251、

Which IPv6 OSPF network type is applied to interface Fa0/0 of R2 by default?
A. multipoint
B. broadcast
C. Ethernet
D. point-to-point
252、Which EIGRP feature allows the use of leak maps?
A. neighbor
B. Stub
C. offset-list
D. address-family
253、Which two statements about EIGRP load balancing are true? (Choose two)
A. Cisco Express Forwarding is required to load-balance across interfaces
B. A path can be used for load balancing only if it is a feasible successor
C. EIGRP supports unequal-cost paths by default
D. Any path in the EIGRP topology table can be used for unequal-cost load balancing
E. EIGRP supports 6 unequal-cost paths
254、Which statement about LISP encapsulation in an EIGRP OTP implementation is true?
A. LISP learns the next hop
B. OTP uses LISP encapsulation to obtain routes from neighbors
C. OTP uses LISP encapsulation for dynamic multipoint tunneling
D. OTP maintains the LISP control plane
255、Which two statements about VRRP are true? (Choose two)
A. It supports both MD5 and SHA1 authentication
B. It is assigned multicast address 224.0.0.9
C. Three versions of the VRRP protocol have been defined
D. It is assigned multicast address 224.0.0.8
E. The TTL for VRRP packets must be 255
F. Its IP address number is 115
256、Which two statements about HSRP are true? (Choose two)
A. It supports unique virtual MAC addresses
B. Its virtual MAC is 0000.0C07.ACxx
C. Its default configuration allows for pre-emption
D. It supports tracking
E. Its multicast virtual MAC is 0000.5E00.01xx
257、What are three valid HSRP states? (Choose three)
A. INIT
B. listen
C. full
D. learing
E. speak
F. established
258、Which two statements about IP SLA are true? (Choose two)
A. It uses NetFlow for passive traffic monitoring
B. It can measure MOS
C. The IP SLA responder is a component in the source Cisco device
D. It is Layer 2 transport-independent
E. It uses active traffic monitoring
F. SNMP access is not supported
259、
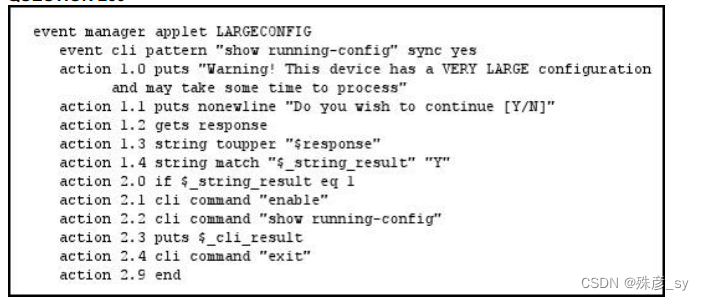
Refer to the exhibit. Which two statements about the EEM applet configuration are true? (Choose two.) CLI;before
A. The EEM applet runs before the CLI command is executed
B. The EEM applet runs after the CLI command is executed
C. The EEM applet requires a case-insensitive response
D. The running configuration is displayed only if the letter Y is entered at the CLI.
260、 Refer to the exhibit. Which network script automation option or tool is used in the exhibit?
 A. EEM
A. EEM
B. Python
C. Bash script
D. NETCONF
E. REST
261、Which data modeling language is commonly used by NETCONF?
A. REST
B. YANG
C. HTML
D. XML
262、Which variable in an EEM applet is set when you use the sync yes option?
A. $_cli_result
B. $_exit_status
C. $_string_result
D. $_result
263、Which IPv6 migration method relies on dynamic tunnels that use the 2002::/16 reserved address space?
A. GRE
B. 6RD
C. 6to4
D. ISATAP
264、A GRE tunnel is down with the error message %TUN-5-RECURDOWN:
![]()
Which two options describe possible causes of the error? (Choose two.)
A. Incorrect destination IP addresses are configured on the tunnel.
B. There is link flapping on the tunnel
C. There is instability in the network due to route flapping
D. The tunnel mode and tunnel IP address are misconfigured
E. The tunnel destination is being routed out of the tunnel interface
265、Refer to the exhibit. An engineer must establish eBGP peering between router R3 and router R4. Both routers should use their loopback interfaces as the BGP router ID.
Which configuration set accomplishes this task?
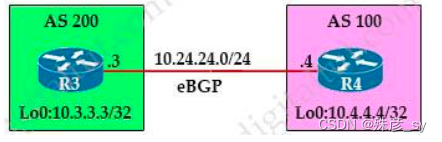
A. R3(config)#router bgp 200
R3(config-router)#neighbor 10.24.24.4 remote-as 100
R3(config-router)#bgp router-id 10.3.3.3
R4(config)#router bgp 100
R4(config-router)#neighbor 10.24.24.3 remote-as 200
R4(config-router)#bgp router-id 10.4.4.4
B. R3(config)#router bgp 200
R3(config-router)#neighbor 10.4.4.4 remote-as 100
R3(config-router)#neighbor 10.4.4.4 update-source loopback0
R4(config)#router bgp 100
R4(config-router)#neighbor 10.3.3.3 remote-as 200
R4(config-router)#neighbor 10.3.3.3 update-source loopback0
C. R3(config)#router bgp 200
R3(config-router)#neighbor 10.24.24.4 remote-as 100
R3(config-router)#neighbor 10.24.24.4 update-source loopback0
R4(config)#router bgp 100
R4(config-router)#neighbor 10.24.24.3 remote-as 200
R4(config-router)#neighbor 10.24.24.3 update-source loopback0
266、What is a benefit of using a Type 2 hypervisor instead of a Type 1 hypervisor?
A. ability to operate on hardware that is running other OSs
B. improved security because the underlying OS is eliminated
C. improved density and scalability
D. better application performance
267、In a wireless Cisco SD-Access deployment, which roaming method is used when a user moves from one access point to another on a different access switch using a single WLC?
A. Layer 3
B. inter-xTR
C. auto anchor
D. fast roam
268、Which DHCP option provides the CAPWAP APs with the address of the wireless controller(s)?
A. 43
B. 66
C. 69
D. 150
269、An engineer must configure HSRP group 300 on a Cisco IOS router. When the router is functional, it must be the active HSRP router. The peer router has been configured using the default priority value. Which three commands are required? (Choose three)
A. standby 300 timers 1 110
B. standby 300 priority 90
C. standby 300 priority 110
D. standby version 2
E. standby version 1
F. standby 300 preempt
270、n a traditional 3 tier topology, an engineer must explicitly configure a switch as the root bridge and exclude it from any further election process for the spanningtree domain. Which action accomplishes this task?
A. Configure the spanning-tree priority to 32768
B. Configure root guard and portfast on all access switch ports
C. Configure BPDU guard in all switch-to-switch connections
D. Configure the spanning-tree priority equal to 0
271、Refer to the exhibit.
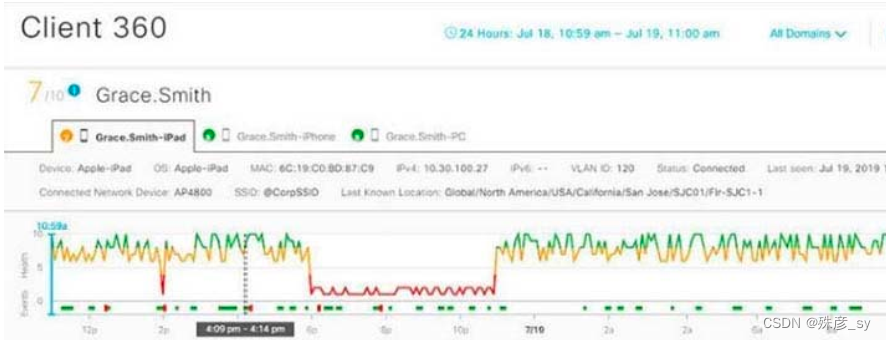
Cisco DNA Center has obtained the username of the client and the multiple devices that the client is using
on the network. How is Cisco DNA Center getting these context details?
A. Those details are provided to Cisco DNA Center by the Identity Services Engine
B. The administrator had to assign the username to the IP address manually in the user database tool on Cisco DNA Center
C. User entered those details in the Assurance app available on iOS and Android devices
D. Cisco DNA Center pulled those details directly from the edge node where the user connected
272、Which QoS queuing method transmits packets out of the interface in the order the packets arrive?
A. custom
B. weighted- fair
C. FIFO
D. priority
273、Refer to the exhibit
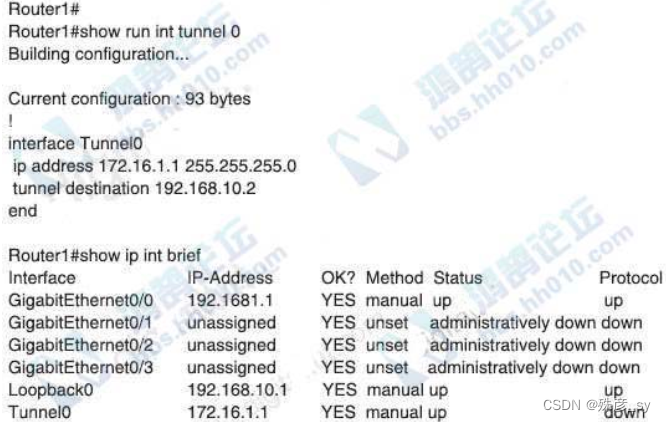
Which command must be applied to Router1 to bring the GRE tunnel to an up/up state?
A. Router1(config-if)#tunnel source Loopback0
B. Router1(config-if)#tunnel source GigabitEthernet0/1
C. Router1(config-if)#tunnel mode gre multipoint
D. Router1(config)#interface tunnel0
274、Refer to the exhibit.

Security policy requires all idle-exec sessions to be terminated in 600 seconds. Which configuration achieves this goal?
A. line vty 0 15
exec-timeout 10 0
B. line vty 0 15
exec-timeout
C. line vty 0 15
absolute-timeout 600
D. line vty 0 4
exec-timeout 600
275、A wireless consultant is designing a high-density wireless network for a lecture hall for 1000 students.
Which antenna type is recommended for this environment?
A. sector antenna
B. dipole antenna
C. parabolic dish
D. omnidirectional antenna
276、Refer to the exhibit. How can you configure a second export destination for IP address 192.168.10.1?
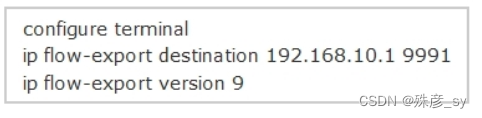
A. Specify a different TCP port
B. Specify a different UDP port
C. Specify a VRF
D. Configure a version 5 flow-export to the same destination
E. Specify a different flow ID
277、Refer to exhibit. What are two reasons for IP SLA tracking failure? (Choose two )
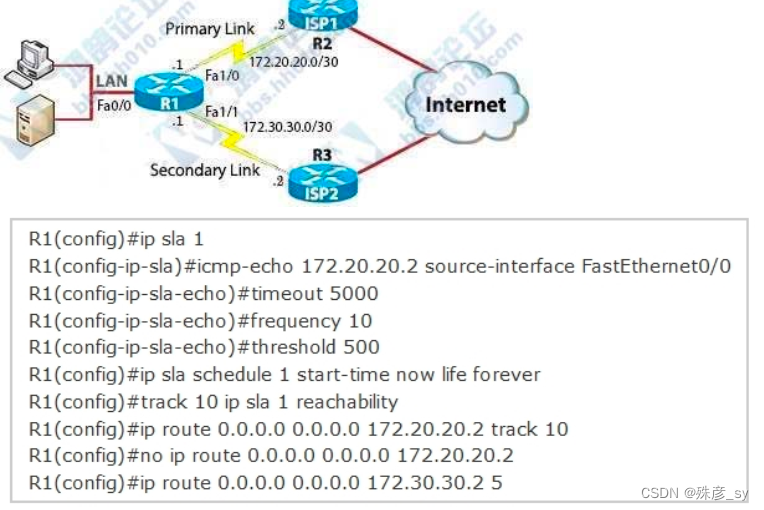
A. The source-interface is configured incorrectly
B. The destination must be 172.30.30.2 for icmp-echo
C. A route back to the R1 LAN network is missing in R2
D. The default route has wrong next hop IP address
E. The threshold value is wrong
278、 Which protocol is responsible for data plane forwarding in a Cisco SD-Access deployment?
A. VXLAN
B. IS-IS
C. OSPF
D. LISP
279、Refer to the exhibit.
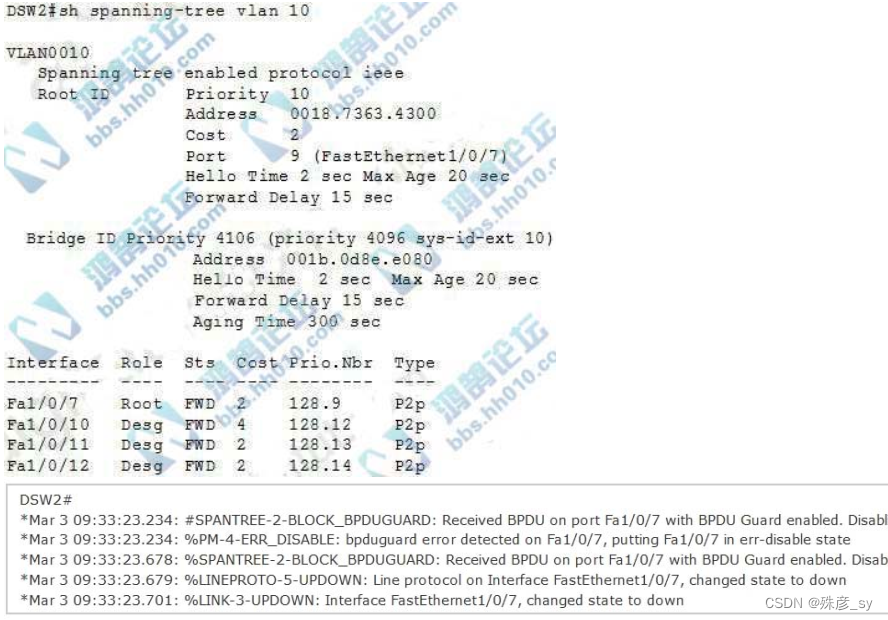
An engineer entered the no spanning-tree bpduguard enable on interface fa1/0/7 command. Which
statement describes the effect of this command?
A. Fa1/0/7 remains in err-disabled state until the shutdown/no shutdown command is entered in the interface configuration mode
B. Interface Fa1/0/7 remains in err-disabled state until the errdisable recovery cause bpduguard command is entered in the interface configuration mode
C. Fa1/0/7 remains in err-disabled state until the errdisable recovery bpduguard command is entered in the interface configuration mode
D. Interface Fa1/0/7 remains in err-disabled state until the spanning-tree portfast bpduguard disable command is entered in the interface configuration mode
E. Interface Fa1/0/7 returns to an up and operational state
280、Refer to the exhibit.
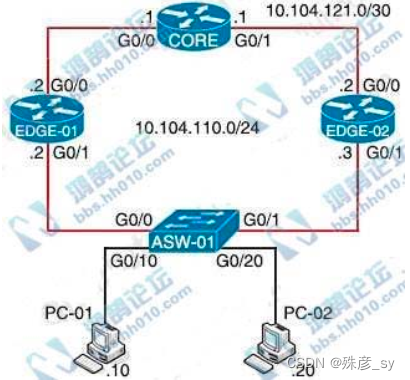
On which interfaces should VRRP commands be applied to provide first hop redundancy to PC-01 and PC-02?
A. G0/0 on Edge-01 and G0/0 on Edge-02
B. G0/1 on Edge-01 and G0/1 on Edge-02
C. G0/0 and G0/1 on Core
D. G0/0 and G0/1 on ASW-01
281、Refer to the exhibit.
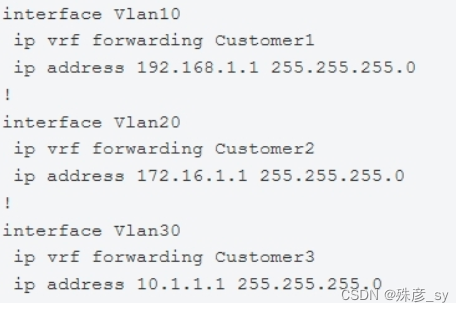
Which configuration allows Customer2 hosts to access the FTP server of Customer1 that has the IP address of 192.168.1.200?
A. ip route vrf Customer1 172.16.1.0 255.255.255.0 172.16.1.1 global
ip route vrf Customer2 192.168.1.200 255.255.255.255 192.168.1.1 global
ip route 192.168.1.0 255.255.255.0 Vlan10
ip route 172.16.1.0 255.255.255.0 Vlan20
B. ip route vrf Customer1 172.16.1.0 255.255.255.0 172.16.1.1 Customer2
ip route vrf Customer2 192.168.1.200 255.255.255.255 192.168.1.1 Customer1
C. ip route vrf Customer1 172.16.1.0 255.255.255.0 172.16.1.1 Customer1
ip route vrf Customer2 192.168.1.200 255.255.255.255 192.168.1.1 Customer2
D. ip route vrf Customer1 172.16.1.1 255.255.255.255 172.16.1.1 global
ip route vrf Customer2 192.168.1.200 255.255.255.0 192.168.1.1 global
ip route 192.168.1.0 255.255.255.0 Vlan10
ip route 172.16.1.0 255.255.255.0 Vlan20
282、Refer to the exhibit.

Which password allows access to line con 0 for a username of “tommy” under normal operation?
A. Cisco
B. local
C. 0 Cisco
D. Tommy
283、 Which tunneling technique is used when designing a Cisco SD-Access fabric data plane?A. VXLAN
B. VRF Lite
C. VRF
D. LISP
284、An engineer has deployed a single Cisco 5520 WLC with a management IP address of 172.16.50.5/24.
The engineer must register 50 new Cisco AIR-CAP2802IE-K9 access points to the WLC using DHCP option 43.
The access points are connected to a switch in VLAN 100 that uses the 172.16.100.0/24 subnet. The engineer has configured the DHCP scope on the switch as follows
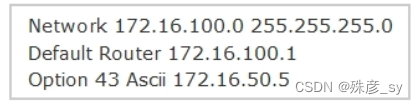
The access points are failing to join the wireless LAN controller. Which action resolves the issue?
A. configure option 43 Hex F104.AC10.3205
B. configure option 43 Hex F104.CA10.3205
C. configure dns-server 172.16.50.5
D. configure dns-server 172.16.100.1
285、Why would a log file contain a * next to the date?
A. The network device is not configured to use NTP time stamps for logging
B. The network device was unable to reach the NTP server when the log messages were recorded.
C. The network device is not configured to use NTP
D. The network device was receiving NTP time when the log messages were recorded
286、Refer to the exhibit.
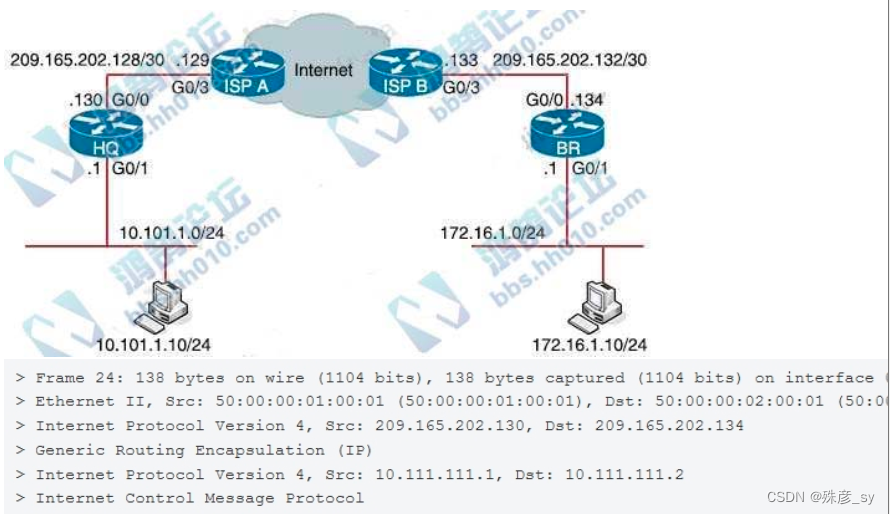
A GRE tunnel has been created between HQ and BR routers. What is the tunnel IP on the HQ router?
A. 209.165.202.130
B. 10.111.111.2
C. 10.111.111.1
D. 209.165.202.134
287、Refer to the exhibit.
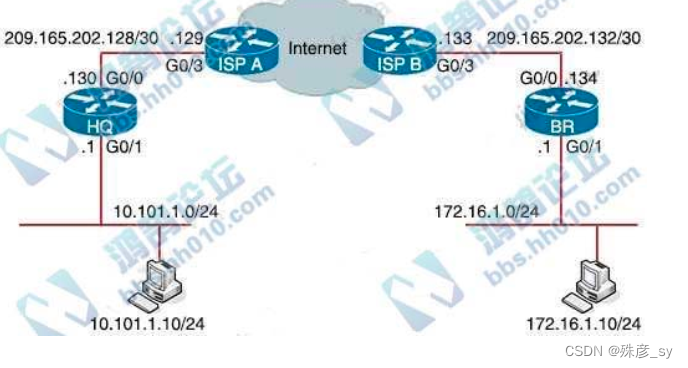
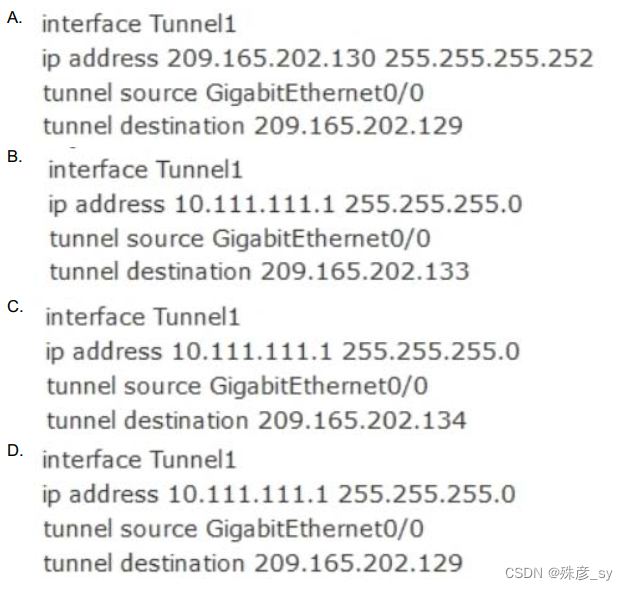
Which configuration must be applied to the HQ router to set up a GRE tunnel between the HQ and BR routers? C
288、A customer has deployed an environment with shared storage to allow for the migration of virtual machines between servers with dedicated operating systems that provide the virtualization platform. What is this operating system described as?
A. hosted virtualization
B. type 1 hypervisor
C. container oriented
D. decoupled
289、Refer to the exhibit.

What is the JSON syntax that is formed from the data?
A. Make”:’Gocar, “Model’: “Zoom”, “Features”: [“Power Windows”, “Manual Dnve”, “Auto AC”]}
B. (“Make”:[ “Gocar”, “Model”: “Zoom”], Features”: [“Power Windows”, “Manual Drive”, “Auto AC”]}
C. {“Make”: Gocar, “Model”: Zoom, “Features”: Power Windows, Manual Drive, Auto AC}
D. {“Make”: “Gocar”, “Model”: “Zoom”, “Features”: [“Power Windows”, “Manual Drive”, “Auto AC”]}
290、 In OSPF, which LAS type is responsible for pointing to the ASBR router?
A. type 1
B. type 2
C. type 3
D. type 4
291、An engineer is configuring GigabitEthernet1/0/0 for VRRP. When the router has the highest priority In group 5, It must assume the master role. Which command set should the engineer add to the configuration to accomplish this task?
interface GigabitEthernet1/0/0
description To IDF A 38-72-100-76
ip address 172.16.13.2 255.255.255.0
A. standby 5 ip 172.16.13.254
standby 5 priority 100
standby 5 preempt
B. vrrp 5 ip 172.16.13.254 255.255.255.0
vrrp 5 track 1 decrement 10
vrrp preempt
C. standby 5 ip 172.16.13.254
standby 5 priority 100
standby 5 track 1 decrement 10
D. vrrp 5 ip 172.16.13.254
vrrp 5 priority 100
292、Which HHTP status code is the correct response for a request with an incorrect password applied to a REST API session?
A. HTTP Status Code 200
B. HTTP Status Code 302
C. HTTP Status Code 401
D. HTTP Status Code: 504
293、Drag and drop the LIPS components on the left to the correct description on the right.
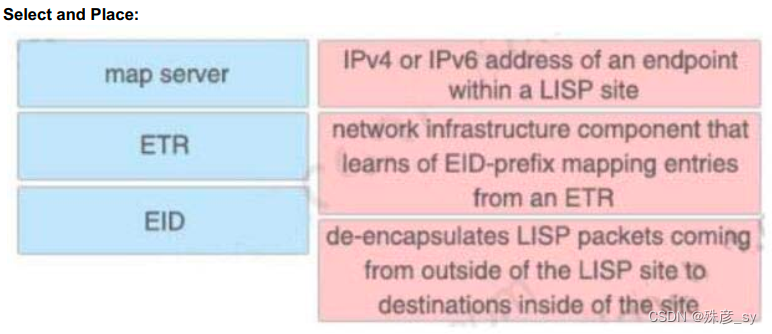
294、

Refer to the exhibit,which configuration must be applied to R1 to enbale R1 to reach the server at
172.16.0.1 ?
A. interface Ethernet 0/0
vrf forwarding hotel
ip address 172.16.0.7 255.255.0.0
router ospf 44 vrf Hotel
network 172.16.0.0 0.0.255.255 area 0
B. interface Ethernet 0/0
vrf forwarding bank
ip address 172.16.0.7 255.255.0.0
router ospf 44 vrf bank
network 172.16.0.0 0.0.255.255 area 0
C. interface Ethernet 0/0
ip address 172.16.0.7 255.255.0.0
router ospf 44 vrf Hotelnetwork 172.16.0.0 0.0.255.255 area 0
D. interface Ethernet 0/0
ip address 172.16.0.7 255.255.0.0
router ospf 44 vrf bank
network 172.16.0.0 0.0.255.255 area 0
295、Refer to the exhibit.What does the snippet of code achive?
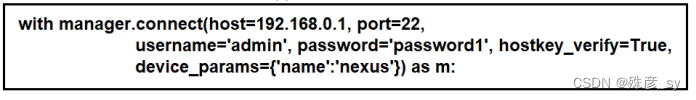
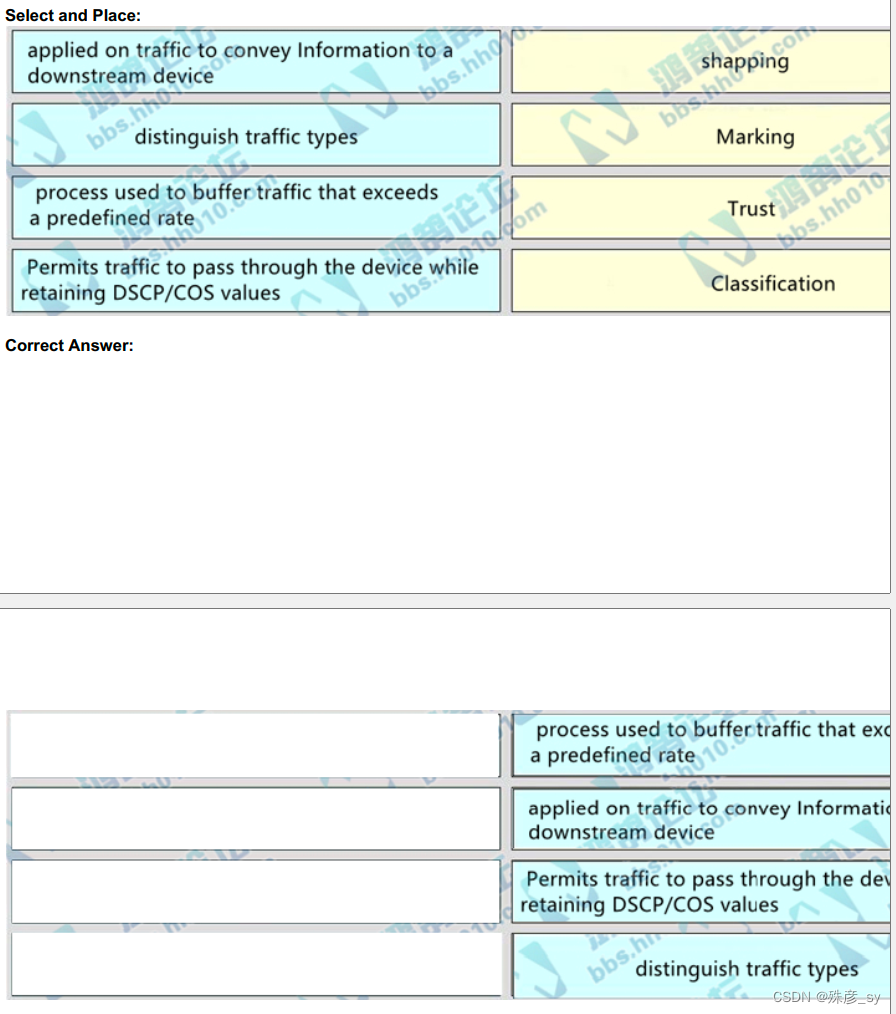
A. It opens an ncclient connection to a cisco Nexus device and maintains it for the duration of the context
B. It creates an SSH connection using the SSH key that is stored,and the password is ignored
C. It opens a tunnel and encapsulates the login information,if the host key is correct
D. It creates a temporary connection to a Cisco Nexus device and retrieves a token to be used for API calls
296、Using the EIRP formula.what parameter is subtracted to determine the EIRP value ?
A. transmitter power
B. antenna cable loss
C. antenna gain
D. signal-to-noise ratio
297、In Cisco SD-WAN,which protocol is used to measure link quality ?
A. BFD
B. RSVP
C. IPsec
D. OMP
298、Refer to the exhibit. Which level message does the WLC send to the syslog server?
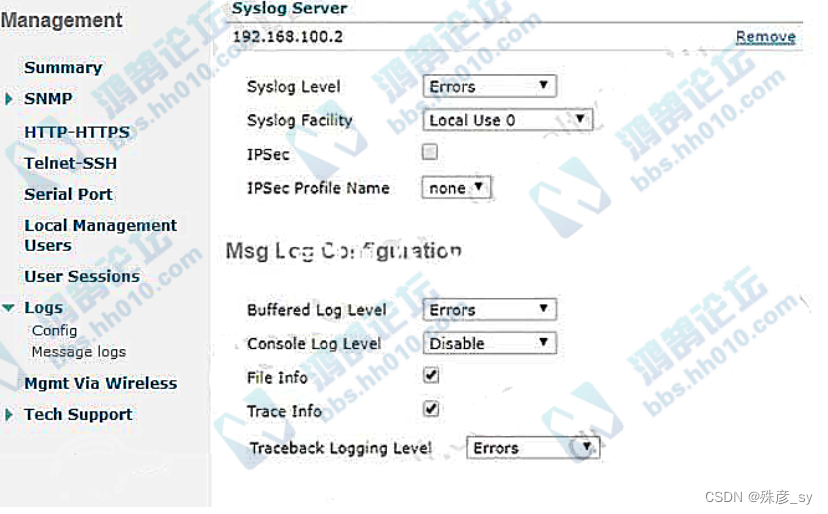
A. syslog level errors and less severity messages
B. syslog level errors messages
C. all syslog levels messages
D. syslog level errors and greater severity messages
299、Refer to the exhibit.
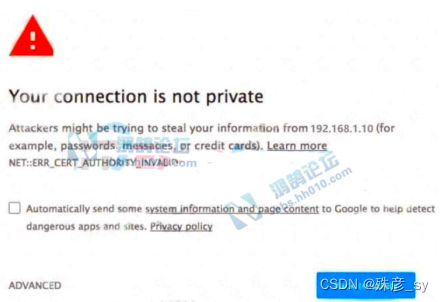
An engineer is designing a guest portal on Cisco ISE using the default configuration. During the testing
phase, the engineer receives a warning when displaying the guest portal. Which issue is occurring?
A. The server that is providing the portal has an expired certificate
B. The server that is providing the portal has a self-signed certificate
C. The connection is using an unsupported protocol
D. The connection is using an unsupported browser
300、 Drag and drop the characteristics from the left onto the QoS components they describe on the right.