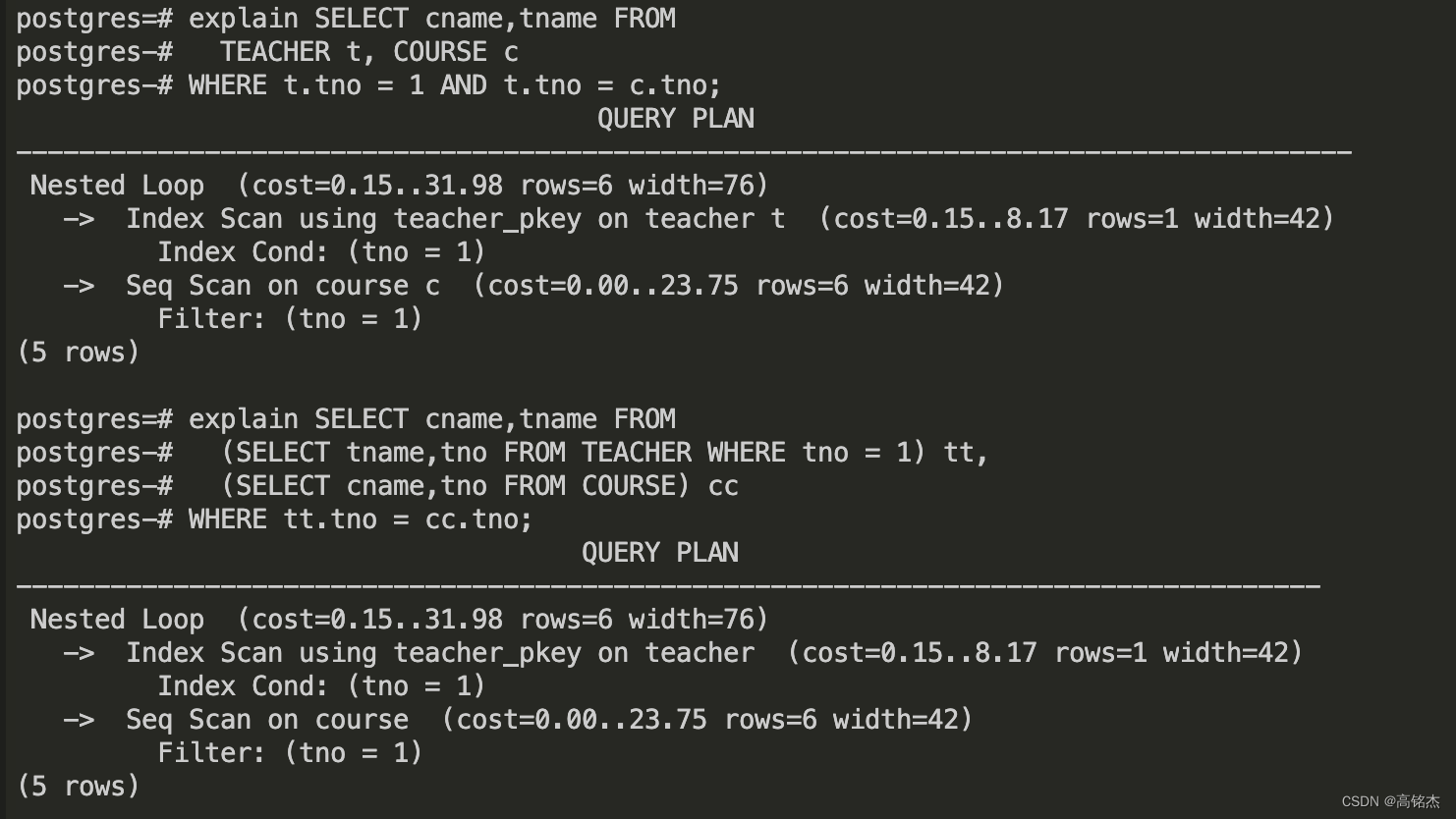
防火墙通过TELNET登录设备
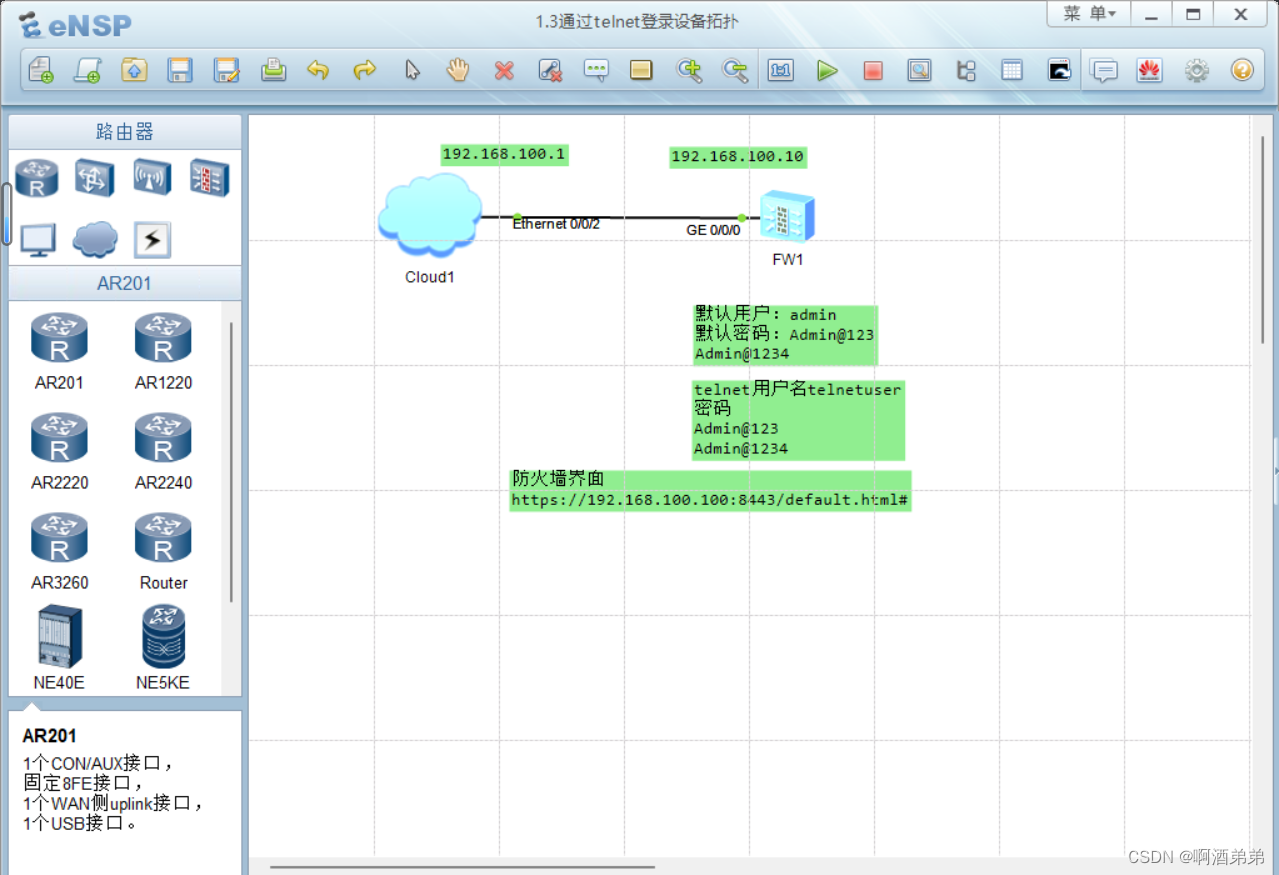
需求:使远程管理员能够通过telnet方式登录到设备上进行管理
| 序号 | 任务 | 任务说明 | 备注 |
|---|---|---|---|
| 1 | 物理连接 | 略 | |
| 2 | 登录设备 | 略 | |
| 3 | 配置设备telnet | 设备默认不支持telnet功能,必须开启telnet功能,以及用于远程登录设备的账号密码等。 | 重点 |
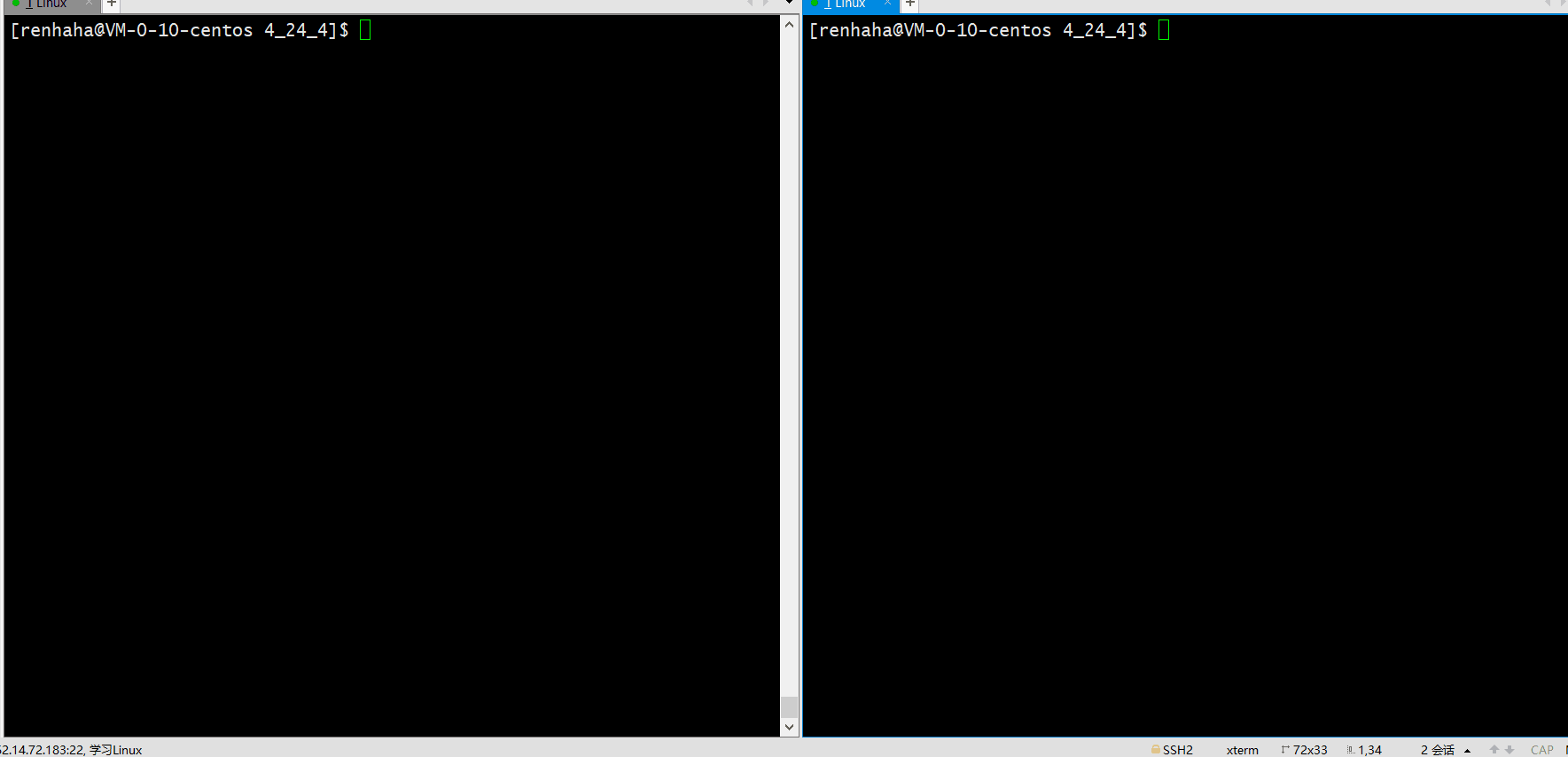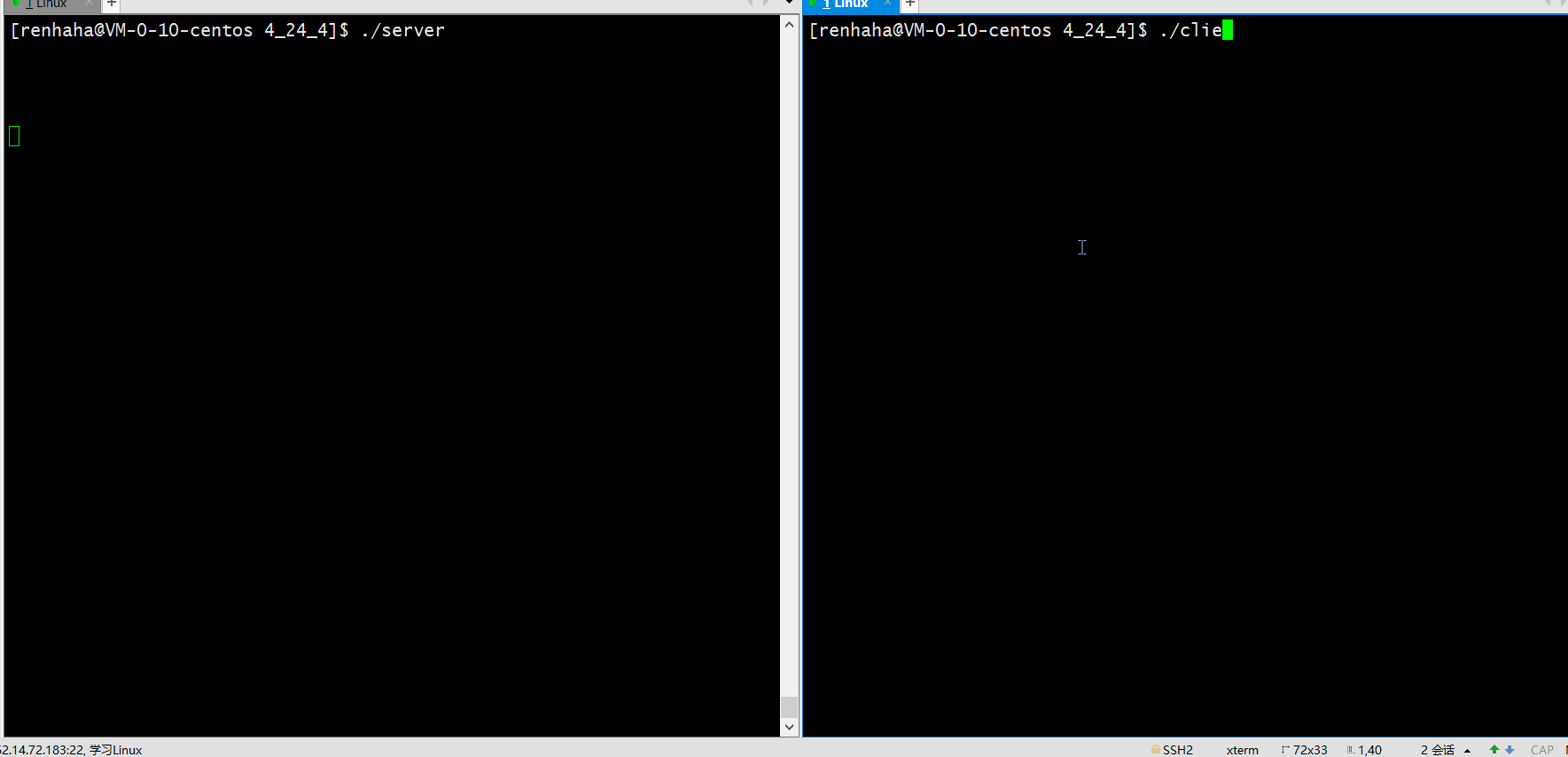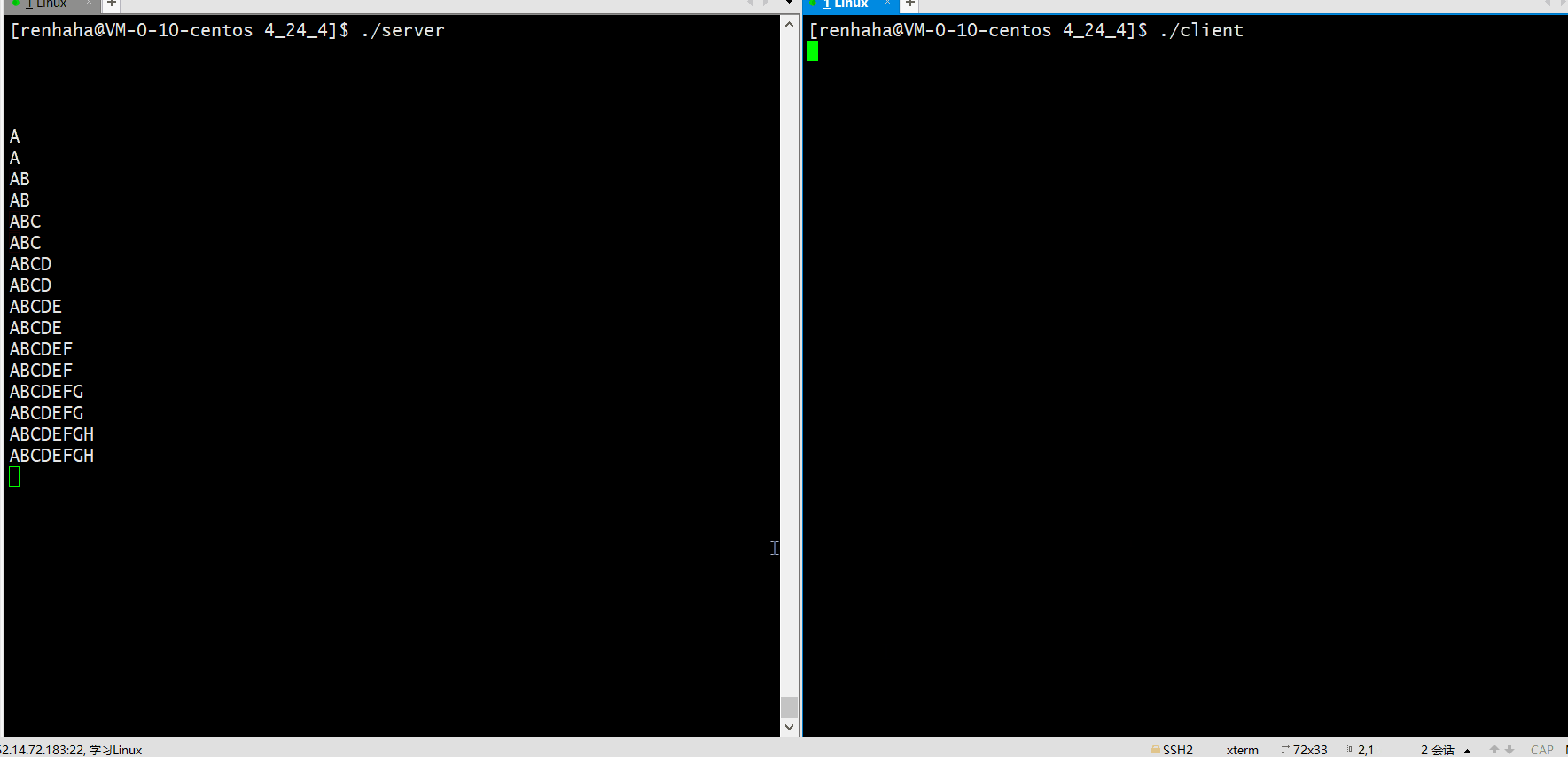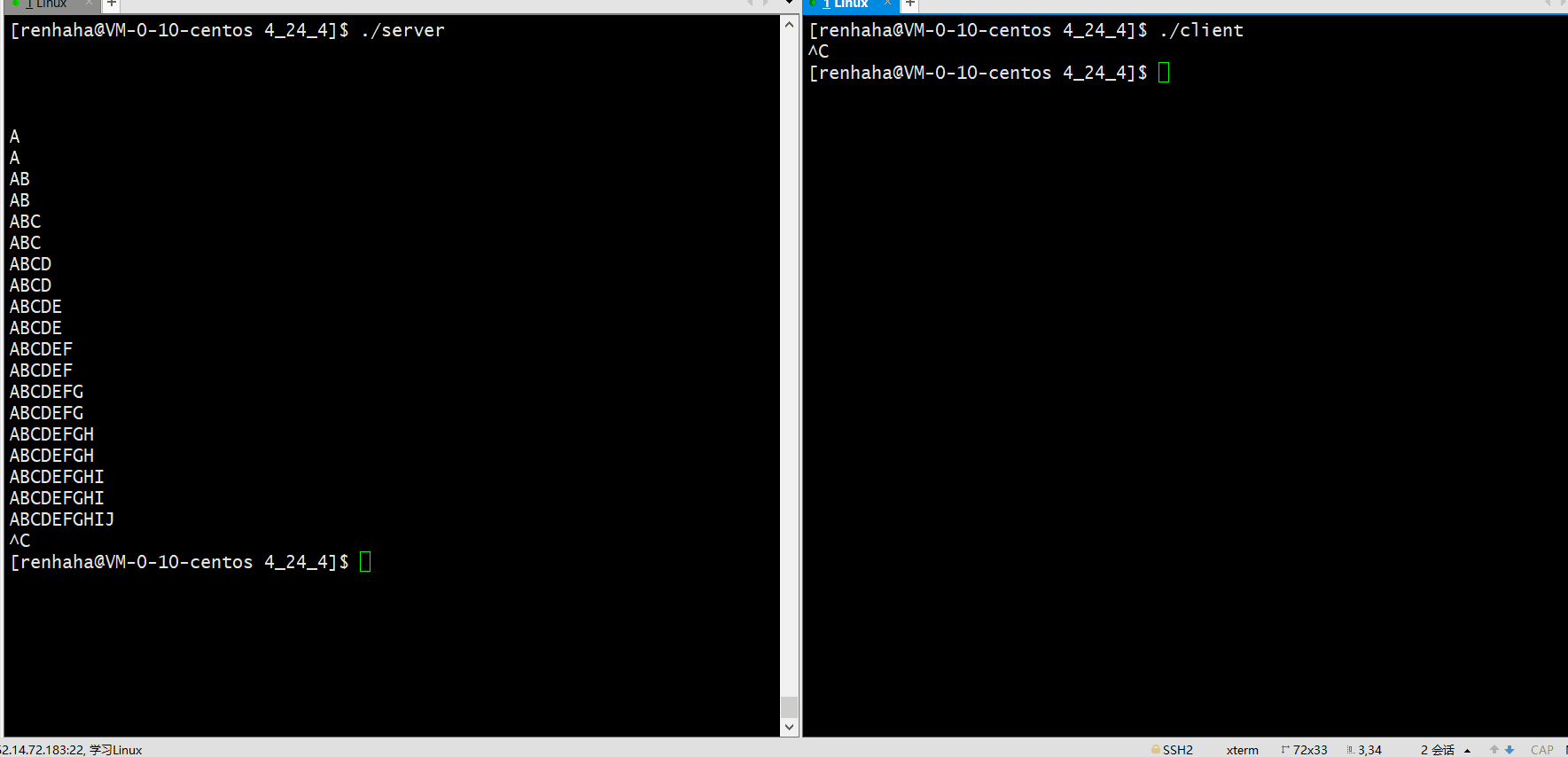
| 4 | 测试telnet功能 | 如图 |
配置设备telnet
- 1.开启telnet
- 2.配置登录接口
- 2.1配置接口的IP地址用于登录
- 2.2配置接口的访问控制功能(可选,防火墙业务口需要此步骤)
- 2.3配置接口加入安全区域(可选,防火墙业务口需要此步骤)
- 3.配置管理员信息
- 3.1配置VTY管理员认证方式为AAA
- 3.2配置telnet管理员
- 3.3为管理员绑定角色(可选,仅防火墙支持)
- 4.登录设备
| 步骤 | 对应代码 |
|---|---|
| 2.配置登录接口 | 2.1配置接口的IP地址用于登录 2.2配置接口的访问控制功能(可选,防火墙业务口需要此步骤) 2.3配置接口加入安全区域(可选,防火墙业务口需要此步骤) |
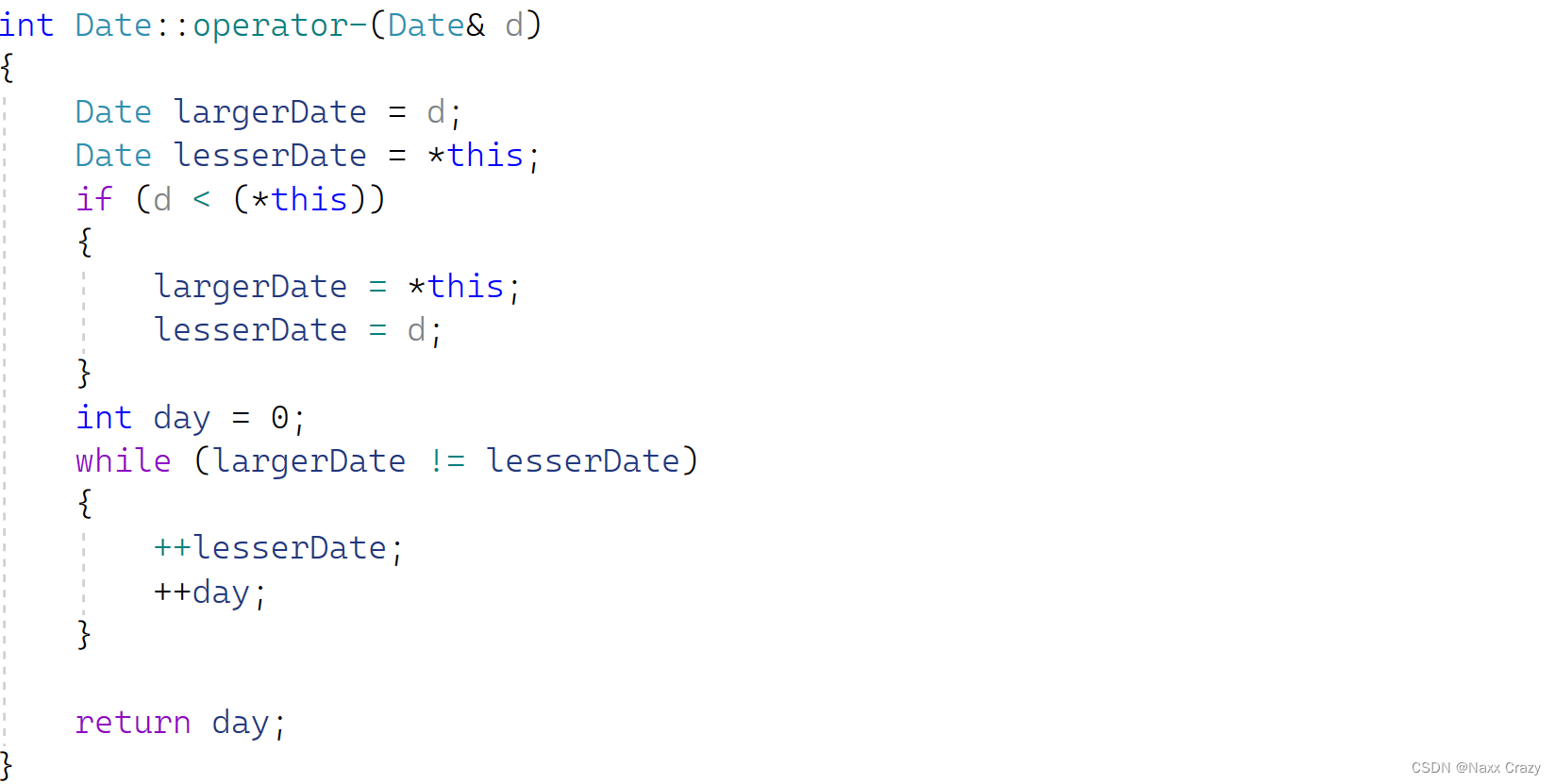
| 2.1配置接口的IP地址用于登录 | <USG6000V1>system-view Enter system view, return user view with Ctrl+Z. [USG6000V1]telnet server enable Info: The Telnet server has been enabled. [USG6000V1]interface g0/0/0 [USG6000V1-GigabitEthernet0/0/0]ip address 192.168.100.100 24 Error: The address already exists. |
| 2.2配置接口的访问控制功能(可选,防火墙业务口需要此步骤) | [USG6000V1-GigabitEthernet0/0/0]service-manage enable [USG6000V1-GigabitEthernet0/0/0]service-manage telnet permit [USG6000V1-GigabitEthernet0/0/0]service-manage https permit [USG6000V1-GigabitEthernet0/0/0]quit |
| 2.3配置接口加入安全区域(可选,防火墙业务口需要此步骤) | [USG6000V1]firewall zone trust [USG6000V1-zone-trust]add interface GigabitEthernet 0/0/0 Error: The interface has been added to trust security zone. [USG6000V1-zone-trust]quit |
| 3.配置管理员信息 | 3.1配置VTY管理员认证方式为AAA 3.2配置telnet管理员 3.3为管理员绑定角色(可选,仅防火墙支持) |
| 3.1配置VTY管理员认证方式为AAA | [USG6000V1]user-interface vty 0 4 [USG6000V1-ui-vty0-4]authentication-mode aaa Warning: The level of the user-interface(s) will be the default level of AAA use rs, please check whether it is correct. [USG6000V1-ui-vty0-4]protocol inbound telnet [USG6000V1-ui-vty0-4]user privilege level 3 [USG6000V1-ui-vty0-4]quit |
| 3.2配置telnet管理员 | [USG6000V1]aaa [USG6000V1-aaa]manager-user telnetuser [USG6000V1-aaa-manager-user-telnetuser]password cipher Admin@1234 Info: You are advised to config on man-machine mode. [USG6000V1-aaa-manager-user-telnetuser]service-type telnet Warning: The user access modes include Telnet or FTP, so security risks exist. [USG6000V1-aaa-manager-user-telnetuser]level 3 Warning: The user binds a role, it’s not allowed to change its level [USG6000V1-aaa-manager-user-telnetuser]quit |
| 3.3为管理员绑定角色(可选,仅防火墙支持) | [USG6000V1-aaa]bind manager-user telnetuser role system-admin [USG6000V1-aaa]quit |
<USG6000V1>system-view
Enter system view, return user view with Ctrl+Z.
[USG6000V1]telnet server enable
Info: The Telnet server has been enabled.
[USG6000V1]interface g0/0/0
[USG6000V1-GigabitEthernet0/0/0]ip address 192.168.100.100 24
Error: The address already exists.
[USG6000V1-GigabitEthernet0/0/0]service-manage enable
[USG6000V1-GigabitEthernet0/0/0]service-manage telnet permit
[USG6000V1-GigabitEthernet0/0/0]service-manage https permit
[USG6000V1-GigabitEthernet0/0/0]quit
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]add interface GigabitEthernet 0/0/0
Error: The interface has been added to trust security zone.
[USG6000V1-zone-trust]quit
[USG6000V1]user-interface vty 0 4
[USG6000V1-ui-vty0-4]authentication-mode aaa
Warning: The level of the user-interface(s) will be the default level of AAA use
rs, please check whether it is correct.
[USG6000V1-ui-vty0-4]protocol inbound telnet
[USG6000V1-ui-vty0-4]user privilege level 3
[USG6000V1-ui-vty0-4]quit
[USG6000V1]aaa
[USG6000V1-aaa]manager-user telnetuser
[USG6000V1-aaa-manager-user-telnetuser]password cipher Admin@1234
Info: You are advised to config on man-machine mode.
[USG6000V1-aaa-manager-user-telnetuser]service-type telnet
Warning: The user access modes include Telnet or FTP, so security risks exist.
[USG6000V1-aaa-manager-user-telnetuser]level 3
Warning: The user binds a role, it's not allowed to change its level
[USG6000V1-aaa-manager-user-telnetuser]quit
[USG6000V1-aaa]bind manager-user telnetuser role system-admin
[USG6000V1-aaa]quit
[USG6000V1]quit
<USG6000V1>save
The current configuration will be written to hda1:/vrpcfg.cfg.
Are you sure to continue?[Y/N]Y
Now saving the current configuration to the slot 0.
Apr 28 2023 08:22:42 USG6000V1 %%01CFM/4/SAVE(s)[0]:The user chose Y when decidi
ng whether to save the configuration to the device.
Save the configuration successfully.
测试


1.3通过telnet登录设备拓扑(网络安全设备小白从零开始)