亚马逊相关文档
1、创建适用于 Amazon S3的IAM策略
创建存储桶amazoneks
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3express:CreateSession",
"Resource": "arn:aws:s3express:ap-east-1:XXXXX:bucket/amazoneks--ap-east-1--x-s3"
}
]
}
创建策略
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "MountpointFullBucketAccess",
"Effect": "Allow",
"Action": [
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::amazoneks"
]
},
{
"Sid": "MountpointFullObjectAccess",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:PutObject",
"s3:AbortMultipartUpload",
"s3:DeleteObject"
],
"Resource": [
"arn:aws:s3:::amazoneks/*"
]
}
]
}
策略命名AmazonS3CSIDriverPolicy
2、创建 IAM 角色
在 Select trusted entity(选择受信任的实体)页面上操作
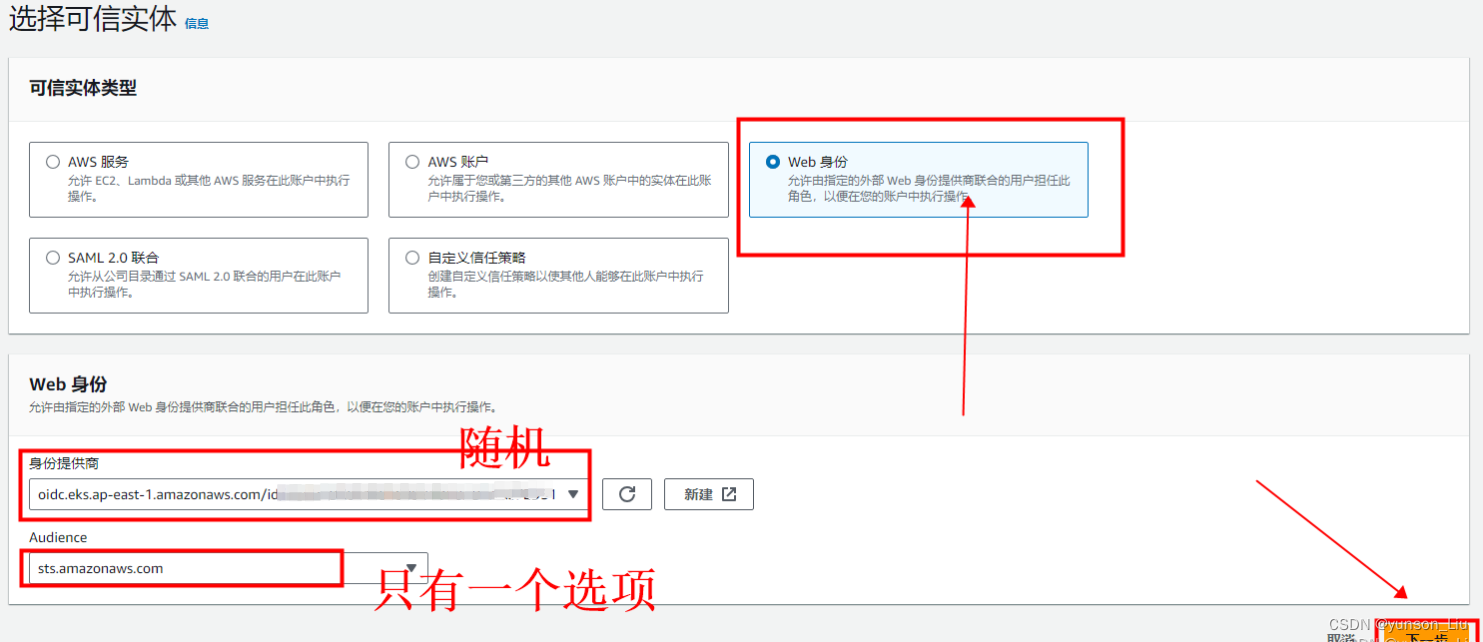
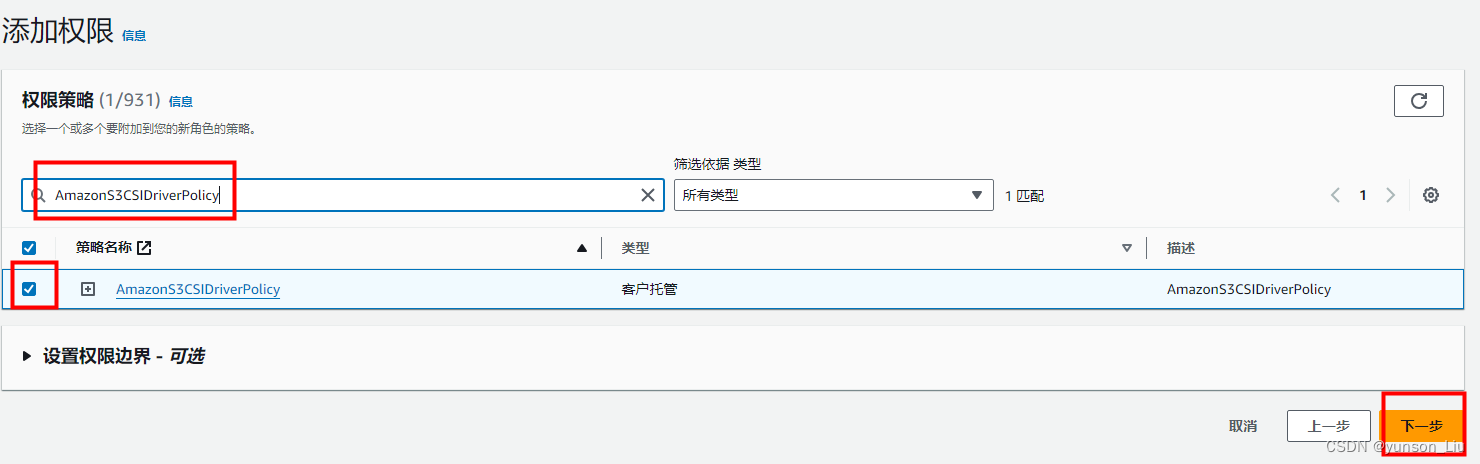
在 Add permissions(添加权限)页面上筛选刚刚创建的AmazonS3CSIDriverPolicy操作
在 Name, review, and create(命名、查看和创建)页面命名AmazonEKS_S3_CSI_DriverRole
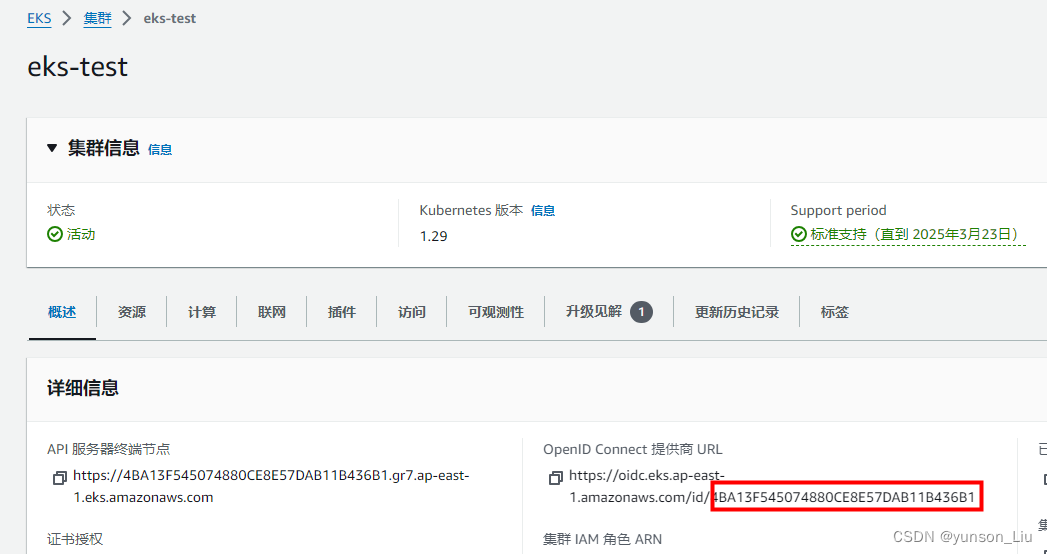
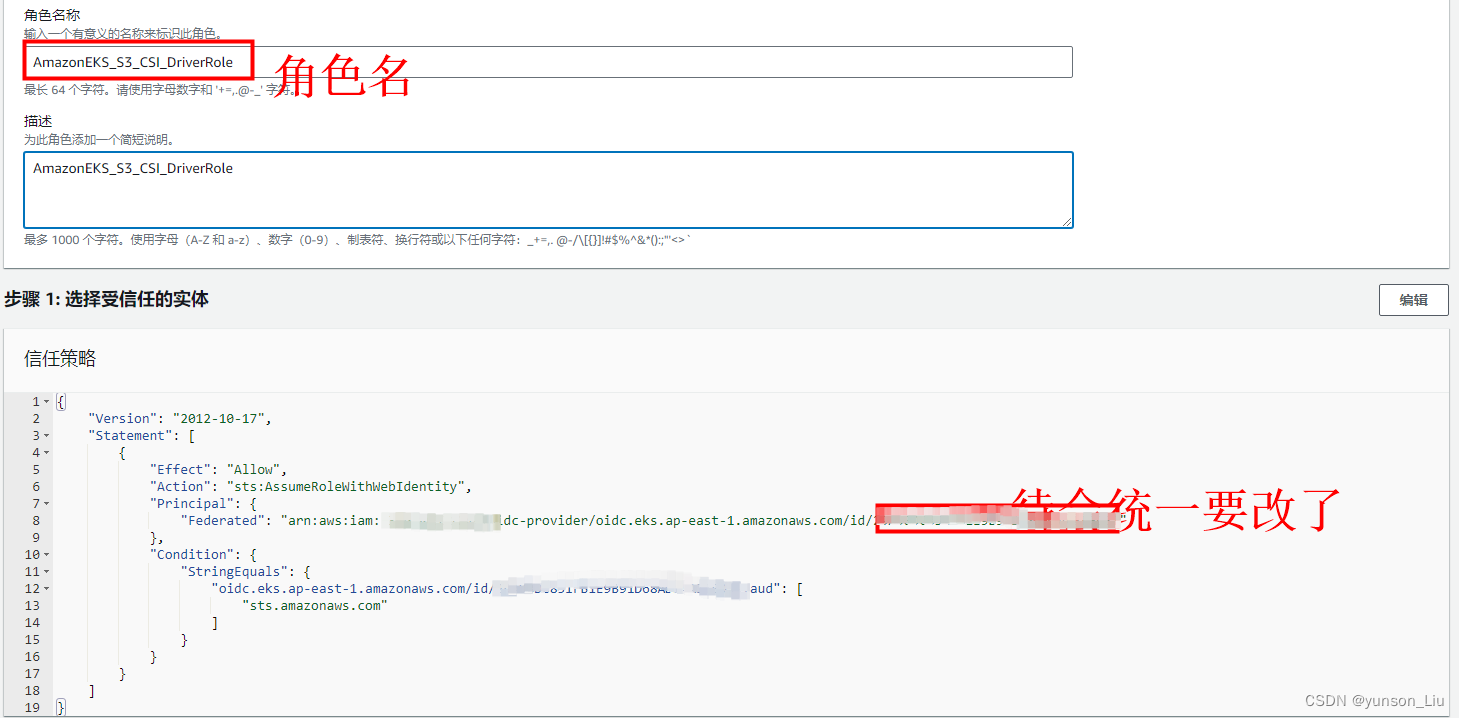
编辑受信任实体
"oidc.eks.region-code.amazonaws.com/id/EXAMPLED539D4633E53DE1B71EXAMPLE:aud": "sts.amazonaws.com"
- 在上一行末尾添加逗号,然后在逗号后添加下一行。将 region-code 替换为集群所在的 AWS 区域。将 EXAMPLED539D4633E53DE1B71EXAMPLE 替换为集群的 OIDC 提供商 ID。
"oidc.eks.region-code.amazonaws.com/id/EXAMPLED539D4633E53DE1B71EXAMPLE:sub": "system:serviceaccount:kube-system:s3-csi-*"
- 将 Condition 运算符从 “StringEquals” 变更为 “StringLike”。
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "arn:aws:iam::XXXXXXX:oidc-provider/oidc.eks.ap-east-1.amazonaws.com/id/4BA13F545074880CE8E57DAB11B436B1"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringLike": {
"oidc.eks.ap-east-1.amazonaws.com/id/4BA13F545074880CE8E57DAB11B436B1:aud": "sts.amazonaws.com",
"oidc.eks.ap-east-1.amazonaws.com/id/4BA13F545074880CE8E57DAB11B436B1:sub": "system:serviceaccount:kube-system:s3-csi-*"
}
}
}
]
}
3、安装适用于 Amazon S3 的 Mountpoint CSI 驱动程序
eksctl create addon --name aws-mountpoint-s3-csi-driver --cluster eks-test --service-account-role-arn arn:aws:iam::XXXXXXX:role/AmazonEKS_S3_CSI_DriverRole --force
2024-05-04 16:30:24 [ℹ] Kubernetes version "1.29" in use by cluster "eks-test"
2024-05-04 16:30:24 [ℹ] using provided ServiceAccountRoleARN "arn:aws:iam::XXXXXXX:role/AmazonEKS_S3_CSI_DriverRole"
2024-05-04 16:30:24 [ℹ] creating addon
2024-05-04 16:31:20 [ℹ] addon "aws-mountpoint-s3-csi-driver" active
查询驱动
# kubectl describe csidriver s3.csi.aws.com
Name: s3.csi.aws.com
Namespace:
Labels: app.kubernetes.io/component=csi-driver
app.kubernetes.io/instance=aws-mountpoint-s3-csi-driver
app.kubernetes.io/managed-by=EKS
app.kubernetes.io/name=aws-mountpoint-s3-csi-driver
Annotations: <none>
API Version: storage.k8s.io/v1
Kind: CSIDriver
Metadata:
Creation Timestamp: 2024-05-04T16:30:26Z
Managed Fields:
API Version: storage.k8s.io/v1
Fields Type: FieldsV1
fieldsV1:
f:metadata:
f:labels:
f:app.kubernetes.io/component:
f:app.kubernetes.io/instance:
f:app.kubernetes.io/managed-by:
f:app.kubernetes.io/name:
f:spec:
f:attachRequired:
Manager: eks
Operation: Apply
Time: 2024-05-04T16:30:26Z
Resource Version: 7490
UID: 1c003853-4dba-42c4-8998-ec9889a99e75
Spec:
Attach Required: false
Fs Group Policy: ReadWriteOnceWithFSType
Pod Info On Mount: false
Requires Republish: false
Se Linux Mount: false
Storage Capacity: false
Volume Lifecycle Modes:
Persistent
Events: <none>
3、创建S3 pv
pv yaml文件
# cat s3-pv.yaml
apiVersion: v1
kind: PersistentVolume
metadata:
name: s3-pv
spec:
capacity:
storage: 120Gi # ignored, required
accessModes:
- ReadWriteMany # supported options: ReadWriteMany / ReadOnlyMany
mountOptions:
- allow-delete
- region ap-east-1
csi:
driver: s3.csi.aws.com # required
volumeHandle: s3-csi-driver-volume
volumeAttributes:
bucketName: amazoneks
创建pv
[root@ip-10-0-7-211 ~]# kubectl apply -f s3-pv.yaml
persistentvolume/s3-pv created
查询pv
# kubectl get pv s3-pv
NAME CAPACITY ACCESS MODES RECLAIM POLICY STATUS CLAIM STORAGECLASS VOLUMEATTRIBUTESCLASS REASON AGE
s3-pv 120Gi RWX Retain Bound default/s3-claim <unset> 2m30s
4、创建S3 pvc
pvc yaml文件
# cat s3-pvc.yaml
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: s3-claim
spec:
accessModes:
- ReadWriteMany # supported options: ReadWriteMany / ReadOnlyMany
storageClassName: "" # required for static provisioning
resources:
requests:
storage: 120Gi # ignored, required
volumeName: s3-pv
创建pv3
[root@ip-10-0-7-211 ~]# kubectl apply -f s3-pvc.yaml
persistentvolumeclaim/s3-claim created
查询pvc
# kubectl get pvc s3-claim
NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS VOLUMEATTRIBUTESCLASS AGE
s3-claim Bound s3-pv 120Gi RWX <unset> 5m48s
5、验证
nginx yaml配置文件
volumeMounts:
- mountPath: /usr/share/nginx/html/
name: volume-xankc
subPath: html
volumes:
- name: volume-xankc
persistentVolumeClaim:
claimName: s3-claim
此时在S3上看得到我们的内容
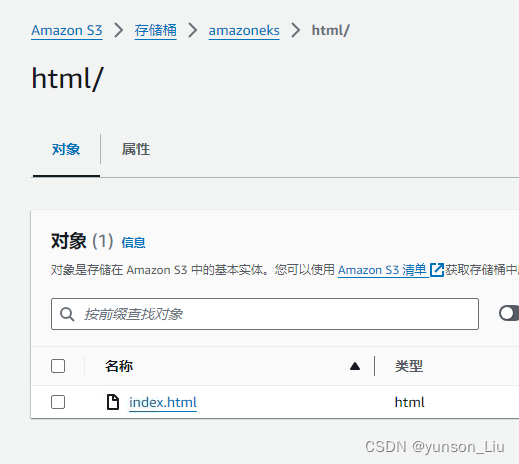
tomcat测试
挂载日志文件,我们在S3上查看是否有新文件生成即可
volumeMounts:
- mountPath: /usr/local/tomcat/logs
name: volume-zcb56
subPath: htm/tomcat/
volumes:
- name: volume-zcb56
persistentVolumeClaim:
claimName: s3-claim
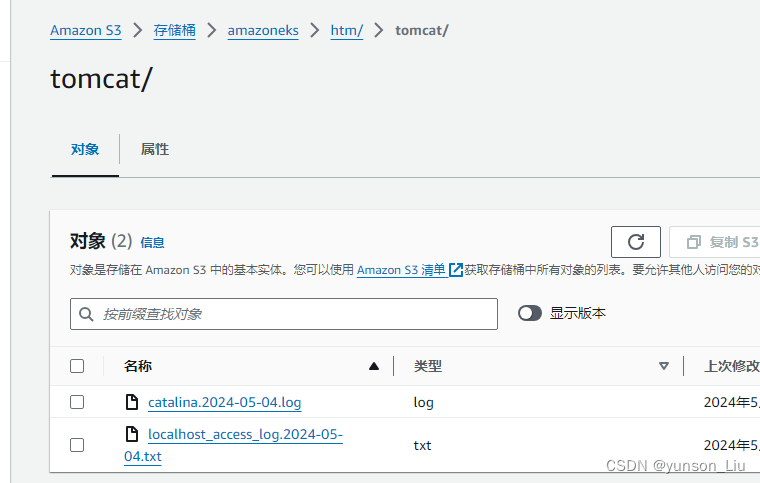
至此测试完毕