文章目录
- 2023LaCTF
- EBE
- a hacker's notes
2023LaCTF
前言:
累了,没有话,下次一定
EBE
I was trying to send a flag to my friend over UDP, one character at a time, but it got corrupted! I think someone else was messing around with me and sent extra bytes, though it seems like they actually abided by RFC 3514 for once. Can you get the flag?
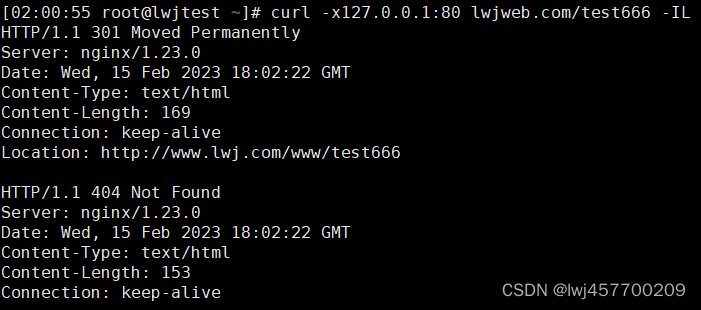
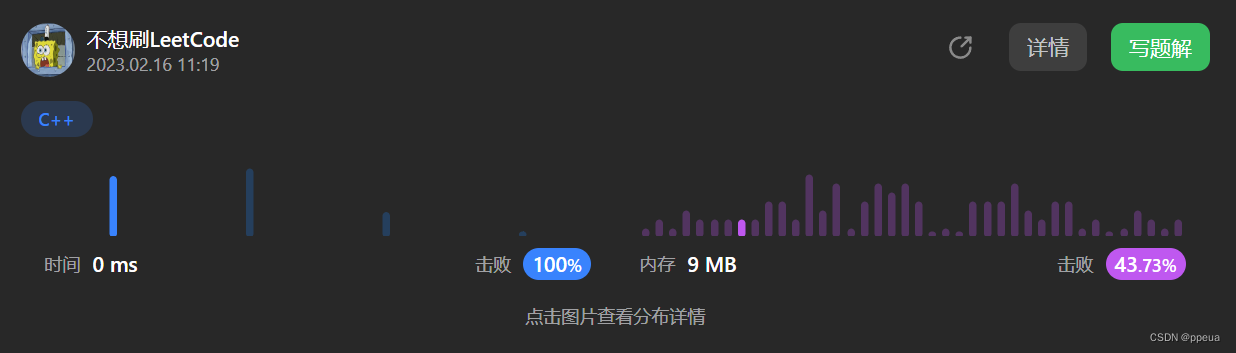
纵览整个流量包,追踪udp流发现可以直接得到明文

在观察每一个流的细节部分,只有两个地方被改变了
且,这两个的变化是一致的

ip.flags == 0x0 ip.checksum == 0x64c1
因此我们筛选任意一部分都是可以的
lactf{j03_4nd_j0S3phIn3_bRU1n_sAY_hi}
对于题目描述中的RFC 3514我其实是没有理解什么意思2333
那先这样吧
暂时over
a hacker’s notes
We managed to get ahold of a flash drive which we think contains the decryption keys for the ransomware that a hacker group tried to deploy on our computer network! However, it seems like the hacker encrypted the flash drive. We know that the organization uses passwords in the format hacker### (hacker + 3 digits) for their disks, but a much stronger encryption password once you login. Can you try to get access to their notes?
暂时放着,明天来写