cert-manager 安装部署
一、官网安装文档
https://cert-manager.io/docs/installation/
1.1、简介
cert-manager 在 Kubernetes 集群中增加了证书 (certificates) 和证书颁发者 (certificate issuers) 作为资源类型,并简化了获取、更新和应用这些证书的过程。
它能够从各种反对的起源签发证书,包含 Let’s Encrypt、HashiCorp Vault 和 Venafi 以及私人 PKI。
1.2、Issuer(证书颁发者)
在装置了 cert-manager 之后,须要配置的第一件事是一个证书颁发者,而后你能够用它来签发证书。
cert-manager 带有一些内置的证书颁发者,它们被示意为在cert-manager.io组中。除了内置类型外,你还能够装置内部证书颁发者。内置和内部证书颁发者的待遇是一样的,配置也相似。
有以下几种证书颁发者类型:
自签名 (SelfSigned)
CA(证书颁发机构)
Hashicorp Vault(金库)
Venafi (SaaS 服务)
External(内部)
ACME(主动证书治理环境)
HTTP01
DNS01
1.3、SelfSigned
如下:
apiVersion: cert-manager.io/v1
kind: Issuer
metadata:
annotations:
meta.helm.sh/release-name: cert-manager-webhook-dnspod
meta.helm.sh/release-namespace: cert-manager
labels:
app: cert-manager-webhook-dnspod
app.kubernetes.io/managed-by: Helm
chart: cert-manager-webhook-dnspod-1.2.0
heritage: Helm
release: cert-manager-webhook-dnspod
name: cert-manager-webhook-dnspod-selfsign
namespace: cert-manager
status:
conditions:
- lastTransitionTime: '2022-03-01T13:38:53Z'
observedGeneration: 1
reason: IsReady
status: 'True'
type: Ready
spec:
selfSigned: {}
1.4、ACME – HTTP01
apiVersion: cert-manager.io/v1
kind: Issuer
metadata:
annotations:
meta.helm.sh/release-name: rancher
meta.helm.sh/release-namespace: cattle-system
generation: 2
labels:
app: rancher
app.kubernetes.io/managed-by: Helm
chart: rancher-2.6.4
heritage: Helm
release: rancher
name: rancher
namespace: cattle-system
status:
acme: {}
conditions:
- lastTransitionTime: '2022-03-08T14:34:08Z'
message: The ACME account was registered with the ACME server
observedGeneration: 2
reason: ACMEAccountRegistered
status: 'True'
type: Ready
spec:
acme:
preferredChain: ''
privateKeySecretRef:
name: letsencrypt-production
server: https://acme-v02.api.letsencrypt.org/directory
solvers:
- http01:
ingress: {}
1.5、ACME – DNS01
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
annotations:
meta.helm.sh/release-name: cert-manager-webhook-dnspod
meta.helm.sh/release-namespace: cert-manager
labels:
app: cert-manager-webhook-dnspod
app.kubernetes.io/managed-by: Helm
chart: cert-manager-webhook-dnspod-1.2.0
heritage: Helm
release: cert-manager-webhook-dnspod
status:
acme:
lastRegisteredEmail: cuikaidong@foxmail.com
uri: https://acme-v02.api.letsencrypt.org/acme/acct/431637010
conditions:
- lastTransitionTime: '2022-03-01T13:38:55Z'
message: The ACME account was registered with the ACME server
observedGeneration: 1
reason: ACMEAccountRegistered
status: 'True'
type: Ready
spec:
acme:
email: cuikaidong@foxmail.com
preferredChain: ''
privateKeySecretRef:
name: cert-manager-webhook-dnspod-letsencrypt
server: https://acme-v02.api.letsencrypt.org/directory
solvers:
- dns01:
webhook:
config:
secretId: <my-secret-id>
secretKeyRef:
key: secret-key
name: cert-manager-webhook-dnspod-secret
ttl: 600
groupName: acme.imroc.cc
solverName: dnspod
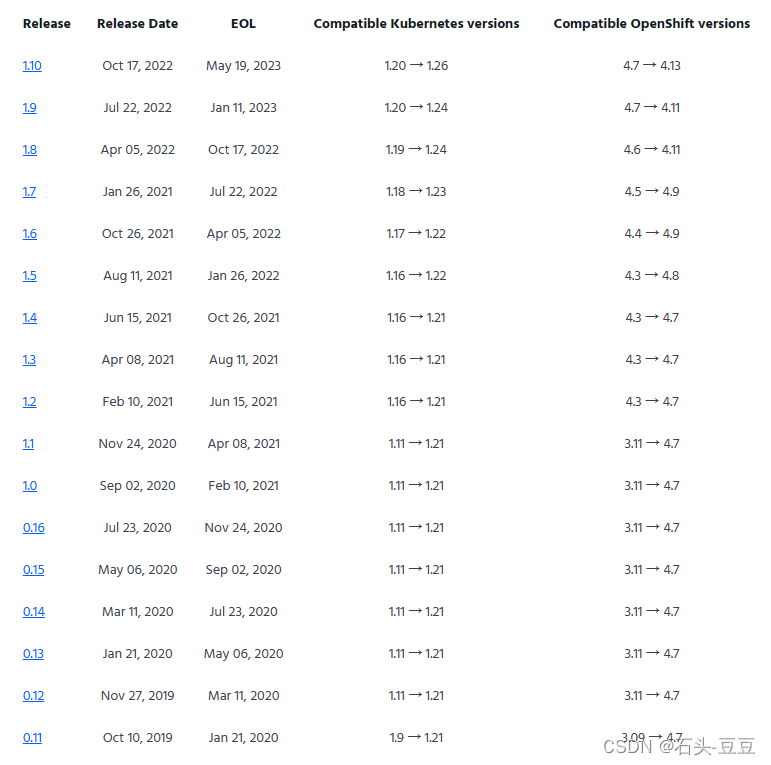
二、cert-manager版本与K8S版本支持关系
官网文档:https://cert-manager.io/docs/installation/supported-releases/
三、yaml方式部署
k8s版本:1.18.20
cert-manager:1.8
kubectl apply -f https://github.com/cert-manager/cert-manager/releases/download/v1.8.0/cert-manager.yaml
验证容器部署
[root@k8s-node rancher]# kubectl get pod -o wide -n cert-manager
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
cert-manager-744c65bc9b-2vgl5 1/1 Running 0 6h2m 10.42.113.139 k8s-node <none> <none>
cert-manager-cainjector-85dd4cc89f-grs6s 1/1 Running 0 6h2m 10.42.113.138 k8s-node <none> <none>
cert-manager-webhook-5cf5c59b-vsg55 1/1 Running 0 6h2m 10.42.113.140 k8s-node <none> <none>
四、helm方式部署
4.1、添加helm源
helm repo add jetstack https://charts.jetstack.io
4.2、更新helm源
helm repo update
4.3、安装cert-manager
helm install \
cert-manager jetstack/cert-manager \
--namespace cert-manager \
--create-namespace \
--version v1.8.0 \
# --set installCRDs=true
五、使用cert-manager申请三个月免费证书
5.1、创建HTTP-01方式issuer
[root@k8s-node ~]# cat clusterissuer-prod.yaml
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: letsencrypt-prod
spec:
acme:
#server: https://acme-staging-v02.api.letsencrypt.org/directory
server: https://acme-v02.api.letsencrypt.org/directory
privateKeySecretRef:
name: letsencrypt-prod
solvers:
- http01:
ingress:
class: nginx
5.2、以HTTP-01方式申请域名证书
[root@k8s-node ~]# cat ssl.yaml
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
name: ssl #证书名称
namespace: cert-manager #名称空间
spec:
secretName: ssl #证书名称
issuerRef:
name: letsencrypt-prod #指定ISSUER
kind: ClusterIssuer
duration: 2160h
renewBefore: 360h
dnsNames:
- www.demo.cn
- app.demo.cn
Issuer/ClusterIssuer: 用于指示 cert-manager 用什么方式签发证书,本文主要讲解签发免费证书的 ACME 方式。ClusterIssuer 与 Issuer 的唯一区别就是 Issuer 只能用来签发自己所在 namespace 下的证书,ClusterIssuer 可以签发任意 namespace 下的证书。
Certificate: 用于告诉 cert-manager 我们想要什么域名的证书以及签发证书所需要的一些配置,包括对 Issuer/ClusterIssuer 的引用。
参考:https://blog.csdn.net/weixin_44692256/article/details/108274385





![[centos]安装mysql8.0.26](https://img-blog.csdnimg.cn/7fd8ee320a3f40e8b2c8a2b8b13b1e0f.png)