Day08-K8S安全框架RBAC
- 0、昨日内容回顾:
- 1、K8S安全框架
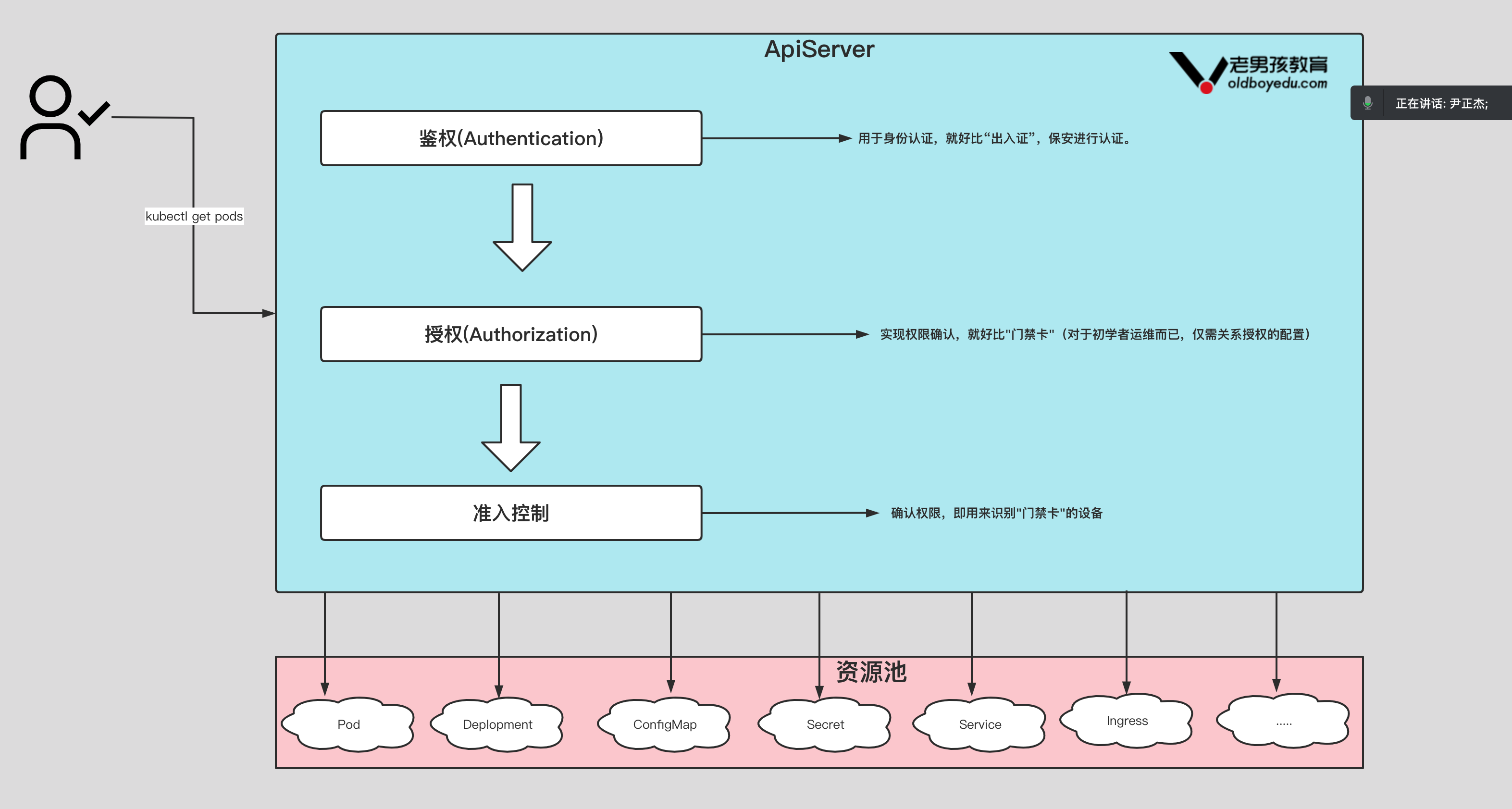
- 1.1 K8S的安全架构流程图解
- 1.2 RBAC
- 1.3 基于用户的权限管理实战
- 1.4 RBAC基于组的方式认证:
- 1.5 serviceaccount
- 2、持久卷与动态存储
- 2.1 传统基于存储卷的方式挂载的缺点
- 2.2 引入PV和PVC实现后端存储解耦
- 2.3 引入动态存储类实现自动创建PV
- 2.4 持久卷Persistent Volume(简称"PV")
- 2.5 持久卷声明Persistent Volume Claim(简称"PVC")
- 2.6 删除pvc验证pv的回收策略
- 2.7 临时更改PV的回收策略
- 2.8 动态存储类sc实战
- 3、Dashboard
- 3.1 安装dashboard
- 3.2 基于token登录案例
- 3.3 基于kubeconfig登录案例
0、昨日内容回顾:
-
污点:
- 格式:
KEY[=VALUE]:effect
effect:
NoScheduler
PreferNoScheduler
NoExecute
- 格式:
-
污点容忍:
-
节点选择器:
-
亲和性:
- 节点亲和性
- Pod亲和性
- Pod反亲和性
-
daemonSets
-
Pod驱逐
-
kubeadm集群的扩缩容
-
kube-proxy的工作切换,由iptables切换为ipvs
-
svc的NodePort类型的端口范围映射
今日内容预告:
-
K8S的安全框架;
-
Ingress
-
add-ons:
- dashboard
- metric-server -
helm
1、K8S安全框架
1.1 K8S的安全架构流程图解
1.2 RBAC

K8S的内置角色:
[root@k8s231 ~]# kubectl get clusterrole |grep -v system
NAME CREATED AT
admin 2024-06-12T01:48:20Z
cluster-admin 2024-06-12T01:48:20Z
edit 2024-06-12T01:48:20Z
flannel 2024-06-12T02:56:26Z
kubeadm:get-nodes 2024-06-12T01:48:22Z
view 2024-06-12T01:48:20Z
K8S内置集群角色:
cluster-admin:
超级管理员,有集群所有权限。
admin:
主要用于授权命名空间所有读写权限。
edit:
允许对大多数对象读写操作,不允许查看或者修改角色,角色绑定。
view:
允许对命名空间大多数对象只读权限,不允许查看角色,角色绑定和secret。
K8S预定好了四个集群角色供用户使用,使用"kubectl get clusterrole"查看,其中"systemd:"开头的为系统内部使用。
clusterrole查看,其中"system:"开头的为系统内部使用。
1.3 基于用户的权限管理实战
1.使用k8s ca签发客户端证书
1.1 解压证书管理工具包
[root@k8s231.oldboyedu.com ~]# wget http://192.168.15.253/Kubernetes/day08-/softwares/oldboyedu-cfssl.tar.gz
[root@k8s231.oldboyedu.com ~]# tar xf oldboyedu-cfssl.tar.gz -C /usr/bin/ && chmod +x /usr/bin/cfssl*
1.2 编写证书请求
[root@k8s231.oldboyedu.com user]# cat > ca-config.json <<EOF
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"kubernetes": {
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
],
"expiry": "87600h"
}
}
}
}
EOF
[root@k8s231.oldboyedu.com user]# cat > oldboyedu-csr.json <<EOF
{
"CN": "oldboyedu",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "k8s",
"OU": "System"
}
]
}
EOF
1.3 生成证书
[root@k8s231.oldboyedu.com user]# cfssl gencert -ca=/etc/kubernetes/pki/ca.crt -ca-key=/etc/kubernetes/pki/ca.key -config=ca-config.json -profile=kubernetes oldboyedu-csr.json | cfssljson -bare oldboyedu
2.生成kubeconfig授权文件
2.1 编写生成kubeconfig文件的脚本
cat > kubeconfig.sh <<'EOF'
# 配置集群
# --certificate-authority
# 指定K8s的ca根证书文件路径
# --embed-certs
# 如果设置为true,表示将根证书文件的内容写入到配置文件中,
# 如果设置为false,则只是引用配置文件,将kubeconfig
# --server
# 指定APIServer的地址。
# --kubeconfig
# 指定kubeconfig的配置文件名称
kubectl config set-cluster oldboyedu-linux \
--certificate-authority=/etc/kubernetes/pki/ca.crt \
--embed-certs=true \
--server=https://10.0.0.231:6443 \
--kubeconfig=oldboyedu-linux.kubeconfig
# 设置客户端认证
kubectl config set-credentials oldboyedu \
--client-key=oldboyedu-key.pem \
--client-certificate=oldboyedu.pem \
--embed-certs=true \
--kubeconfig=oldboyedu-linux.kubeconfig
# 设置默认上下文
kubectl config set-context linux \
--cluster=oldboyedu-linux \
--user=oldboyedu \
--kubeconfig=oldboyedu-linux.kubeconfig
# 设置当前使用的上下文
kubectl config use-context linux --kubeconfig=oldboyedu-linux.kubeconfig
EOF
2.2 生成kubeconfig文件
bash kubeconfig.sh
3.创建RBAC授权策略
3.1 创建rbac等配置文件
[root@k8s231.oldboyedu.com user]# cat rbac.yaml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: linux-role-reader
rules:
# API组,""表示核心组,该组包括但不限于"configmaps","nodes","pods","services"等资源.
- apiGroups: ["","apps/v1"]
# 资源类型,不支持写简称,必须写全称哟!!
# resources: ["pods","deployments"]
resources: ["pods","deployments","services"]
# 对资源的操作方法.
# verbs: ["get", "list"]
verbs: ["get", "list","delete"]
- apiGroups: ["","apps"]
resources: ["configmaps","secrets","daemonsets"]
verbs: ["get", "list"]
- apiGroups: [""]
resources: ["secrets"]
verbs: ["delete"]
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: oldboyedu-linux81-resources-reader
namespace: default
subjects:
# 主体类型
- kind: User
# 用户名
name: oldboyedu
apiGroup: rbac.authorization.k8s.io
roleRef:
# 角色类型
kind: Role
# 绑定角色名称
name: linux-role-reader
apiGroup: rbac.authorization.k8s.io
[root@k8s231.oldboyedu.com user]#
3.2 应用rbac授权
[root@k8s231.oldboyedu.com user]# kubectl apply -f rbac.yaml
3.3 访问测试
[root@k8s232.oldboyedu.com ~]# kubectl get po,cm,secret --kubeconfig=oldboyedu-linux.kubeconfig
NAME READY STATUS RESTARTS AGE
pod/oldboyedu-linux85-ds-xgp9v 1/1 Running 0 2m18s
pod/oldboyedu-linux85-wordpress-6b757777b7-l78gl 0/1 ImagePullBackOff 0 14m
pod/oldboyedu-linux85-wordpress-6b757777b7-n7m8d 0/1 ImagePullBackOff 0 14m
pod/oldboyedu-linux85-wordpress-6b757777b7-scqf4 0/1 ImagePullBackOff 0 14m
NAME DATA AGE
configmap/kube-root-ca.crt 1 8d
configmap/oldboyedu-linux85-games 1 6d17h
NAME TYPE DATA AGE
secret/default-token-4qknd kubernetes.io/service-account-token 3 8d
secret/es-https Opaque 3 6d16h
secret/linux85 kubernetes.io/dockerconfigjson 1 6d15h
secret/linux85-harbor kubernetes.io/dockerconfigjson 1 3d22h
[root@k8s232.oldboyedu.com ~]#
[root@k8s232.oldboyedu.com ~]# kubectl delete configmap/oldboyedu-linux85-games --kubeconfig=oldboyedu-linux.kubeconfig
Error from server (Forbidden): configmaps "oldboyedu-linux85-games" is forbidden: User "oldboyedu" cannot delete resource "configmaps" in API group "" in the namespace "default"
[root@k8s232.oldboyedu.com ~]#
[root@k8s232.oldboyedu.com ~]#
[root@k8s232.oldboyedu.com ~]# kubectl delete secret/linux85-harbor --kubeconfig=oldboyedu-linux.kubeconfig
secret "linux85-harbor" deleted
[root@k8s232.oldboyedu.com ~]#
1.4 RBAC基于组的方式认证:
CN: 代表用户,
O: 组。
1.使用k8s ca签发客户端证书
1.1 编写证书请求
[root@k8s231.oldboyedu.com groups]# cat > ca-config.json <<EOF
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"kubernetes": {
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
],
"expiry": "87600h"
}
}
}
}
EOF
[root@k8s231.oldboyedu.com groups]# cat > oldboyedu-csr.json <<EOF
{
"CN": "linux",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "oldboyedu",
"OU": "System"
}
]
}
EOF
1.3 生成证书
[root@k8s231.oldboyedu.com groups]# cfssl gencert -ca=/etc/kubernetes/pki/ca.crt -ca-key=/etc/kubernetes/pki/ca.key -config=ca-config.json -profile=kubernetes oldboyedu-csr.json | cfssljson -bare oldboyedu-groups
2.生成kubeconfig授权文件
2.1 编写生成kubeconfig文件的脚本
[root@k8s231.oldboyedu.com groups]# cat > kubeconfig.sh <<'EOF'
kubectl config set-cluster oldboyedu-linux-groups \
--certificate-authority=/etc/kubernetes/pki/ca.crt \
--embed-certs=true \
--server=https://10.0.0.231:6443 \
--kubeconfig=oldboyedu-linux.kubeconfig
# 设置客户端认证
kubectl config set-credentials oldboyedu \
--client-key=oldboyedu-groups-key.pem \
--client-certificate=oldboyedu-groups.pem \
--embed-certs=true \
--kubeconfig=oldboyedu-linux.kubeconfig
# 设置默认上下文
kubectl config set-context linux-groups \
--cluster=oldboyedu-linux-groups \
--user=oldboyedu \
--kubeconfig=oldboyedu-linux.kubeconfig
# 设置当前使用的上下文
kubectl config use-context linux-groups --kubeconfig=oldboyedu-linux.kubeconfig
EOF
2.2 生成kubeconfig文件
[root@k8s231.oldboyedu.com groups]# bash kubeconfig.sh
[root@k8s231.oldboyedu.com groups]# scp oldboyedu-linux.kubeconfig 10.0.0.233:~
3.创建RBAC授权策略
[root@k8s231.oldboyedu.com groups]# cat rbac.yaml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: default
name: linux-role-reader
rules:
# API组,""表示核心组,该组包括但不限于"configmaps","nodes","pods","services"等资源.
- apiGroups: ["","apps"]
# 资源类型,不支持写简称,必须写全称哟!!
resources: ["pods","nodes","services","deployments","configmaps"]
# 对资源的操作方法.
verbs: ["get", "watch", "list"]
---
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: oldboyedu-to-linux84-role-reader
namespace: default
subjects:
# 主体类型
- kind: Group
# 用户名
name: oldboyedu
apiGroup: rbac.authorization.k8s.io
roleRef:
# 角色类型
kind: Role
# 绑定角色名称
name: linux-role-reader
apiGroup: rbac.authorization.k8s.io
[root@k8s231.oldboyedu.com groups]#
[root@k8s231.oldboyedu.com groups]# kubectl apply -f rbac.yaml
4.验证权限
[root@k8s233.oldboyedu.com ~]# kubectl get po,cm,deploy --kubeconfig=oldboyedu-linux.kubeconfig
5.创建新用户加入oldboyedu组
5.1使用k8s ca签发客户端证书
5.1.1 编写证书请求
[root@k8s231.oldboyedu.com jasonyin]# cat > ca-config.json <<EOF
{
"signing": {
"default": {
"expiry": "87600h"
},
"profiles": {
"kubernetes": {
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
],
"expiry": "87600h"
}
}
}
}
EOF
[root@k8s231.oldboyedu.com jasonyin]# cat > oldboyedu-csr.json <<EOF
{
"CN": "jasonyin",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "oldboyedu",
"OU": "System"
}
]
}
EOF
5.1.2 生成证书
[root@k8s231.oldboyedu.com jasonyin]# cfssl gencert -ca=/etc/kubernetes/pki/ca.crt -ca-key=/etc/kubernetes/pki/ca.key -config=ca-config.json -profile=kubernetes oldboyedu-csr.json | cfssljson -bare oldboyedu-jasonyin
5.2 生成kubeconfig文件文件
5.2.1 编写生成kubeconfig文件的脚本
[root@k8s231.oldboyedu.com jasonyin]# cat > kubeconfig.sh <<'EOF'
kubectl config set-cluster oldboyedu-jasonyin \
--certificate-authority=/etc/kubernetes/pki/ca.crt \
--embed-certs=true \
--server=https://10.0.0.231:6443 \
--kubeconfig=oldboyedu-linux.kubeconfig
# 设置客户端认证
kubectl config set-credentials jasonyin \
--client-key=oldboyedu-jasonyin-key.pem \
--client-certificate=oldboyedu-jasonyin.pem \
--embed-certs=true \
--kubeconfig=oldboyedu-linux.kubeconfig
# 设置默认上下文
kubectl config set-context linux-jasonyin \
--cluster=oldboyedu-jasonyin \
--user=jasonyin \
--kubeconfig=oldboyedu-linux.kubeconfig
# 设置当前使用的上下文
kubectl config use-context linux-jasonyin --kubeconfig=oldboyedu-linux.kubeconfig
EOF
5.2.2 生成kubeconfig文件
[root@k8s231.oldboyedu.com jasonyin]# bash kubeconfig.sh
[root@k8s231.oldboyedu.com jasonyin]# scp oldboyedu-linux.kubeconfig 10.0.0.233:/tmp/
5.3 验证权限
[root@k8s233.oldboyedu.com ~]# kubectl get po,cm,deploy --kubeconfig=/tmp/oldboyedu-linux.kubeconfig
NAME READY STATUS RESTARTS AGE
pod/oldboyedu-linux85-ds-xgp9v 1/1 Running 0 50m
pod/oldboyedu-linux85-wordpress-6b757777b7-l78gl 0/1 ErrImagePull 0 62m
pod/oldboyedu-linux85-wordpress-6b757777b7-n7m8d 0/1 ImagePullBackOff 0 62m
pod/oldboyedu-linux85-wordpress-6b757777b7-scqf4 0/1 ImagePullBackOff 0 62m
NAME DATA AGE
configmap/kube-root-ca.crt 1 8d
configmap/oldboyedu-linux85-games 1 6d18h
NAME READY UP-TO-DATE AVAILABLE AGE
deployment.apps/oldboyedu-linux85-wordpress 0/3 3 0 17h
[root@k8s233.oldboyedu.com ~]#
1.5 serviceaccount
一般用于程序的用户名。
创建方式
- 响应式创建serviceAccounts
[root@k8s231.oldboyedu.com serviceAccount]# kubectl create serviceaccount oldboyedu-linux
serviceaccount/oldboyedu-linux created
[root@k8s231.oldboyedu.com serviceAccount]#
- 声明式创建serviceaccount
[root@k8s231.oldboyedu.com serviceaccounts]# cat 01-sa.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: oldboyedu-linux
[root@k8s231.oldboyedu.com serviceaccounts]#
- 授权容器中的Python程序对K8S API访问权限案例
授权容器中Python程序对K8S API访问权限步骤:
-
创建Role;
-
创建ServiceAccount;
-
将ServiceAccount于Role绑定;
-
为Pod指定自定义的SA;
-
进入容器执行Python程序测试操作K8S API权限;
-
基于服务账号授权案例
[root@k8s231.oldboyedu.com serviceAccount]# ll
total 16
-rw-r--r-- 1 root root 73 Apr 21 11:18 01-sa.yaml
-rw-r--r-- 1 root root 173 Apr 21 11:19 02-Role.yaml
-rw-r--r-- 1 root root 246 Apr 21 11:19 03-RoleBinding.yaml
-rw-r--r-- 1 root root 532 Apr 21 11:32 04-deploy.yaml
[root@k8s231.oldboyedu.com serviceAccount]#
[root@k8s231.oldboyedu.com serviceAccount]#
[root@k8s231.oldboyedu.com serviceAccount]# cat 01-sa.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: oldboyedu-python
[root@k8s231.oldboyedu.com serviceAccount]#
[root@k8s231.oldboyedu.com serviceAccount]# cat 02-Role.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: oldboyedu-pod-reader
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "watch", "list"]
[root@k8s231.oldboyedu.com serviceAccount]#
[root@k8s231.oldboyedu.com serviceAccount]# cat 03-RoleBinding.yaml
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: oldboyedu-sa-to-role
subjects:
- kind: ServiceAccount
name: oldboyedu-python
roleRef:
kind: Role
name: oldboyedu-pod-reader
apiGroup: rbac.authorization.k8s.io
[root@k8s231.oldboyedu.com serviceAccount]#
[root@k8s231.oldboyedu.com serviceAccount]# cat 04-deploy.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: oldboyedu-linux-web
spec:
replicas: 2
selector:
# matchLabels:
# apps: web
matchExpressions:
- key: apps
operator: Exists
template:
metadata:
labels:
apps: web
spec:
# 指定sa的名称,请确认该账号是有权限访问K8S集群的哟!
serviceAccountName: oldboyedu-python
containers:
- image: harbor.oldboyedu.com/dev/python:3.9.16
name: web
command: ["tail","-f","/etc/hosts"]
[root@k8s231.oldboyedu.com serviceAccount]#
- 编写Python程序,进入到"python"Pod所在的容器执行以下Python代码即可!
[root@k8s231.oldboyedu.com serviceAccount]# kubectl get pods
NAME READY STATUS RESTARTS AGE
oldboyedu-linux-web-7d68c9d554-2hppj 1/1 Running 0 9m52s
oldboyedu-linux-web-7d68c9d554-j8lh4 1/1 Running 0 9m52s
[root@k8s231.oldboyedu.com serviceAccount]#
[root@k8s231.oldboyedu.com serviceAccount]# kubectl exec -it oldboyedu-linux-web-7d68c9d554-2hppj -- sh
/ # cat > oldboyedu-python-k8s.py <<'EOF'
from kubernetes import client, config
with open('/var/run/secrets/kubernetes.io/serviceaccount/token') as f:
token = f.read()
# print(token)
configuration = client.Configuration()
configuration.host = "https://kubernetes" # APISERVER地址
configuration.ssl_ca_cert="/var/run/secrets/kubernetes.io/serviceaccount/ca.crt" # CA证书
configuration.verify_ssl = True # 启用证书验证
configuration.api_key = {"authorization": "Bearer " + token} # 指定Token字符串
client.Configuration.set_default(configuration)
apps_api = client.AppsV1Api()
core_api = client.CoreV1Api()
try:
print("###### Deployment列表 ######")
#列出default命名空间所有deployment名称
for dp in apps_api.list_namespaced_deployment("default").items:
print(dp.metadata.name)
except:
print("没有权限访问Deployment资源!")
try:
#列出default命名空间所有pod名称
print("###### Pod列表 ######")
for po in core_api.list_namespaced_pod("default").items:
print(po.metadata.name)
except:
print("没有权限访问Pod资源!")
EOF
/ #
/ # pip install kubernetes -i https://pypi.tuna.tsinghua.edu.cn/simple/ # 安装Python程序依赖的软件包并测试
/ #
/ # python3 oldboyedu-python-k8s.py

2、持久卷与动态存储
2.1 传统基于存储卷的方式挂载的缺点

2.2 引入PV和PVC实现后端存储解耦

2.3 引入动态存储类实现自动创建PV

2.4 持久卷Persistent Volume(简称"PV")
手动创建PV
1.准备nfs路径
[root@k8s231.oldboyedu.com ~]# mkdir -pv /oldboyedu/data/kubernetes/pv/linux/pv00{1,2,3}
(1)编写PV资源清单
[root@k8s231.oldboyedu.com persistentvolumes]# cat > 01-manual-pv.yaml <<'EOF'
apiVersion: v1
kind: PersistentVolume
metadata:
name: oldboyedu-linux-pv01
labels:
school: oldboyedu
spec:
# 声明PV的访问模式,常用的有"ReadWriteOnce","ReadOnlyMany"和"ReadWriteMany":
# ReadWriteOnce:(简称:"RWO")
# 只允许单个worker节点读写存储卷,但是该节点的多个Pod是可以同时访问该存储卷的。
# ReadOnlyMany:(简称:"ROX")
# 允许多个worker节点进行只读存储卷。
# ReadWriteMany:(简称:"RWX")
# 允许多个worker节点进行读写存储卷。
# ReadWriteOncePod:(简称:"RWOP")
# 该卷可以通过单个Pod以读写方式装入。
# 如果您想确保整个集群中只有一个pod可以读取或写入PVC,请使用ReadWriteOncePod访问模式。
# 这仅适用于CSI卷和Kubernetes版本1.22+。
accessModes:
- ReadWriteMany
# 声明存储卷的类型为nfs
nfs:
path: /oldboyedu/data/kubernetes/pv/linux/pv001
server: 10.0.0.231
# 指定存储卷的回收策略,常用的有"Retain"和"Delete"
# Retain:
# "保留回收"策略允许手动回收资源。
# 删除PersistentVolumeClaim时,PersistentVolume仍然存在,并且该卷被视为"已释放"。
# 在管理员手动回收资源之前,使用该策略其他Pod将无法直接使用。
# Delete:
# 对于支持删除回收策略的卷插件,k8s将删除pv及其对应的数据卷数据。
# Recycle:
# 对于"回收利用"策略官方已弃用。相反,推荐的方法是使用动态资源调配。
# 如果基础卷插件支持,回收回收策略将对卷执行基本清理(rm -rf /thevolume/*),并使其再次可用于新的声明。
persistentVolumeReclaimPolicy: Retain
# 声明存储的容量
capacity:
storage: 2Gi
---
apiVersion: v1
kind: PersistentVolume
metadata:
name: oldboyedu-linux-pv02
labels:
school: oldboyedu
spec:
accessModes:
- ReadWriteMany
nfs:
path: /oldboyedu/data/kubernetes/pv/linux/pv002
server: 10.0.0.231
persistentVolumeReclaimPolicy: Retain
capacity:
storage: 5Gi
---
apiVersion: v1
kind: PersistentVolume
metadata:
name: oldboyedu-linux-pv03
labels:
school: oldboyedu
spec:
accessModes:
- ReadWriteMany
nfs:
path: /oldboyedu/data/kubernetes/pv/linux/pv003
server: 10.0.0.231
persistentVolumeReclaimPolicy: Retain
capacity:
storage: 10Gi
EOF
(2)创建pv
[root@k8s231.oldboyedu.com persistentvolumes]# kubectl apply -f 01-manual-pv.yaml
(3)查看pv资源
[root@k8s231.oldboyedu.com persistentvolumes]# kubectl get pv
NAME :
pv的名称
CAPACITY :
pv的容量
ACCESS MODES:
pv的访问模式
RECLAIM POLICY:
pv的回收策略。
STATUS :
pv的状态。
CLAIM:
pv被哪个pvc使用。
STORAGECLASS
sc的名称。
REASON
pv出错时的原因。
AGE
创建的时间。
参考链接:
https://kubernetes.io/docs/concepts/storage/persistent-volumes/#access-modes
https://kubernetes.io/docs/concepts/storage/persistent-volumes/#reclaiming
2.5 持久卷声明Persistent Volume Claim(简称"PVC")
[root@k8s231.oldboyedu.com persistentvolumeclaims]# ll
total 8
-rw-r--r-- 1 root root 260 Apr 21 12:04 01-manual-pvc.yaml
-rw-r--r-- 1 root root 764 Apr 21 12:11 02-deploy-nginx-pvc.yaml
[root@k8s231.oldboyedu.com persistentvolumeclaims]#
[root@k8s231.oldboyedu.com persistentvolumeclaims]#
[root@k8s231.oldboyedu.com persistentvolumeclaims]#
[root@k8s231.oldboyedu.com persistentvolumeclaims]# cat 01-manual-pvc.yaml
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: oldboyedu-linux-pvc
spec:
# 声明资源的访问模式
accessModes:
- ReadWriteMany
# 声明资源的使用量
resources:
limits:
storage: 4Gi
requests:
storage: 3Gi
[root@k8s231.oldboyedu.com persistentvolumeclaims]#
[root@k8s231.oldboyedu.com persistentvolumeclaims]#
[root@k8s231.oldboyedu.com persistentvolumeclaims]# cat 02-deploy-nginx-pvc.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: oldboyedu-nginx-pvc
spec:
replicas: 2
selector:
matchExpressions:
- key: apps
operator: Exists
template:
metadata:
labels:
apps: nginx
spec:
volumes:
- name: data
# 声明是一个PVC类型
persistentVolumeClaim:
# 引用哪个PVC
claimName: oldboyedu-linux-pvc
containers:
- name: web
image: harbor.oldboyedu.com/web/apps:v1
volumeMounts:
- name: data
mountPath: /usr/share/nginx/html
---
apiVersion: v1
kind: Service
metadata:
name: oldboyedu-linux-nginx
spec:
type: NodePort
selector:
apps: nginx
ports:
- port: 80
targetPort: 80
nodePort: 30080
[root@k8s231.oldboyedu.com persistentvolumeclaims]#
[root@k8s231 persistentvolumeclaims]# kubectl get pods -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
oldboyedu-linux-web-7d68c9d554-bc2ch 1/1 Running 0 37m 10.100.2.15 k8s233.oldboyedu.com <none> <none>
oldboyedu-linux-web-7d68c9d554-qn99k 1/1 Running 0 37m 10.100.1.24 k8s232.oldboyedu.com <none> <none>
oldboyedu-nginx-pvc-65d849f8bd-5r7sb 1/1 Running 0 78s 10.100.1.25 k8s232.oldboyedu.com <none> <none>
oldboyedu-nginx-pvc-65d849f8bd-dzlv2 1/1 Running 0 78s 10.100.2.16 k8s233.oldboyedu.com <none> <none>
[root@k8s231 persistentvolumeclaims]# curl -I 10.100.1.25
HTTP/1.1 403 Forbidden
Server: nginx/1.20.1
Date: Thu, 11 Jul 2024 07:47:02 GMT
Content-Type: text/html
Content-Length: 153
Connection: keep-alive
[root@k8s231 persistentvolumeclaims]# kubectl exec -it oldboyedu-nginx-pvc-65d849f8bd-5r7sb -- sh
/ # cd /usr/share/nginx/html/
/usr/share/nginx/html # ls
/usr/share/nginx/html # echo "<h1>www.oldboyedu.com</h1>" > index.html
/usr/share/nginx/html #
[root@k8s231 persistentvolumeclaims]# curl -I 10.100.1.25
HTTP/1.1 200 OK
Server: nginx/1.20.1
Date: Thu, 11 Jul 2024 07:48:39 GMT
Content-Type: text/html
Content-Length: 27
Last-Modified: Thu, 11 Jul 2024 07:48:30 GMT
Connection: keep-alive
ETag: "668f8e4e-1b"
Accept-Ranges: bytes
2.6 删除pvc验证pv的回收策略
Retain:
"保留回收"策略允许手动回收资源,删除pvc时,pv仍然存在,并且该卷被视为"已释放(Released)"。
在管理员手动回收资源之前,使用该策略其他Pod将无法直接使用。
温馨提示:
(1)在k8s1.15.12版本测试时,删除pvc发现nfs存储卷的数据并不会被删除,pv也不会被删除;
Delete:
对于支持删除回收策略的卷插件,k8s将删除pv及其对应的数据卷数据。建议使用动态存储类(sc)实现,才能看到效果哟!
对于AWS EBS, GCE PD, Azure Disk, or OpenStack Cinder等存储卷会被删除。
温馨提示:
(1)在k8s1.15.12版本测试时,在不使用sc时,则删除pvc发现nfs存储卷的数据并不会被删除;
(2)在k8s1.15.12版本测试时,在使用sc后,可以看到删除效果哟;
Recycle:
对于"回收利用"策略官方已弃用。相反,推荐的方法是使用动态资源调配。而动态存储类已经不支持该类型啦!
如果基础卷插件支持,回收回收策略将对卷执行基本清理(rm -rf /thevolume/*),并使其再次可用于新的声明。
温馨提示,在k8s1.15.12版本测试时,删除pvc发现nfs存储卷的数据被删除。
2.7 临时更改PV的回收策略
(1)給pv打补丁
[root@k8s231.oldboyedu.com persistentvolumeclaims]# kubectl get pv,pvc
NAME CAPACITY ACCESS MODES RECLAIM POLICY STATUS CLAIM STORAGECLASS REASON AGE
persistentvolume/oldboyedu-linux-pv01 2Gi RWX Retain Available 157m
persistentvolume/oldboyedu-linux-pv02 5Gi RWX Retain Released default/oldboyedu-linux-pvc 157m
persistentvolume/oldboyedu-linux-pv03 10Gi RWX Retain Available 157m
[root@k8s231.oldboyedu.com persistentvolumeclaims]#
[root@k8s231.oldboyedu.com persistentvolumeclaims]#
[root@k8s231.oldboyedu.com persistentvolumeclaims]# kubectl patch pv oldboyedu-linux-pv03 -p '{"spec":{"persistentVolumeReclaimPolicy":"Recycle"}}'
persistentvolume/oldboyedu-linux-pv03 patched
[root@k8s231.oldboyedu.com persistentvolumeclaims]#
[root@k8s231.oldboyedu.com persistentvolumeclaims]# kubectl get pv,pvc
NAME CAPACITY ACCESS MODES RECLAIM POLICY STATUS CLAIM STORAGECLASS REASON AGE
persistentvolume/oldboyedu-linux-pv01 2Gi RWX Retain Available 157m
persistentvolume/oldboyedu-linux-pv02 5Gi RWX Retain Released default/oldboyedu-linux-pvc 157m
persistentvolume/oldboyedu-linux-pv03 10Gi RWX Recycle Available 157m
[root@k8s231.oldboyedu.com persistentvolumeclaims]#
(2)测试
[root@k8s231.oldboyedu.com persistentvolumeclaims]# cat 01-manual-pvc.yaml
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: oldboyedu-linux-pvc
spec:
# 声明资源的访问模式
accessModes:
- ReadWriteMany
# 声明资源的使用量
resources:
limits:
storage: 4Gi
requests:
storage: 3Gi
[root@k8s231.oldboyedu.com persistentvolumeclaims]#
[root@k8s231.oldboyedu.com persistentvolumeclaims]#
[root@k8s231.oldboyedu.com persistentvolumeclaims]# cat 02-deploy-nginx-pvc.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: oldboyedu-nginx-pvc
spec:
replicas: 2
selector:
matchExpressions:
- key: apps
operator: Exists
template:
metadata:
labels:
apps: nginx
spec:
volumes:
- name: data
# 声明是一个PVC类型
persistentVolumeClaim:
# 引用哪个PVC
claimName: oldboyedu-linux-pvc
containers:
- name: web
image: harbor.oldboyedu.com/web/apps:v1
volumeMounts:
- name: data
mountPath: /usr/share/nginx/html
---
apiVersion: v1
kind: Service
metadata:
name: oldboyedu-linux-nginx
spec:
type: NodePort
selector:
apps: nginx
ports:
- port: 80
targetPort: 80
nodePort: 30080
[root@k8s231.oldboyedu.com persistentvolumeclaims]#
2.8 动态存储类sc实战
(1)k8s组件原生并不支持NFS动态存储
https://kubernetes.io/docs/concepts/storage/storage-classes/#provisioner
(2)NFS不提供内部配置器实现动态存储,但可以使用外部配置器。
[root@k8s231.oldboyedu.com storageclasses]# yum -y install git
[root@k8s231.oldboyedu.com storageclasses]# git clone https://gitee.com/yinzhengjie/k8s-external-storage.git
(3)修改配置文件
[root@k8s231.oldboyedu.com storageclasses]# cd k8s-external-storage/nfs-client/deploy
[root@k8s231.oldboyedu.com deploy]# cat deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nfs-client-provisioner
labels:
app: nfs-client-provisioner
# replace with namespace where provisioner is deployed
namespace: default
spec:
replicas: 1
strategy:
type: Recreate
selector:
matchLabels:
app: nfs-client-provisioner
template:
metadata:
labels:
app: nfs-client-provisioner
spec:
serviceAccountName: nfs-client-provisioner
containers:
- name: nfs-client-provisioner
# image: quay.io/external_storage/nfs-client-provisioner:latest
image: registry.cn-hangzhou.aliyuncs.com/yinzhengjie-k8s/sc:nfs-client-provisioner
volumeMounts:
- name: nfs-client-root
mountPath: /persistentvolumes
env:
- name: PROVISIONER_NAME
value: oldboyedu/linux85
# value: fuseim.pri/ifs
- name: NFS_SERVER
value: 10.0.0.231
- name: NFS_PATH
value: /oldboyedu/data/kubernetes/sc
volumes:
- name: nfs-client-root
nfs:
server: 10.0.0.231
# path: /ifs/kubernetes
path: /oldboyedu/data/kubernetes/sc
[root@k8s231.oldboyedu.com deploy]#
(4)修改动态存储类的配置文件
[root@k8s231.oldboyedu.com deploy]# cat class.yaml
apiVersion: storage.k8s.io/v1
kind: StorageClass
metadata:
name: managed-nfs-storage
# provisioner: fuseim.pri/ifs # or choose another name, must match deployment's env PROVISIONER_NAME'
provisioner: oldboyedu/linux85
parameters:
# archiveOnDelete: "false"
archiveOnDelete: "true"
[root@k8s231.oldboyedu.com deploy]#
温馨提示:
生产环境建议设置回收策略为保留(Retain)。
cat > class.yaml <<'EOF'
apiVersion: storage.k8s.io/v1
kind: StorageClass
metadata:
name: managed-nfs-storage
# provisioner: fuseim.pri/ifs # or choose another name, must match deployment's env PROVISIONER_NAME'
provisioner: oldboyedu/linux
parameters:
# 注意哈,仅对"reclaimPolicy: Delete"时生效,如果回收策略是"reclaimPolicy: Retain",则无视此参数!
# 如果设置为false,删除数据后,不会在存储卷路径创建"archived-*"前缀的目录哟!
# archiveOnDelete: "false"
# 如果设置为true,删除数据后,会在存储卷路径创建"archived-*"前缀的目录哟
archiveOnDelete: "true"
# 声明PV回收策略,默认值为Delete
reclaimPolicy: Retain
EOF
(5)nfs服务器端创建sc需要共享路径
[root@k8s231.oldboyedu.com deploy]# mkdir -pv /oldboyedu/data/kubernetes/sc
(6)创建动态存储类
[root@k8s231.oldboyedu.com deploy]# kubectl apply -f class.yaml && kubectl get sc
(7)创建授权角色
[root@k8s231.oldboyedu.com deploy]# kubectl apply -f rbac.yaml
(8)部署nfs动态存储配置器
[root@k8s231.oldboyedu.com deploy]# kubectl apply -f deployment.yaml
(9)查看是否部署成功(如下图所示)
[root@k8s231.oldboyedu.com deploy]# kubectl get pods,sc
NAME READY STATUS RESTARTS AGE
pod/nfs-client-provisioner-c494888bb-rxvtf 1/1 Running 0 90s
NAME PROVISIONER RECLAIMPOLICY VOLUMEBINDINGMODE ALLOWVOLUMEEXPANSION AGE
storageclass.storage.k8s.io/managed-nfs-storage oldboyedu/linux85 Delete Immediate false 2m27s
[root@k8s231.oldboyedu.com deploy]#
(10)测试动态存储类
[root@k8s231.oldboyedu.com deploy]# cat test-claim.yaml
kind: PersistentVolumeClaim
apiVersion: v1
metadata:
name: test-claim-001
annotations:
volume.beta.kubernetes.io/storage-class: "managed-nfs-storage"
spec:
#storageClassName: managed-nfs-storage
accessModes:
- ReadWriteMany
resources:
requests:
storage: 20Mi
[root@k8s231.oldboyedu.com deploy]#
[root@k8s231.oldboyedu.com deploy]#
[root@k8s231.oldboyedu.com deploy]# cat test-pod.yaml
kind: Pod
apiVersion: v1
metadata:
name: test-pod
spec:
containers:
- name: test-pod
image: harbor.oldboyedu.com/web/apps:v1
command:
- "/bin/sh"
args:
- "-c"
- "touch /mnt/SUCCESS && exit 0 || exit 1"
volumeMounts:
- name: nfs-pvc
mountPath: "/mnt"
restartPolicy: "Never"
volumes:
- name: nfs-pvc
persistentVolumeClaim:
claimName: test-claim-001
[root@k8s231.oldboyedu.com deploy]#
# 报错问题
# k8s默认StorageClass,无法绑定pv,解决pvc一直处于“Pending”
# 查看 nfs-provisioner pod日志
# kubectl logs nfs-client-provisioner-5548ffc98f-b5h42 -n default
# 注:Kubernetes 1.20及以后版本废弃了 selfLink 所致。
# 解决方案
# 修改kube-apiserver.yaml参数
# vim /etc/kubernetes/manifests/kube-apiserver.yaml
# 添加 - --feature-gates=RemoveSelfLink=false 后重启apiserver
# systemctl daemon-reload
# systemctl restart kubelet
[root@k8s231 deploy]# kubectl describe pod test-pod
......
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Warning FailedScheduling 21s default-scheduler 0/3 nodes are available: 3 pod has unbound immediate PersistentVolumeClaims.
Warning FailedScheduling 18s (x1 over 20s) default-scheduler 0/3 nodes are available: 3 pod has unbound immediate PersistentVolumeClaims.
[root@k8s231 deploy]# kubectl get pv,pvc
NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
persistentvolumeclaim/test-claim Pending managed-nfs-storage 15h
[root@k8s231 deploy]# kubectl get pv
No resources found
[root@k8s231 deploy]# kubectl get pvc
NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
test-claim Pending managed-nfs-storage 15h
[root@k8s231 deploy]# kubectl describe pvc test-claim
......
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal ExternalProvisioning 15h (x43 over 15h) persistentvolume-controller waiting for a volume to be created, either by external provisioner "oldboyedu/linux85" or manually created by system administrator
Normal ExternalProvisioning 79s (x165 over 26m) persistentvolume-controller waiting for a volume to be created, either by external provisioner "oldboyedu/linux85" or manually created by system administrator
[root@k8s231 deploy]# vim /etc/kubernetes/manifests/kube-apiserver.yaml
......
- --etcd-servers=https://127.0.0.1:2379
- --feature-gates=RemoveSelfLink=false # 添加这一条
- --kubelet-client-certificate=/etc/kubernetes/pki/apiserver-kubelet-client.crt
......
[root@k8s231 deploy]# systemctl daemon-reload
[root@k8s231 deploy]# systemctl restart kubelet
[root@k8s231 deploy]# kubectl get pvc
NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
test-claim Pending managed-nfs-storage 15h
[root@k8s231 deploy]# kubectl get pods -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nfs-client-provisioner-765d9bb488-pgnf7 1/1 Running 0 21m 10.100.2.23 k8s233.oldboyedu.com <none> <none>
oldboyedu-linux-web-7d68c9d554-bc2ch 1/1 Running 1 (43m ago) 18h 10.100.2.21 k8s233.oldboyedu.com <none> <none>
oldboyedu-linux-web-7d68c9d554-qn99k 1/1 Running 1 (43m ago) 18h 10.100.1.27 k8s232.oldboyedu.com <none> <none>
test-pod 0/1 Completed 0 18m 10.100.1.28 k8s232.oldboyedu.com <none> <none>
[root@k8s231 deploy]# ll /oldboyedu/data/kubernetes/sc/
总用量 0
drwxrwxrwx 2 root root 21 2024-07-12 09:12 default-test-claim-pvc-13421638-733e-4fd3-bf9a-f2bb78a77c5a
[root@k8s231 deploy]# kubectl get pv,pvc
NAME CAPACITY ACCESS MODES RECLAIM POLICY STATUS CLAIM STORAGECLASS REASON AGE
persistentvolume/pvc-13421638-733e-4fd3-bf9a-f2bb78a77c5a 1Mi RWX Delete Bound default/test-claim managed-nfs-storage 105s
NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
persistentvolumeclaim/test-claim Bound pvc-13421638-733e-4fd3-bf9a-f2bb78a77c5a 1Mi RWX managed-nfs-storage 15h
3、Dashboard
它是K8S集群管理的一个GUI的WebUI实现,它是一个k8s附加组件,所以需要单独部署。
我们可以以图形化的方式创建k8s资源。
GitHub地址:
https://github.com/kubernetes/dashboard#kubernetes-dashboard
3.1 安装dashboard
(1)下载dashboard资源清单
[root@k8s231.oldboyedu.com dashabord]# wget -O k8s_1_23-dashabord.yaml https://raw.githubusercontent.com/kubernetes/dashboard/v2.5.1/aio/deploy/recommended.yaml
[root@k8s231.oldboyedu.com dashabord]#
(2)修改資源清单
[root@k8s231.oldboyedu.com dashabord]# vim k8s_1_23-dashabord.yaml
...
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
# 修改svc的类型
type: NodePort
ports:
- port: 443
targetPort: 8443
# 添加端口映射
nodePort: 8443
selector:
k8s-app: kubernetes-dashboard
(3)安装dashboard
[root@k8s231.oldboyedu.com dashabord]# kubectl apply -f k8s_1_23-dashabord.yaml
(4)访问dashboard页面
https://10.0.0.231:8443/
# 鼠标单机空白处,输入以下代码:
thisisunsafe

3.2 基于token登录案例
(1)编写K8S的yaml资源清单文件
[root@k8s231.oldboyedu.com dashabord]# cat > oldboyedu-dashboard-rbac.yaml <<'EOF'
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
# 创建一个名为"oldboyedu"的账户
name: oldboyedu
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
k8s-app: kubernetes-dashboard
name: oldboyedu-dashboard
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
# 既然绑定的是集群角色,那么类型也应该为"ClusterRole",而不是"Role"哟~
kind: ClusterRole
# 关于集群角色可以使用"kubectl get clusterrole | grep admin"进行过滤哟~
name: cluster-admin
subjects:
- kind: ServiceAccount
# 此处要注意哈,绑定的要和我们上面的服务账户一致哟~
name: oldboyedu
namespace: kube-system
EOF
(2)创建资源清单
[root@k8s231.oldboyedu.com dashabord]# kubectl apply -f oldboyedu-dashboard-rbac.yaml
(3)查看sa资源的Tokens名称
[root@k8s231.oldboyedu.com dashabord]# kubectl describe serviceaccounts -n kube-system oldboyedu | grep Tokens
Tokens: oldboyedu-token-5f5qf
[root@k8s231.oldboyedu.com dashabord]#
(4)根据上一步的token名称的查看token值
[root@k8s231.oldboyedu.com dashabord]# kubectl -n kube-system describe secrets oldboyedu-token-5f5qf
Name: oldboyedu-token-5f5qf
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: oldboyedu
kubernetes.io/service-account.uid: e807b664-59c9-4b2e-a2d9-50b55faa108a
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1099 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6ImxyU0dWc1lPaG1yeUFtUGdkR2Q5WE5lbjVtb2hsWEMzZ0Q3MGREMEpkX2sifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJvbGRib3llZHUtdG9rZW4td3dobGYiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoib2xkYm95ZWR1Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiZTgwN2I2NjQtNTljOS00YjJlLWEyZDktNTBiNTVmYWExMDhhIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmUtc3lzdGVtOm9sZGJveWVkdSJ9.rxeYxmgiNJkz7jdiwjTdWqvROtSa0m7CyHgfxNZHHS_GkzhgoZHjhgbrnKs5nyOpBl6ncl210lXIoUAgIKXuH6nAWc8TSEeZzmTkMTKcui7sOSR8h3EDdK0AEXk4ltZccH0uOPa1MUj5PL-TcxYYxuRLxhEza2ChGdnMnsBef2QRFzVcz38ZcY52jgeBVUZ1_tEgtnjqjY6PGahwRokZ_lSvNPHua4fUfA4QBZh3p6-59INFpL8Wiv0ekH9pvRPhc6UOdhrkhuaUCHfIQYoRRR_8g1Jy6-AFNqC5S73nfgkUVycsoP7ULJAFWg1BWQuoOoNKQ3t-c_GYYk5N1jefdQ
[root@k8s231.oldboyedu.com dashabord]#
(5)登录dashboard的WebUI
使用上一步的Token值登录即可(注意,复制时不要有换行哟)

3.3 基于kubeconfig登录案例
(1)编写生成kubeconf的配置文件的脚本
cat > oldboyedu-generate-context-conf.sh <<'EOF'
#!/bin/bash
# auther: Jason Yin
# 获取secret的名称
SECRET_NAME=`kubectl get secrets -n kube-system | grep oldboyedu | awk {'print $1'}`
# 指定API SERVER的地址
API_SERVER=k8s231.oldboyedu.com:6443
# 指定kubeconfig配置文件的路径名称
KUBECONFIG_NAME=/root/oldboyedu-k8s-dashboard-admin.kubeconfig
# 获取oldboyedu用户的tocken
OLDBOYEDU_TOCKEN=`kubectl get secrets -n kube-system $SECRET_NAME -o jsonpath={.data.token} | base64 -d`
# 在kubeconfig配置文件中设置群集项
kubectl config set-cluster oldboyedu-k8s-dashboard-cluster --server=$API_SERVER --kubeconfig=$KUBECONFIG_NAME
# 在kubeconfig中设置用户项
kubectl config set-credentials oldboyedu-k8s-dashboard-user --token=$OLDBOYEDU_TOCKEN --kubeconfig=$KUBECONFIG_NAME
# 配置上下文,即绑定用户和集群的上下文关系,可以将多个集群和用户进行绑定哟~
kubectl config set-context oldboyedu-admin --cluster=oldboyedu-k8s-dashboard-cluster --user=oldboyedu-k8s-dashboard-user --kubeconfig=$KUBECONFIG_NAME
# 配置当前使用的上下文
kubectl config use-context oldboyedu-admin --kubeconfig=$KUBECONFIG_NAME
EOF
(2)运行上述脚本并下载上一步生成的配置文件到桌面,如上图所示,选择并选择该文件进行登录
[root@k8s231 dashabord]# bash oldboyedu-generate-context-conf.sh
Cluster "oldboyedu-k8s-dashboard-cluster" set.
User "oldboyedu-k8s-dashboard-user" set.
Context "oldboyedu-admin" created.
Switched to context "oldboyedu-admin".
[root@k8s231 dashabord]# ll /root
总用量 242168
-rw-------. 1 root root 1354 2024-02-18 16:37 anaconda-ks.cfg
drwxr-xr-x 6 root root 82 2024-06-25 17:14 dockerfile
-rw-r--r-- 1 root root 8260608 2023-06-14 10:56 flannel-cni-plugin.tar
-rw-r--r-- 1 root root 65180672 2023-06-14 10:55 flannel.tar
-rw-r--r-- 1 root root 4459 2024-02-18 12:59 kube-flannel.yml
-rw-r--r-- 1 root root 3819537 2024-02-18 13:21 oldboyedu-cfssl.tar.gz
drwxr-xr-x 2 root root 4096 2023-04-12 15:26 oldboyedu-docker-rpm-20.10
-rw-r--r-- 1 root root 101239922 2024-02-18 13:03 oldboyedu-docker-rpm-20_10_24.tar.gz
-rw------- 1 root root 1287 2024-07-12 10:44 oldboyedu-k8s-dashboard-admin.kubeconfig
drwxr-xr-x 2 root root 4096 2023-04-12 16:35 oldboyedu-kubeadmin-rpm-1_23_17
-rw-r--r-- 1 root root 69440057 2024-02-18 13:02 oldboyedu-kubeadmin-rpm-1_23_17.tar.gz
-rw-r--r-- 1 root root 326 2024-02-18 12:59 oldboyedu-linux85-ds.yaml
[root@k8s231 ~]# sz oldboyedu-k8s-dashboard-admin.kubeconfig
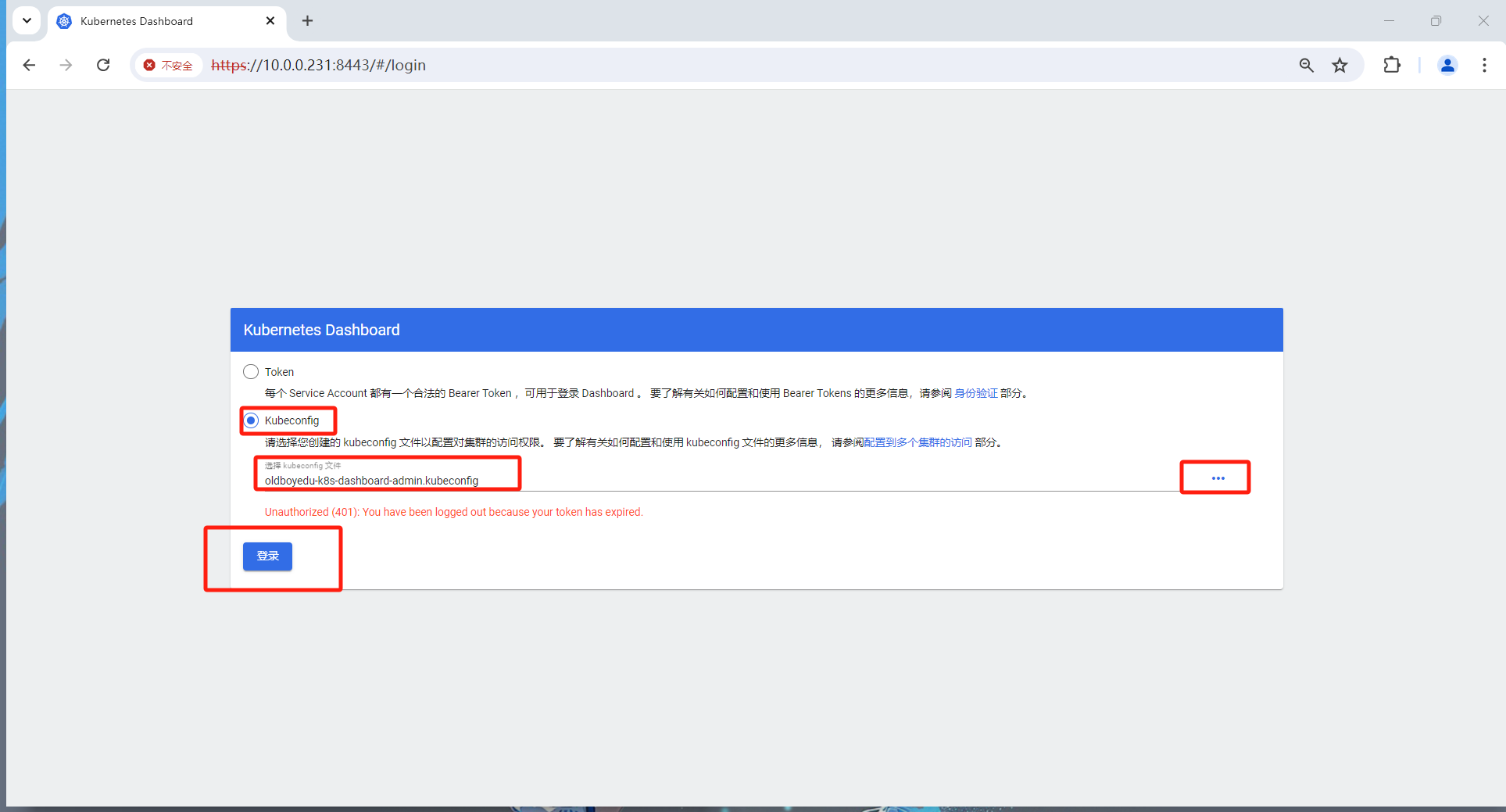
(3)进入到dashboard的WebUI
如下图所示,我们可以访问任意的Pod,当然也可以直接进入到有终端的容器哟
周末作业:
- 完成课堂的所有练习并整理思维导图;
- 使用kubectl管理2套以上K8S集群;
- 将"jasonyin2020/oldboyedu-games:v0.1"游戏镜像拆分成5个游戏镜像,要求使用一下几种资源:
- deployment
- configMap
- secret
- pv
- pvc
- sc
- dashabord
…
扩展作业:
- 将"考试问卷系统"部署k8s集群;
- 部署kubesphere系统,并完成作业3的部署。
参考文档:
https://kubesphere.io/zh/ - 完成istio的服务部署;











![[陇剑杯 2021]wifi WP](https://i-blog.csdnimg.cn/direct/f0a94071ecf64ec1b22d84c0b926484d.png)