文章目录
- 1、漏洞代码
- 2、修复XSS
- 2.1、单个文件修复
- 2.2、通用过滤
- 3、一些补充
之前的文章,
php代码审计14之XSS
1、漏洞代码
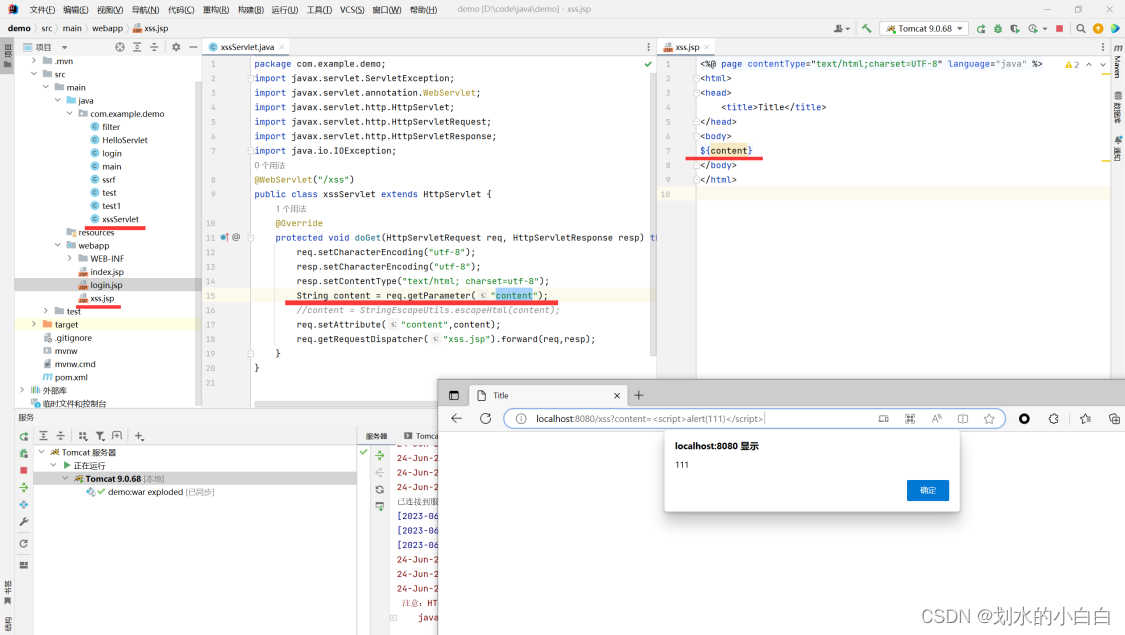
xssServlet.java
package com.example.demo;
import javax.servlet.ServletException;
import javax.servlet.annotation.WebServlet;
import javax.servlet.http.HttpServlet;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
@WebServlet("/xss")
public class xssServlet extends HttpServlet {
@Override
protected void doGet(HttpServletRequest req, HttpServletResponse resp) throws ServletException, IOException {
req.setCharacterEncoding("utf-8");
resp.setCharacterEncoding("utf-8");
resp.setContentType("text/html; charset=utf-8");
String content = req.getParameter("content");
//content = StringEscapeUtils.escapeHtml(content);
req.setAttribute("content",content);
req.getRequestDispatcher("xss.jsp").forward(req,resp);
}
}
xss.jsp
<%@ page contentType="text/html;charset=UTF-8" language="java" %>
<html>
<head>
<title>Title</title>
</head>
<body>
${content}
</body>
</html>
测试下,
http://localhost:8080/xss?content=%3Cscript%3Ealert(111)%3C/script%3E
2、修复XSS
2.1、单个文件修复
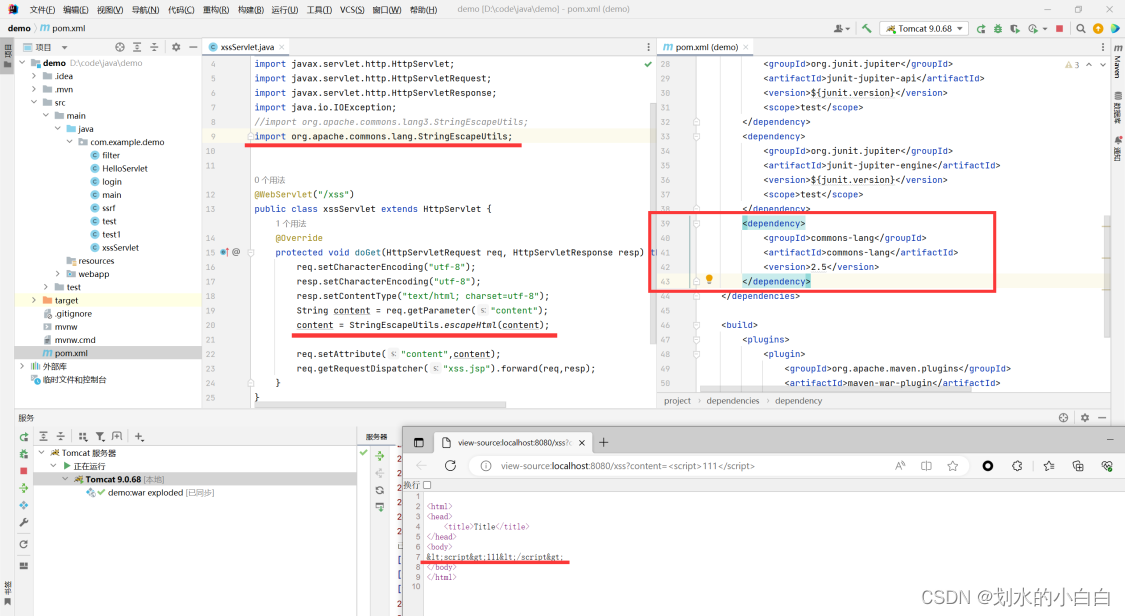
xssServlet.java
package com.example.demo;
import javax.servlet.ServletException;
import javax.servlet.annotation.WebServlet;
import javax.servlet.http.HttpServlet;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
//import org.apache.commons.lang3.StringEscapeUtils;
import org.apache.commons.lang.StringEscapeUtils;
@WebServlet("/xss")
public class xssServlet extends HttpServlet {
@Override
protected void doGet(HttpServletRequest req, HttpServletResponse resp) throws ServletException, IOException {
req.setCharacterEncoding("utf-8");
resp.setCharacterEncoding("utf-8");
resp.setContentType("text/html; charset=utf-8");
String content = req.getParameter("content");
content = StringEscapeUtils.escapeHtml(content);
req.setAttribute("content",content);
req.getRequestDispatcher("xss.jsp").forward(req,resp);
}
}
pom.xml
<dependency>
<groupId>commons-lang</groupId>
<artifactId>commons-lang</artifactId>
<version>2.5</version>
</dependency>
访问下,
http://localhost:8080/xss?content=%3Cscript%3Ealert(111)%3C/script%3E
2.2、通用过滤
上述的方式仅仅对单个文件生效,
实际的项目上肯定不能这么搞,这么搞的后果就是部分文件传参容易遗忘过滤导致漏洞的造成,
正常的思路是直接在过滤器统一处理传参,
新建两个文件,
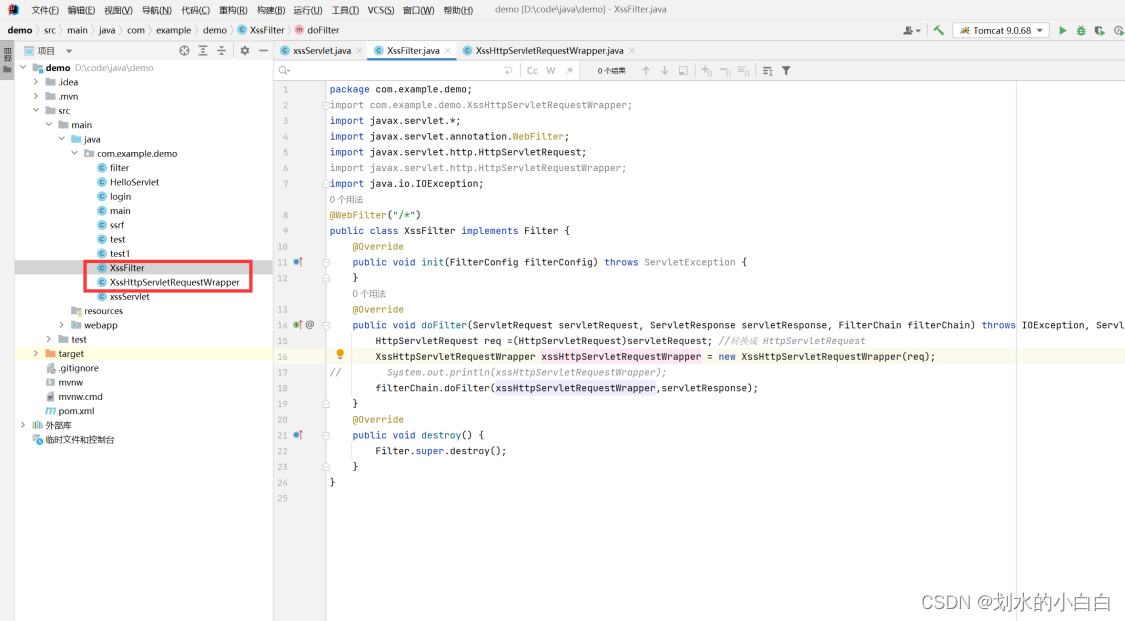
XssFilter.java
package com.example.demo;
import com.example.demo.XssHttpServletRequestWrapper;
import javax.servlet.*;
import javax.servlet.annotation.WebFilter;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletRequestWrapper;
import java.io.IOException;
@WebFilter("/*")
public class XssFilter implements Filter {
@Override
public void init(FilterConfig filterConfig) throws ServletException {
}
@Override
public void doFilter(ServletRequest servletRequest, ServletResponse servletResponse, FilterChain filterChain) throws IOException, ServletException {
HttpServletRequest req =(HttpServletRequest)servletRequest; //转换成 HttpServletRequest
XssHttpServletRequestWrapper xssHttpServletRequestWrapper = new XssHttpServletRequestWrapper(req);
// System.out.println(xssHttpServletRequestWrapper);
filterChain.doFilter(xssHttpServletRequestWrapper,servletResponse);
}
@Override
public void destroy() {
Filter.super.destroy();
}
}
XssHttpServletRequestWrapper.java
package com.example.demo;
import org.apache.commons.lang.StringEscapeUtils;
import org.apache.commons.lang.StringUtils;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletRequestWrapper;
public class XssHttpServletRequestWrapper extends HttpServletRequestWrapper {
private HttpServletRequest request;
public XssHttpServletRequestWrapper(HttpServletRequest request) {
super(request);
this.request=request;
}
@Override
public String getParameter(String name) {
String oldname= super.getParameter(name);
if(!StringUtils.isEmpty(oldname)){
oldname = StringEscapeUtils.escapeHtml(oldname);
}
return oldname;
}
}
3、一些补充
安全评审的话,在数据库查询的语句,尽量不要使“ * ”,采用最小化原则。
数据库查出来的类型,要和类使用的类型一致。
一般没有过滤,我们打的XSS的payload还没有弹框,一般有两个原因:
没有进行语句闭合
一些标签自带转义效果,比如:textarea标签
如何判断一个项目是否存在全局XSS过滤,
直接全局搜索“XSS过滤” 、“XSSFilter”
假设没有找到类似的代码,大概率是存在xss的