201、An engineer attempts to configure a trunk between switch SW1 and switch SW2 using DTP, but the trunk does not form. Which command should the engineer apply to switch SW2 to resolve this issue?

A. switchport mode dynamic desirable
B. switchport mode access
C. no switchport
D. switchport nonegotiate
202、 How does the EIGRP metric differ from the OSPF metric?
A. The EIGRP metric is calculated based on bandwidth only. The OSPF metric is calculated on delay only.
B. The EIGRP metric is calculated based on delay only. The OSPF metric is calculated on bandwidth and delay
C. The EIGRP metric is calculated based on bandwidth and delay. The OSPF metric is calculated on bandwidth only.
D. The EIGRP metric is calculated based on hop count and bandwidth. The OSPF metric is calculated on bandwidth and delay
203、Which deployment option of Cisco NGFW provides scalability?
A. clustering
B. high availability
C. tap
D. inline tap
204、What are two considerations when using sso as a network redundancy feature? (Choose two.)
A. must be combined with NSF to support uninterrupted Layer 3 operations
B. requires synchronization between supervisors in order to guarantee continuous connectivity
C. the multicast state is preserved during switchover
D. must be combined with NSF to support uninterrupted Layer 2 operations
E. both supervisors must be configured separately
205、What is the purpose of the LISP routing and addressing architecture?
A. It creates two entries for each network node, one for its identity and another for its location on the network
B. It allows LISP to be applied as a network virtualization overlay though encapsulation
C. It allows multiple instances of a routing table to co exist within the same router
D. It creates head-end replication used to deliver broadcast and multicast frames to the entire network
206、In a Cisco SD- Access fabric, which control plane protocol is used for mapping and resolving endpoints?
A. DHCP
B. VXLAN
C. SXP
D. LISP
207、

Refer to the exhibit. The traceroute fails from R1 to R3. What is the cause of the failure?
A. An ACL applied inbound on loopbacko of R2 is dropping the traffic.
B. Redistribution of connected routes into OSPF is not configured
C. An ACL applied inbound on fa0/1 of R3 is dropping the traffic.
D. The loopback on R3 is in a shutdown state
208、Refer to the exhibit. Which two commands ensure that DSW1 becomes root bridge for
VLAN 10 and 20? (Choose two)

A. spanning-tree mstp vlan 10,20 root primary
B. spanning-tree mst vlan 10,20 priority root
C. spanning-tree mst 1 root primary
D. spanning-tree mst 1 priority 4096
E. spanning-tree mst 1 priority 1
209、What is the responsibility of a secondary WLC?
A. It enables Layer 2 and Layer 3 roaming between itself and the primary controller.
B. It shares the traffic load of the LAPs with the primary controller
C. It avoids congestion on the primary controller by sharing the registration load on the LAPs.
D. It registers the LAPs if the primary controller fails.
210、A wireless consultant is designing a high-density wireless network for a lecture hall for 1000 students.
Which antenna type is recommended for this environment?
A. sector antenna
B. dipole antenna
C. parabolic dish
D. omnidirectional antenna
211、Which command set configures RSPAN to capture outgoing traffic from VLAN3 on interface
GigabitEthernet 0/3 while ignoring other VLAN trafic on the same interface?
A. monitor session 2 source interface gigabitethernet 0/3 tx
monitor session 2 filter vlan 1 - 2 , 4 - 4094
B. monitor session 2 source interface gigabitethernet 0/3 tx
monitor session 2 filter vlan 3
C. monitor session 2 source interface gigabitethernet 0/3 rx
monitor session 2 filter vlan 1 - 2 , 4 - 4094
D. monitor session 2 source interface gigabitethernet 0/3 rx
monitor session 2 filter vlan 3
212、Refer to the exhibit Onlv administrators from the subnet 10.10.10.0/24 are permitted to have access to the router. A secure protocol must be for the remote access and management of the router instead of cleartext protocols. Which configuration achieves this goal?

A. access-list 23 permit 10.10.10.0 0.0.0.255
line vty 0 15
access-class 23 out
transport input all
B. access-list 23 permit 10.10.10.0 255.255.255.0
line vty 0 15
access-class 23 in
transport input ssh
C. access-list 23 permit 10.10.10.0 0.0.0.255
line vty 0 4
access-class 23 in
transport input ssh
D. access-list 23 permit 10.10.10.0 0.0.0.255
line vty 0 15
access-class 23 in
transport input ssh
213、 Refer to the exhibit. An engineer must deny Telnet taffic from the loopback interface of router R3 to the loopback interface of router R2 during the weekend hours. All other traffic between the loopback interfaces of routers R3 and R2 must be allowed at all times. Which command set accomplishes this task?

A. R3(config )#time-range WEEKEND
R3(config-time range)#periodic Saturday Sunday 00:00 to 23:59
R3(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range
WEEKEND
R3(config)#access-list 150 permit ip any any time-range WEEKEND
R3(config)#interface G0/1
R3(config-if)#ip access-group 150 out
B. R1(config )#time-range WEEKEND
R1(config-time range)#periodic weekend 00:00 to 23:59
R1(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range
WEEKEND
R1(config)#access-list 150 permit ip any any
R1(config)#interface G0/1R1(config-if)#ip access-group 150 in
C. R1(config )#time-range WEEKEND
R1(config-time range)#periodic Friday Sunday 00:00 to 23:59
R1(config)#access-list 150 deny tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range
WEEKEND
R1(config)#access-list 150 permit ip any any
R1(config)#interface G0/1
R1(config-if)#ip access-group 150 in
D. R3(config )#time-range WEEKEND
R3(config-time range)#periodic weekend 00:00 to 23:59
R3(config)#access-list 150 permit tcp host 10.3.3.3 host 10.2.2.2 eq 23 time-range
WEEKEND
R3(config)#access-list 150 permit ip any any time-range WEEKEND
R3(config)#interface G0/1
R3(config-if)#ip access-group 150 out
214、What is provided by the Stealthwatch component of the Cisco Cyber Threat Defense solution?
A. real-time threat management to stop DDoS attacks to the core and access networks
B. real-time awareness of users, devices, and traffic on the network
C. malware control
D. dynamic threat control for web traffic
215、An engineer is configuring GigabitEthernet1/0/0 for VRRP. When the router has the highest priority in group 5, it must assume the master role. Which command set should the engineer add to the configuration to accomplish this task?
interface GigabitEthernet1/0/0
description To IDF A 38-38-720.28
ip address 172.16.13.2 255 255.255.0
A. vrrp 5 ip 172.16.13.254 255.255.255.0
vrrp 5 track 1 decrement 10
vrrp 5 preempt
B. standby 5 ip 172.16.13.254
standby 5 priority 100
standby 5 track 1 decrement 10C. standby 5 ip 172.16.13.254
standby 5 priority 100
standby 5 preempt
D. vrrp 5 ip 172.16.13.254
vrrp 5 priority 100
216、Which A record type should be configured for access points to resolve the IP address of a wireless LAN
controller using DNS?
A. CISCO.CONTROLLER.localdomain
B. CISCO.CAPWAP.CONTROLLER.localdomain
C. CISCO-CONTROLLER.localdomain
D. CISCO-CAPWAP-CONTROLLER.localdomain
217、

Refer to the exhibit. An engineer has configured Cisco ISE to assign VLANs to clients based on their method of authentication, but this is not working as expected. Which action will resolve this issue?
A. enable AAA override
B. utilize RADIUS profiling
C. require a DHCP address assignment
D. set a NAC state
218、
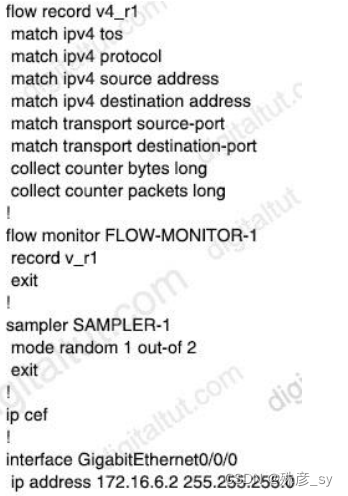
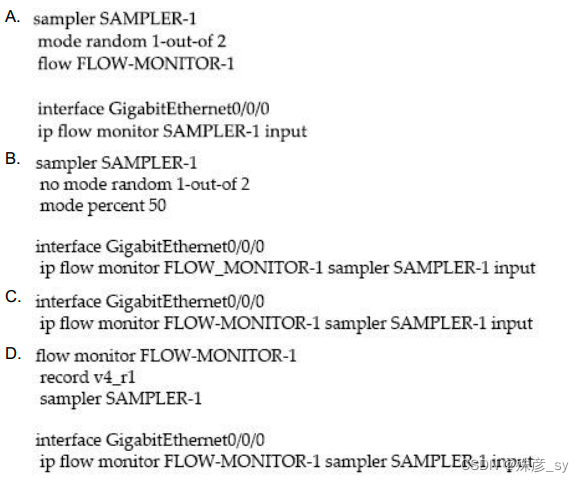
Refer to the exhibit. Which command set must be added to the configuration to analyze
50 packets out of every 100? C
219、An engineer must configure a ACL that permits packets which include an ACK in the
TCP header. Which entry must be included in the ACL?
A. access-list 110 permit tcp any any eq 21 tcp-ack
B. access-list 10 permit ip any any eq 21 tcp-ack
C. access-list 10 permit tcp any any eq 21 established
D. access-list 110 permit tcp any any eq 21 established
220、Which two sources cause interference for Wi-Fi networks? (Choose two)
A. mirrored wall
B. fish tank
C. 900MHz baby monitor
D. DECT 6.0 cordless
E. incandesent lights
221、What are two differences between the RIB and the FIB? (Choose two)
A. The FIB is derived from the data plane, and the RIB is derived from the FIB
B. The RIB is a database of routing prefixes, and the FIB is the information used to
choose the egress interface for each packet
C. FIB is a database of routing prefixes, and the RIB is the information used to choose
the egress interface for each packet
D. The FIB is derived from the control plane, and the RIB is derived from the FIB.
E. The RIB is derived from the control plane, and the FIB is derived from the RIB.
222、What is the function of the fabric control plane node in a Cisco SD-Access deployment?
A. It is responsible for policy application and network segmentation in the fabric
B. It performs traffic encapsulation and security profiles enforcement in the fabric
C. It holds a comprehensive database that tracks endpoints and networks in the fabric
D. It provides integration with legacy nonfabric-enabled environments
223、

Refer to the exhibit. An engineer must allow all users in the 10.2.2.0/24 subnet to access
the Internet. To conserve address space, the public interface address of 209.165.201.1
must be used for all external communication. Which command set accomplishes these
requirements?
A. access-list 10 permit 10.2.2.0 0.0.0.255
interface G0/3 ip nat outside
interface G0/2 ip nat inside
ip nat inside source list 10 interface G0/2 overload
B. access-list 10 permit 10.2.2.0 0.0.0.255
interface G0/3 ip nat outside
interface G0/2 ip nat inside
ip nat inside source list 10 209.165.201.1
C. access-list 10 permit 10.2.2.0 0.0.0.255
interface G0/3 ip nat outside
interface G0/2 ip nat inside
ip nat inside source list 10 interface G0/3
D. access-list 10 permit 10.2.2.0 0.0.0.255
interface G0/3 ip nat outside
interface G0/2 ip nat inside
ip nat inside source list 10 interface G0/3 overload
224、

Refer to the exhibit. After an engineer configures an EtherChannel between switch SW1
and switch SW2, this error message is logged on switch SW2. Based on the output from
SW1 and the log message received on Switch SW2, what action should the engineer
take to resolve this issue?
A. Configure the same protocol on the EtherChannel on switch SW1 and SW2.
B. Connect the configuration error on interface Gi0/1 on switch SW1.
C. Define the correct port members on the EtherChannel on switch SW1.
D. Correct the configuration error on interface Gi0/0 switch SW1
225、Which method does Cisco DNA Center use to allow management of non-Cisco devices
through southbound protocols?
A. It creates device packs through the use of an SDK
B. It obtains MIBs from each vendor that details the APIs available
C. It uses an API call to interrogate the devices and register the returned data.
D. It imports available APIs for the non-Cisco device in a CSV format.
226、
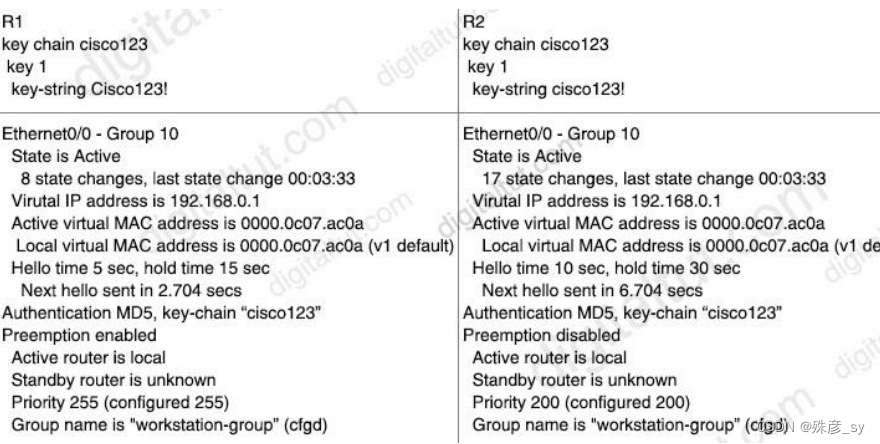
An engineer is installing a new pair of routers in a redundant configuration. When
checking on the standby status of each router the engineer notices that the routers are
not functioning as expected. Which action will resolve the configuration error?
A. configure matching hold and delay timers
B. configure matching key-strings
C. configure matching priority values
D. configure unique virtual IP addresses
227、 What is used to validate the authenticity of the client and is sent in HTTP requests as a
JSON object?
A. SSH
B. HTTPS
C. JWT
D. TLS
228、In a Cisco SD-Access wireless architecture, which device manages endpoint ID to Edge
Node bindings?
A. fabric control plane node
B. fabric wireless controller
C. fabric border node
D. fabric edge node
229、Which control plane protocol is used between Cisco SD-WAN routers and vSmart
controllers?
A. BGP
B. OMP
C. TCP
D. UDP
230、In a Cisco Catalyst switch equipped with two supervisor modules an administrator must
temporally remove the active supervisor from the chassis to perform hardware
maintenance on it. Which mechanism ensure that the active supervisor removal is not
disruptive to the network operation?
A. NSF/NSR
B. SSO
C. HSRP
D. VRRP
231、Refer to the exhibit.

The IP SLA is configured in a router. An engineer must configure an EEM applet to shutdown the interface and bring it back up when there is a problem with the IP SLA. Which configuration should the engineer use?
A. event manager applet EEM_IP_SLA
event track 10 state down
B. event manager applet EEM_IP_SLA
event track 10 state unreachable
C. event manager applet EEM_IP_SLA
event sla 10 state unreachable
D. event manager applet EEM_IP_SLA
event sla 10 state down
232、A network engineer is configuring Flexible NetFlow and enters these commands:

Which are two results of implementing this feature instead of traditional NetFlow?
(Choose two)
A. Only the flows of top 100 talkers are exported
B. CPU and memory utilization are reduced
C. The data export flow is more secure
D. The accuracy of the data to be analyzed is improved
E. The number of packets to be analyzed are reduced
233、 Which feature of EIGRP is not supported in OSPF?
A. load balancing of unequal-cost paths
B. load balance over four equal-costs paths
C. uses interface bandwidth to determine best path
D. per-packet load balancing over multiple paths
234、In a Cisco SD-WAN solution, how is the health of a data plane tunnel monitored?
A. with IP SLA
B. ARP probing
C. using BFD
D. with OMP
235、A server running Linux is providing support for virtual machines along with DNS and DHCP services for a small business. Which technology does this represent?
A. container
B. Type 1 hypervisor
C. hardware pass-thru
D. Type 2 hypervisor
236、Which characteristic distinguishes Ansible from Chef?
A. Ansible lacs redundancy support for the master server. Chef runs two masters in an active/active mode
B. Ansible uses Ruby to manage configurations. Chef uses YAML to manage configurations
C. Ansible pushes the configuration to the client. Chef client pulls the configuration from the server
D. The Ansible server can run on Linux, Unix or Windows. The Chef server must run on Linux or Unix
237、What function does vxlan perform in an SD-Access deployment?
A. policy plane forwarding
B. control plane forwarding
C. data plane forwarding
D. systems management and orchestration
238、Refer to the exhibit.

MTU has been configured on the underlying physical topology, and no MTU command has been
configured on the tunnel interfaces. What happens when a 1500-byte IPv4 packet traverses the GRE tunnel from host X to host Y, assuming the DF bit is cleared?
A. The packet arrives on router C without fragmentation
B. The packet is discarded on router A
C. The packet is discarded on router B
D. The packet arrives on router C fragmented
239、
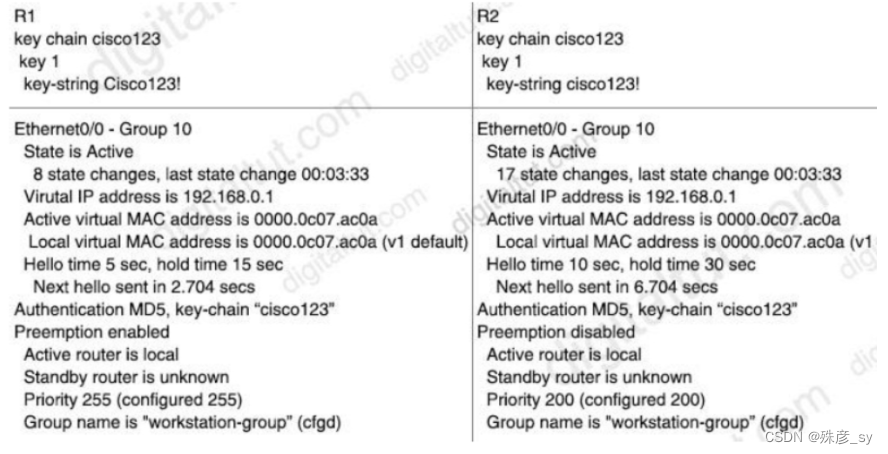
Refer to the exhibit.An engineer is installing a new pair of routers in a redundant configuration. Which protocol ensures that traffic is not disrupted in the event of a hardware failure?
A. HSRPv1
B. GLBP
C. VRRP
D. HSRPv2
240、
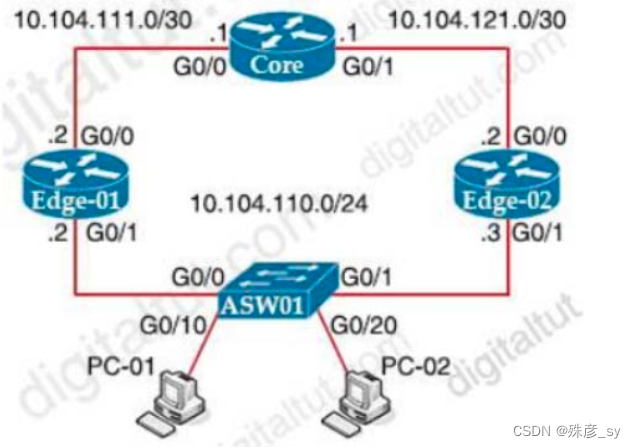
Refer to the exhibit. Edge-01 is currently operational as the HSRP primary with priority
110. Which command on Edge-02 causes it to take over the forwarding role when Edge-
01 is down?
A. standby 10 priority
B. standby 10 preempt
C. standby 10 track
D. standby 10 timers
241、 What is one fact about Cisco SD-Access wireless network deployments?
A. The access point is part of the fabric underlay
B. The WLC is part of the fabric underlay
C. The access point is part the fabric overlay
D. The wireless client is part of the fabric overlay
242、Which QoS mechanism will prevent a decrease in TCP performance?
A. Shaper
B. Rate-Limit
C. Policer
D. Fair-Queue
E. WRED
F. LLQ
243、Which statement about the default QoS configuration on a Cisco switch is true?
A. The Cos value of each tagged packet is modified
B. Port trust is enabled
C. The Port Cos value is 0
D. All traffic is sent through four egress queues
244、How are the Cisco Express Forwarding table and the FIB related to each other?
A. Cisco Express Forwarding uses a FIB to make IP destination prefix-based switching decisions correct
B. The FIB is used to populate the Cisco Express Forwarding table
C. There can be only one FIB but multiple Cisco Express Forwarding tables on IOS devices
D. The Cisco Express Forwarding table allows route lookups to be forwarded to the route processor for processing before they are sent to the FIB
245、Which two statements about Cisco Express Forwarding load balancing are true? (Choose two)
A. Each hash maps directly to a single entry in the RIB
B. It combines the source IP address subnet mask to create a hash for each destination
C. Cisco Express Forwarding can load-balance over a maximum of two destinations
D. It combines the source and destination IP addresses to create a hash for each destination
E. Each hash maps directly to a single entry in the adjacency table
246、Which two statements about VRF-lite are true? (Choose two)
A. It can support multiple customers on a single switch
B. It supports most routing protocols, including EIGRP, ISIS, and OSPF
C. It should be used when a customer’s router is connected to an ISP over OSPF
D. It can increase the packet switching rate
E. It supports MPLS-VRF label exchange and labeled packets
247、

You have just created a new VRF on PE3. You have enabled debug ip bgp vpnv4 unicast updates on PE1,and you can see the route in the debug, but not in the BGP VPNv4 table. Which two statements are true?(Choose two)
A. After you configure route-target import 999:999 for a VRF on PE1, the route will be accepted
B. VPNv4 is not configured between PE1 and PE3
C. address-family ipv4 vrf is not configured on PE3
D. PE1 will reject the route due to automatic route filtering
E. After you configure route-target import 999:999 for a VRF on PE3, the route will be accepted
248、What is the main function of VRF-lite?
A. To connect different autonomous systems together to share routes
B. To allow devices to use labels to make Layer 2 Path decisions
C. To route IPv6 traffic across an IPv4 backbone
D. To segregate multiple routing tables on a single device
249、

Which LISP component do routers in the public IP network use to forward traffic between the two
networks?
A. RLOC
B. map resolver
C. EID
D. map Server
250、Into which two pieces of information does the LISP protocol split the device identity?(Choose two)
A. Device ID
B. Enterprise Identifier
C. LISP ID
D. Routing Locator
E. Resource Location
F. Endpoint Identifier