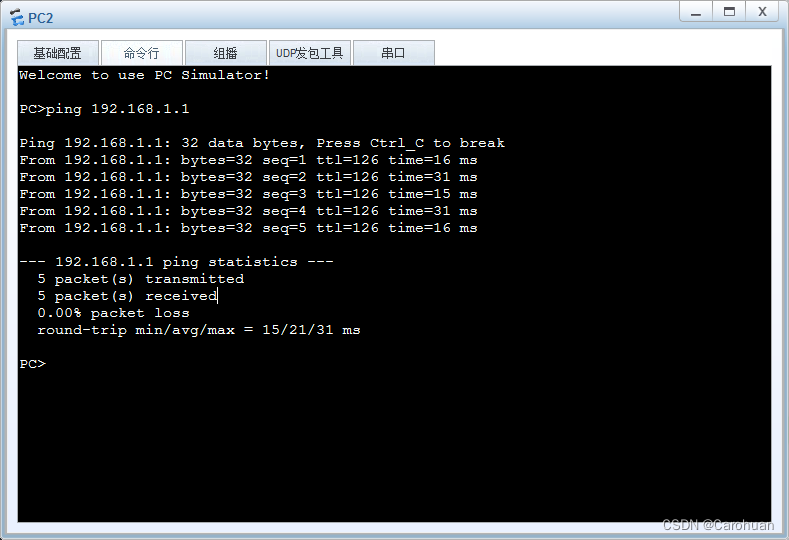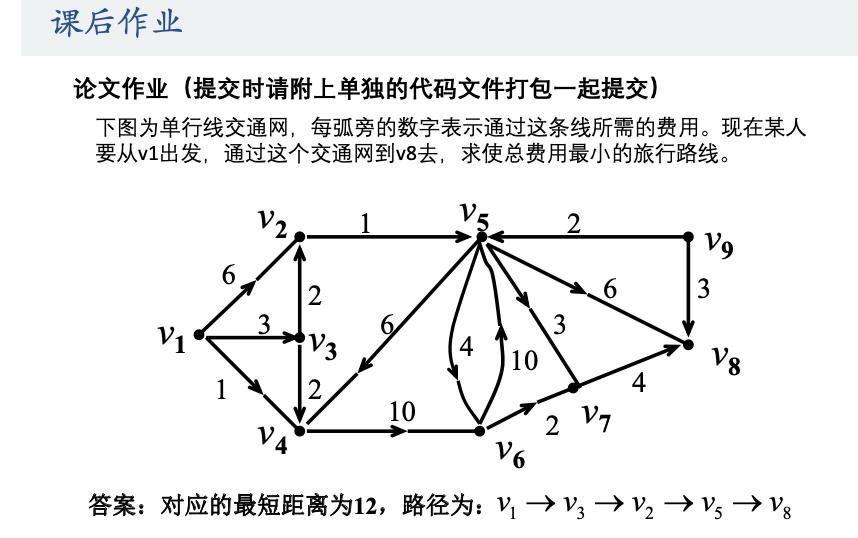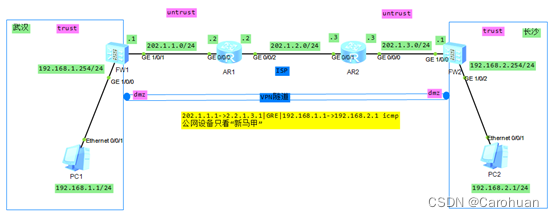
首先分析一下数据的流向:
PC1->PC2
1、FW1:trust->dmz 【192.168.1.1->192.168.2.1 ICMP】
2、AR1->AR2:【202.1.1.1->202.1.3.1|GRE|192.168.1.1->192.168.2.1 icmp】
3、FW2:
①untrust->local 202.1.1.1->202.1.3.1 GRE
②dmz->trust 【192.168.1.1->192.168.2.1 ICMP】
PC2->PC1
4、FW2: trust->dmz 【192.168.1.1<-192.168.2.1 ICMP】
5、AR2->AR1: 【202.1.1.1<-202.1.3.1|GRE|192.168.1.1<-192.168.2.1 icmp】
6、FW1:
① untrust->local 202.1.1.1<-202.1.3.1|GRE
②dmz->trust 【192.168.1.1<-192.168.2.1 ICMP】
一、基础配置+建立VPN通道+引流(参考ENSP实验三带内容)
**将Tunnel1逻辑接口配到dmz区域中
ping流量【192.168.1.1->192.168.2.1 icmp】从PC1流至FW1
二、FW1配置安全策略(单向:PC1->PC2):
[FW1]security-policy
[FW1-policy-security]rule name test1
[FW1-policy-security-rule-test1]source-zone trust
[FW1-policy-security-rule-test1]destination-zone dmz
[FW1-policy-security-rule-test1]source-address 192.168.1.1 mask 255.255.255.255
[FW1-policy-security-rule-test1]destination-address 192.168.2.1 mask 255.255.255
.255
[FW1-policy-security-rule-test1]service icmp
[FW1-policy-security-rule-test1]action permit将流量送至FW1后,根据外层头二次查表,送至下一个路由AR1【202.1.1.1->202.1.3.1|GRE|192.168.1.1->192.168.2.1 icmp】
AR1查表,将流量送至AR2
三、配置FW2收流量带安全策略(单向:PC1->PC2)
收到AR2传来的流量【202.1.1.1->202.1.3.1|GRE|192.168.1.1->192.168.2.1 icmp】
1、策略1:决定收不收流量
[FW2]security-policy
[FW2-policy-security]rule name test1
[FW2-policy-security-rule-test1]source-zone untrust
[FW2-policy-security-rule-test1]destination-zone local
[FW2-policy-security-rule-test1]source-address 202.1.1.1 mask 255.255.255.255
[FW2-policy-security-rule-test1]destination-address 202.1.3.1 mask 255.255.255.2
55
[FW2-policy-security-rule-test1]service gre 或者service protocol 47
[FW2-policy-security-rule-test1]action permit
2、策略2:将流量送至trust区
[FW2]security-policy
[FW2-policy-security]rule name test2
[FW2-policy-security-rule-test2]display this
#
rule name test2
source-zone dmz
destination-zone trust
source-address 192.168.1.1 32
destination-address 192.168.2.1 32
service icmp
action permit
#
*Icmp对应ping命令
四、反向配安全策略(PC2->PC1)
配置好后的策略:
*取消放行所有的安全策略:
[FW1]security-policy
[FW1-policy-security]default action deny[FW2-policy-security]display this
#
security-policy
rule name test1
source-zone untrust
destination-zone local
source-address 202.1.1.1 32
destination-address 202.1.3.1 32
service protocol 47
action permit
rule name test2
source-zone trust
source-zone dmz
destination-zone trust
destination-zone dmz
source-address 192.168.1.1 32
source-address 192.168.2.1 32
destination-address 192.168.1.1 32
destination-address 192.168.2.1 32
service icmp
action permit
#
[FW1-policy-security] display this
#
security-policy
rule name test1
source-zone trust
source-zone dmz
destination-zone trust
destination-zone dmz
source-address 192.168.1.1 32
source-address 192.168.2.1 32
destination-address 192.168.1.1 32
destination-address 192.168.2.1 32
service icmp
action permit
rule name test2
source-zone untrust
destination-zone local
source-address 202.1.3.1 32
destination-address 202.1.1.1 32
service protocol 47
action permit
#
配置好后可实现PC1与PC2之间的ping