目录
openssl的版本如下:
SM3使用实例
1. SM3的扎凑实例
SM2使用实例
1. 生成SM2密钥对
2.查看SM2密钥对
3.生成自签名证书
4.查看证书详情
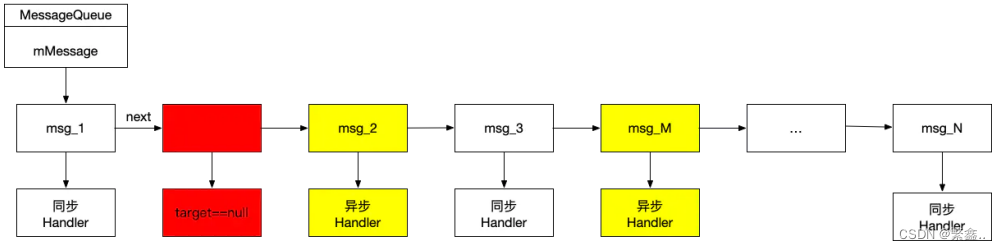
5.私钥签名消息
6.证书验证消息签名
SM4 使用实例
openssl的版本如下:
![]()
SM3使用实例
SM3是中华人民共和国政府采用的一种密码散列函数标准,由国家密码管理局于2010年12月17日发布。相关标准为“GM/T 0004-2012 《SM3密码杂凑算法》”。
1. SM3的扎凑实例
echo "adsfad" > plain.dat
openssl sm3 plain.dat
SM2使用实例
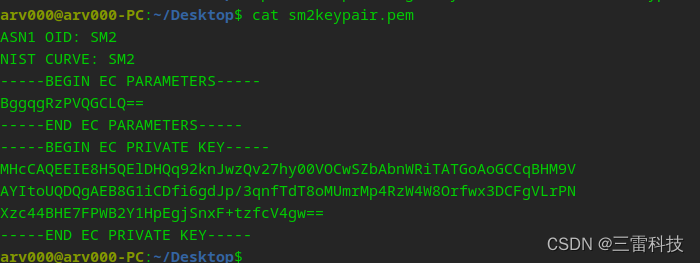
1. 生成SM2密钥对
openssl ecparam -genkey -name SM2 -out sm2keypair.pem -text2.查看SM2密钥对
openssl ecparam -in sm2keypair.pem -text3.生成自签名证书
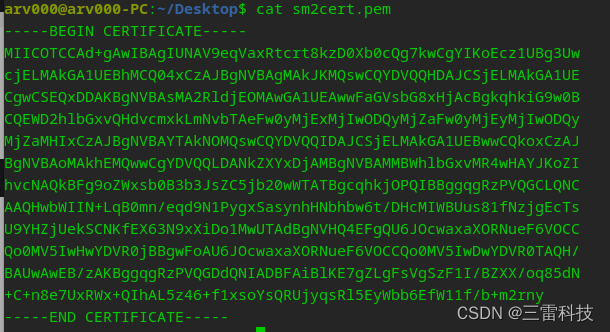
openssl req -x509 -key sm2keypair.pem -subj "/C=CN/ST=BJ/L=BJ/O=HD/OU=dev/CN=hello/emailAddress=hello@world.com" -out sm2cert.pem4.查看证书详情
openssl x509 -in sm2cert.pem -text执行结果如下:
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
34:05:7d:7a:a5:5a:c5:1b:5c:ae:df:24:cc:3d:17:6f:47:10:83:b9
Signature Algorithm: sm3WithSM2Sign
Issuer: C = CN, ST = BJ, L = BJ, O = HD, OU = dev, CN = hello, emailAddress = hello@world.com
Validity
Not Before: Nov 22 08:42:26 2022 GMT
Not After : Dec 22 08:42:26 2022 GMT
Subject: C = CN, ST = BJ, L = BJ, O = HD, OU = dev, CN = hello, emailAddress = hello@world.com
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:07:c1:b5:88:20:df:8b:a8:1d:26:9f:f7:aa:77:
d3:75:3f:28:31:49:ab:32:9e:11:cd:6e:16:f0:ea:
df:c3:1d:c3:08:58:15:2e:b3:cd:5f:37:38:e0:11:
c4:ec:53:d6:07:66:35:1e:91:20:8d:29:f1:17:eb:
73:7d:c5:78:83
ASN1 OID: SM2
NIST CURVE: SM2
X509v3 extensions:
X509v3 Subject Key Identifier:
E8:93:9C:C1:AC:5A:5C:E4:4D:B9:E1:7A:54:E0:82:42:8D:0C:57:92
X509v3 Authority Key Identifier:
keyid:E8:93:9C:C1:AC:5A:5C:E4:4D:B9:E1:7A:54:E0:82:42:8D:0C:57:92
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sm3WithSM2Sign
30:45:02:20:65:28:4e:e0:64:b8:05:b1:58:12:cc:5d:48:fc:
16:57:5f:fa:2a:f3:97:4d:f8:2f:a7:f1:ee:d4:c5:15:b1:f9:
02:21:00:be:73:e3:af:9f:d7:1b:28:62:c4:11:52:3c:aa:b1:
19:79:13:25:9b:6f:a1:1f:5b:5d:5f:fd:bf:a6:da:b9:f2
-----BEGIN CERTIFICATE-----
MIICOTCCAd+gAwIBAgIUNAV9eqVaxRtcrt8kzD0Xb0cQg7kwCgYIKoEcz1UBg3Uw
cjELMAkGA1UEBhMCQ04xCzAJBgNVBAgMAkJKMQswCQYDVQQHDAJCSjELMAkGA1UE
CgwCSEQxDDAKBgNVBAsMA2RldjEOMAwGA1UEAwwFaGVsbG8xHjAcBgkqhkiG9w0B
CQEWD2hlbGxvQHdvcmxkLmNvbTAeFw0yMjExMjIwODQyMjZaFw0yMjEyMjIwODQy
MjZaMHIxCzAJBgNVBAYTAkNOMQswCQYDVQQIDAJCSjELMAkGA1UEBwwCQkoxCzAJ
BgNVBAoMAkhEMQwwCgYDVQQLDANkZXYxDjAMBgNVBAMMBWhlbGxvMR4wHAYJKoZI
hvcNAQkBFg9oZWxsb0B3b3JsZC5jb20wWTATBgcqhkjOPQIBBggqgRzPVQGCLQNC
AAQHwbWIIN+LqB0mn/eqd9N1PygxSasynhHNbhbw6t/DHcMIWBUus81fNzjgEcTs
U9YHZjUekSCNKfEX63N9xXiDo1MwUTAdBgNVHQ4EFgQU6JOcwaxaXORNueF6VOCC
Qo0MV5IwHwYDVR0jBBgwFoAU6JOcwaxaXORNueF6VOCCQo0MV5IwDwYDVR0TAQH/
BAUwAwEB/zAKBggqgRzPVQGDdQNIADBFAiBlKE7gZLgFsVgSzF1I/BZXX/oq85dN
+C+n8e7UxRWx+QIhAL5z46+f1xsoYsQRUjyqsRl5EyWbb6EfW11f/b+m2rny
-----END CERTIFICATE-----5.私钥签名消息
msg.dat : 代签名数据
sm2keypair.pem:带签名私钥
openssl dgst -sm3 -sign sm2keypair.pem -out sm2_file.sign plain.dat6.证书验证消息签名
SM4 使用实例
SM4:(原名SMS4.0)是中华人民共和国政府采用的一种分组密码标准,由国家密码管理局于2012年3月21日发布。相关标准为“GM/T 0002-2012《SM4分组密码算法》(原SMS4分组密码算法)”。
echo "asdf" | openssl sm4-cbc > ci.bin
enter sm4-cbc encryption password:
Verifying - enter sm4-cbc encryption password:
*** WARNING : deprecated key derivation used.
Using -iter or -pbkdf2 would be better.
openssl sm4-cbc -d -in ci.bin
enter sm4-cbc decryption password:
*** WARNING : deprecated key derivation used.
Using -iter or -pbkdf2 would be better.
asdf