51、Which statement about a fabric access point is true?
A. It is in local mode and must be connected directly to the fabric edge switch.
B. It is in local mode and must be connected directly to the fabric border node
C. It is in FlexConnect mode and must be connected directly to the fabric border node.
D. It is in FlexConnect mode and must be connected directly to the fabric edge switch.
52、Which First Hop Redundancy Protocol maximizes uplink utilization and minimizes the amount of configuration that is necessary?
A. GLBP
B. HSRP v2
C. VRRP
D. HSRP v1
53、Which standard access control entry permits traffic from odd-numbered hosts in the 10.0.0.0/24 subnet?
A. permit 10.0.0.0 0.0.0.1
B. permit 10.0.0.1 0.0.0.254
C. permit 10.0.0.1 0.0.0.0
D. permit 10.0.0.0 255.255.255.254
54、Refer to the exhibit
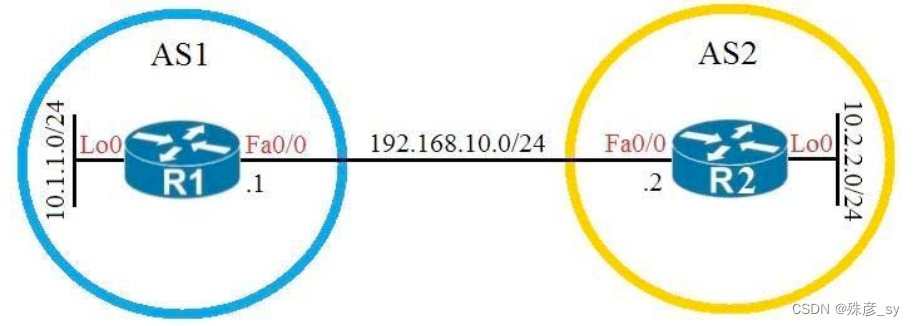
Which configuration establishes EBGP connected neighborship between these two directly connected neighbors and exchanges the loopback network of the two routers through BGP?
A. R1(config)#router bgp 1
R1(config-router)#neighbor 192.168.10.2 remote-as 2
R1(config-router)#network 10.1.1.0 mask 255.255.255.0
R2(config)#router bgp 2
R2(config-router)#neighbor 192.168.10.1 remote-as 1
R2(config-router)#network 10.2.2.0 mask 255.255.255.0
B. R1(config)#router bgp 1
R1(config-router)#neighbor 10.2.2.2 remote-as 2
R1(config-router)#network 10.1.1.0 mask 255.255.255.0
R2(config)#router bgp 2
R2(config-router)#neighbor 10.1.1.1 remote-as 1
R2(config-router)#network 10.2.2.0 mask 255.255.255.0
C. R1(config)#router bgp 1
R1(config-router)#neighbor 192.168.10.2 remote-as 2
R1(config-router)#network 10.0.0.0 mask 255.0.0.0
R2(config)#router bgp 2
R2(config-router)#neighbor 192.168.10.1 remote-as 1
R2(config-router)#network 10.0.0.0 mask 255.0.0.0
D. R1(config)#router bgp 1
R1(config-router)#neighbor 10.2.2.2 remote-as 2
R1(config-router)#neighbor 10.2.2.2 update-source |o0
R1(config-router)#network 10.1.1.0 mask 255.255.255.0
R2(config)#router bgp 2
R2(config-router)#neighbor 10.1.1.1 remote-as 1
R2(config-router)#neighbor 10.1.1.1 update-source |o0
R2(config-router)#network 10.2.2.0 mask 255.255.255.0
55、Refer to the exhibit.
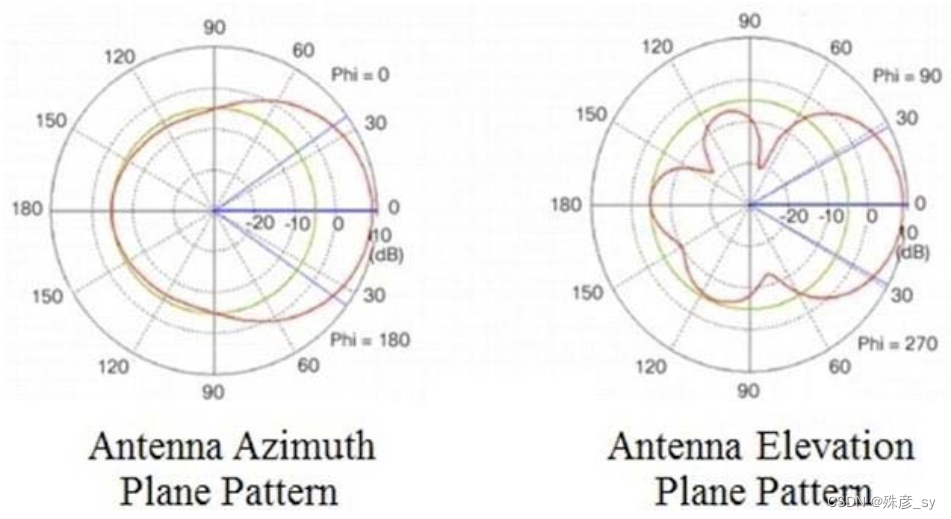
Which type of antenna do the radiation patterns present?
A. Yagi
B. patch
C. omnidirectional
D. dipole
56、Which method creates an EEM applet policy that is registered with EEM and runs on demand or manually?
A. event manager applet ondemand
event none
action 1.0 syslog priority critical msg ‘This is a message from ondemand’
B. event manager applet ondemand
action 1.0 syslog priority critical msg ‘This is a message from ondemand’
C. event manager applet ondemand
event register
action 1.0 syslog priority critical msg ‘This is a message from ondemand’
D. event manager applet ondemand
event manual
action 1.0 syslog priority critical msg ‘This is a message from ondemand’
57、An engineer is configuring local web authentication on a WLAN. The engineer chooses the Authentication radio button under the Layer 3 Security options for Web Policy.
Which device presents the web authentication for the WLAN?
A. ISE server
B. RADIUS server
C. anchor WLC
D. local WLC
58、Which controller is the single plane of management for Cisco SD-WAN?
A. vBond
B. vSmart
C. vManage
D. vEdge
59、A network is being migrated from IPv4 to IPv6 using a dual-stack approach. Network management is already 100% IPv6 enabled.
In a dual-stack network with two dual-stack NetFlow collectors, how many flow exporters are needed per network device in the flexible NetFlow configuration?
A. 1
B. 2
C. 4
D. 8
60、Which statement about TLS is true when using RESTCONF to write configurations on network devices?
A. It is used for HTTP and HTTPS requests.
B. It requires certificates for authentication.
C. It is provided using NGINX acting as a proxy web server.
D. It is not supported on Cisco devices.
61、Which reason could cause an OSPF neighborship to be in the EXSTART/EXCHANGE state?
A. mismatched OSPF link costs
B. mismatched OSPF network type
C. mismatched areas
D. mismatched MTU size
62、Which LISP device is responsible for publishing EID-to-RLOC mappings for a site?
A. ETR
B. MR
C. ITR
D. MS
63、Which method does the enable secret password option use to encrypt device passwords?
A. MD5
B. PAP
C. CHAP
D. AES
64、Which statement about agent-based versus agentless configuration management tools is true?
A. Agentless tools use proxy nodes to interface with slave nodes.
B. Agentless tools require no messaging systems between master and slaves.
C. Agent-based tools do not require a high-level language interpreter such as Python or Ruby on slave nodes.
D. Agent-based tools do not require installation of additional software packages on the slave nodes.
65、Which statement about Cisco Express Forwarding is true?
A. The CPU of a router becomes directly involved with packet switching decisions.
B. It uses a fast cache that is maintained in a router data plane.
C. It maintains two tables in the data plane: the FIB and adjacency table.
D. It makes forwarding decisions by a process that is scheduled through the IOS scheduler.
66、Refer to the exhibit.

What are two effects of this configuration? (Choose two.)
A. It establishes a one-to-one NAT translation.
B. The 209.165.201.0/27 subnet is assigned as the outside local address range.
C. The 10.1.1.0/27 subnet is assigned as the inside local addresses.
D. Inside source addresses are translated to the 209.165.201.0/27 subnet.
E. The 10.1.1.0/27 subnet is assigned as the inside global address range.
67、When configuring WPA2 Enterprise on a WLAN, which additional security component configuration is required?
A. PKI server
B. NTP server
C. RADIUS server
D. TACACS server
68、What is the structure of a JSON web token?
A. three parts separated by dots: header, payload, and signature
B. three parts separated by dots: version, header, and signature
C. header and payload
D. payload and signature
69、A response code of 404 is received while using the REST API on Cisco DNA Center to POST to this URI: /dna/intent/api/v1/template-programmer/project
What does the code mean?
A. The POST/PUT request was fulfilled and a new resource was created. Information about the resourceis in the response body.
B. The request was accepted for processing, but the processing was not completed.
C. The client made a request for a resource that does not exist.
D. The server has not implemented the functionality that is needed to fulfill the request.
70、What is a benefit of deploying an on-premises infrastructure versus a cloud infrastructure deployment?
A. ability to quickly increase compute power without the need to install additional hardware
B. less power and coding resources needed to run infrastructure on-premises
C. faster deployment times because additional infrastructure does not need to be purchased
D. lower latency between systems that are physically located near each other
71、A customer has several small branches and wants to deploy a Wi-Fi solution with local management using CAPWAP.
Which deployment model meets this requirement?
A. local mode
B. autonomous
C. SD-Access wireless
D. Mobility Express
72、Which two operations are valid for RESTCONF? (Choose two.)
A. PULL
B. PUSH
C. PATCH
D. REMOVE
E. ADD
F. HEAD
73、Refer to the exhibit
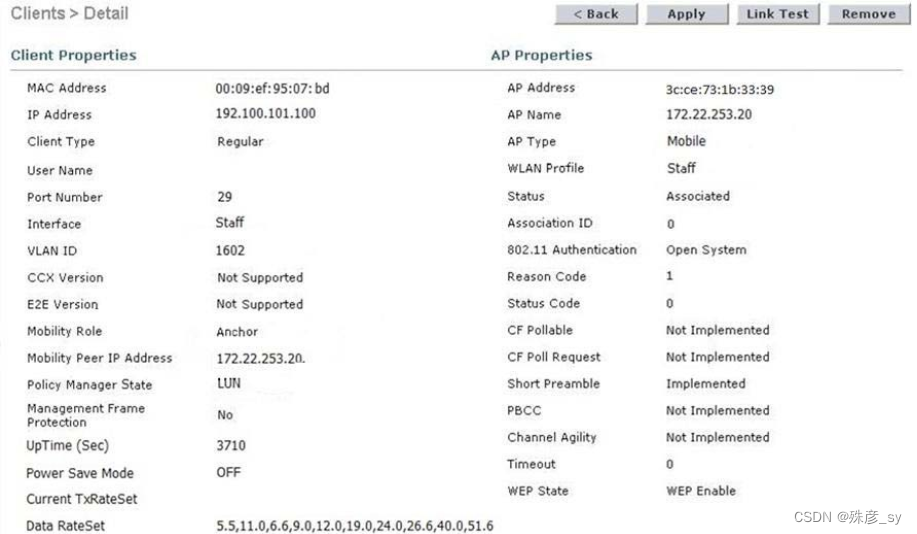
The WLC administrator sees that the controller to which a roaming client associates has Mobility Role Anchor configured under Clients > Detail.
Which type of roaming is supported?
A. indirect
B. Layer 3 intercontroller
C. intracontroller
D. Layer 2 intercontroller
74、In which part of the HTTP message is the content type specified?
A. HTTP method
B. body
C. header
D. URI
75、Which statement about VXLAN is true?
A. VXLAN encapsulates a Layer 2 frame in an IP-UDP header, which allows Layer 2 adjacency across router boundaries.
B. VXLAN uses the Spanning Tree Protocol for loop prevention.
C. VXLAN extends the Layer 2 Segment ID field to 24-bits, which allows up to 4094 unique Layer 2 segments over the same network.
D. VXLAN uses TCP as the transport protocol over the physical data center network.
76、What is the fact about Cisco EAP-FAST?
A. It requires a client certificate.
B. It is an IETF standard.
C. It does not require a RADIUS server certificate.
D. It operates in transparent mode.
77、What do Cisco DNA southbound APIs provide?
A. interface between the controller and the consumer
B. RESTful API interface for orchestrator communication
C. interface between the controller and the network devices
D. NETCONF API interface for orchestrator communication
78、Which DNS lookup does an access point perform when attempting CAPWAP discovery?
A. CISCO-CONTROLLER.local
B. CAPWAP-CONTROLLER.local
C. CISCO-CAPWAP-CONTROLLER.local
D. CISCO-DNA-CONTROLLER.local
79、Which TCP setting is tuned to minimize the risk of fragmentation on a GRE/IP tunnel?
A. MSS
B. MTU
C. MRU
D. window size
80、Which statement about an RSPAN session configuration is true?
A. Only one session can be configured at a time.
B. A special VLAN type must be used as the RSPAN destination.
C. A filter must be configured for RSPAN sessions.
D. Only incoming traffic can be monitored.
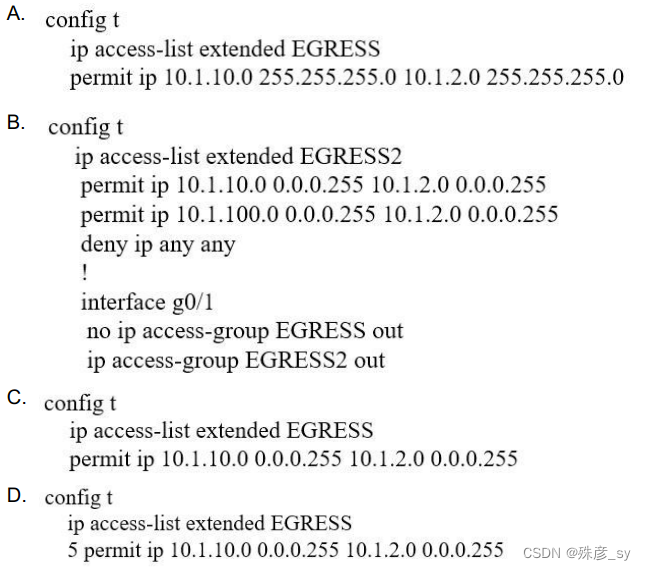
81、Refer to the exhibit.

An engineer must modify the access control list EGRESS to allow all IP traffic from subnet 10.1.10.0/24 to 10.1.2.0/24. The access control list is applied in the outbound direction on router interface GigabitEthernet 0/1.
Which configuration commands can the engineer use to allow this traffic without disrupting existing traffic flows? D
82、What is the role of a fusion router in an SD-Access solution?
A. acts as a DNS server
B. provides additional forwarding capacity to the fabric
C. performs route leaking between user-defined virtual networks and shared services
D. provides connectivity to external networks
83、Refer to the exhibit.
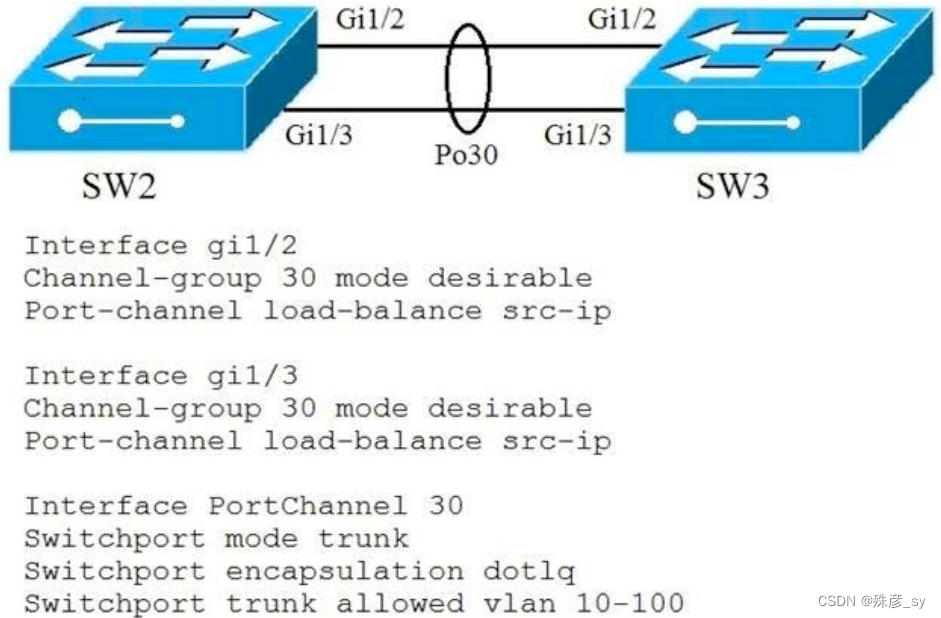
A port channel is configured between SW2 and SW3. SW2 is not running a Cisco operating system. When all physical connections are made, the port channel does not establish.
Based on the configuration except of SW3, what is the cause of the problem?
A. The port-channel mode should be set to auto.
B. The port channel on SW2 is using an incompatible protocol.
C. The port-channel trunk is not allowing the native VLAN.
D. The port-channel interface load balance should be set to src-mac.
84、What does this EEM applet event accomplish?
"event snmp oid 1.3.6.1.3.7.0.9.5.3.1.2.9 get-type next entry-op gt entry-val 75 poll-interval 5"
A. Upon the value reaching 75%, a SNMP event is generated and sent to the trap server.
B. It reads an SNMP variable, and when the value exceeds 75%, it triggers an action.
C. It issues email when the value is greater than 75% for five polling cycles.
D. It presents a SNMP variable that can be interrogated.
85、Which method displays text directly into the active console with a synchronous EEM applet policy?
A. event manager applet boom
event syslog pattern ‘UP’
action 1.0 syslog priority direct msg ‘logging directly to console’
B. event manager applet boom
event syslog pattern ‘UP’
action 1.0 gets ‘logging directly to console’
C. event manager applet boom
event syslog pattern ‘UP’
action 1.0 string ‘logging directly to console’
D. event manager applet boom
event syslog pattern ‘UP’
action 1.0 puts ‘logging directly to console’
86、Which two GRE features are configured to prevent fragmentation? (Choose two.)
A. TCP window size
B. IP MTU
C. TCP MSS
D. DF bit clear
E. MTU ignore
87、Which action is the vSmart controller responsible for in an SD-WAN deployment?
A. onboard vEdge nodes into the SD-WAN fabric
B. gather telemetry data from vEdge routers
C. distribute security information for tunnel establishment between vEdge routers
D. manage, maintain, and gather configuration and status for nodes within the SD-WAN fabric
88、what is fact about Cisco SD-access wireless network infrastructure deployments?
A. The access point is part of the fabric overlay.
B. The wireless client is part of the fabric overlay.
C. The access point is part of the fabric underlay.
D. The WLC is part of the fabric underlay.
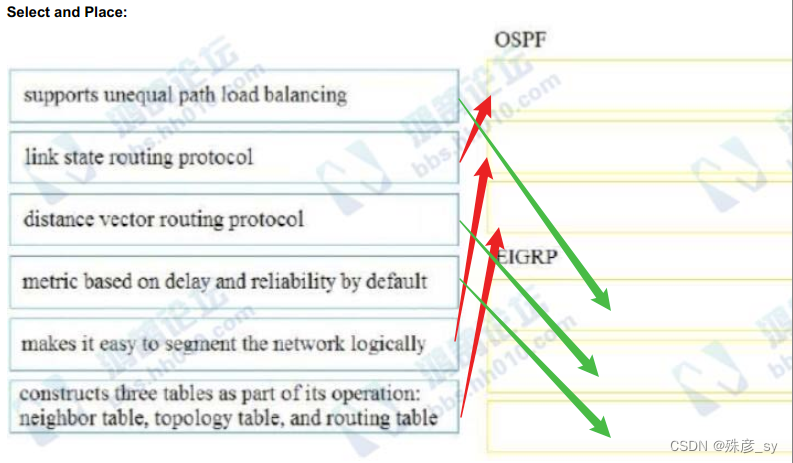
89、Which feature is supported by EIGRP but is not supported by OSPF?
A. route filtering
B. unequal-cost load balancing
C. route summarization
D. equal-cost load balancing
90、What is the correct EBGP path attribute list, ordered from most preferred to least preferred, that the BGP best-path algorithm uses?
A. local preference, weight, AS path, MED
B. weight, local preference, AS path, MED
C. weight, AS path, local preference, MED
D. local preference, weight, MED, AS path
91、At which layer does Cisco DNA Center support REST controls?
A. session layer
B. northbound APIs
C. EEM applets or scripts
D. YAML output from responses to API calls
92、On which protocol or technology is the fabric data plane based in Cisco SD-Access fabric?
A. VXLAN
B. LISP
C. Cisco TrustSec
D. IS-IS
93、What is the difference between the enable password and the enable secret password when service password encryption is enabled on an IOS device?
A. The enable secret password is protected via stronger cryptography mechanisms.
B. The enable password cannot be decrypted.
C. The enable password is encrypted with a stronger encryption method.
D. There is no difference and both passwords are encrypted identically.
94、Which access control list allows only TCP traffic with a destination port range of 22-443, excluding port 80?
A. deny tcp any any eq 80
permit tcp any any gt 21 lt 444
B. permit tcp any any range 22 443
deny tcp any any eq 80
C. permit tcp any any eq 80
D. deny tcp any any eq 80permit tcp any any range 22 443
95、Which statement describes the IP and MAC allocation requirements for virtual machines on Type 1 hypervisors?
A. Virtual machines do not require a unique IP or unique MAC. They share the IP and MAC address of the physical server.
B. Each virtual machine requires a unique IP address but shares the MAC address with the physical server.
C. Each virtual machine requires a unique IP and MAC addresses to be able to reach to other nodes.
D. Each virtual machine requires a unique MAC address but shares the IP address with the physical server.
96、A local router shows an EBGP neighbor in the Active state.
Which statement is true about the local router?
A. The local router is attempting to open a TCP session with the neighboring router.
B. The local router is receiving prefixes from the neighboring router and adding them in RIB-IN.
C. The local router has active prefixes in the forwarding table from the neighboring router.
D. The local router has BGP passive mode configured for the neighboring router.
97、Which feature must be configured to allow packet capture over Layer 3 infrastructure?
A. RSPAN
B. ERSPAN
C. VSPAN
D. IPSPAN
98、Drag and drop the descriptions from the left onto the correct QoS components on the right.


99、Drag and drop the characteristics from the left onto the correct infrastructure deployment types on the right.


100、Drag and drop the characteristics from the left onto the correct routing protocol types on the right.