Kubernetes之配置dashboard
概述
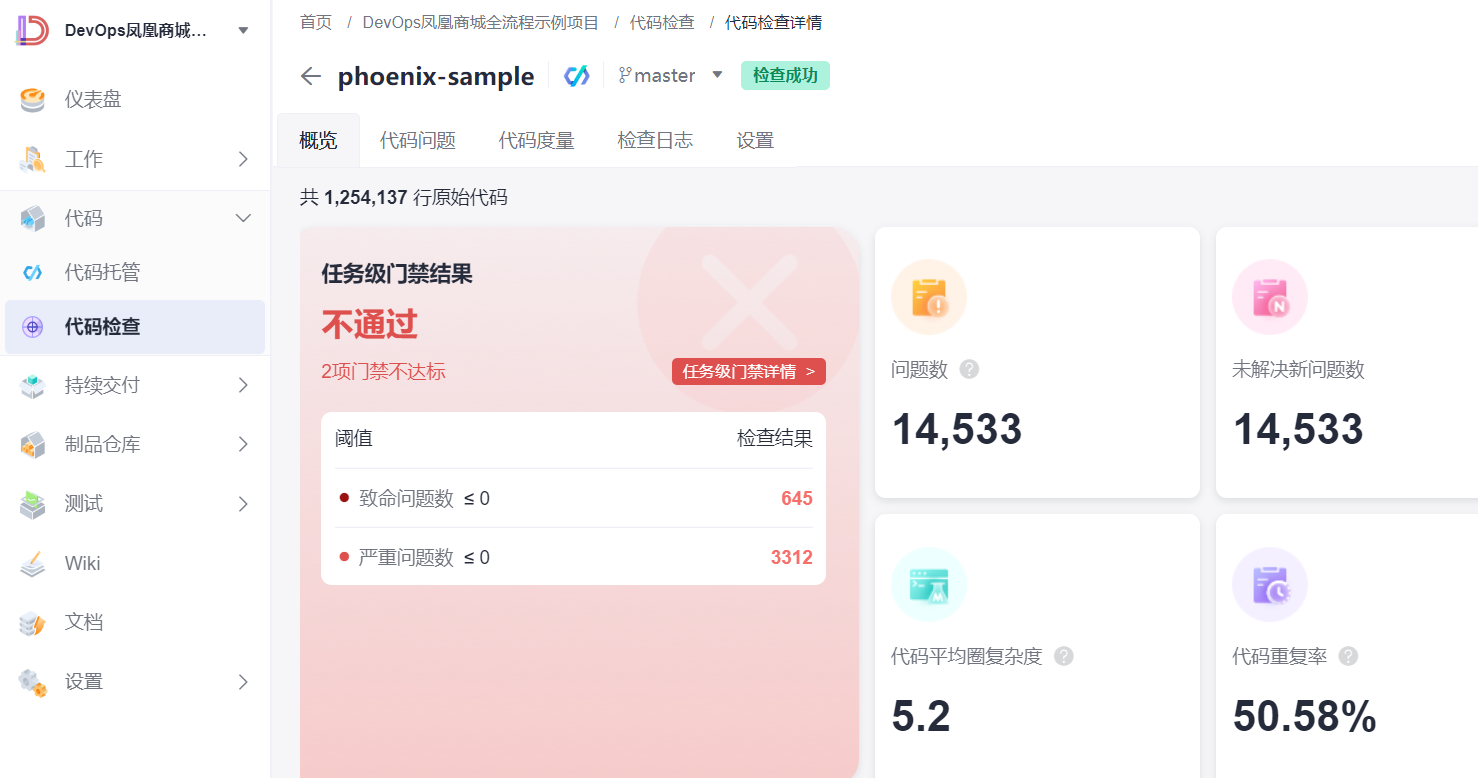
Dashboard 是基于网页的 Kubernetes 用户界面。 你可以使用 Dashboard 将容器应用部署到 Kubernetes 集群中,也可以对容器应用排错,还能管理集群资源。 你可以使用 Dashboard 获取运行在集群中的应用的概览信息,也可以创建或者修改 Kubernetes 资源 (如 Deployment,Job,DaemonSet 等等)。但是一般还是图形化界面一般还是给开发或者对kubernetes不太熟悉的人查看使用。
安装部署
可以安装自己所需版本下载。和k8s具体的使用版本关系部大,可任意选择。我此次测试使用的是v2.7.0版本。
默认安装
#下载所需yaml文件
[root@k8s-m1 certs]# wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.7.0/aio/deploy/recommended.yaml
#修改recommended.yaml中service的相关部分,可以临时使用nodeport的方式访问
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort
ports:
- port: 443
targetPort: 8443
nodePort: 32443
selector:
k8s-app: kubernetes-dashboard
获取登录的token
[root@k8s-m1 certs]# kubectl -n kubernetes-dashboard describe secret $(kubectl -n kubernetes-dashboard get secret | grep dashboard-token | awk '{print $1}')
登录查看
使用集群任意节点的ip地址登录,端口上面暴露的32443。认证方式使用token,具体的为上面命令获取。
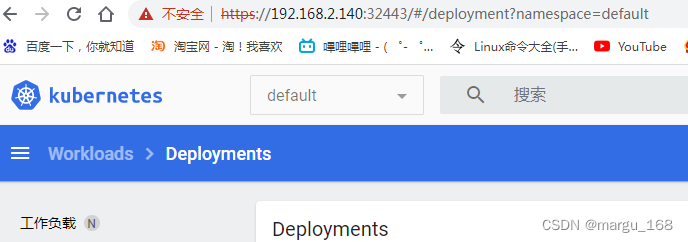
通过登录发现,只能查看default命名空间下的资源,下面我们通过自己创建账户查看集群内所有资源,并手动添加证书(貌似新版本已经不需要手动添加了,如果浏览器不支持自动生成的证书,可以手动创建)。
自定义安装
创建证书
[root@k8s-m1 k8s-dashboard]# (umask 077;openssl genrsa -out dashboard.key 2048)
Generating RSA private key, 2048 bit long modulus
...........+++
................................+++
e is 65537 (0x10001)
[root@k8s-m1 k8s-dashboard]# openssl req -nodes -newkey rsa:2048 -keyout certs/dashboard.key -out certs/dashboard.csr -subj "/C=/ST=/L=/O=/OU=/CN=kubernetes-dashboard"
Generating a 2048 bit RSA private key
...............+++
..................................+++
writing new private key to 'certs/dashboard.key'
-----
No value provided for Subject Attribute C, skipped
No value provided for Subject Attribute ST, skipped
No value provided for Subject Attribute L, skipped
No value provided for Subject Attribute O, skipped
No value provided for Subject Attribute OU, skipped
[root@k8s-m1 k8s-dashboard]# openssl x509 -req -sha256 -days 365 -in certs/dashboard.csr -signkey certs/dashboard.key -out certs/dashboard.crt
Signature ok
subject=/CN=kubernetes-dashboard
Getting Private key
[root@k8s-m1 k8s-dashboard]# kubectl create secret generic kubernetes-dashboard-certs --from-file=$HOME/certs -n kubernetes-dashboard
secret/kubernetes-dashboard-certs created
修改yaml文件
在上面基础安装上继续修改recommended.yaml,如下。添加使用自己生成的证书,增加token过期实时间。
containers:
- name: kubernetes-dashboard
image: kubernetesui/dashboard:v2.7.0
imagePullPolicy: Always
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
- --tls-cert-file=/certs/dashboard.crt
- --tls-key-file=/certs/dashboard.key
- --namespace=kubernetes-dashboard
- --token-ttl=604800
##然后直接部署
[root@k8s-m1 k8s-dashboard]# kubectl apply -f recommended.yaml
namespace/kubernetes-dashboard unchanged
serviceaccount/kubernetes-dashboard unchanged
service/kubernetes-dashboard unchanged
Warning: kubectl apply should be used on resource created by either kubectl create --save-config or kubectl apply
secret/kubernetes-dashboard-certs configured
secret/kubernetes-dashboard-csrf configured
secret/kubernetes-dashboard-key-holder unchanged
configmap/kubernetes-dashboard-settings unchanged
role.rbac.authorization.k8s.io/kubernetes-dashboard unchanged
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard unchanged
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard unchanged
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard configured
service/dashboard-metrics-scraper unchanged
deployment.apps/dashboard-metrics-scraper unchanged
创建 admin 账户
创建一个kubernetes-dashboard这个服务使用的serviceAccount,如admin
[root@k8s-m1 k8s-dashboard]# cat dashboard-admin.yaml
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kubernetes-dashboard
登录
通过如下命令获取 token ,并通过 https 进行 dashboard 端口访问
[root@k8s-m1 k8s-dashboard]# kubectl -n kubernetes-dashboard get secret $(kubectl -n kubernetes-dashboard get sa/admin-user -o jsonpath="{.secrets[0].name}") -o go-template="{{.data.token | base64decode}}"
eyJhbGciOiJSUzI1NiIsImtpZCI6IjJMRm8zNktIWkdvaHRDZ2szX2Vyd3JFQTE5OEZ6TjNuRnUyYTFueGE3emMifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi11c2VyLXRva2VuLWd6Nmw0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImFkbWluLXVzZXIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2OTEzMDRjOC1lMGUzLTQ0YzEtOGM3ZC0xYzYwMmZkMTJlMGUiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZXJuZXRlcy1kYXNoYm9hcmQ6YWRtaW4tdXNlciJ9.TafS9ncca0pQwm74MtIUbkmilR_KW3tMmuJIkyUEpm02pn3bptZ4WNwMxge9BeP_WZaDOXkEZ8TQtXLjAzI-oTPY9FP0wGUQ0Ae-OoMtsKefryvJblBZj2g9G5HOVAdUm9vlnl-i0EiwdgYzro-klI5YSvWr4V2-xODlfwTeVvH1lP40__Xu0_uXv7KqdQi6t3Ls_dGHuYnIcRQAQmkDZLx4ADuE0bdA98tOcXWrc88De--aXzWJc8MJtpS4ibJZy71_RgUe5Y1EZjU5aD7PzWJqYSWobuGh9jtrTVR7J91pMp_ubBxAmL0fNdpmzV4tZLVtnsQUEJqMe-zwB_Vnyw
[root@k8s-m1 k8s-dashboard]#
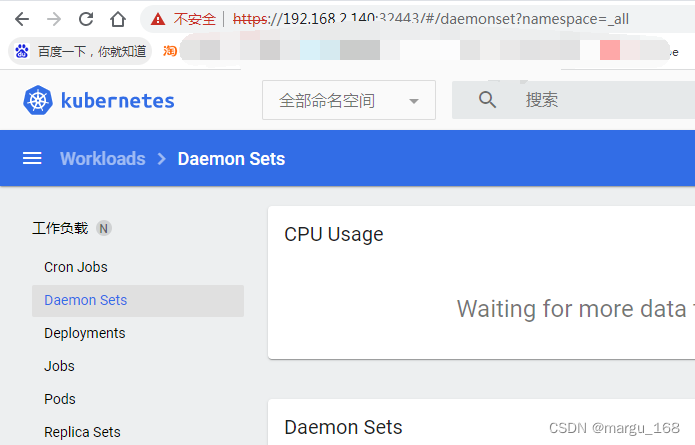
可以检查一下资源是否正常查看访问。
通过kubeconfig登录dashboard
由于每次登录都去找token的话相当麻烦,下面我们生成一个kubeconfig的文件用于登录。
## 创建cluster集群,注意集群信息,ip、端口写正确
[root@k8s-m1 k8s-dashboard]# kubectl config set-cluster kubernetes --certificate-authority=/etc/kubernetes/pki/ca.crt --server="https://192.168.2.250:8443" --embed-certs=true --kubeconfig=./dashboard-admin.conf
## 创建credentials
#创建credentials需要使用上面的kubernetes-dashboard-token-***对应的token信息
[root@k8s-m1 k8s-dashboard]# TOKEN=`kubectl -n kubernetes-dashboard get secret $(kubectl -n kubernetes-dashboard get sa/admin-user -o jsonpath="{.secrets[0].name}") -o go-template="{{.data.token | base64decode}}"`
[root@k8s-m1 k8s-dashboard]# kubectl config set-credentials dashboard-admin --token=$TOKEN --kubeconfig=./dashboard-admin.conf
## 创建context
[root@k8s-m1 k8s-dashboard]# kubectl config set-context dashboard-admin@kubernetes --cluster=kubernetes --user=dashboard-admin --kubeconfig=./dashboard-admin.conf
## 切换context的current-context
[root@k8s-m1 k8s-dashboard]# kubectl config use-context dashboard-admin@kubernetes --kubeconfig=./dashboard-admin.conf
##切换后检查用新的上下文是否能正常查看
[root@k8s-m1 k8s-dashboard]# kubectl get pod -A
## 把dashboard-admin.conf文件下载到电脑桌面,然后使用dashboard-admin.conf作为kubeconfig登录即可
[root@k8s-m1 k8s-dashboard]# sz dashboard-admin.conf
更多关于kubernetes的知识分享,请前往博客主页。编写过程中,难免出现差错,敬请指出