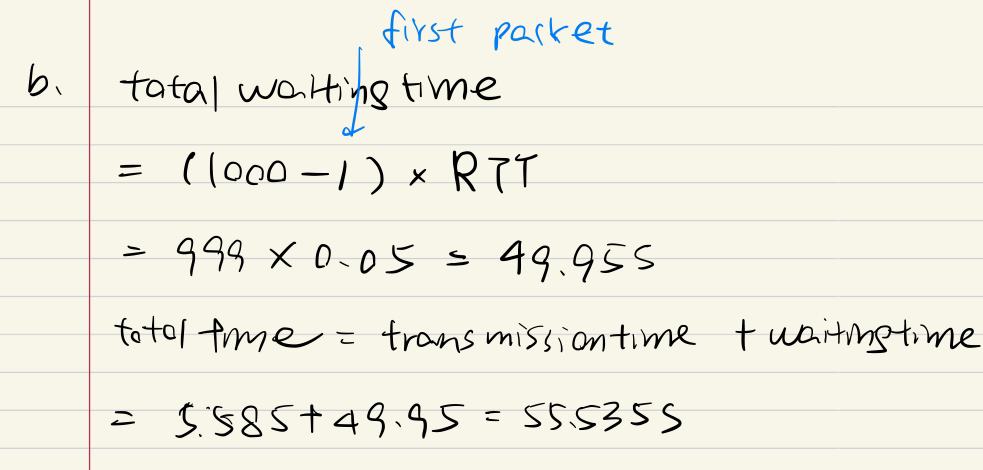
网络性能计算
e.g1.1 算RTT
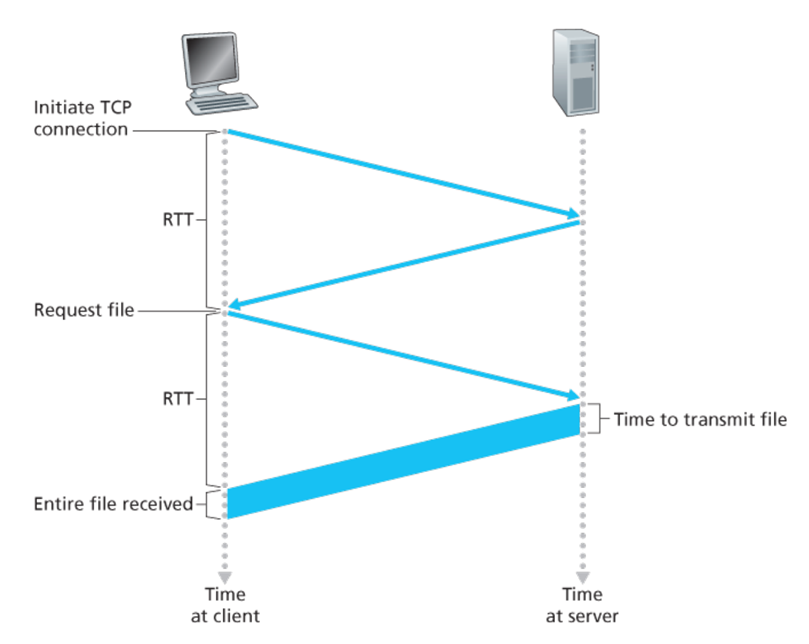

传输时间


when you enter the URL in your browser, it initiates an HTTP request. This request is encapsulated in TCP, which is then further encapsulated in IP for routing. The data is transmitted over the physical medium using link layer protocols like Ethernet. Finally, your router facilitates the communication between your computer and the web server.
e.g1.2 算RTT
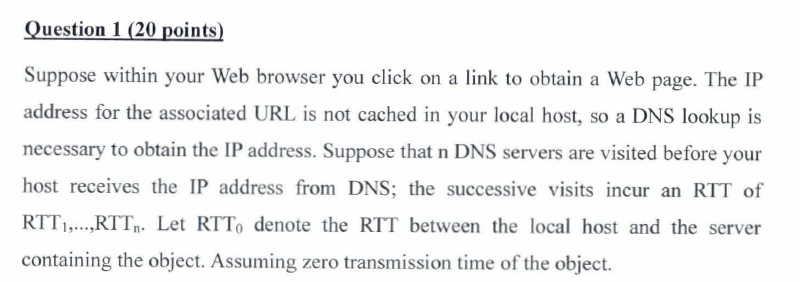
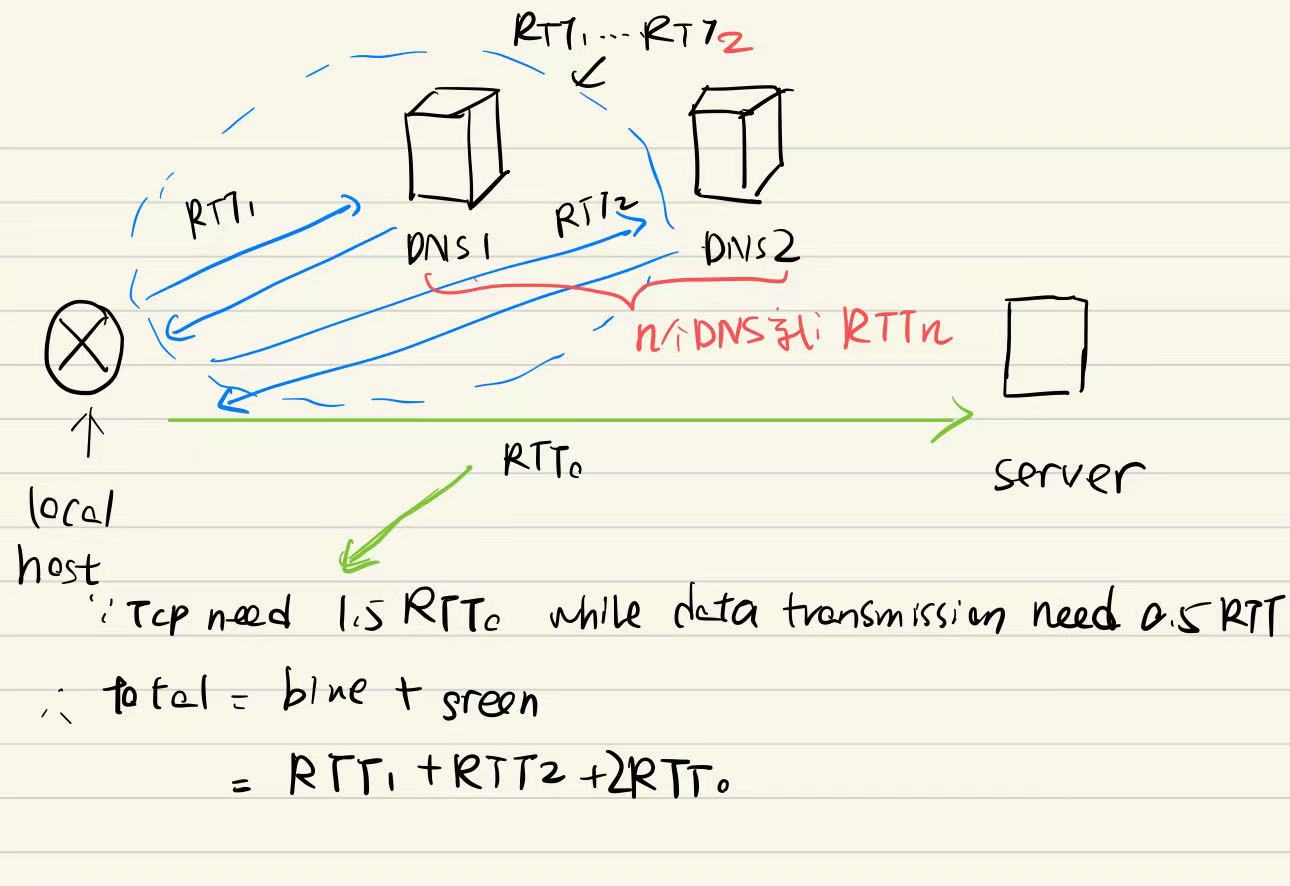
Consider the IP address of total amount of time:
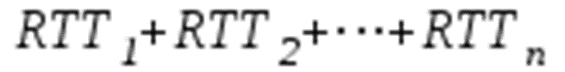
Time elapses from when the client clicks on the link until the client receives the object :
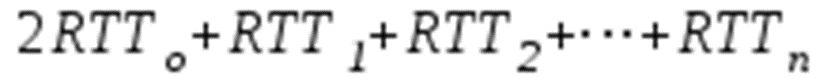
e.g2
e.g3

e.g4 RTT计算+延迟计算








误差检验
e.g1 校验和





0110001111010011

if 11010011+00101100 != 111111111, it shows there's errrors in transmission.
Not possible
Possible, the two errors happen in the same bit, the error couldn't be detected

-
Physical Layer (Layer 1): parity checks and cyclic redundancy checks (CRC).
-
Data Link Layer (Layer 2): Error Detection Method: Frame Check Sequence (FCS) is commonly used at this layer. CRC is a common algorithm for generating FCS to detect errors in data frames.
-
Network Layer (Layer 3): no
-
Transport Layer (Layer 4): Transport layer protocols, such as TCP
-
Application Layer (Layer 5): Error detection at the application layer depends on the specific application protocol being used. For example, protocols like File Transfer Protocol (FTP) may include their own error detection mechanisms. SSL

- The sender and receiver both agree on the generator polynomial beforehand.
- The sender performs a division operation on the extended message (data + appended zeros) using the generator polynomial.
- The remainder of this division, which is the result of the CRC calculation, is the CRC check value.
Efficiency, Simple Implementation, Collision Resistance, Widely Used in Networking Protocols
e.g2 校验和


because to translate the sum,
HTTP
e.g1

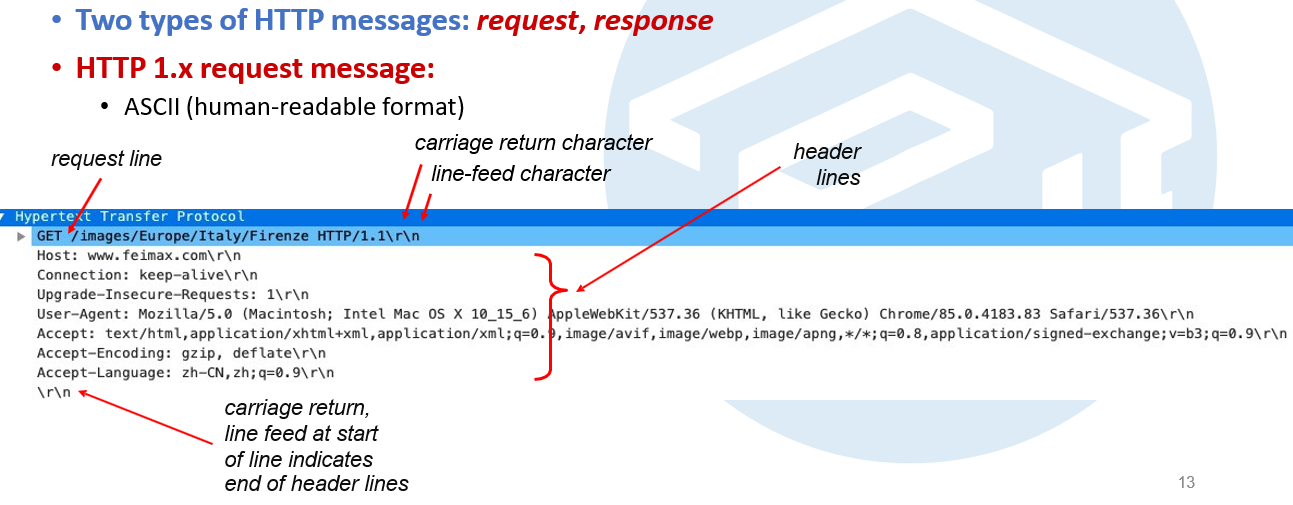
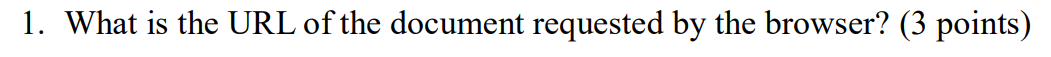
protocol + hostname + path to a file
http://sat.xjtlu.edu.cn/can201/index.html
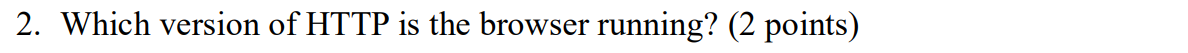
The browser is running HTTP version 1.1

"Connection: keep-alive" -> persistent
在HTTP/1.1中,持久连接可以通过在响应头部中设置Connection: keep-alive来指示。如果响应头部中包含Connection: keep-alive,则表示该连接是持久连接。如果响应头部中没有包含该字段或者设置为Connection: close,则表示该连接是非持久连接。
HTTP/1.0就都是非持久连接了
**********

The server usually uses the Domain Name System (DNS) to resolve the web server's domain name to its IP address. The following is an overview of this process.
The client sends a request to the server with the web server's domain name, e.g. "www.xjtlu.edu.cn".
The server checks its local cache to see if it already has an IP address for that domain name. If it does, it uses that IP address to connect to the web server.
通过DNS协议得到websever 的ip address的
If the server does not have the IP address in its cache, it sends a request to the DNS server to resolve the domain name.
The DNS server checks its own cache to see if it already has the IP address for the domain name. If it does, it sends the IP address back to the server.
If the DNS server does not have the IP address in its cache, it may send requests to other DNS servers in a hierarchical fashion to resolve the IP address, starting with the root DNS server, followed by the TLD, and then the authoritative DNS server.
Once the DNS server resolves the domain name to an IP address, it sends the IP address back to the server.
The server stores that IP address in its cache and uses it to connect to the web server and request content.
-
Browser checks its cache: The browser may first check its local cache to see if it has recently resolved the domain name to an IP address. If it finds a match, it can use that IP address.
-
Operating System's DNS cache: If the browser's cache doesn't have the information, the browser may then check the operating system's DNS cache for a previously resolved IP address.
-
DNS resolution: If the domain name's IP address is not found in the caches, the browser sends a DNS query to a DNS server. This DNS server is typically provided by the user's Internet Service Provider (ISP) or a third-party DNS service.
-
DNS server lookup: The DNS server looks up the IP address associated with the domain name in its records. If it has the information, it returns the IP address to the browser.
-
Browser connects to the server: Once the browser has the IP address, it can establish a connection to the web server using that address. The server then responds to the browser's request, and the web page is loaded.
*******
这个考的概率大
直接从User-Agent 的后面开始找
Mozilla/5.0
The browser type information is needed by the server to send different versions of the same object to different types of browsers.
The browser is included as a header field in the HTTP request message because it provides the server with important information about the client making the request. Here are a few reasons why the browser is required in the HTTP request message
Device compatibility. Different browsers have different capabilities and support different technologies, so browser information helps the server determine if the client can handle the requested content.
Security. Different browsers have different levels of security, and the server can use this information to determine if the client is using the latest secure browser before serving content.
Analysis and logging. Browser information is used to analyze the performance of the site and to understand how the site is being used, such as browser type, version, etc.
Content delivery. Depending on the browser, the server may choose to deliver different content, such as images or web styles, to optimize the user experience.
Malicious user agents. Some attackers may use malware, scripts, or malware to make requests that provide a fake user agent to evade detection. User agent strings are useful in detecting such cases
Compliance: Certain regulations, such as GDPR, CCPA, etc., may require logging of user agents for compliance purposes.
In summary, browser information in HTTP request messages is used to provide the server with important information about the client that can be used to optimize user experience, security and performance, and compliance.
e.g2

TCP/UDP相关
e.g1




e.g2



e.g3



e.g4

e.g5

网桥转发表
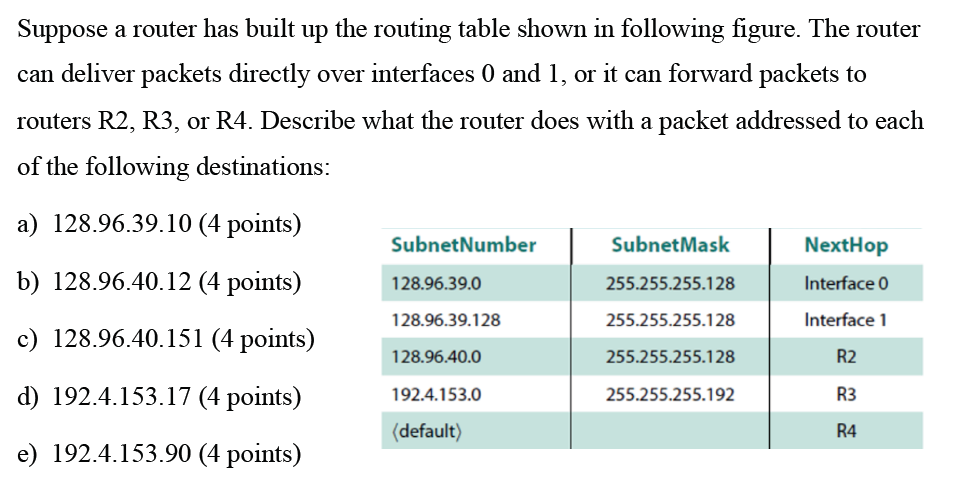

3. 网络RSA
e.g1
![]()
Router works on the network layer. and is responsible for forwarding packets between different networks. It understands IP addresses and makes decisions based on those addresses to send packets from the source network to the destination network.
Switch works on the link layer.It is mainly responsible for transferring data frames between devices in the same network. It uses the MAC address to decide which device the packet should be forwarded to



![]()

e.g2

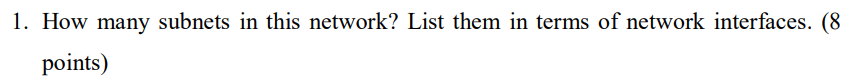
3
interface理解为谁和谁是一个子网
subnet1: Host1, host2
subnet2 Host3
subnet3 Host4,host5

25的意思是前面25位都是subnet part,后面才是host part
首先先把ip地址写成二进制的形式
10.0.2.1
00001010 00000000 00000010 0000 0001
这里橙色部分是确定不变的
largest
后面剩7位,所以是2^7-1(留一广播位),127
00001010 00000000 00000010 0111 1110
10.0.2.127
mask 是划分到了25位
255.255.255.1000 0000
所以是
255.255.255. 2^(8-1) = 255.255.255.128
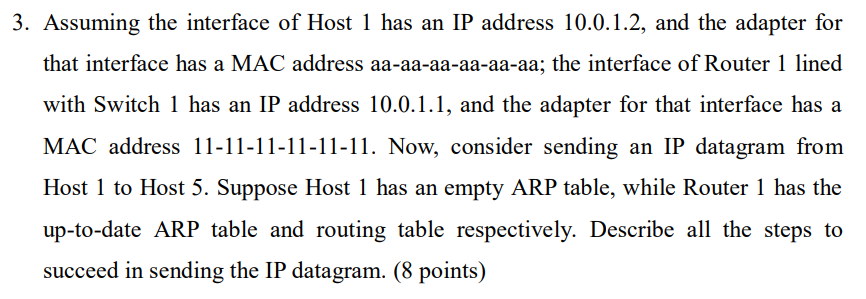
ARP协议只能在一段链路或者一个网络中使用
思路:发的源头没有arp table但是中途是有的
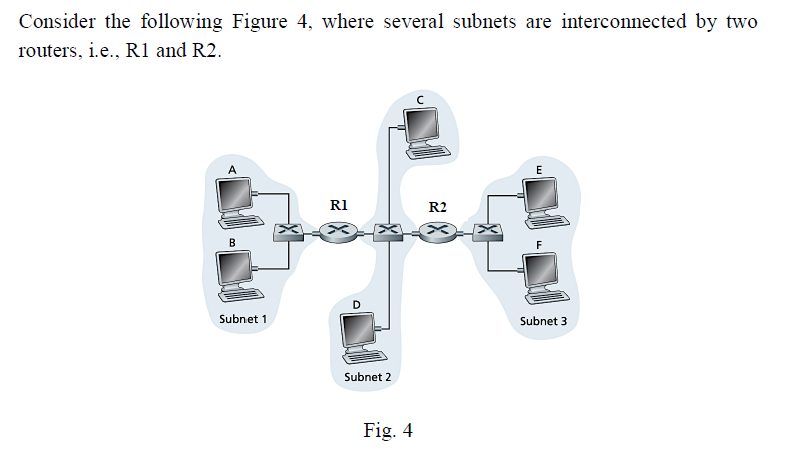
an overview of the steps for sending an IP datagram from Host 1 to Host 5:
Host 1 creates an IP datagram containing the destination IP address of Host 5, and the source IP address of 10.0.1.2, the packet also contains the destination port and source port
Host 1 checks its ARP table to see if it has the MAC address of the next hop router, R1, corresponding to the IP address 10.0.1.1. If it is empty, Host 1 sends an ARP request broadcast to all devices on the local network. Switch 1 receives and forwards.
Router R1 receives the ARP request from switch 1 and checks its ARP table, it finds the corresponding IP address and MAC address of Host 1 (10.0.1.2 and aa-aa-aa-aa-aa-aa) and sends an ARP reply with its own MAC address (11-11-11-11-11-11)
Host 1 receives the ARP reply and updates its ARP table with the IP address and MAC address of R1
Host 1 sends the IP datagram to R1's MAC address, the packet will go to switch 1, switch 1 will check its MAC table and finds the corresponding port to forward the packet to R1
R1 receives the IP datagram, checks its routing table, and finds the route to the destination IP address of Host 5.
R1 checks its ARP table, finds the corresponding MAC address of host 5 and sends the IP datagram directly to host 5, the packet will go to switch 2, switch 2 will check its MAC table and finds the corresponding port to forward the packet to Host 5.
Host 5 receives the IP datagram.
3.加密
e.g1

![]()
Symmetric cryptosystems have a problem of key transportation. The secret key is to be transmitted to the receiving system before the actual message is to be transmitted. Every means of electronic communication is insecure as it is impossible to guarantee that no one will be able to tap communication channels.

A disadvantage of using public-key cryptography for encryption is speed. There are many secret-key encryption methods that are significantly faster than any currently available public-key encryption method.

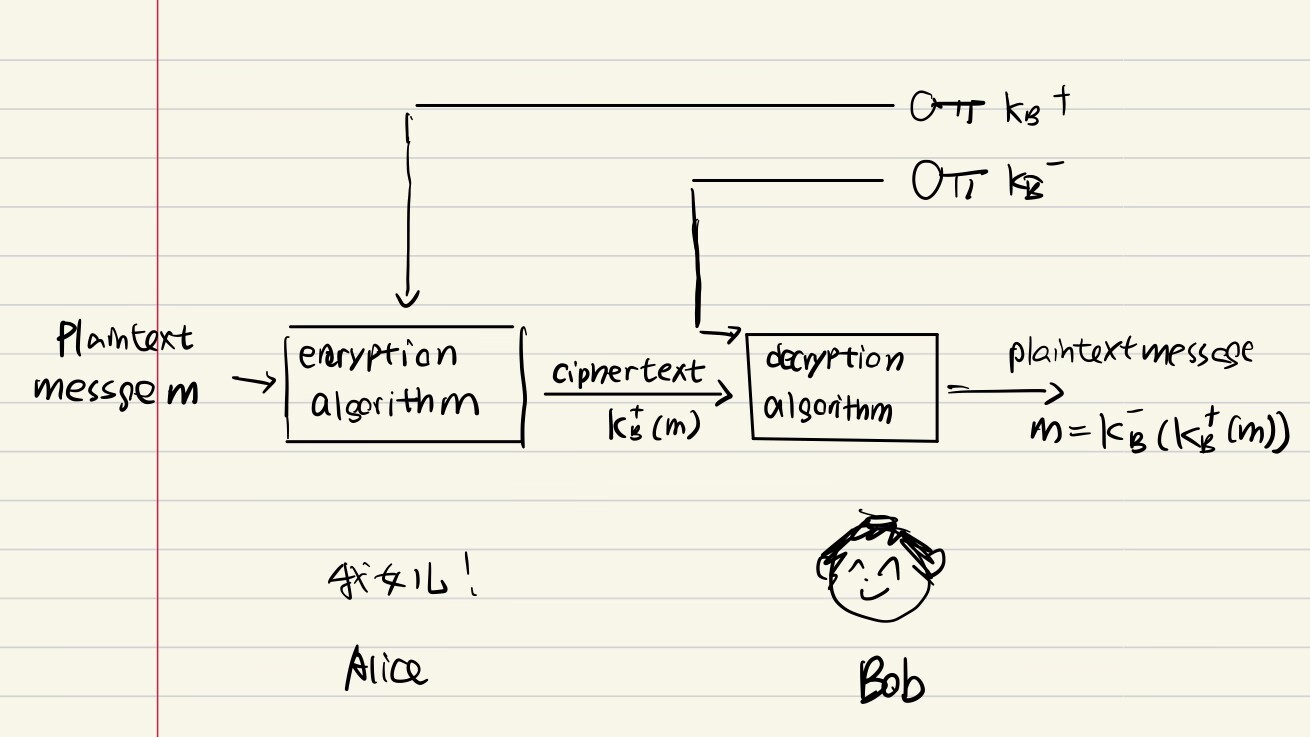

When there is no CA distributing the public keys, the main problem that arises is the problem of trust. Without a trusted third party to issue and distribute the public keys, it can be difficult for the parties involved to trust that the key they are using actually belongs to the intended recipient.
Additionally, without a CA, there will be no way to verify the authenticity of the public key, or to ensure that the public key belongs to a specific individual or organization. This could make it easier for an attacker to impersonate a legitimate entity or to create a false identity and use it to intercept or manipulate sensitive information.
Another problem with not having a CA is the difficulty in revocation of keys. In case of a compromised key, there will be no authority responsible to revoke the key, this would mean the compromised key would continue to be used which would be a huge security risk.
In summary, without a CA distributing public keys, it can be difficult for parties to trust the authenticity of the keys, increasing the risk of man-in-the-middle attacks or impersonation, and would make it harder to ensure the authenticity of the public keys and to revoke them in case of compromise.
感觉它好喜欢好喜欢考disadvantage

如果没有钥匙认证就很容易伪造钥匙,会传递错误的信息给对方
e.g2

![]()
x不会考
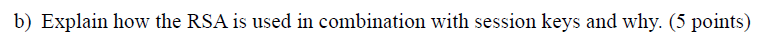
session key 会话密钥


8 bit hash value = 2^8 hash values
The total number of possible 4096-byte data blocks is 2^(4096 * 8)
Since we have a uniform hash function, each of the 256 hash values is equally likely to be produced for any of the 2^(32768) data blocks.
Number of data blocks per hash value = 2^(32768) / 256 = 2^(32768 - 8)
e.g3



![]()