前言:
RSA属于非对称加密。所谓非对称加密,需要两个密钥:公钥 (publickey) 和私钥 (privatekey)。公钥和私钥是一对,如果用公钥对数据加密,那么只能用对应的私钥解密。如果用私钥对数据加密,只能用对应的公钥进行解密。因为加密和解密用的是不同的密钥,所以称为非对称加密。
废话不多说,上代码
/**
* @description: RSA工具类
* @author: JuZi
* @create: 2023-08-25 10:30:14
**/
@Slf4j
@Component
public class RsaUtil {
private static final String KEY_ALGORITHM = "RSA";
private static final int KEY_SIZE = 2048;//设置长度
private static final String PUBLIC_KEY = "publicKey";
private static final String PRIVATE_KEY = "privateKey";
public static final String SIGNATURE_ALGORITHM = "SHA256withRSA";
/**
* 生成公、私钥
* 根据需要返回String或byte[]类型
*
* @return
*/
private static Map<String, String> createRSAKeys() {
Map<String, String> keyPairMap = new HashMap<>();
try {
KeyPairGenerator keyPairGenerator = KeyPairGenerator.getInstance(KEY_ALGORITHM);
keyPairGenerator.initialize(KEY_SIZE, new SecureRandom());
KeyPair keyPair = keyPairGenerator.generateKeyPair();
PublicKey publicKey = keyPair.getPublic();
PrivateKey privateKey = keyPair.getPrivate();
//获取公、私钥值
String publicKeyValue = byte2Base64String(publicKey.getEncoded());
String privateKeyValue = byte2Base64String(privateKey.getEncoded());
//存入
keyPairMap.put(PUBLIC_KEY, publicKeyValue);
keyPairMap.put(PRIVATE_KEY, privateKeyValue);
} catch (Exception e) {
e.printStackTrace();
}
return keyPairMap;
}
/**
* 通过私钥对参数进行加密
*
* @param Data
* @param privateKey
* @return
*/
public static String MakeSign(String Data, String privateKey) {
try {
byte[] data = Data.getBytes();
byte[] keyBytes = base64String2Byte(privateKey);
PKCS8EncodedKeySpec pkcs8KeySpec = new PKCS8EncodedKeySpec(keyBytes);
KeyFactory keyFactory = KeyFactory.getInstance(KEY_ALGORITHM);
PrivateKey priKey = keyFactory.generatePrivate(pkcs8KeySpec);
//这个根据需求填充SHA1WithRSA或SHA256WithRSA
Signature signature = Signature.getInstance(SIGNATURE_ALGORITHM);
signature.initSign(priKey);
signature.update(data);
return byte2Base64String(signature.sign());
} catch (Exception e) {
return "";
}
}
/**
* 使用公钥
*
* @param Data_ori
* @param Singnature
* @param publicKeyBase64Str
* @return
*/
public static boolean VeriSign(String Data_ori, String Singnature, String publicKeyBase64Str) {
try {
byte[] signed = base64String2Byte(Singnature);
X509EncodedKeySpec keySpec = new X509EncodedKeySpec(base64String2Byte(publicKeyBase64Str));
KeyFactory keyFactory = null;
keyFactory = KeyFactory.getInstance(KEY_ALGORITHM);
PublicKey publicKey = keyFactory.generatePublic(keySpec);
//这个根据需求填充SHA1WithRSA或SHA256WithRSA
Signature signature = Signature.getInstance(SIGNATURE_ALGORITHM);
signature.initVerify(publicKey);
signature.update(Data_ori.getBytes(StandardCharsets.UTF_8));
return signature.verify(signed);
} catch (Exception e) {
return false;
}
}
/**
* base64字符串转字节数组
*
* @param base64Str
* @return
*/
public static byte[] base64String2Byte(String base64Str) {
return Base64.decodeBase64(base64Str);
}
/**
* 字节数组转base64字符串
*
* @param bytes
* @return
*/
public static String byte2Base64String(byte[] bytes) {
return new String(new Base64().encode(bytes));
}
public static byte charToByte(char c) {
return (byte) "0123456789ABCDEF".indexOf(c);
}
}
工具类全文如上所示,接下来看看效果
测试代码
public static void main(String[] args) throws Exception {
log.info("-----开始生成公钥和私钥-----");
Map<String, String> keys = createRSAKeys();
log.info("-----公钥base64:{}-----", keys.get(PUBLIC_KEY));
log.info("-----私钥base64:{}-----", keys.get(PRIVATE_KEY));
log.info("-----开始对数据进行加密-----");
String data = "hello word !";
log.info("-----源数据:{}-----", data);
String sign = RsaUtil.MakeSign(data, keys.get(PRIVATE_KEY));
log.info("-----私钥加密结果:{}-----", sign);
log.info("-----开始用公钥对私钥的加密验证-----");
log.info("-----公钥验证结果:{}-----", VeriSign(data, sign, keys.get(PUBLIC_KEY)));
}
测试结果
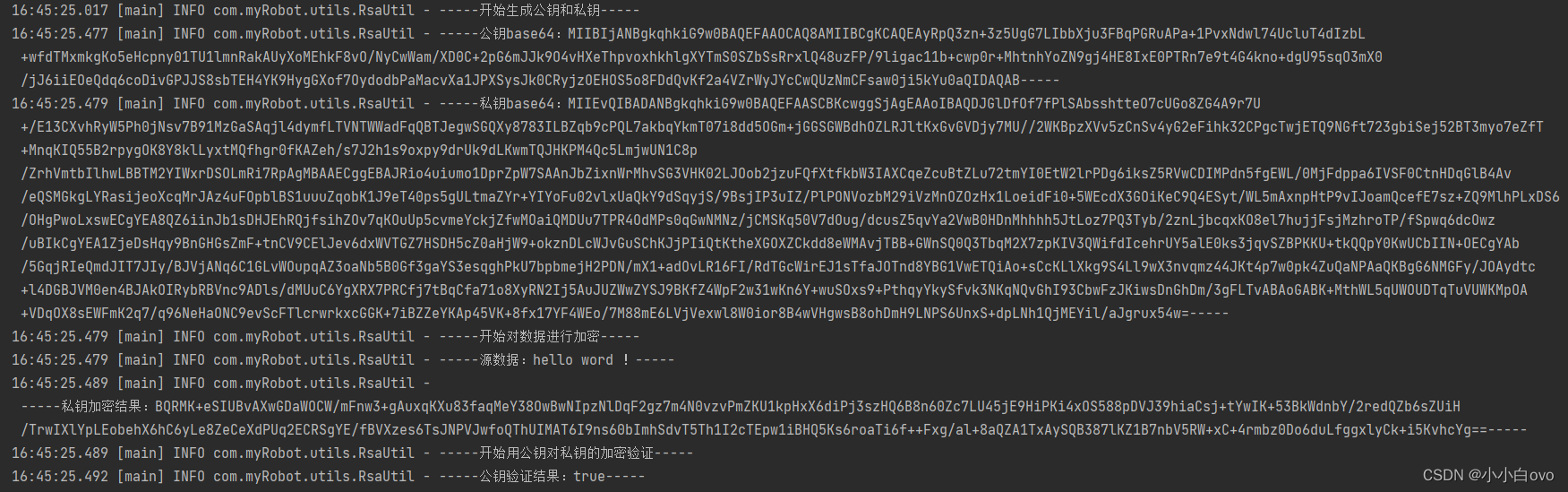
看起来没问题拿下了。
对逆向感兴趣的盆友可以关注交流,不定时更新常用算法和加密。