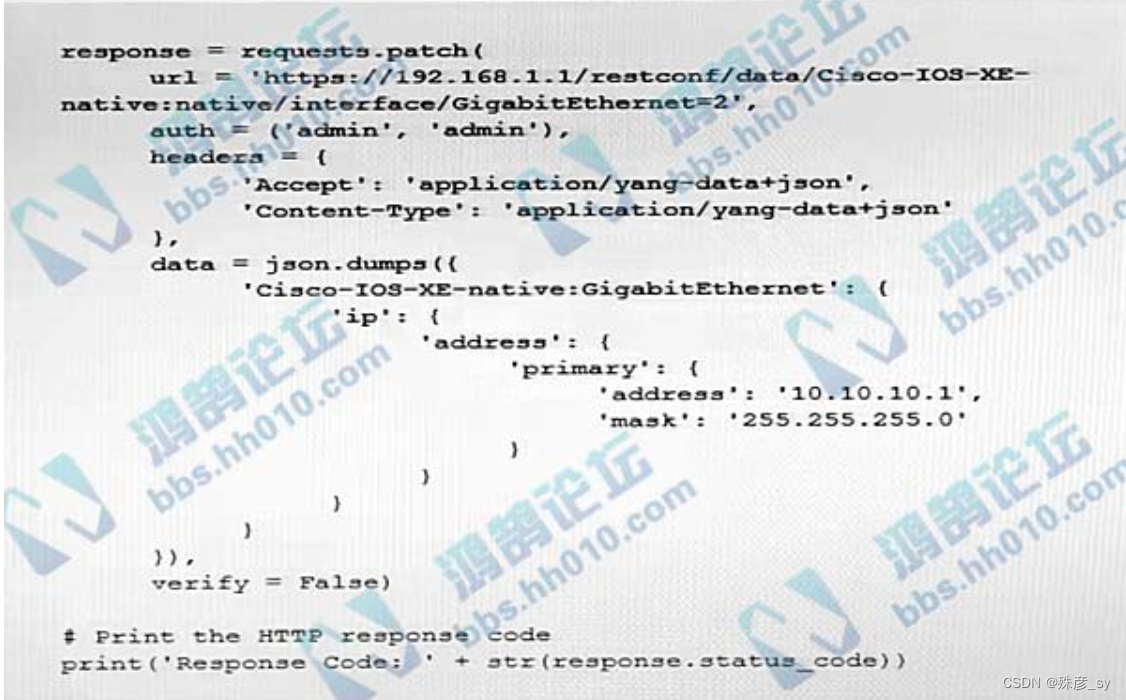
A. The configuration is successfully sent to the device in cleartext.
B. The configuration fails because interface GigabitEthernet2 is missing on the target device.
C. The configuration fails because another interface is already configured with IP address 10.10.10.1/24
D. Interface GigabitEthernet2 is configured with IP address 10.10.10.1/24.
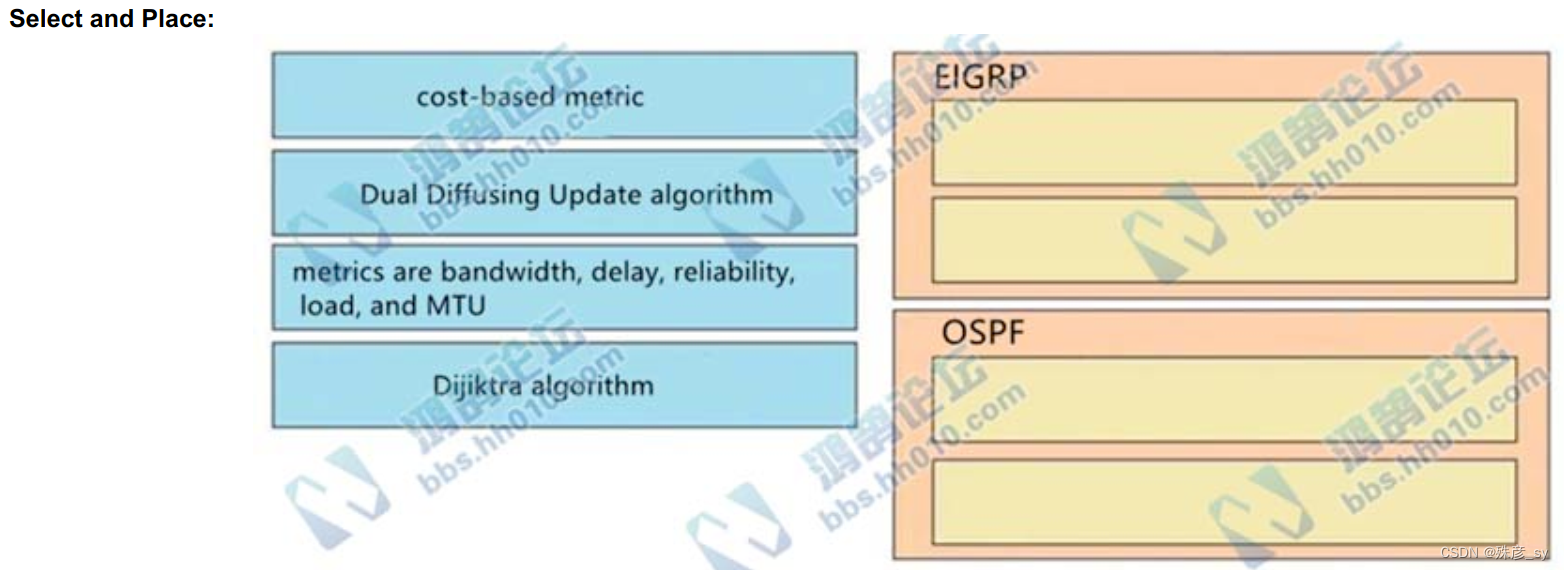
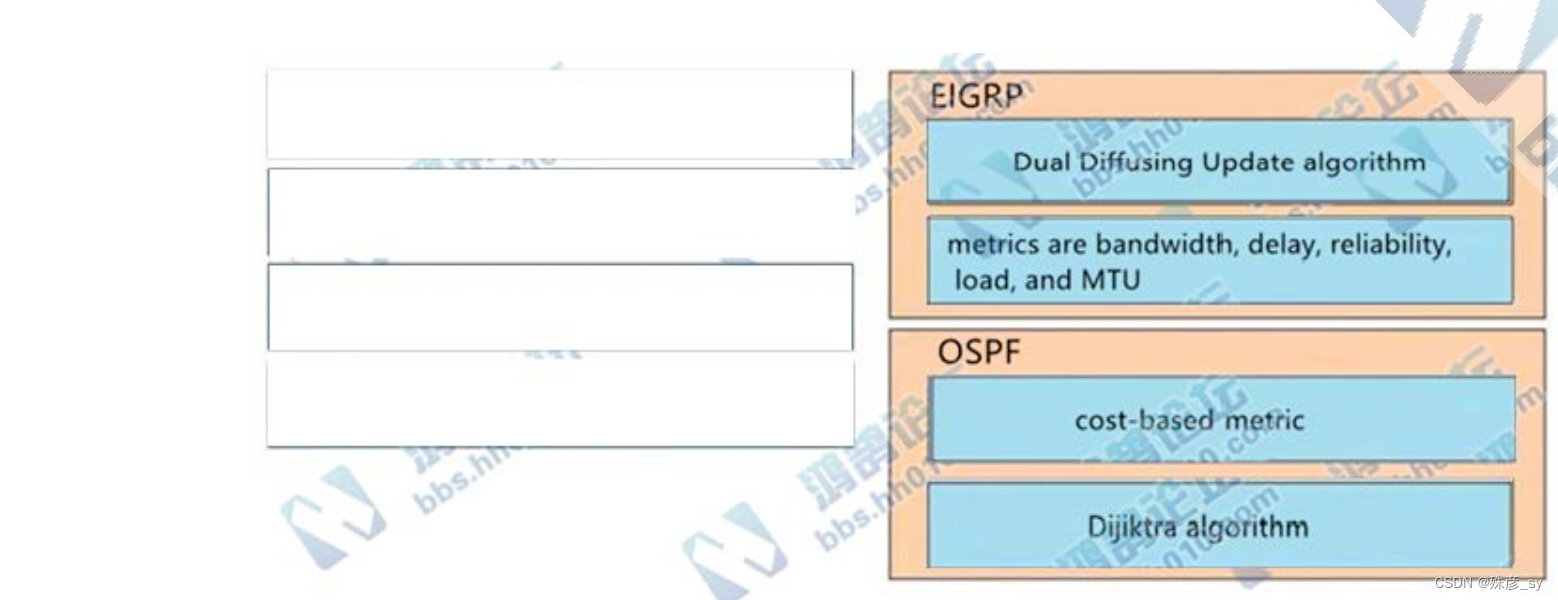
604、 Drag and drop the characteristics from the left onto the routing protocols they describe on the right
605、Refer to the exhibit. An engineer must configure static NAT on R1 to allow users HTTP access to the web server on TCP pot 80.The web server must be reachable through ISP 1 and ISP 2.Which command set should be applied to R1 to fulfill these requirements?

A. ip nat inside source static tcp 10.1.1.100 80 209.165.200.225 80
ip nat inside source static tcp 10.1.1.100 8080 209.165.201.1 8080
B. ip nat inside source static tcp 10.1.1.100 80 209.165.200.225 80
ip nat inside source static tcp 10.1.1.100 80 209.165.201.180
C. ip nat inside source static tcp 10.1.1.100 80 209.165.200.225 80 extendable
ip nat inside source static tcp 10.1.1.100 80 209.165.201.1 80 extendable
D. ip nat inside source static tcp 10.1.1.100 80 209.165.200.225 80 no-alias
ip nat inside source static tcp 10.1.1.100 80 209.165.201.1 80 no-alias
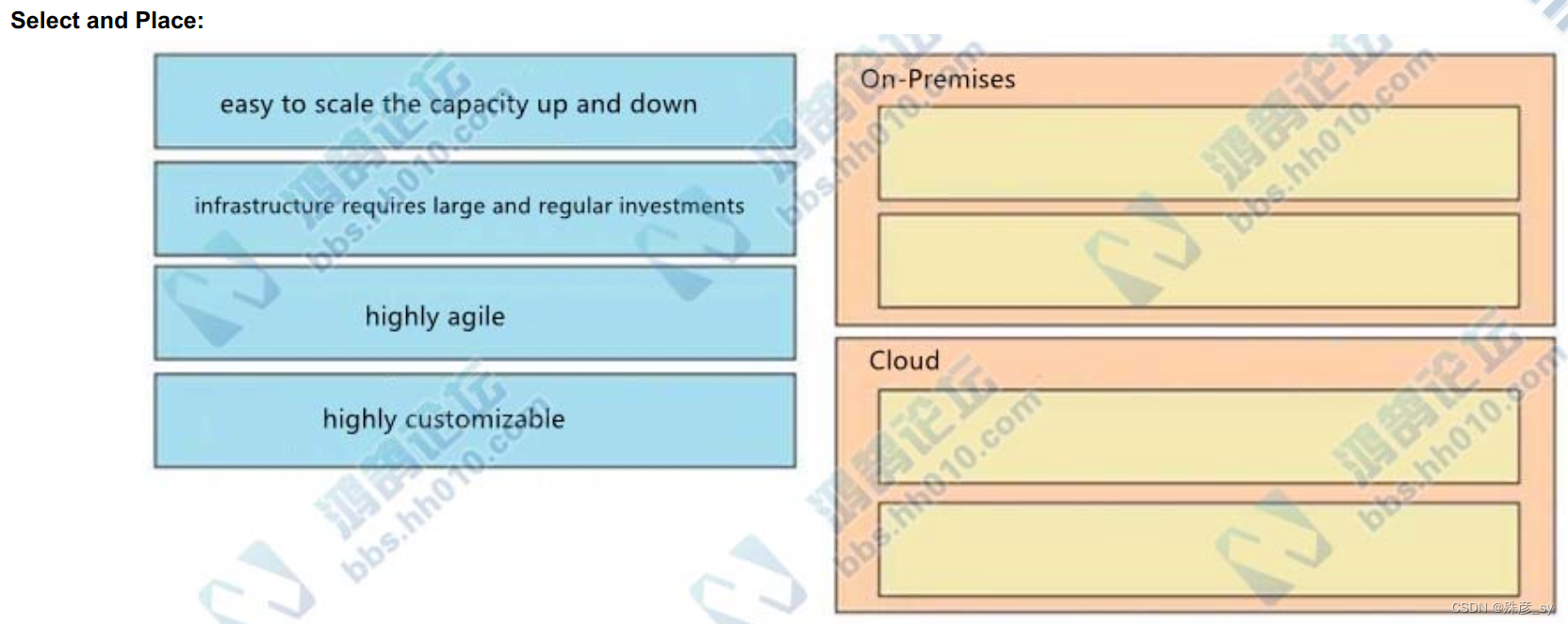
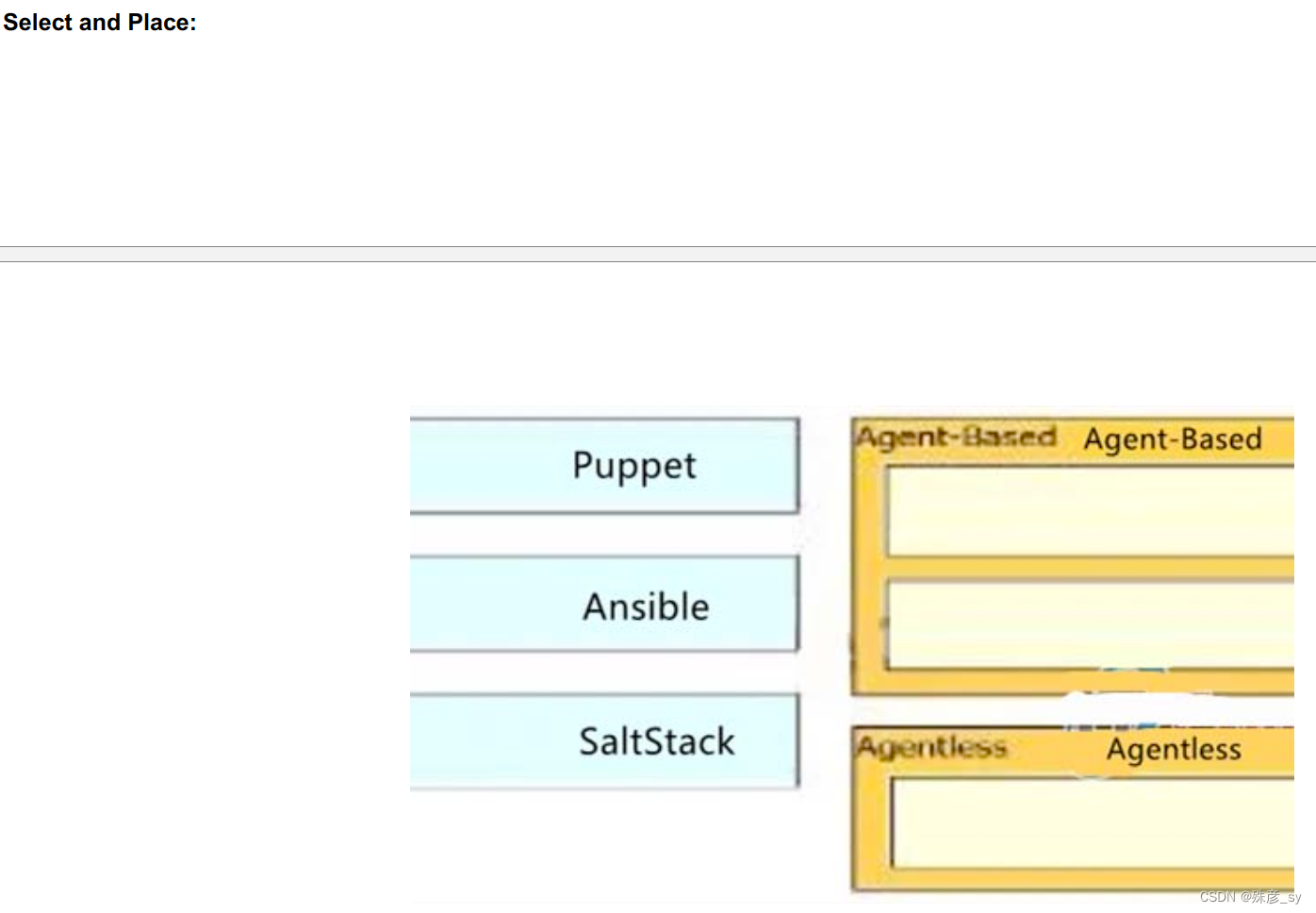
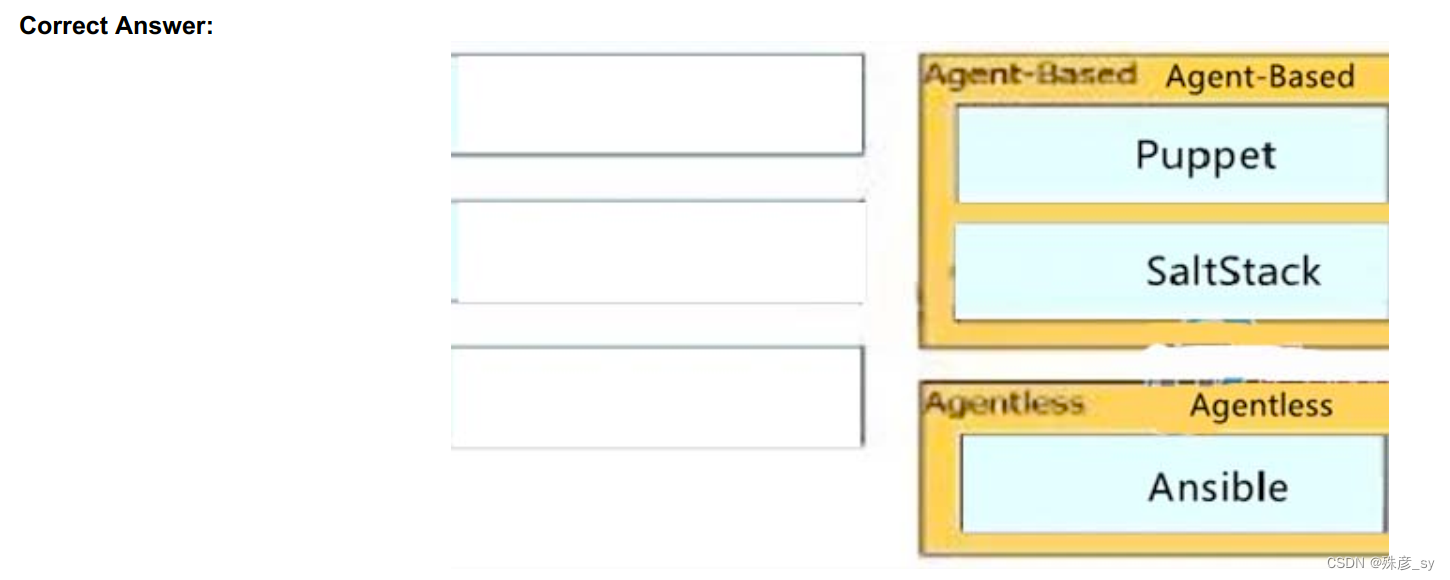
606、Drag and drop the characteristics from the left onto the infrastructure deployment models they describe on the right.

607、A network engineer configures a WLAN controller with increased security for web access .There is IP connectvity with the WLAN contoller but the engineer cannot start a management session from a web browser. Which action resolves the issue?
A. Disable JavaScript on the web browser
B. Use a private or incognito session
C. Use a browser that supports 128-bit or larger ciphers.
D. Disable Adobe Flash Player
608、In a Cisco SD-Access solution, which protocol is used by an extended node to connect to a single edge node ?
A. VXLAN
B. IS-IS
C. 802.1Q
D. CTS
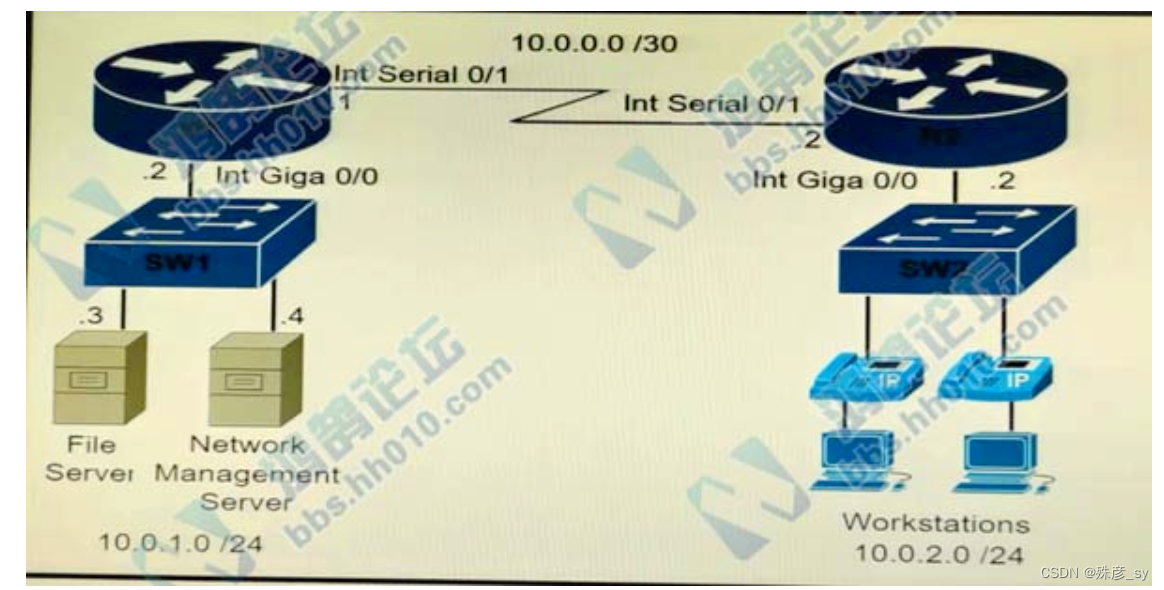
609、An engineer must configure and validate a CoPP policy that allws the network management server to monitor router R1 via SNMP while protecting the control plane. Which two commands or command sets must be used? (Choose two.)
A. show policy-map control-plane
B. access-list 150 permit udp 10.0.1.4 0.0.0.0 host 10.0.1.2 eq snmp
class-map match-all CoPP-management
match access-group 150
policy-map CoPP-policy
class CoPP-management
police 8000 conform-action transmit exceed-action transmit
violate-action transmit
control-plane
Service-policy input CoPP-policy
C. access-list 150 permit udp 10.0.1.4 0.0.0.0 host 10.0.1.2 eq snmp
access-list 150 permit udp 10.0.1.4 0.0.0.0 eq snmp host 10.0.1.2
class-map match-all CoPP-management
match access-group 150
policy-map CoPP-policy
class CoPP-managementpolice 8000 conform-action transmit exceed-action transmit
violate-action drop
control-plane
Service-policy input CoPP-policy
D. show ip interface brief
E. show quality-of-service-profile
610、What does a northbound API accomplish?
A. programmatic control of abstracted network resources through a centralized controller
B. access to controlled network resources from a centralized node
C. communication between SDN controllers and physical switches
D. controlled access to switches from automated security applications
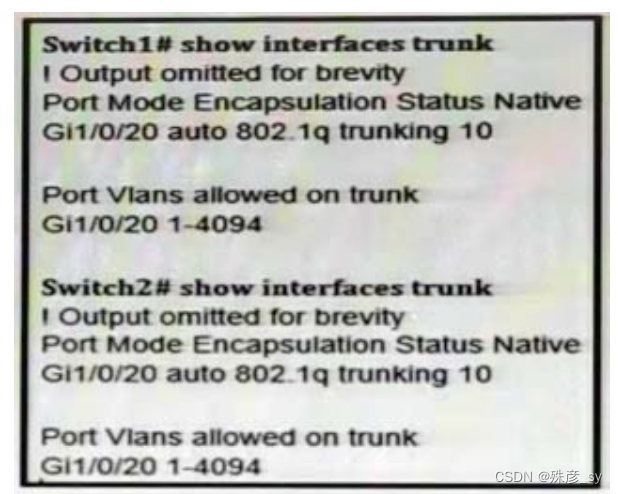
611、Refer to the exhibit ,The trunk does not work over the back-to-back link between Swich1 interface Gig1/0/20 and Switch2 inerace Gig1/0/20. which configuration fixes the problem?
A. Switch 1(config)#interface gig1/0/20
Switch1(config-if)#switchport mode dynamic auto
B. Switch2(config)#interface gig1/0/20
Switch2(config-if)#switchport mode dynamic desirable
C. Switch2(config)#interface gig1/0/20
Switch2(config-if)#switchport mode dynamic auto
D. Switch1(config)#interface gig1/0/20
Switch 1(config-if)#switchport trunk native vlan 1
Switch2(config)#interface gig1/0/20
Switch2(config-if)#switchport trunk native vlan 1
612、An engineer must enable a login authentication method that allows a user to log in by using local authentication if all other defined authentication methods failWhich configuration should be applied?
A. aaa authentication login CONSOLE group radius local-case enable aaa
B. authentication login CONSOLE group radius local enable none
C. aaa authentication login CONSOLE group radius local enable
D. aaa authentication login CONSOLE group tacacs+ local enable
613、Refer to the exhibit. Which command set changes the neighbor state from Idle (Admin) to Active?

A. R1(config)#router bgp 65002
R1(config-router)#neighbor 192.168.50.2 activate
B. R1(config)#router bgp 65001
R1(config-router)#neighbor 192.168.50.2 activate
C. R1(config)#router bgp 65001
R1(config-router)#no neighbor 192.168.50.2 shutdown
D. R1(config)#router bgp 65001
R1(config-router)#neighbor 192.168.50.2 remote-as 65001
614、Refer to the exhibit. A network engineer is enabling logging to a local buffer, to the terminal and to a syslog server for all debugging level logs filtered by facility
code 7. Which command is needed to complete this configuration snippet?
logging buffered discriminator Disc1
logging monitor discriminator Disc1
logging host 10.1.55.237 discriminator Disc1
A. logging buffered debugging
B. logging discriminator Disc1 severity includes 7
C. logging buffered discriminator Disc1 debugging
D. logging discriminator Disc1 severity includes 7 facility includes fac7
615、An engineer must create a new SSID on a Cisco 9800 wireless LAN controller. The client has asked to use a pre-shared key for authentication Which profile must the engineer edit to achieve this requirement?
A. RF
B. Policy
C. WLAN
D. Flex
616、Refer to the exhibit. VPN-A sends point-to-point traffic to VPN-B and receives traffic only from VPN-C VPN-B sends point-to-point traffic to VPN-C and receives traffic only from VPN-A. Which configuration is applied?

A. PE-2
vrf VPN-B address-family ipv4 unicast
import route-target 100:1
export route-target 100:2
B. PE-3
vrf VPN-B address-family ipv4 unicast
import route-target 100:1
export route-target 100:2
C.
D
617、Refer to the exhibit. An engineer configures the BGP adjacency between R1 and R2, however, it fails to establish Which action resolves the issue?
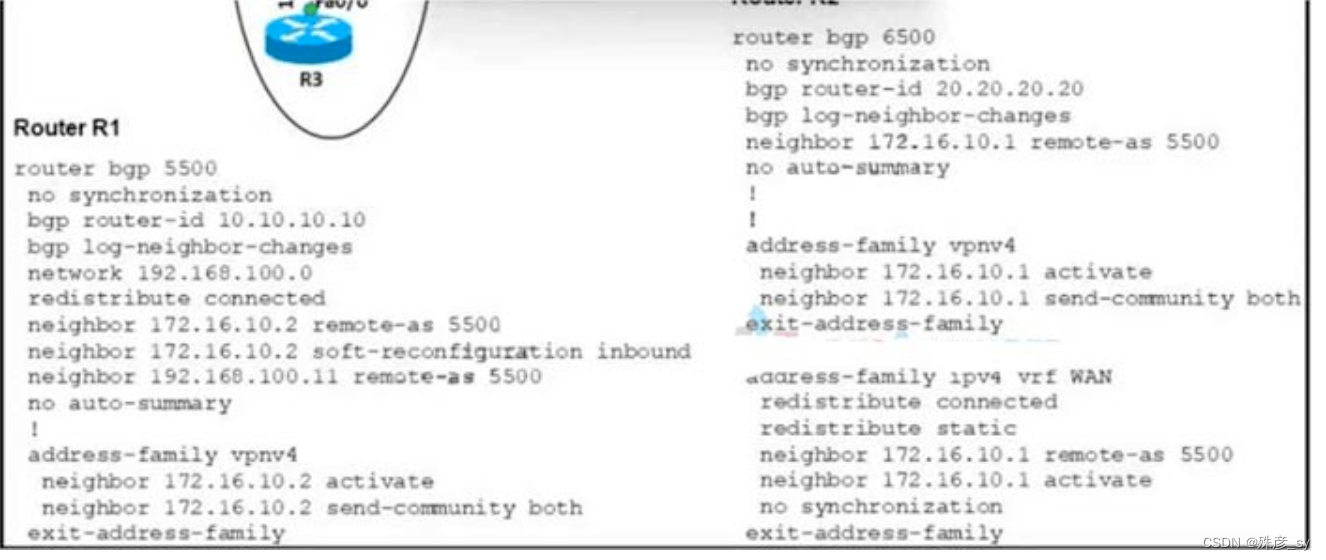
A. Change the network statement on R1 to 172.16 10.0
B. Change the remote-as number for 192 168.100.11.
C. Enable synchronization on R1 and R2
D. Change the remote-as number on R1 to 6500
618、 Which method is used by an AP to join HA controllers and is configured in NVRAM?
A. stored WLC information
B. DNS
C. IP Helper Addresses
D. Primary/Secondary/Tertiary/Backup
619、If a client’s radio device receives a signal strength of -67 dBm and the noise floor is -85 dBm, what is the SNR value?
A. 15 dB
B. 16 dB
C. 18 dB
D. 20 dB
620、A customer wants to use a single SSID to authenticate loT devices using different passwords. Which Layer 2 security type must be configured in conjunction with Cisco ISE to achieve this requirement?
A. Fast Transition
B. Central Web Authentication
C. Cisco Centralized Key Management
D. Identity PSK
621、Refer to the exhibit. R2 is the neighboring router of R1. R2 receives an advertisement for network 192 168.10.50/32. Which configuration should be applied for the
subnet to be advertised with the original /24 netmask?
R1#show run | b router ospf
router ospf 1
network 192.168.10.0 0.0.0.255 area 0
R1#show run | b interface loopback0
interface loopback0
ip address 192.168.10.50 255.255.255.0
A. R1(config)# router ospf 1
R1(config-router)# network 192.168.10.0 255.255.255.0 area 0
B. R1(config)#interface loopback0
R1(confia-if)# ip ospf 1 area 0
C. R1(config)# interface loopback0
R1(config-if)# ip ospf network point-to-point
D. R1(config)# interface loopback0
R1(config-if)# ip ospf network non-broadcast
622、How are map-register messages sent in a LISP deployment?
A. egress tunnel routers to map resolvers to determine the appropriate egress tunnel router
B. ingress tunnel routers to map servers to determine the appropriate egress tunnel router
C. egress tunnel routers to map servers to determine the appropriate egress tunnel router
D. ingress tunnel routers to map resolvers to determine the appropnate egress tunnel router
623、A network monitoring system uses SNMP polling to record the statistics of router interfaces The SNMP queries work as expected until an engineer installs a new interface and reloads the router After this action, all SNMP queries for the router fail What is the cause of this issue?
A. The SNMP community is configured incorrectly
B. The SNMP interface index changed after reboot.
C. The SNMP server traps are disabled for the interface index
D. The SNMP server traps are disabled for the link state
624、Refer to the exhibit. An engineer must permit traffic from these networks and block all other traffic An informational log message should be triggered when traffic
enters from these prefixes Which access list must be used?
10.0.32.0/24
10.0.33.0/24
10.0.34.0/24
10.0.35.0/24
10.0.36.0/24
10.0.37.0/24
10.0.38.0/24
10.0.39.0/24
A. access-list acl_subnets permit ip 10.0.32.0 0 0.0.255 log
B. access-list acl_subn*ls permit ip 10.0.32.0 0.0.7.255 log
C. access-list acl_subnets permit ip 10.0.32.0 0.0.7.255
access-list acl_subnets deny ip any log
D. access-list acl_subnets permit ip 10.0.32.0 255.255.248.0 log
625、A customer requests a design that includes GLBP as the FHRP The network architect discovers that the members of the GLBP group have different throughput
capabilities. Which GLBP load balancing method supports this environment?
A. host dependent
B. least connection
C. round robin
D. weighted
626、Refer to the exhibit. An engineer attempts to bundle interface Gi0/0 into the port channel, but it does not function as expected. Which action resolves the issue?

A. Configure channel-group 1 mode active on interface Gi0/0.
B. Configure no shutdown on interface Gi0/0
C. Enable fast LACP PDUs on interface Gi0/0.
D. Set LACP max-bundle to 2 on interface Port-channel
627、 Refer to the exhibit. An engineer must prevent the R6 loopback from getting into Area 2 and Area 3 from Area 0. Which action must the engineer take?
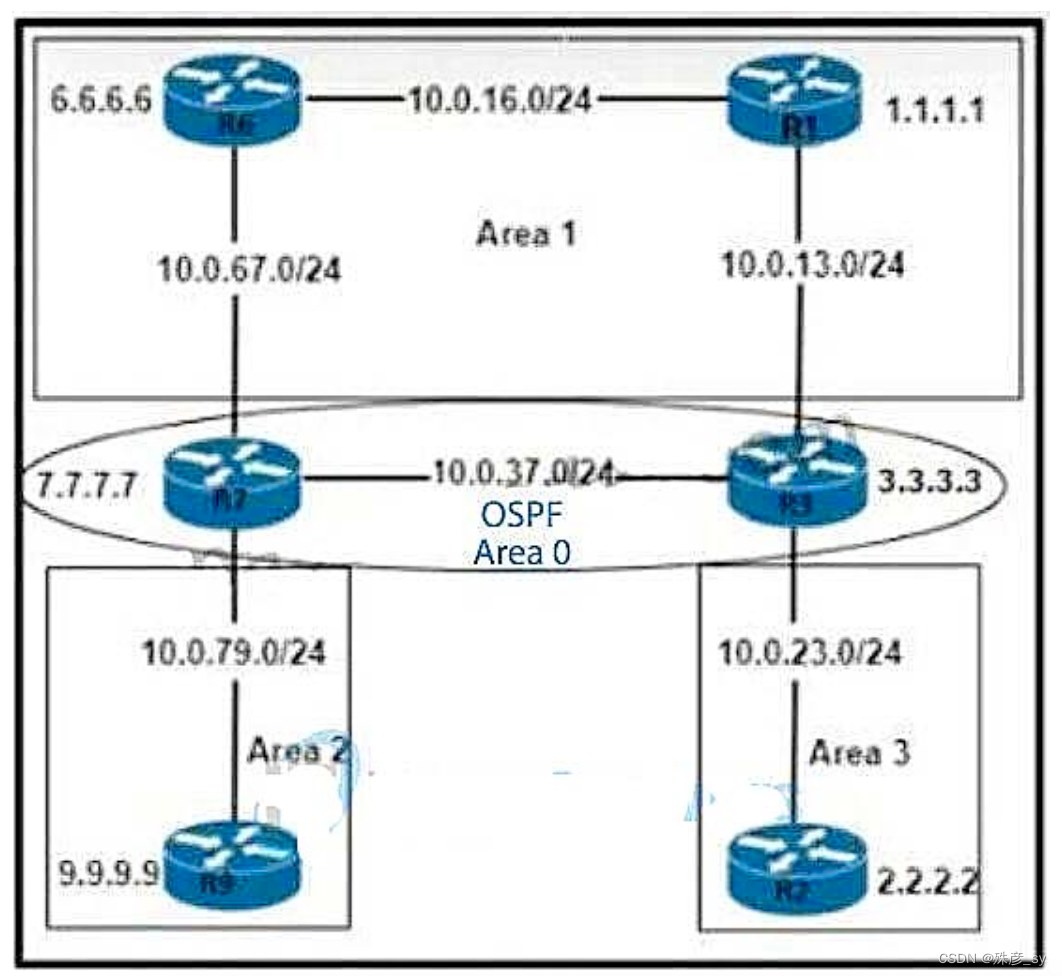
A. Apply a fitter list inbound on R2 and R9
B. Apply a filter list outbound on R3 and R7
C. Apply a filter list outbound on R7 only.
D. Apply a filter list inbound on R3 and R7
628、How can an engineer prevent basic replay attacks from people who try to brute force a system via REST API?
A. Add a timestamp to the request In the API header.
B. Use a password hash
C. Add OAuth to the request in the API header.
D. UseHTTPS
629、An administrator must enable Telnet access to Router X using the router username and password database for authentication. Which configuration should be
applied?
A. RouterX(config)# line aux 0
RouterX(config line)# password cisco
RouterX(config-line)# login
B. RouterX(config)# aaa new-model
RouterX(config)# aaa authentication login auth-list local
C. RouterX(config)# line vty 0 4
RouterX(config-line)# login local
RouterX(config-line)# end
D. RouterX(config)# line vty 0 4
RouterX(config-line)# login
RouterX(config-line)# end
630、When firewall capabilities are considered, which feature is found only in Cisco nextgeneration firewalls?
A. malware protection
B. stateful inspection
C. traffic filtering
D. active/standby high availability
631、
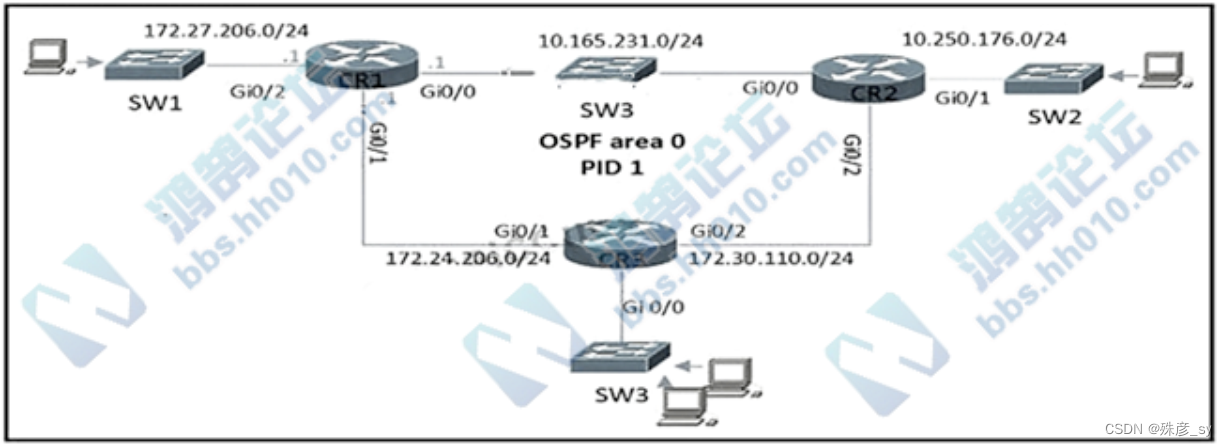
Refer to the exhibit. CR2 and CR3 ate configured with OSPF. Which configuration, when applied to CR1. allows CR1 to exchange OSPF Information with CR2 and
CR3 but not with other network devices or on new Interfaces that are added to CR1?
A. router ospf 1
network 0.0.0.0 255.255.255.255 area 0
passive-interface GigabitEthernet0/2
B. router ospf 1
network 10.165.231.0 0.0.0.255 area 0
network 172.27.206.0 0.0.0.255 area 0
network 172.24.206.0 0.0.0.255 area 0
C. interface Gi0/2
ip ospf 1 area 0
router ospf 1
passive-interface GigabitEthernet0/2
D. router ospf 1
network 10.0.0.0 0.255.255.255 area 0
network 172.16.0.0 0.15.255.255 area 0
passive-interface GigabitEthernet0/2
632、In which two ways does TCAM differ from CAM? (Choose two.)
A. CAM is used to make Layer 2 forwarding decisions, and TCAM is used for Layer 3 address lookups.
B. The MAC address table is contained in CAM, and ACL and QoS Information Is stored in TCAM.
C. CAM Is used by routers for IP address lookups, and TCAM is used to make Layer 2 forwarding decisions.
D. CAM is used for software switching mechanisms, and TCAM Is used for hardware switching mechanisms.
E. The MAC address table Is contained in TCAM, and ACL and QoS information is stored in CAM.
633、Refer to the exhibit. An engineer must configure HSRP for VLAN 1000 on SW2. The secondary switch must immediately take over the role of active router If the
interlink with the primary switch fails. Which command set completes this task?
SW2(config)#track 1000 interface gigabitEthernet0/0 line-protocol
SW2(config-track)#exit
SW2(config)#interface vlan 1000
SW2(config-if)#ip address 10.23.87.3 255.255.255.0
A. SW2(config-if)# standby version 2
SW2(config-if)# standby 1000 ip 10.23.87.1
SW2(config-if)# standby 1000 priority 95
SW2(config-if)# standby 1000 preelept
SW2(config-if)# standby 1000 track gigabitethernet0/0
B. SW2(config-if)# standby 1000 ip 10.23.87.1
SW2(config-if)# standby 1000 priority 95
SW2(config-if)# standby 1000 preempt
SW2(config-if)# standby 1000 track 1000
C. SW2(config-if)# standby version 2
SW2(config-if)# standby 1000 ip 10.23.87.1
SW2(config-if)# standby 1000 priority 95
SW2(config-if)# standby 1000 preempt
SW2(config-if)# standby 1000 track 1000
D. SW2(config if)# standby version 2
SW2(config-if)# standby 1000 ip 10.23.87.1
SW2(config-if)# standby 1000 priority 95
SW2(config-if)# standby 1000 track 1000
634、Refer to the exhibit. An engineer attempts to establish BGP peering between router CORP and two ISP routers. What is the root cause for the failure between CORP and ISP#2?
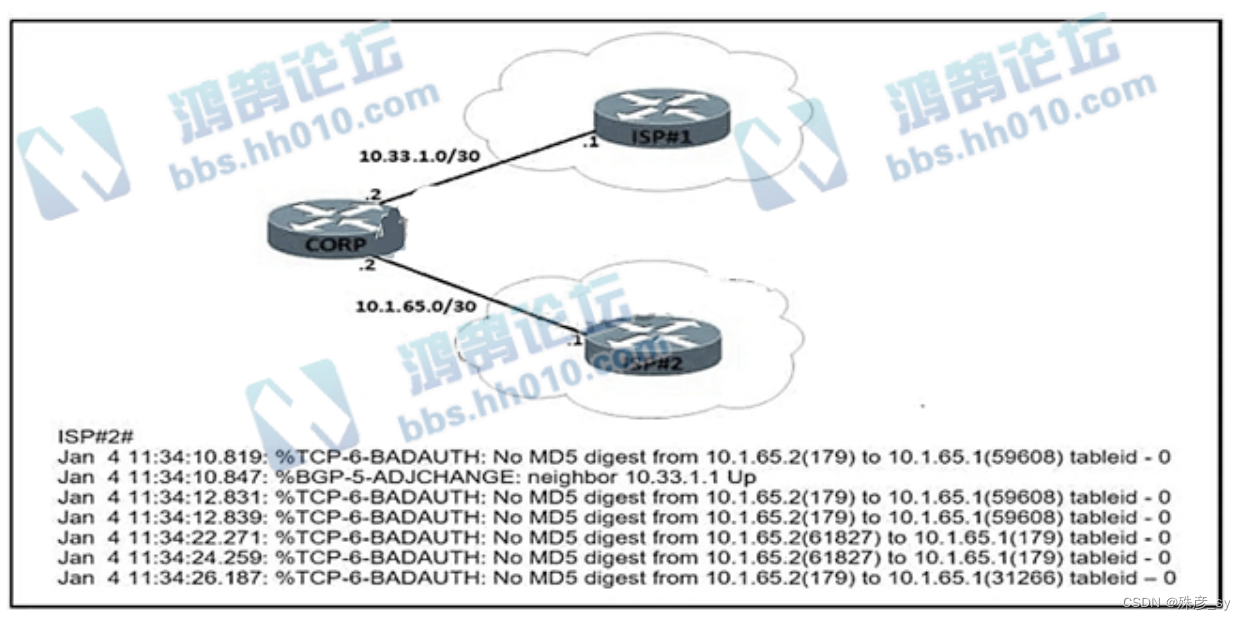
A. Router ISP#2 is configured to use SHA-1 authentication.
B. There is a password mismatch between router CORP and router ISP#2.
C. Router CORP is configured with an extended access control list.
D. MD5 authorization is configured incorrectly on router ISP#2.
635、
636、Refer to the exhibit Users cannot reach the web server at 192.168.100.1.What is the root cause for the failure?
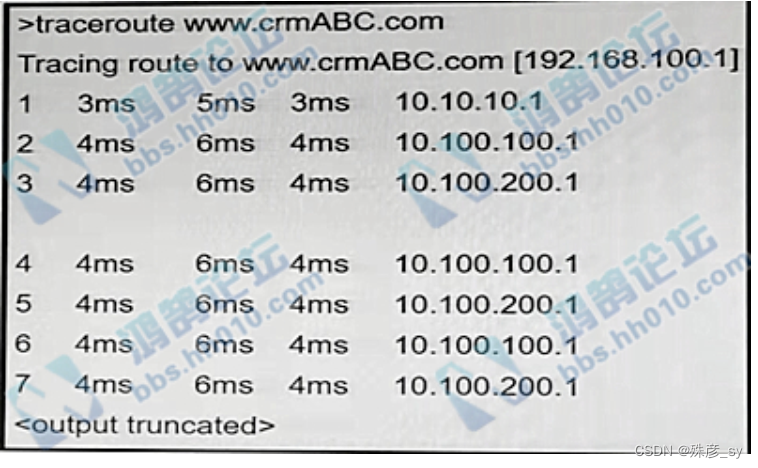
A. There is a loop in the path to the server.
B. The server is attempting to load balance between links 10.100.100.1 and 10.100.200.1
C. The server is out of service.
D. The gateway cannot translate the server domain name
637、An engineer must configure a multicast UDP jitter operation. Which configuration should be applied?
A. Router(confg)#ip sla 1Router(config )#udp-jitter 192.0.2.115 65051 num-packets 20
B. Router(config)#ip sla 1
Router(confg )#udp-jitter 192.0.2.115 65051
C. Router(config)#ip sla 1
Router(config)#udp jitter 239.1.1.1 65051 end-point list List source-ip 192.168.1.1
D. Router(config)#ip sla 1
Router(config)#udp jitter 10.0.0.1 source-ip 192.168.1.1
638、What is the API keys option for REST API authentication?
A. a username that is stored in the local router database
B. a predetermined string that is passed from client to server
C. a credential that is transmitted unencrypted
D. a one-time encrypted token
639、Refer to the exhibit. An administrator configures two switches with LACP EtherChannels, but packets are not being exchanged between the switches. What is the reason, and what fixes the issue?
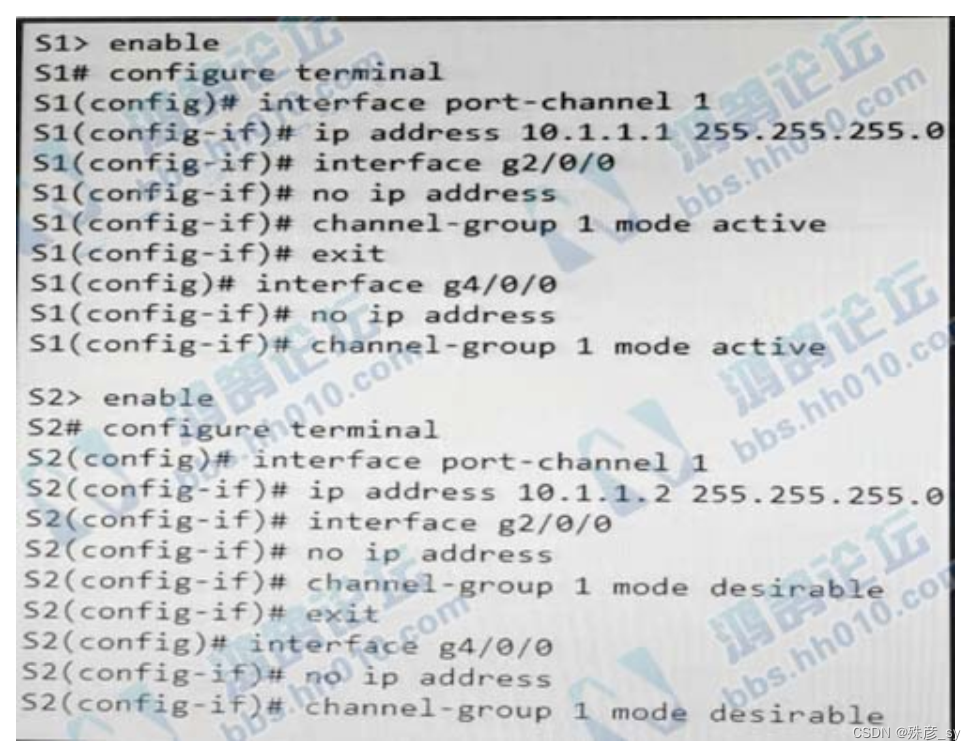
A. S1 is configured as PAgP. Change the channel group mode to desirable.
B. S2 is configured as LACP. Change the channel group mode to passive.
C. S2 is configured with PAgP. Change the channel group mode to active.
D. S1 is configured with LACP. Change the channel group mode to on
640、How must network management traffic be treated when defining QoS policies?
A. using the same marking as IP routing
B. as best effort
C. as delay-sensitive traffic in a low latency queue
D. using minimal bandwidth guarantee
641、Refer to the exhibit. Which configuration enables password checking on the console line, using only a password?
router#sh run I b line con
line con 0
password cisco
stopbits 1
line aux 0
stopbits 1
line vty 0 4
!
end
router#sh run | i username|aaa
no aaa new-model
username user password 0 user
router#
A. router(config)# line con 0
router(config-line)# login local
B. router(config)# line vty 0 4
router(config-line)# login
C. router(config)# line con 0
router(config-line)# login
D. router(config)# line con 0
router(config-line)# exec-timeout 0 0
642、Refer to the exhibit. An engineer must allow R1 to advertise the 192.168.1.0/24 network to R2. R1 must perform this action without sending OSPF packets to SW1. Which command set should be applied?

A. R1(confg)# router ospf 1
R1(config-router)# no passive-interface gig0/0
B. R1(config)# interface gig0/0
R1(config-f)# ip ospf hello-interval 65535
C. R1(config)# router ospf 1
R1(config-router)# passive-interface gig0/0
D. R1(config)# interface gig0/0
R1(config-if)# ip ospf hello-interval 0
643、Which IPv4 packet field carries the QoS IP classification marking?
A. ID
B. TTL
C. FCS
D. ToS
644、Refer to the exhibit. What does the response "204 No Content" mean for the REST API request?
![]()
A. The DELETE method is not supported.
B. Interface loopback 100 is not removed from the configuration.
C. Interface loopback 100 is not found in the configuration.
D. Interface loopback 100 is removed from the configuration
645、 Which beneft is realized by implementing SSO?
A. IP first hop redundancy
B. communication between different nodes for cluster setup
C. physical link redundancy
D. minimal network downtime following an RP switchover
646、How does Cisco Express Forwarding (CEF) switching differ from process switching on Cisco devices?
A. Cisco Express Forwarding (CEF) switching saves memory by sorting adjacency tables in dedicate memory on the line cards, and process switching stores all tables in the main memory
B. Cisco Express Forwarding (CEF) switching uses adjacency tables built by the CDP protocol, and process switching uses the routing table
C. Cisco Express Forwarding (CEF) switching uses dedicated hardware processors, and process switching uses the main processor
D. Cisco Express Forwarding (CEF) switching uses proprietary protocol based on IS-IS for MAC address lookup, and process switching uses in MAC address table
647、What is one difference between EIGRP and OSPF?
A. OSPF is a Cisco proprietary protocol, and EIGRP is an IETF open standard protocol.
B. OSPF uses the DUAL distance vector algorithm, and EIGRP uses the Dijkstra link-state algorithm
C. EIGRP uses the variance command lot unequal cost load balancing, and OSPF supports unequal cost balancing by default.
D. EIGRP uses the DUAL distance vector algorithm, and OSPF uses the Dijkstra link-state algorithm
648、Which function does a fabric wireless LAN controller perform In a Cisco SD-Access deployment?
A. manages fabric-enabled APs and forwards client registration and roaming information to the Control Plane Node
B. coordinates configuration of autonomous nonfabric access points within the fabric
C. performs the assurance engine role for both wired and wireless clients
D. is dedicated to onboard clients in fabric-enabled and nonfabric-enabled APs within the fabric
649、Refer to the exhibit. An engineer must set up connectivity between a campus aggregation layer and a branch office access layer. The engineer uses dynamic
trunking protocol to establish this connection, however, management traffic on VLAN1 is not passing. Which action resolves the issue and allow communication for
all configured VLANs?
SW2#
%CDP-4-NATIVE_VLAN_MISMATCH:NATIVE VLAN mismatch discovered on GigabitEthernet0/1(1),with SW1 GigabitEthernet 0/1(30).
SW2#
A. Allow all VLANs on the trunk links
B. Disable Spanning Tree for the native VLAN.
C. Configure the correct native VLAN on the remote interface
D. Change both interfaces to access ports
650、How must network management traffic be treated when defining QoS policies?
A. as delay-sensitive traffic in a low latency queue
B. using minimal bandwidth guarantee
C. using the same marking as IP routing
D. as best effort